Shodan Computer Search Engine Matt Jennings Road Map











- Slides: 25

Shodan Computer Search Engine Matt Jennings

Road Map • • • What is Shodan? How does Shodan work? HTTP banners Example searches Who uses Shodan? Conclusion

What is Shodan? • Shodan is a computer search engine • Developed by John Matherly and launched in 2009 • Originally developed for marketing research purposes • Shodan is somewhat similar to Google, Bing, Yahoo etc.

What is Shodan? • Media Attention • People were able to access – Powerplants, hockey rinks, red-light cameras, webcams, particle accelerators • Brought to light the lack of security

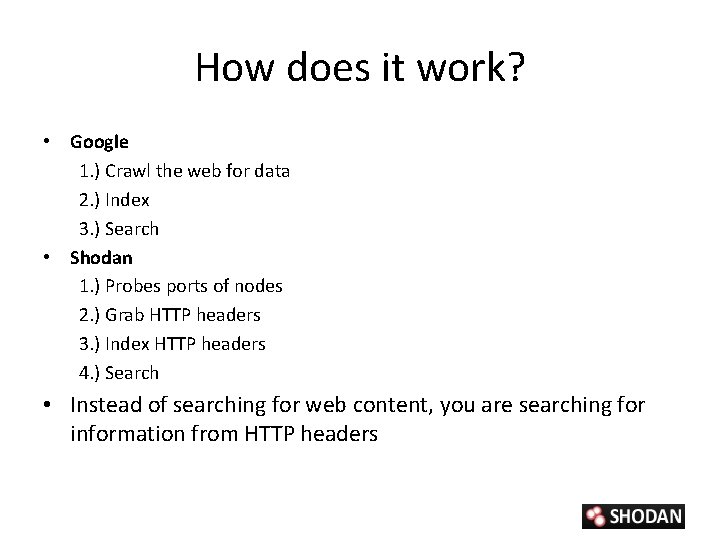
How does it work? • Google 1. ) Crawl the web for data 2. ) Index 3. ) Search • Shodan 1. ) Probes ports of nodes 2. ) Grab HTTP headers 3. ) Index HTTP headers 4. ) Search • Instead of searching for web content, you are searching for information from HTTP headers

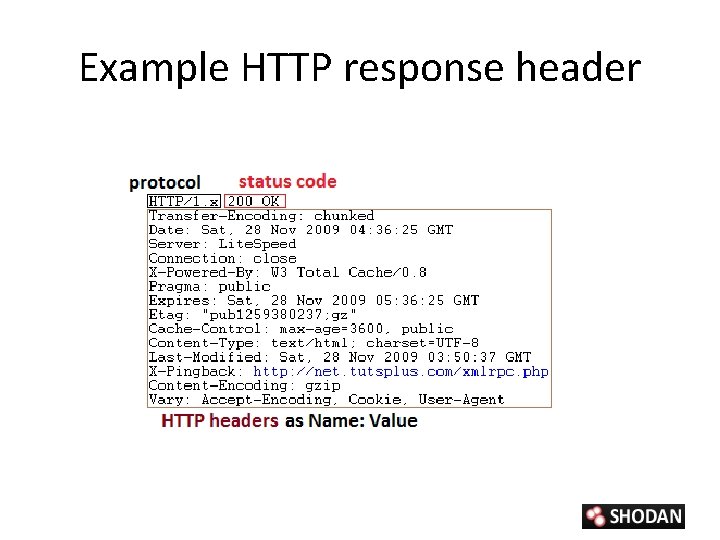
Service Headers • Information can be gathered from: – HTTP(port 80), FTP(21), SSH(22) and other service headers • Headers contain information such as date, server, last updated, connection, content type, welcome message, etc.

Example HTTP response header

Shodan • Does not require account creation to search • Without account: – Only 10 results per query – Can’t filter by ‘country’ or ‘net’ • With account: – 50 results per query – Increased filters – Export XML data

