Phishing COEN 252 Computer Forensics Thomas Schwarz S











- Slides: 37

Phishing COEN 252 Computer Forensics Thomas Schwarz, S. J. 2006

URL Obscuring �Internet based criminal activity that subverts web technology: �Phishing (fraud) �Traffic redirection �Hosting of illegal sites �Child pornography

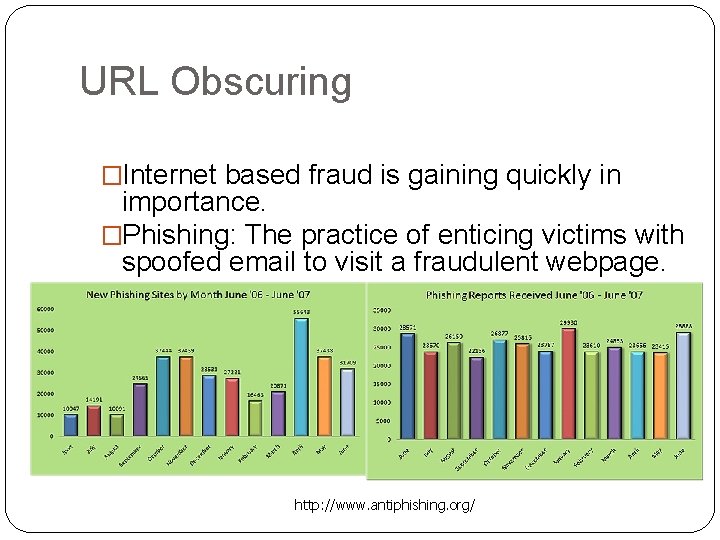
URL Obscuring �Internet based fraud is gaining quickly in importance. �Phishing: The practice of enticing victims with spoofed email to visit a fraudulent webpage. http: //www. antiphishing. org/

URL Obscuring �Technical Subterfuge: �Plants crimeware onto PCs. �Example: Vulnerable web browser executes remote script at a criminal website. � Just staying away from porn no longer protects you. �Payload: � Use Trojan keylogger spyware. � Search for financial data and send it to an untraceable email address

URL Obscuring �Social Engineering: �Target receives e-mail pretending to be from an institution inviting to go to the institutions website. �Following the link leads to a spoofed website, which gathers data. �It is possible to establish a web-presence without any links: � Establish website with stolen / gift credit card. � Use email to send harvested information to an untraceable account, etc. � Connect through public networks.

URL Obscuring �Phishing �Targets general population �Thrives even with very low success rate �Spear Phishing �Targets individuals �More sophisticated and more expensive �Individual success has higher value

