UDP TCP User Datagram Protocol Transmission Control Protocol



- Slides: 17

UDP & TCP User Datagram Protocol & Transmission Control Protocol BS IT 4 th Semester By: Muhammad Hanif

Quote of the day…… Many of life's failures are people who did not realize how close they were to success when they gave up. ~Thomas Edison Have a blessed day!

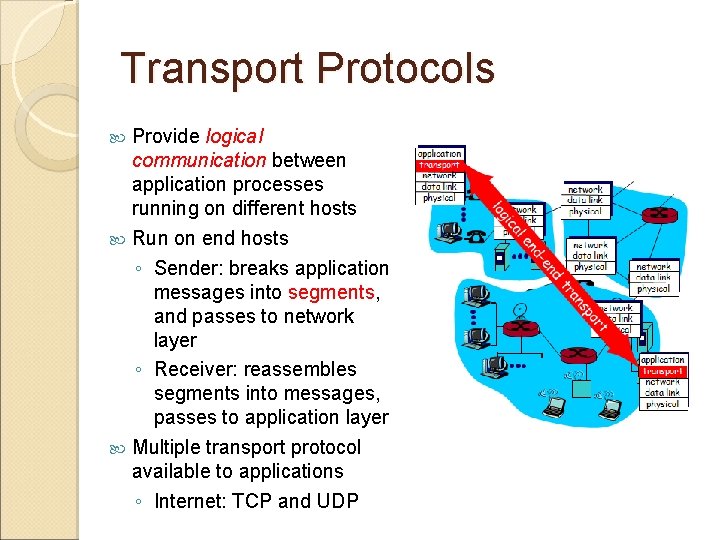
Transport Protocols Provide logical communication between application processes running on different hosts Run on end hosts ◦ Sender: breaks application messages into segments, and passes to network layer ◦ Receiver: reassembles segments into messages, passes to application layer Multiple transport protocol available to applications ◦ Internet: TCP and UDP

UDP User Datagram Protocol BS IT 4 th Semester By: Muhammad Hanif

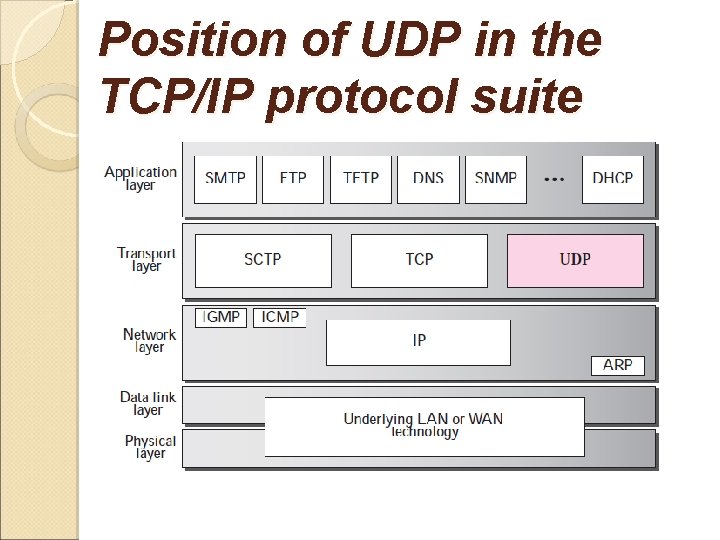
Position of UDP in the TCP/IP protocol suite

User Datagram Protocol UDP is an end-to-end or transport protocol that allows an application program to serve as the end-point of communication

UDP Characteristics End-to-end Connectionless Message-oriented ◦ Each UDP message must fit within one IP datagram ◦ UDP message can be lost, duplicated, or corrupted ◦ Suitable for applications that can tolerate delivery errors ◦ One-to-one, one-to-many E. g. Call Internet Telephony, Conference

