WLAN 1 WLAN Security Requirements for Secure Wireless








- Slides: 25

WLAN 보안 1

WLAN Security • Requirements for Secure Wireless LANs – Authentication – Access Control – Data Privacy – Data Integrity – Protection Against Replay 2


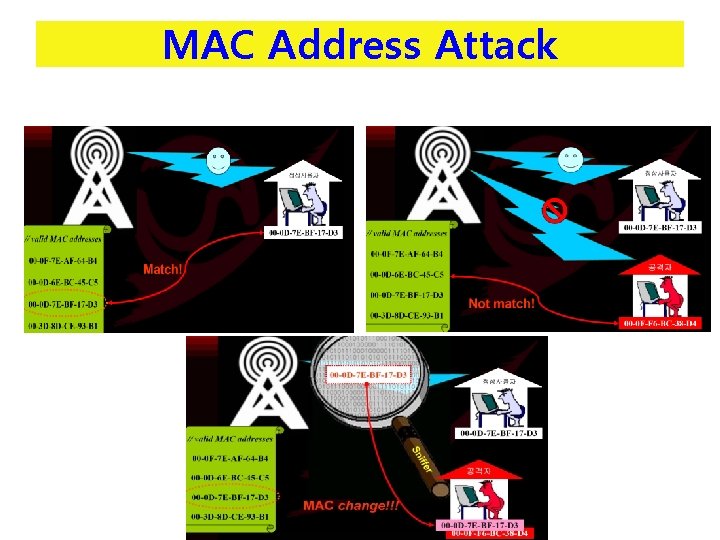
MAC address Authentication Attack • Strengths (장점) – MAC 주소를 기반으로 AP에 접속하고자 하는 Station들을 제어 • Weaknesses (단점) – MAC 주소는 쉽게 위조 가능 – 무선랜 네트워크를 모니터링(sniffing)함으로써 쉽게 MAC 주소를 획득 – 공격자들은 무선랜 통신을 계속 감시 가능 – MAC 주소의 Brute-force 공격이 가능 – Man in the middle attack 기술로 네트워크가 공격에 노출 - TOOL - Windows üAiro. Peek : Wireless Network Management Tool üSMAC : MAC address Changer - Linux üKismet : Wireless Network Sniffing Tool ümacchanger : MAC address Changer 4

