SIA 400 The Cryptography Chronicles Explaining the Unexplained


























































- Slides: 76

SIA 400 The Cryptography Chronicles Explaining the Unexplained: Part One Andy Malone CEO & Founder The Cybercrime Security Forum Andrew. malone@quality-training. co. uk

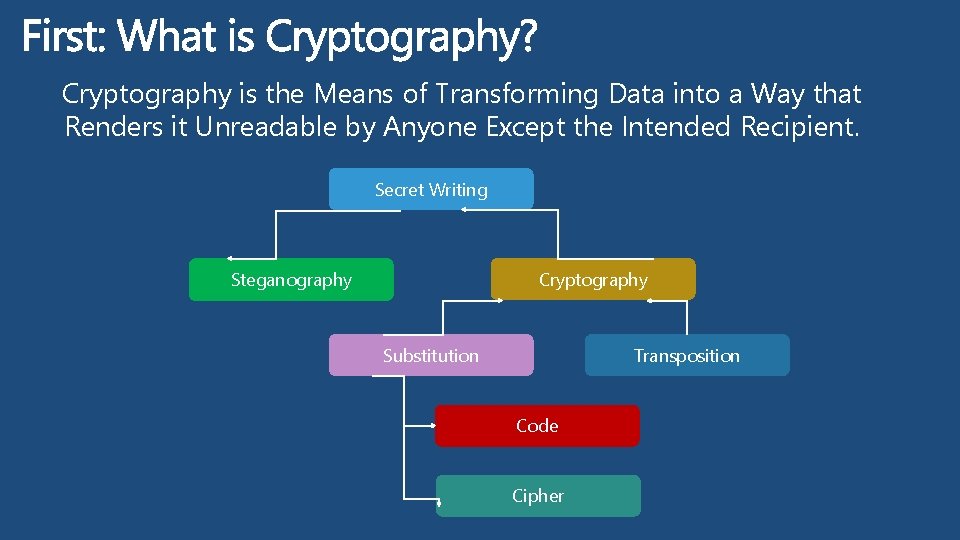
Note: Although this is a level 400 session. It is designed to be a training session providing history, development and practical uses of Cryptography and as such if you already consider yourself an expert in cryptography then this session will be 300 Level.



Cryptography Let’s Start at the Beginning!

