Wired and Wireless network management 1 PART 1











- Slides: 48

Wired and Wireless network management 1 PART 1: NETWORK COMPONENTS AND TRANSMISSION MEDIUM

Outline 2 �Network components �Transmission medium �The three-layer hierarchical design model

Network components 3 �Hubs �Bridges/Switches/Multilayer Switches Unmanaged Layer 2 Switches Managed Layer 3 Switches (Multilayer Switches) �Routers �Firewalls (VPN Concentrators) �Access Points �Content Filters �Load balancer. �Packet Shapers/Policers http: //www. ciscopress. com/articles/printerfriendly/2434666

Hubs 4 �This is a very simple device that connects together multiple local area network (LAN) devices. �The only function of the hub is repeating the electrical signals received on one port, relaying those signals to all other connected ports. �Hubs work at Open Systems Interconnection (OSI) Layer 1.

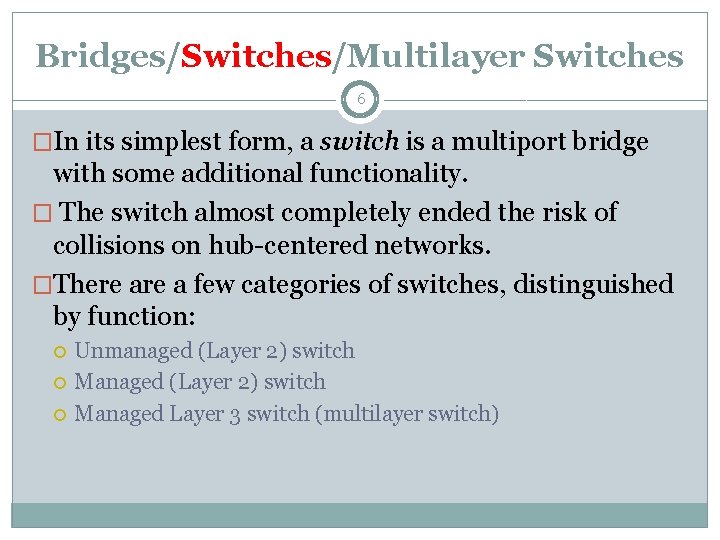
Bridges/Switches/Multilayer Switches 5 �A bridge is used to connect multiple LAN segments together, forming multiple collision domains. �By separating two or more LAN segments into multiple collision domains, the bridge reduces the number of collisions that could potentially occur on a LAN segment (fewer LAN speakers on the same segment), which improves network performance.

Bridges/Switches/Multilayer Switches 6 �In its simplest form, a switch is a multiport bridge with some additional functionality. � The switch almost completely ended the risk of collisions on hub-centered networks. �There a few categories of switches, distinguished by function: Unmanaged (Layer 2) switch Managed Layer 3 switch (multilayer switch)

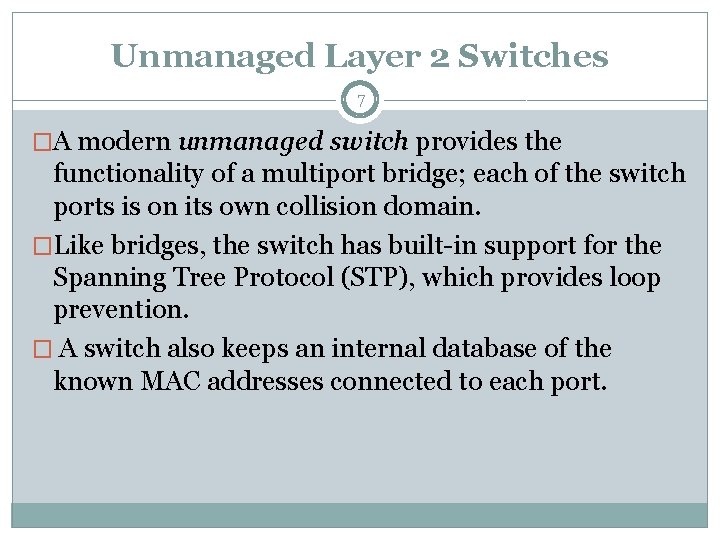
Unmanaged Layer 2 Switches 7 �A modern unmanaged switch provides the functionality of a multiport bridge; each of the switch ports is on its own collision domain. �Like bridges, the switch has built-in support for the Spanning Tree Protocol (STP), which provides loop prevention. � A switch also keeps an internal database of the known MAC addresses connected to each port.