MAC Address Attack 5


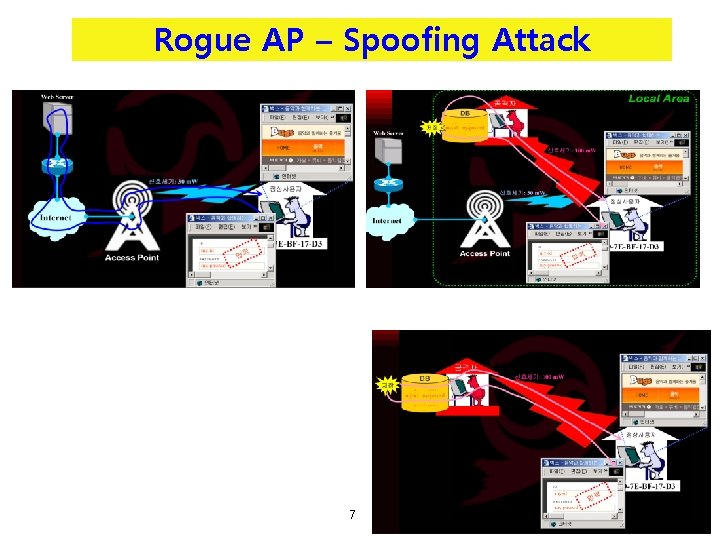
Rogue AP – Spoofing Attack 7

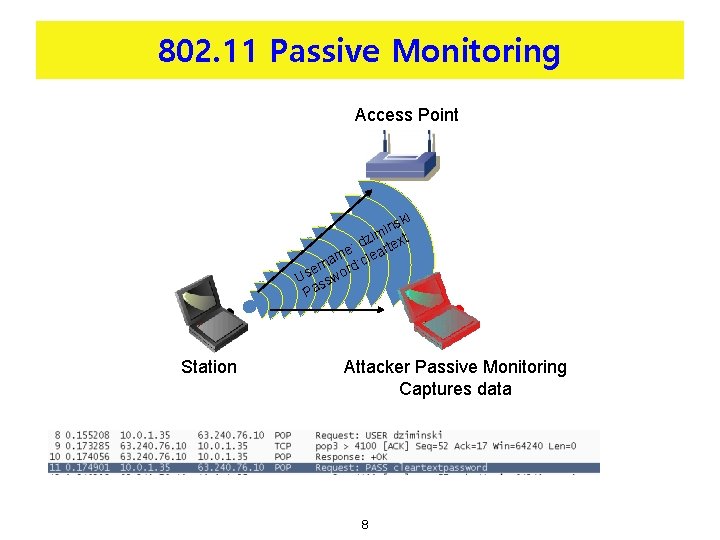
802. 11 Passive Monitoring Access Point ki ns i zim ext d e: eart m l rna ord: c e Us ssw Pa Station Attacker Passive Monitoring Captures data 8

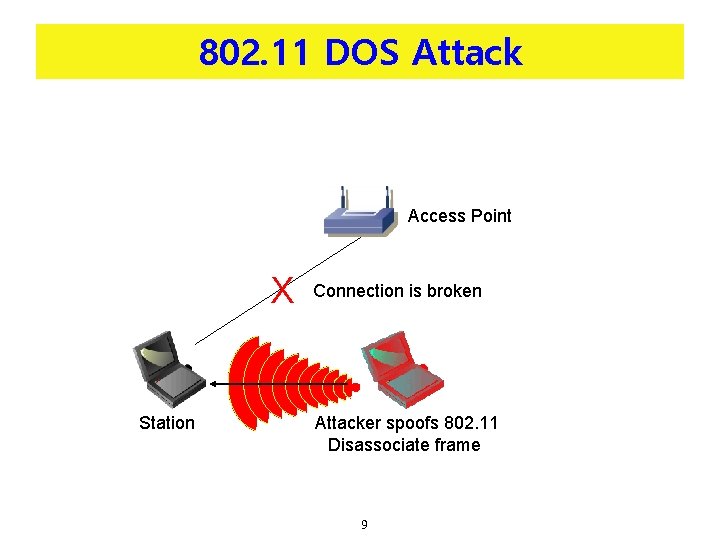
802. 11 DOS Attack Access Point X Station Connection is broken Attacker spoofs 802. 11 Disassociate frame 9

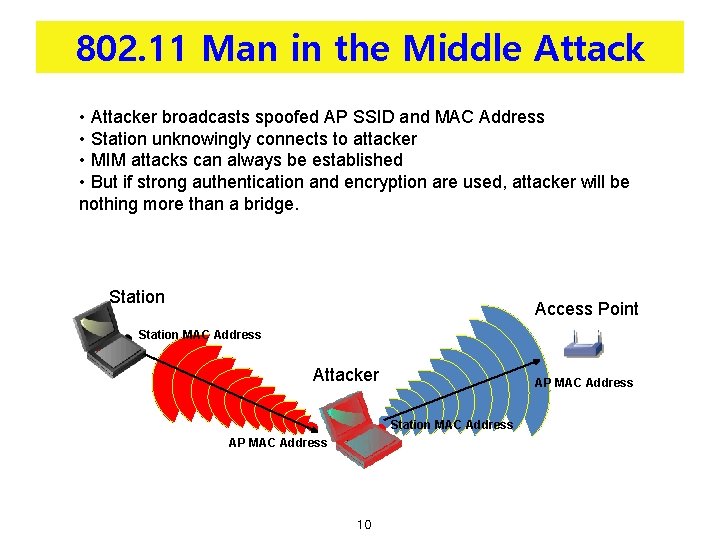
802. 11 Man in the Middle Attack • Attacker broadcasts spoofed AP SSID and MAC Address • Station unknowingly connects to attacker • MIM attacks can always be established • But if strong authentication and encryption are used, attacker will be nothing more than a bridge. Station Access Point Station MAC Address Attacker AP MAC Address Station MAC Address AP MAC Address 10

