ITEC 350 Networks I Lecture 1 Hwajung Lee

![Why Computer Networks? ü Business Applications § [Goal 1] Resource Sharing • To connect Why Computer Networks? ü Business Applications § [Goal 1] Resource Sharing • To connect](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-4.jpg)
![§ [Goal 2] Communication Medium • Electronic mail (e-mail) • Shared resources (ex: shared § [Goal 2] Communication Medium • Electronic mail (e-mail) • Shared resources (ex: shared](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-5.jpg)
![§ [Goal 3] Electronic Commerce (e-commerce) • To do business electronically with other companies. § [Goal 3] Electronic Commerce (e-commerce) • To do business electronically with other companies.](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-6.jpg)
![ü Home Applications § [Goal 1] Access to remote information • Newspapers, Digital library ü Home Applications § [Goal 1] Access to remote information • Newspapers, Digital library](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-7.jpg)
![ü Home Applications (cont. ) § [Goal 3] Interactive entertainment • Video on demand, ü Home Applications (cont. ) § [Goal 3] Interactive entertainment • Video on demand,](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-8.jpg)
![ü Mobile Network Users § [Goal] To have a portable office • Cellular phone, ü Mobile Network Users § [Goal] To have a portable office • Cellular phone,](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-9.jpg)














- Slides: 56

ITEC 350 Networks I Lecture 1 Hwajung Lee

References ü Panko, “Business Data Networks and Telecommunications, ” 4 th Edition, Prentice Hall, 2003. ü Tanenbaum, “Computer Networks, ” 4 th Edition, Prentice Hall PTR, 2003. ü Wells, “Guide to Linux Networking and Securitity, ” Course Technology, 2003. ü Minasi, “Mastering Windows Server 2003, ” SYBEX Inc. , 2003.

What is Computer Networks? ü A collection of autonomous computers interconnected by a single technology § Interconnected via: • • • Copper wire Fiber optics Microwaves Infrared Communication satellites, etc.
![Why Computer Networks ü Business Applications Goal 1 Resource Sharing To connect Why Computer Networks? ü Business Applications § [Goal 1] Resource Sharing • To connect](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-4.jpg)
Why Computer Networks? ü Business Applications § [Goal 1] Resource Sharing • To connect isolated computer and information to be able to extract and correlate information about the entire company. • To make all programs, equipment (ex: printers, scanners, and CD burners), and especially data available to anyone on the network without regard to the physical location of the resource an the user.
![Goal 2 Communication Medium Electronic mail email Shared resources ex shared § [Goal 2] Communication Medium • Electronic mail (e-mail) • Shared resources (ex: shared](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-5.jpg)
§ [Goal 2] Communication Medium • Electronic mail (e-mail) • Shared resources (ex: shared hard driver) • Videoconferencing, a shared virtual blackboard
![Goal 3 Electronic Commerce ecommerce To do business electronically with other companies § [Goal 3] Electronic Commerce (e-commerce) • To do business electronically with other companies.](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-6.jpg)
§ [Goal 3] Electronic Commerce (e-commerce) • To do business electronically with other companies. (ex: order the parts of a product from a variety of suppliers) • To do business with consumers over the Internet.
![ü Home Applications Goal 1 Access to remote information Newspapers Digital library ü Home Applications § [Goal 1] Access to remote information • Newspapers, Digital library](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-7.jpg)
ü Home Applications § [Goal 1] Access to remote information • Newspapers, Digital library § [Goal 2] Person-to-person communication • Email, Instant messaging, Chat room, Worldwide newsgroups • Peer-to-peer communication (ex: Napster) • Internet phone, Internet video phone, Internet radio, Telelearning
![ü Home Applications cont Goal 3 Interactive entertainment Video on demand ü Home Applications (cont. ) § [Goal 3] Interactive entertainment • Video on demand,](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-8.jpg)
ü Home Applications (cont. ) § [Goal 3] Interactive entertainment • Video on demand, Interactive live television show, Multiperson real-time simulation games – possibly with worldwide shared virtual reality. § [Goal 4] Electronic commerce • Home shopping, Electric flea markets, On-line auctions
![ü Mobile Network Users Goal To have a portable office Cellular phone ü Mobile Network Users § [Goal] To have a portable office • Cellular phone,](https://slidetodoc.com/presentation_image_h/37f408587bc531b74d09e7b0fb60c991/image-9.jpg)
ü Mobile Network Users § [Goal] To have a portable office • Cellular phone, PDA, Military use, Wireless sensor networks, Mobile-commerce, Wearable wireless computers Combinations of wireless networks and mobile computing.

Network Types Based on Roles ü Terminal Connection

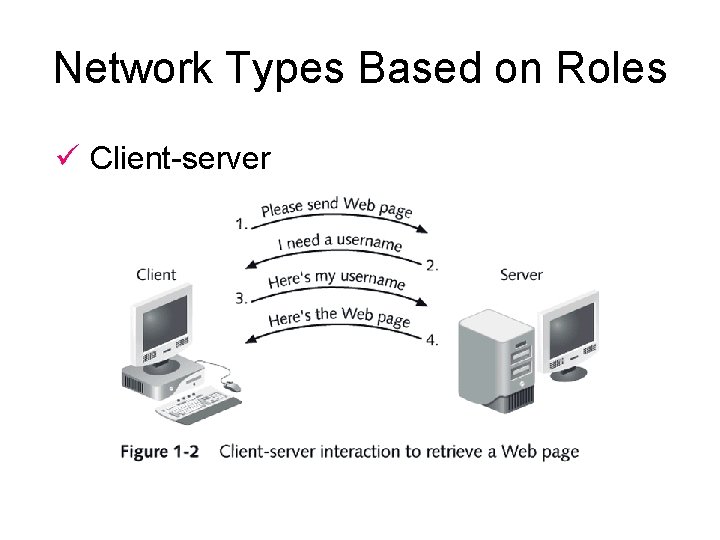
Network Types Based on Roles ü Client-server

