Policy Description Enforcement Languages Anis Yousefi anis yousefimehr

















- Slides: 29

Policy Description & Enforcement Languages Anis Yousefi anis. yousefi@mehr. sharif. edu sharif university of technology

Outline o o Motivation and background Related work n n n o Rei: A RDF Schema-based language for policy specification. KAo. S: A policy representation language based on OWL. Ponder: An object-oriented policy language for the management of distributed systems and networks. Some issues sharif university of technology 2

Motivation o o A key need for the vision of the Semantic Web and Pervasive Computing to succeed is the ability to handle security and privacy and the ability to automate these protocols. A good approach: Policy based security and privacy protection Until recently: semantic web languages representing web content & services Our goal: to find suitable semantic web languages to describe and reason about policies sharif university of technology 3

Policy Advantages o o o Automated system management & Controlling the behavior of complex systems Allowing administrators to modify system behavior without changing source code or requiring the consent or cooperation of the components being governed separation of rules that govern the behavior of a system from the functionality provided by that system sharif university of technology 4

Benefits of policy-based approaches o o o o Reusability Efficiency Extensibility Context sensitivity Verifiability Support for both simple & sophisticated components Protection from poorly designed, buggy or malicious components Reasoning about component behavior sharif university of technology 5

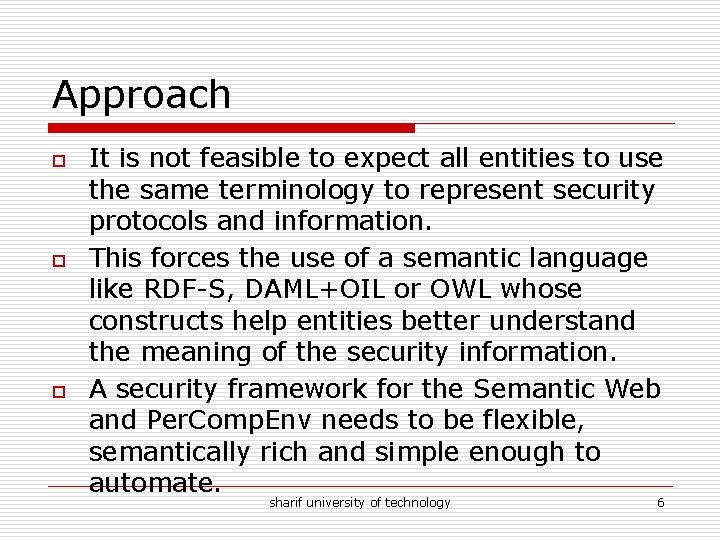
Approach o o o It is not feasible to expect all entities to use the same terminology to represent security protocols and information. This forces the use of a semantic language like RDF-S, DAML+OIL or OWL whose constructs help entities better understand the meaning of the security information. A security framework for the Semantic Web and Per. Comp. Env needs to be flexible, semantically rich and simple enough to automate. sharif university of technology 6

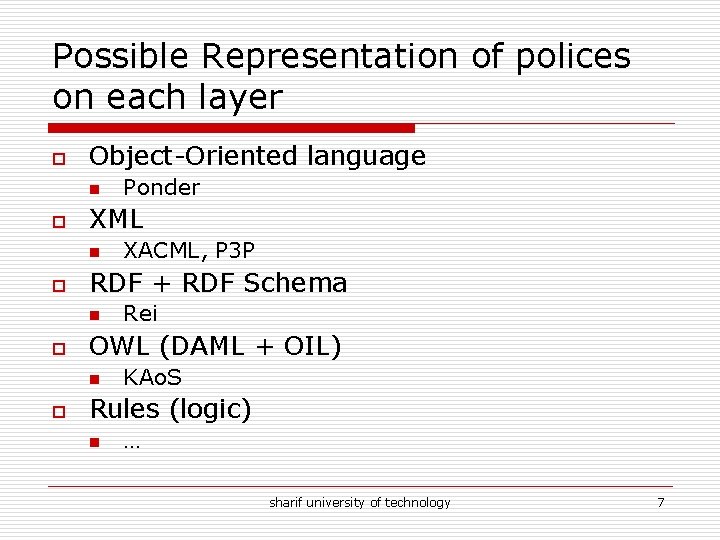
Possible Representation of polices on each layer o Object-Oriented language n o XML n o Rei OWL (DAML + OIL) n o XACML, P 3 P RDF + RDF Schema n o Ponder KAo. S Rules (logic) n … sharif university of technology 7