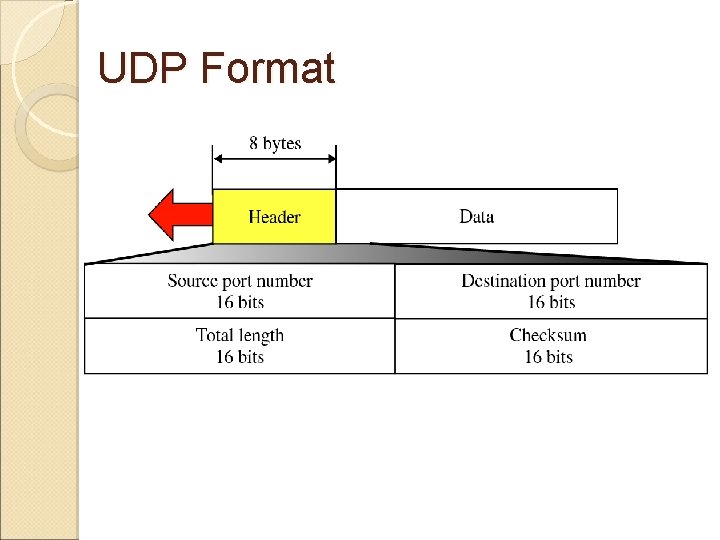
UDP Format

UDP Format Detail Source Port/Destination Port: A port Virtual circuit between two communicating processes on two different computers or devices The source port is the port on the sending device. The destination port is a TCP port on a receiving device that corresponds with the source port on the sending device Length: contains information about the length of the frame Checksum: This field is used to detect errors over the entire user datagram (header plus data). ◦ Placed in the frame by the sending station. ◦ The recipient also calculates the checksum and compares its calculation with the value in the checksum field.

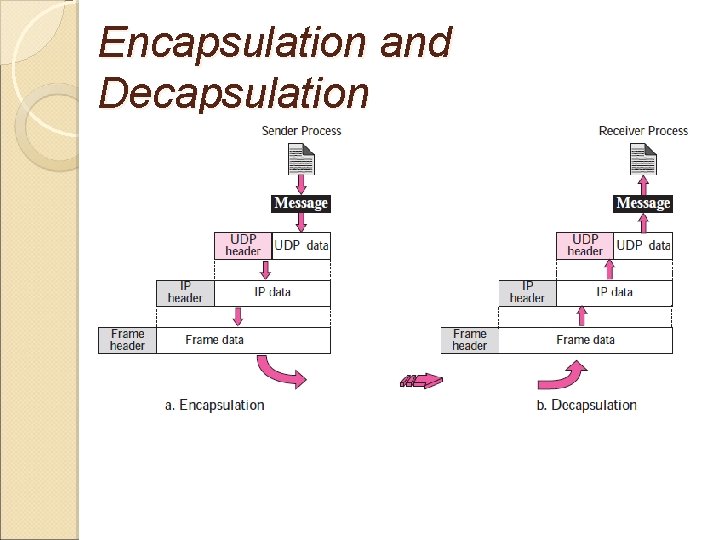
Encapsulation and Decapsulation

TCP Transmission Control Protocol BS IT 4 th Semester By: Muhammad Hanif

Quote of the day…… Be noble minded! Our own heart, and not other men's opinions of us, forms our true honor. - Johann Friedrich was a German anatomist.

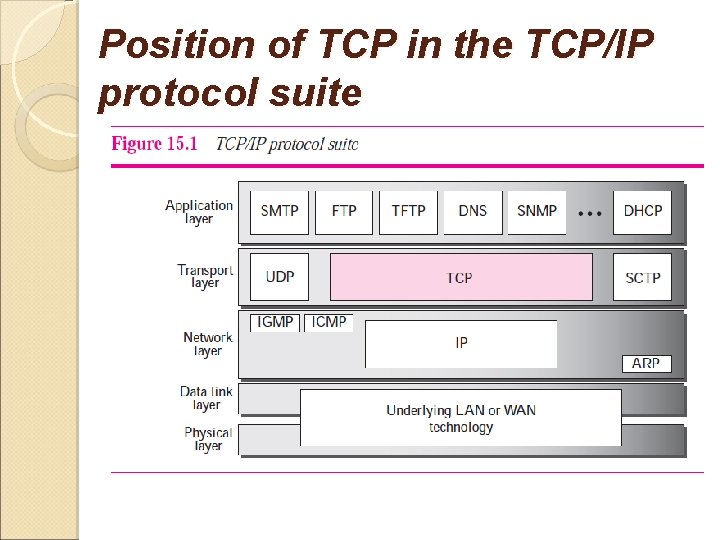
Position of TCP in the TCP/IP protocol suite