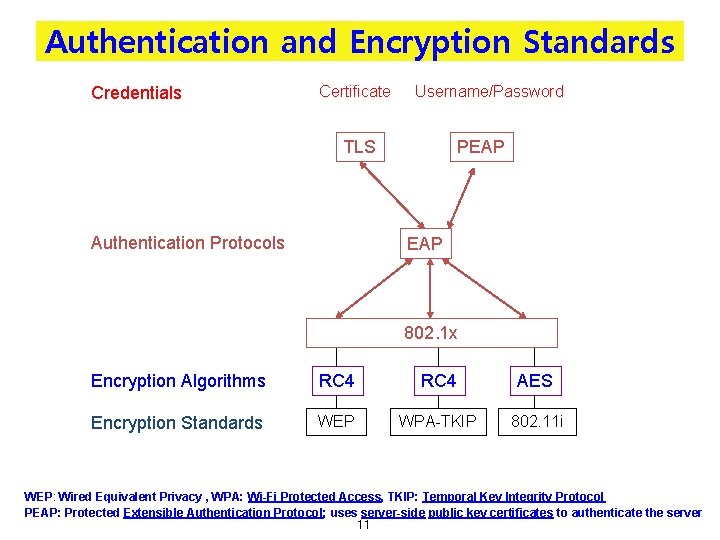
Authentication and Encryption Standards Credentials Certificate Username/Password TLS Authentication Protocols PEAP 802. 1 x Encryption Algorithms RC 4 AES Encryption Standards WEP WPA-TKIP 802. 11 i WEP: Wired Equivalent Privacy , WPA: Wi-Fi Protected Access, TKIP: Temporal Key Integrity Protocol PEAP: Protected Extensible Authentication Protocol; uses server-side public key certificates to authenticate the server 11

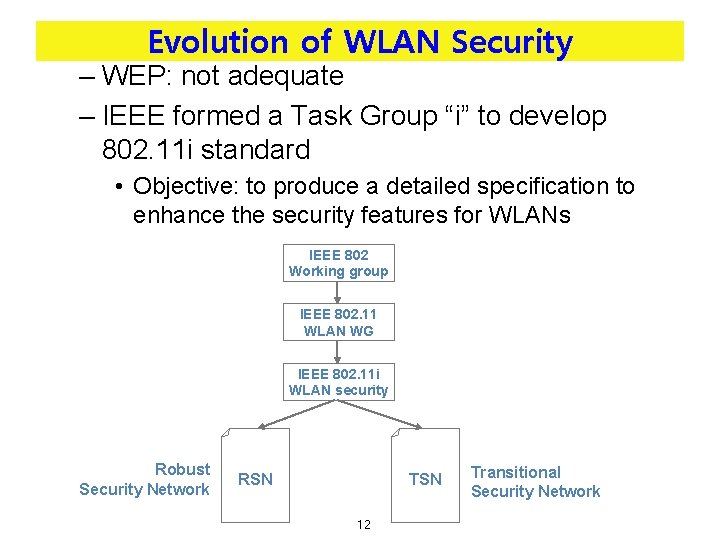
Evolution of WLAN Security – WEP: not adequate – IEEE formed a Task Group “i” to develop 802. 11 i standard • Objective: to produce a detailed specification to enhance the security features for WLANs IEEE 802 Working group IEEE 802. 11 WLAN WG IEEE 802. 11 i WLAN security Robust Security Network RSN TSN 12 Transitional Security Network

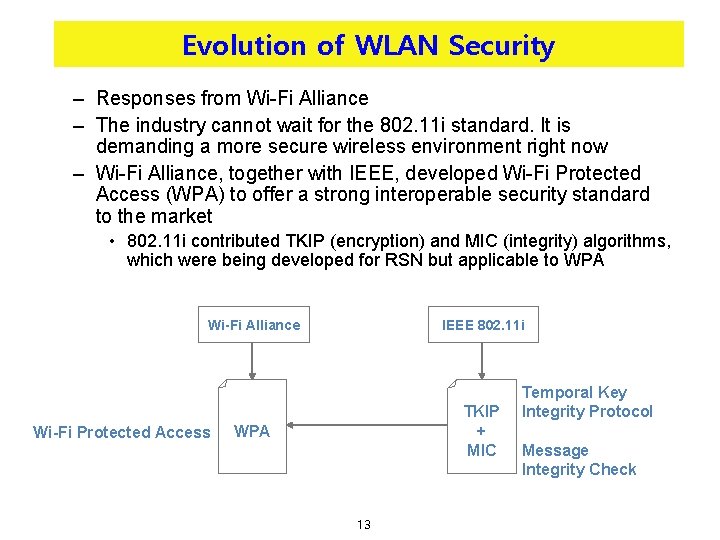
Evolution of WLAN Security – Responses from Wi-Fi Alliance – The industry cannot wait for the 802. 11 i standard. It is demanding a more secure wireless environment right now – Wi-Fi Alliance, together with IEEE, developed Wi-Fi Protected Access (WPA) to offer a strong interoperable security standard to the market • 802. 11 i contributed TKIP (encryption) and MIC (integrity) algorithms, which were being developed for RSN but applicable to WPA Wi-Fi Alliance Wi-Fi Protected Access IEEE 802. 11 i TKIP + MIC WPA 13 Temporal Key Integrity Protocol Message Integrity Check