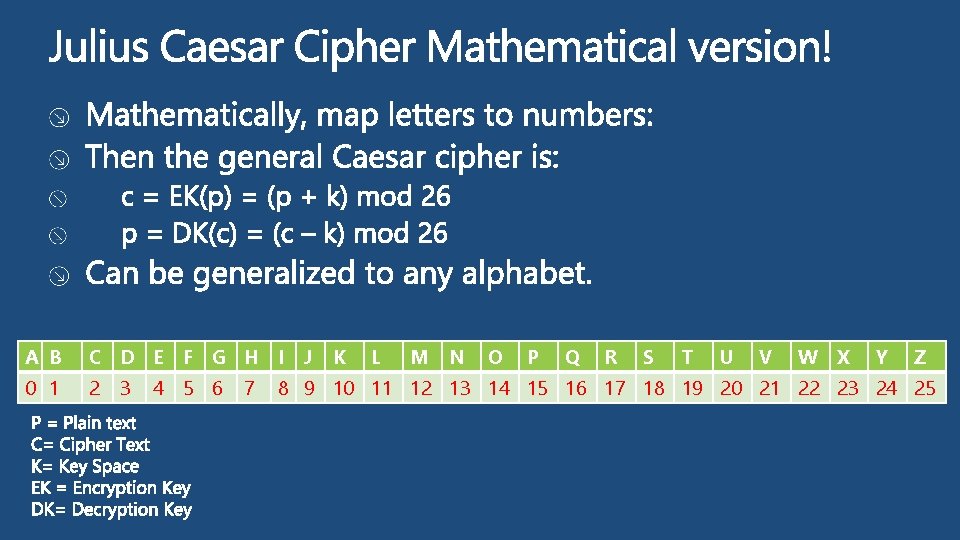
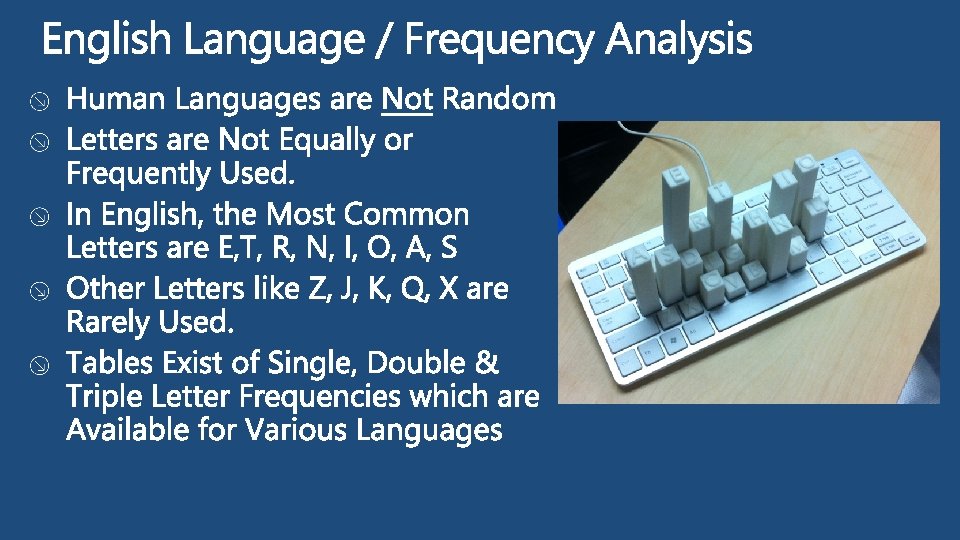
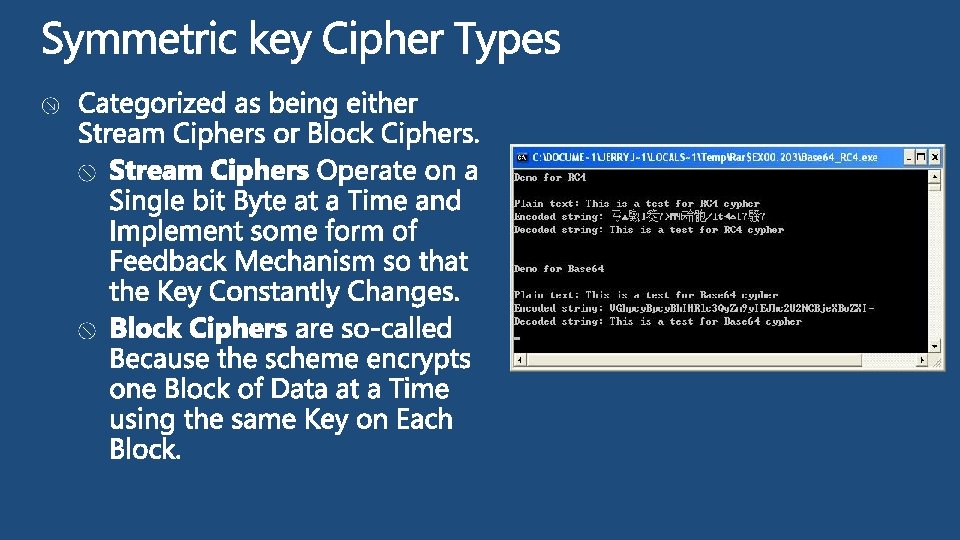
Cryptography is the Means of Transforming Data into a Way that Renders it Unreadable by Anyone Except the Intended Recipient. Secret Writing Cryptography Steganography Substitution Transposition Code Cipher


Military Use Defence Against External/Internal Hackers Defence against Industrial Espionage Securing E-commerce Securing Bank Accounts/Electronic Payment Technologies Securing Intellectual Property Avoiding Liability


