Wireless LAN WLAN Security and VPN WLAN VPN




















- Slides: 41

Wireless LAN, WLAN Security, and VPN 麟瑞科技 台南辦事處 技術經理 張晃崚

WLAN & VPN FAQ • • • What is WLAN? 802. 11 a? 802. 11 b? 802. 11 g? Which standard (product) should we use? How to deploy WLAN? How to block intruders? How to authenticate users? How to keep data secure? What is roaming? How to provide a fast path for some VIP users? How to exchange data securely between offices?

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

What is Wireless Network • Wireless Network: – 802. 11 x standards (Wi-Fi) – Cell phones – Bluetooth – Home. RF – Fixed Broadband wireless, IEEE 802. 16 – Mobile broadband – Optical point-to-point wireless

What is Wireless LAN • IEEE 802. 11 -based networks • Bluetooth is regarded as a PAN (Personal Area Network) • Need Wireless NIC and Access Point(AP)

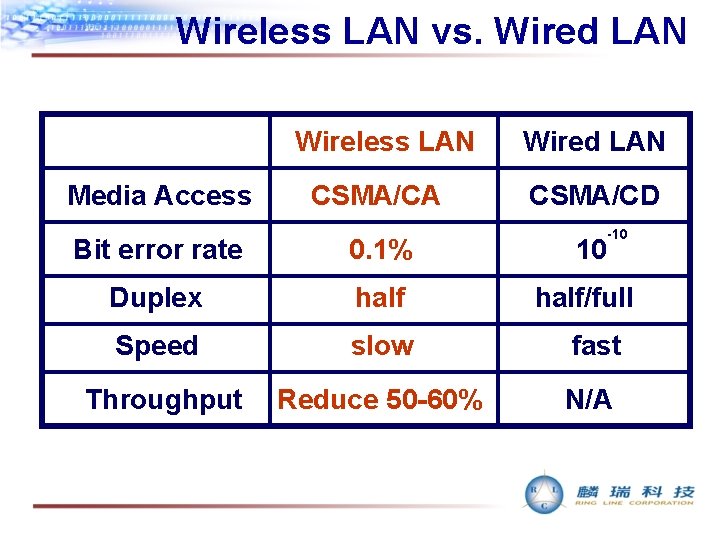
Wireless LAN vs. Wired LAN Wireless LAN Media Access CSMA/CA Wired LAN CSMA/CD -10 Bit error rate 0. 1% 10 Duplex half/full Speed slow fast Throughput Reduce 50 -60% N/A

Wireless LAN vs. Wired LAN • All 802 WLANs employ handshaked transmission to compensate • WLAN just like PUSH-to-TALK radio • WLAN will be a step backward: slower speed, half duplex, shared media. • BUT, gain FREEDOM • AP usually is a Layer 2 bridge (between wired LAN and wireless LAN) • Spanning Tree Protocol issue

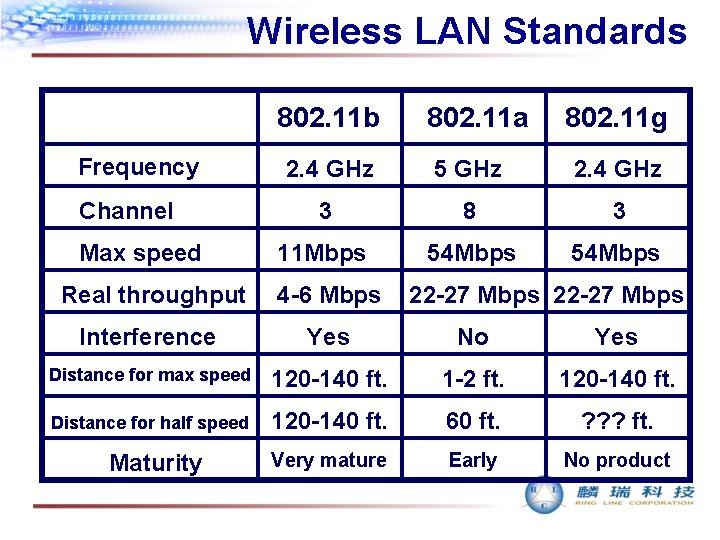
Wireless LAN Standards 802. 11 b Frequency Channel Max speed 802. 11 a 802. 11 g 2. 4 GHz 5 GHz 2. 4 GHz 3 8 3 11 Mbps 54 Mbps Real throughput 4 -6 Mbps Interference Yes No Yes Distance for max speed 120 -140 ft. 1 -2 ft. 120 -140 ft. Distance for half speed 120 -140 ft. 60 ft. ? ? ? ft. Very mature Early No product Maturity 22 -27 Mbps