KAo. S o o o Collection of componentized agent services compatible with several agent frameworks : Corba, Nomads, … KAo. S domain services provide the capability for groups of software components, people, resources, and other entities to be organized into domains and subdomains to facilitate agent-agent collaboration and external policy administration. KAo. S policy services allow for the specification, management, conflict resolution, and enforcement of policies within domains. Policies are currently represented in DAML+OIL as ontologies. (soon OWL) sharif university of technology 8

KAo. S Policy Ontology o o o KPO (KAos Policy Ontology): distinguish between authorizations & obligations Obligations: constraints that require some action to be performed or else serve to waive such a requirement Authorizations: constraints that permit or forbid some action Policy type: Positive|negative Obligation|Authorization Policy: instance of policy type Properties & Property restrictions sharif university of technology 9

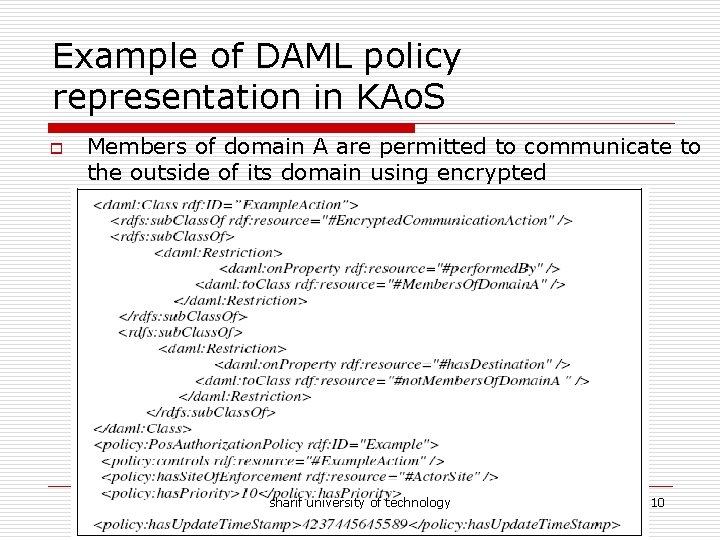
Example of DAML policy representation in KAo. S o Members of domain A are permitted to communicate to the outside of its domain using encrypted communication sharif university of technology 10

features o o o Work with arbitrary written components Dynamic runtime policy changes Extensible to a variety of execution platforms which policy enforcement mechanisms may be written Robust & Adaptable – attack or failure of components Easy-to-use policy-based administration tools: GUI for monitoring, visualizing & dynamically modifying policies at runtime sharif university of technology 11

KPAT o o KAos Policy Administration Tool Graphical tool for policy specification, revision & application, brows and load ontologies, deconflict newly defined policies. Policy templates: high level, domain specific abstraction Rich set of queries sharif university of technology 12

Conflict detection - KAo. S o o At specification time: add new policy to dirctory service Three types of conflict n n n o positive vs. negative authorization positive vs. negative obligation positive obligation vs. negative authorization The algorithms rely on Stanford’s Java Theorem Prover (JTP) sharif university of technology 13

Policy deployment Model-KAos o o Domain manager: management of domains of agents and assures policy consistency at all the levels of the domain hierarchy Directory Service: overall policy management Gaurds: interpret policies and pass them on to enforcers Enforcers: platform-specific components sharif university of technology 14