High-level Differences Between RSN and WPA • RSN • WPA – Designed from the start, without regards to existing WEP systems – Will require new hardware to support new methods of encryption – Supports options for encryption (privacy) • TKIP • AES – Designed with constraints around existing WEP systems – Objective: use same hardware and upgrade software only – Only supports one encryption standard: TKIP Essentially, the two approaches are very similar and built around the same security architecture 14

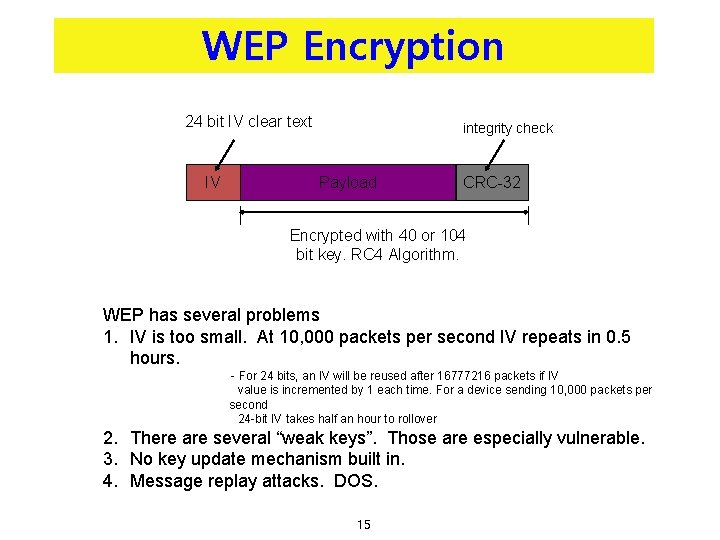
WEP Encryption 24 bit IV clear text IV integrity check Payload CRC-32 Encrypted with 40 or 104 bit key. RC 4 Algorithm. WEP has several problems 1. IV is too small. At 10, 000 packets per second IV repeats in 0. 5 hours. - For 24 bits, an IV will be reused after 16777216 packets if IV value is incremented by 1 each time. For a device sending 10, 000 packets per second 24 -bit IV takes half an hour to rollover 2. There are several “weak keys”. Those are especially vulnerable. 3. No key update mechanism built in. 4. Message replay attacks. DOS. 15

WPA • Key features to address WEP vulnerabilities – Access Control and Authentication: • Implements 802. 1 X EAP based authentication to enforce mutual authentication – Encryption • Applies Temporal Key Integrity Protocol (TKIP) on existing WEP to impose strong data encryption – Integrity • Uses Message Integrity Check (MIC) rather than CRC-32 for message integrity • WPA also presents some potential security issues – There are still potential encryption weaknesses in TKIP. Fortunately, the successful crack is expected to be heavy and expensive. – Performance may be sacrificed potentially due to a more complex and computation intensive authentication and encryption protocols. Note: The ultimate wireless security solution is still 802. 11 i RSN. All products are supposed to comply with RSN standard since it is released, often under the name WPA 2. 16

Wi-Fi Protected Access (WPA) TKIP-Encryption • Wi-Fi Protected Access is an interim standard created by the Wi-Fi alliance (group of manufacturers). • WPA-TKIP fixes problems with WEP. - IV changes to 48 bits with no weak keys. 900 years to repeat an IV at 10 k packets/sec - Use IV as a replay counter - Message integrity - Per-packet keying • Supported on many wireless card and on Windows XP (after applying 2 hot fixes). • Uses 802. 1 x for key distribution. • Can also use static keys. 17