802. 11 b+ • IEEE 802. 11 g will be finalized in May 2003 • Not a formal IEEE specification • Texas Instruments (TI) applied PBCC to enable 22 Mbps data rate • Interoperable with 802. 11 b device at 11 Mbps • Must use TI’s chip to enable 22 Mbps

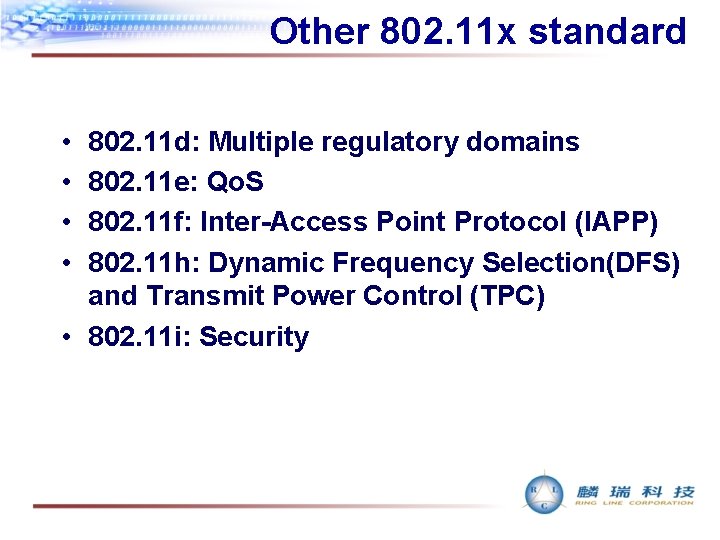
Other 802. 11 x standard • • 802. 11 d: Multiple regulatory domains 802. 11 e: Qo. S 802. 11 f: Inter-Access Point Protocol (IAPP) 802. 11 h: Dynamic Frequency Selection(DFS) and Transmit Power Control (TPC) • 802. 11 i: Security

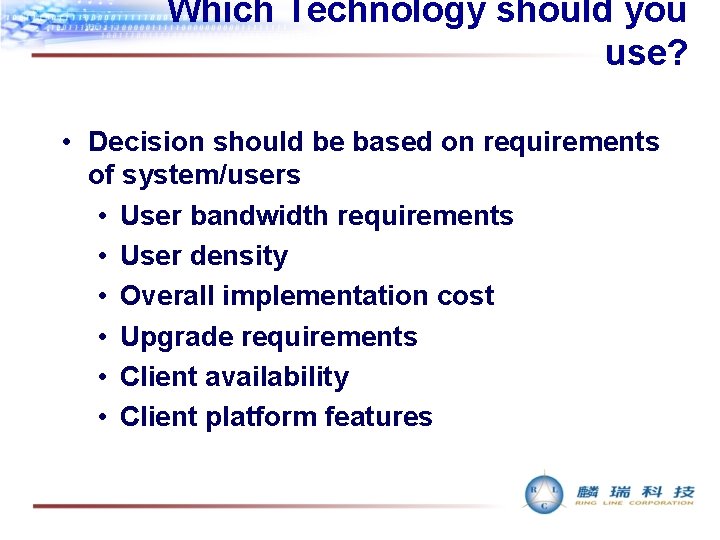
Which Technology should you use? • Decision should be based on requirements of system/users • User bandwidth requirements • User density • Overall implementation cost • Upgrade requirements • Client availability • Client platform features