Rei: A policy language o o o Policy framework: specification, analysis & reasoning in Per. Comp The Rei deontic concept-based policy language allows users to express and represent the concepts of rights, prohibitions, obligations, and dispensations. (+, - A, O in KAo. S & Ponder) Rei relies on an application-independent ontology to represent the concepts of rights, prohibitions, obligations, dispensations, and policy rules. sharif university of technology 15

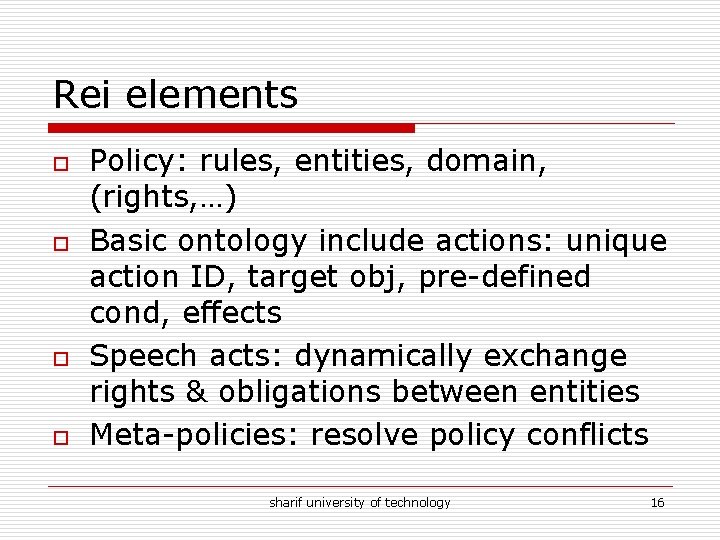
Rei elements o o Policy: rules, entities, domain, (rights, …) Basic ontology include actions: unique action ID, target obj, pre-defined cond, effects Speech acts: dynamically exchange rights & obligations between entities Meta-policies: resolve policy conflicts sharif university of technology 16

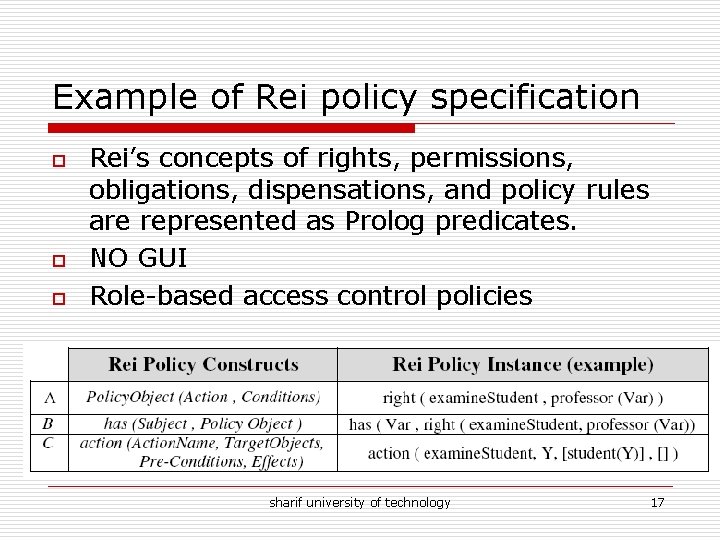
Example of Rei policy specification o o o Rei’s concepts of rights, permissions, obligations, dispensations, and policy rules are represented as Prolog predicates. NO GUI Role-based access control policies sharif university of technology 17

Reasoning - Rei o The Rei framework provides a policy engine that reasons about the policy specifications. n n o The engine accepts policy specification in both the Rei language and in RDF-S, consistent with the Rei ontology. RDF to (subject, predicate, object) The engine is consistent and complete and allows queries according to the Prolog language about any policies, meta-policies, and domain dependent knowledge that have been loaded in its knowledge base. sharif university of technology 18

