Key Infection Smart Trust for Smart Dust Ross











- Slides: 33

Key Infection: Smart Trust for Smart Dust Ross Anderson Haowen Chan Adrian Perrig University of Cambridge Carnegie Mellon Uni. Presented by EMRAH ATILGAN

Outline Introduction Previous Works Contribution Analysis Multihop and Multipath Key Establishment Economic Issues Questions

Sensors A sensor is a device that measures a physical quantity and converts it into a signal which can be read by an observer or by an instrument. Example: Mercury thermometer Converts the measured temperature into expansion and contraction of a liquid which can be read on a calibrated glass tube. Cars, machines, aerospace, medicine, manufacturing and robotics.

Constraints of Sensors �Should be small, lightweight, inexpensive and low -power �Energy efficiency of network communications. �Computational energy consumption �Communications energy consumption �Rechargeability �Sleep patterns �Transmission range �Memory �Location sensing �Tamper protection

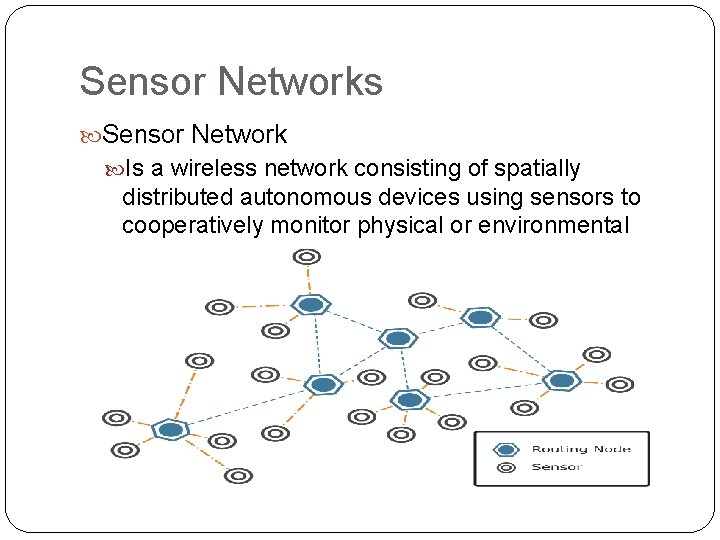
Sensor Networks Sensor Network Is a wireless network consisting of spatially distributed autonomous devices using sensors to cooperatively monitor physical or environmental conditions.

Sensor Networks Security for sensor networks is important Managing cryptographic key Low-cost nodes are neither tamper-proof nor capable of performing public key cryptographic efficiently.

Sensor Networks Typical sensor networks consist of a large number of small, low-cost nodes that use peer-to peer communication to form of a self-organized network. use multi-hop routing algorithms based on dynamic network and resource discovery protocols. do not have tamper-proof hardware. PROBLEM!!! Small fraction of nodes in the network may be compromised by an adversary over time.

Security Issues of Sensor Networks � Physical destruction � Barrage jamming � Network flooding � Byzantine Attack �An arbitrary fault during the execution of an algorithm by a distributed system. �When it occurs, the system may response in any unpredictable way. � The results of such attacks �Loss of personal privacy �Loss of service of critical sensor systems �Etc…

Smart dust A network of tiny wireless microelectromechanical systems sensors, robots, or devices, installed with wireless communications Can detect Light, temperature, vibration, heat, pressure, sound, etc. . The goal Make sensors so small and cheap Distribute them in large numbers over an area by random scattering

Previous Work �In a typical sensor network, when a node (i) broadcasts identity, if j hears it, it replies. Then these two nodes set RF power at just the level needed for communication. �To save power: the nodes turn off their communications, only waking up and listening for radio signals intermittently. �The routing architecture �Rely on shared symmetric key �Initial keys are diversified from master keys: �Still vulnerable �An opponent can use direction from finding locate them, then either destroy them or subvert them

Possible countermeasures Use normal nodes as base stations and have other nodes replace them after random periods of time. For the first generation of base stations to possess master keys that are destroyed once a network has been established and link keys have been set up between neighboring nodes. Enough symmetric keys are pre-loaded on each node that any two nodes will probably share a key after deployment. Require pre-computation phase And a lot of memory to store keys

A Real World Attacker Model � Previous works have assumed highly capable and motivated attacker �World War II � Consider a tactical deployment of 10, 000 smart dust motes air-dropped into enemy territory. i J KM � Use KM to generate to a session key: � However; �Some motes are broken on impact �The enemy can probe out KM

Non-critical commodity sensor networks Require pre-deployment step must be minimal Less valuable as targets and little damage if security shell is broken House or bank? ?

