University of Science and Technology of China USTC














- Slides: 51

University of Science and Technology of China (USTC) Cryptography and Network Security Chapter 3 Block Cipher and Data Encryption Standard Fourth Edition by William Stallings



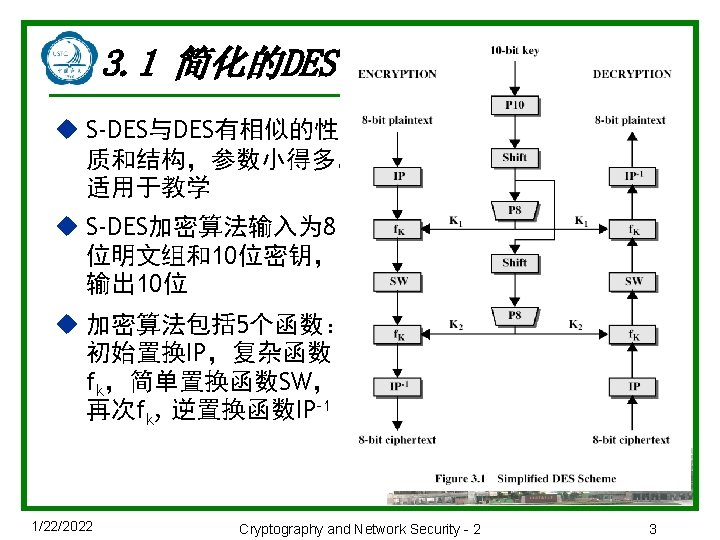
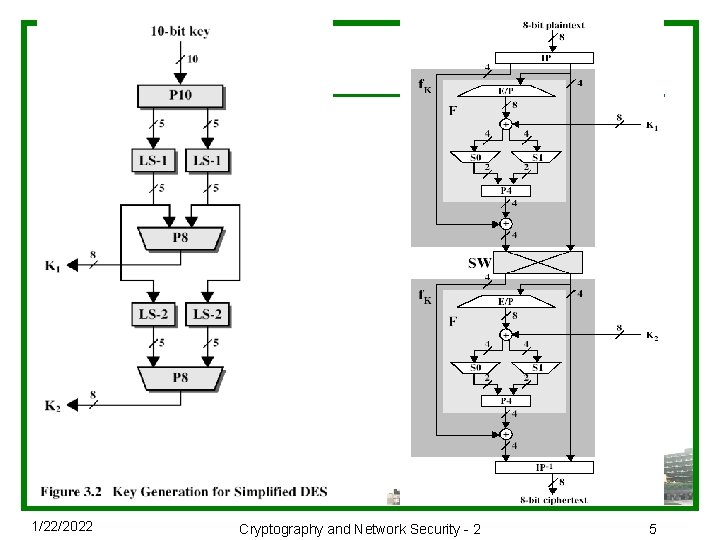
简化DES的加密和解密 u 加密过程: ciphertext = IP-1(f. K 2(SW(f. K 1(IP(plaintext))))) where K 1 = P 8(Shift(P 10(key))) K 2 = P 8(Shift(P 10(key)))) u 解密过程: plaintext = IP-1(f. K 1(SW(f. K 2(IP(ciphertext))))) 1/22/2022 Cryptography and Network Security - 2 4

1/22/2022 Cryptography and Network Security - 2 5



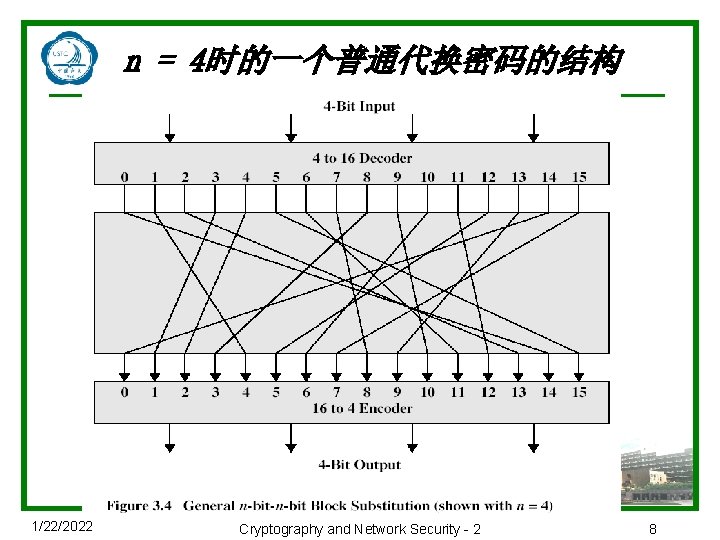
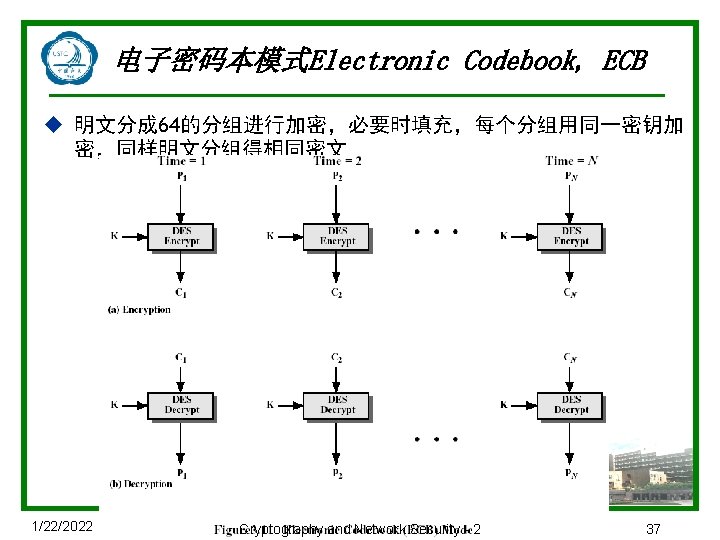
n = 4时的一个普通代换密码的结构 1/22/2022 Cryptography and Network Security - 2 8