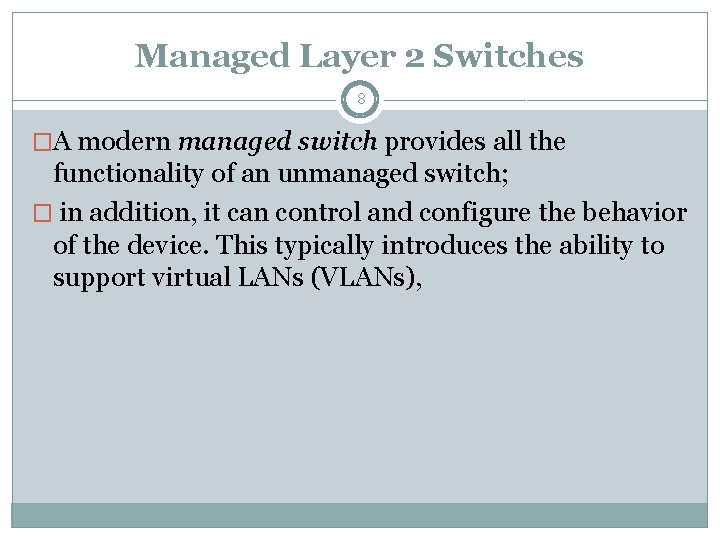
Managed Layer 2 Switches 8 �A modern managed switch provides all the functionality of an unmanaged switch; � in addition, it can control and configure the behavior of the device. This typically introduces the ability to support virtual LANs (VLANs),

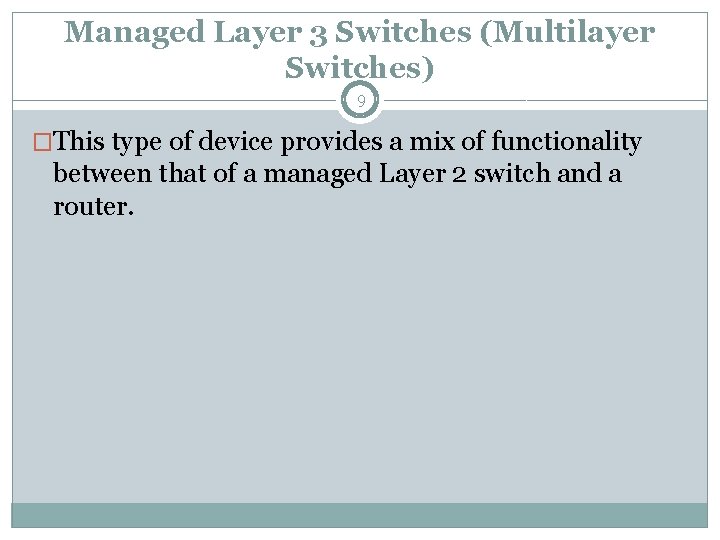
Managed Layer 3 Switches (Multilayer Switches) 9 �This type of device provides a mix of functionality between that of a managed Layer 2 switch and a router.

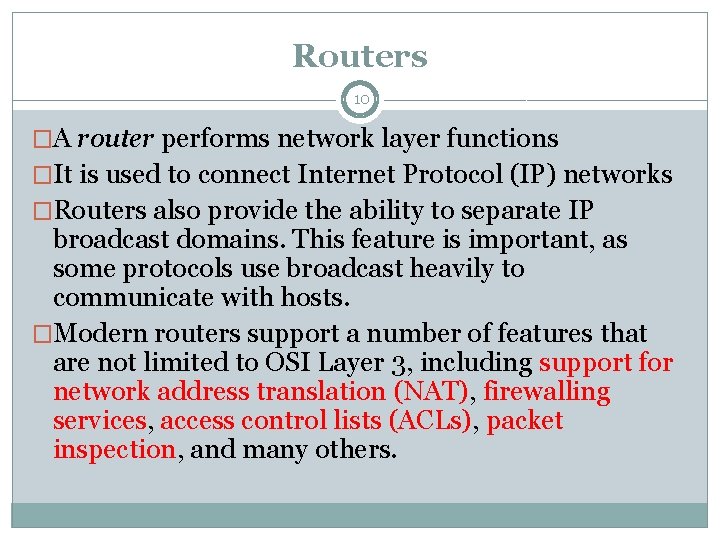
Routers 10 �A router performs network layer functions �It is used to connect Internet Protocol (IP) networks �Routers also provide the ability to separate IP broadcast domains. This feature is important, as some protocols use broadcast heavily to communicate with hosts. �Modern routers support a number of features that are not limited to OSI Layer 3, including support for network address translation (NAT), firewalling services, access control lists (ACLs), packet inspection, and many others.

