Honeypots and Honeynets Source The Honey Net Project













- Slides: 26

Honeypots and Honeynets Source: The Honey. Net Project http: //www. honeynet. org/ Mehedy Masud September 16, 2009 mehedy@utdallas. edu

Why Honey. Pots A great deal of the security profession and the IT world depend on honeypots. Honeypots ◦ ◦ ◦ Build anti-virus signatures. Build SPAM signatures and filters. ISP’s identify compromised systems. Assist law-enforcement to track criminals. Hunt and shutdown botnets. Malware collection and analysis.

What are Honeypots are real or emulated vulnerable systems ready to be attacked. Primary value of honeypots is to collect information. This information is used to better identify, understand protect against threats. Honeypots add little direct value to protecting your network.

Types of Honey. Pot Server: Put the honeypot on the Internet and let the bad guys come to you. Client: Honeypot initiates and interacts with servers Other: Proxies

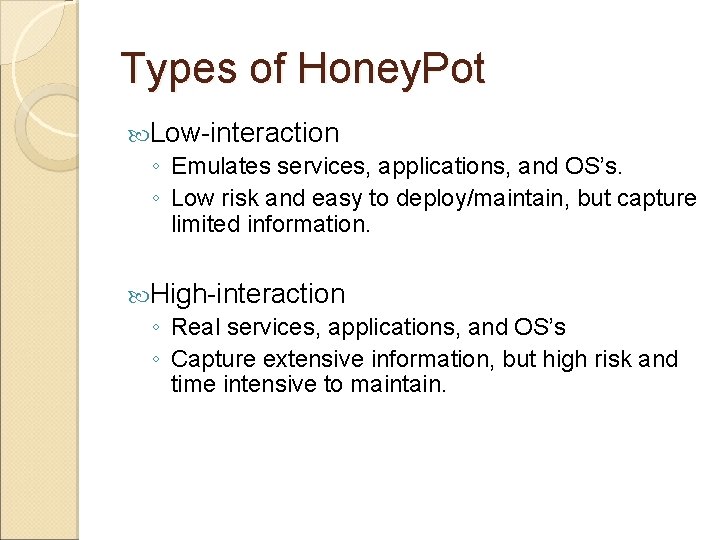
Types of Honey. Pot Low-interaction ◦ Emulates services, applications, and OS’s. ◦ Low risk and easy to deploy/maintain, but capture limited information. High-interaction ◦ Real services, applications, and OS’s ◦ Capture extensive information, but high risk and time intensive to maintain.

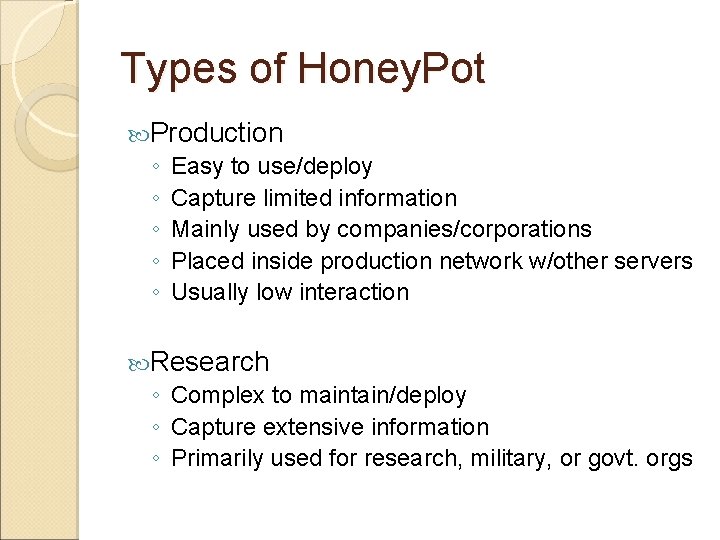
Types of Honey. Pot Production ◦ Easy to use/deploy ◦ Capture limited information ◦ Mainly used by companies/corporations ◦ Placed inside production network w/other servers ◦ Usually low interaction Research ◦ Complex to maintain/deploy ◦ Capture extensive information ◦ Primarily used for research, military, or govt. orgs

Examples Of Honeypots Low Interaction Back. Officer Friendly KFSensor Honeyd Honeynets High Interaction

Honeynets High-interaction honeypot designed to capture in-depth information. Information has different value to different organizations. Its an architecture you populate with live systems, not a product or software. Any traffic entering or leaving is suspect.

