WLAN Security Antti Miettinen What is WLAN A













- Slides: 20

WLAN Security Antti Miettinen

What is WLAN? • A wireless data communication system implemented as an extension to, or alternative for, a wired local area network. • Operates at uncontrolled ISM (Industrial, Scientific and Medical) band 24. 9. 2021 2

What is WLAN? (cont. ) • Standards by IEEE for 802. 11 – 802. 11 First standard, up to 2 Mbps@2. 4 Ghz – 802. 11 a Accepted standard, up to 54 Mbps@5 GHz – 802. 11 b Accepted standard, up to 11 Mbps@2. 4 GHz – 802. 11 d MAC Enhancements for wider use of 802. 11 24. 9. 2021 3

What is WLAN? (cont. ) • Standards by IEEE for 802. 11 (cont. ) – 802. 11 e MAC Enhancements for Quality of Service – 802. 11 f Recommended Practice for Inter Access Point Protocol = Roaming & hand over – 802. 11 g Accepted standard, up to 54 Mbps@2. 4 Ghz – 802. 11 i Improved WEP 24. 9. 2021 4

What is WLAN? (cont. ) • Standards by ETSI – Hiper. LAN/1 23, 5 Mbps@5 GHz • published 1999 – Hiper. LAN/2 54 Mbps@5 Ghz (http: //www. hiperlan 2. com/) • Asynchronous data communication • Support for Qo. S (real-time voice & video) • support Transmit Power Control and Dynamic Frequency Selection (required in Europe at 5 GHz) • Uses 56 bit to 168 bit key encryption (DES) 24. 9. 2021 5

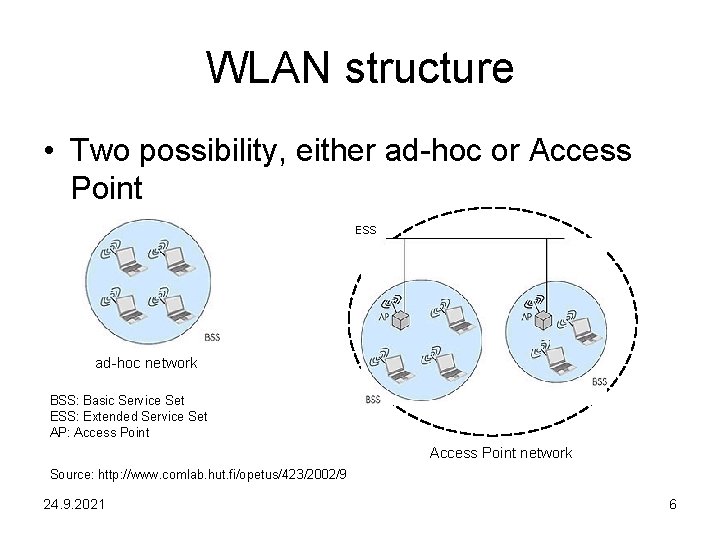
WLAN structure • Two possibility, either ad-hoc or Access Point ESS ad-hoc network BSS: Basic Service Set ESS: Extended Service Set AP: Access Point network Source: http: //www. comlab. hut. fi/opetus/423/2002/9 24. 9. 2021 6

802. 11 WLAN security features • DSSS (Direct sequence Spread Spectrum) – Isn’t very secure, although theoretically it could be a good security feature • ESSID (Extended Service Set Identifier) – By default all stations are broadcasting ESSID – Can be passively received, when legitimate user associates with Access Point • WEP (Wired Equivalent privacy) – By default is turned off – Includes flaws • MAC-address controlled authorization to Access Point – MAC-address is easy to spoof (command line) 24. 9. 2021 7

WEP • Goals – Access control: To prevent unauthorized users who lack a correct WEP key from gaining access to the network. – Privacy: To protect wireless LAN data streams by encrypting them and allowing decryption only by users with the correct WEP keys. • Includes security flaws! 24. 9. 2021 8

WEP Authentication • Access request by client • Challenge text sent to client by AP • Challenge text encoded by client using shared secret then sent to AP • If challenge text encoded properly AP allows access else denied 24. 9. 2021 9