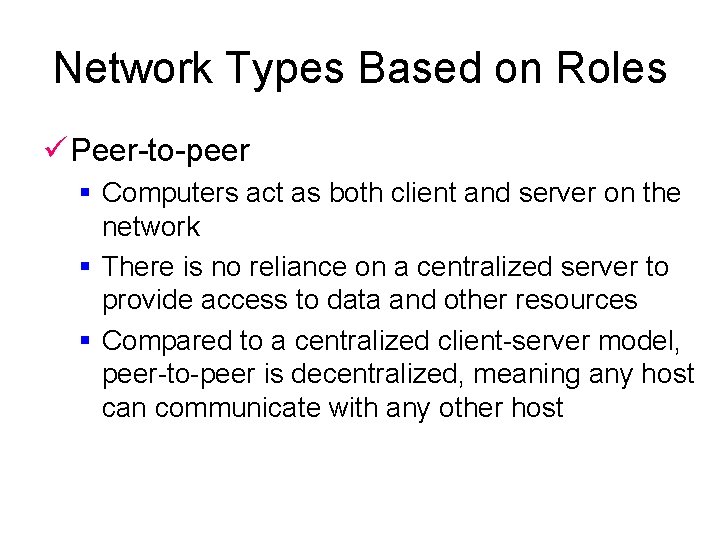
Network Types Based on Roles ü Peer-to-peer § Computers act as both client and server on the network § There is no reliance on a centralized server to provide access to data and other resources § Compared to a centralized client-server model, peer-to-peer is decentralized, meaning any host can communicate with any other host

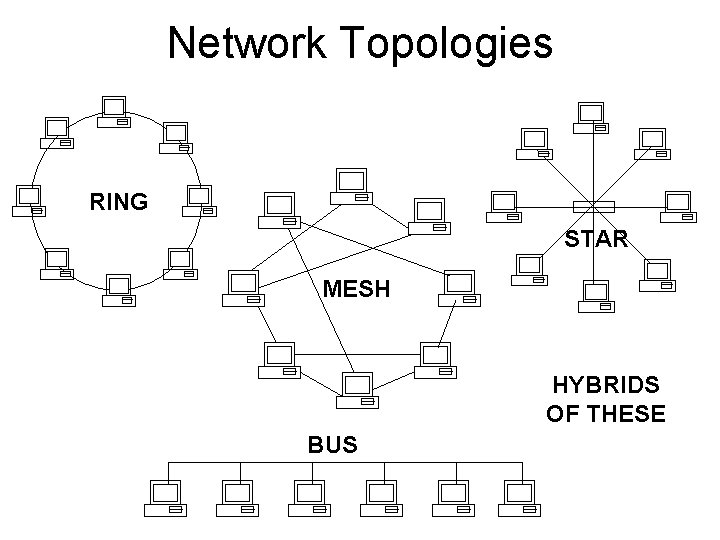
Network Topologies RING STAR MESH HYBRIDS OF THESE BUS

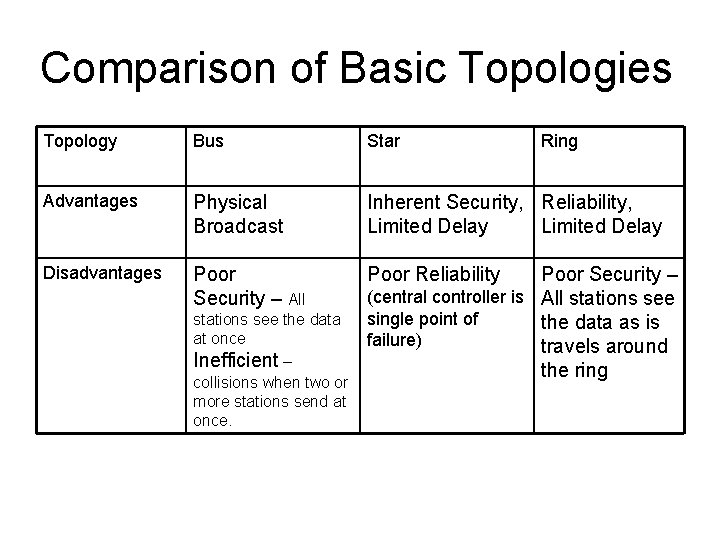
Comparison of Basic Topologies Topology Bus Star Advantages Physical Broadcast Inherent Security, Reliability, Limited Delay Disadvantages Poor Security – All Poor Reliability stations see the data at once Inefficient – collisions when two or more stations send at once. Ring Poor Security – (central controller is All stations see single point of the data as is failure) travels around the ring

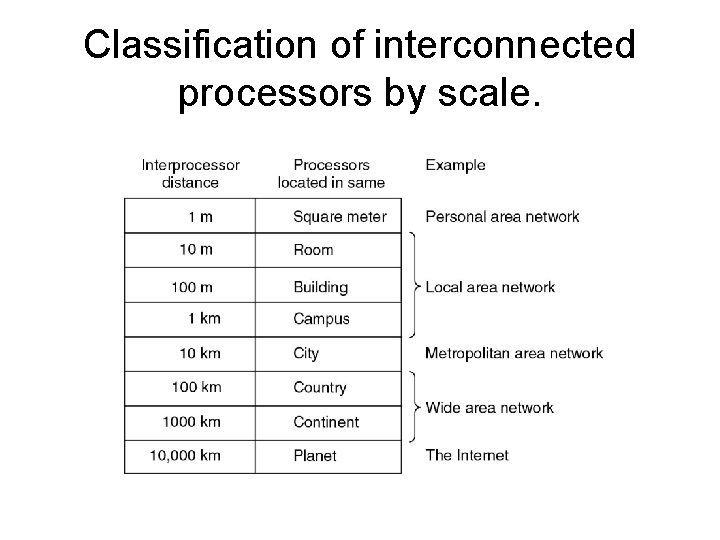
Classification of interconnected processors by scale.

