Security Virtualization and Value Added Services IDC IT











- Slides: 30

Security Virtualization and Value Added Services IDC IT Security Roadshow, June 03, 2008 Securing Your Business: Technology Meets People David Maman, Fortinet (dmaman@fortinet. com)

What is Virtualization? The act of abstracting the (physical and logical) boundaries of a technology.

Many ways to Virtualization § § § Servers Desktops Applications Networks Storage Fortinet Confidential

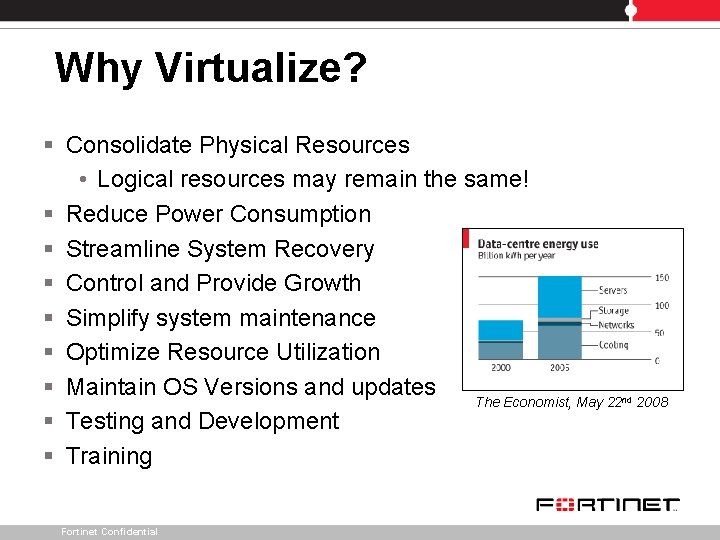
Why Virtualize? § Consolidate Physical Resources • Logical resources may remain the same! § Reduce Power Consumption § Streamline System Recovery § Control and Provide Growth § Simplify system maintenance § Optimize Resource Utilization § Maintain OS Versions and updates The Economist, May 22 § Testing and Development § Training Fortinet Confidential nd 2008

Consolidated security MSSP - Managed Security Service Provider Virtual Presence – The saga Web X. 0 / HTT-What? / SAAS Fortinet

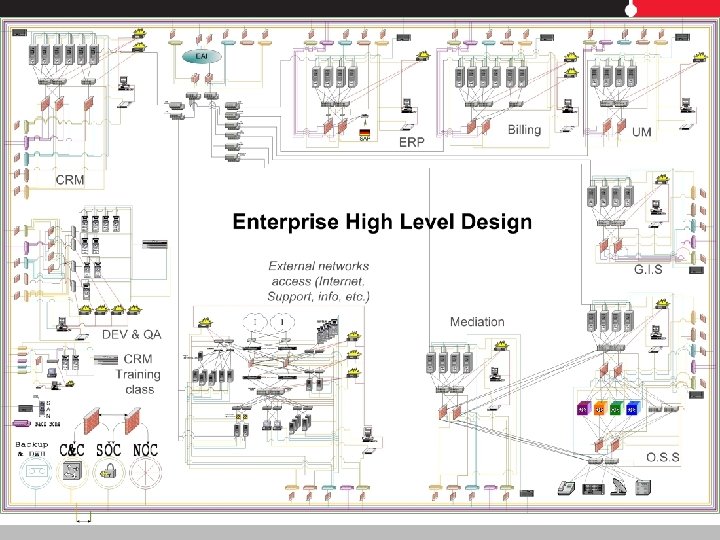
Centralized (Virtualized) Security (Consolidated security)


Information Security Over head. Ø High availability solutions Ø Separated management Interfaces Ø Troubleshooting madness Ø Training period Ø Updates and upgrades Ø Support ? ! Who and for what? Ø Logging a reporting Ø Hardware coasts Fortinet Confidential

Virtualized Security must feel with, Without. Ø Performance Ø Management Ø Flexibility Ø Content Security Ø Reliability / Density Ø Logging / Reporting Fortinet Confidential Of course it’s not running in a Virtual…. .

