IDS Intrusion Detection System C Edward Chow cs






![Rule option: Content content: [!] “<content string>”; n n n It allows the user Rule option: Content content: [!] “<content string>”; n n n It allows the user](https://slidetodoc.com/presentation_image_h/809cb3ee66d15399b7a6b9322039935b/image-12.jpg)


![Detection Results n #0 -(3 -1) [snort] WEB-IIS cmd. exe access 2003 -04 -14 Detection Results n #0 -(3 -1) [snort] WEB-IIS cmd. exe access 2003 -04 -14](https://slidetodoc.com/presentation_image_h/809cb3ee66d15399b7a6b9322039935b/image-17.jpg)













- Slides: 35

IDS: Intrusion Detection System C. Edward Chow cs 691 1 chow

Outline of The Talk n n n Definition, Concepts Network Intrusion Detection: Snort A 2 D 2 (Integrating NIDS with Firewall) Host Intrusion Detection: Tripwire References: l Chapter 25 Intrusion Detection, by Matt Bishop. l Chapter 7 Network Intrusion Detection, Inside Network Perimeter Security, by Northcutt et al (reserved in UCCS Library) l NIST IDS Survey: http: //cs. uccs. edu/~chow/pub/ids/NISTsp 800 -31. pdf l A 2 D 2: http: //cs. uccs. edu/~chow/pub/master/acearns/doc/ l http: //cs. uccs. edu/~chow/pub/ids/2001_vigna_kemmerer_blix_raid 01. p df l Snort: http: //www. snort. org/ l Tripwire: http: //www. tripwire. org/ cs 691 2 chow

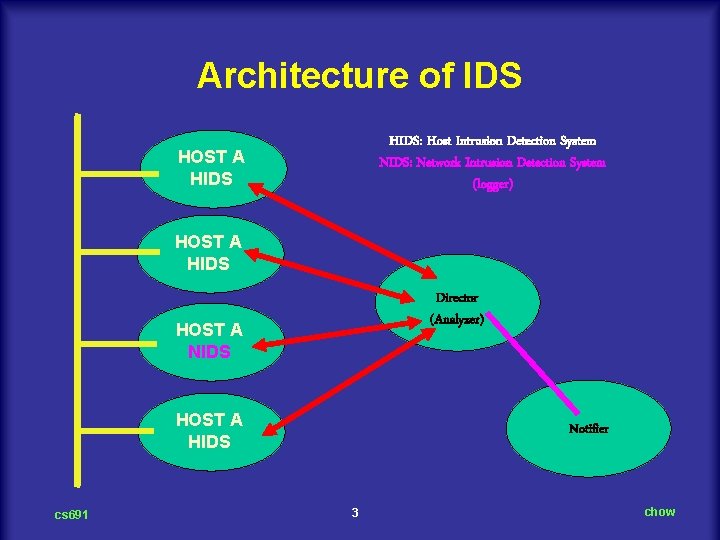
Architecture of IDS HIDS: Host Intrusion Detection System NIDS: Network Intrusion Detection System (logger) HOST A HIDS Director (Analyzer) HOST A NIDS HOST A HIDS cs 691 Notifier 3 chow

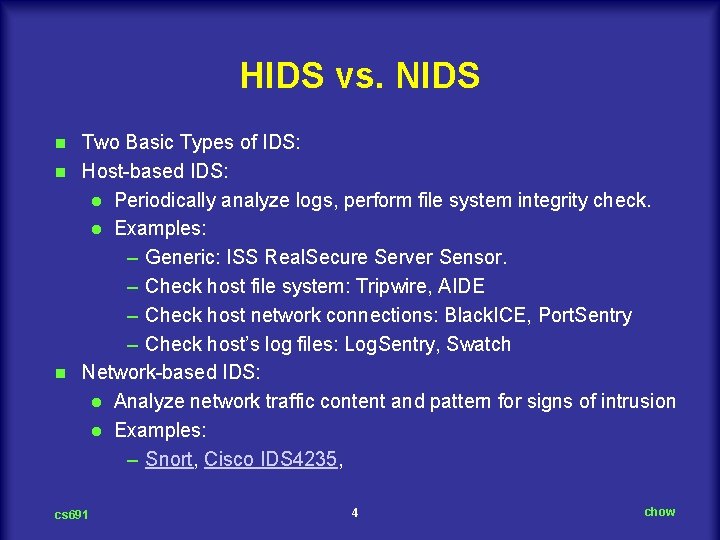
HIDS vs. NIDS Two Basic Types of IDS: n Host-based IDS: l Periodically analyze logs, perform file system integrity check. l Examples: – Generic: ISS Real. Secure Server Sensor. – Check host file system: Tripwire, AIDE – Check host network connections: Black. ICE, Port. Sentry – Check host’s log files: Log. Sentry, Swatch n Network-based IDS: l Analyze network traffic content and pattern for signs of intrusion l Examples: – Snort, Cisco IDS 4235, n cs 691 4 chow