1/22/2022 Cryptography and Network Security - 2 9

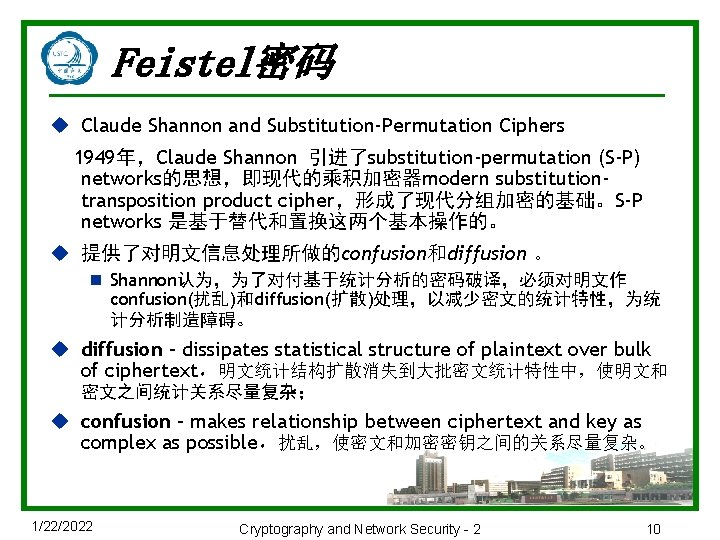
Feistel密码 u Claude Shannon and Substitution-Permutation Ciphers 1949年,Claude Shannon 引进了substitution-permutation (S-P) networks的思想,即现代的乘积加密器modern substitutiontransposition product cipher,形成了现代分组加密的基础。S-P networks 是基于替代和置换这两个基本操作的。 u 提供了对明文信息处理所做的confusion和diffusion 。 n Shannon认为,为了对付基于统计分析的密码破译,必须对明文作 confusion(扰乱)和diffusion(扩散)处理,以减少密文的统计特性,为统 计分析制造障碍。 u diffusion – dissipates statistical structure of plaintext over bulk of ciphertext,明文统计结构扩散消失到大批密文统计特性中,使明文和 密文之间统计关系尽量复杂; u confusion – makes relationship between ciphertext and key as complex as possible,扰乱,使密文和加密密钥之间的关系尽量复杂。 1/22/2022 Cryptography and Network Security - 2 10

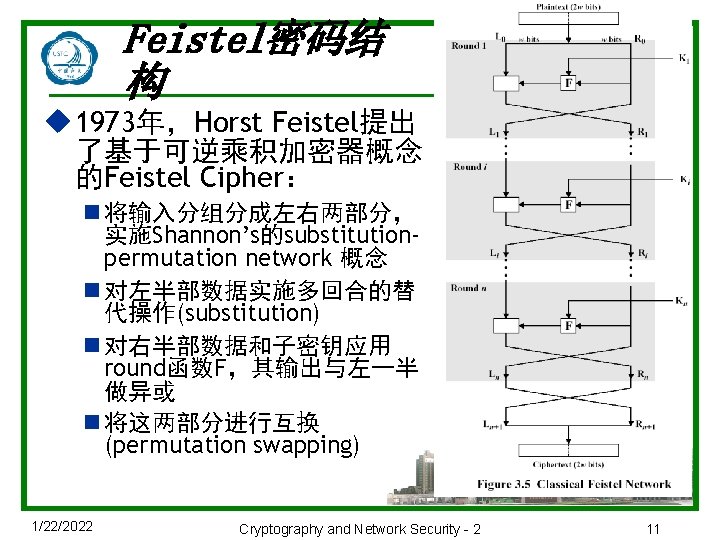
Feistel密码结 构 u 1973年,Horst Feistel提出 了基于可逆乘积加密器概念 的Feistel Cipher: n 将输入分组分成左右两部分, 实施Shannon’s的substitutionpermutation network 概念 n 对左半部数据实施多回合的替 代操作(substitution) n 对右半部数据和子密钥应用 round函数F,其输出与左一半 做异或 n 将这两部分进行互换 (permutation swapping) 1/22/2022 Cryptography and Network Security - 2 11


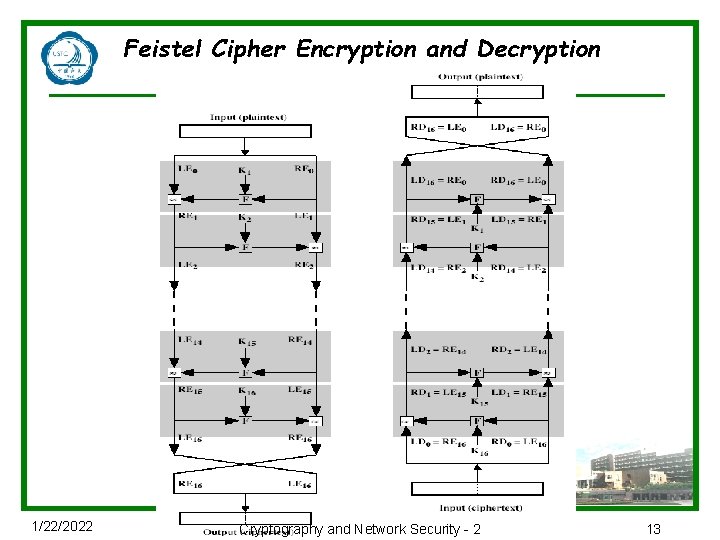
Feistel Cipher Encryption and Decryption 1/22/2022 Cryptography and Network Security - 2 13