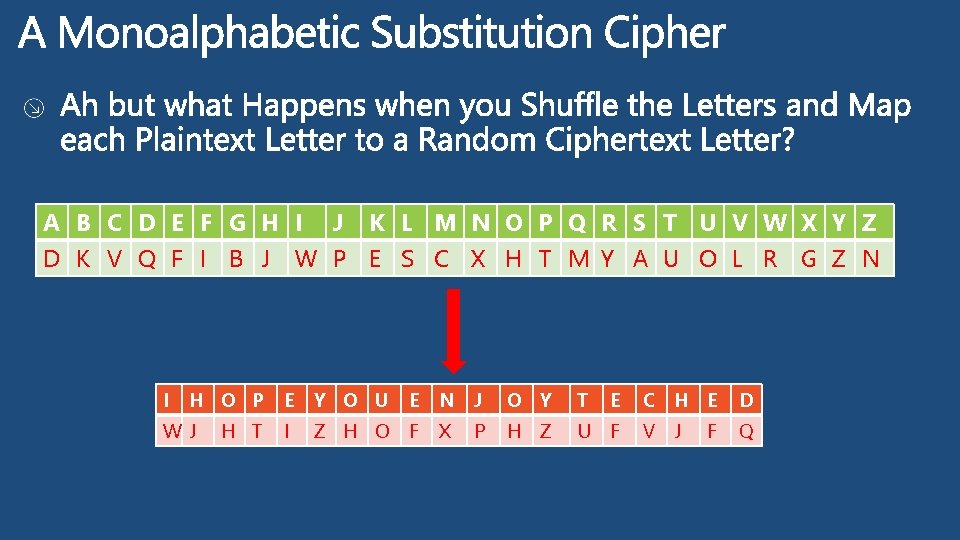
Cryptography How it all Began…




A B C D E F G H I J K L MN O P Q R S T U V WX Y Z D E F G HI J K L MN O P Q R S T U V WX Y Z A B C MICROSOFT TECHED PLFURVRIW WHFKHG

A B C D E F G H I J 0 1 2 3 4 5 6 7 K L M N O P Q R S T U V W X Y Z 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25


A B C D E F G H I J K L M N O P Q R S T U V W X Y Z D K V Q F I B J W P E S C X H T M Y A U O L R G Z N I H O P E Y O U E N J O Y T WJ I H Z U F H T Z H O F X P E C H E D V J Q F




Z Z Z Z ZW Z Z Z

Z ZW Z Z Z

Z ZW Z Z Z

Z ZW Z Z Z

Z ZW Z Z Z

Z ZW Z Z Z


P 13. 33 Z 11. 67 S 8. 33 U 8. 33 O 7. 50 M 6. 67 H D E V X 5. 83 5. 00 4. 17 F W Q T A 3. 33 2. 50 1. 67 B G Y I J 1. 67 0. 83 C K L N R 0. 00