TCP Features Reliable, in-order delivery (TCP) ◦ Connection Oriented ◦ Discarding of corrupted packets ◦ Retransmission of lost packets ◦ Flow control

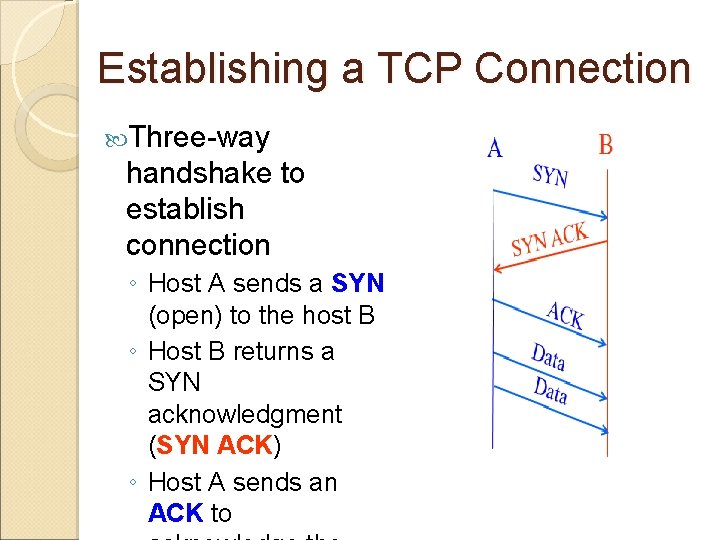
Establishing a TCP Connection Three-way handshake to establish connection ◦ Host A sends a SYN (open) to the host B ◦ Host B returns a SYN acknowledgment (SYN ACK) ◦ Host A sends an ACK to

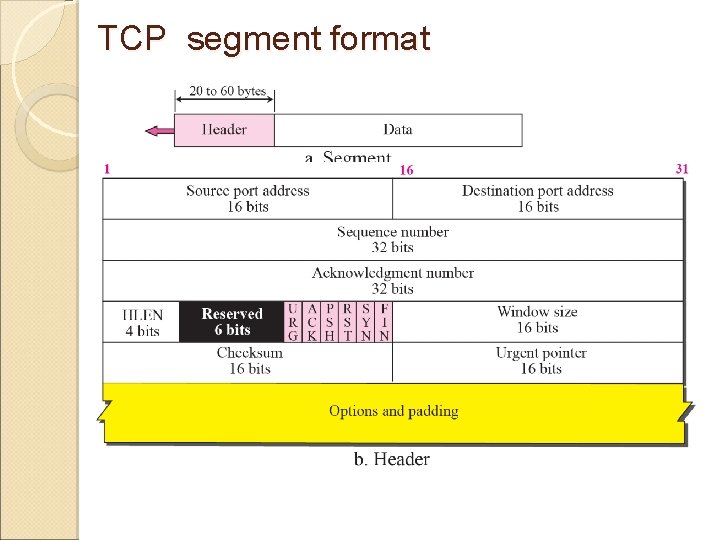
TCP segment format

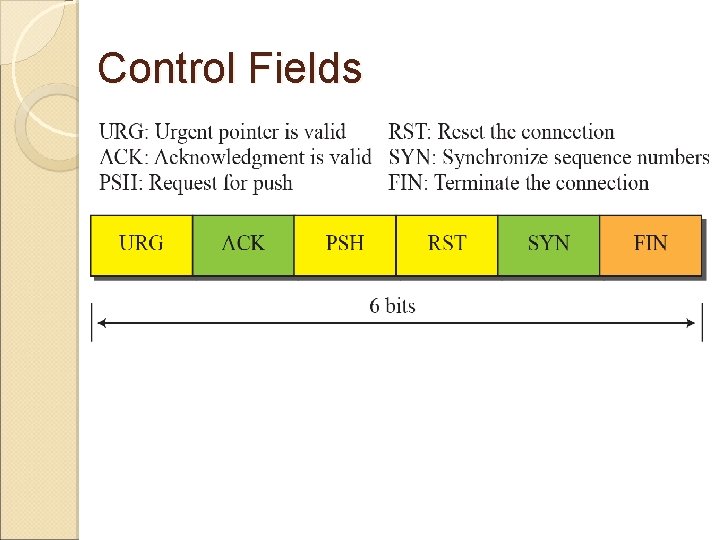
Control Fields