ü Personal Area Network (PAN) § A person’s body or desk area

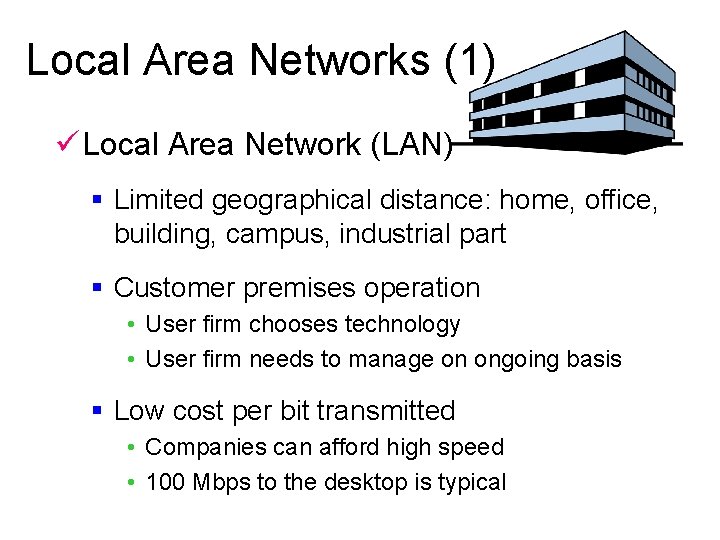
Local Area Networks (1) ü Local Area Network (LAN) § Limited geographical distance: home, office, building, campus, industrial part § Customer premises operation • User firm chooses technology • User firm needs to manage on ongoing basis § Low cost per bit transmitted • Companies can afford high speed • 100 Mbps to the desktop is typical

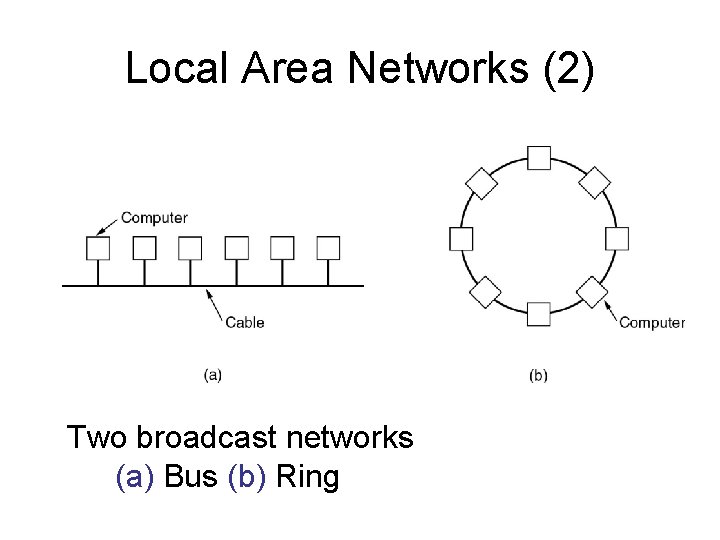
Local Area Networks (2) Two broadcast networks (a) Bus (b) Ring

Local Area Networks (3) ü Ethernet § Most popular LAN Architecture of the original Ethernet.

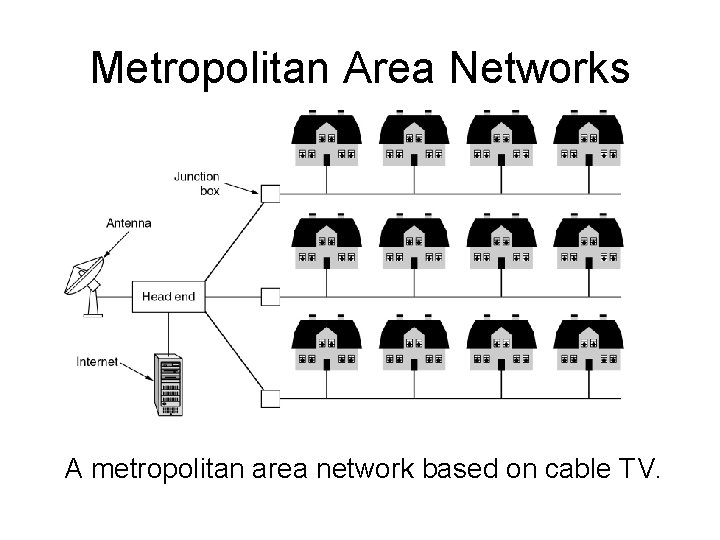
Metropolitan Area Networks ü Metropolitan Area Network (MAN) § Single urban area (city and its suburbs) § Faster than long-distance WANs § Still slower than LANs

Metropolitan Area Networks A metropolitan area network based on cable TV.

