Chapter 11 User Datagram Protocol UDP MiJung Choi



- Slides: 39

Chapter 11 User Datagram Protocol (UDP) Mi-Jung Choi Dept. of Computer Science and Engineering mjchoi@postech. ac. kr 1

Contents 11. 1 PROCESS-TO-PROCESS COMMUNICATION 11. 2 USER DATAGRAM 11. 3 CHECKSUM 11. 4 UDP OPERATION 11. 5 USE OF UDP 11. 6 UDP PACKAGE 2

Objectives o Be able to explain process-to-process communication o Know the format of a UDP user datagram o Be able to calculate a UDP checksum o Understand the operation of UDP o Know when it is appropriate to use UDP o Understand the modules in a UDP package 3

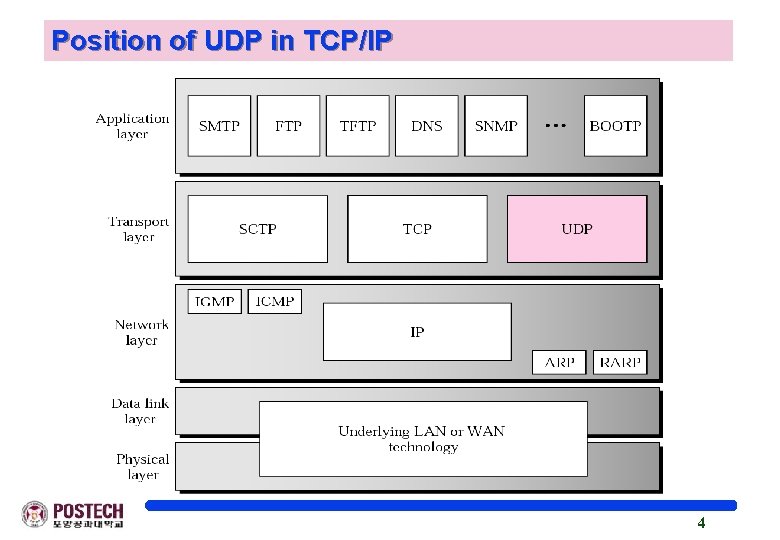
Position of UDP in TCP/IP 4

UDP protocol duties o To create a process-to-process communication: UDP port number o Error control to some extent If UDP detects an error in the received packet, it silently drops it o No flow control and no acknowledgement for received data o Connectionless, unreliable transport protocol o A very simple protocol using minimum overhead The disadvantages come some advantages o Sending a small messages b/w UDP 5

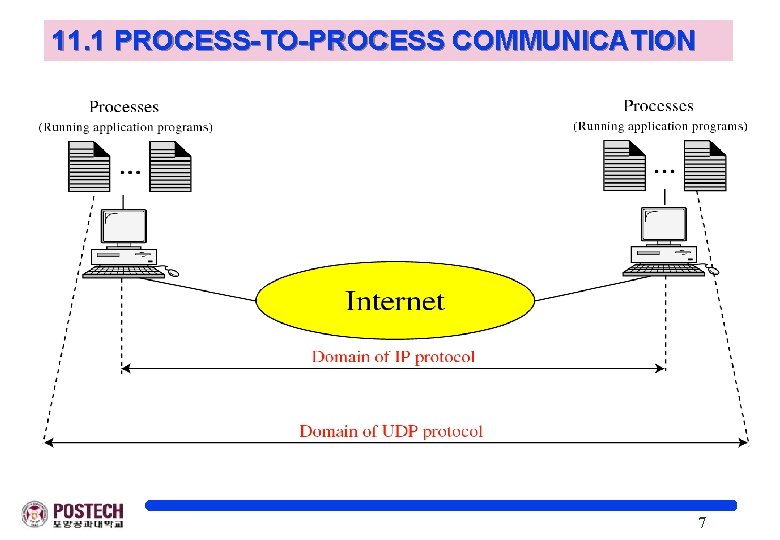
11. 1 PROCESS-TO-PROCESS COMMUNICATION o Before we examine UDP, we must first understand host-to-host communication and process-to-process communication and the difference between them. o The topics discussed in this section include: Port Numbers Socket Addresses 6

11. 1 PROCESS-TO-PROCESS COMMUNICATION 7

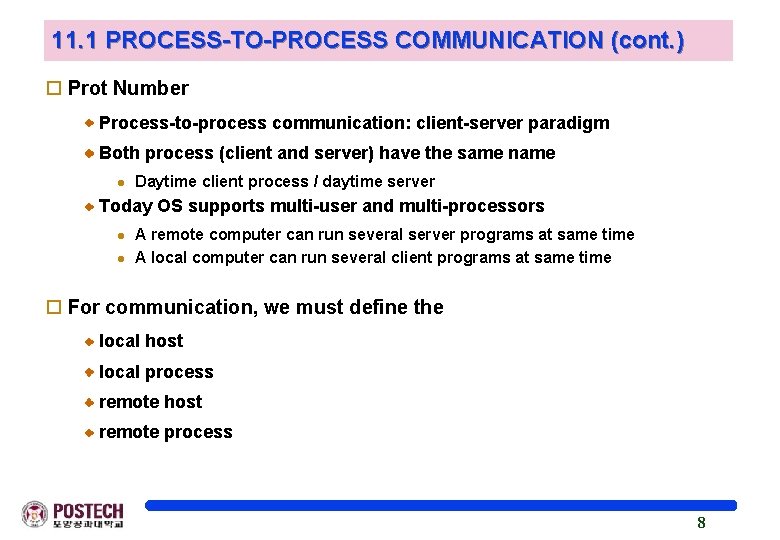
11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o Prot Number Process-to-process communication: client-server paradigm Both process (client and server) have the same name l Daytime client process / daytime server Today OS supports multi-user and multi-processors l l A remote computer can run several server programs at same time A local computer can run several client programs at same time o For communication, we must define the local host local process remote host remote process 8

