ITEC 275 Computer Networks Switching Routing and WANs

































- Slides: 61

ITEC 275 Computer Networks – Switching, Routing, and WANs Week 6 Robert D’Andrea Some slides provide by Priscilla Oppenheimer and used with permission

Agenda • Learning Activities – IP Addressing – Static and Dynamic Assignment – IPv 6 – IPv 4 to IPv 6 Transition Methods

Guidelines for Addressing and Naming • Use a structured model for addressing and naming • Assign addresses and names hierarchically • Decide in advance if you will use – Central or distributed authority for addressing and naming – Public or private addressing – Static or dynamic addressing and naming

Advantages of Structured Models for Addressing & Naming • It makes it easier to – Read network maps – Operate network management software – Recognize devices in protocol analyzer traces – Meet goals for usability – Design filters on firewalls and routers – Implement route summarization

Public IP Addresses • Managed by the Internet Assigned Numbers Authority (IANA) • Users are assigned IP addresses by Internet service providers (ISPs). • ISPs obtain allocations of IP addresses from their appropriate Regional Internet Registry (RIR)

Regional Internet Registries (RIR) • American Registry for Internet Numbers (ARIN) serves North America and parts of the Caribbean. • RIPE Network Coordination Centre (RIPE NCC) serves Europe, the Middle East, and Central Asia. • Asia-Pacific Network Information Centre (APNIC) serves Asia and the Pacific region. • Latin American and Caribbean Internet Addresses Registry (LACNIC) serves Latin America and parts of the Caribbean. • African Network Information Centre (Afri. NIC) serves Africa.

Criteria for Using Static Vs. Dynamic Addressing • • • The number of end systems The likelihood of needing to renumber The need for high availability Security requirements The importance of tracking addresses Whether end systems need additional information – (DHCP can provide more than just an address)

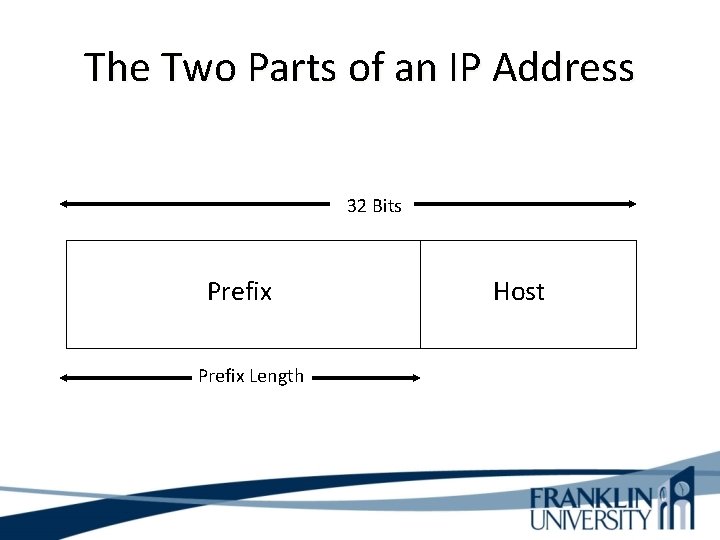
The Two Parts of an IP Address 32 Bits Prefix Length Host

Prefix Length • An IP address is accompanied by an indication of the prefix length – Subnet mask – /Length • Examples – 192. 168. 10. 1 255. 0 – 192. 168. 10. 1/24

Subnet Mask • 32 bits long • Specifies which part of an IP address is the network/subnet field and which part is the host field – The network/subnet portion of the mask is all 1 s in binary. – The host portion of the mask is all 0 s in binary. – Convert the binary expression back to dotted-decimal notation for entering into configurations. • Alternative – Use slash notation (for example /24) – Specifies the number of 1 s

Subnet Mask Example • 11111111 0000 • What is this in slash notation? • What is this in dotted-decimal notation?

Subnet Mask Example • 11111111 0000 • What is this in slash notation? – /24 • What is this in dotted-decimal notation? – 255. 0

Another Subnet Mask Example • 111111110000 • What is this in slash notation? • What is this in dotted-decimal notation?

Another Subnet Mask Example • 111111110000 • What is this in slash notation? – /20 • What is this in dotted-decimal notation? – 255. 240. 0

One More Subnet Mask Example • 11111111000 0000 • What is this in slash notation? • What is this in dotted-decimal notation?