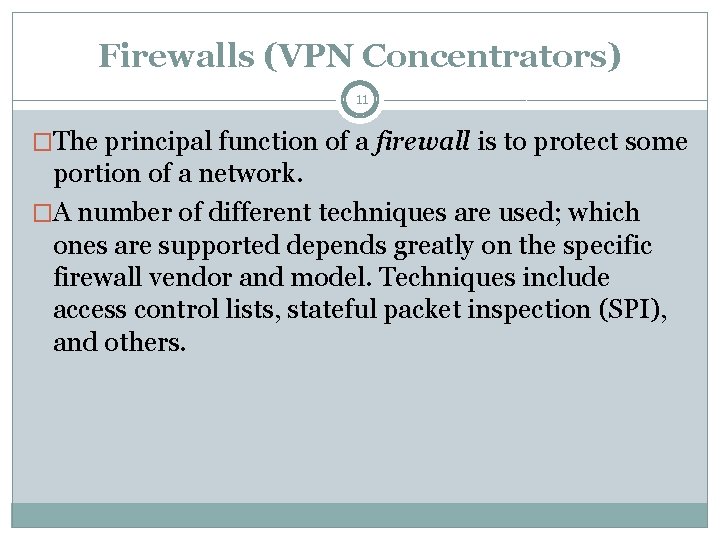
Firewalls (VPN Concentrators) 11 �The principal function of a firewall is to protect some portion of a network. �A number of different techniques are used; which ones are supported depends greatly on the specific firewall vendor and model. Techniques include access control lists, stateful packet inspection (SPI), and others.

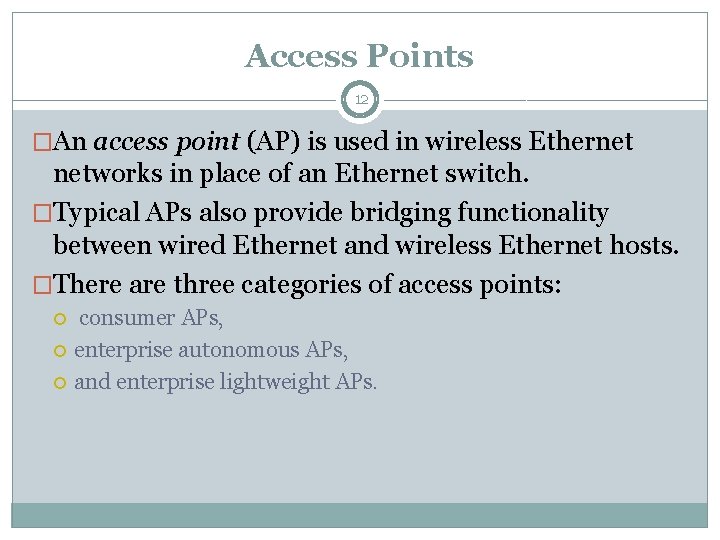
Access Points 12 �An access point (AP) is used in wireless Ethernet networks in place of an Ethernet switch. �Typical APs also provide bridging functionality between wired Ethernet and wireless Ethernet hosts. �There are three categories of access points: consumer APs, enterprise autonomous APs, and enterprise lightweight APs.

Content Filters 13 �Content filters are used on some networks to control the type of data that is allowed to pass through the network

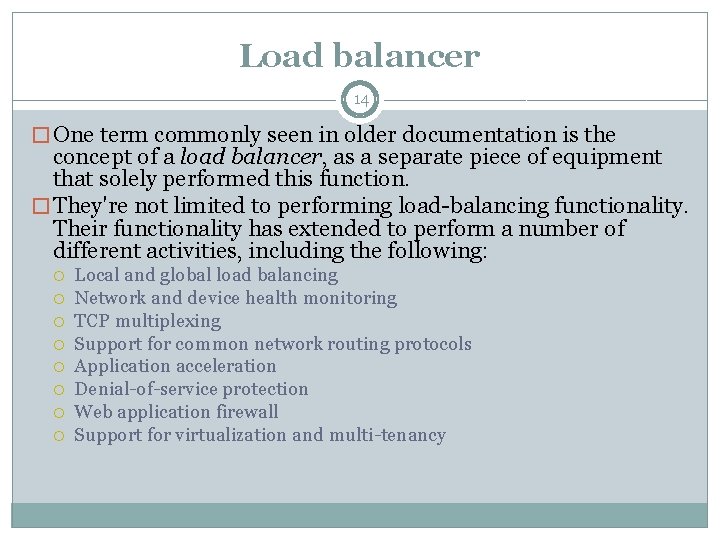
Load balancer 14 � One term commonly seen in older documentation is the concept of a load balancer, as a separate piece of equipment that solely performed this function. � They're not limited to performing load-balancing functionality. Their functionality has extended to perform a number of different activities, including the following: Local and global load balancing Network and device health monitoring TCP multiplexing Support for common network routing protocols Application acceleration Denial-of-service protection Web application firewall Support for virtualization and multi-tenancy

Packet Shapers/Policers 15 �A packet shaper or policer controls the flow of information into or out of a specific device �The shaping or policing functionality is typically built into routers (and some switches) to deal with times when network demand outpaces the ability of a device or its port. �In situations of no congestion, the shaping and/or policing functionality is not used. When there is congestion, these features will control how the excessive traffic is handled.