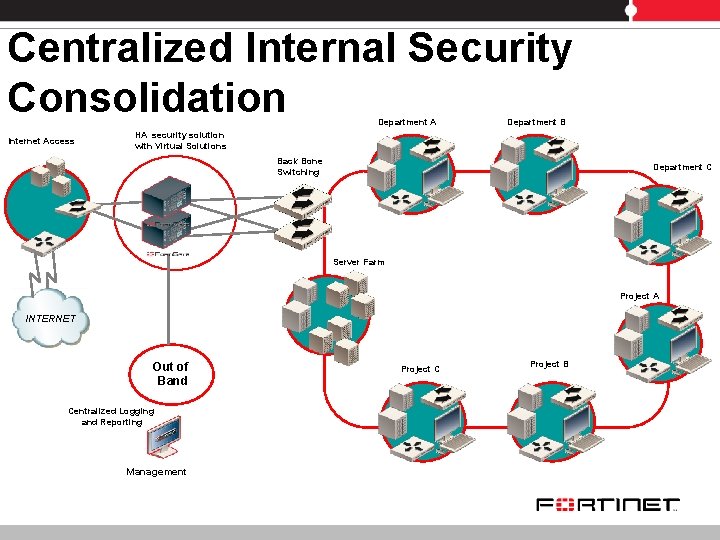
Centralized Internal Security Consolidation Department A Internet Access Department B HA security solution with Virtual Solutions Back Bone Switching Department C Server Farm Project A INTERNET Out of Band Centralized Logging and Reporting Management Project C Project B

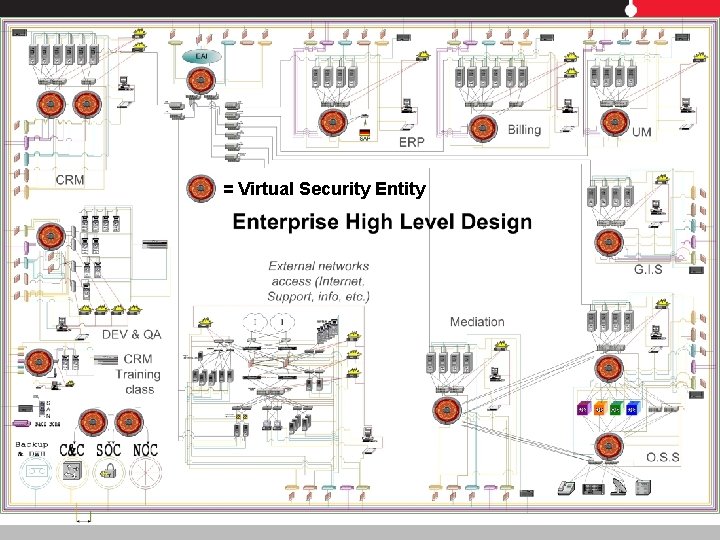
= Virtual Security Entity

Consolidated security MSSP - Managed Security Service Provider Virtual Presence – The saga Web X. 0 / HTT-What? / SAAS Fortinet

MSSP Solution Managed Security Service Managed Security Solutions Provider

Managed Security Services • Customer Premises § § Provider independent Affordable quality of security Low cost of entry & operations Enforcing Internal information security • Centralized ‘In the cloud’ § § § Provider dependent High availability & Controlled environment Simple logistics “Clean Pipe” to the customer Centralized upgrade Fortinet Confidential