One More Subnet Mask Example • 11111111000 0000 • What is this in slash notation? – 21 • What is this in dotted-decimal notation? – 255. 248. 0

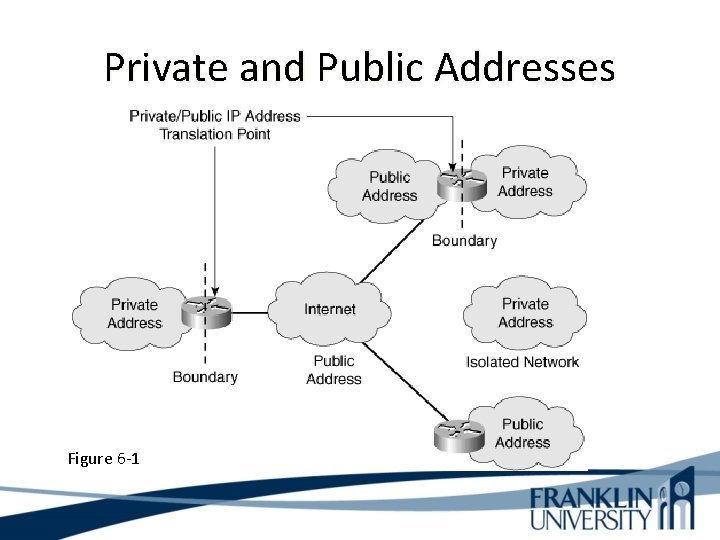
Private and Public Addresses Figure 6 -1

NAT • Static – One private address to one public address – Used for servers that must be visible to the public network • Dynamic – Many unregistered addresses to one registered address from a pool of addresses – Used for workstations that only connect to the public network when required • Combination – Used by most organizations

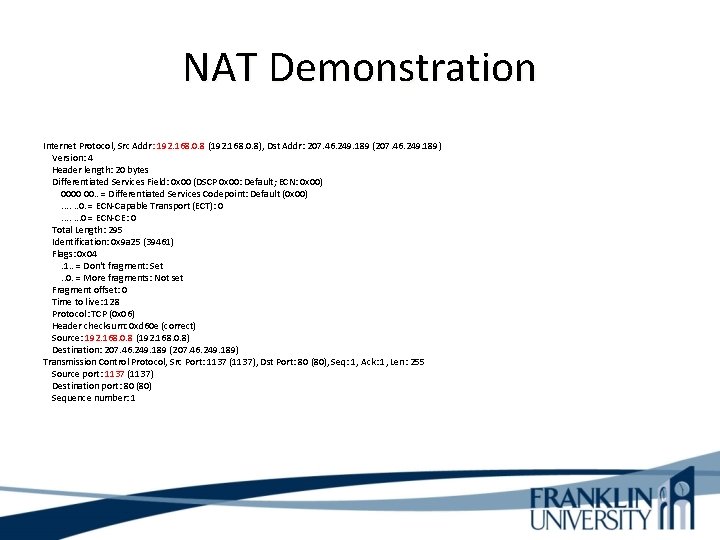
NAT Demonstration Internet Protocol, Src Addr: 192. 168. 0. 8 (192. 168. 0. 8), Dst Addr: 207. 46. 249. 189 (207. 46. 249. 189) Version: 4 Header length: 20 bytes Differentiated Services Field: 0 x 00 (DSCP 0 x 00: Default; ECN: 0 x 00) 0000 00. . = Differentiated Services Codepoint: Default (0 x 00). . . 0. = ECN-Capable Transport (ECT): 0. . . . 0 = ECN-CE: 0 Total Length: 295 Identification: 0 x 9 a 25 (39461) Flags: 0 x 04. 1. . = Don't fragment: Set. . 0. = More fragments: Not set Fragment offset: 0 Time to live: 128 Protocol: TCP (0 x 06) Header checksum: 0 xd 60 e (correct) Source: 192. 168. 0. 8 (192. 168. 0. 8) Destination: 207. 46. 249. 189 (207. 46. 249. 189) Transmission Control Protocol, Src Port: 1137 (1137), Dst Port: 80 (80), Seq: 1, Ack: 1, Len: 255 Source port: 1137 (1137) Destination port: 80 (80) Sequence number: 1

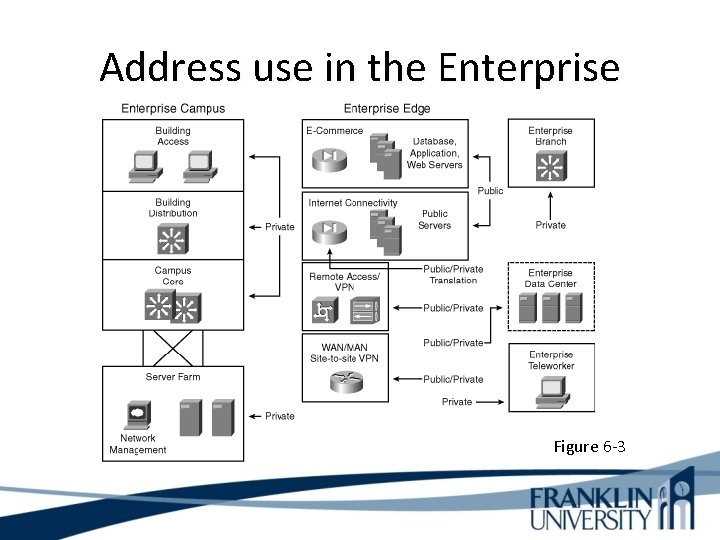
Address use in the Enterprise Figure 6 -3