How It Works A highly controlled network where every packet entering or leaving is monitored, captured, and analyzed. ◦ Data Control ◦ Data Capture ◦ Data Analysis

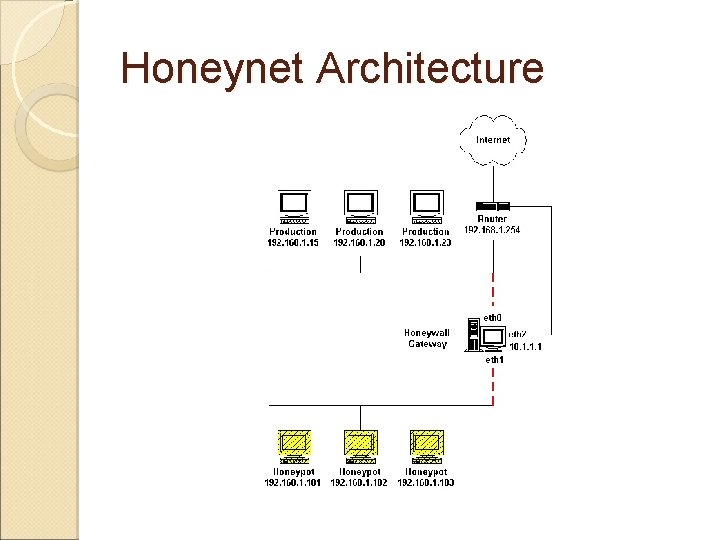
Honeynet Architecture

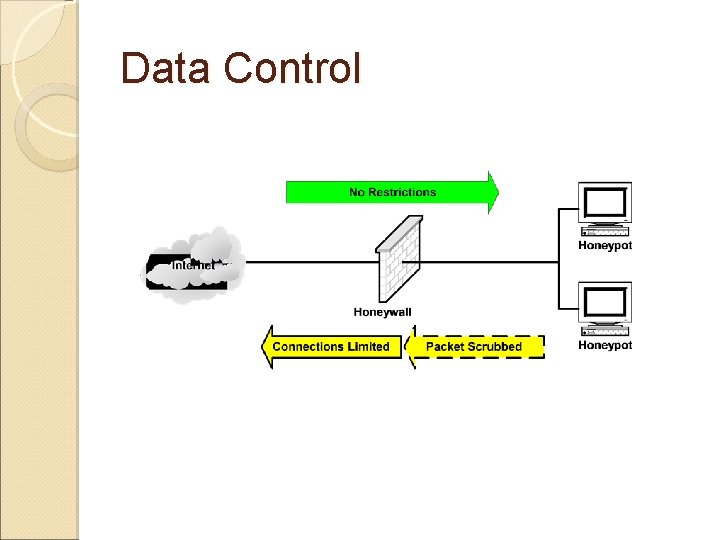
Data Control Mitigate risk of honeynet being used to harm non-honeynet systems. • Count outbound connections. • IPS (Snort-Inline) • Bandwidth Throttling •

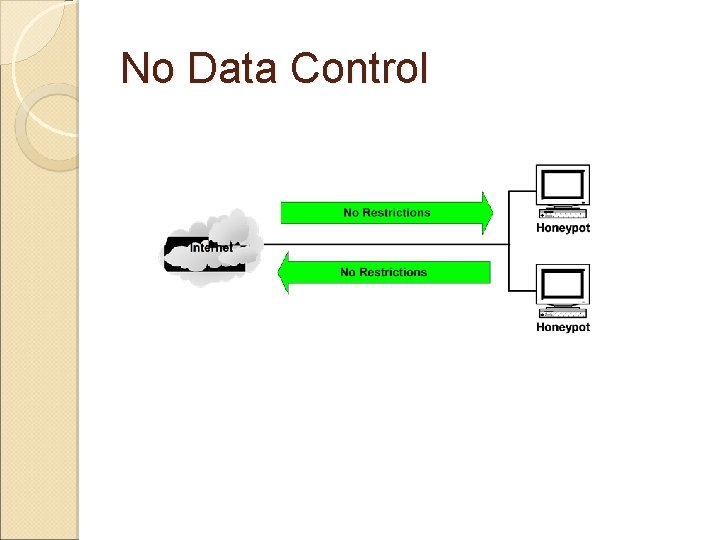
No Data Control

Data Control

Data Capture all activity at a variety of levels. Network activity. Application activity. System activity.

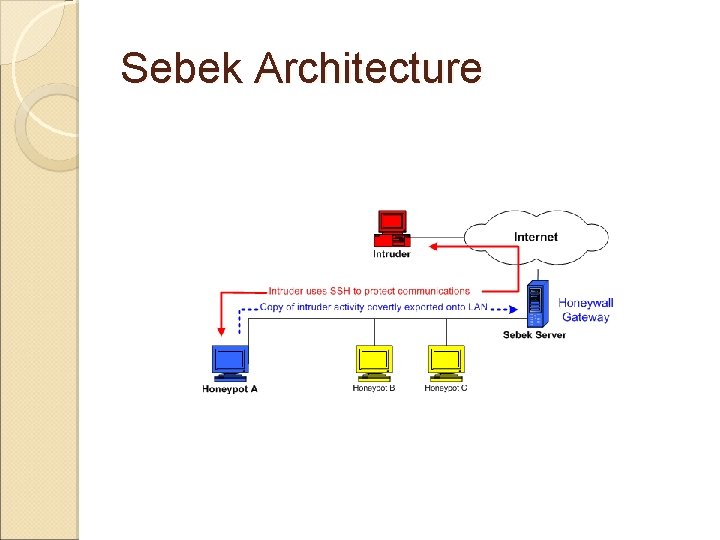
Sebek Hidden kernel module that captures all host activity Dumps activity to the network. Attacker cannot sniff any traffic based on magic number and dst port.