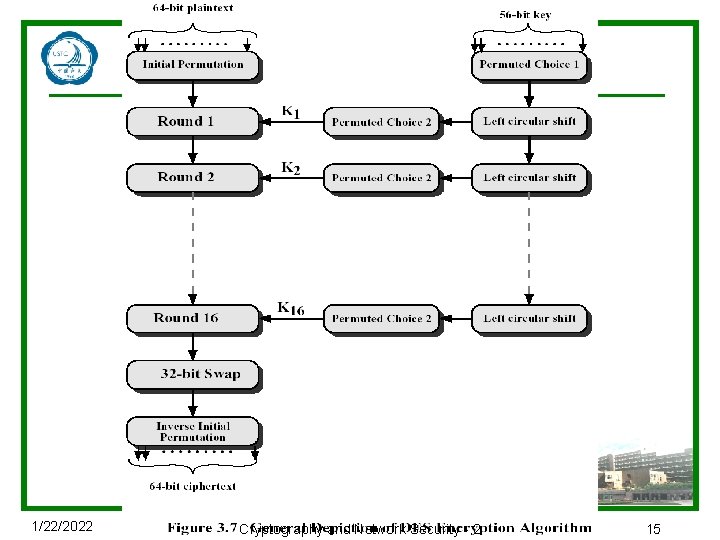
3. 3 数据加密标准 u 历史的回顾 n IBM developed Lucifer cipher (1971) • by team led by Horst Feistel • used 64 -bit data blocks with 128 -bit key n Tuchman-Mayer redeveloped as a commercial cipher with input from NSA and others, 56 -bit key, easy to implement on single chip n In 1973 NBS issued request for proposals for a national cipher standard n IBM submitted their revised Lucifer which was eventually accepted as the DES u DES加密 1/22/2022 Cryptography and Network Security - 2 14

1/22/2022 Cryptography and Network Security - 2 15

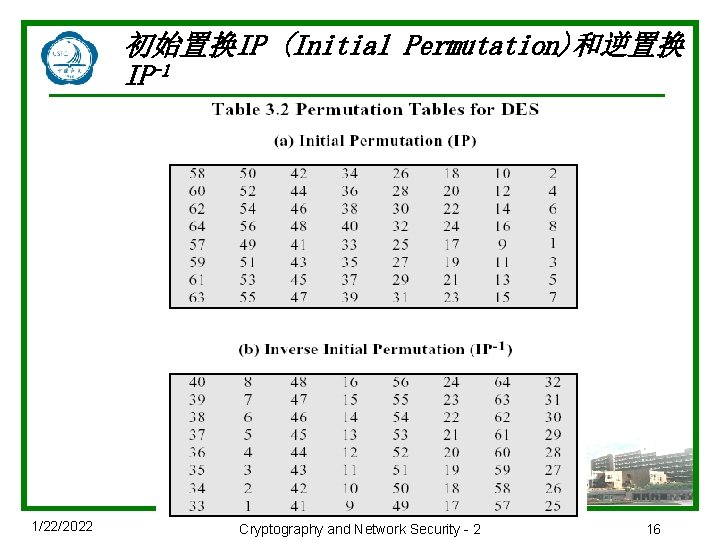
初始置换IP (Initial Permutation)和逆置换 IP-1 1/22/2022 Cryptography and Network Security - 2 16

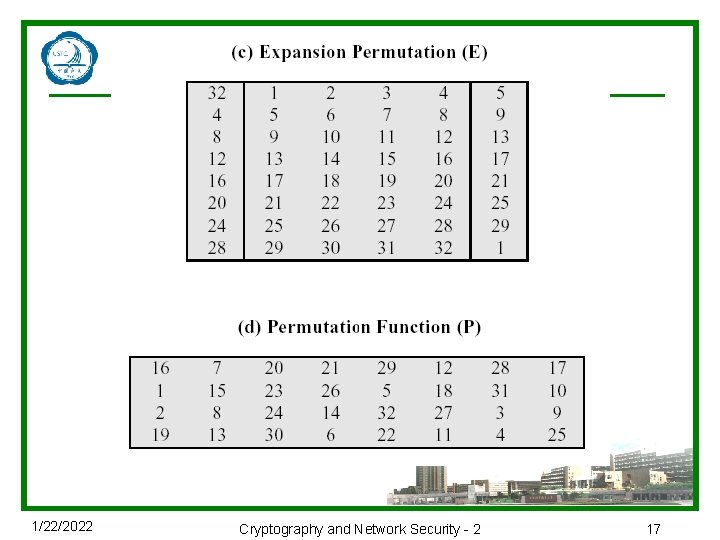
1/22/2022 Cryptography and Network Security - 2 17