Designing Networks with Subnets • Determining subnet size • Computing subnet mask • Computing IP addresses

Determinations • How many locations? – How many segments are required? • How many devices? – How large must each segment be? • What are the IP addressing requirements for each location? – Is public access required? • What subnet size is appropriate? – Determined by first and second questions

Addresses to Avoid When Subnetting • • A node address of all ones (broadcast) A node address of all zeros (network) A subnet address of all ones (all subnets) A subnet address of all zeros (confusing) – Cisco IOS configuration permits a subnet address of all zeros with the ip subnet-zero command

Practice Network is 172. 16. 0. 0 You want to divide the network into subnets. You will allow 600 nodes per subnet. What subnet mask should you use? What is the address of the first node on the first subnet? • What address would this node use to send to all devices on its subnet? • • •

Practice • Network is 172. 16. 0. 0 • You want to divide the network into subnets. – 64 • You will allow 600 nodes per subnet. – 1022 • What subnet mask should you use? – 255. 252. 0 (/22) • What is the address of the first node on the first subnet? – 172. 16. 0. 1 • What address would this node use to send to all devices on its subnet? – 172. 16. 3. 255

More Practice • Network is 172. 16. 0. 0 • You have eight LANs, each of which will be its own subnet. • What subnet mask should you use? • What is the address of the first node on the first subnet? • What address would this node use to send to all devices on its subnet?

More Practice • Network is 172. 16. 0. 0 • You have eight LANs, each of which will be its own subnet. • What subnet mask should you use? – 255. 224. 0 (/19) • What is the address of the first node on the first subnet? – 172. 16. 0. 1 • What address would this node use to send to all devices on its subnet? – 172. 16. 31. 255

One More Network is 192. 168. 55. 0 You want to divide the network into subnets. You will have approximately 25 nodes per subnet. What subnet mask should you use? What is the address of the last node on the last subnet? • What address would this node use to send to all devices on its subnet? • • •

One More • Network is 192. 168. 55. 0 • You want to divide the network into subnets. – 8 • You will have approximately 25 nodes per subnet. – 30 • What subnet mask should you use? – 255. 224 (/27) • What is the address of the last node on the last subnet? – 192. 168. 255. 254 • What address would this node use to send to all devices on its subnet? – 192. 168. 255

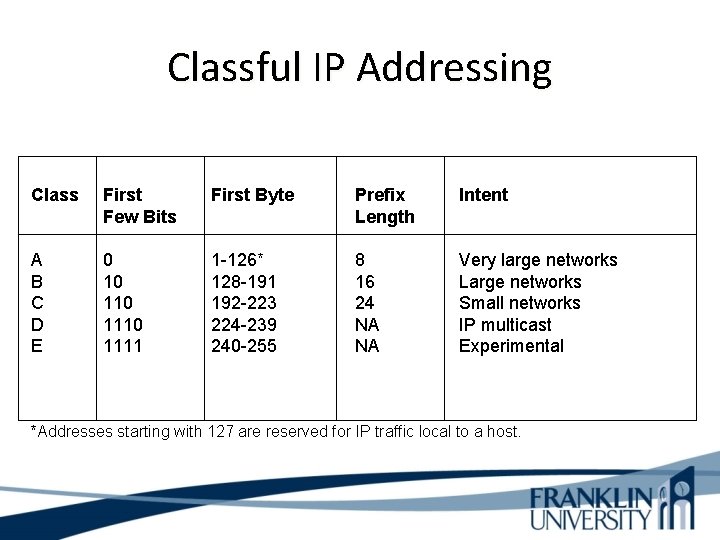
IP Address Classes • Classes are now considered obsolete • But you have to learn them because – Everyone in the industry still talks about them! – You may run into a device whose configuration is affected by the classful system

Classful IP Addressing Class First Few Bits First Byte Prefix Length Intent A B C D E 0 10 1110 1111 1 -126* 128 -191 192 -223 224 -239 240 -255 8 16 24 NA NA Very large networks Large networks Small networks IP multicast Experimental *Addresses starting with 127 are reserved for IP traffic local to a host.