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

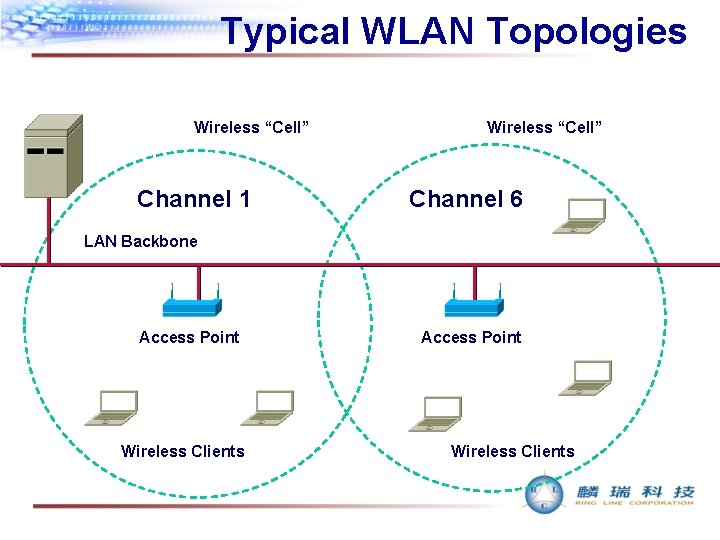
Typical WLAN Topologies Wireless “Cell” Channel 1 Wireless “Cell” Channel 6 LAN Backbone Access Point Wireless Clients

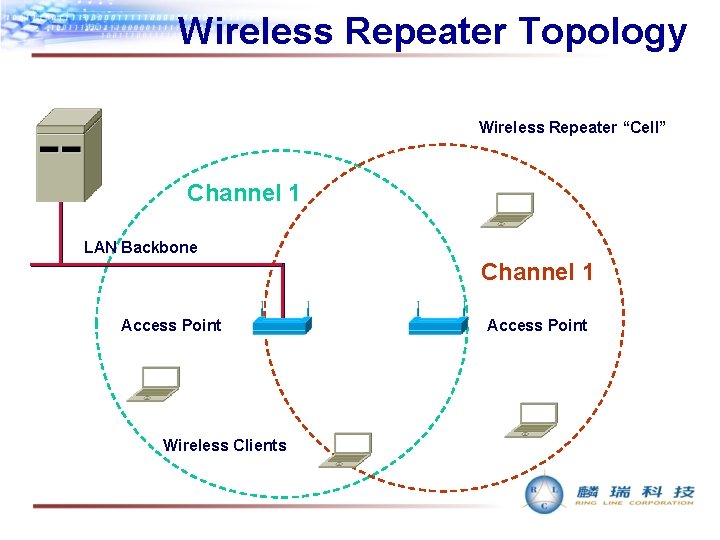
Wireless Repeater Topology Wireless Repeater “Cell” Channel 1 LAN Backbone Channel 1 Access Point Wireless Clients Access Point

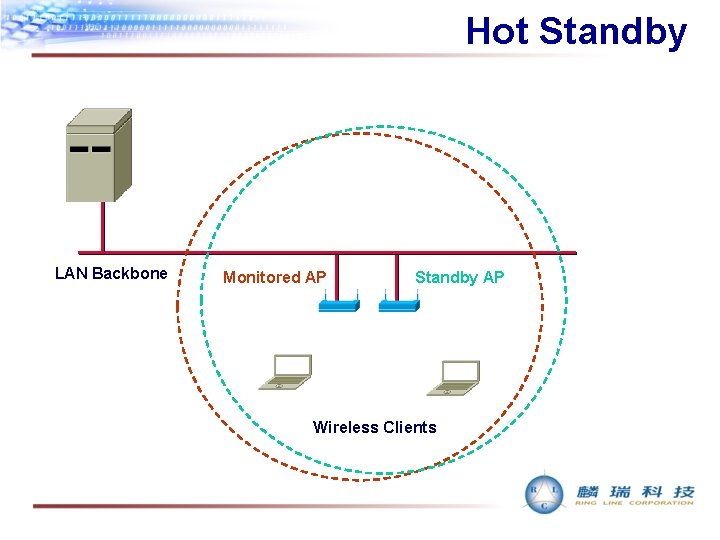
Hot Standby LAN Backbone Monitored AP Standby AP Wireless Clients