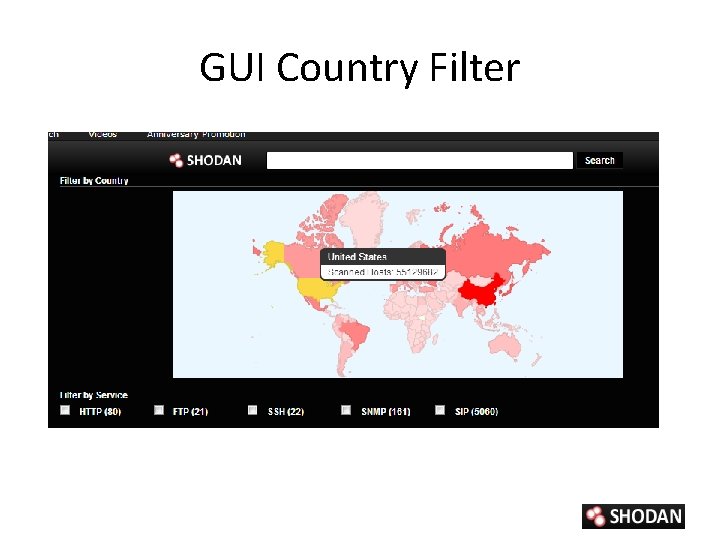
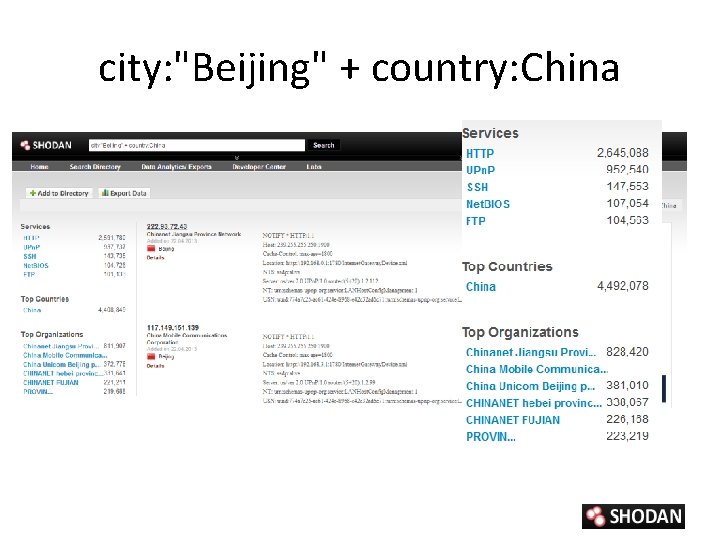
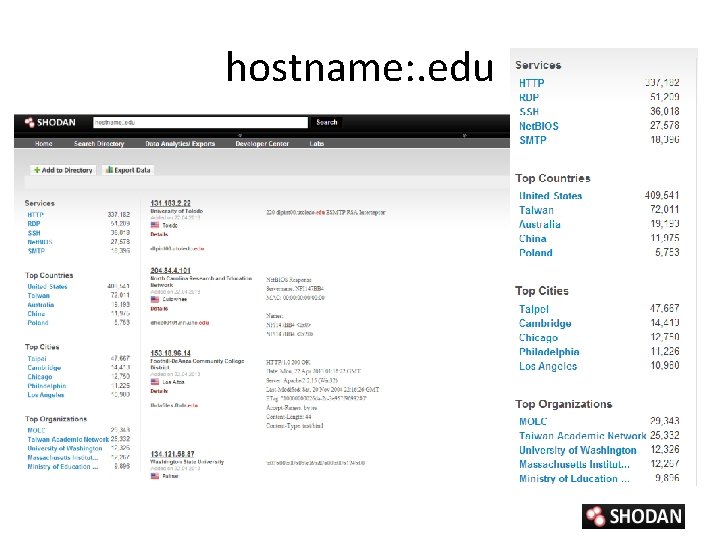
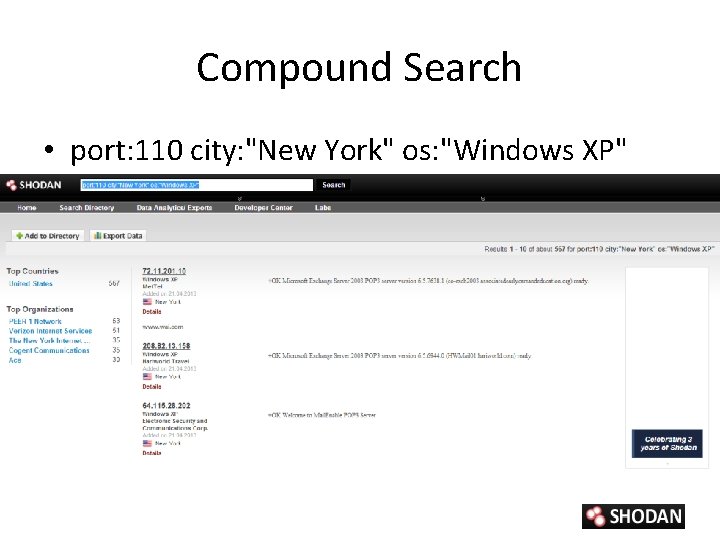
Shodan Filters • Syntax : ‘filter: value’ with boolean operators (+, -, |) – city and country • city: ”Pittsburgh” + country: US – geo • Geo: 32. 8, -117, 50 – hostname • hostname: . ca – net • net. 192. 168. 1. 1/24 – port • port: 21(ftp) – os • os: ”windows 2000” • SSL filters