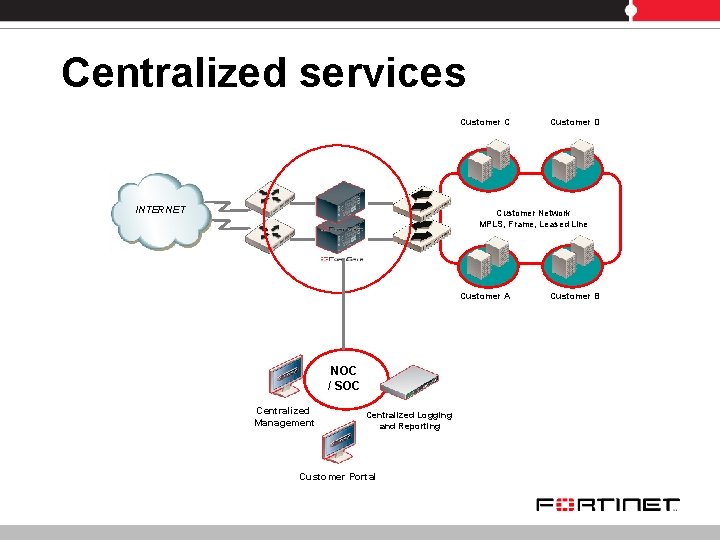
Centralized services Customer C INTERNET Customer D Customer Network MPLS, Frame, Leased Line Customer A NOC / SOC Centralized Management Centralized Logging and Reporting Customer Portal Customer B

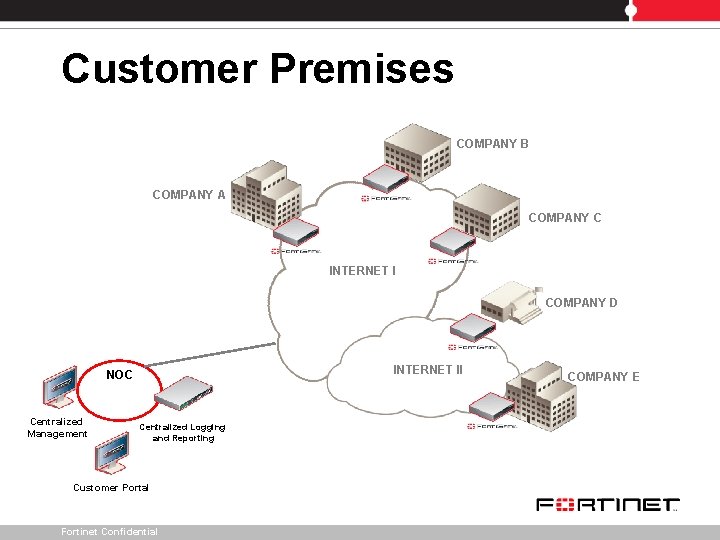
Customer Premises COMPANY B COMPANY A COMPANY C INTERNET I COMPANY D INTERNET II NOC Centralized Management Centralized Logging and Reporting Customer Portal Fortinet Confidential COMPANY E

Managed Security Services • Customer Premises § § Provider independent Affordable quality of security Low cost of entry & operations Enforcing Internal information security • Centralized ‘In the cloud’ § § § Provider dependent High availability & Controlled environment Simple logistics “Clean Pipe” to the customer Centralized upgrade Fortinet Confidential

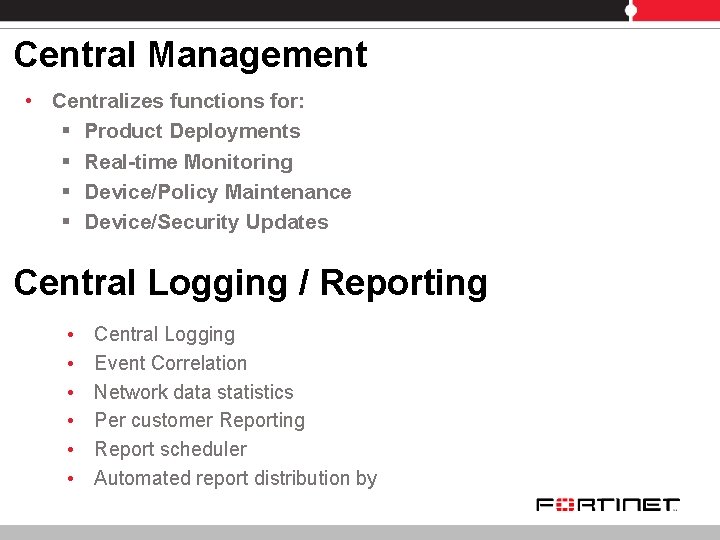
Central Management • Centralizes functions for: § Product Deployments § Real-time Monitoring § Device/Policy Maintenance § Device/Security Updates Central Logging / Reporting • • • Central Logging Event Correlation Network data statistics Per customer Reporting Report scheduler Automated report distribution by Fortinet Confidential