ü Wide Area Network (WAN) WAN § To link sites • Long distances § Requires the use of carriers to provide service • Limited and complex choices but carrier manages § High cost per bit transmitted • Companies cannot afford high speeds • Usually low speed (56 kbps to a few megabits per second)

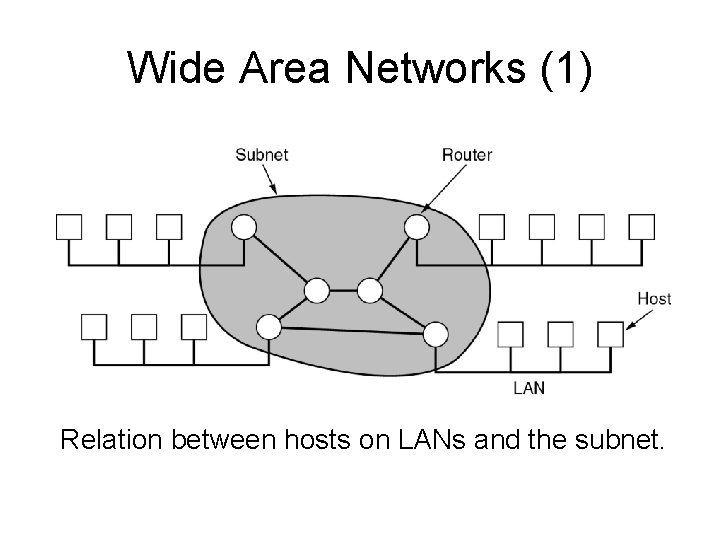
Wide Area Networks (1) Relation between hosts on LANs and the subnet.

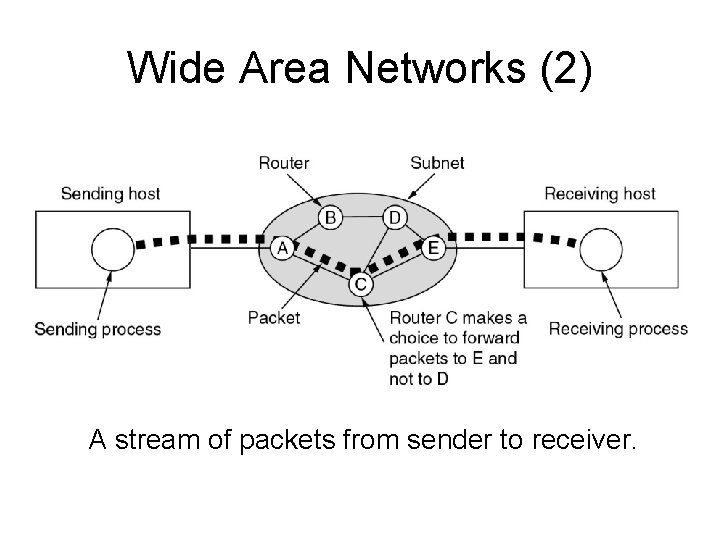
Wide Area Networks (2) A stream of packets from sender to receiver.

Wireless Networks ü Categories of wireless networks: § System interconnection § Wireless LANs • Speed: Upto about 50 Mbps • Distance: Tens of meters § Wireless WANs (ex: cellular system) • Speed: below 1 Mbps • Distance: Kilometers

Wireless Networks (2) (a) Bluetooth configuration (b) Wireless LAN

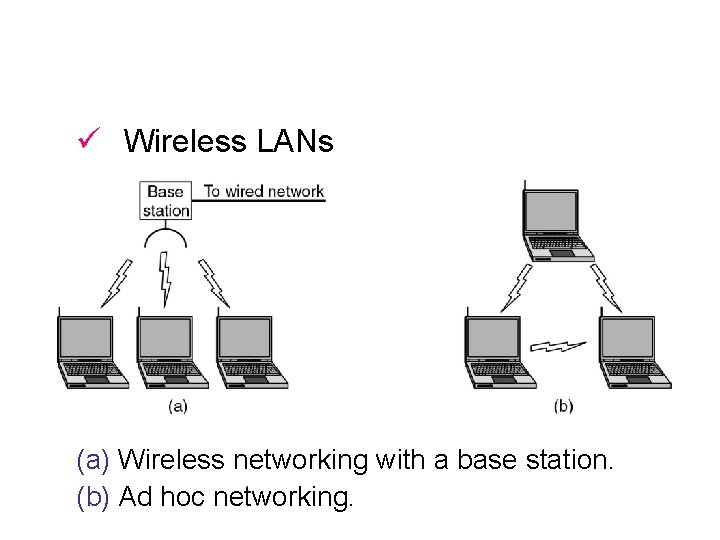
ü Wireless LANs (a) Wireless networking with a base station. (b) Ad hoc networking.

ü Standard for Wireless LANs IEEE 802. 11 network.

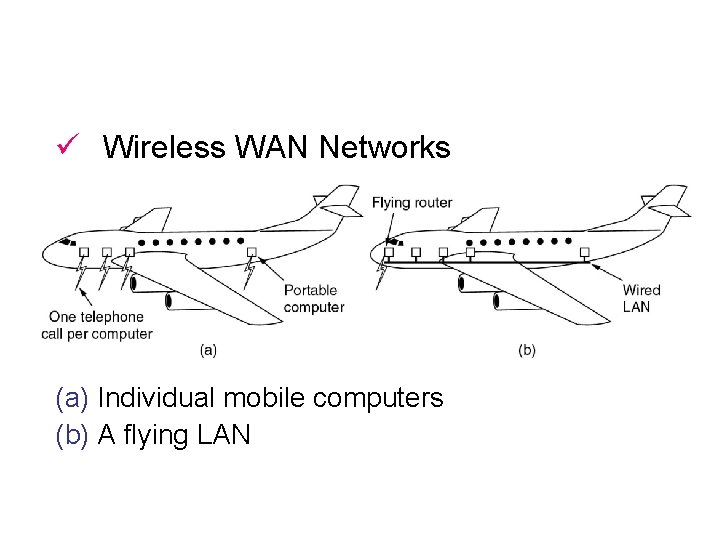
ü Wireless WAN Networks (a) Individual mobile computers (b) A flying LAN