Sebek Architecture

Honeywall CDROM Attempt to combine all requirements of a Honeywall onto a single, bootable CDROM. May, 2003 - Released Eeyore May, 2005 - Released Roo

Roo Honeywall CDROM Based on Fedora Core 3 Vastly improved hardware and international support. Automated, headless installation New Walleye interface for web based administration and data analysis. Automated system updating.

Installation Just insert CDROM and boot, it installs to local hard drive. After it reboots for the first time, it runs a hardening script based on NIST and CIS security standards. Following installation, you get a command prompt and system is ready to configure.

Further Information http: //www. honeynet. org/book

Network Telescope Also known as a darknet, internet motion sensor or black hole Allows one to observe different large-scale events taking place on the Internet. The basic idea is to observe traffic targeting the dark (unused) address-space of the network. Since all traffic to these addresses is suspicious, one can gain information about possible network attacks ◦ random scanning worms, and DDo. S backscatter As well as other misconfigurations by

Honeytoken honeytokens are honeypots that are not computer systems. Their value lies not in their use, but in their abuse. As such, they are a generalization of such ideas as the honeypot and the canary values often used in stack protection schemes. Honeytokens can exist in almost any form, ◦ from a dead, fake account to a ◦ database entry that would only be selected by malicious queries, ◦ making the concept ideally suited to ensuring data integrity— any use of them is inherently suspicious if not necessarily

Honeytoken In general, they don't necessarily prevent any tampering with the data, ◦ but instead give the administrator a further measure of confidence in the data integrity. An example of a honeytoken is a fake email address used to track if a mailing list has been stolen

Honeymonkey Honey. Monkey, ◦ short for Strider Honey. Monkey Exploit Detection System, is a Microsoft Research honeypot. The implementation uses a network of computers ◦ to crawl the World Wide Web searching for websites that use browser exploits to install malware on the Honey. Monkey computer. ◦ A snapshot of the memory, executables and registry of the honeypot computer is recorded before crawling a site. ◦ After visiting the site, the state of memory, executables, and registry is compared to the previous snapshot. ◦ The changes are analyzed to determine whether the visited site installed malware onto the honeypot computer.

Honeymonkey Honey. Monkey is based on the honeypot concept, with the difference that it actively seeks websites that try to exploit it. The term was coined by Microsoft Research in 2005. With honeymonkeys it is possible to find open security holes that aren't yet publicly known but are exploited by attackers.

Tarpit A tarpit (also known as Teergrube, the German word for tarpit) is a service on a computer system (usually a server) that delays incoming connections for as long as possible. The technique was developed as a defense against a computer worm, and the idea is that network abuses such as spamming or broad scanning are less effective if they take too long. The name is analogous with a tar pit, in which animals can get bogged down and slowly sink under the surface.
 Honeypots and honeynets
Honeypots and honeynets Honey and mumford
Honey and mumford Symbiotic relationship between honeyguide bird and badger
Symbiotic relationship between honeyguide bird and badger Bread and honey meaning
Bread and honey meaning Bread and honey meaning
Bread and honey meaning Cockney money
Cockney money Bread and honey meaning
Bread and honey meaning Earths honey
Earths honey Los javaloyas honey
Los javaloyas honey Honeybee lifespan
Honeybee lifespan Adjectives to describe miss honey
Adjectives to describe miss honey Honeybadger latency
Honeybadger latency Honeypot
Honeypot Sickle dance of honey bee
Sickle dance of honey bee Honey bee wax glands
Honey bee wax glands Honey bee tools
Honey bee tools How many eyes do bees have
How many eyes do bees have Bee anatomy diagram
Bee anatomy diagram Roann mendriq wikipedia
Roann mendriq wikipedia Gaya pembelajaran honey dan mumford
Gaya pembelajaran honey dan mumford Honey alonso
Honey alonso Mhn honeypot
Mhn honeypot Homogeneous mixtures examples
Homogeneous mixtures examples Casa de la señorita miel
Casa de la señorita miel Decrypt
Decrypt Latin america and spain map
Latin america and spain map Phil mulder
Phil mulder