802. 11 i RSN • Key features to address WEP vulnerabilities – Access Control and Authentication • Implements 802. 1 X EAP based authentication to enforce mutual authentication (same as WPA) • WRAP: RSN includes a Wireless Robust Authentication Protocol. Uses AES in offset codebook mode (OCB) for encryption and integrity. – Encryption • TKIP: In order to support legacy device, the 802. 11 i chooses TKIP as one of the encryption options • AES: Stands for Advanced Encryption Standard, which is a much stronger encryption algorithm. AES requires a hardware coprocessor to operate – Integrity • Uses Michael Message Integrity Check (MIC) for message integrity – Other security features: Secure IBSS (Ad Hoc mode), secure fast handoff, secure de-authentication and disassociation. – Supports Roaming – Is referred to as WPA 2 by the Wi-Fi Alliance 18 IBSS: Independent Basic Service Set

802. 11 i AES-encryption • Ratified by the IETF in June of 04. • Uses the AES algorithm for encryption and 802. 1 x for key distribution. • Backwards compatible with TKIP to support WPA clients. • 802. 11 i not in many products yet. 19

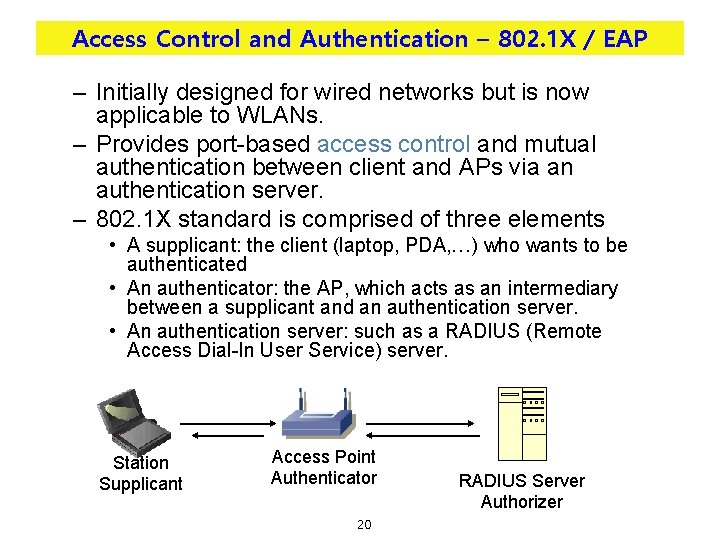
Access Control and Authentication – 802. 1 X / EAP – Initially designed for wired networks but is now applicable to WLANs. – Provides port-based access control and mutual authentication between client and APs via an authentication server. – 802. 1 X standard is comprised of three elements • A supplicant: the client (laptop, PDA, …) who wants to be authenticated • An authenticator: the AP, which acts as an intermediary between a supplicant and an authentication server. • An authentication server: such as a RADIUS (Remote Access Dial-In User Service) server. Station Supplicant Access Point Authenticator 20 RADIUS Server Authorizer

Access Control and Authentication – 802. 1 X / EAP • EAP – EAP (Extensible Authentication Protocol): protocol that 802. 1 X uses to manage mutual authentication. – Initially developed for use with PPP (RFC 2284) – Several EAP types depending on the authentication method (passwords, PKI certificates, …) • • • EAP-MD 5 EAP-TLS EAP-TTLS PEAP LEAP EAP-SIM – The authenticator does not need to understand the details about authentication methods. It simply package and repackage EAP packets, usually between Supplicant and RADIUS 21

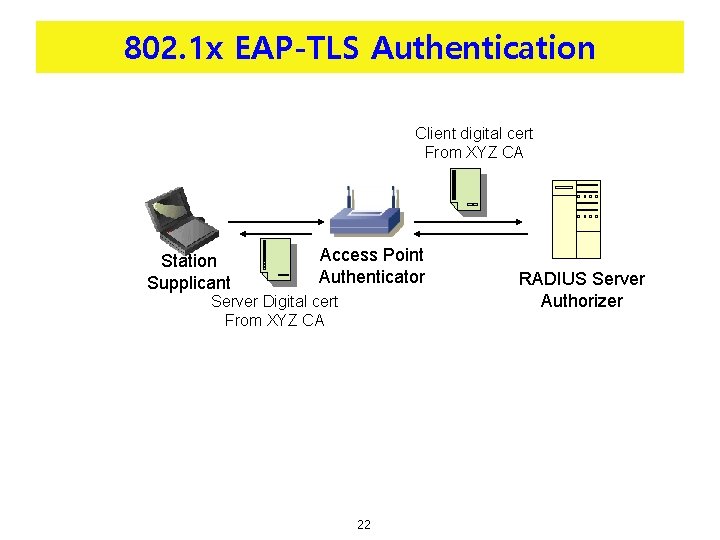
802. 1 x EAP-TLS Authentication Client digital cert From XYZ CA Station Supplicant Access Point Authenticator Server Digital cert From XYZ CA 22 RADIUS Server Authorizer