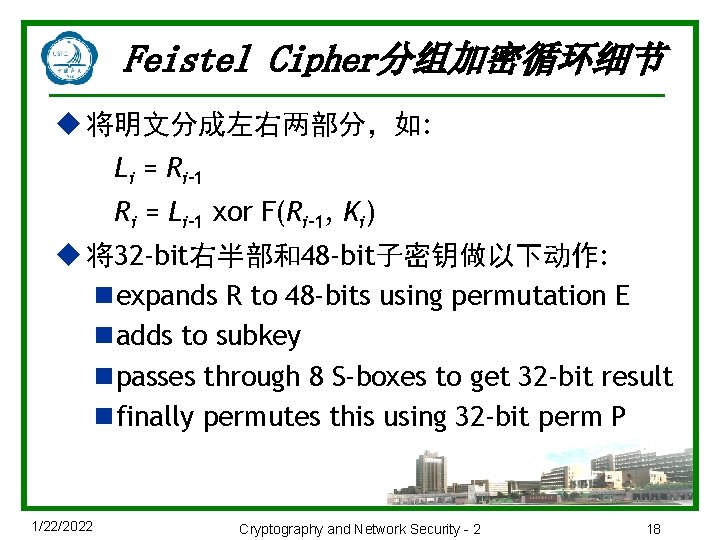
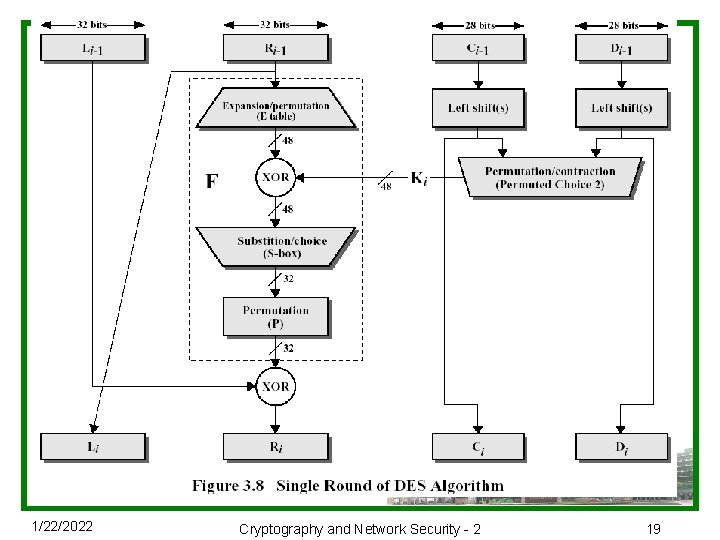
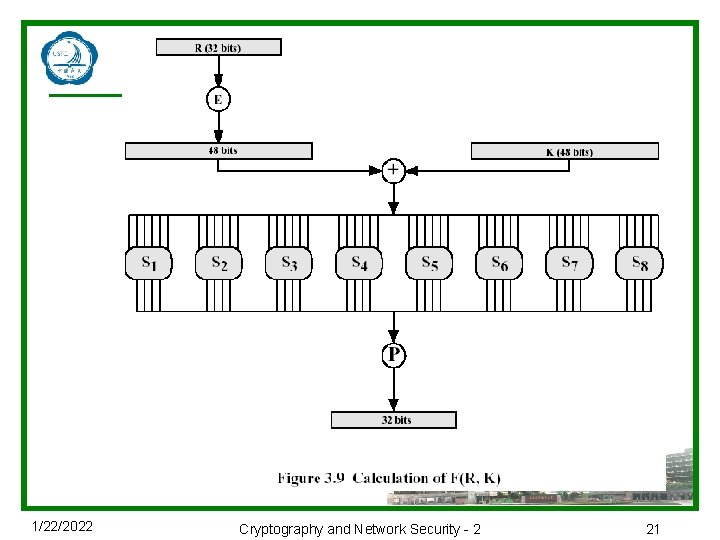
Feistel Cipher分组加密循环细节 u 将明文分成左右两部分,如: Li = Ri– 1 Ri = Li– 1 xor F(Ri– 1, Ki) u 将32 -bit右半部和48 -bit子密钥做以下动作: nexpands R to 48 -bits using permutation E nadds to subkey npasses through 8 S-boxes to get 32 -bit result nfinally permutes this using 32 -bit perm P 1/22/2022 Cryptography and Network Security - 2 18

1/22/2022 Cryptography and Network Security - 2 19

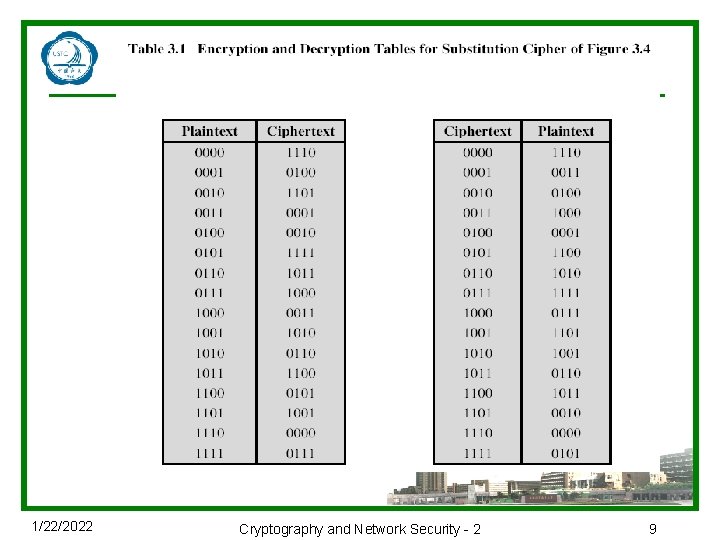
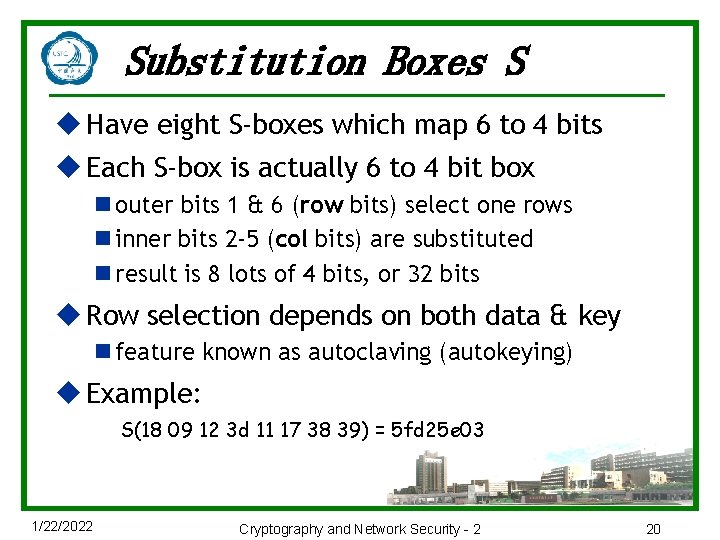
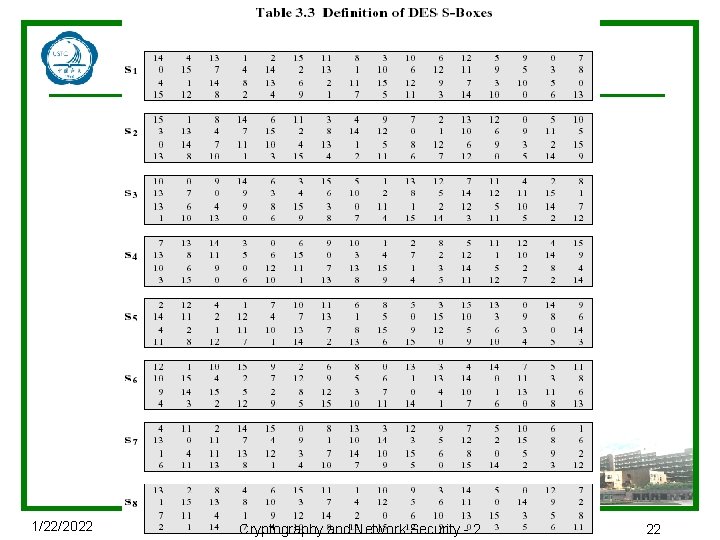
Substitution Boxes S u Have eight S-boxes which map 6 to 4 bits u Each S-box is actually 6 to 4 bit box n outer bits 1 & 6 (row bits) select one rows n inner bits 2 -5 (col bits) are substituted n result is 8 lots of 4 bits, or 32 bits u Row selection depends on both data & key n feature known as autoclaving (autokeying) u Example: S(18 09 12 3 d 11 17 38 39) = 5 fd 25 e 03 1/22/2022 Cryptography and Network Security - 2 20