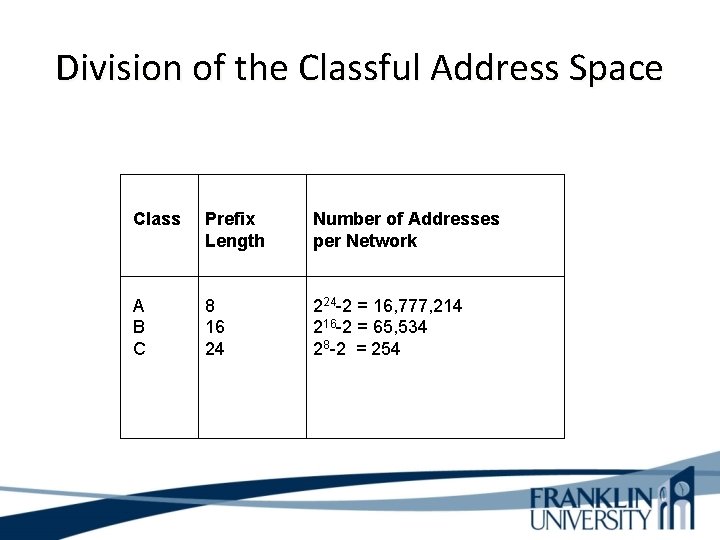
Division of the Classful Address Space Class Prefix Length Number of Addresses per Network A B C 8 16 24 224 -2 = 16, 777, 214 216 -2 = 65, 534 28 -2 = 254

Classful IP is Wasteful • • Class A uses 50% of address space Class B uses 25% of address space Class C uses 12. 5% of address space Class D and E use 12. 5% of address space

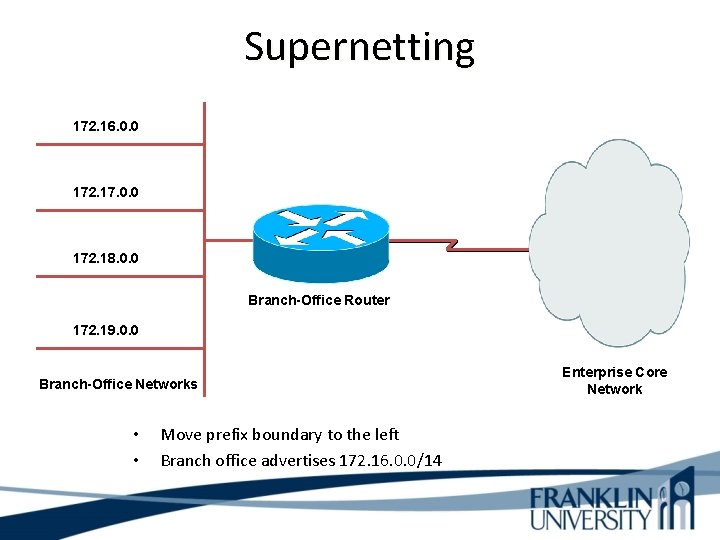
Classless Addressing • Prefix/host boundary can be anywhere • Less wasteful • Supports route summarization – Also known as • • • Aggregation Supernetting Classless routing Classless inter-domain routing (CIDR) Prefix routing

Supernetting 172. 16. 0. 0 172. 17. 0. 0 172. 18. 0. 0 Branch-Office Router 172. 19. 0. 0 Branch-Office Networks • • Move prefix boundary to the left Branch office advertises 172. 16. 0. 0/14 Enterprise Core Network

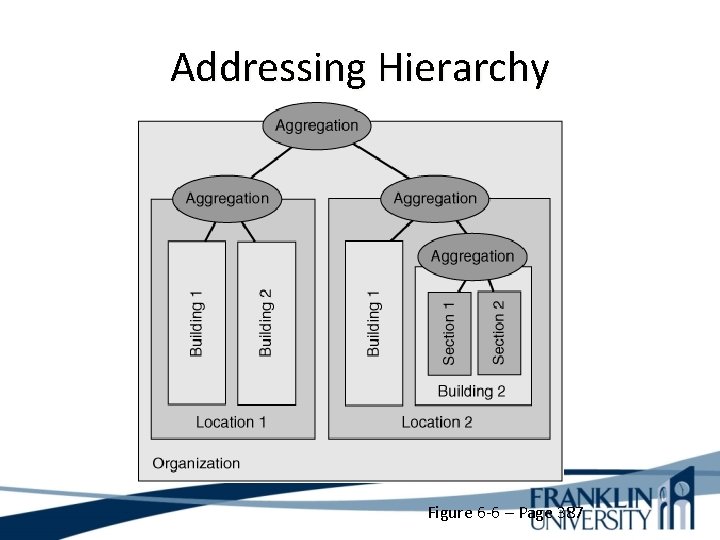
Addressing Hierarchy Figure 6 -6 – Page 387