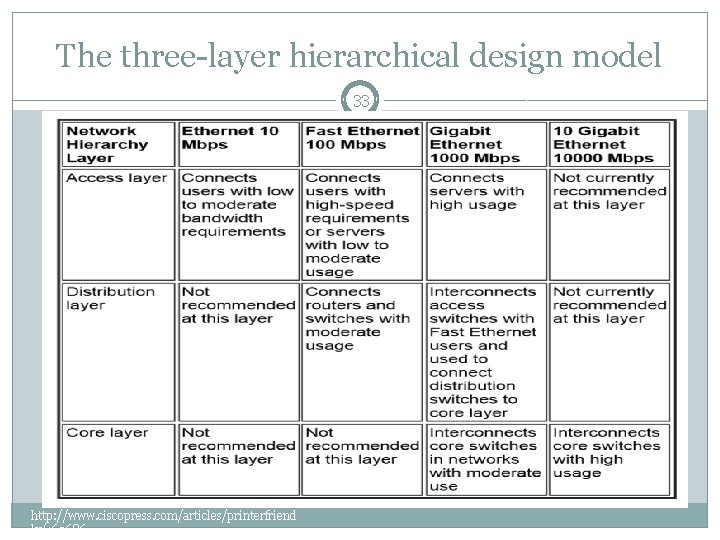
Transmission medium 16 The choice of media type affects: �The type of network interface cards installed. �The speed of the network. �The ability of the network to meet future needs. http: //www. ciscopress. com/articles/printerfriend ly/169686

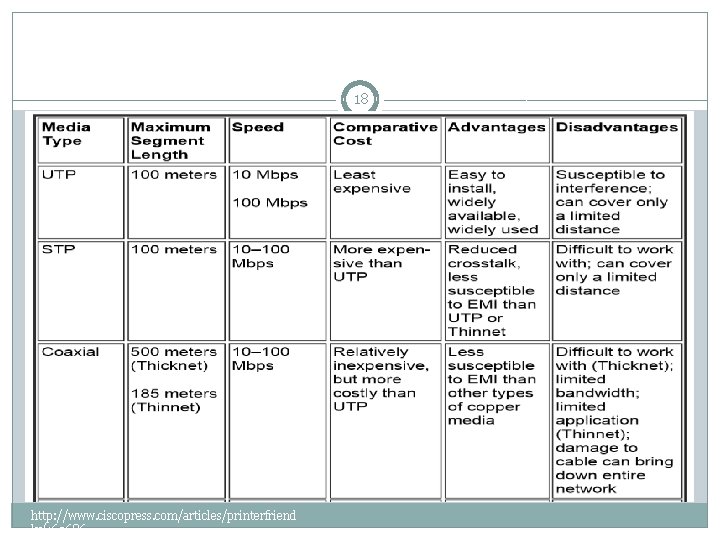
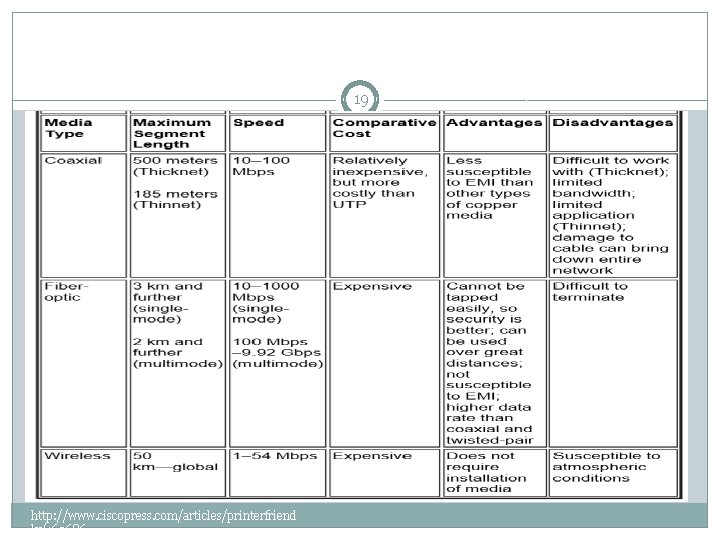
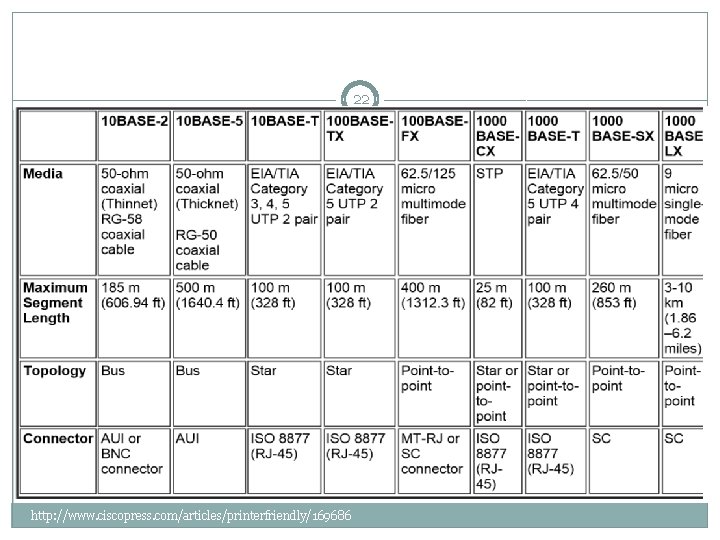
Transmission medium 17 �Table 4 -1 compares the features of the common network media, including UTP, STP, coaxial cable, fiber-optic, and wireless connections. http: //www. ciscopress. com/articles/printerfriend ly/169686