Network Software ü Protocol Hierarchies ü Design Issues for the Layers ü Connection-Oriented and Connectionless Services ü Service Primitives ü The Relationship of Services to Protocols

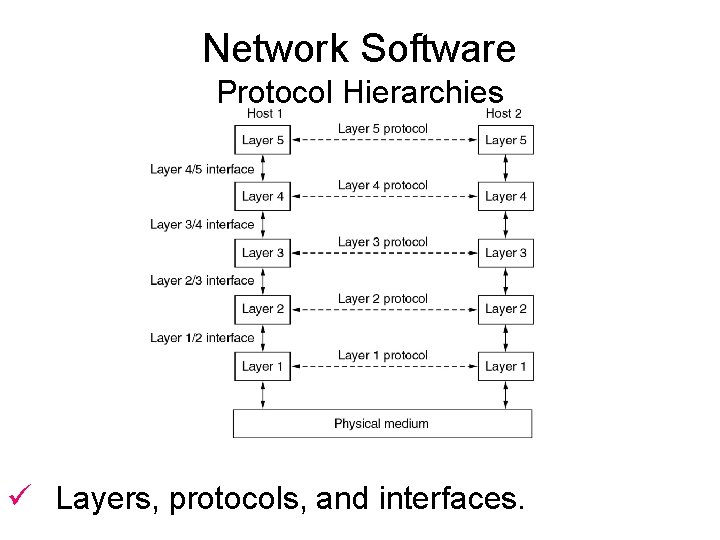
Network Software Protocol Hierarchies ü Layers, protocols, and interfaces.

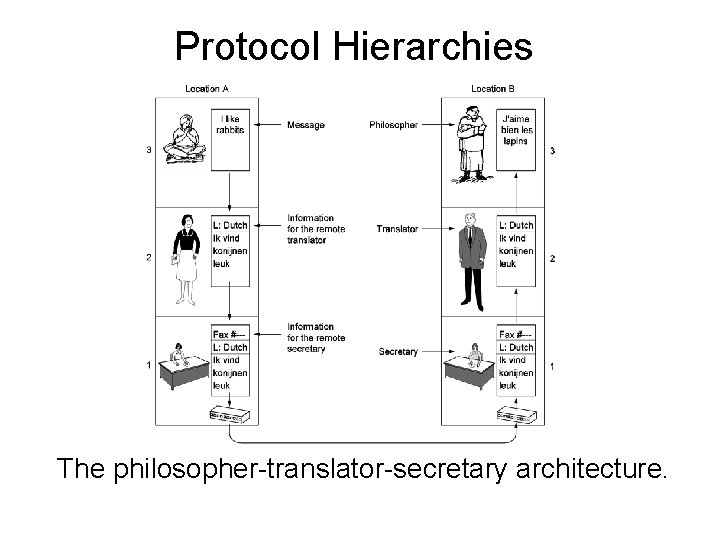
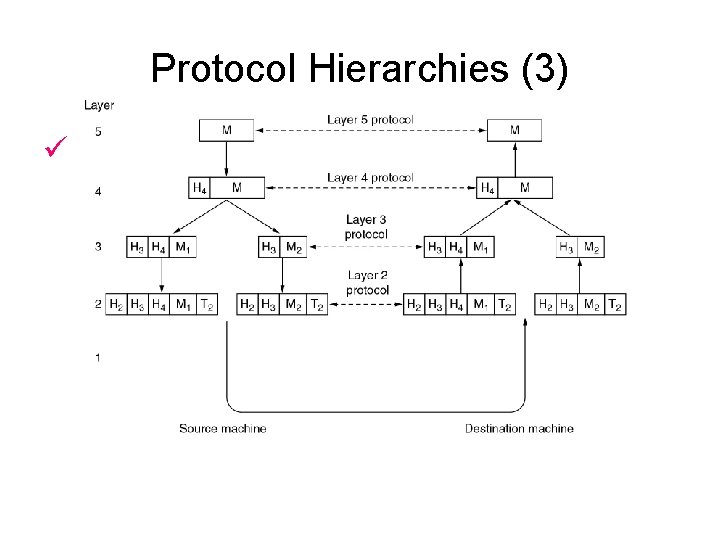
Protocol Hierarchies The philosopher-translator-secretary architecture.

Protocol Hierarchies (3) ü Example information flow supporting virtual communication in layer 5.