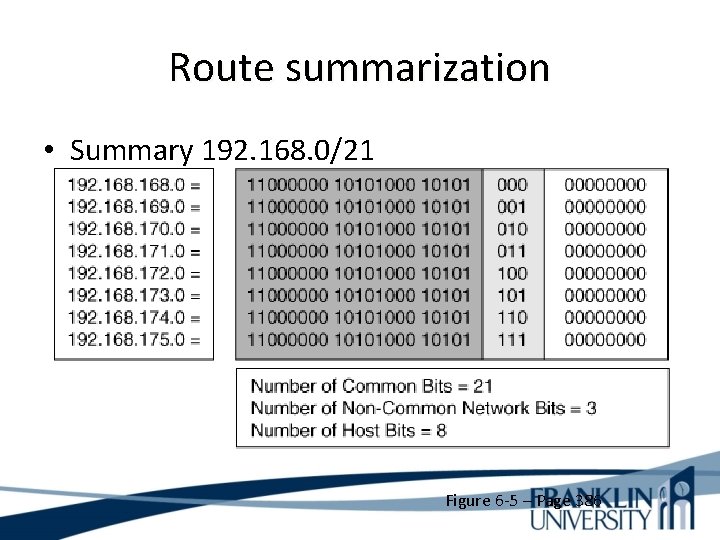
Route summarization • Summary 192. 168. 0/21 Figure 6 -5 – Page 386

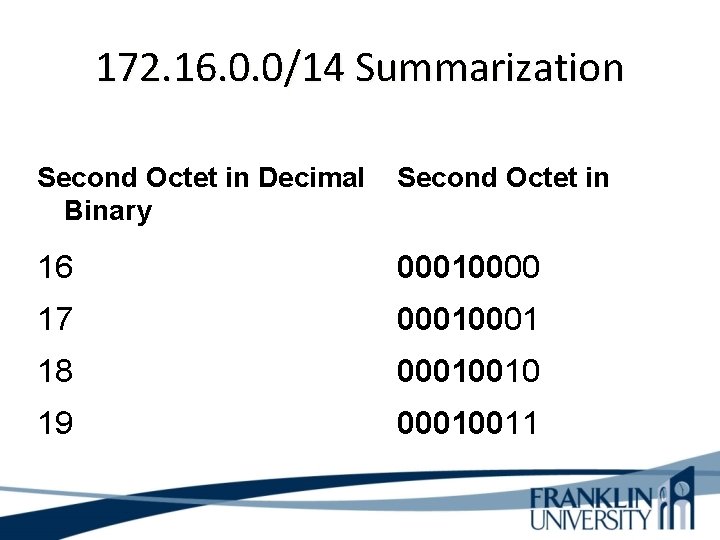
172. 16. 0. 0/14 Summarization Second Octet in Decimal Binary Second Octet in 16 00010000 17 0001 18 00010010 19 00010011

Private Addressing • 10. 0 – 10. 255 • 172. 16. 0. 0 – 172. 31. 255 • 192. 168. 0. 0 – 192. 168. 255

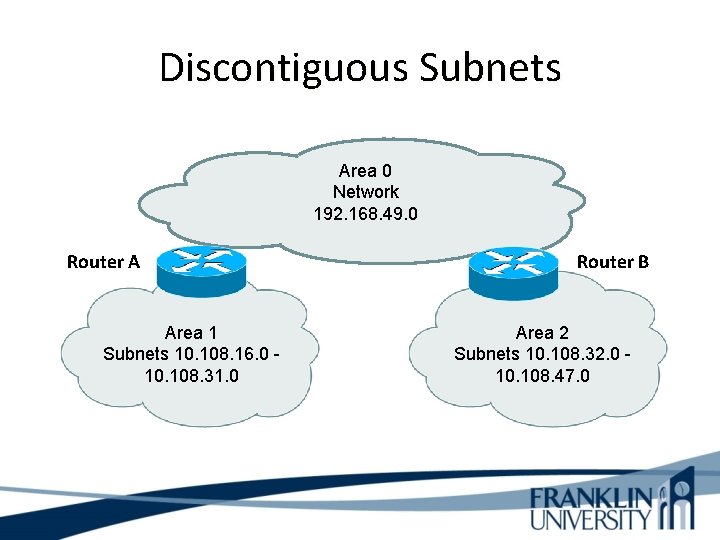
Discontiguous Subnets Area 0 Network 192. 168. 49. 0 Router A Area 1 Subnets 10. 108. 16. 0 10. 108. 31. 0 Router B Area 2 Subnets 10. 108. 32. 0 10. 108. 47. 0

