The Honeynet Project Trapping the Hackers Lance Spitzner



























- Slides: 33

The Honeynet Project: Trapping the Hackers Lance Spitzner, Sun Microsystems Presented by Vikrant Karan 1

Outline l l l The Honeynet Project Honeypots: Not just for bears anymore Different kinds of honeynets What the honeynet collects The legal ramifications of operating a honeypot Conclusion 2

The Honeynet Project l Few questions in front of security professionals: – What specific threats do computer networks face from hackers? – Who's perpetrating these threats and how? 3

The Honeynet Project l The Honeynet Project is an organization dedicated to answering these questions. It studies the bad guys and shares the lessons learned. The group gathers information by deploying networks (called honeynets) that are designed to be compromised. 4

The Honeynet Project l a security-research organization dedicated to learning the black-hat community's tools, tactics, and motives and then sharing any lessons learned. l The organization comprises international security professionals who volunteer their time and resources to deploy networks (or honeynets) that are designed to be attacked. l The team then analyzes the information collected from these attacks. 5

The Honeynet Project began in 1999 as an informal mailing list of a small group of individuals l Official declaration in June 2000 l board of directors, including Bruce Schneier, George Kurtz, Elias Levy, and Jennifer Granick. l Honeynet Research Alliance's include organizations in Brazil, Greece, India, Mexico, Ireland, and the l United States. 6

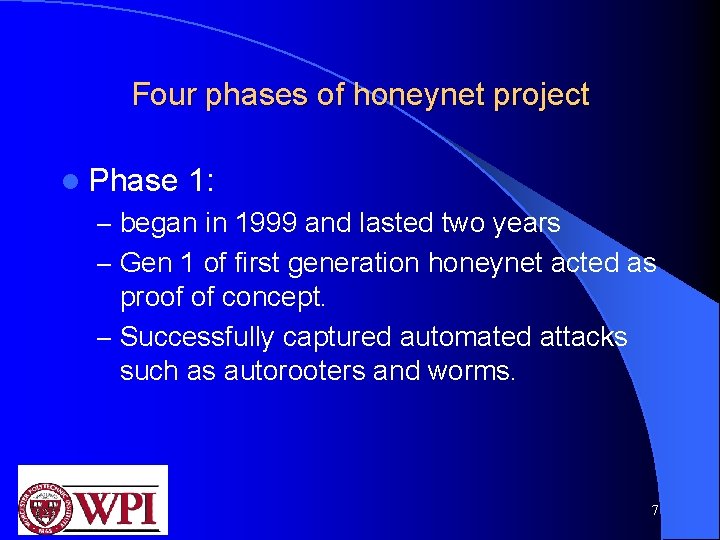
Four phases of honeynet project l Phase 1: – began in 1999 and lasted two years – Gen 1 of first generation honeynet acted as proof of concept. – Successfully captured automated attacks such as autorooters and worms. 7

Four phases of honeynet project l Phase 2: – began in 2002 and will continue for two years. – Gen. II honeynets, will feature more advanced methods to monitor and control attacker's activities. – Published 3 papers and deployed the first wireless honeynet in 2002 in Washington, DC – More improved and easy to deploy solutions. 8

Four phases of honeynet project l Phase 3: – begins in 2003 and should last approximately one year – Apply Gen 2 technology into bootable CDROM. – Organizations only need to boot the CDROM to get honeynet functionality. – It allows to log all captured activities in a centralized data base. 9

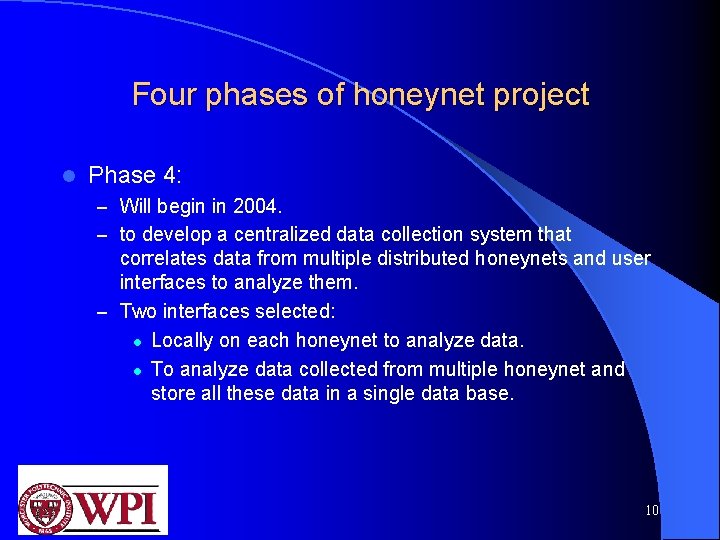
Four phases of honeynet project l Phase 4: – Will begin in 2004. – to develop a centralized data collection system that correlates data from multiple distributed honeynets and user interfaces to analyze them. – Two interfaces selected: l Locally on each honeynet to analyze data. l To analyze data collected from multiple honeynet and store all these data in a single data base. 10