Consolidated security MSSP - Managed Security Service Provider Virtual Presence – The saga Web X. 0 / HTT-What? / SAAS Fortinet

Cross platform/media users Virtual identity • Users identity is roaming across multiple access layers § Access where ever(net access, VOIP presents, free mind) § Web based access (ssl-vpn, etc. ) advanced functionalities • Always available § IM and other applications over multiple access layers § Mail access in multiple variations of delivery/retrieval • The OS’s § Multiple operating systems are part of this experience § In The Claude/Network solution is not adequate • The solutions transparency as part of the user experience is part of this evolutions

Consolidated security MSSP - Managed Security Service Provider Virtual Presence – The saga Web X. 0 / HTT-What? / SAAS Fortinet

Web x. 0 / HTT? / SAAS challenges • Identity, privacy, reputation and anonymity is changing • Everyone is a content/service provider • Any user is part of the system/experience • Is there End-to-end security architecture? • The content is delivered and shared everywhere • Cross site scripting is required • It’s part of the advantages • HTTP/S as a transport layer (oovoo, rpc, etc) • For years it’s among the only un inspected tunnel’s we’ve allowed, and now it’s almost impossible to validate and control the application level.

Web x. 0 / HTT? / SAAS challenges • Changing the way Dynamic content is delivered • Asynchronous Java. Script (AJAX) and XML will provide a whole new frontier regarding inspection for incoming and out going traffic. • Dynamic analysis approach for security • Web x. 0 public key infrastructure? • Security services over Web x. 0 • We all like cookies (Transport layer) • Lately several Trojan horses been using cookies negotiation as a transport layer for data and commands, can we block/inspect this layer?

Consolidated security MSSP - Managed Security Service Provider Virtual Presence – The saga Web X. 0 / HTT-What? / SAAS About Fortinet

Company Overview • First Multi-Layered Security Platform provider that leverages ASIC technology • Largest private network security company • § ~ 1100 employees / > 650 R&D § 320, 000 + Forti. Gate devices WW § Founded in 2000 § Largest Privately Held Security Company § Global Operations in U. S. , EMEA & Asia Pac Independent certifications § 8 ICSA certifications (only vendor) § Government Certifications (FIPS-2, C C EAL 4+) § 60+ industry awards § 11 patents; 80+ pending § Virus Bulletin 100 approved (2005, 06, 07) and NSS Certifications Fortinet Confidential