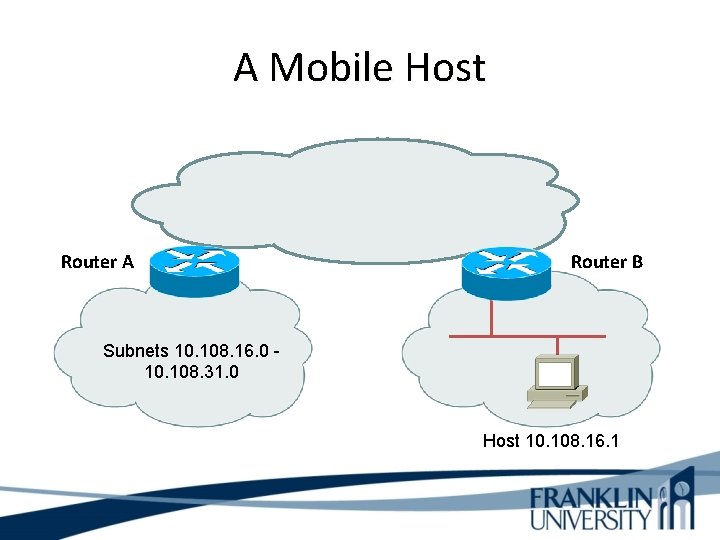
A Mobile Host Router A Router B Subnets 10. 108. 16. 0 10. 108. 31. 0 Host 10. 108. 16. 1

IPv 6 • A technology developed to overcome the limitations of the current standard, IPv 4 • Combines expanded addressing with a more efficient and feature-rich header to improve scaling • Satisfies the increasingly complex requirements of hierarchical addressing that IPv 4 does not support

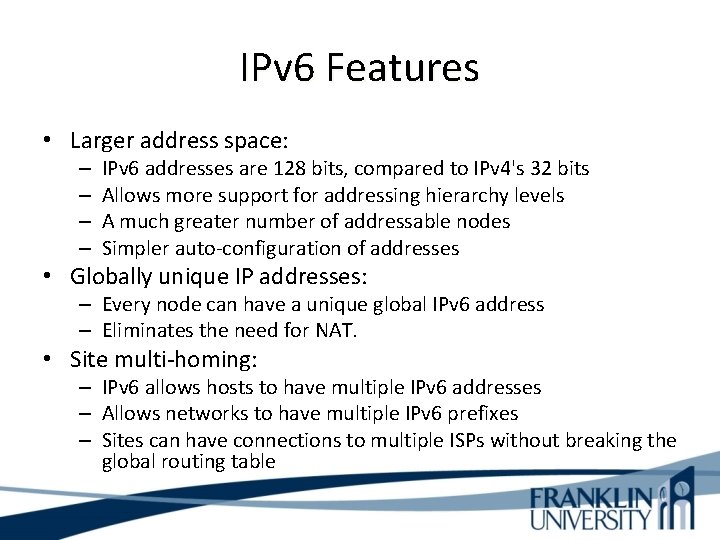
IPv 6 Features • Larger address space: – – IPv 6 addresses are 128 bits, compared to IPv 4's 32 bits Allows more support for addressing hierarchy levels A much greater number of addressable nodes Simpler auto-configuration of addresses • Globally unique IP addresses: – Every node can have a unique global IPv 6 address – Eliminates the need for NAT. • Site multi-homing: – IPv 6 allows hosts to have multiple IPv 6 addresses – Allows networks to have multiple IPv 6 prefixes – Sites can have connections to multiple ISPs without breaking the global routing table

IPv 6 Features (continued) • Header format efficiency: – A simplified header with a fixed header size makes processing more efficient. • Improved privacy and security: – IPsec is the IETF standard for IP network security, available for both IPv 4 and IPv 6. Although the functions are essentially identical in both environments, IPsec is mandatory in IPv 6 also has optional security headers. • Flow labeling capability: – A new capability enables the labeling of packets belonging to particular traffic flows for which the sender requests special handling, such as nondefault quality of service (Qo. S) or real-time service. • Increased mobility and multicast capabilities: – Mobile IPv 6 allows an IPv 6 node to change its location on an IPv 6 network and still maintain its existing connections. With Mobile IPv 6, the mobile node is always reachable through one permanent address. A connection is established with a specific permanent address assigned to the mobile node, and the node remains connected no matter how many times it changes locations and addresses

IPv 6 Address Format • The format is x: x: x, where x is a 16 -bit hexadecimal field – 2035: 0001: 2 BC 5: 0000: 087 C: 0000: 000 A • Leading 0 s within each set of four hexadecimal digits can be omitted, and a pair of colons (: : ) can be used, once within an address, to represent any number of successive 0 s. – 2035: 1: 2 BC 5: : 87 C: 0: A