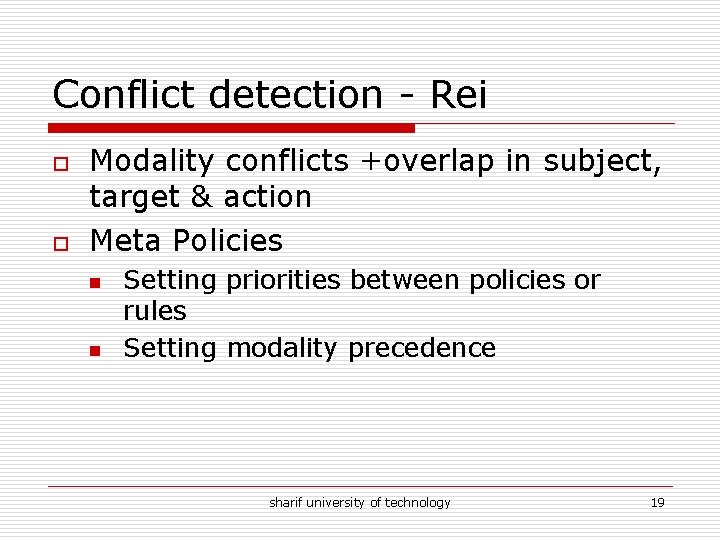
Conflict detection - Rei o o Modality conflicts +overlap in subject, target & action Meta Policies n n Setting priorities between policies or rules Setting modality precedence sharif university of technology 19

Policy deployment model-Rei o o o Policy engine: reason about policies & reply to queries No enforcement model No protection from malicious or noncompliant components or agents sharif university of technology 20

Ponder o o Declarative object-oriented language Specification of management policies for distributed object systems Basic Policy: rules governing choices in system behavior n Set of subjects and set of targets with management responsibility: have the authority to initiate a management decision Composite Policy: grouping basic policies of organization n Role: groups of policies governing the behavior of the same subject by specifying its rights & duties n Relationship: right & duties of rules towards each other sharif university of technology 21

Ponder policy o Two fundamental policy types n n o obligation authorization obligation: the actions that policy subjects must perform on target entities when specific relevant events occurs authorization: what operations a subject is authorized to do on target objects Management domains: group of objects to which policies apply sharif university of technology 22

Policy specification o o Type policy: user defined policy types Parameterized : context specific Policy instances No default rules: permit or forbid action? sharif university of technology 23

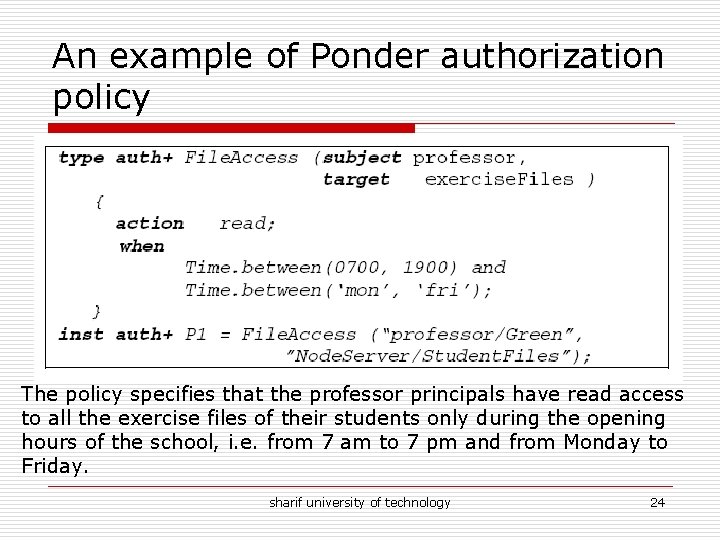
An example of Ponder authorization policy The policy specifies that the professor principals have read access to all the exercise files of their students only during the opening hours of the school, i. e. from 7 am to 7 pm and from Monday to Friday. sharif university of technology 24