Z ZW Z Z Z


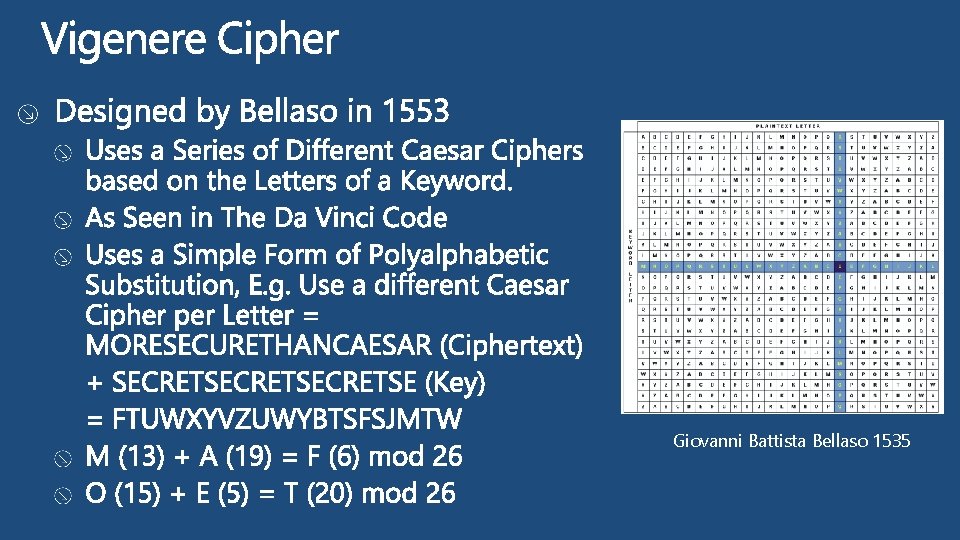
Giovanni Battista Bellaso 1535

Cryptography The Modern Age Begins…

1871 1942 1837 1975 – Present Day 1903 1946 – Present Day


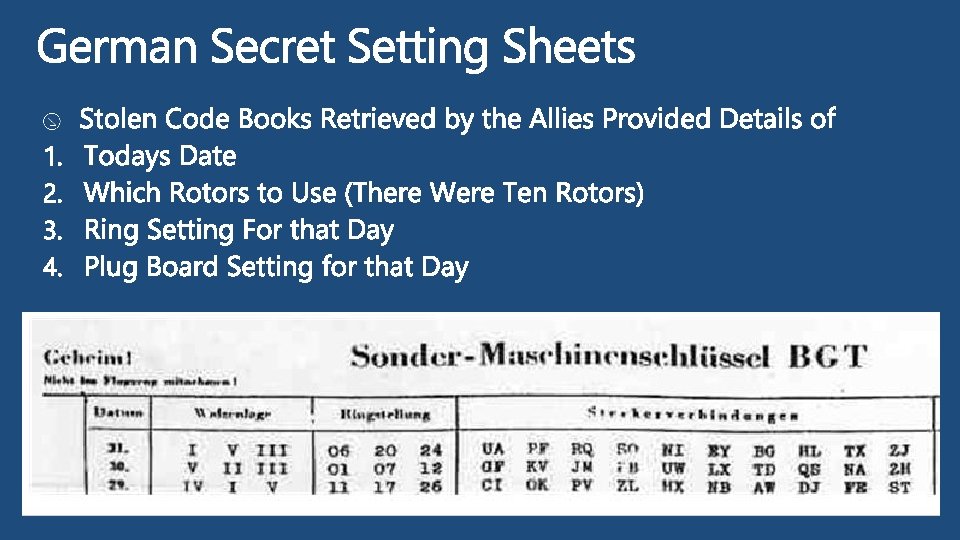
Try The Enigma Simulator For Yourself: http: //users. telenet. be/d. rijmenants/en/enigmasim. htm