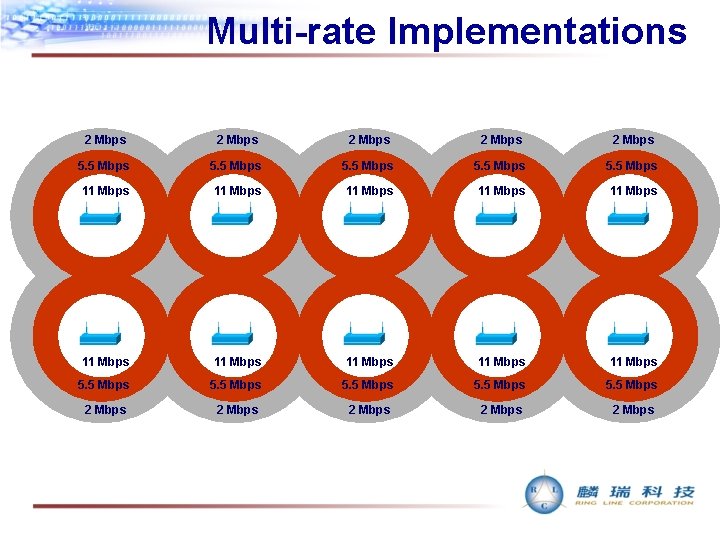
Multi-rate Implementations 2 Mbps 2 Mbps 5. 5 Mbps 11 Mbps 11 Mbps 11 Mbps 5. 5 Mbps 2 Mbps 2 Mbps

Vendor Offering • • • Higher and variable transmission power External antennas Little throughput degradation with encryption Line-power via the wired Ethernet cable Dual-band: 802. 11 b + 802. 11 a AP load balancing Roaming between IP subnets Hot Standby AP VLAN support Lockable case Enhanced security features: 802. 1 x, 802. 11 i draft, etc.

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

WLAN Security Issues • Wireless is like having an RJ 45 jack in the parking lot • Need to deny access to intruders • Need to secure message with good encryption technology

WLAN Security Issues • Managing the security side of you networks requires several things –Protecting the ‘network’ from intruders • Requires authentication for users –Protecting the Wireless DATA from sniffers • Requires some type of encryption –Protecting you RF networks from being detected –The ability to MANAGE you users credentials • Includes WEP keys, users names, passwords, etc. –Protecting your wireless infrastructure from improper configuration • Required a good user manager interface on APs

WLAN Security Issues • Managing the security side of you networks requires several things –To dynamically assign user’s IP address, gateway, etc. • Deploy DHCP server –To let roaming users be authenticated by their original account and passwords • Requires authentication roaming features for authentication servers

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

Authentication Techniques • Open System Authentication • No security • SSID Authentication • SSID is broadcast in clear text form • Can be obtained by snooping on traffic • Shared key Authentication (WEP) • Key stolen • Employee leaves

Authentication Techniques • MAC address Authentication • • MAC is sent in clear form Can be obtained be snooping Attackers may change their MAC to match Not flexible and scalable • 802. 1 x and Extensible Authentication Protocol (EAP) • Secure not only client but also devices • Only Windows XP and few vendors support this technique

