User Datagram Protocol UDP Chapter 11 Know TCPIP








- Slides: 23

User Datagram Protocol (UDP) Chapter 11

Know TCP/IP transfers datagrams around n n Forwarded based on destination’s IP address At IP layer, destination address identifies host Made no further distinction about which application on the host gets the datagram This chapter extends TCP/IP protocol suite n n Adds mechanism to distinguish among hosts Multiple applications on a given computer can send and receive datagrams independently

The Ultimate Destination Most OSs support multiprogramming n n n Multiple applications execute simultaneously In OS terms, each executing program is a process, task, application program, or user level process Systems are called multitasking systems

Is a process the ultimate destination? n Seems natural; but is a bit misleading Processes are created and destroyed dynamically Want to replace processes without notifying senders Want to identify destinations by function n Not by process that implements them Single process may handle multiple functions n n Want process to decide which function the sender wants So, we will abstract the problem Imagine each machine has a set of protocol ports Each port identified by a positive integer Local OS provides means to specify or access a port

Most OS’s provide synchronous port access n Computation stops during port access operation Block process extracting data if no data there Most ports are buffered n Puts waiting data in a finite queue To communicate with a foreign port n n Sender must know IP address & protocol port # Messages must carry Destination port on the machine receiving the msg Source port on the machine sending the msg

User Datagram Protocol (UDP) Provides primary mechanism for application programs to swap datagrams n n n Provides protocol ports to distinguish among multiple executing programs Uses IP to transport messages between machines Provides same unreliable, connectionless image No acknowledgements; no ordering of incoming msgs No feedback for rate control; can lose messages

n Application programs have full responsibility for: Reliability Message loss Duplication Out-of-order delivery Loss of connectivity n Unfortunately, most application programmers ignore this responsibility Testing is usually done in controlled, reliable LANs Fail dramatically when used in TCP/IP internet

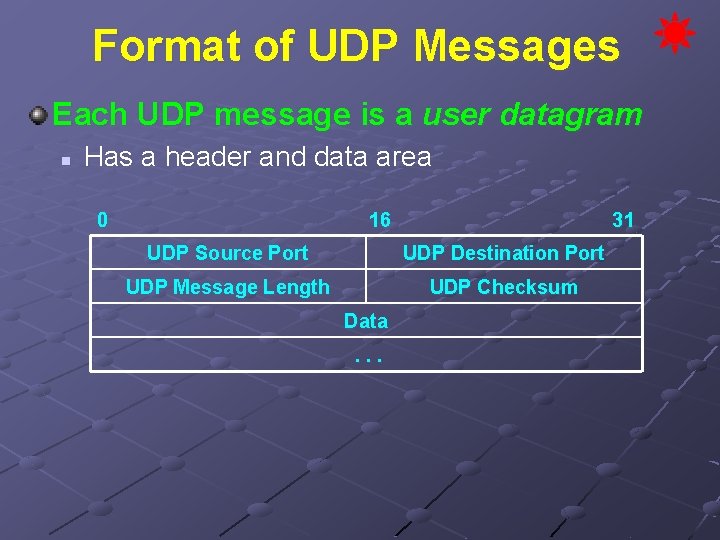
Format of UDP Messages Each UDP message is a user datagram n Has a header and data area 0 16 31 UDP Source Port UDP Destination Port UDP Message Length UDP Checksum Data. . .

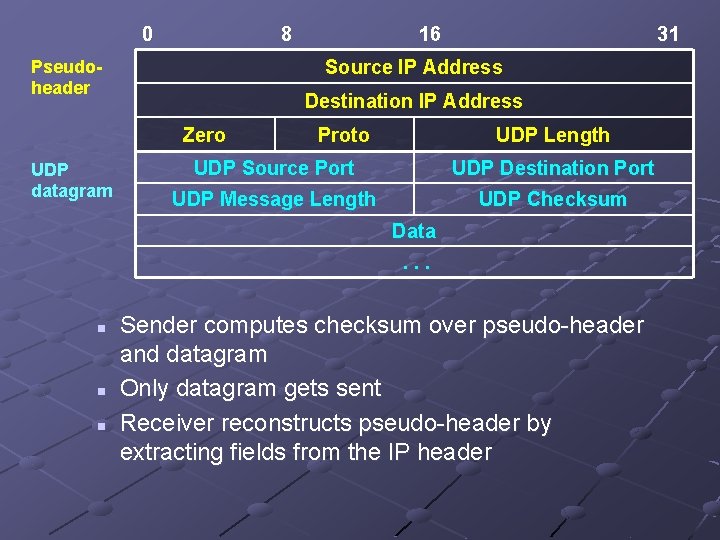
UDP Pseudo-Header Checksum can cover data in datagram n n Need to ensure more than that Datagram only has protocol port number Correct destination includes specific machine Want to compute checksum on destination IP as well as UDP datagram Constructs pseudo-header and includes in checksum computation