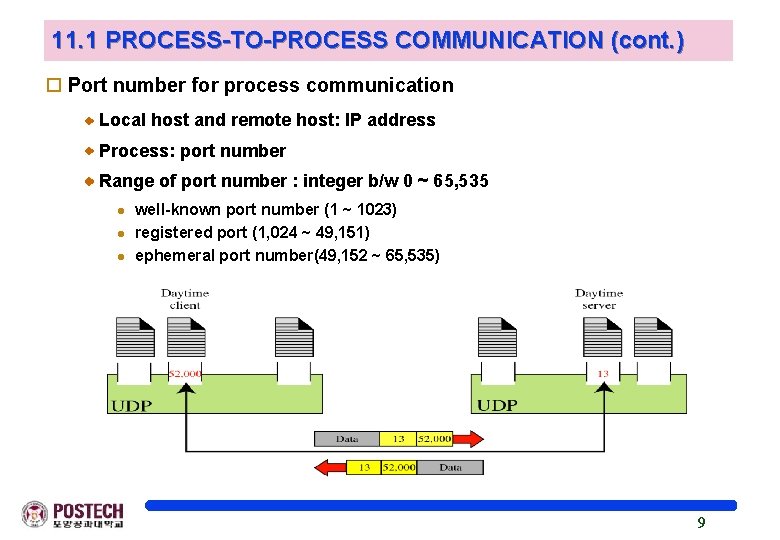
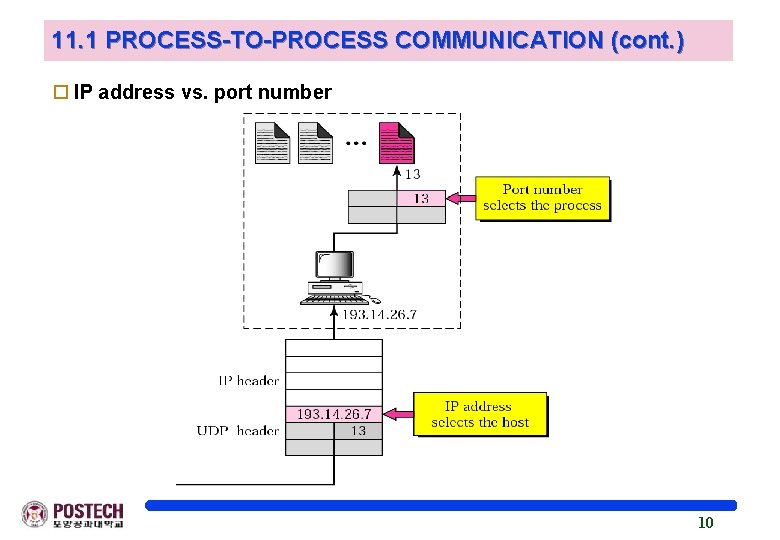
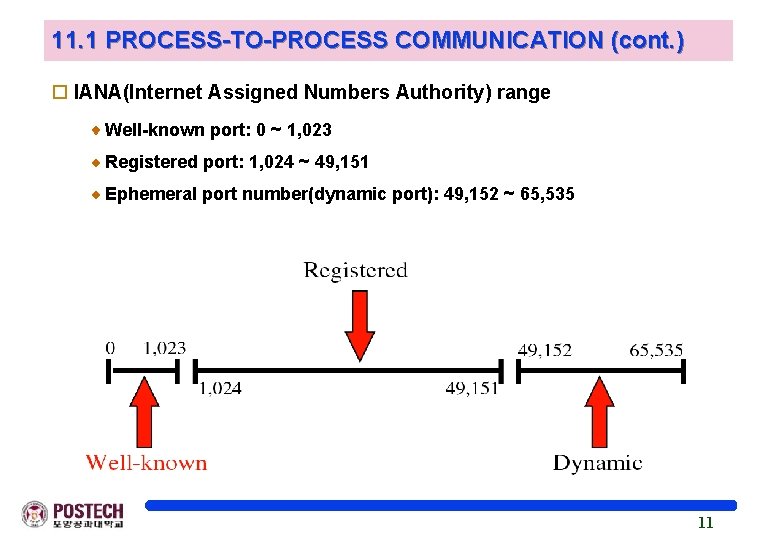
11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o Port number for process communication Local host and remote host: IP address Process: port number Range of port number : integer b/w 0 ~ 65, 535 l l l well-known port number (1 ~ 1023) registered port (1, 024 ~ 49, 151) ephemeral port number(49, 152 ~ 65, 535) 9

11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o IP address vs. port number 10

11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o IANA(Internet Assigned Numbers Authority) range Well-known port: 0 ~ 1, 023 Registered port: 1, 024 ~ 49, 151 Ephemeral port number(dynamic port): 49, 152 ~ 65, 535 11

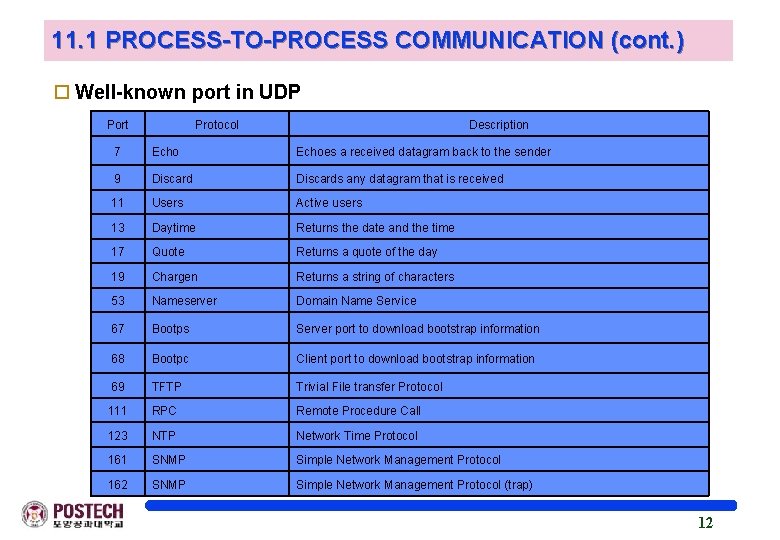
11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o Well-known port in UDP Port Protocol Description 7 Echoes a received datagram back to the sender 9 Discards any datagram that is received 11 Users Active users 13 Daytime Returns the date and the time 17 Quote Returns a quote of the day 19 Chargen Returns a string of characters 53 Nameserver Domain Name Service 67 Bootps Server port to download bootstrap information 68 Bootpc Client port to download bootstrap information 69 TFTP Trivial File transfer Protocol 111 RPC Remote Procedure Call 123 NTP Network Time Protocol 161 SNMP Simple Network Management Protocol 162 SNMP Simple Network Management Protocol (trap) 12