1/22/2022 Cryptography and Network Security - 2 21

1/22/2022 Cryptography and Network Security - 2 22

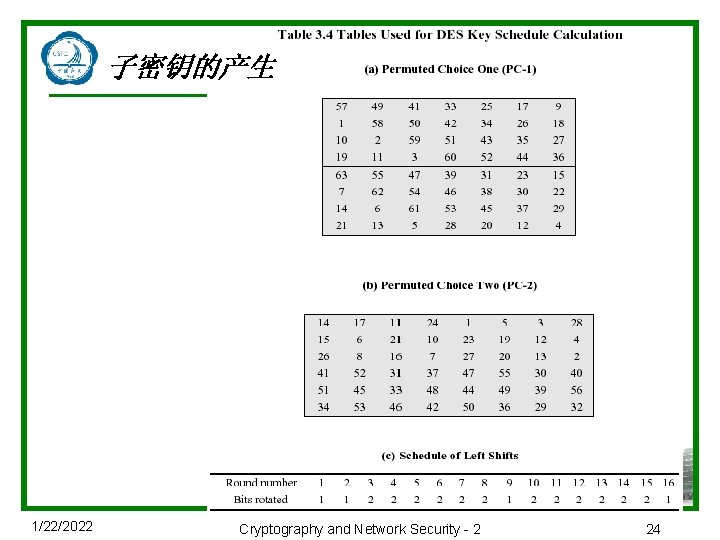
子密钥的产生 u. Forms subkeys used in each round u. Consists of: n. Initial permutation of the key (PC 1) which selects 56 -bits in two 28 -bit halves n 16 stages consisting of: • selecting 24 -bits from each half • permuting them by PC 2 for use in function f, • rotating each half separately either 1 or 2 places depending on the key rotation schedule K 1/22/2022 Cryptography and Network Security - 2 23

子密钥的产生 1/22/2022 Cryptography and Network Security - 2 24


1/22/2022 Cryptography and Network Security - 2 26



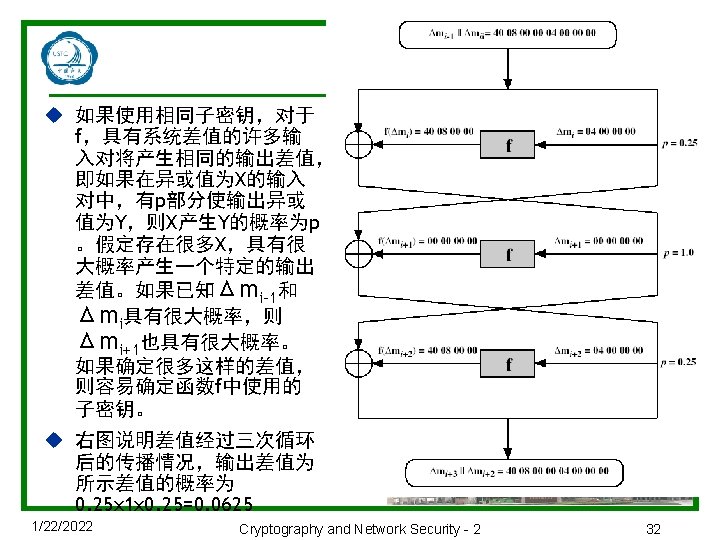
3. 5 差分分析和线性分析 u 差分密码分析Differential Cryptanalysis n 历史 1990年,Murphy、Biham和Shamir首次提出用差分密码分析攻击 分组密码和散列函数,是第一种可以以少于255的复杂性对DES进行 破译的方法。 Differential Cryptanalysis compares two related pairs of encryptions. n 差分密码分析攻击方法 with a known difference in the input, searching for a known difference in output when same subkeys are used. 两个报文的异或Δm=m⊕m’,中间过程有Δmi=mi⊕mi’,则 1/22/2022 Cryptography and Network Security - 2 29

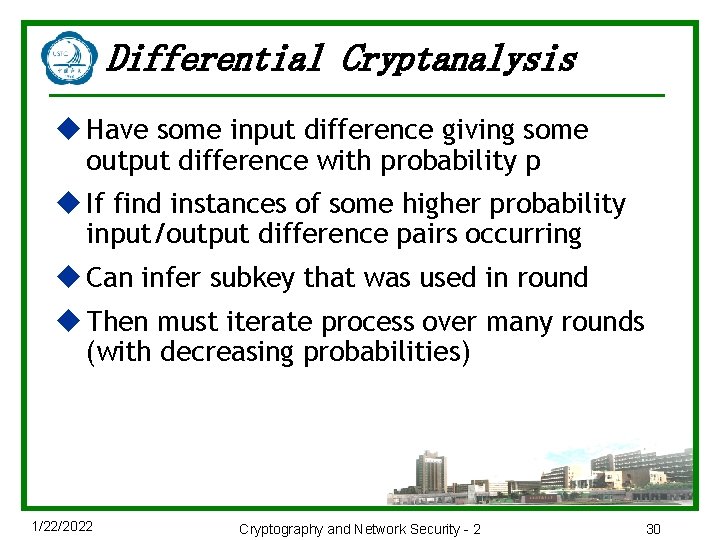
Differential Cryptanalysis u Have some input difference giving some output difference with probability p u If find instances of some higher probability input/output difference pairs occurring u Can infer subkey that was used in round u Then must iterate process over many rounds (with decreasing probabilities) 1/22/2022 Cryptography and Network Security - 2 30