0 8 31 Source IP Address Pseudoheader Destination IP Address Zero UDP datagram 16 Proto UDP Length UDP Source Port UDP Destination Port UDP Message Length UDP Checksum Data. . . n n n Sender computes checksum over pseudo-header and datagram Only datagram gets sent Receiver reconstructs pseudo-header by extracting fields from the IP header

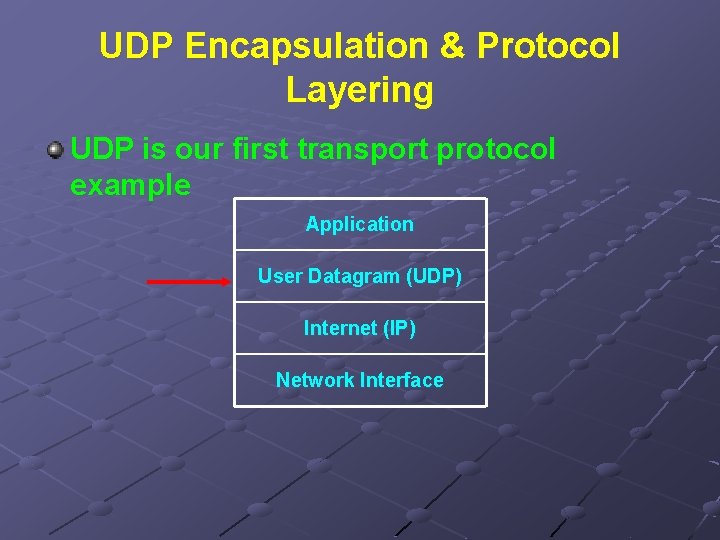
UDP Encapsulation & Protocol Layering UDP is our first transport protocol example Application User Datagram (UDP) Internet (IP) Network Interface

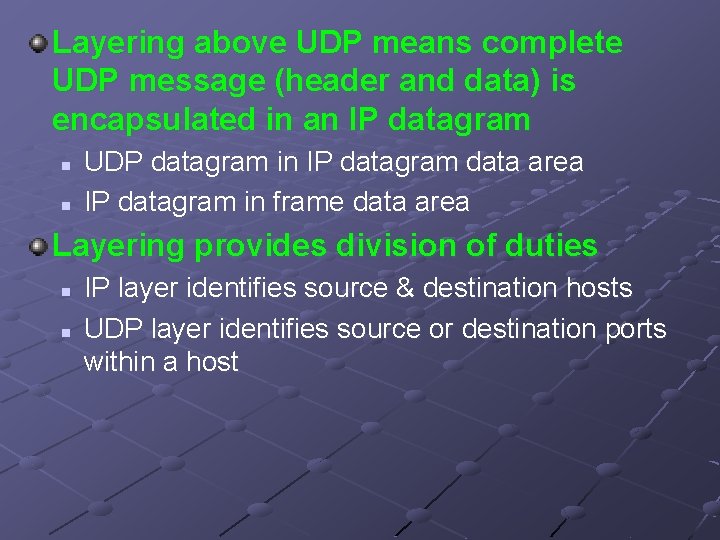
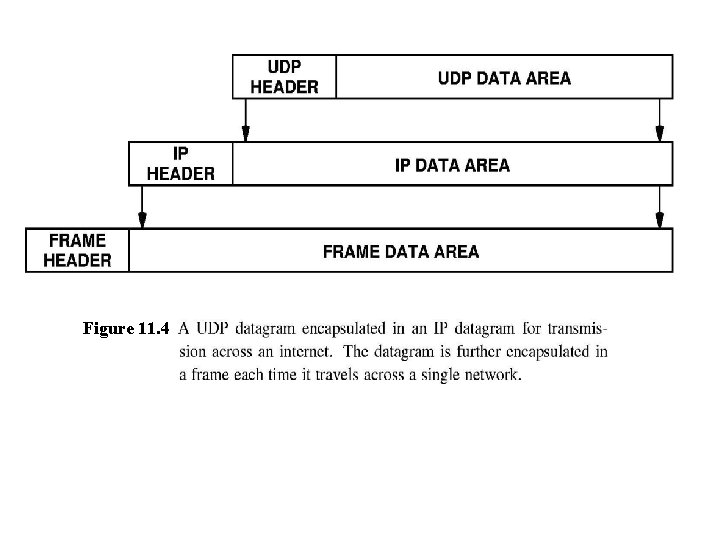
Layering above UDP means complete UDP message (header and data) is encapsulated in an IP datagram n n UDP datagram in IP datagram data area IP datagram in frame data area Layering provides division of duties n n IP layer identifies source & destination hosts UDP layer identifies source or destination ports within a host