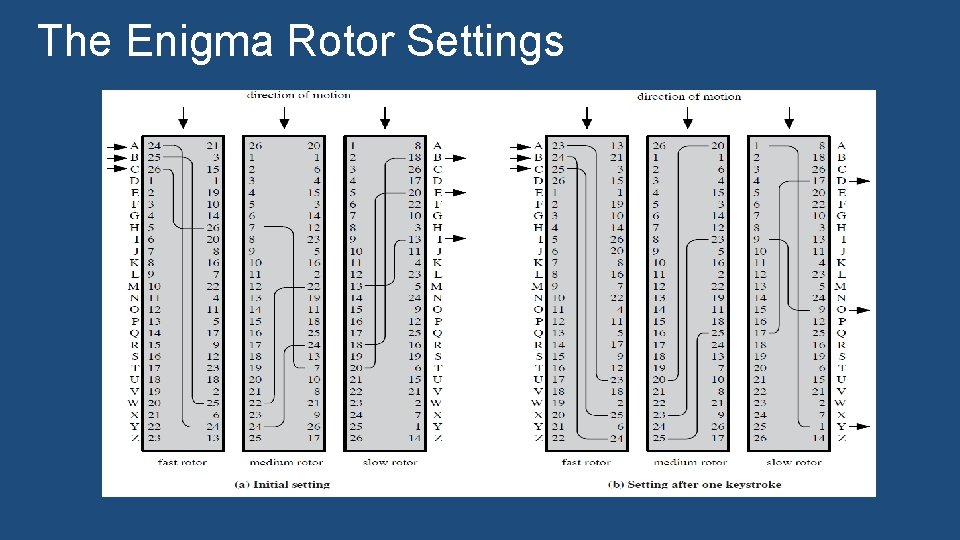
The Enigma Rotor Settings


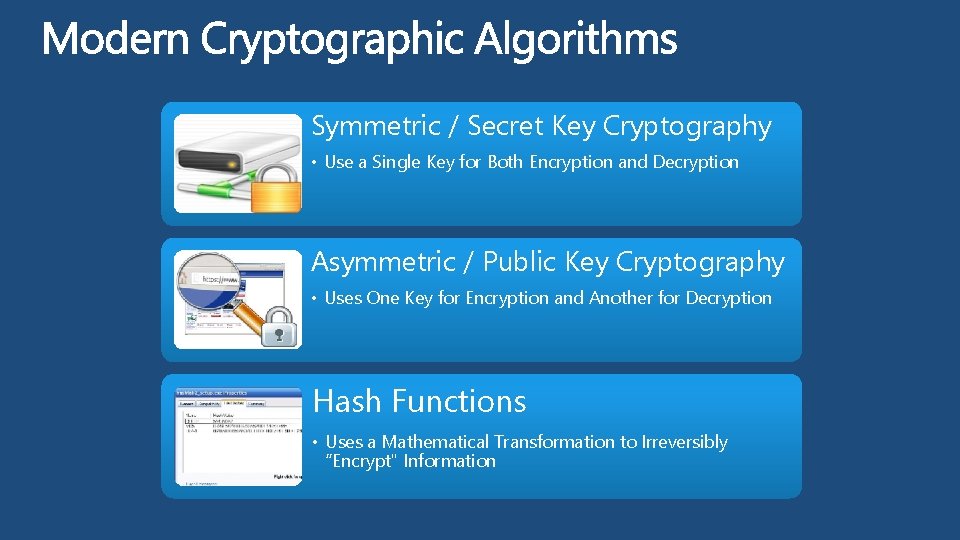
Symmetric / Secret Key Cryptography • Use a Single Key for Both Encryption and Decryption Asymmetric / Public Key Cryptography • Uses One Key for Encryption and Another for Decryption Hash Functions • Uses a Mathematical Transformation to Irreversibly “Encrypt" Information

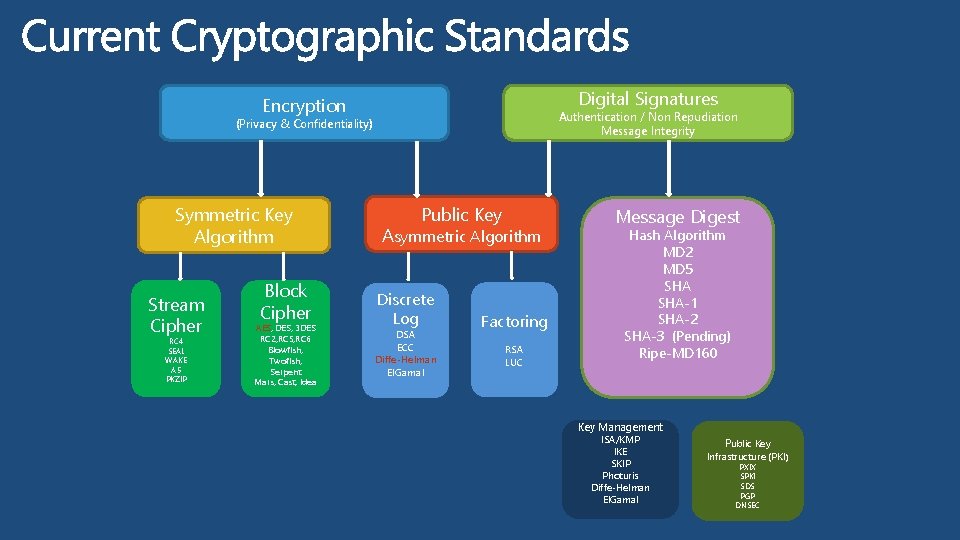
Digital Signatures Encryption Authentication / Non Repudiation Message Integrity (Privacy & Confidentiality) Symmetric Key Algorithm Stream Cipher RC 4 SEAL WAKE A 5 PKZIP Block Cipher AES, DES, 3 DES RC 2, RC 5, RC 6 Blowfish, Twofish, Serpent Mars, Cast, Idea Public Key Asymmetric Algorithm Discrete Log DSA ECC Diffe-Helman El. Gamal Factoring RSA LUC Message Digest Hash Algorithm MD 2 MD 5 SHA-1 SHA-2 SHA-3 (Pending) Ripe-MD 160 Key Management ISA/KMP IKE SKIP Photuris Diffe-Helman El. Gamal Public Key Infrastructure (PKI) PXIX SPKI SDS PGP DNSEC