Differential Cryptanalysis u Perform attack by repeatedly encrypting plaintext pairs with known input XOR until obtain desired output XOR u When found n if intermediate rounds match required XOR have a right pair n if not then have a wrong pair, relative ratio is S/N for attack u Can then deduce keys values for the rounds n right pairs suggest same key bits n wrong pairs give random values u For large numbers of rounds, probability is so low that more pairs are required than exist with 64 -bit inputs u Biham and Shamir have shown how a 13 -round iterated characteristic can break the full 16 -round DES 1/22/2022 Cryptography and Network Security - 2 31





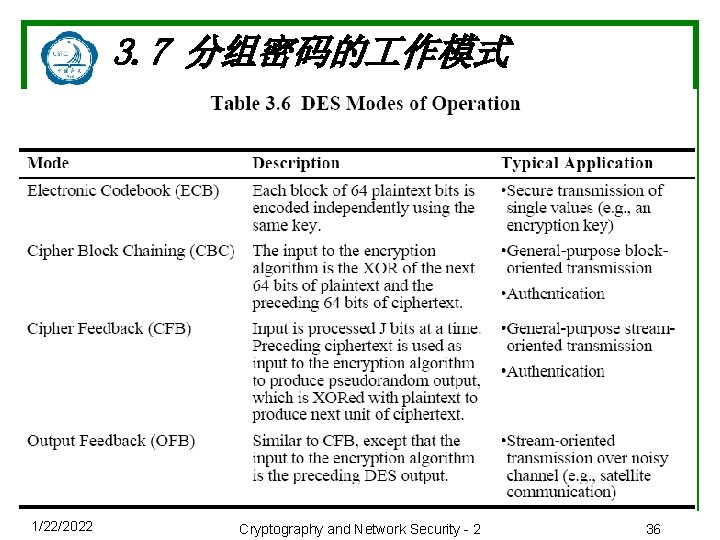
3. 7 分组密码的 作模式 1/22/2022 Cryptography and Network Security - 2 36


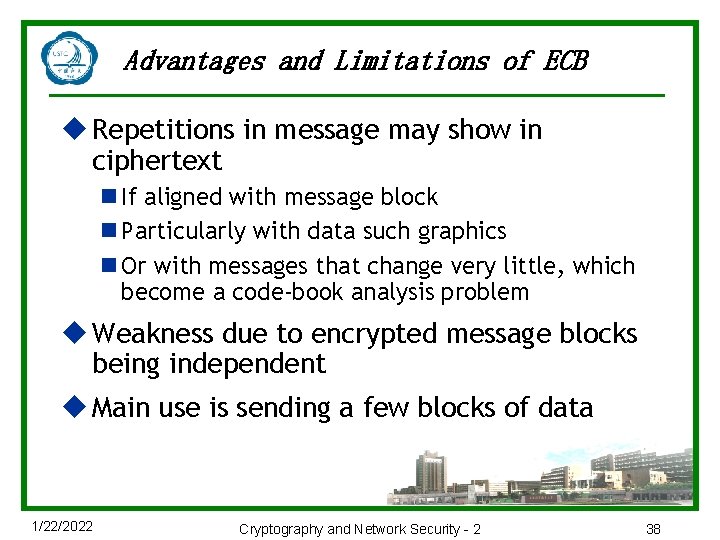
Advantages and Limitations of ECB u Repetitions in message may show in ciphertext n If aligned with message block n Particularly with data such graphics n Or with messages that change very little, which become a code-book analysis problem u Weakness due to encrypted message blocks being independent u Main use is sending a few blocks of data 1/22/2022 Cryptography and Network Security - 2 38


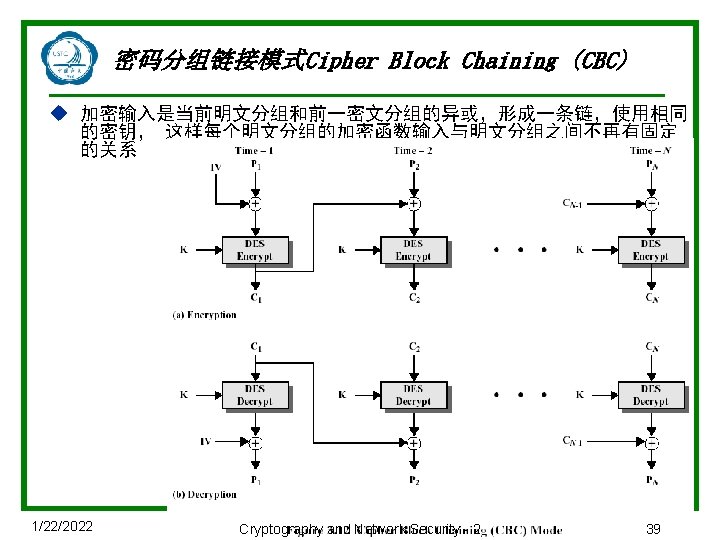
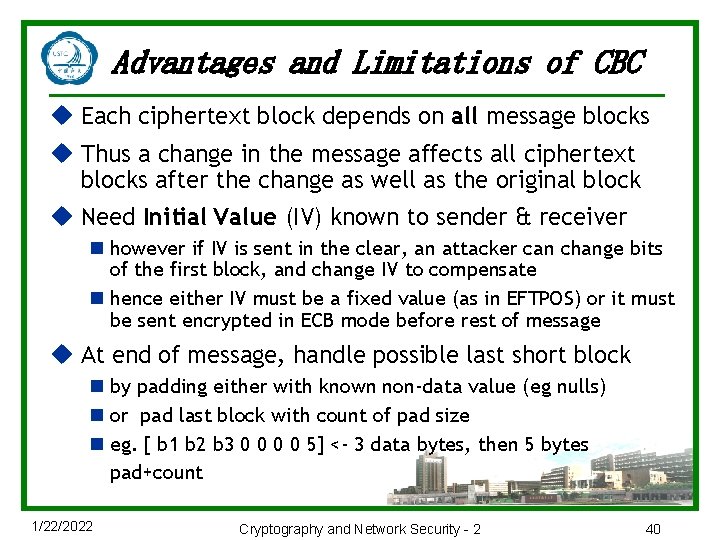
Advantages and Limitations of CBC u Each ciphertext block depends on all message blocks u Thus a change in the message affects all ciphertext blocks after the change as well as the original block u Need Initial Value (IV) known to sender & receiver n however if IV is sent in the clear, an attacker can change bits of the first block, and change IV to compensate n hence either IV must be a fixed value (as in EFTPOS) or it must be sent encrypted in ECB mode before rest of message u At end of message, handle possible last short block n by padding either with known non-data value (eg nulls) n or pad last block with count of pad size n eg. [ b 1 b 2 b 3 0 0 5] <- 3 data bytes, then 5 bytes pad+count 1/22/2022 Cryptography and Network Security - 2 40