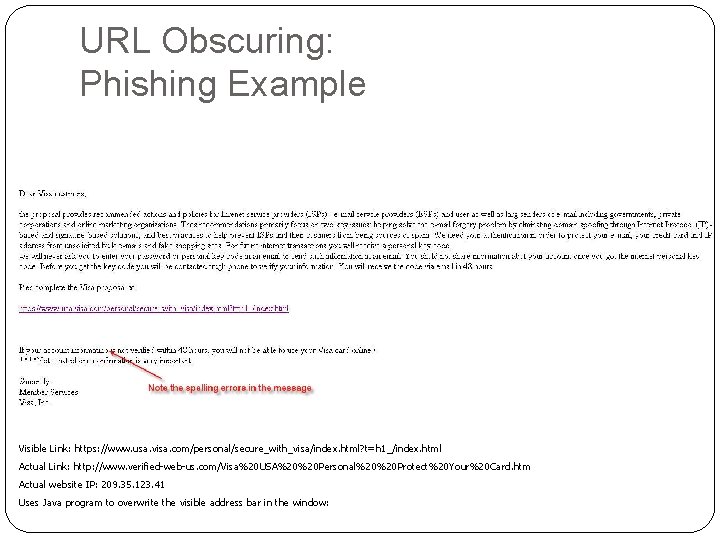
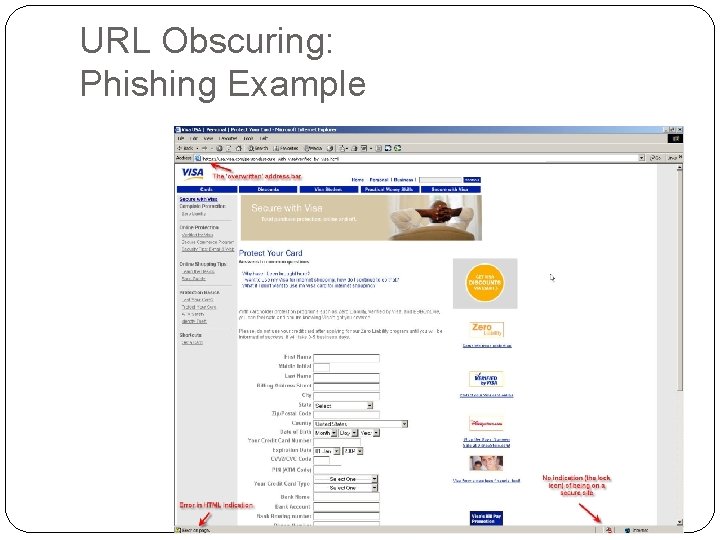
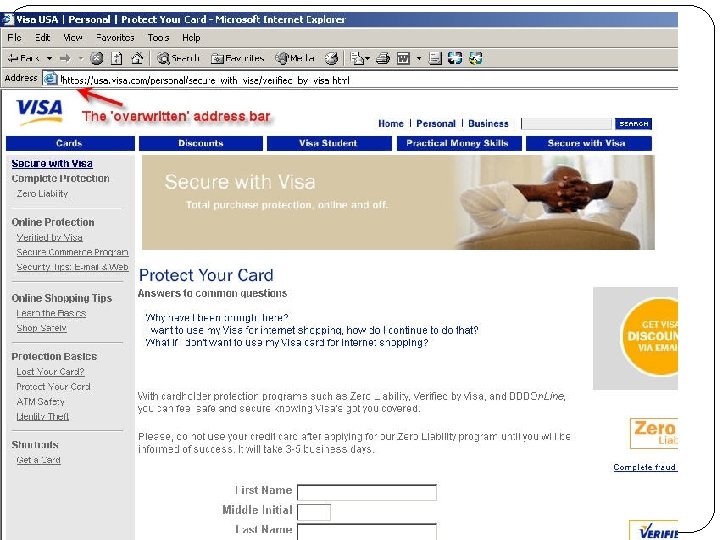
URL Obscuring: Phishing Example Visible Link: https: //www. usa. visa. com/personal/secure_with_visa/index. html? t=h 1_/index. html Actual Link: http: //www. verified-web-us. com/Visa%20 USA%20%20 Personal%20%20 Protect%20 Your%20 Card. htm Actual website IP: 209. 35. 123. 41 Uses Java program to overwrite the visible address bar in the window:

URL Obscuring: Phishing Example

Phishing Tendencies �Phishs currently are very unsophisticated �Sophistication does not yield much better success rate

URL Obscuring �Phishs need to hide web-servers �URL Obscuring �Javascript or other active web-technology overwrites URL field �no longer possible in latest browsers �Other techniques to hide web-server address �Use hosts file �Hiding illegal web-server at legal site �Hijacking site to host pages.

URL Basics �Phishs can use obscure features of URL. �URL consists of three parts: �Service �Address of server �Location of resource. http: //www. cse. scu. edu/~tschwarz/coen 252_03/Lectures/URLObscuring. html

