http project honeynet orgmiscproject html Use of Honeypots








- Slides: 18

http: //project. honeynet. org/misc/project. html Use of Honey-pots to Detect Exploited Systems Across Large Enterprise Networks Ashish Gupta Network Security May 2004

Overview • Motivation • What are Honeypots? – Gen I and Gen II • The Georgia. Tech Honeynet System – Hardware/Software – IDS – Logging and review • Some detected Exploitations – Worm exploits – Sage of the Warez Exploit • Words of Wisdom • Conclusions

Why Honeynets ? An additional layer of security

Security: A serious Problem Firewall IDS A Traffic Cop Detection and Alert Problems: Internal Threats False Positives Virus Laden Programs False Negatives

The Security Problem Firewall IDS Honey. Nets An additional layer of security

• • Captures all inbound/outbound data Standard production systems Intended to be compromised Data Capture – Stealth capturing – Storage location – away from the honeynet • Data control – Protect the network from honeynets

Two types Gen II Good for simpler attacks Unsophisticated targets Sophisticated Data Control : Stealth Fire-walling Limited Data Control Gen I chosen


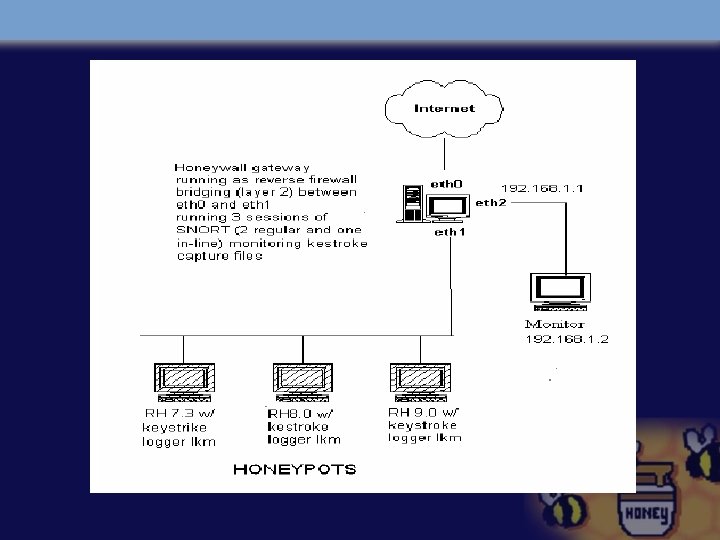
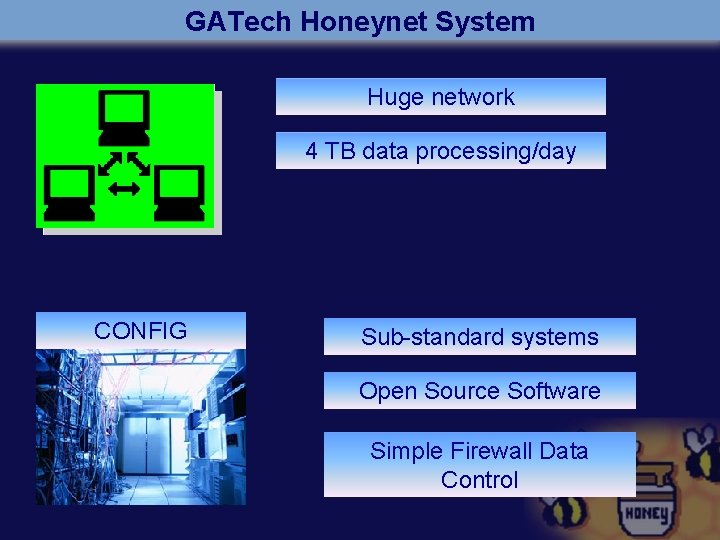
GATech Honeynet System Huge network 4 TB data processing/day CONFIG Sub-standard systems Open Source Software Simple Firewall Data Control

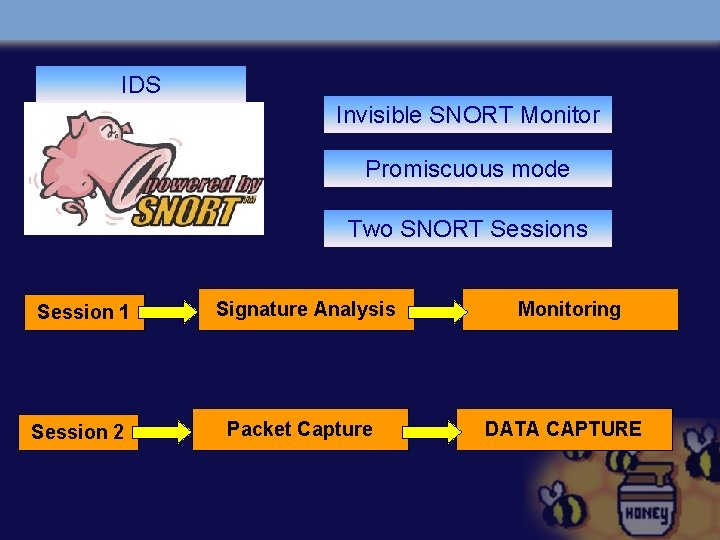
IDS Invisible SNORT Monitor Promiscuous mode Two SNORT Sessions Session 1 Signature Analysis Monitoring Session 2 Packet Capture DATA CAPTURE