Contributions Design a lightweight security protocol suitable for non-critical commodity sensor networks. Key Infection The attacker can monitor only a fixed percentage α of communication channel. Relaxed attacker model Low computation overhead No memory overhead No prior key setup It is suitable for implementation in low-cost commodity sensor nodes.

Contributions Identify a more realistic attacker model that is applicable to non-critical commodity sensor networks. Key Infection A light-weight key-distribution mechanism that is so efficient that is applicable even to smart dust sensor nodes. Analyze the security of key infection, and design Secrecy Amplification An additional mechanism to strengthen the security of key infection in the presence of an active attacker. COST and USABILITY

Assume the attacker…. Does not have physical access to the deployment site during the deployment phase Is able to monitor only a small proportion α of the communications of the sensor network during the deployment phase. After key exchange is complete, attacker is able to monitor all communications at will Is unable to execute active attacks (such as jumming or flooding) during the deployment phase. After key exchange is complete, attacker is free to launch any kind of attack.

Requirements for adversary He has to have the foresight to deploy surveillance equipment or adversarial nodes at the target site before the sensor network is deployed there. His eavesdropping devices must remain in place, operational an undetected, until the sensor perform key exchange He needs to be able to identify, retrieve and process the relevant eavesdropped product in order to extract the key exchange messages. Too expensive to maintain anticipatory.

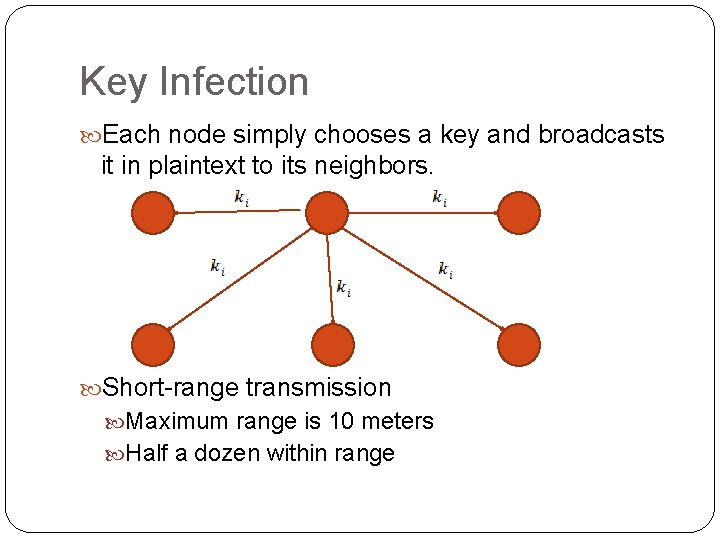
Key Infection Each node simply chooses a key and broadcasts it in plaintext to its neighbors. Short-range transmission Maximum range is 10 meters Half a dozen within range

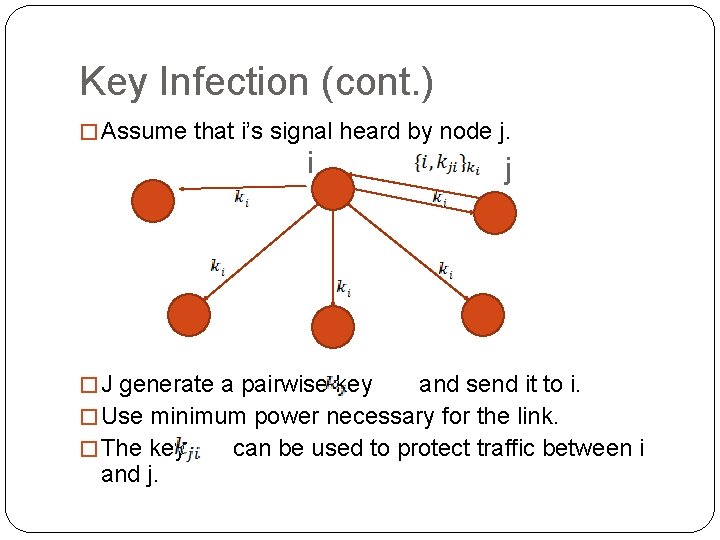
Key Infection (cont. ) � Assume that i’s signal heard by node j. i � J generate a pairwise key j and send it to i. � Use minimum power necessary for the link. � The key can be used to protect traffic between i and j.