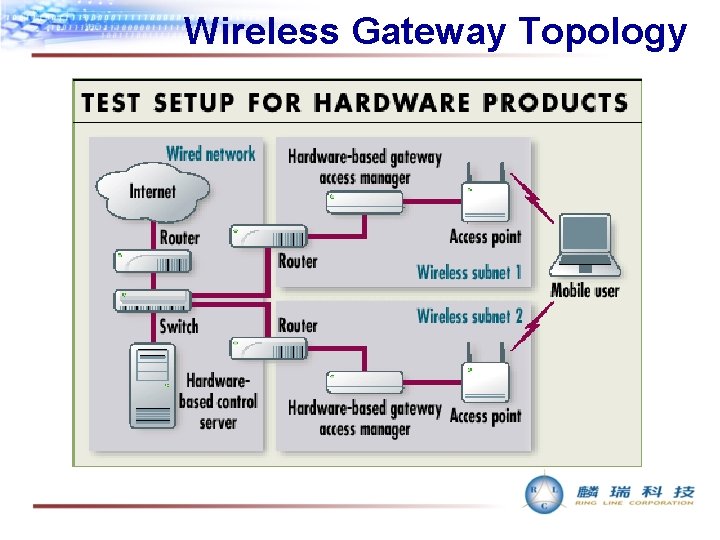
Authentication Techniques • VPN client Authentication • Does good authentication and encryption • Variable authentication and encryption method to choose • Need VPN client software installed • Wireless Gateway Authentication • No need to install any client software • Pop up authentication window when initiating connection (use web browser) • Easy to install and configure • One wireless gateway for a subnet

Wireless Gateway Topology

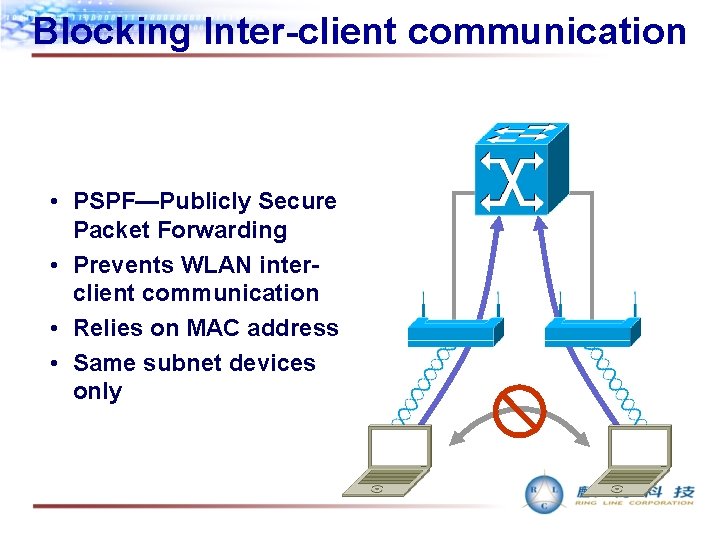
Blocking Inter-client communication • PSPF—Publicly Secure Packet Forwarding • Prevents WLAN interclient communication • Relies on MAC address • Same subnet devices only

Encryption Techniques • Key Management • Can be painful • Requires a power tool to manage keys • Easy to hack with well-know single key • Key Rotation • Changing the user’s key periodically • • Broadcast Key Rotation WEP Encryption 128 bit WEP IPsec

Encryption Techniques • IEEE 802. 11 i • TKIP (Data Integrity) • MIC (Data Integrity) • AES (Encryption) • Not yet complete

WLAN Security Solution Product • Wireless Gateway • Bluesocket • Vernier • Reef. Edge • VPN • Cisco VPN concentrator/router/client • Net. Screen • Authentication Server • Cisco ACS (RADIUS, TACACS, LEAP) • RADIUS