GUI Country Filter

city: "Beijing" + country: China

hostname: . edu

Compound Search • port: 110 city: "New York" os: "Windows XP"

General Search • “tomcat 6. 0”

Network Radar

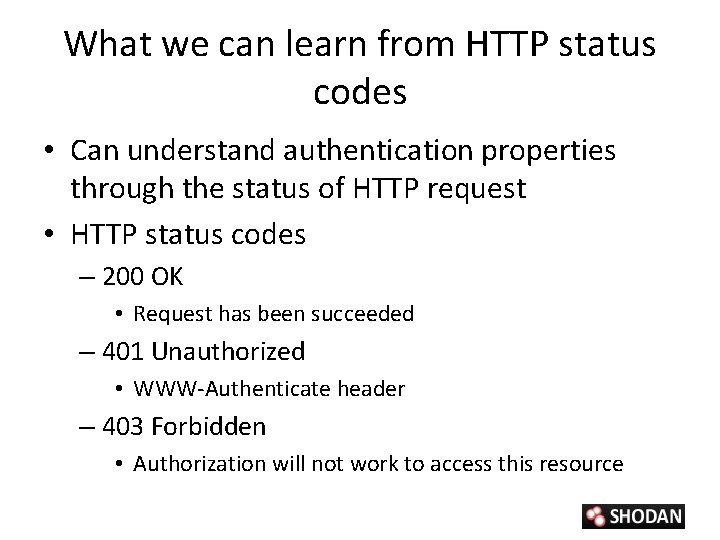
What we can learn from HTTP status codes • Can understand authentication properties through the status of HTTP request • HTTP status codes – 200 OK • Request has been succeeded – 401 Unauthorized • WWW-Authenticate header – 403 Forbidden • Authorization will not work to access this resource

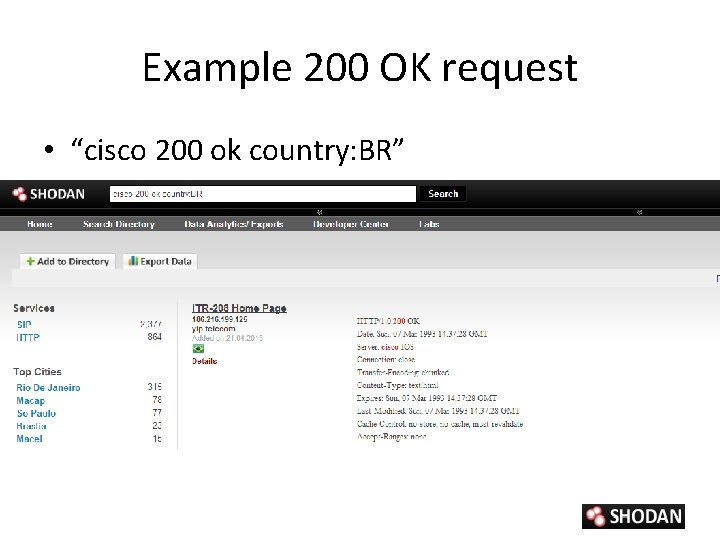
Example 200 OK request • “cisco 200 ok country: BR”