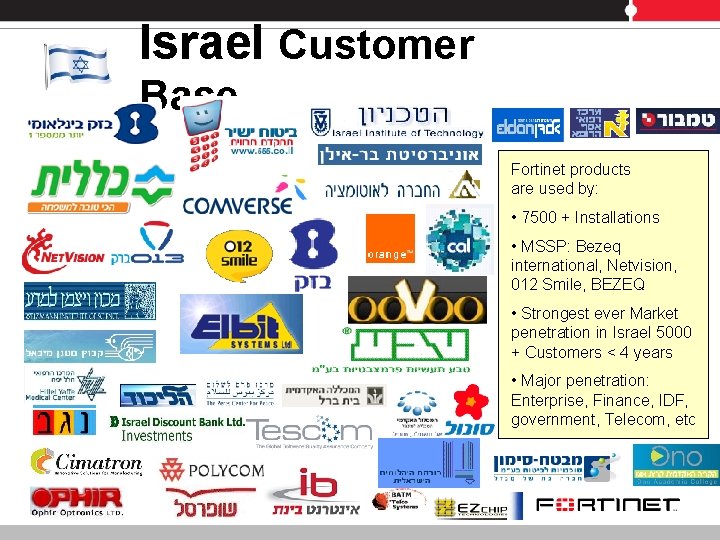
Israel Customer Base Fortinet products are used by: • 7500 + Installations • MSSP: Bezeq international, Netvision, 012 Smile, BEZEQ • Strongest ever Market penetration in Israel 5000 + Customers < 4 years • Major penetration: Enterprise, Finance, IDF, government, Telecom, etc

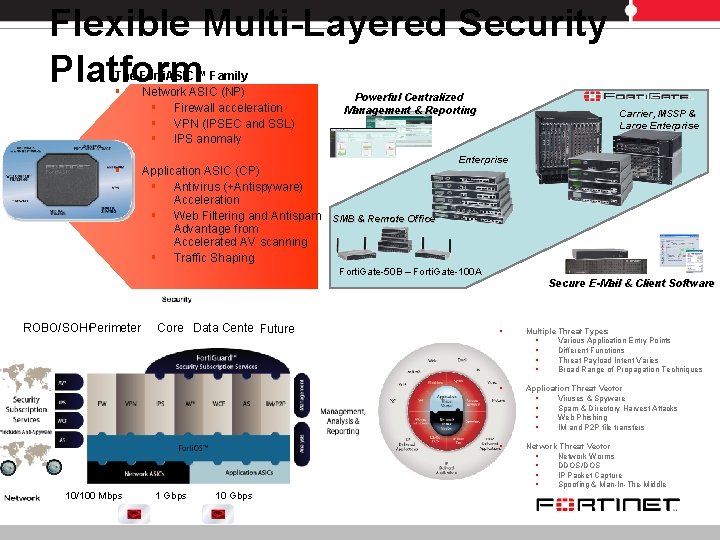
Flexible Multi-Layered Security Platform The Forti. ASIC™ Family § Network ASIC (NP) § Firewall acceleration § VPN (IPSEC and SSL) § IPS anomaly § Application ASIC (CP) § Antivirus (+Antispyware) Acceleration § Web Filtering and Antispam Advantage from Accelerated AV scanning § Traffic Shaping Powerful Centralized Management & Reporting Carrier, MSSP & Large Enterprise SMB & Remote Office Forti. Gate-50 B – Forti. Gate-100 A Secure E-Mail & Client Software ROBO/SOHO Perimeter 10/100 Mbps Core Data Center Future 1 Gbps 10 Gbps § Multiple Threat Types § Various Application Entry Points § Different Functions § Threat Payload Intent Varies § Broad Range of Propagation Techniques § Application Threat Vector § Viruses & Spyware § Spam & Directory Harvest Attacks § Web Phishing § IM and P 2 P file transfers § Network Threat Vector § Network Worms § DDOS/DOS § IP Packet Capture § Spoofing & Man-In-The-Middle

Fortinet is the Only: • Only complete solution with custom ASICs • Only complete solution from remote office to core and service providers with consistent code/hardware base. • Only complete solution that can do deep packet inspection • Only company with internal research on WCF, AS, AV, IPS • Only complete solution that does layer three routing • Only True virtualized solution for MSSP and enterprise • Only Security solution with Virtual solutions in Route and Transparent over the same Hardware!!! • Only solution with complete layer two switching • Only solution with real centralized Management interface • Only solution with real reporting and logging interface

Fortinet MSSP Customers Success …rely on protection from Fortinet Confidential

Thank You! For more information please visit http: //www. fortinet. com