Key Infection (cont. ) Even if there are opponents already present at the time of deployment, it will still give significant protection For example; There is 1 black (hostile) dust sensor node for every 100 white nodes, Each node has an average 4 neighbors within range, Only 2. 4% of link will be compromised. Key whispering protocol The probability falls to 0. 8%

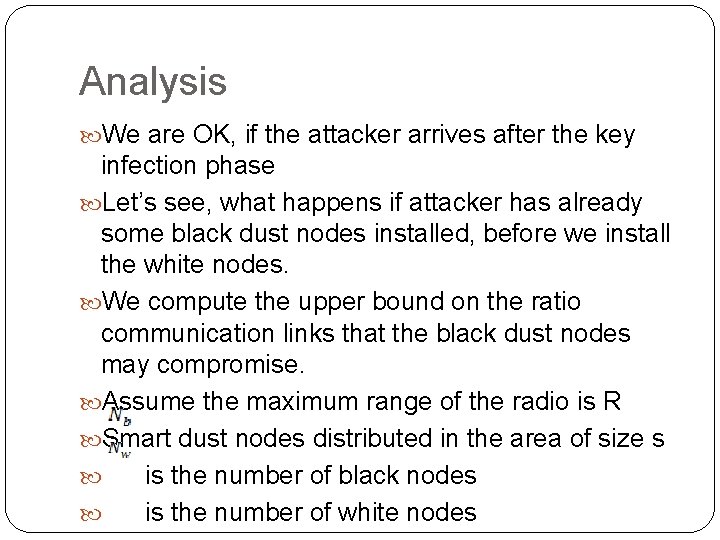
Analysis We are OK, if the attacker arrives after the key infection phase Let’s see, what happens if attacker has already some black dust nodes installed, before we install the white nodes. We compute the upper bound on the ratio communication links that the black dust nodes may compromise. Assume the maximum range of the radio is R Smart dust nodes distributed in the area of size s is the number of black nodes is the number of white nodes

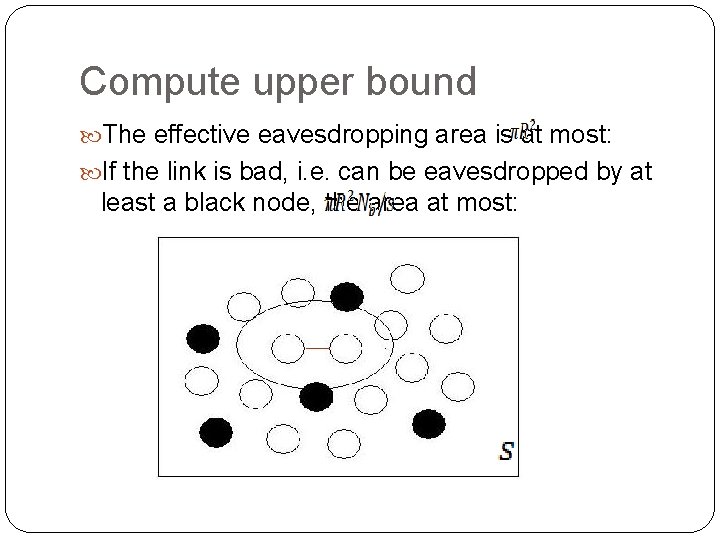
Compute upper bound The effective eavesdropping area is at most: If the link is bad, i. e. can be eavesdropped by at least a black node, the area at most:

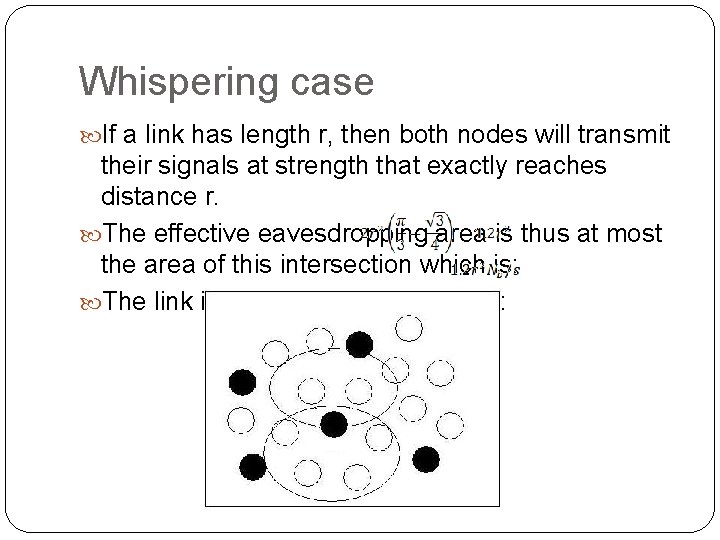
Whispering case If a link has length r, then both nodes will transmit their signals at strength that exactly reaches distance r. The effective eavesdropping area is thus at most the area of this intersection which is: The link is compromised is at most:

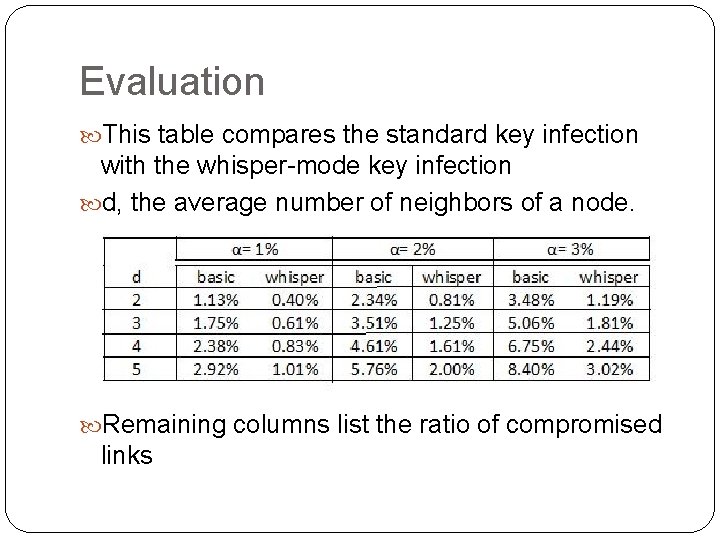
Evaluation This table compares the standard key infection with the whisper-mode key infection d, the average number of neighbors of a node. Remaining columns list the ratio of compromised links

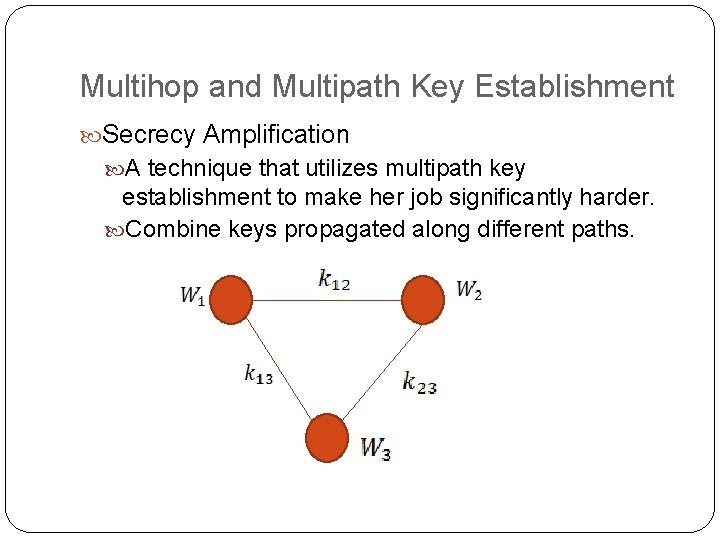
Multihop and Multipath Key Establishment Secrecy Amplification A technique that utilizes multipath key establishment to make her job significantly harder. Combine keys propagated along different paths.