18 http: //www. ciscopress. com/articles/printerfriend ly/169686

19 http: //www. ciscopress. com/articles/printerfriend ly/169686

20 �Before implementing a network, you need to determine the requirements for the network. You can remember a few common recommendations on how various Ethernet technologies can be used in a campus network environment. http: //www. ciscopress. com/articles/printerfriend ly/169686

Importance of choosing appropriate Ethernet 21 �In many modern installations, infrastructure costs for cabling and adapters can be high. Using the appropriate Ethernet connectivity provides the necessary speed for the parts of the network that require it while controlling costs. http: //www. ciscopress. com/articles/printerfriend ly/169686

22 http: //www. ciscopress. com/articles/printerfriendly/169686

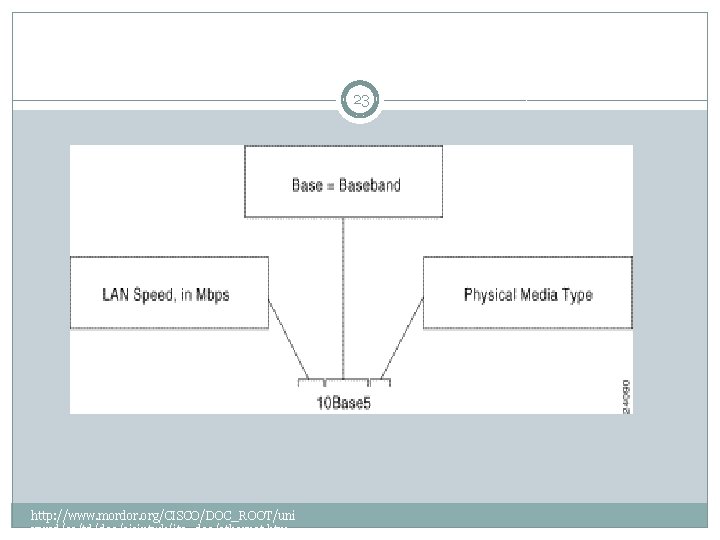
23 http: //www. mordor. org/CISCO/DOC_ROOT/uni vercd/cc/td/doc/cisintwk/ito_doc/ethernet. htm

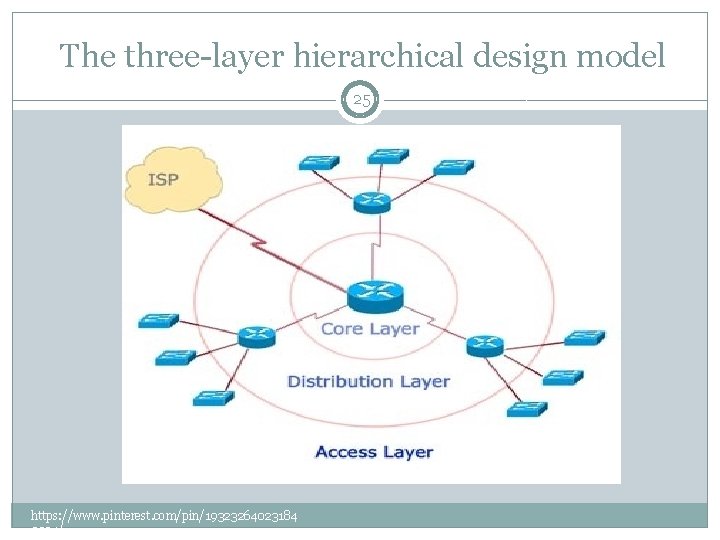
The three-layer hierarchical design model 24 �A hierarchical network design model breaks the complex problem of network design into smaller, more manageable problems. �Each level, or tier in the hierarchy addresses a different set of problems http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

The three-layer hierarchical design model 25 https: //www. pinterest. com/pin/19323264023184 3394/

The three-layer hierarchical design model 26 In the three-layer network design model, network devices and links are grouped according to three layers: • Core • Distribution • Access http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