Figure 11. 4

Layering & UDP Checksum Violation of layering rules with checksum n Pseudo-header needs source & dest IP address UDP must interact with IP layer to get these Regardless of method, still interacts n Violates separation of functionality by layering UDP is tightly integrated with IP Compromise made for practical reasons

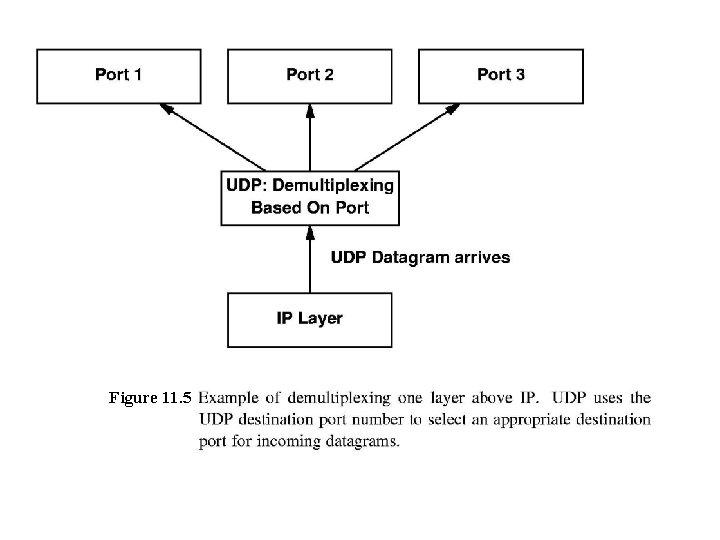
UDP Multiplexing, Demultiplexing, & Ports Thru the layers, SW must mux and demux among multiple objects at next layer UDP provides another example of this n n Accepts UDP datagrams from many application programs Passes to IP for transmission Takes arriving datagrams Passes each to appropriate application program

Figure 11. 5

Conceptually, mux & demux occurs at ports n In practice, little more involved Applications negotiate with OS to obtain a port protocol and associated port number One assigned, application puts the port number in all outgoing UDP datagrams n Think of ports as queues OS creates internal queue when provides port UDP receives datagram, see if port # matches one n n If not, sends port unreachable ICMP error msg, discards If is, enqueues datagram at port for application program If port full, get error and datagram discarded

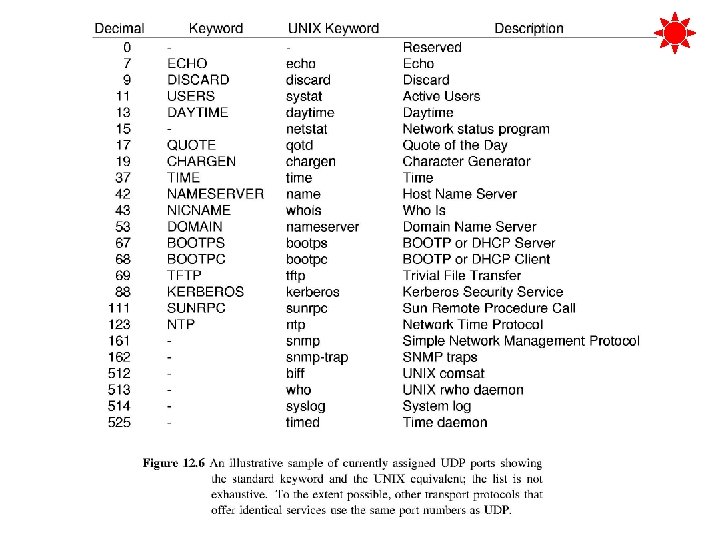
Reserved & Available Ports How should port numbers be assigned? n Two computers must agree on port numbers A wants file from B; needs to know what port the file transfer program on B uses Two fundamental approaches n n Central authority Dynamic binding

Central Authority n n Everyone agrees that central authority assigns List of assignments will be published All software will be built according to the list Also called universal assignment Called well-known port assignments Dynamic Binding n n Ports not globally known Software assigns ports when needed Must send request to computer to learn of assignments Target machine replies with the port number to use

TCP/IP uses hybrid approach n Some ports globally assigned a priori n Many left available for local sites or applications Low values going up are assigned Higher values left open


Summary Can have multiple applications executing n n UDP distinguishes among these processes Uses two 16 -bit integers for port numbers Some are pre-assigned (well-known) Some available for arbitrary use

UDP is a thin protocol n n Not add significantly to semantics of IP Provides way for applications to use IP to communicate Unreliable, connectionless UDP lies in transport layer n Conceptual independence between it and internet layer is somewhat violated