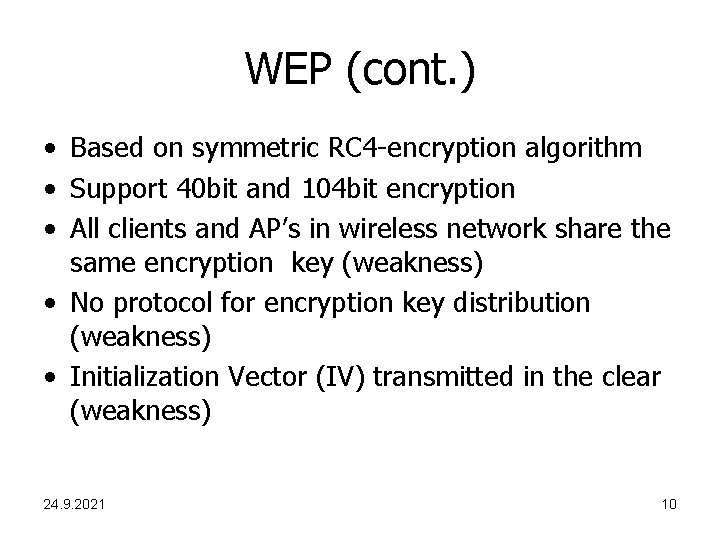
WEP (cont. ) • Based on symmetric RC 4 -encryption algorithm • Support 40 bit and 104 bit encryption • All clients and AP’s in wireless network share the same encryption key (weakness) • No protocol for encryption key distribution (weakness) • Initialization Vector (IV) transmitted in the clear (weakness) 24. 9. 2021 10

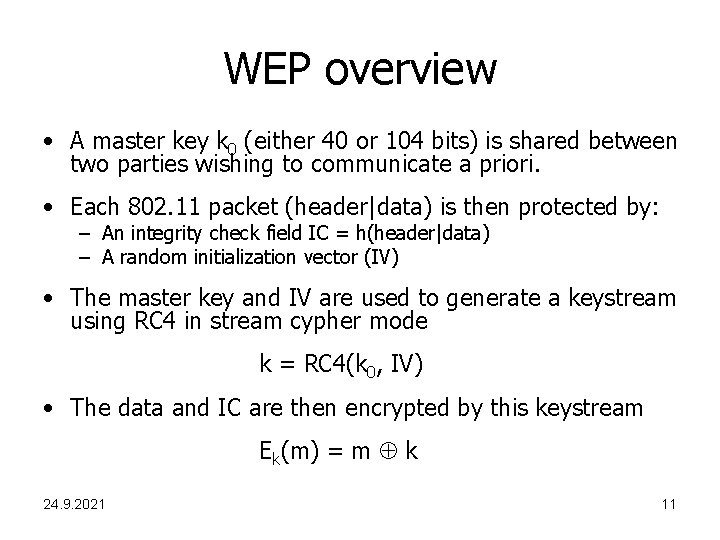
WEP overview • A master key k 0 (either 40 or 104 bits) is shared between two parties wishing to communicate a priori. • Each 802. 11 packet (header|data) is then protected by: – An integrity check field IC = h(header|data) – A random initialization vector (IV) • The master key and IV are used to generate a keystream using RC 4 in stream cypher mode k = RC 4(k 0, IV) • The data and IC are then encrypted by this keystream Ek(m) = m k 24. 9. 2021 11

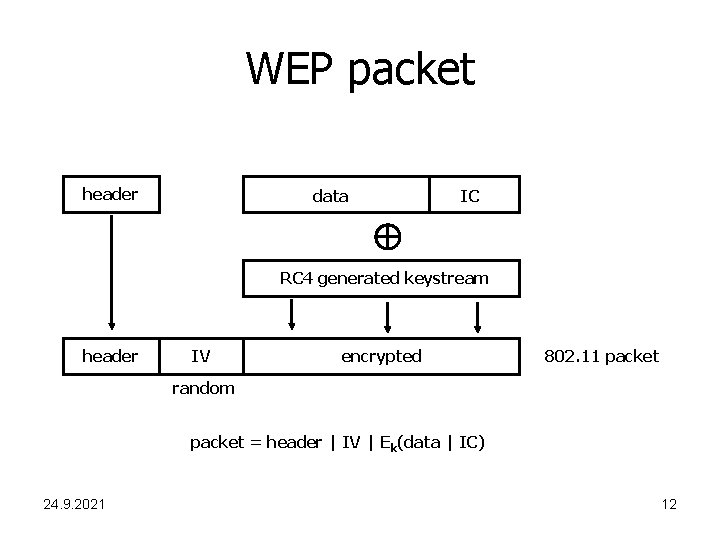
WEP packet header data IC RC 4 generated keystream header IV encrypted 802. 11 packet random packet = header | IV | Ek(data | IC) 24. 9. 2021 12