IPv 6 Addresses • Link-local address: The host configures its own link-local address autonomously, using the link-local prefix FE 80: : 0/10 and a 64 -bit identifier for the interface, in an EUI-64 format. • Stateless autoconfiguration: A router on the link advertises—either periodically or at the host's request—network information, such as the 64 bit prefix of the local network and its willingness to function as a default router for the link. Hosts can automatically generate their global IPv 6 addresses by using the prefix in these router messages; the hosts do not need manual configuration or the help of a device such as a DHCP server. • Stateful using DHCP for IPv 6 (DHCPv 6): DHCPv 6 is an updated version of DHCP for IPv 4. DHCPv 6 gives the network administrator more control than stateless autoconfiguration and can be used to distribute other information, including the address of the DNS server. DHCPv 6 can also be used for automatic domain name registration of hosts using a dynamic DNS server. DHCPv 6 uses multicast addresses.

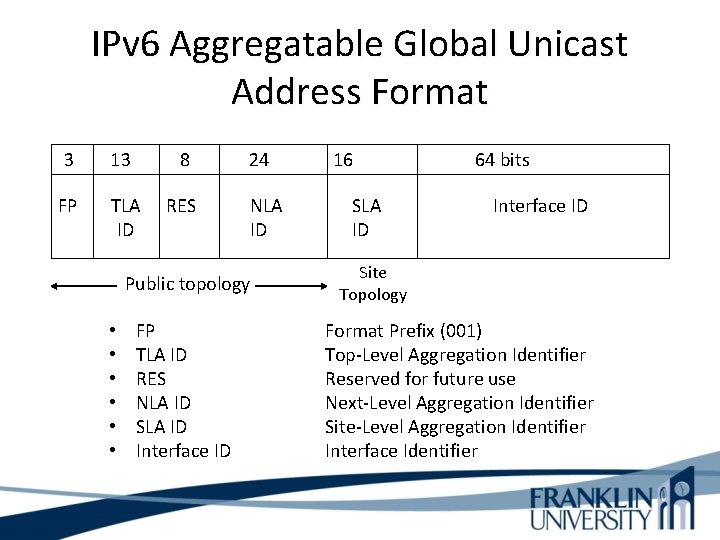
IPv 6 Aggregatable Global Unicast Address Format 3 13 8 FP TLA ID RES 24 NLA ID Public topology • • • FP TLA ID RES NLA ID SLA ID Interface ID 16 SLA ID 64 bits Interface ID Site Topology Format Prefix (001) Top-Level Aggregation Identifier Reserved for future use Next-Level Aggregation Identifier Site-Level Aggregation Identifier Interface Identifier

Upgrading to IPv 6 • Dual stack • Tunneling • Translation

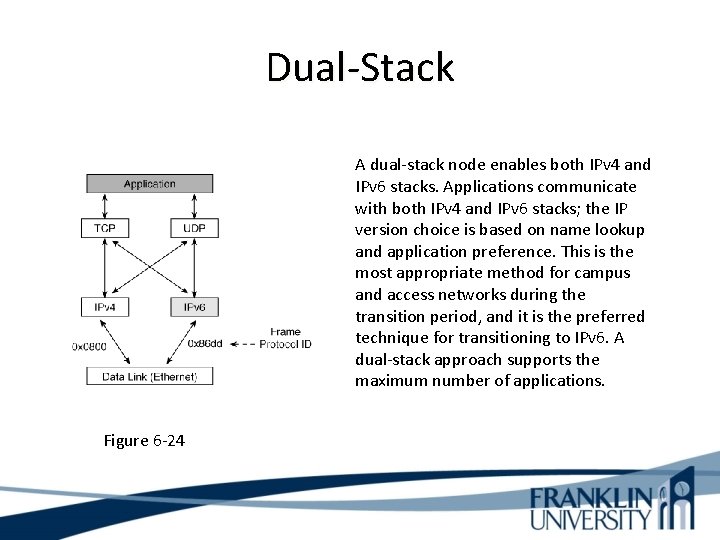
Dual-Stack A dual-stack node enables both IPv 4 and IPv 6 stacks. Applications communicate with both IPv 4 and IPv 6 stacks; the IP version choice is based on name lookup and application preference. This is the most appropriate method for campus and access networks during the transition period, and it is the preferred technique for transitioning to IPv 6. A dual-stack approach supports the maximum number of applications. Figure 6 -24