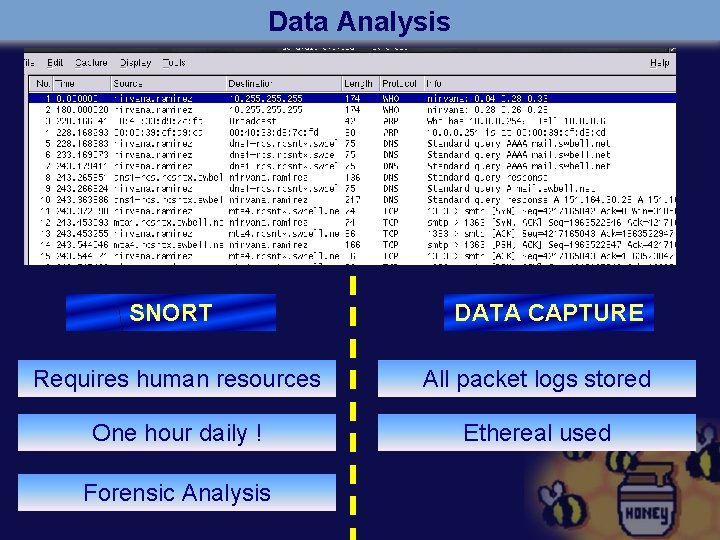
Data Analysis SNORT DATA CAPTURE Requires human resources All packet logs stored One hour daily ! Ethereal used Forensic Analysis

Detected Exploitations 16 compromises detected Worm attacks Hacker Attacks

DETECTING WORM EXPLOITS Honey Net traffic is Suspicious Heuristic for worm detection: Frequent port scans Specific OS-vulnerability monitoring possible Captured traffic helps signature development

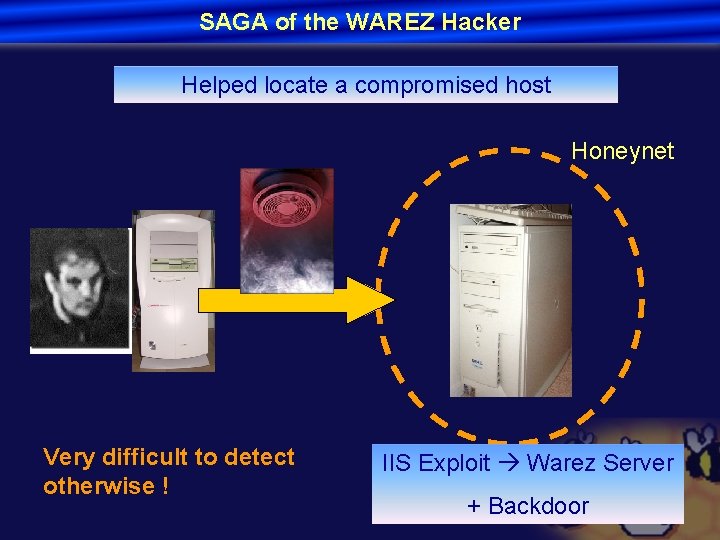
SAGA of the WAREZ Hacker Helped locate a compromised host Honeynet Very difficult to detect otherwise ! IIS Exploit Warez Server + Backdoor

Words of Wisdom • • • Start small Good relationships help Focus on Internal attacks Don’t advertise Be prepared to spend time

Conclusion • Helped locate compromised systems • Can boost IDS research – Data capture • Distributed Honey nets ?

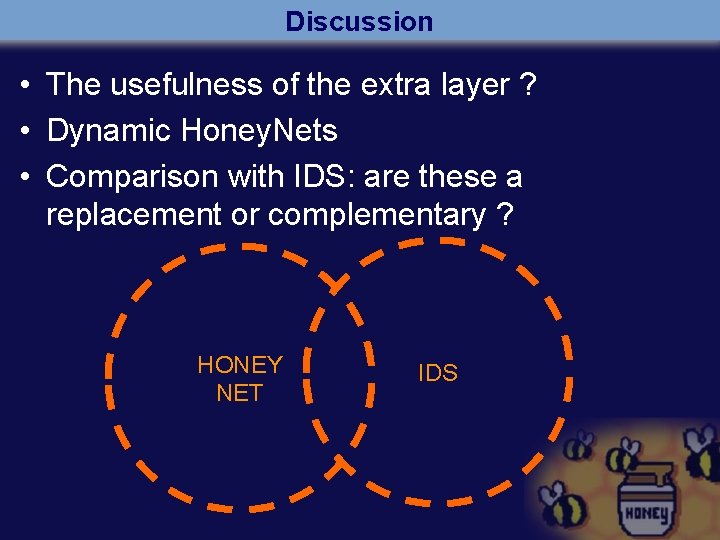
Discussion • The usefulness of the extra layer ? • Dynamic Honey. Nets • Comparison with IDS: are these a replacement or complementary ? HONEY NET IDS