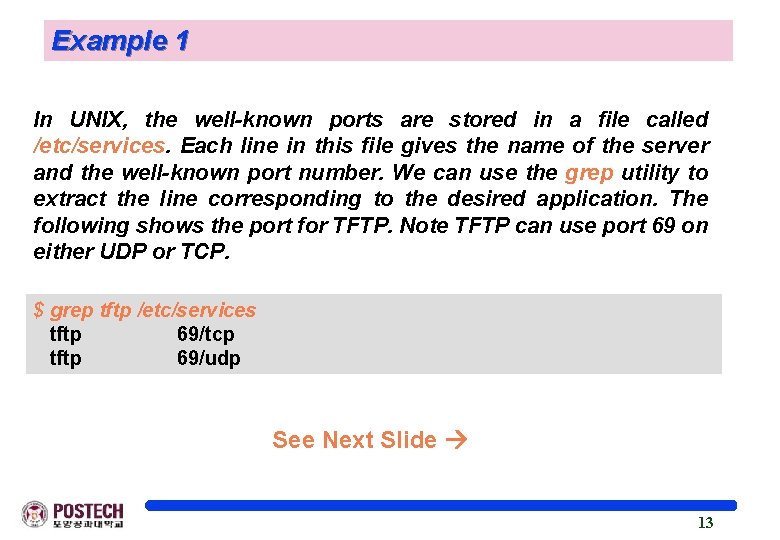
Example 1 In UNIX, the well-known ports are stored in a file called /etc/services. Each line in this file gives the name of the server and the well-known port number. We can use the grep utility to extract the line corresponding to the desired application. The following shows the port for TFTP. Note TFTP can use port 69 on either UDP or TCP. $ grep tftp /etc/services tftp 69/tcp tftp 69/udp See Next Slide 13

Example 1 (cont. ) SNMP uses two port numbers (161 and 162), each for a different purpose, as we will see in Chapter 21 $ grep snmp /etc/services snmp 161/tcp snmp 161/udp snmptrap 162/udp #Simple Net Mgmt Proto #Traps for SNMP 14

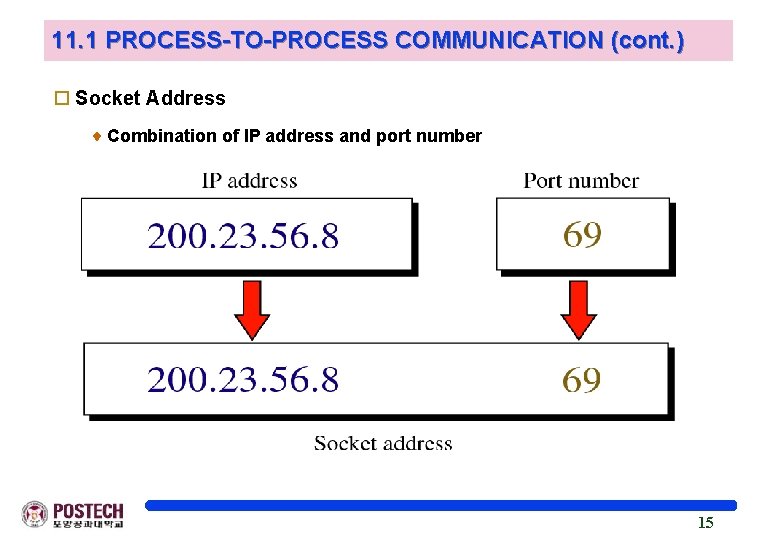
11. 1 PROCESS-TO-PROCESS COMMUNICATION (cont. ) o Socket Address Combination of IP address and port number 15

11. 2 USER DATAGRAM o UDP packets are called user datagrams and have a fixed-size header of 8 bytes. UDP length = IP length − IP header’s length 16

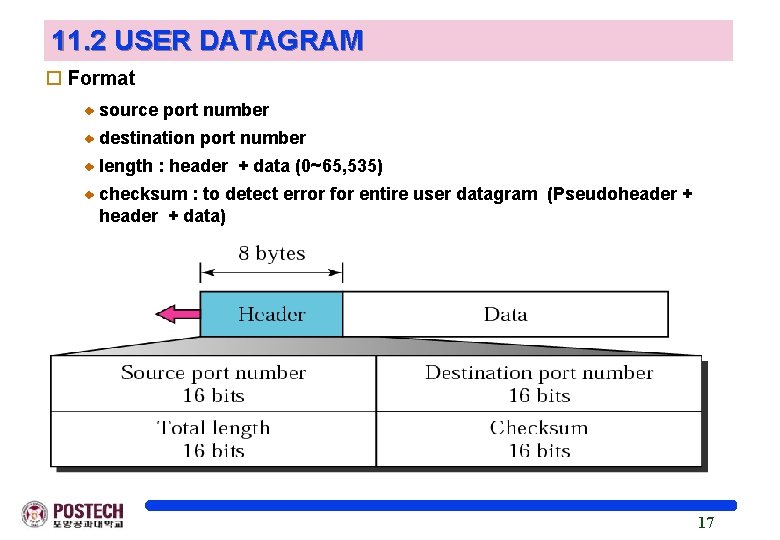
11. 2 USER DATAGRAM o Format source port number destination port number length : header + data (0~65, 535) checksum : to detect error for entire user datagram (Pseudoheader + data) 17

11. 3 CHECKSUM UDP checksum calculation is different from the one for IP and ICMP. Here the checksum includes three sections: a pseudoheader, the UDP header, and the data coming from the application layer. The topics discussed in this section include: Checksum Calculation at Sender Checksum Calculation at Receiver Optional Use of the Checksum 18