Honeypots: Not just for bears anymore A security resource whose value lies in being probed attacked, or compromised. l if any packet or any interaction is attempted with your honeypot, it's most likely a probe, scan or attack l Honeypots get little traffic, but what they do get is of high value. l Disadvantages: – limited view field: they only capture activity directed towards them, thus missing some of the attacks directed towards servers. – It may be used to attack other systems. l 11

Categories of honeypots Production honeypots: – protect the organization – directly increase resource security – organizations can prevent, detect, or respond to attacks. l Research honeypots: – gathers information on attackers. – Distributed research honeypots can gather information on a global scale l l production honeypots is easier to deploy but capture less information on attackers. 12

Data capture and data control system Data capture ensures that you can detect and capture all the attacker's activities, even if they are obfuscated or encrypted. l Data control's purpose is to reduce risk it ensures that once an attacker breaks into your honeynet's systems, those compromised systems cannot be used to attack or harm other systems. l 13

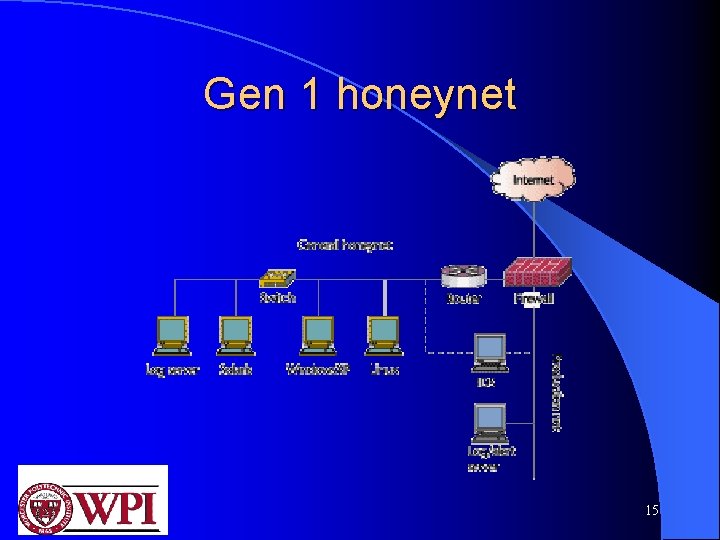
Different kinds of honeynets A honeynet is essentially a research honeypot; its purpose is to collect information on attackers. l it uses real systems and applications. l l Gen 1 honeynet 14

Gen 1 honeynet 15

Gen 1 honeynet (contd) l l l Honeynet is a contained environment in which you can watch everything happening. Positioned in this environment are the target systems (highlighted in yellow). counts the number of outbound connections. systems initiate a certain number of outbound connections and then block any further links once the limit is met. Useful for blocking denial of service attacks scans, or other malicious activity But, gives attacker more room to attack. 16