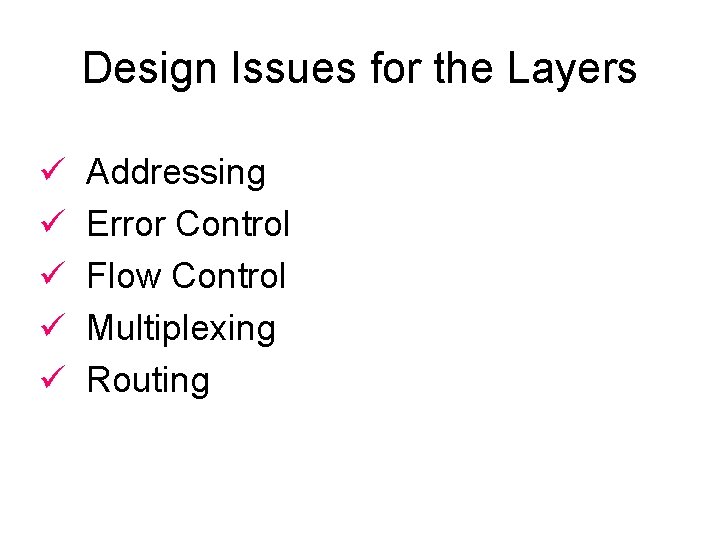
Design Issues for the Layers ü ü ü Addressing Error Control Flow Control Multiplexing Routing

Connection-Oriented and Connectionless Services ü The software used to maintain each protocol is often called a protocol stack ü Transport layer protocols can be: § Connectionless, or stateless, which sends each packet without regard to whether any other packet was received by the destination computer (implementation: packet switching, UDP) § Connection oriented, or stateful, which maintains information about which packets have been correctly received by the destination computer (implm. : circuit-switching, TCP)

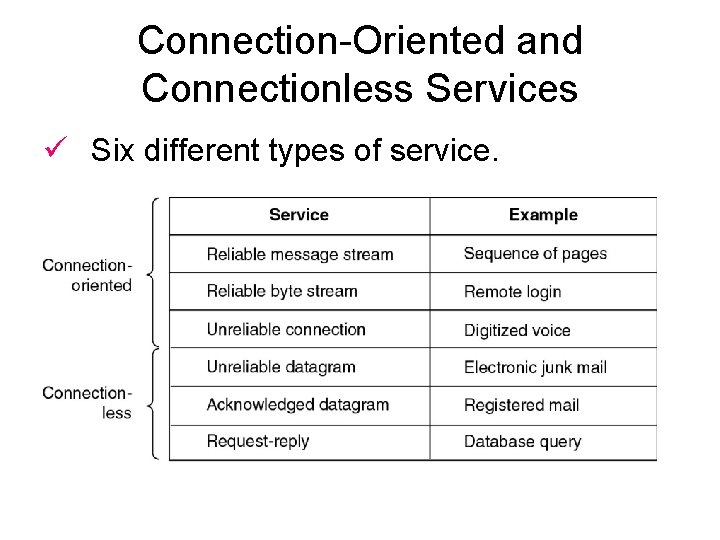
Connection-Oriented and Connectionless Services ü Six different types of service.

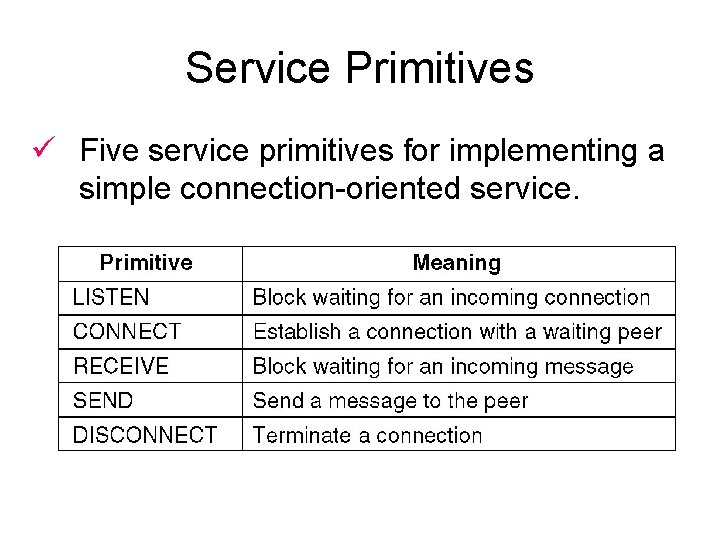
Service Primitives ü Five service primitives for implementing a simple connection-oriented service.

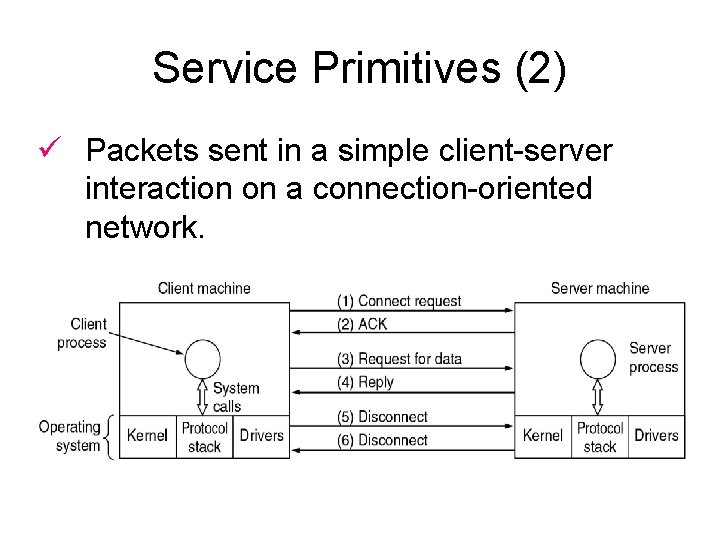
Service Primitives (2) ü Packets sent in a simple client-server interaction on a connection-oriented network.

Services to Protocols Relationship The relationship between a service and a protocol.

Why Standard or Reference Model? ü Consumer § Easy to select a product which is compatible with other equipments. ü Supplier § Minimize risk when it develops new technologies.