Winners of the NIST 2001 AES Design Competition Joan Daemen and Vincent Rijmen



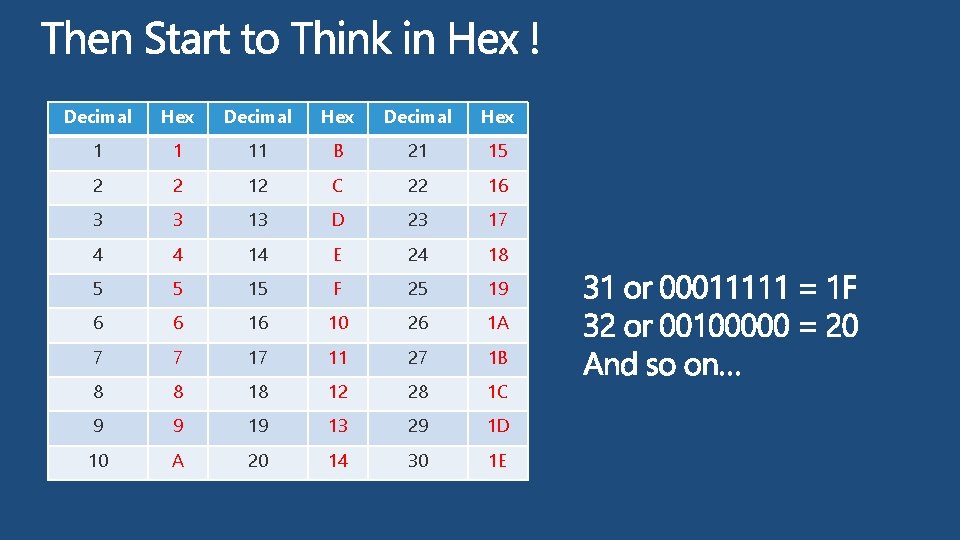
Decimal Hex 1 1 11 B 21 15 2 2 12 C 22 16 3 3 13 D 23 17 4 4 14 E 24 18 5 5 15 F 25 19 6 6 16 10 26 1 A 7 7 17 11 27 1 B 8 8 18 12 28 1 C 9 9 19 13 29 1 D 10 A 20 14 30 1 E


Animation Symmetric Encryption: AES The AES Inspector Click Me

Animation Symmetric Encryption: AES With Special Thanks to Enrique Zabala Click Me

Encryption/Decryption Digital Signatures Key Exchange Secure Communications




Considered to be The Fathers of Public Key Cryptography Whitfield Diffie and Martin Hellman