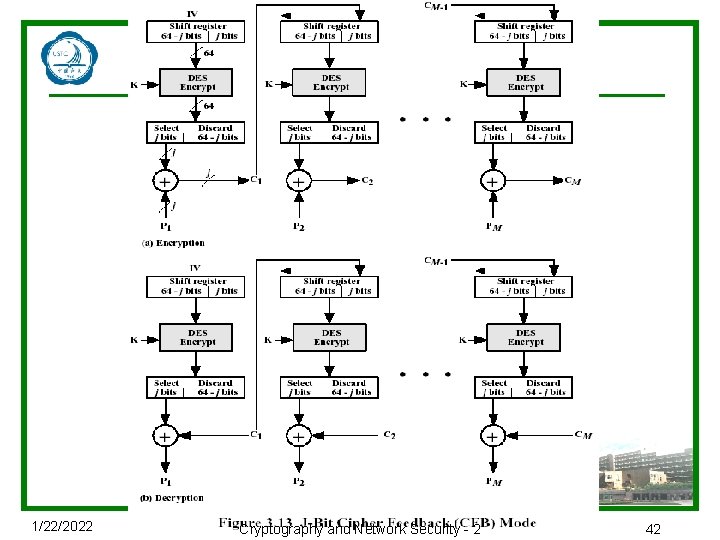
1/22/2022 Cryptography and Network Security - 2 42

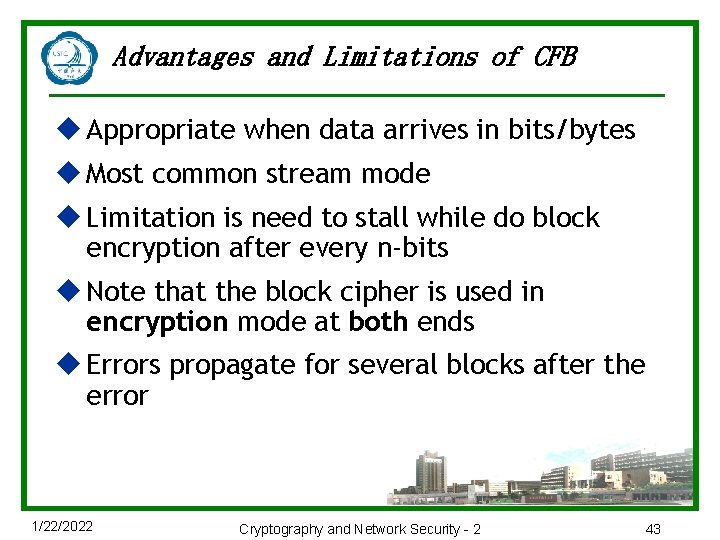
Advantages and Limitations of CFB u Appropriate when data arrives in bits/bytes u Most common stream mode u Limitation is need to stall while do block encryption after every n-bits u Note that the block cipher is used in encryption mode at both ends u Errors propagate for several blocks after the error 1/22/2022 Cryptography and Network Security - 2 43


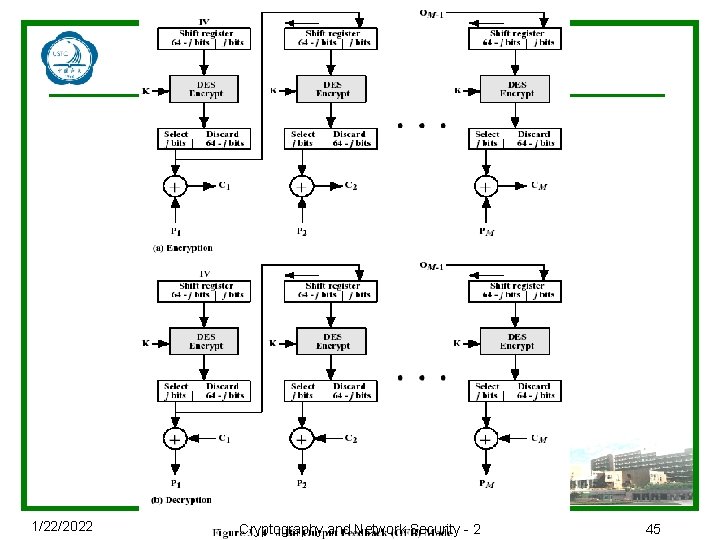
1/22/2022 Cryptography and Network Security - 2 45

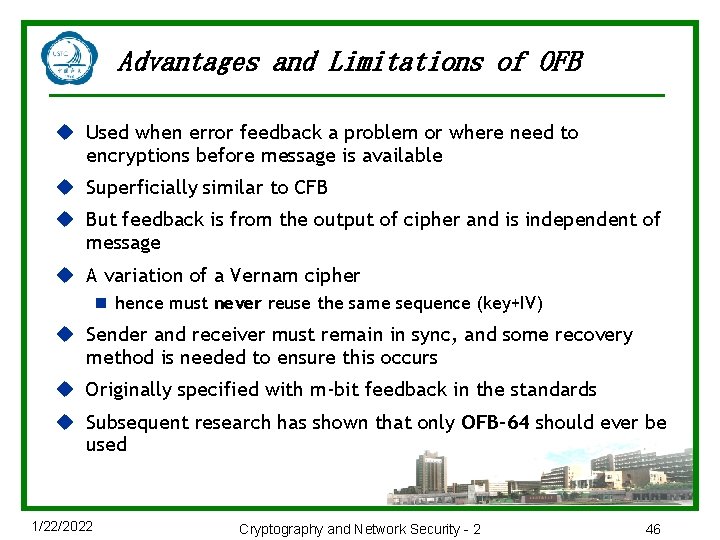
Advantages and Limitations of OFB u Used when error feedback a problem or where need to encryptions before message is available u Superficially similar to CFB u But feedback is from the output of cipher and is independent of message u A variation of a Vernam cipher n hence must never reuse the same sequence (key+IV) u Sender and receiver must remain in sync, and some recovery method is needed to ensure this occurs u Originally specified with m-bit feedback in the standards u Subsequent research has shown that only OFB-64 should ever be used 1/22/2022 Cryptography and Network Security - 2 46