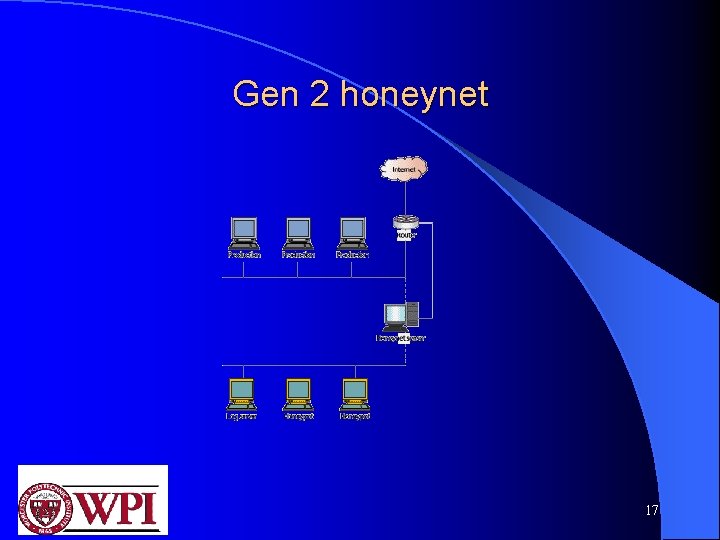
Gen 2 honeynet 17

Gen 2 honeynet(contd. . ) This forces all traffic going to and from the honeynet systems to first flow through an "invisible" layer-two bridge l This bridge lets the bad guys come in, but it controls what they can do on their way out. l layer-two bridging device (called the honeynet sensor in the l figure) isolates and contains systems in the honeynet. allows outbound activity but removing the ability to harm. l a second layer of data control: an IPS (or intrusion prevention system) gateway l 18

Snort inline l an open-source IDS technology l Instead of blocking detected outbound attacks, we modify and disable them l One risk is the chance that the IDS gateway will not detect a new or obfuscated attack 19

Snort inline example 20

Snort inline (contd. . ) l Snort-Inline signature used to modify and disable a known DNS attack using the replace option. l Highlighted in bold is the command used to modify and disable the attack. 21

Data capture elements Layer 1: The IDS gateway that identifies and blocks attacks passively sniffs every packet and its full payload on the network. l Layer 2: the firewall log: packet-filtering mechanism to block outbound connections once a connection limit is met. l layer 3: is for capturing the attacker's keystrokes and activity on the system. l 22

Data capture elements Honeynet Project has developed kernel modules to insert in target systems. l These capture all the attacker's activities, such as encrypted keystrokes or scp. l The IDS gateway captures all the data and dump the data generated by the attackers without letting attacker know. l multiple layers of data capture help ensure that we gain a clear perspective of the attacker's activities. l 23

Examples Honeynet Project has actively deployed different types of operating systems in its honeynets – Solaris-, Open. BSD-, Linux-, and Window-based honeypots. l Windows: worms or simple automated attacks, such as scans for open shares or pop-up l Linux systems: commonly known vulnerabilities and automated attack tools, such as TESO's wu-ftpd massrooter. l Solaris and Open BSD: more advanced or interesting attacks, such as the use of IPv 6 tunneling l 24

What the honeynet collects captured in Jan 2002: Captured IP protocol 11 packet sent to the hacked honeypot. The command is encoded to obfuscate its purpose l Data 25

Captured data 26

Decoded Packet 27

Figure explanation an example of how commands were remotely sent to the hacked system. l actual command being executed on the remote system. l attacker is telling our hacked honeypot to download a tool from another hacked site, run the tool, and then delete the downloaded binary. l In this case, the tool was used to proxy IRC sessions. l 28

The legal ramifications of operating a honeypot l Three legal issues need to be considered: – take into account the laws that restrict your right to monitor user activities on your system – recognize and address the risk that attackers will misuse your honeypot to harm others. – defendant could argue that your undercover server entrapped him or her 29

Monitoring users l Monitoring can be made improper by statutes (state and federal), privacy or employment policies, terms-of-service agreements, l Honeypots monitors the user traffic, therefore it should be designed carefully. 30

Limitations in US Constitution and federal statutes Fourth Amendment: It can restrict monitoring and evidence obtained from monitoring in violation of the Constitution can be suppressed at trial l Wiretap Act: It forbids anyone from intercepting communications unless one of the exceptions listed in the act applies. l Patriot Act: expressly authorizes warrantless monitoring of hackers by the government in certain situations. l 31

Limitations in US Constitution and federal statutes(contd. . ) l Harming others: Pay attention to your honeypot to reduce the risk that it will be used for illegal purposes. l Entrapment: This issue has been overstated by the critique. 32

Conclusion Honeynet technology collect valuable information which can avoid security risks. l honeynets' real potential will not be realized until organizations can effectively deploy multiple honeynets and correlate the information they collect l bootable CD ROM, which will make honeynets much easier to deploy and standardize the information they collect. l 33