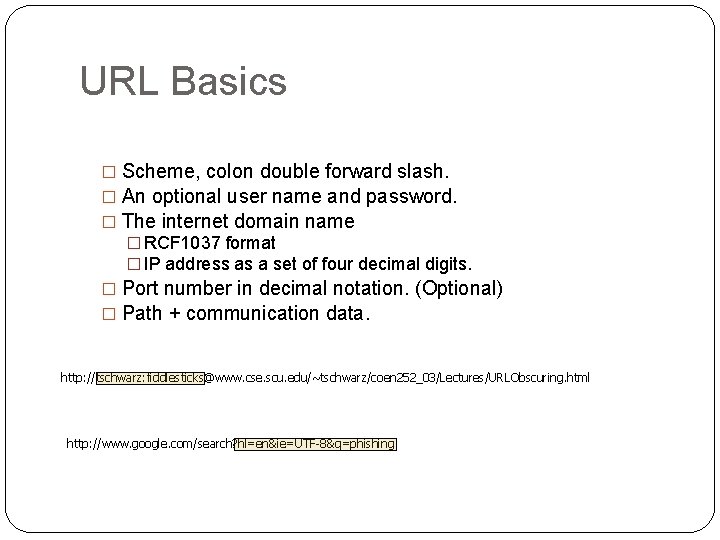
URL Basics � Scheme, colon double forward slash. � An optional user name and password. � The internet domain name � RCF 1037 format � IP address as a set of four decimal digits. � Port number in decimal notation. (Optional) � Path + communication data. http: //tschwarz: fiddlesticks@www. cse. scu. edu/~tschwarz/coen 252_03/Lectures/URLObscuring. html http: //www. google. com/search? hl=en&ie=UTF-8&q=phishing

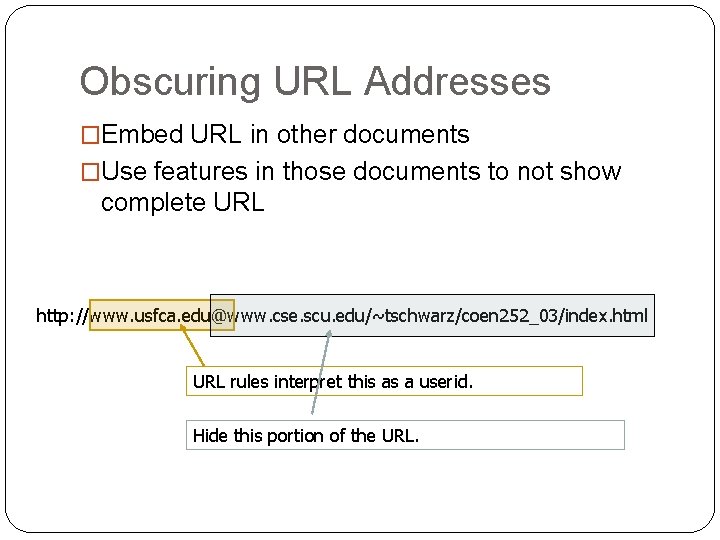
Obscuring URL Addresses �Embed URL in other documents �Use features in those documents to not show complete URL http: //www. usfca. edu@www. cse. scu. edu/~tschwarz/coen 252_03/index. html URL rules interpret this as a userid. Hide this portion of the URL.

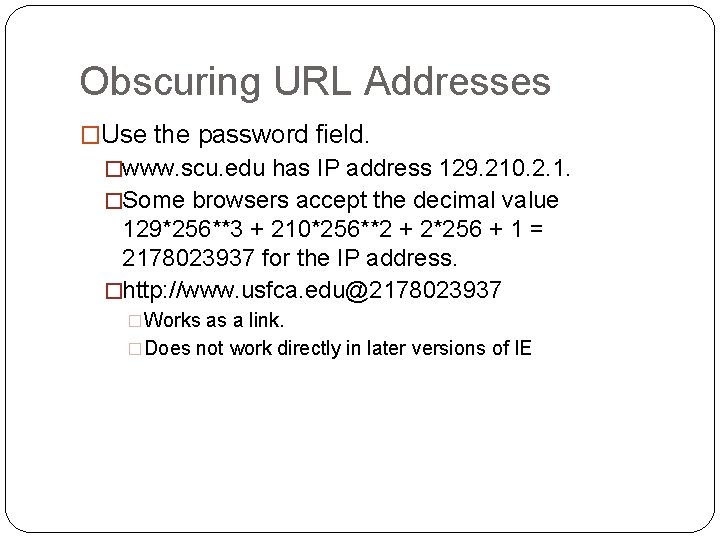
Obscuring URL Addresses �Use the password field. �www. scu. edu has IP address 129. 210. 2. 1. �Some browsers accept the decimal value 129*256**3 + 210*256**2 + 2*256 + 1 = 2178023937 for the IP address. �http: //www. usfca. edu@2178023937 �Works as a link. �Does not work directly in later versions of IE