Possible Attacks • War-driving, war-walking etc. – Moving around the city and scanning the WLANs – Many of the WLANs are without protection! • (about in 50% of present WLANs WEP isn’t enabled) – Usually used to find networks, not to penetrate them • Monitoring – Just listening the traffic 24. 9. 2021 13

Possible Attacks (cont. ) • DOS-attack – Use high power 2, 45 Ghz (or 5 GHz) signal generator • for instance, microwave oven – Send continuous streams of CLS (clear-to-send) frames to a fictitious user • Legitimate users won’t be able to access the medium – Send deassociate frame in name of others (MACaddress can be faked) • It is possible! – Take the Access Point down! 24. 9. 2021 14

Possible Attacks (cont. ) • Man-in-the-middle attack – If WEP is used, the secret key must first be solved – Set up fake Access Point • No authentication required (from Access Points) • Legitimate users change their Access Point to yours, if it has better SNR. You can e. g. deassociate them from the real Access Point. 24. 9. 2021 15

Why is WLAN still used? • It is fast and easy to set up • It supports mobility • Reduced installation time and costs compared with cable • Broadband connection, up to 54 Mbps 24. 9. 2021 16

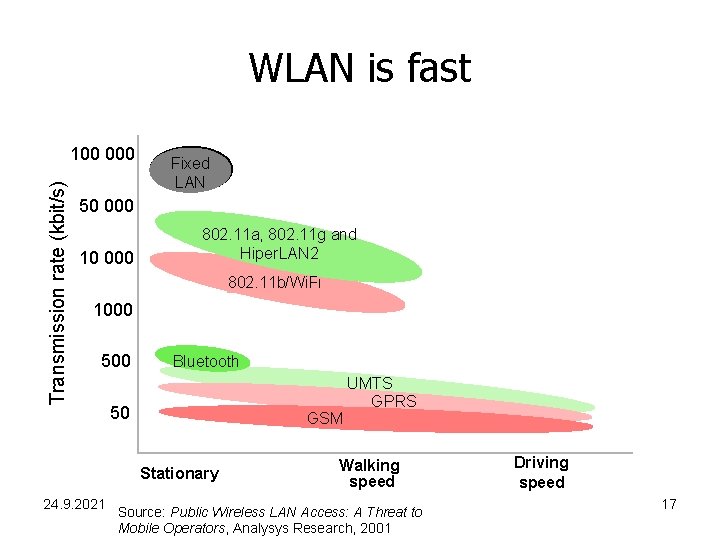
WLAN is fast Transmission rate (kbit/s) 100 000 Fixed LAN 50 000 10 000 802. 11 a, 802. 11 g and Hiper. LAN 2 802. 11 b/Wi. Fi 1000 500 Bluetooth 50 GSM Stationary 24. 9. 2021 UMTS GPRS Walking speed Source: Public Wireless LAN Access: A Threat to Mobile Operators, Analysys Research, 2001 Driving speed 17

How to check security of your WLAN-network? • Air. Snort (http: //airsnort. shmoo. com/) – For Linux and Windows – Recovers encryption keys – Operates by passively • WEPCrack (http: //wepcrack. sourceforge. net/) – Open source tool for breaking 802. 11 WEP secret keys – For Linux only 24. 9. 2021 18

How to check security of your WLAN-network? • Other software: – Netstumbler (http: //www. netstumbler. com/) • Only for Windows – Dstumbler (http: //www. dachb 0 den. com/projects/dstumb ler. html) • Only for Linux – Kismet (http: //www. kismetwireless. net/) • Only for Linux 24. 9. 2021 19

WLAN security • To Be Continued… 24. 9. 2021 20
 Avanne ja alkoholi
Avanne ja alkoholi Timo miettinen
Timo miettinen Merja miettinen
Merja miettinen Ari miettinen
Ari miettinen Teija miettinen
Teija miettinen Provate security
Provate security Antti myllynen
Antti myllynen Elina parviainen
Elina parviainen Sosiaalitieteet valmennuskurssi
Sosiaalitieteet valmennuskurssi Antti halmetoja
Antti halmetoja Luode consulting oy
Luode consulting oy Antti ivanoff
Antti ivanoff Antti lahti
Antti lahti Antti tuomikoski
Antti tuomikoski Antti ahlava
Antti ahlava Antti karjaluoto
Antti karjaluoto Antti helin
Antti helin Vesa lappalainen
Vesa lappalainen Antti kuivasniemi
Antti kuivasniemi Diaaritiedot
Diaaritiedot Silja kinnunen
Silja kinnunen