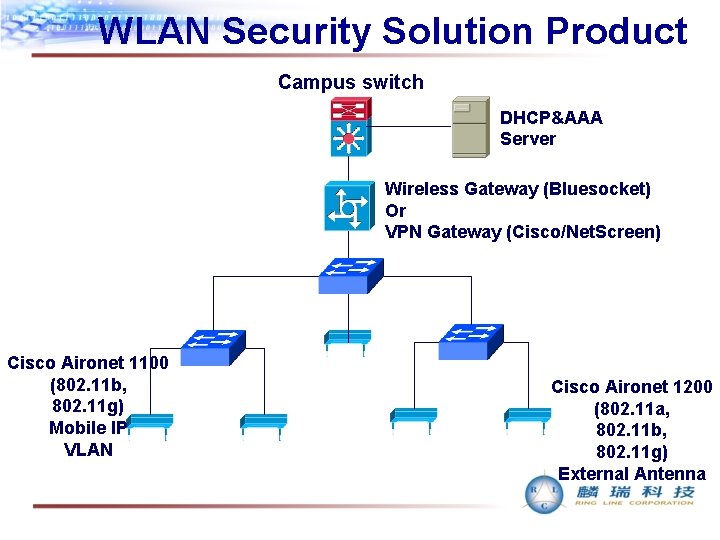
WLAN Security Solution Product Campus switch DHCP&AAA Server Wireless Gateway (Bluesocket) Or VPN Gateway (Cisco/Net. Screen) Cisco Aironet 1100 (802. 11 b, 802. 11 g) Mobile IP VLAN Cisco Aironet 1200 (802. 11 a, 802. 11 b, 802. 11 g) External Antenna

Cisco Aironet 1200 AP • Modular platform for single or dual band operation • Field upgradeable radios • Modular design enhances future upgrade ability • Simultaneous dual radio operation • 10/100 Ethernet LAN uplink

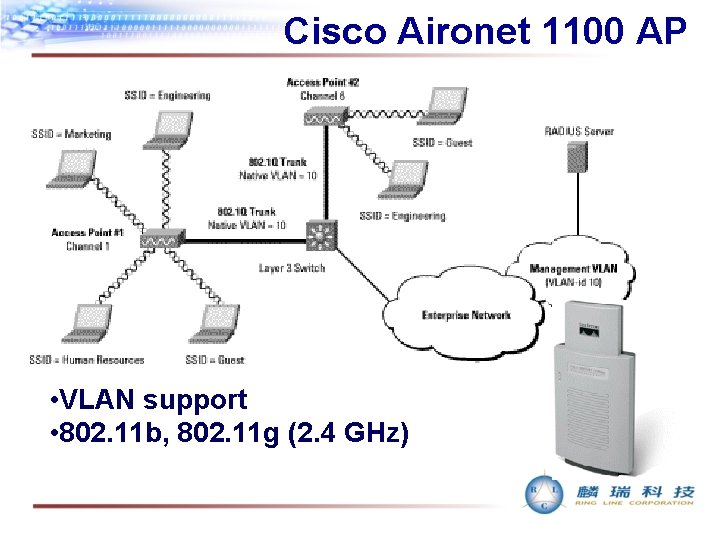
Cisco Aironet 1100 AP • VLAN support • 802. 11 b, 802. 11 g (2. 4 GHz)

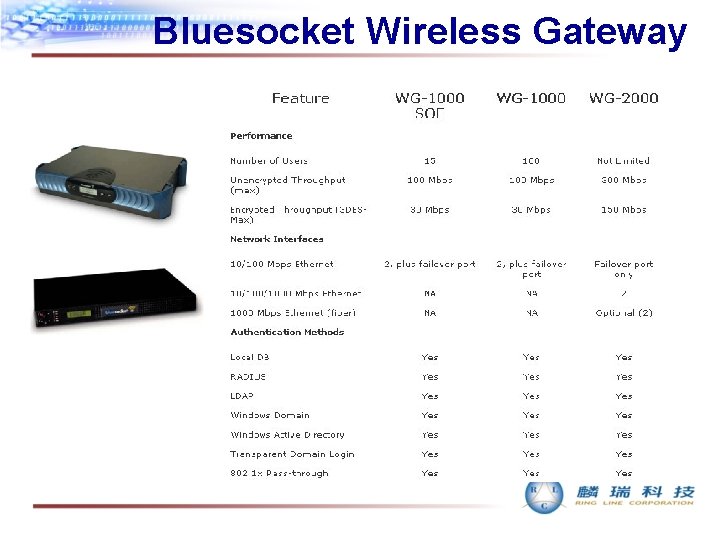
Bluesocket Wireless Gateway

Agenda • • • Introduction to Wireless LAN WLAN deployments WLAN security issues WLAN security solutions VPN solutions