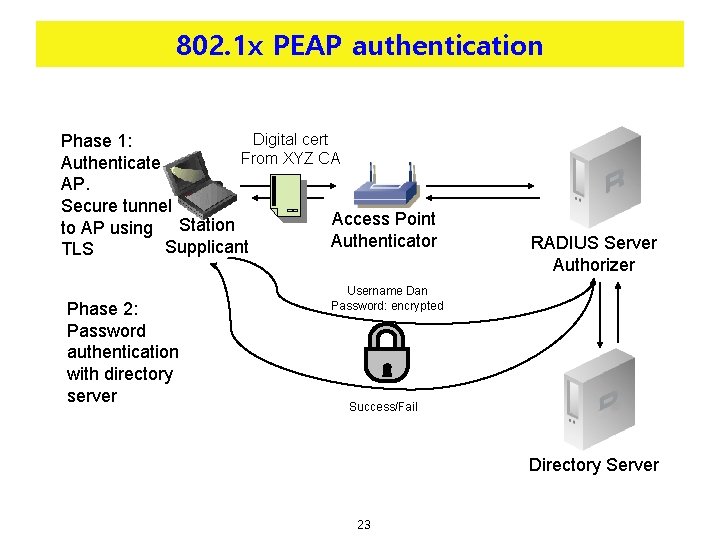
802. 1 x PEAP authentication Digital cert Phase 1: From XYZ CA Authenticate AP. Secure tunnel Access Point to AP using Station Authenticator Supplicant TLS Phase 2: Password authentication with directory server RADIUS Server Authorizer Username Dan Password: encrypted Success/Fail Directory Server 23

LEAP (Lightweight Extensible Authentication Protocol) • LEAP Characteristics – Primarily developed by Cisco for Aironet WLAN deployments. – Cisco is now licensing the software, other vendors are now beginning to support LEAP in their wireless LAN adapters. – Encrypts data transmissions using dynamically generated WEP keys and supports mutual authentication. – No certificates are required – Uses bi-directional challenge-response with user password as shared secret – Transaction sent in clear text (dictionary attacks !) 24

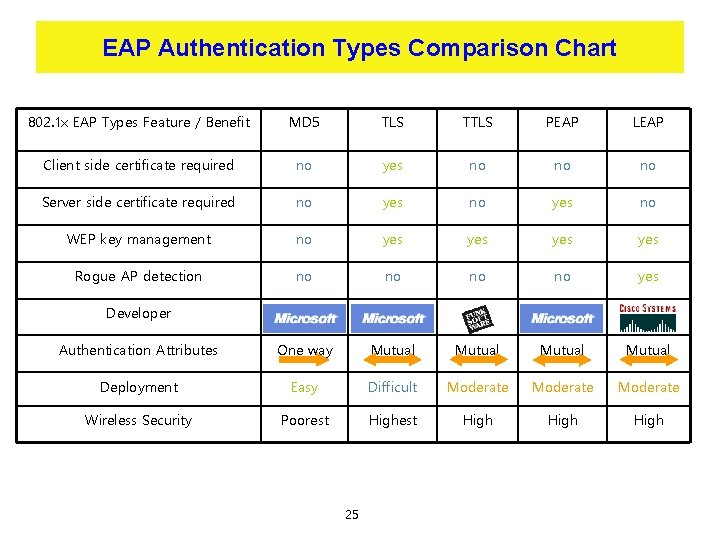
EAP Authentication Types Comparison Chart 802. 1 x EAP Types Feature / Benefit MD 5 TLS TTLS PEAP LEAP Client side certificate required no yes no no no Server side certificate required no yes no WEP key management no yes yes Rogue AP detection no no yes Authentication Attributes One way Mutual Deployment Easy Difficult Moderate Wireless Security Poorest High Developer 25