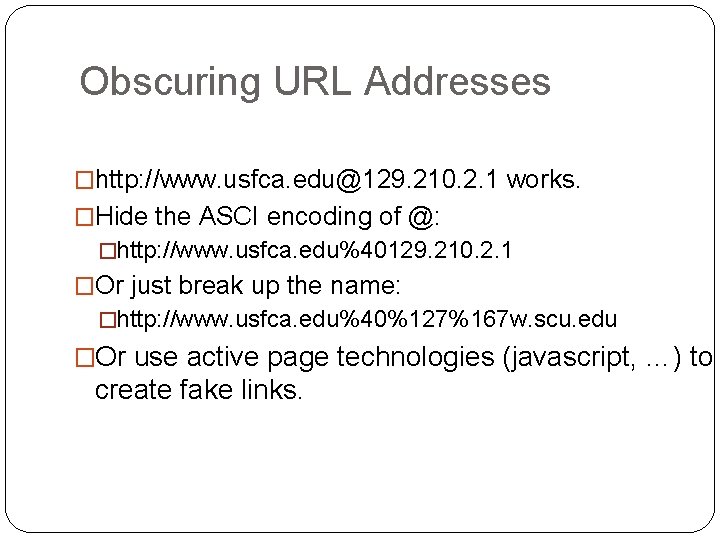
Obscuring URL Addresses �http: //www. usfca. edu@129. 210. 2. 1 works. �Hide the ASCI encoding of @: �http: //www. usfca. edu%40129. 210. 2. 1 �Or just break up the name: �http: //www. usfca. edu%40%127%167 w. scu. edu �Or use active page technologies (javascript, …) to create fake links.

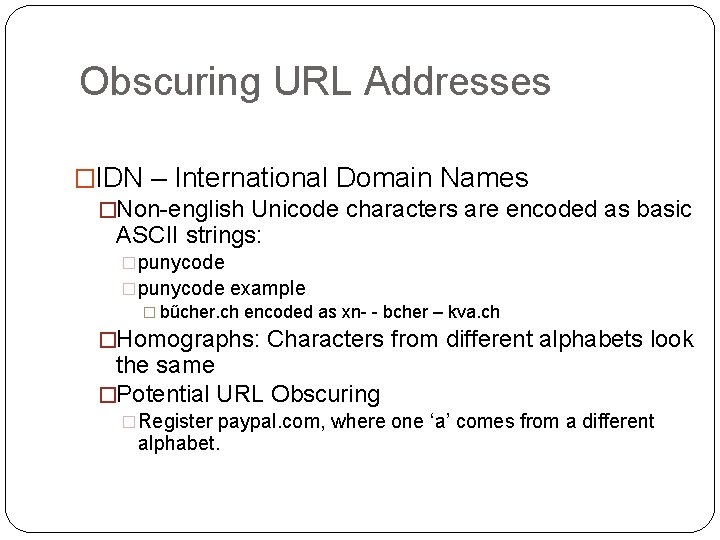
Obscuring URL Addresses �IDN – International Domain Names �Non-english Unicode characters are encoded as basic ASCII strings: �punycode example � bűcher. ch encoded as xn- - bcher – kva. ch �Homographs: Characters from different alphabets look the same �Potential URL Obscuring �Register paypal. com, where one ‘a’ comes from a different alphabet.

Obscuring URL Addresses �Padding URLs �. . means go up �create directory … �http: //129. 210. 2. 1/. . . /error. html

Obscuring URL Addresses � Redirection �Direct target redirects to main site �Chances of main site getting shut down is less � Technologies �Page-based redirection � Add meta tag to head section � <meta http-equiv=“refresh” content=“ 0; URL=http: //bobadilla. engr. scu. edu”> �Server-based redirection � Apache: httpd. conf with a redirect statement �Redirection via vulnerable websites � 2006 e. Bay run a script that redirected based on query string to any site.