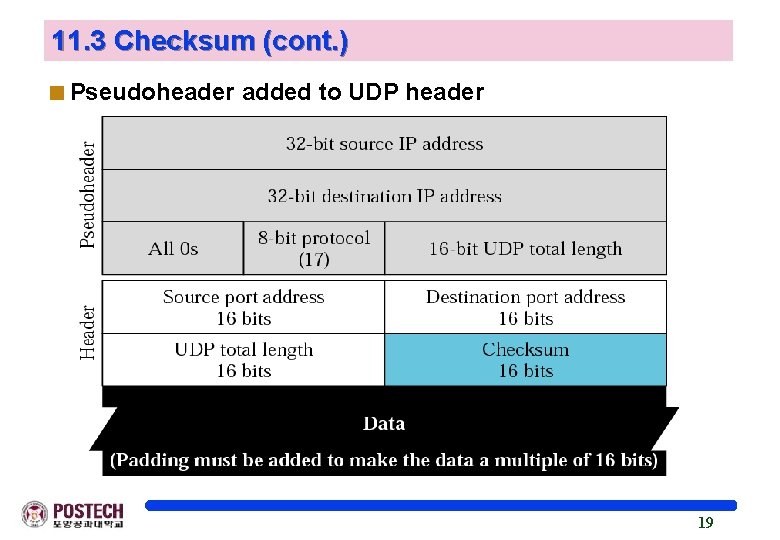
11. 3 Checksum (cont. ) <Pseudoheader added to UDP header 19

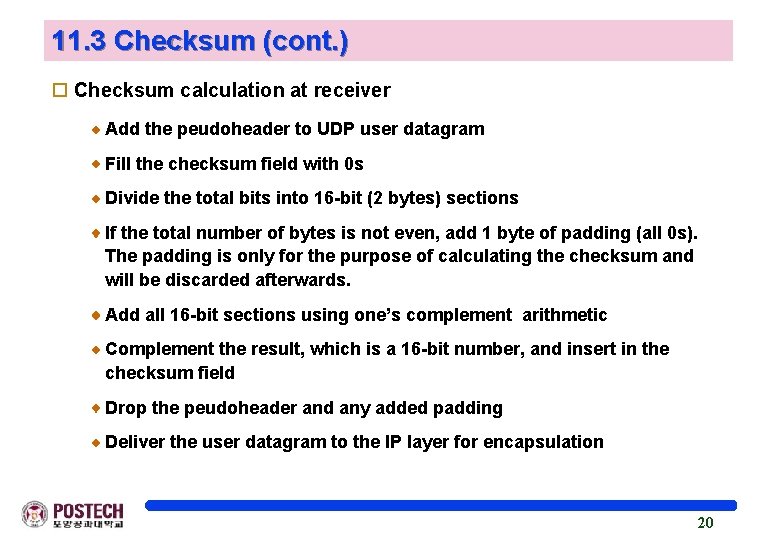
11. 3 Checksum (cont. ) o Checksum calculation at receiver Add the peudoheader to UDP user datagram Fill the checksum field with 0 s Divide the total bits into 16 -bit (2 bytes) sections If the total number of bytes is not even, add 1 byte of padding (all 0 s). The padding is only for the purpose of calculating the checksum and will be discarded afterwards. Add all 16 -bit sections using one’s complement arithmetic Complement the result, which is a 16 -bit number, and insert in the checksum field Drop the peudoheader and any added padding Deliver the user datagram to the IP layer for encapsulation 20

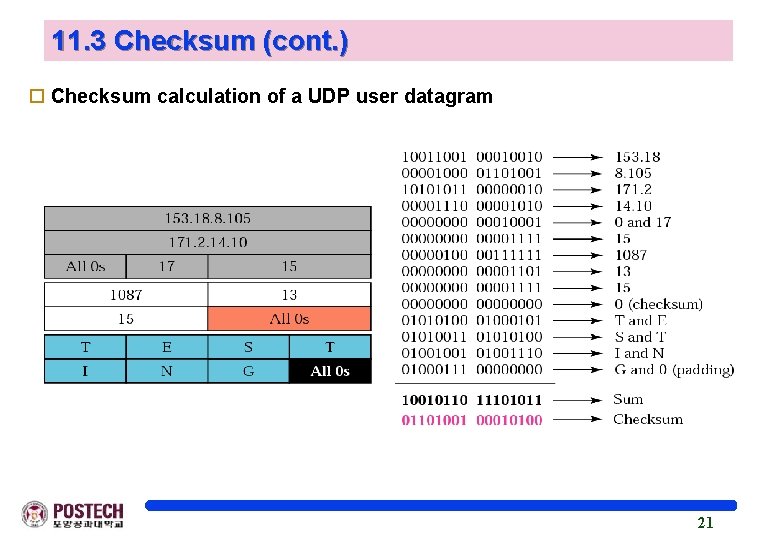
11. 3 Checksum (cont. ) o Checksum calculation of a UDP user datagram 21

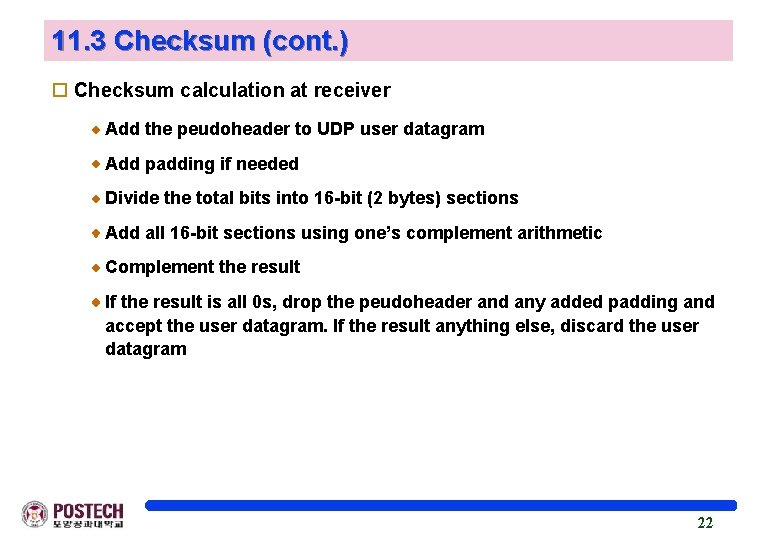
11. 3 Checksum (cont. ) o Checksum calculation at receiver Add the peudoheader to UDP user datagram Add padding if needed Divide the total bits into 16 -bit (2 bytes) sections Add all 16 -bit sections using one’s complement arithmetic Complement the result If the result is all 0 s, drop the peudoheader and any added padding and accept the user datagram. If the result anything else, discard the user datagram 22