The three-layer hierarchical design model 27 �Devices at each layer have similar and well-defined functions. �This allows administrators to easily add, replace, and remove individual pieces of the network. � This kind of flexibility and adaptability makes a hierarchical network design highly scalable. http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

The three-layer hierarchical design model 28 At the same time, layered models can be difficult to comprehend because the exact composition of each layer varies from network to network. Each layer of the three-tiered design model may include the following: • A router • A switch • A link • A combination of these http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

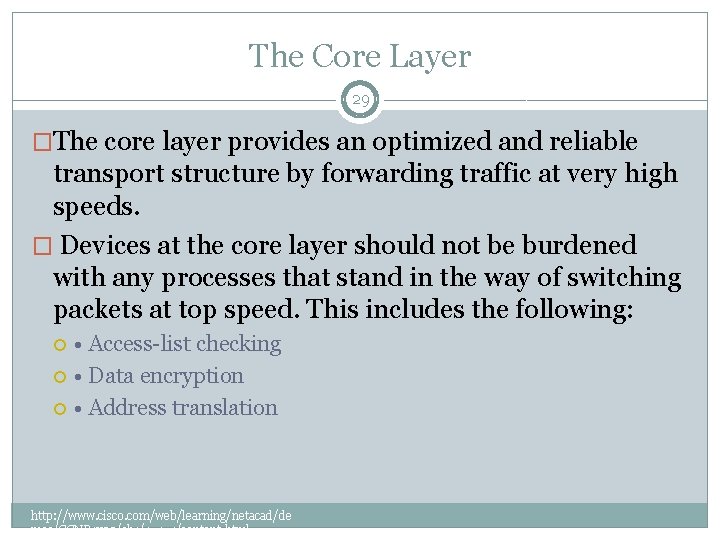
The Core Layer 29 �The core layer provides an optimized and reliable transport structure by forwarding traffic at very high speeds. � Devices at the core layer should not be burdened with any processes that stand in the way of switching packets at top speed. This includes the following: • Access-list checking • Data encryption • Address translation http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

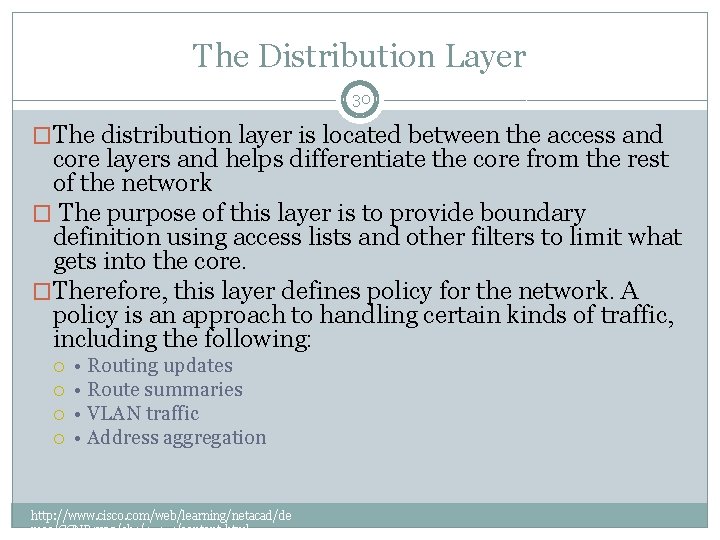
The Distribution Layer 30 �The distribution layer is located between the access and core layers and helps differentiate the core from the rest of the network � The purpose of this layer is to provide boundary definition using access lists and other filters to limit what gets into the core. �Therefore, this layer defines policy for the network. A policy is an approach to handling certain kinds of traffic, including the following: • Routing updates • Route summaries • VLAN traffic • Address aggregation http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

The Distribution Layer 31 �If a network has two or more routing protocols, information between the different routing domains is shared, or redistributed, at the distribution layer. http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

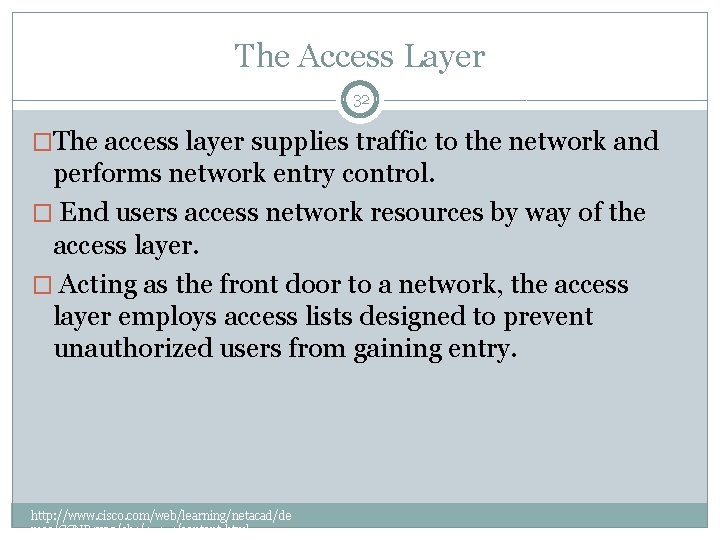
The Access Layer 32 �The access layer supplies traffic to the network and performs network entry control. � End users access network resources by way of the access layer. � Acting as the front door to a network, the access layer employs access lists designed to prevent unauthorized users from gaining entry. http: //www. cisco. com/web/learning/netacad/de mos/CCNP 1 v 30/ch 1/1_1_1/content. html