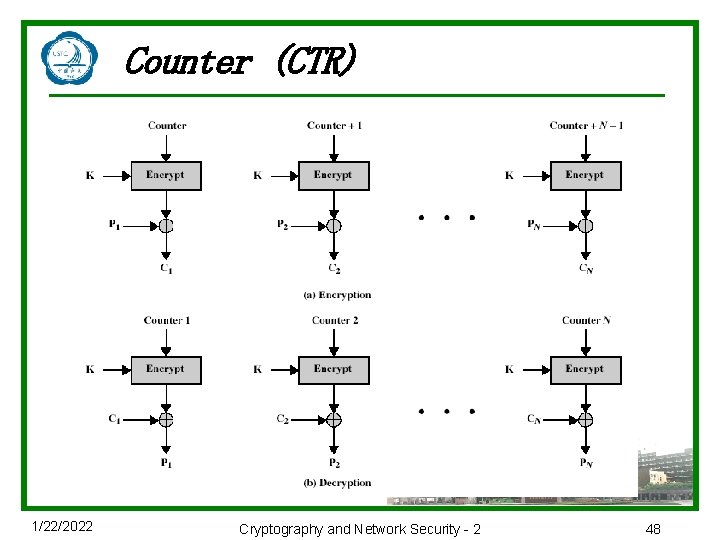
计数器模式Counter (CRT) u. Counter (CTR) n. A “new” mode, though proposed early on n. Similar to OFB but encrypts counter value rather than any feedback value n. Must have a different key & counter value for every plaintext block (never reused) Ci = Pi XOR Oi Oi = DESK 1(i) n. Uses: high-speed network encryptions 1/22/2022 Cryptography and Network Security - 2 47

Counter (CTR) 1/22/2022 Cryptography and Network Security - 2 48

Advantages and Limitations of CTR u Efficiency n can do parallel encryptions n in advance of need n good for burst high speed links u Random access to encrypted data blocks u Provable security (good as other modes) u But must ensure never reuse key/counter values, otherwise could break (cf OFB) u Simplicity 1/22/2022 Cryptography and Network Security - 2 49

Summary We have considered in this chapter: u. Block cipher design principles u. DES ndetails nstrength u. Differential & Linear Cryptanalysis u. Modes of Operation n. ECB, CBC, CFB, OFB, CTR 1/22/2022 Cryptography and Network Security - 2 50

Assignments u. William Stallings book, Chapter 3: 第四版: 3. 5,3. 11,3. 12,3. 13,3. 14 第三版: 3. 4,3. 11,3. 12,3. 13,3. 14 Due day: October 8 th, 2007 1/22/2022 Cryptography and Network Security - 2 51
 Lunc and ustc
Lunc and ustc East china university of political science and law
East china university of political science and law Ustc repeg
Ustc repeg Mail.ustc.edu.n
Mail.ustc.edu.n Dong liu ustc
Dong liu ustc Dong liu ustc
Dong liu ustc Ustc search
Ustc search Dong liu ustc
Dong liu ustc Usth
Usth Ulsan university of science and technology
Ulsan university of science and technology Science technology university yemen
Science technology university yemen Jordan university of science and technology
Jordan university of science and technology Jordan university of science and technology
Jordan university of science and technology Jordan university of science and technology
Jordan university of science and technology University of shanghai for science and technology
University of shanghai for science and technology University of science and technology of mazandaran
University of science and technology of mazandaran Pingtung university of science and technology
Pingtung university of science and technology University of science and technology kumasi
University of science and technology kumasi Mongolian university of science and technology logo
Mongolian university of science and technology logo National yunlin university of science and technology
National yunlin university of science and technology Science fusion online
Science fusion online My favorite subject is english and math
My favorite subject is english and math China automotive technology & research center
China automotive technology & research center China telecommunication technology labs
China telecommunication technology labs China titans energy technology group
China titans energy technology group China telecommunication technology labs
China telecommunication technology labs National natural science foundation of china
National natural science foundation of china University of chemistry and technology in prague
University of chemistry and technology in prague University of chemical technology and metallurgy sofia
University of chemical technology and metallurgy sofia Moscow state university of design and technology
Moscow state university of design and technology Georgetown university communication culture and technology
Georgetown university communication culture and technology Bme gtk neptun
Bme gtk neptun Budapest university of technology and economics
Budapest university of technology and economics Budapest university of technology and economics rector
Budapest university of technology and economics rector University of chemistry and technology prague tuition fee
University of chemistry and technology prague tuition fee Kazakh university of technology and business
Kazakh university of technology and business Georgetown university communication culture and technology
Georgetown university communication culture and technology Georgetown university communication culture and technology
Georgetown university communication culture and technology Scste meghalaya
Scste meghalaya Mail @ stcu.int
Mail @ stcu.int Masdar institute of science and technology
Masdar institute of science and technology Madhav institute of technology and science
Madhav institute of technology and science Grade 4 natural science term 2 practical tasks
Grade 4 natural science term 2 practical tasks Science, technology and society module answer key
Science, technology and society module answer key Adverb science
Adverb science Stone age science and technology
Stone age science and technology Tufts science and technology center
Tufts science and technology center Term 4 natural science grade 6
Term 4 natural science grade 6 Ns grade 6 term 2
Ns grade 6 term 2 Natural science grade 6 term 1
Natural science grade 6 term 1 Kigali institute of science and technology
Kigali institute of science and technology Journal of semiconductor technology and science
Journal of semiconductor technology and science