11. 4 UDP OPERATION UDP uses concepts common to the transport layer. These concepts will be discussed here briefly, and then expanded in the next chapter on the TCP protocol. The topics discussed in this section include: Connectionless Services Flow and Error Control Encapsulation and Decapsulation Queuing Multiplexing and Demultiplexing 23

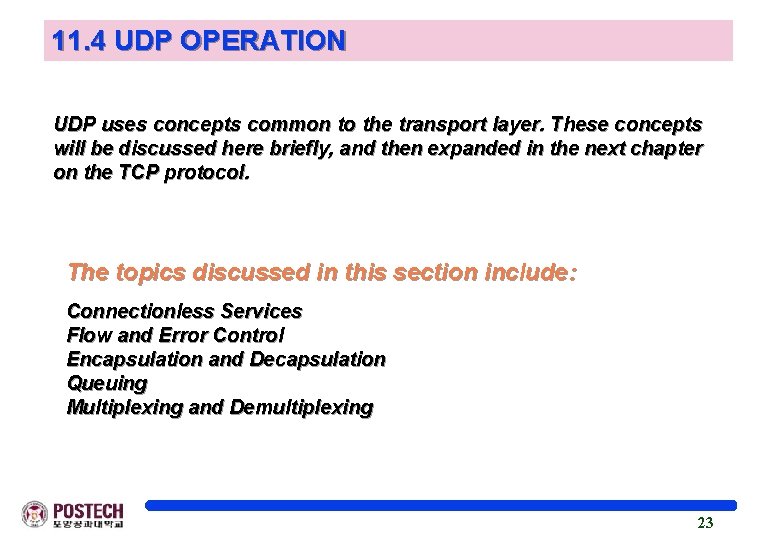
11. 4 UDP OPERATION o Connectionless services o No flow control and a simple error check o Encapsulation and Decapsulation 24

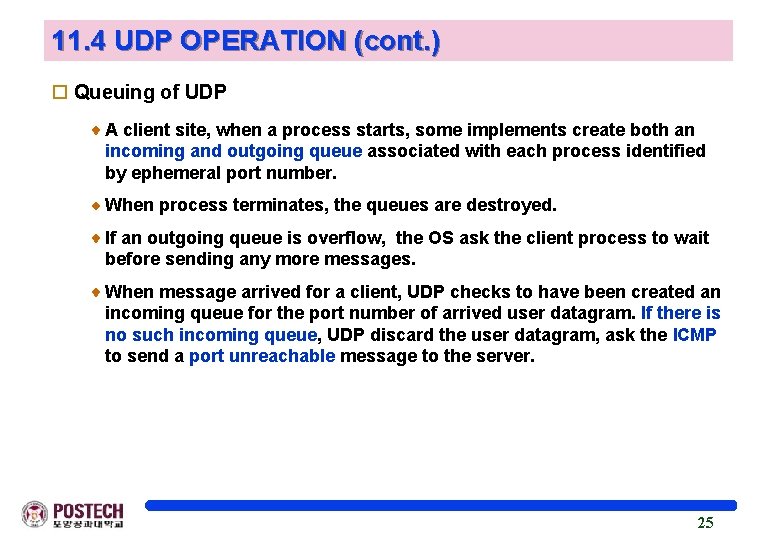
11. 4 UDP OPERATION (cont. ) o Queuing of UDP A client site, when a process starts, some implements create both an incoming and outgoing queue associated with each process identified by ephemeral port number. When process terminates, the queues are destroyed. If an outgoing queue is overflow, the OS ask the client process to wait before sending any more messages. When message arrived for a client, UDP checks to have been created an incoming queue for the port number of arrived user datagram. If there is no such incoming queue, UDP discard the user datagram, ask the ICMP to send a port unreachable message to the server. 25

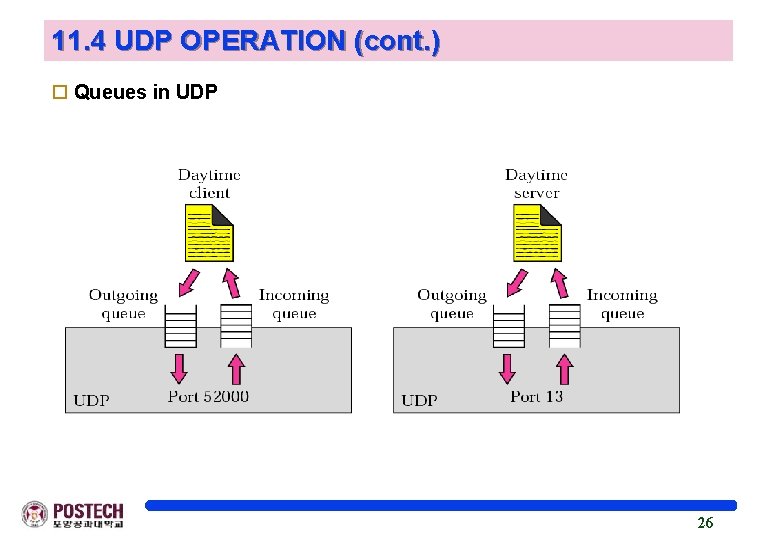
11. 4 UDP OPERATION (cont. ) o Queues in UDP 26