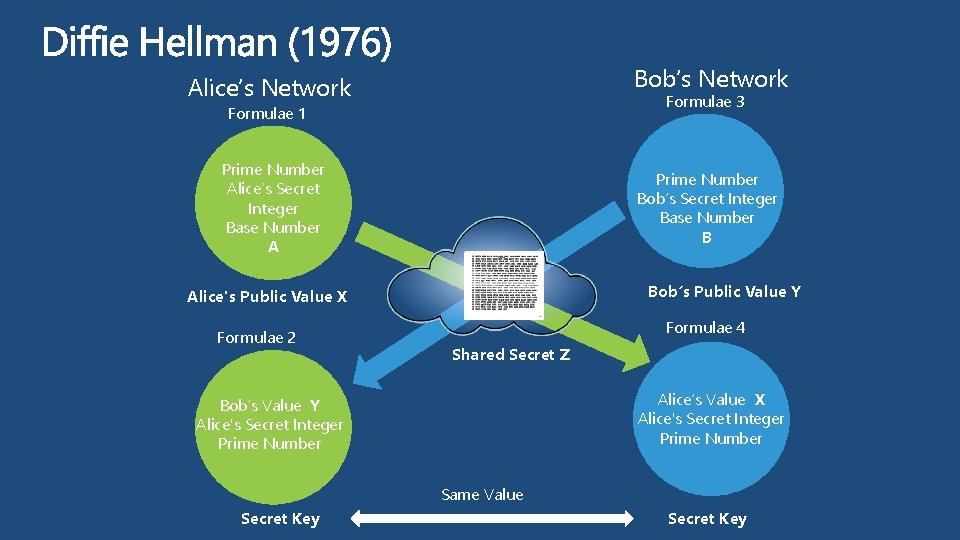
Bob’s Network Alice’s Network Formulae 3 Formulae 1 Prime Number Alice’s Secret Integer Base Number A Prime Number Bob’s Secret Integer Base Number B Bob’s Public Value Y Alice's Public Value X Formulae 2 Formulae 4 Shared Secret Z Alice’s Value X Alice's Secret Integer Prime Number Bob’s Value Y Alice's Secret Integer Prime Number Same Value Secret Key

F(x)+ Y X X


Once selected Alice Raises RA No Matter how large the number is A Will Eventually Map into a Range Between 0 & N -1 = X Tools Exist to Calculate X From A to Raise RA(A) and find X is easy. Very.

RB

RAx. B RA B B B A A


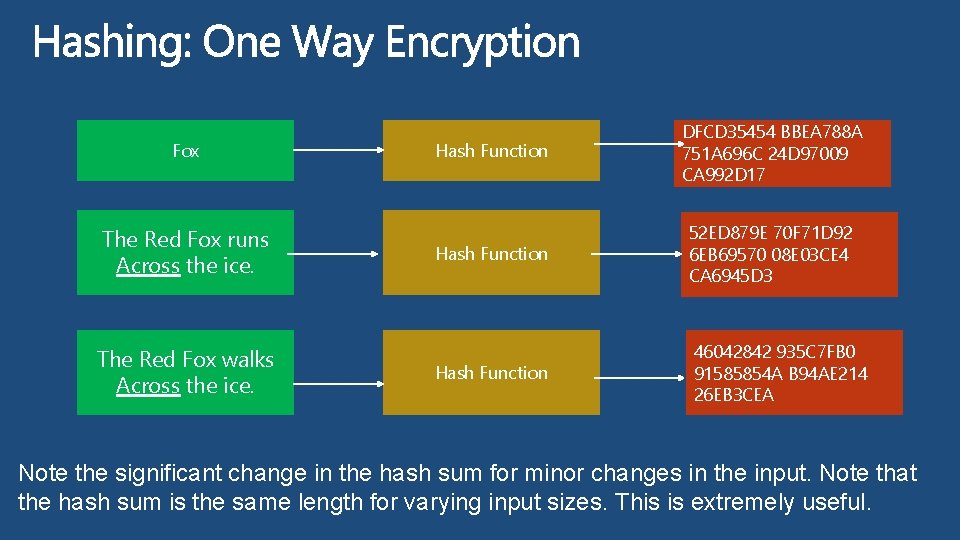
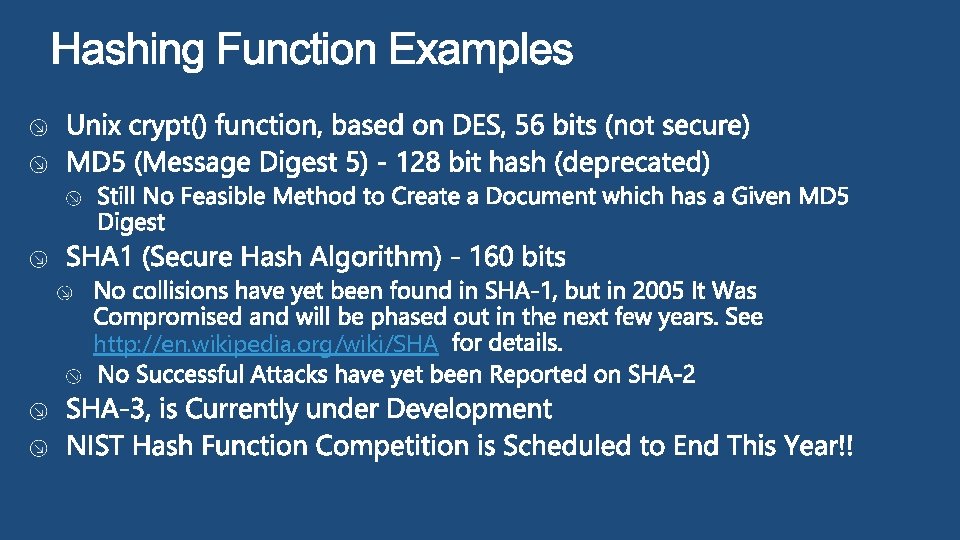
Fox The Red Fox runs Across the ice. The Red Fox walks Across the ice. Hash Function DFCD 35454 BBEA 788 A 751 A 696 C 24 D 97009 CA 992 D 17 Hash Function 52 ED 879 E 70 F 71 D 92 6 EB 69570 08 E 03 CE 4 CA 6945 D 3 Hash Function 46042842 935 C 7 FB 0 91585854 A B 94 AE 214 26 EB 3 CEA Note the significant change in the hash sum for minor changes in the input. Note that the hash sum is the same length for varying input sizes. This is extremely useful.