The three-layer hierarchical design model 33 http: //www. ciscopress. com/articles/printerfriend ly/169686

Wired and Wireless network management 34 PART 2: WIRELESS

outline 35 �Wireless applications �Wireless LAN transmission medium �WLAN modes �WLAN design consideration �WLAN management functions

Wireless applications 36 Some common applications of wireless data communication include the following: • Accessing the Internet using a cellular phone • Home or business Internet connection over satellite • Beaming data between two handheld computing devices • Wireless keyboard and mouse for the PC http: //www. ciscopress. com/articles/printerfriend ly/169686

WLAN 37 Another common application of wireless data communication is the wireless LAN (WLAN), which is built in accordance with Institute of Electrical and Electronic Engineers (IEEE) 802. 11 standards. . http: //www. ciscopress. com/articles/printerfriend ly/169686

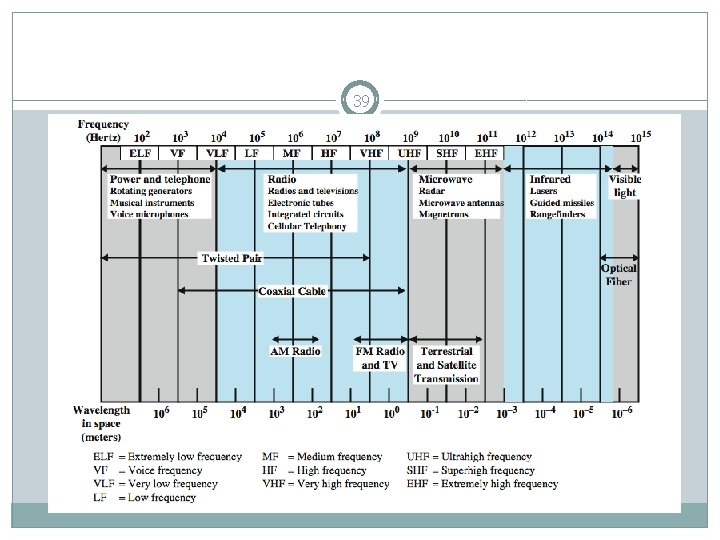
WLAN transmission medium 38 WLANs typically use: �Radio waves (for example, 902 MHz), �Microwaves (for example, 2. 4 GHz), �Infrared (IR) waves (for example, 820 nm) for communication. http: //www. ciscopress. com/articles/printerfriend ly/169686

39

WLAN modes 40 �Infrastructure mode �Ad hoc mode http: //ccm. net/contents/804 -wifi-modes-ofoperation-802 -11 -or-wi-fi

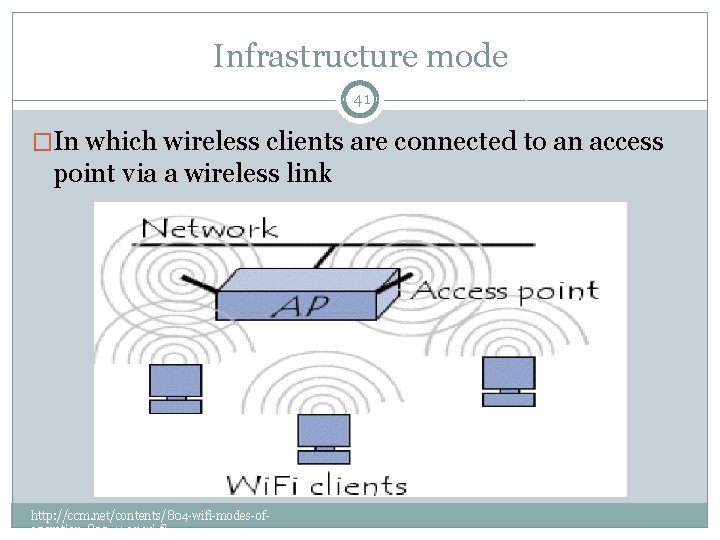
Infrastructure mode 41 �In which wireless clients are connected to an access point via a wireless link http: //ccm. net/contents/804 -wifi-modes-ofoperation-802 -11 -or-wi-fi