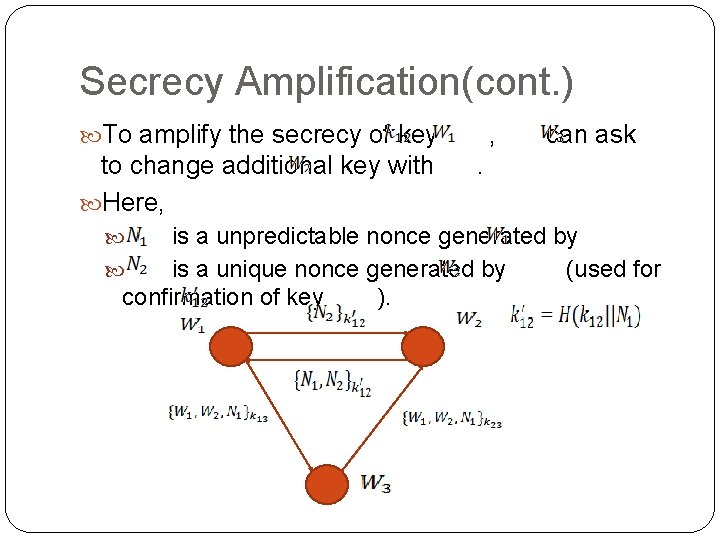
Secrecy Amplification(cont. ) To amplify the secrecy of key to change additional key with Here, , can ask . is a unpredictable nonce generated by is a unique nonce generated by (used for confirmation of key ).

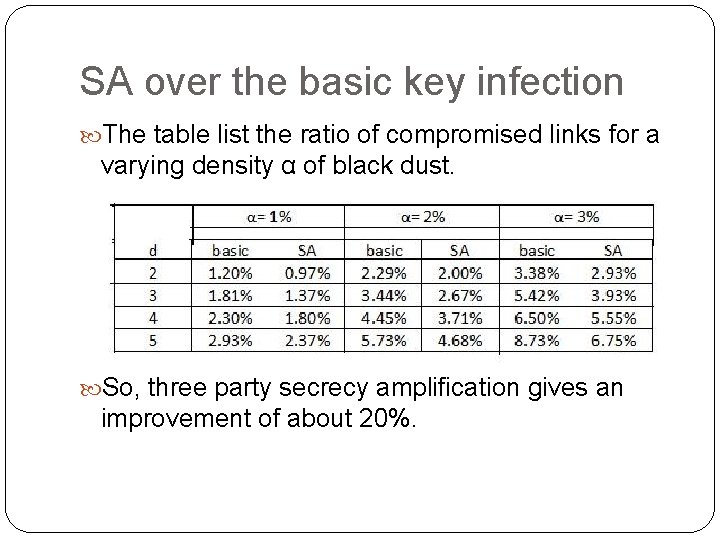
SA over the basic key infection The table list the ratio of compromised links for a varying density α of black dust. So, three party secrecy amplification gives an improvement of about 20%.

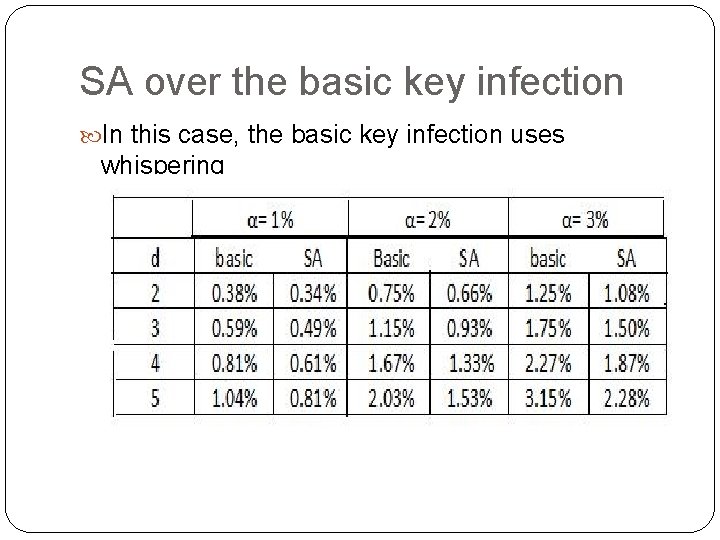
SA over the basic key infection In this case, the basic key infection uses whispering