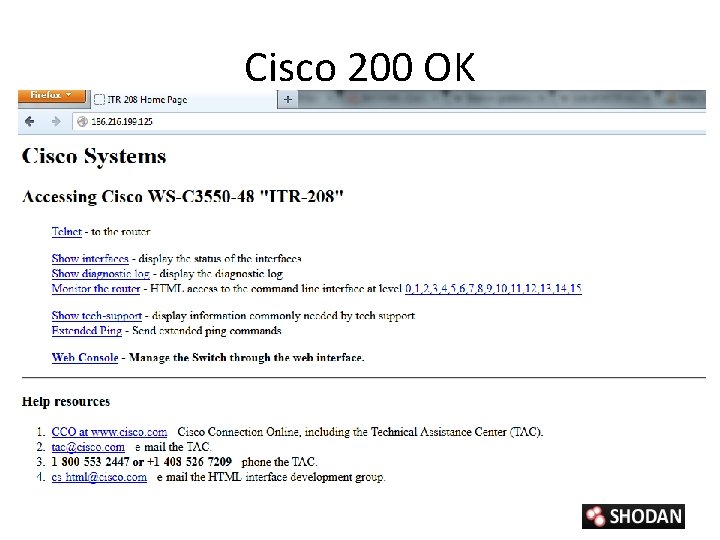
Cisco 200 OK

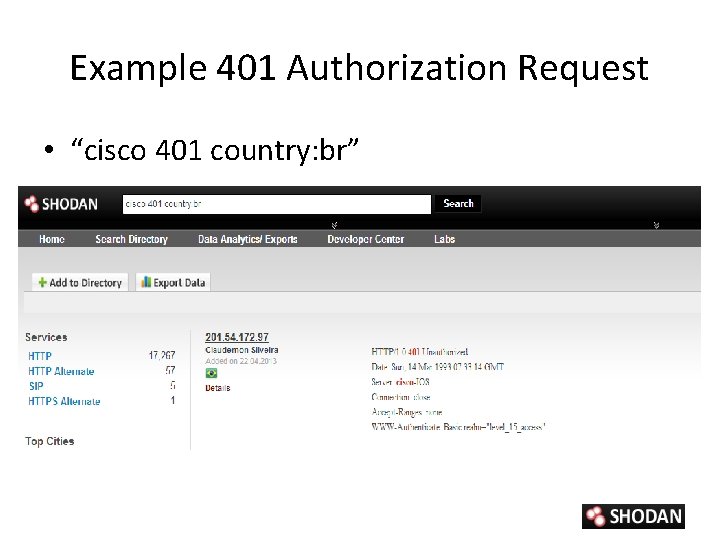
Example 401 Authorization Request • “cisco 401 country: br”

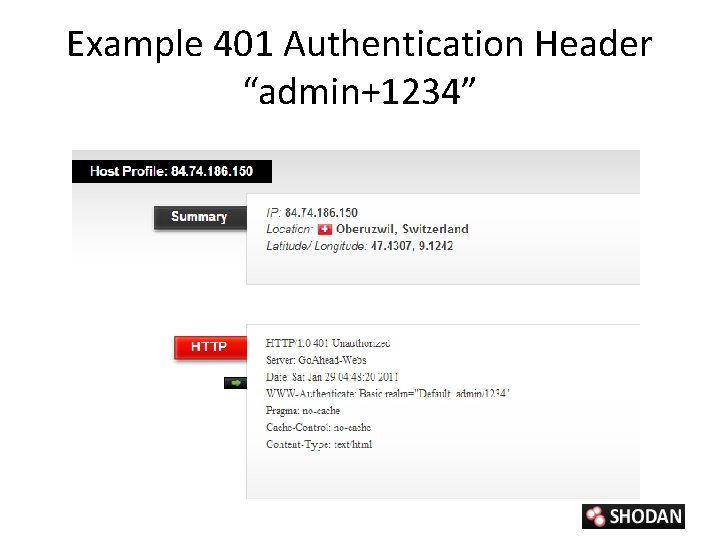
Example 401 Authentication Header “admin+1234”

ICS-Cert Recommendations • Place all important systems behind a firewall and separated from other networks • Use VPN • Rename and change password of any default accounts • Use lockout policies to prevent brute force attempts • Strong password policies

Who uses Shodan • Cybersecurity professionals – Penetration testers • Researchers • Law enforcement • Cybercriminals

Conclusion • Seems scary – Not anonymous • Huge resource of information • Increased security of devices

References • http: //www. shodanhq. com/ • http: //money. cnn. com/2013/04/08/technology/security /shodan/index. html • http: //articles. washingtonpost. com/2012 -0603/news/35459595_1_computer-systems-desktopcomputers-search-engine • http: //en. wikipedia. org/wiki/Shodan_(website) • http: //www. theregister. co. uk/2013/03/20/scada_honey pot_research/ • http: //ics-cert. us-cert. gov/pdf/ICS-Alert-10 -301 -01. pdf • http: //www. zdnet. com/blog/security/shodan-searchexposes-insecure-scada-systems/7611

Questions