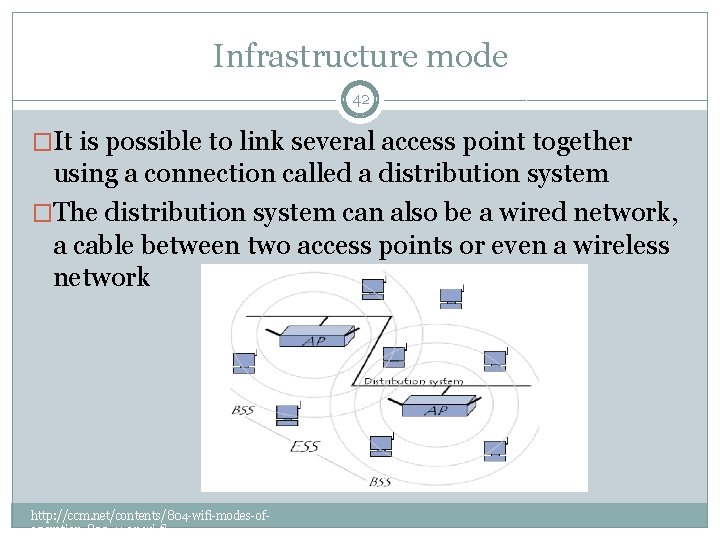
Infrastructure mode 42 �It is possible to link several access point together using a connection called a distribution system �The distribution system can also be a wired network, a cable between two access points or even a wireless network http: //ccm. net/contents/804 -wifi-modes-ofoperation-802 -11 -or-wi-fi

Infrastructure mode 43 �The closer an access point is, the higher its data transfer capacity is �So, a station within range of multiple access points may choose the access point offering the balance of capacity and current traffic load http: //ccm. net/contents/804 -wifi-modes-ofoperation-802 -11 -or-wi-fi

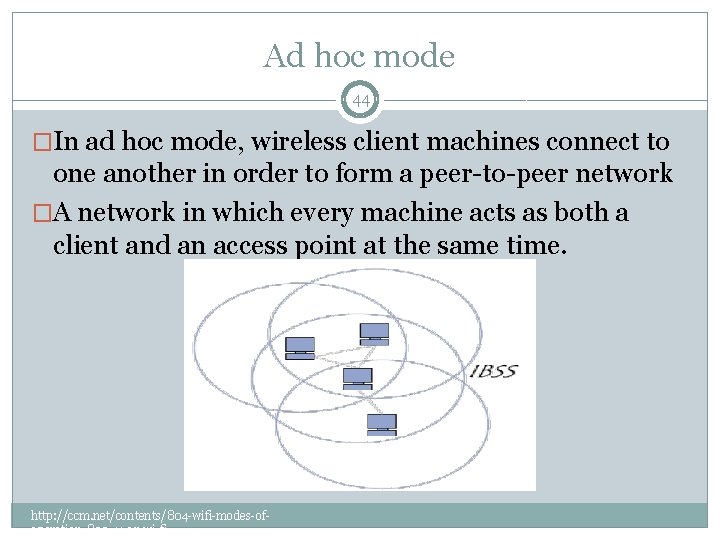
Ad hoc mode 44 �In ad hoc mode, wireless client machines connect to one another in order to form a peer-to-peer network �A network in which every machine acts as both a client and an access point at the same time. http: //ccm. net/contents/804 -wifi-modes-ofoperation-802 -11 -or-wi-fi

WLAN design consideration 45 �The following factors should be considered when designing wireless access layer: Client device power Radio frequency (RF) vulnerabilities Volume of network traffic Controller-Based Wireless LAN Fundamentals: An end-to-end reference guide to design, deploy, manage, and secure 802. 11 wireless networks 1 st Edition

Continuous Availability and Outage Planning 46 The factors that affect availability and for which the design considerations should be made to make the wireless deployment resilient include the following: �Power loss �RF interference Controller-Based Wireless LAN Fundamentals: An end-to-end reference guide to design, deploy, manage, and secure 802. 11 wireless networks 1 st Edition

WLAN capacity 47 It can be increased by: � increasing the number of cells making the cell size smaller, which means fewer users per cell sharing the media �Utilizing more channels which requires managing the RF spectrum Controller-Based Wireless LAN Fundamentals: An end-to-end reference guide to design, deploy, manage, and secure 802. 11 wireless networks 1 st Edition

key system management functions that should already be included in your WLAN bundle. 48 � WLAN planning tools � Automated deployment and operations � Monitoring and control � Optimization and extensibility � Reporting and logs � RF spectrum management � Security � Mobility management � Troubleshooting and remediation � Accessible interface � Managing voice services � Location and tracking � Visitor and guest access � Multi-site management http: //www. networkworld. com/article/2275699/wireless/navigating-the-wlan-management-maze. html