Reference Models ü The OSI Reference Model § § ISO (International Organization for Standardization) OSI (Open Systems Interconnection) Model ü The TCP/IP Reference Model § § TCP (Transmission Control Protocol) IP (Internet Protocol) ü A Critique of the OSI Model and Protocols ü A Critique of the TCP/IP Reference Model

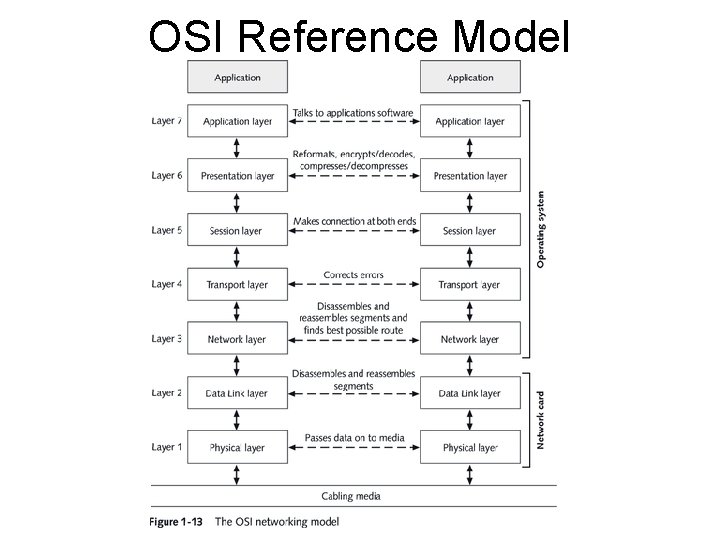
OSI Reference Model

OSI Reference Model

The TCP/IP reference model

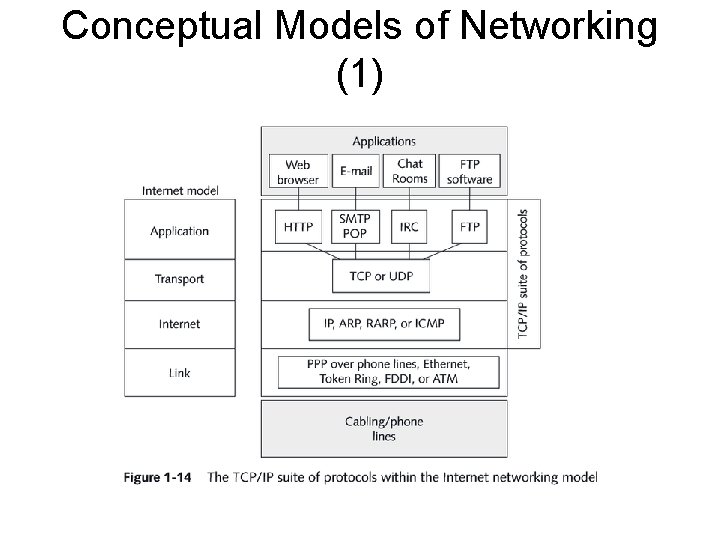
Conceptual Models of Networking (1)

Acronyms ü POP (Post Office Protocol) ü FTP (File Transfer Protocol) ü UDP (User Datagram Protocol) ü TCP (Transmission Control Protocol) ü SMTP (Simple Mail Transport Protocol) ü HTTP (Hypertext Transport Protocol) ü DNS (Domain Name Service) ü ICMP (Internet Control Message Protocol) ü PPP (Point-to-Point Protocol) ü SATNET (Satellite Networks) ü IRC (Internet Relay Chat)

A Critique of the OSI Model and Protocols ü Why OSI did not take over the world § § § Bad timing Bad implementations Bad politics

Bad Timing ü The apocalypse of the two elephants.

A Critique of the TCP/IP Reference Model ü Problems: § § § Service, interface, and protocol not distinguished Not a general model Host-to-network “layer” not really a layer No mention of physical and data link layers Minor protocols deeply entrenched, hard to replace

Networking Technologies ü Ethernet § Most widely used technology § Three variation of Ethernet based on transmission speed, or bandwidth ü Token-ring § Uses a token to identify which computer on the network has the right to transmit data § Not as fast as Ethernet, and may be more expensive

Networking Technologies ü Fiber Distributed Data Interface (FDDI) § Reliable, but slower and costlier than Ethernet ü Arcnet § Reliable, but slower token-passing technology ü Asynchronous Transfer Mode (ATM) § high-speed, very reliable and very expensive used for Internet backbones ü Wireless LAN (WLAN) § No cables used to connect nodes to the network § Data is transmitted via radio signals of infrared

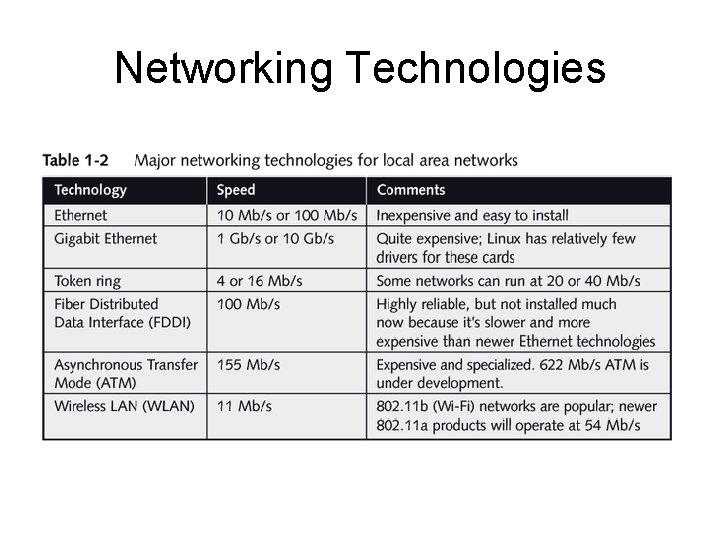
Networking Technologies

Network Standardization ü Who’s Who in the Telecommunications World ü Who’s Who in the International Standards World ü Who’s Who in the Internet Standards World