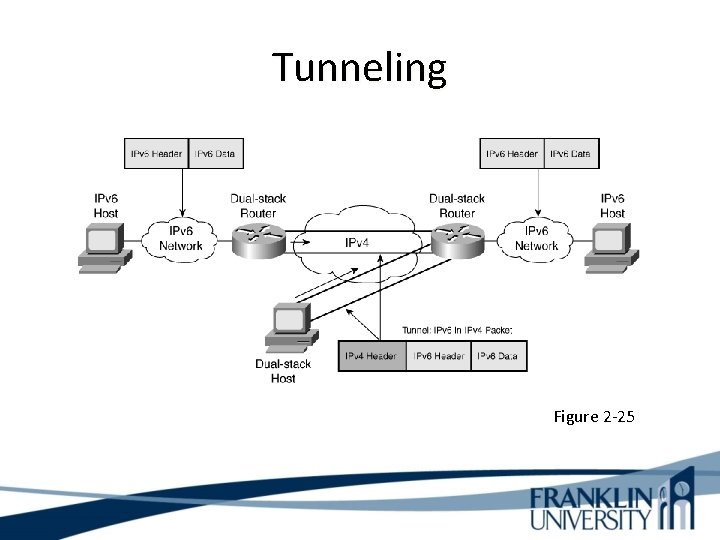
Tunneling Figure 2 -25

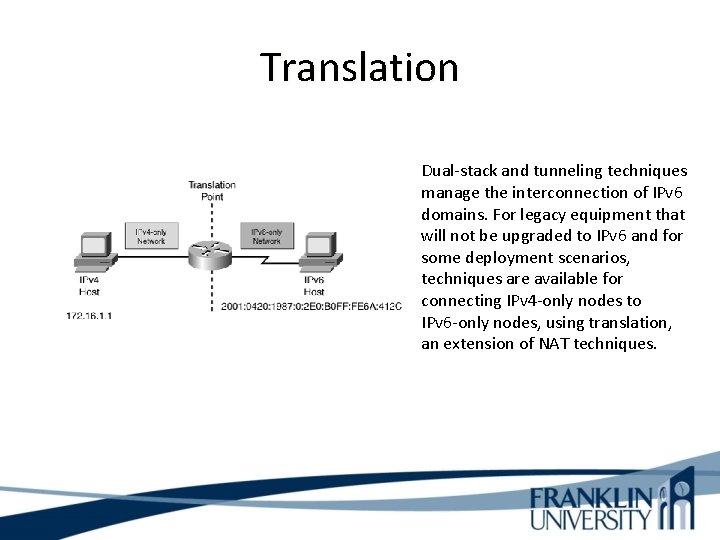
Translation Dual-stack and tunneling techniques manage the interconnection of IPv 6 domains. For legacy equipment that will not be upgraded to IPv 6 and for some deployment scenarios, techniques are available for connecting IPv 4 -only nodes to IPv 6 -only nodes, using translation, an extension of NAT techniques.

Guidelines for Assigning Names • Names should be – Short – Meaningful – Unambiguous – Distinct – Case insensitive • Avoid names with unusual characters – Hyphens, underscores, asterisks, and so on

Domain Name System (DNS) • Maps names to IP addresses • Supports hierarchical naming – example: frodo. rivendell. middle-earth. com • A DNS server has a database of resource records (RRs) that maps names to addresses in the server’s “zone of authority” • Client queries server – Uses UDP port 53 for name queries and replies – Uses TCP port 53 for zone transfers

DNS Details • Client/server model • Client is configured with the IP address of a DNS server – Manually or DHCP can provide the address • DNS resolver software on the client machine sends a query to the DNS server. Client may ask for recursive lookup.

DNS Recursion • A DNS server may offer recursion, which allows the server to ask other servers – Each server is configured with the IP address of one or more root DNS servers. • When a DNS server receives a response from another server, it replies to the resolver client software. The server also caches the information for future requests. – The network administrator of the authoritative DNS server for a name defines the length of time that a non-authoritative server may cache information.

Summary • Use a systematic, structured, top-down approach to addressing and naming • Assign addresses in a hierarchical fashion • Distribute authority for addressing and naming where appropriate • IPv 6 looms in our future

Review Questions • Why is it important to use a structured model for addressing and naming? • When is it appropriate to use IP private addressing versus public addressing? • When is it appropriate to use static versus dynamic addressing? • What are some approaches to upgrading to IPv 6?

This Week’s Outcomes • • IP Addressing Static and Dynamic Assignment IPv 6 IPv 4 to IPv 6 Transition Methods

Due this week • 5 -1 – Concept questions 4 • 1 -5 -1 – Network design project – Switches

Next week • Read chapters 7 in Top-Down Network Design • 6 -1 – Concept questions 5 • Franklin. Live session 7

Q&A • Questions, comments, concerns?