http: //en. wikipedia. org/wiki/SHA

Animation Useful Crypto Tools Free & Available


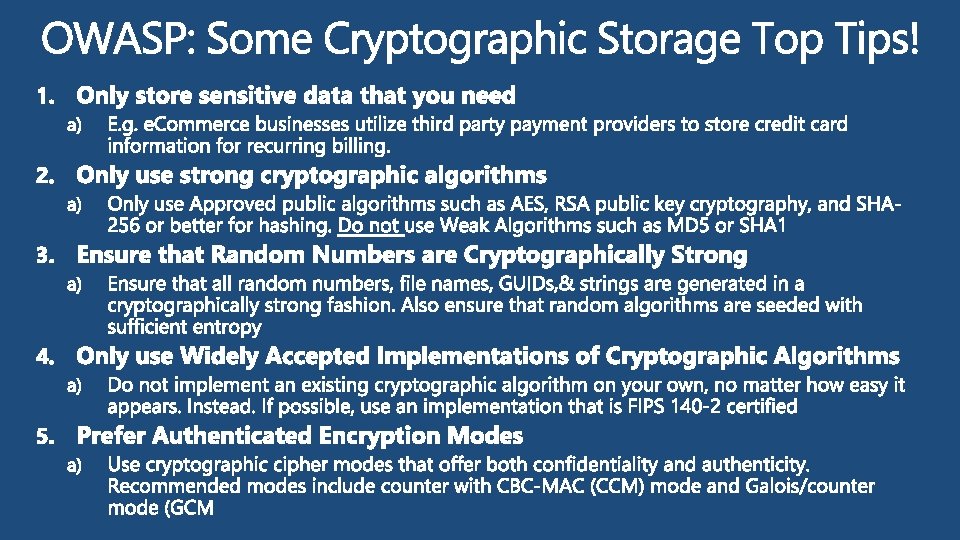
Open Web Application Security Project



SIA 400: The Cryptography Chronicles: Explaining the Unexplained Part 1 SIA 401: The Cryptography Chronicles: Explaining the Unexplained Part 2 SIA 301 Lock, Stock & Two Smoking Smart Devices! SIA 203 Cyber Threats Security Panel Find Me Later At…Ask The Experts

www. microsoft. com/twc www. microsoft. com/security www. microsoft. com/privacy www. microsoft. com/reliability

Complete an evaluation on Comm. Net and enter to win!

Scan the Tag to evaluate this session now on my. Tech. Ed Mobile

Thanks For Attending : -) Andy Malone CEO & Founder The Cybercrime Security Forum Follow me @Andy. Malone Andrew. malone@quality-training. co. uk