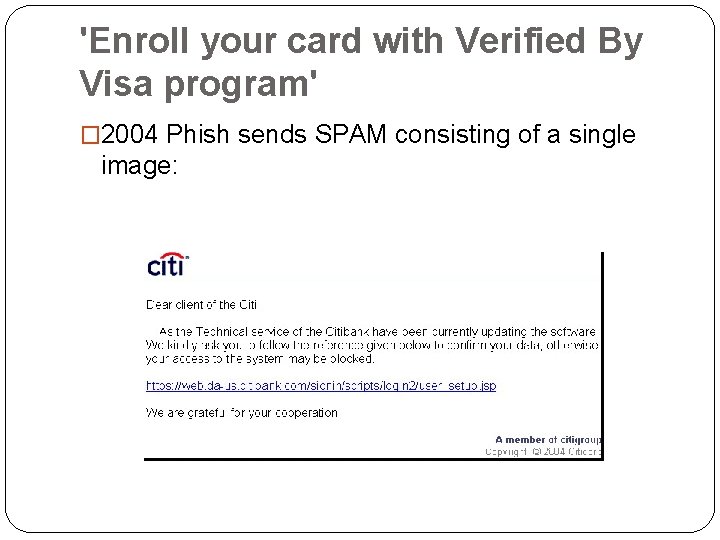
'Enroll your card with Verified By Visa program' � 2004 Phish sends SPAM consisting of a single image:

'Enroll your card with Verified By Visa program' � The whole text is a single image, linked to the correct citi URL. �If the mouse hovers over the image, it displays the correct citi URL. � But surrounded by an HTML box that leads to the phishing website.

'Enroll your card with Verified By Visa program' �Target webpage has an address bar that is overwritten with a picture with a different URL. �Go to www. antiphishing. org.



Phishing �Phishers now use bogus https techniques. �Exploiting browser flaws to display secure icon. �Hacking legitimate sites or frames from these sites directly. �Purchase and present certificates for sites that are named in resemblance of the target sites. �The SSL lock icon is no longer a guarantee for a legitimate site.

Registrar Impersonation Phishing Attacks �Phisher sets up a bogus registrar customer portal �Phisher composes email correspondence from registrar �Phisher sends email to the contact email addresses for a domain name �Victims visit bogus registrar customer portal and disclose login credentials �Phisher collects account credentials for subsequent misuse

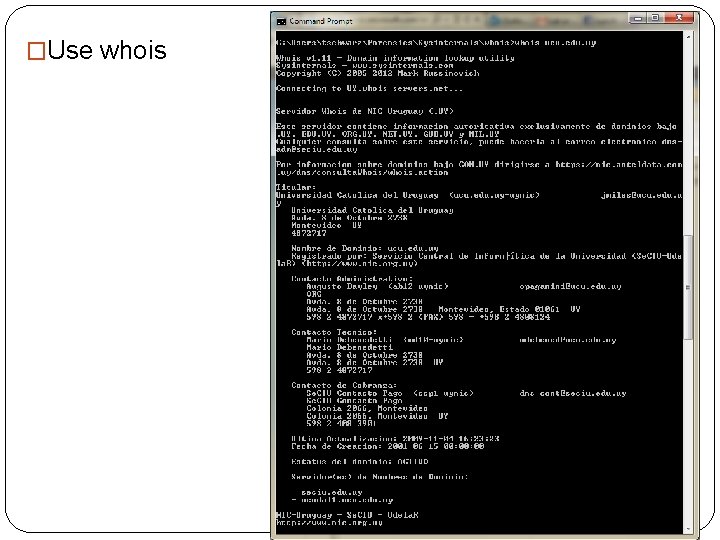
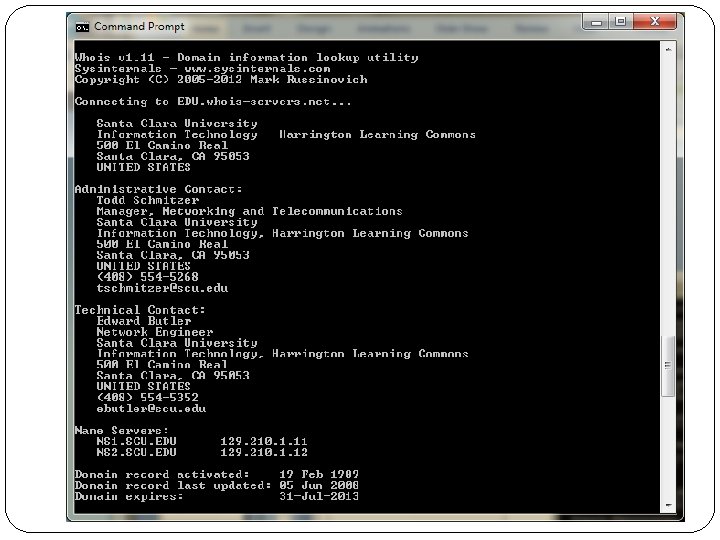
Registrar Impersonation Phishing Attacks �Domain name registration information is open to the public �E. g. whois for windows or linux/unix �Adversary can use this information (plus web) in order to target potential victims �For example, those whose registration is close to expiration �The information is also used to enhance the credibility of the message