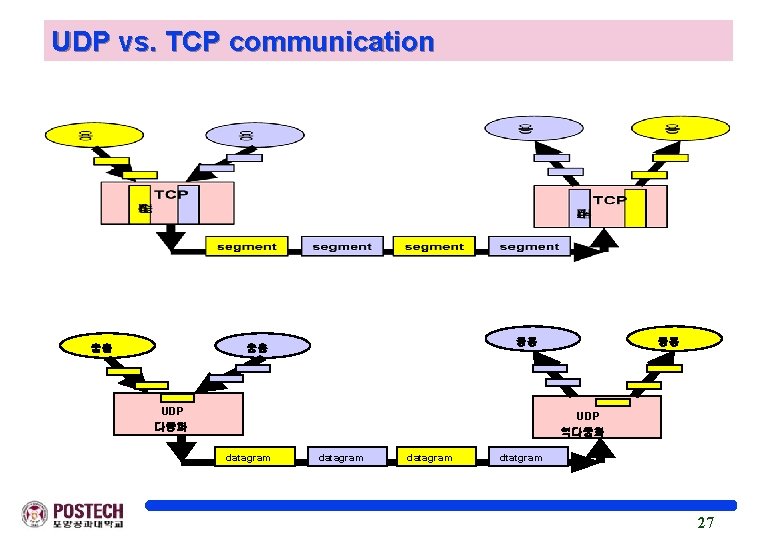
UDP vs. TCP communication 응용 응용 응용 UDP 다중화 응용 UDP 역다중화 datagram dtatgram 27

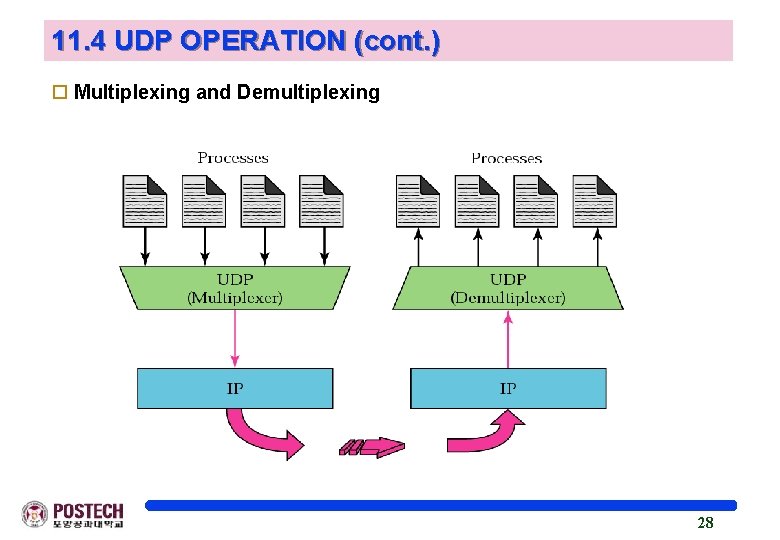
11. 4 UDP OPERATION (cont. ) o Multiplexing and Demultiplexing 28

11. 5 USE OF UDP o A simple request-response communication with little concern for flow and error control (not to send bulk data: ftp…) o A process with internal flow and error control mechanism. o Transport protocol for multicasting and broadcasting. o For management process such as SNMP o For some route updating protocols such as RIP (Routing Information Protocol) 29

11. 6 UDP PACKAGE o To show UDP handles the sending and receiving of UDP packets, we present a simple version of the UDP package. The UDP package involves five components: a control-block table, input queues, a control-block module, an input module, and an output module. The topics discussed in this section include: Control-Block Table Input queue Control-block module Input module Output module 30

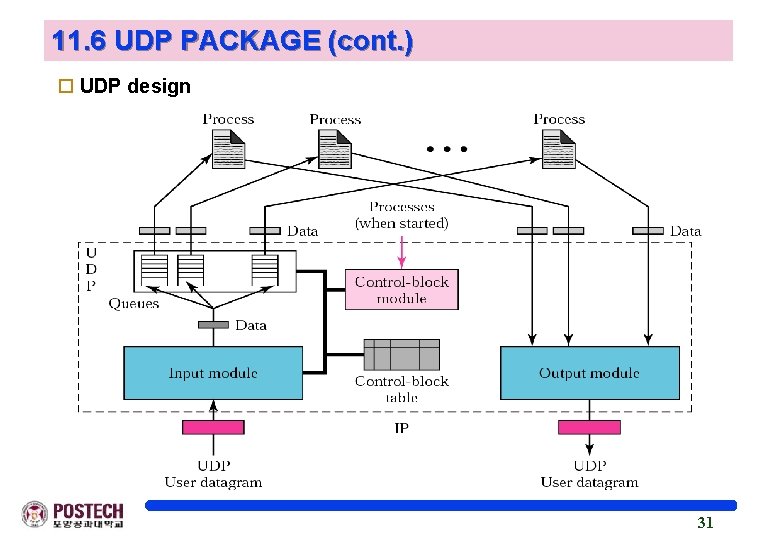
11. 6 UDP PACKAGE (cont. ) o UDP design 31

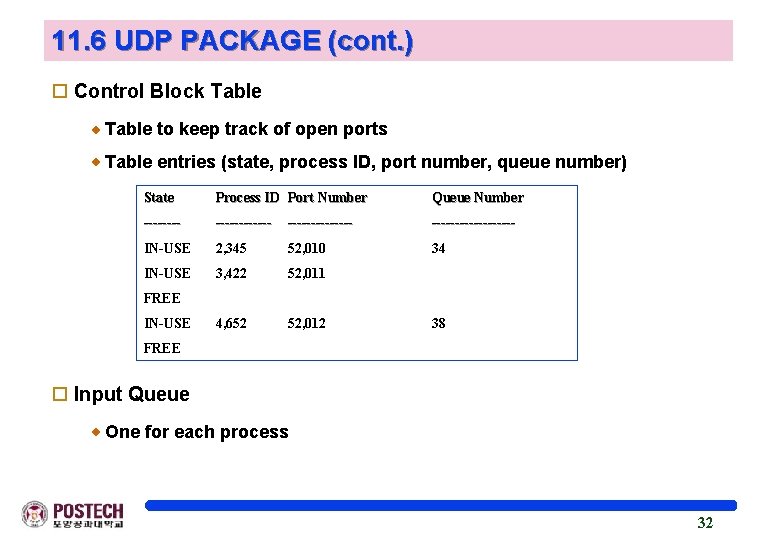
11. 6 UDP PACKAGE (cont. ) o Control Block Table to keep track of open ports Table entries (state, process ID, port number, queue number) State Process ID Port Number Queue Number -------------- IN-USE 2, 345 52, 010 34 IN-USE 3, 422 52, 011 4, 652 52, 012 FREE IN-USE 38 FREE o Input Queue One for each process 32