Ponder tools o o Ponder provides various graphical tools for editing, updating, removing, and browsing Ponder policies. There also tools for syntactic and semantic analysis of policy specifications and for transforming Ponder language specifications directly into XML or Java code that can be interpreted at runtime. sharif university of technology 25

Conflict detection - Ponder o A prototype conflict detection tool to detect overlaps and conflicts between policies. n n Modality conflicts: policies with modalities of opposite signs that refer to the same subjects, targets & actions Ex: conflicts between permissions & prohibitions or between obligations and prohibitions Application specific conflicts: policy content & external criteria Ex: conflict between an obligation to access a resource and a limitation on the resource availability sharif university of technology 26

Policy deployment model. Ponder o o o Policy specification Ponder compiler: java class, java object Runtime changes not possible Distribution and enforcement model: distinguish between authorization and obligation policies Specification of the interfaces for enforcement agents but NO implementation Some systems implement in application domain sharif university of technology 27

Issues o o Choice should be driven by the characteristics of the application domain and by Simplicity, readability, analyzability scalability and enforceability requirements Ontology advantages: n n n o Complex systems: multiple levels of abstraction Description of the environment using concepts: simplifying the description, facilitating analysis & reasoning, conflict detection Simplify the access to policy information: quering the ontology accotding its schema dynamically calculating relations between policies and environment Sharing: negotiate between entities and agree Technical difficulties n n Complex syntax Long declarative description Hyperlinks & references to external resources (Ponder, DAML) Gap between specifiactionand implementation of policies sharif university of technology 28

References o o o o G. Tonti, etc, "Semantic Web Languages for Policy Representation and Reasoning: A Comparison of KAos, Rei, and Ponder", ISWC'03, 2003 A. Uszok, etc, "KAo. S Policy and Domain Services: Toward a Description-Logic Approach to Policy Representation, Deconfliction, and Enforcement", Policy'03, 2003 L. Kagal, etc, "A Policy Based Approach to Security for the Semantic Web", ISWC'03, 2003 N. Damianou, etc, "The Ponder Policy Specification Language", Policy'01, 2001 T. Finin, etc, "Agents, Trust, and Information Access on the Semantic Web", ACM SIGMOD Record, 2002 Y. Hu, etc, "Trust on the Semantic Web Pyramid: Some Issues and Challenges", ISWC'03, 2003 L. Kagal, etc, "Authorization and Privacy for Semantic Web Services", IEEE Computer Society, 2004 sharif university of technology 29
 Hivnet
Hivnet Narrative analysis
Narrative analysis Heamoconcentration
Heamoconcentration Altawbah
Altawbah Anis diagram
Anis diagram Deportista esfuerzo apostador suerte
Deportista esfuerzo apostador suerte Uwes anis chaeruman
Uwes anis chaeruman Hardware description language
Hardware description language Fines enforcement registry
Fines enforcement registry Asean wildlife enforcement network
Asean wildlife enforcement network Scrimmage kick
Scrimmage kick Military and law enforcement
Military and law enforcement Second line enforcement adalah
Second line enforcement adalah Nllea
Nllea Planning enforcement officers association
Planning enforcement officers association Tec traffic enforcement centre
Tec traffic enforcement centre Law enforcement mental health and wellness act
Law enforcement mental health and wellness act Law enforcement agency
Law enforcement agency [email protected]
[email protected] Columbus ms city hall
Columbus ms city hall Nc dmv license and theft bureau inspector
Nc dmv license and theft bureau inspector Crane night vision lease program
Crane night vision lease program Njdep compliance and enforcement
Njdep compliance and enforcement Hpd enforcement desk bed bugs
Hpd enforcement desk bed bugs Law enforcement information exchange
Law enforcement information exchange Law enforcement and emergency services video association
Law enforcement and emergency services video association Director of labour market enforcement
Director of labour market enforcement Ilea dishes
Ilea dishes Ncr linx
Ncr linx Calphoto dmv law enforcement
Calphoto dmv law enforcement