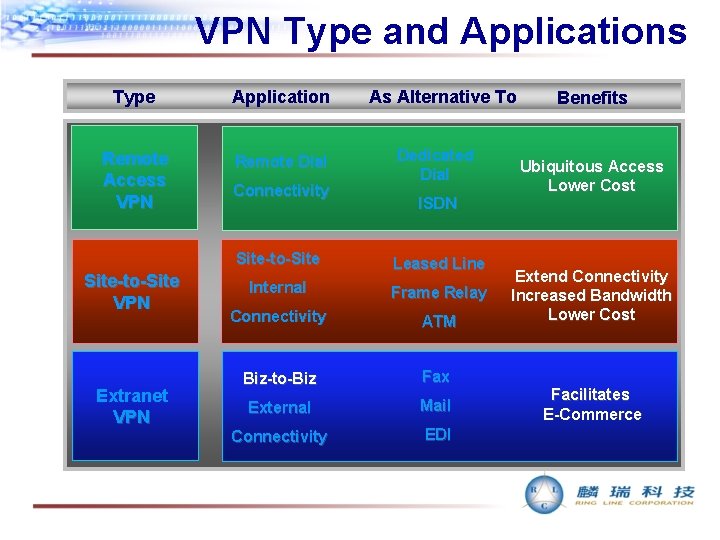
VPN Type and Applications Type Application Remote Access VPN Remote Dial Site-to-Site VPN Extranet VPN Connectivity As Alternative To Dedicated Dial ISDN Site-to-Site Leased Line Internal Frame Relay Connectivity ATM Biz-to-Biz Fax External Mail Connectivity EDI Benefits Ubiquitous Access Lower Cost Extend Connectivity Increased Bandwidth Lower Cost Facilitates E-Commerce

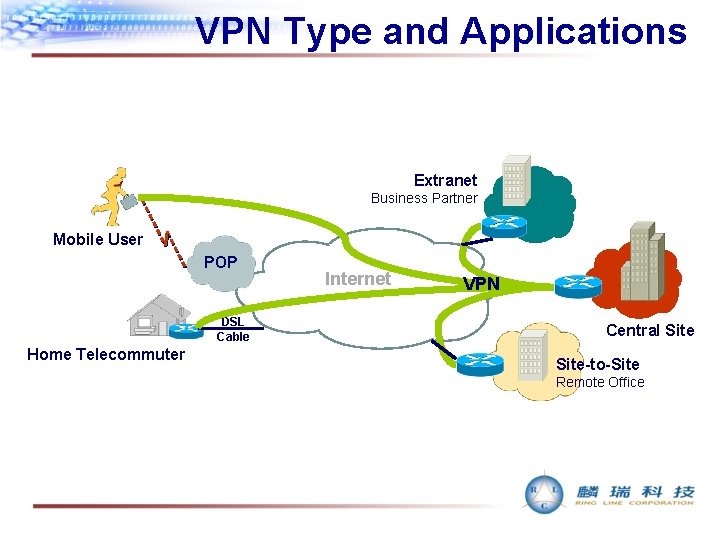
VPN Type and Applications Extranet Business Partner Mobile User POP DSL Cable Home Telecommuter Internet VPN Central Site-to-Site Remote Office