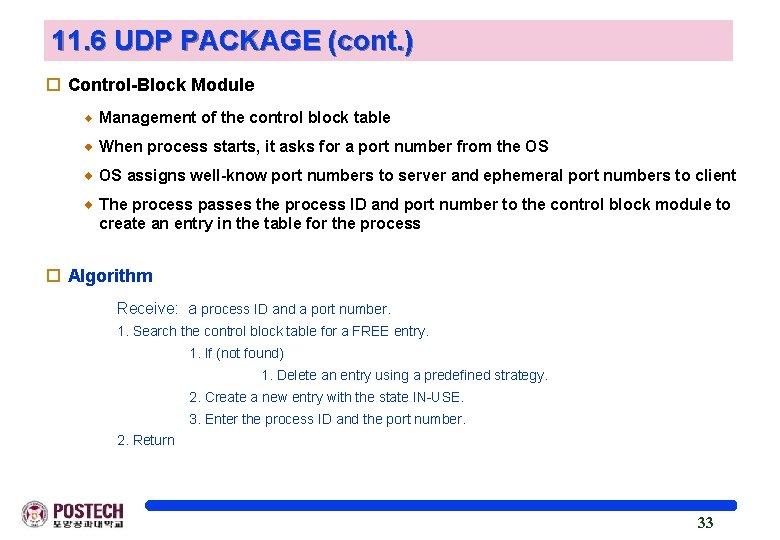
11. 6 UDP PACKAGE (cont. ) o Control-Block Module Management of the control block table When process starts, it asks for a port number from the OS OS assigns well-know port numbers to server and ephemeral port numbers to client The process passes the process ID and port number to the control block module to create an entry in the table for the process o Algorithm Receive: a process ID and a port number. 1. Search the control block table for a FREE entry. 1. If (not found) 1. Delete an entry using a predefined strategy. 2. Create a new entry with the state IN-USE. 3. Enter the process ID and the port number. 2. Return 33

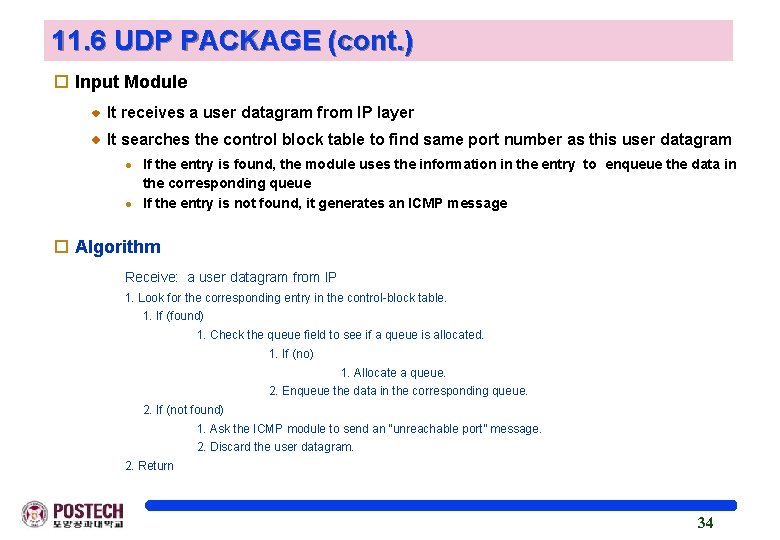
11. 6 UDP PACKAGE (cont. ) o Input Module It receives a user datagram from IP layer It searches the control block table to find same port number as this user datagram l l If the entry is found, the module uses the information in the entry to enqueue the data in the corresponding queue If the entry is not found, it generates an ICMP message o Algorithm Receive: a user datagram from IP 1. Look for the corresponding entry in the control-block table. 1. If (found) 1. Check the queue field to see if a queue is allocated. 1. If (no) 1. Allocate a queue. 2. Enqueue the data in the corresponding queue. 2. If (not found) 1. Ask the ICMP module to send an “unreachable port” message. 2. Discard the user datagram. 2. Return 34

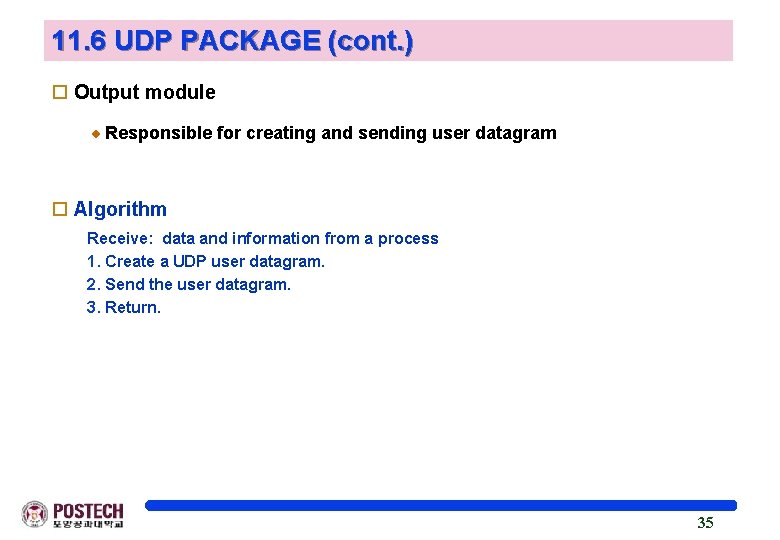
11. 6 UDP PACKAGE (cont. ) o Output module Responsible for creating and sending user datagram o Algorithm Receive: data and information from a process 1. Create a UDP user datagram. 2. Send the user datagram. 3. Return. 35