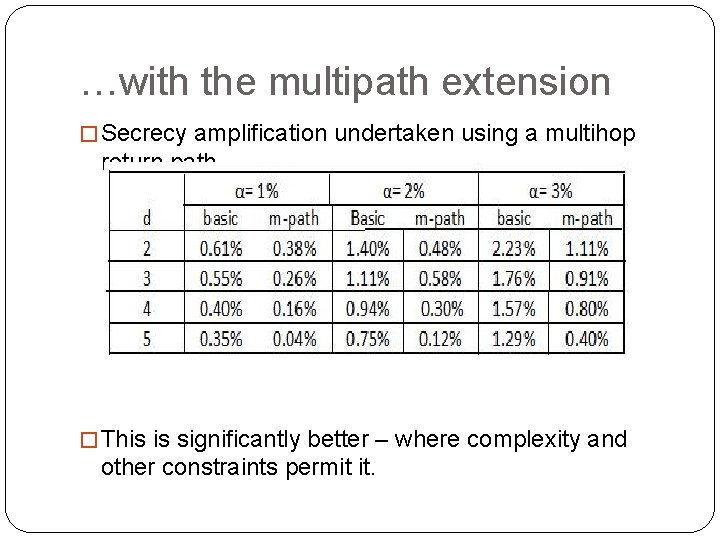
…with the multipath extension � Secrecy amplification undertaken using a multihop return path. � This is significantly better – where complexity and other constraints permit it.

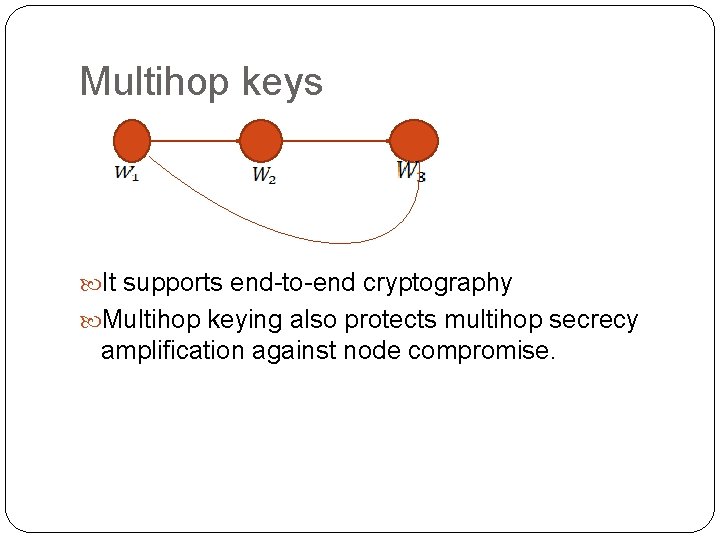
Multihop keys It supports end-to-end cryptography Multihop keying also protects multihop secrecy amplification against node compromise.

Interaction with routing algorithms �Some works on secure ad-hoc routing assumes a particular routing strategy. �This work does not… �This key infection protocol can also support other mechanisms. �Automatically discovers paths that may be used for this as needed �Example: �In biology, the immune response normally stops you catching the same disease twice �If you are a smart dust mote, the more keys you ‘catch’ from a colleague, the better.

Conclusion � The authors proposed a novel and quite counterintuitive way of managing key sensor networks. �Each nodes bootstraps itself by broadcasting an initial key in the clear. �Exchange keys and build up trust structures as they do network and resource discovery. �This is almost as secure as using pre-loaded initial keys. � This paper shows how the benefits of initial keying can be analyzed separately from the benefits of later stage key management activities, �key updating, �the use of alternative trust routes, and �the invocation of backups

Questions