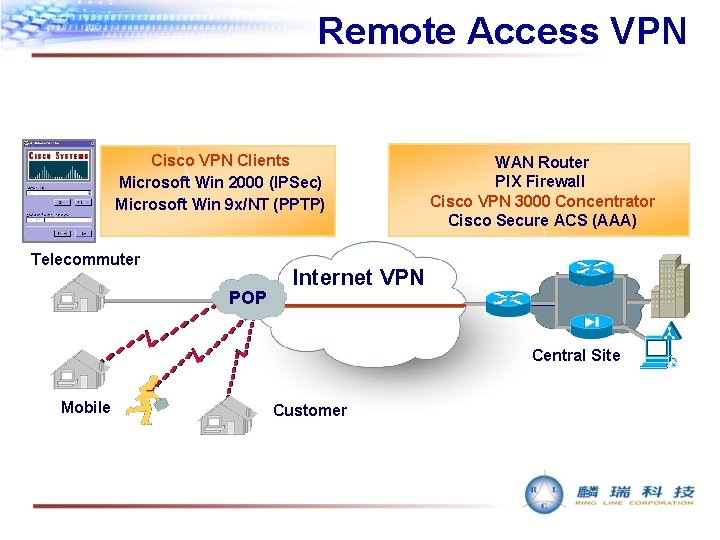
Remote Access VPN Cisco VPN Clients Microsoft Win 2000 (IPSec) Microsoft Win 9 x/NT (PPTP) Telecommuter POP WAN Router PIX Firewall Cisco VPN 3000 Concentrator Cisco Secure ACS (AAA) Internet VPN Central Site Mobile Customer

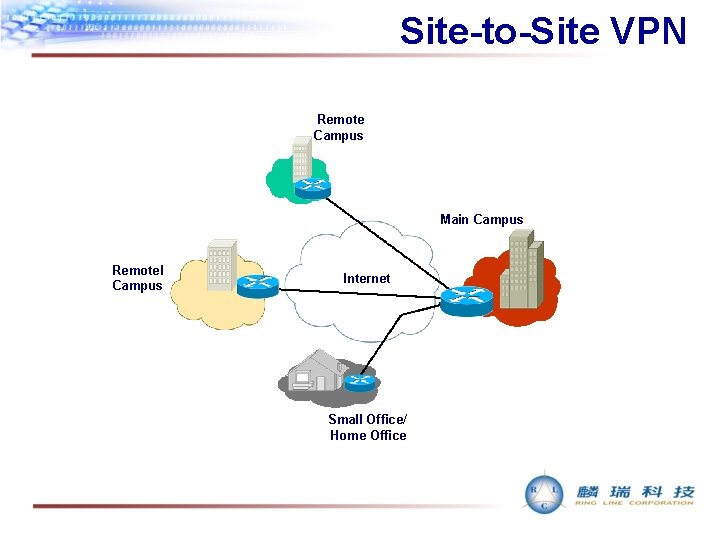
Site-to-Site VPN Remote Campus Main Campus Remotel Campus Internet Small Office/ Home Office

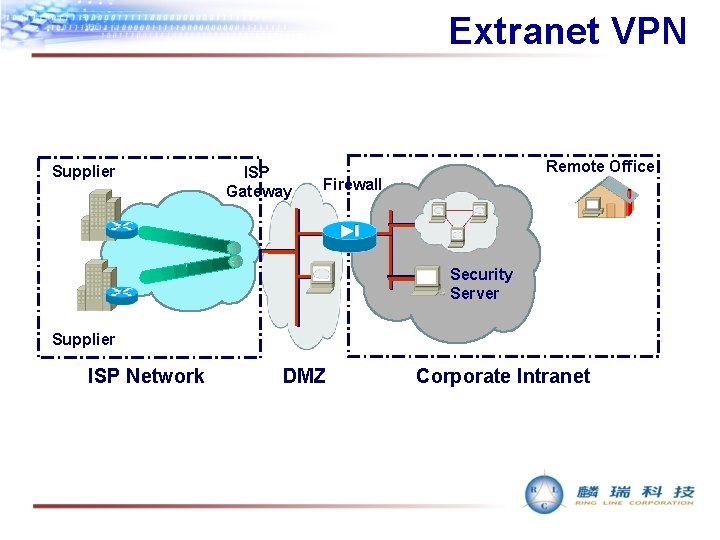
Extranet VPN Supplier ISP Gateway Remote Office Firewall Security Server Supplier ISP Network DMZ Corporate Intranet