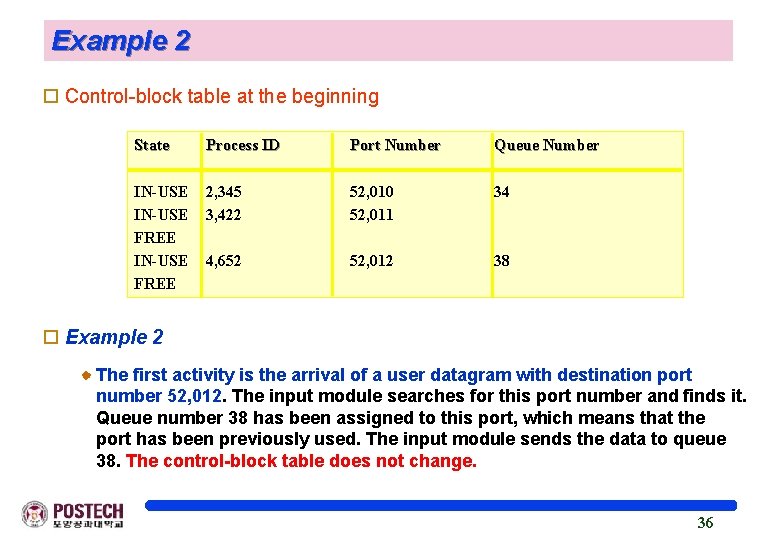
Example 2 o Control-block table at the beginning State -------IN-USE FREE Process ID ------2, 345 3, 422 Port Number -------52, 010 52, 011 Queue Number ---------34 4, 652 52, 012 38 o Example 2 The first activity is the arrival of a user datagram with destination port number 52, 012. The input module searches for this port number and finds it. Queue number 38 has been assigned to this port, which means that the port has been previously used. The input module sends the data to queue 38. The control-block table does not change. 36

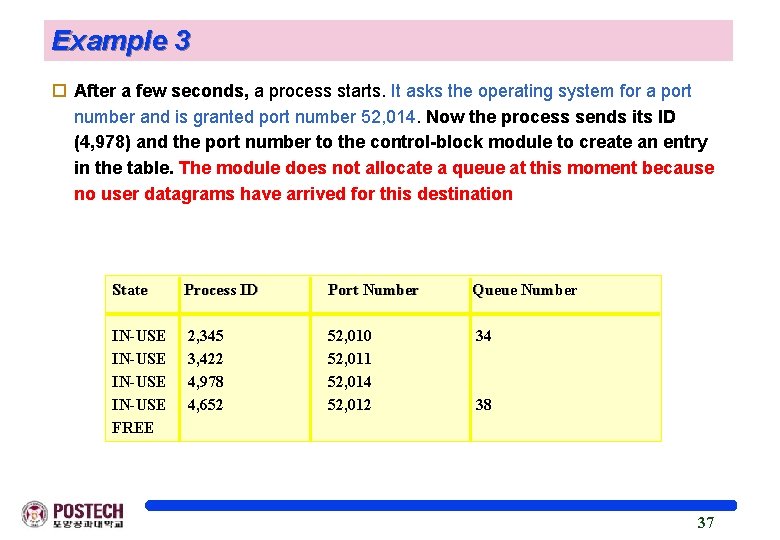
Example 3 o After a few seconds, a process starts. It asks the operating system for a port number and is granted port number 52, 014. Now the process sends its ID (4, 978) and the port number to the control-block module to create an entry in the table. The module does not allocate a queue at this moment because no user datagrams have arrived for this destination State -------IN-USE FREE Process ID ------2, 345 3, 422 4, 978 4, 652 Port Number -------52, 010 52, 011 52, 014 52, 012 Queue Number ---------34 38 37

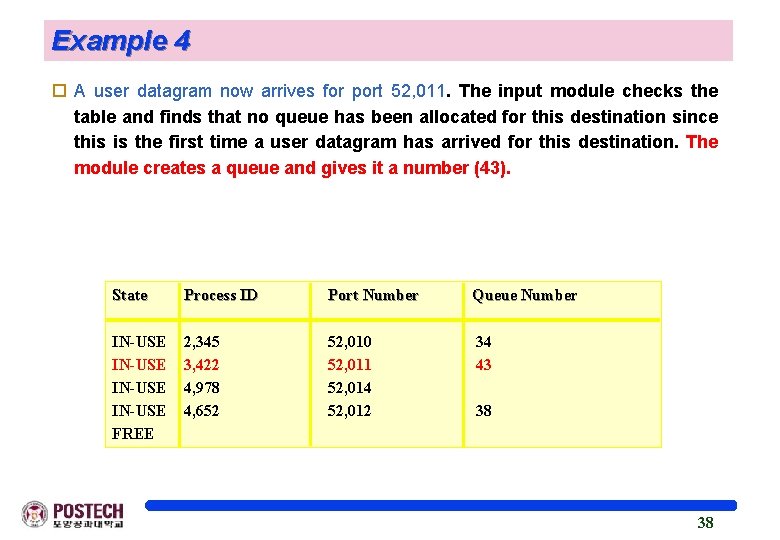
Example 4 o A user datagram now arrives for port 52, 011. The input module checks the table and finds that no queue has been allocated for this destination since this is the first time a user datagram has arrived for this destination. The module creates a queue and gives it a number (43). State -------IN-USE FREE Process ID ------2, 345 3, 422 4, 978 4, 652 Port Number -------52, 010 52, 011 52, 014 52, 012 Queue Number ---------34 43 38 38

Examples 5 & 6 o Example 5: After a few seconds, a user datagram arrives for port 52, 222. The input module checks the table and cannot find the entry for this destination. The user datagram is dropped and a request is made to ICMP to send an “unreachable port” message to the source. o Example 6: After a few seconds, a process needs to send a user datagram. It delivers the data to the output module which adds the UDP header and sends it. 39