ITU (International Telecommunication Union) ü Main sectors • • • Radiocommunications Telecommunications Standardization Development ü Classes of Members • • National governments Sector members Associate members Regulatory agencies

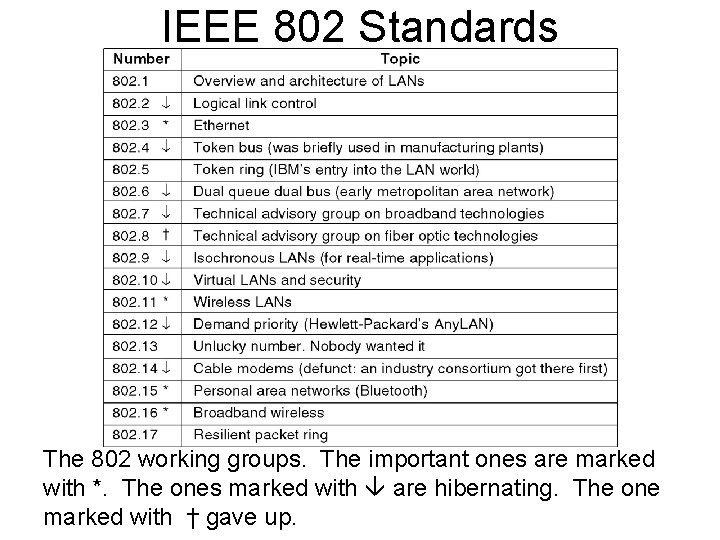
IEEE 802 Standards The 802 working groups. The important ones are marked with *. The ones marked with are hibernating. The one marked with † gave up.

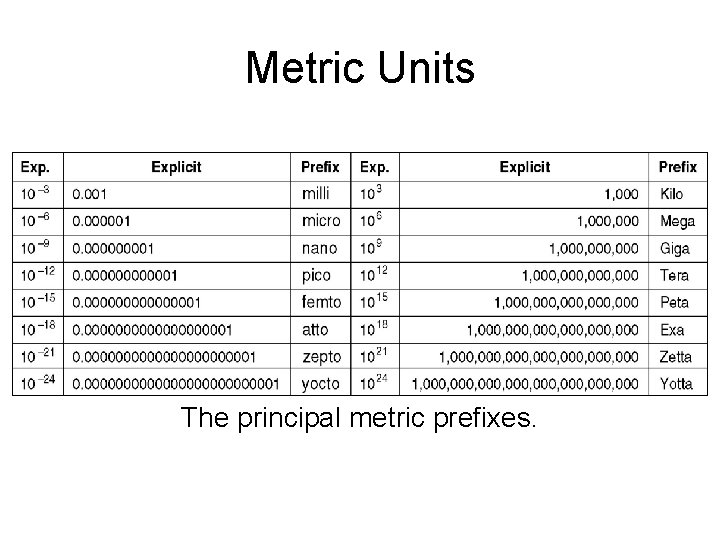
Metric Units The principal metric prefixes.
 Itec 350
Itec 350 Hwajung
Hwajung Lee pipes
Lee pipes Hwajung
Hwajung 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Virtual circuit approach
Virtual circuit approach Backbone networks in computer networks
Backbone networks in computer networks Itec 3220
Itec 3220 Itec
Itec Itec 1000
Itec 1000 Nic borg
Nic borg Itec 4010
Itec 4010 First cut design class diagram
First cut design class diagram Itec 3220
Itec 3220 Itec
Itec Itec 1000
Itec 1000 Qu es
Qu es Itec 3220
Itec 3220 Itec 1000
Itec 1000 Exponent mantissa
Exponent mantissa Itec 1000
Itec 1000 Cs itec
Cs itec Projet itec terminale sti2d
Projet itec terminale sti2d Itec 1010
Itec 1010 Gestin itec
Gestin itec Itec irrigation controller
Itec irrigation controller Itec 1000
Itec 1000 Bectra
Bectra Itec 3010
Itec 3010 Itec software
Itec software Itec exam results
Itec exam results Ims-350
Ims-350 Nt$1 350 to usd
Nt$1 350 to usd Cse350
Cse350 250 nearest 100
250 nearest 100 Softeng 350
Softeng 350 Mechanics of materials
Mechanics of materials Softeng 350
Softeng 350 Fincoid 350
Fincoid 350 Lifebreath 350 dcs
Lifebreath 350 dcs If a runner exerts 350 j of work
If a runner exerts 350 j of work Xkcd 350
Xkcd 350 Csce 350
Csce 350 Comp 350
Comp 350 Cisco aironet 350 driver
Cisco aironet 350 driver 100 tl nin yüzde 25 i kaçtır
100 tl nin yüzde 25 i kaçtır Softeng 350
Softeng 350 Jarak yogyakarta malang 350 km
Jarak yogyakarta malang 350 km Softeng 350
Softeng 350 Eli 350
Eli 350 Cis 350
Cis 350 Alvear y cardeza 350
Alvear y cardeza 350 Dropbox csce
Dropbox csce Diamond products pc6000
Diamond products pc6000 Ptt-350
Ptt-350 Bt 350 professional
Bt 350 professional 350 forts in maharashtra
350 forts in maharashtra