�Use whois


Registrar Impersonation Phishing Attacks �Once authentication information is obtained �Modify DNS records to point to name servers under attacker’s control �MX: Points to mail hosts under attacker’s control and use them to send spam, … �The victim was trusted �AAAA or A: To point to systems under attacker control �To host phony content �To provide false authentication portals

Registrar Impersonation Phishing Attacks �Fast Flux attacks �Fully qualified domain name has multiple (hundreds or even thousands) IP addresses assigned to it.

Registrar Impersonation Phishing Attacks �Counter measures taken: �Registrars limit open information severely �Should not use email to communicate with clients

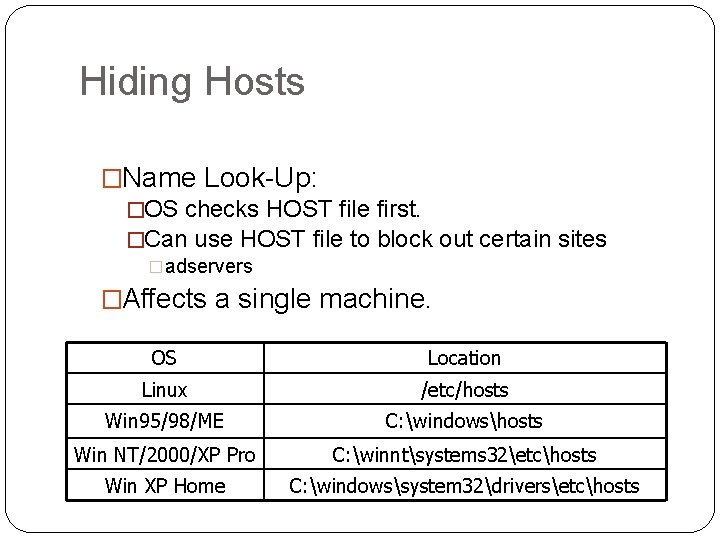
Hiding Hosts �Name Look-Up: �OS checks HOST file first. �Can use HOST file to block out certain sites �adservers �Affects a single machine. OS Location Linux /etc/hosts Win 95/98/ME C: windowshosts Win NT/2000/XP Pro C: winntsystems 32etchosts Win XP Home C: windowssystem 32driversetchosts

Subverting IP Look-Up �In general, not used for phishing. �Economic Damage �Hillary for Senate campaign attack. �Hiding illegal websites. (Kiddie Porn) �DNS Server Sabotage �IP Forwarding

Subverting IP Look-Up �Port Forwarding �URLs allow port numbers. �Legitimate business at default port number. �Illegitimate at an obscure port number. �Screen clicks �Embed small picture. �Single pixel. �Forward from picture to the illegitimate site. �Easily detected in HTML source code. �Password screens �Depending on access control, access to different sites.

Phisher-Finder �Carefully investigate the message to find the URL. �Do not expect this to be successful unless the phisher is low-tech. �Capture network traffic with Ethereal to find the actual URL / IP address. �Use Sam Spade or similar tools to collect data about the IP address.

Phisher-Finder �Capture network traffic with Ethereal when going to the site. �This could be dangerous. �Disable active webpages. �Do not use IE (too popular). �Look at the http messages actually transmitted. �Expect some cgi etc. script.

Phisher-Finder �Investigation now needs to find the person that has access to the website. �This is were you can expect to loose the trace. �The data entered can be transmitted in various forms, such as anonymous email. � For example, they can be sent to a free email account. � IPS usually has the IP data of the computer from which the account was set up and from which the account was recently accessed. � Perpetrator can use publicly available computers and / or unencrypted wireless access points. � Investigator is usually left with vague geographical data.