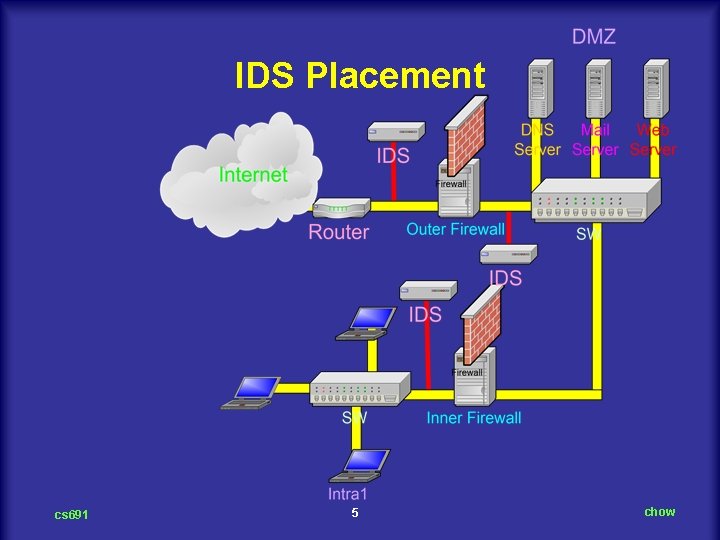
IDS Placement cs 691 5 chow

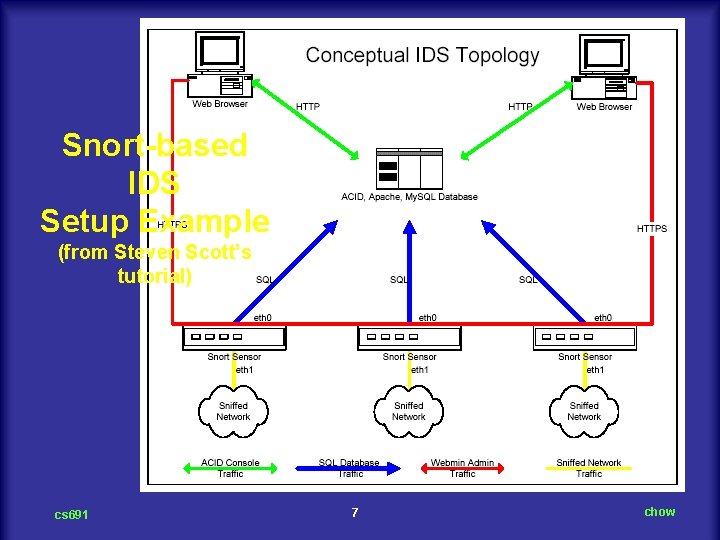
Snort n n n A popular network intrusion public domain package, available on www. snort. org. It allows the user to specify a set of rules which specifies the pattern in the packets, and the corresponding actions (typically just an alert msg) for matched packets. It also allows the user to create their own plug-in for additional detection that is not available with default pattern matching. For example, the subnet flooding, it requires modification of preprocessing step. It was used by many other packages and products. On snort download site, installation steps are given for integrating snort with mysql, apache, webmin, and ACID for easy web-based access and display of the intrusion instance, statistics, and related intrusion event databases, such as CVE, arach. NIDS. See http: //www. snort. org/docs/snort-rh 7 -mysql-ACID-1 -5. pdf for more details. cs 691 6 chow

Snort-based IDS Setup Example (from Steven Scott’s tutorial) cs 691 7 chow

Basic Snort Usage n Snort has three main modes: l Sniffer mode: read packets and display on console. – E. g. , >Snort -dev – v: verbose; d: dump application data; e: extensive l Packet Logger: read packets and log to the disk. – E. g. , > snort –dev –l. /log –h 192. 168. 1. 0/24 – l: log, h: only capture packets relative to the host l NIDS: analyze packets and matched against user defined rules and perform actions. – E. g. , > snort –dev –l. /log –c snort. conf – add –D will have snort run as daemon. – -A [fast | full | unsock | non] – -b for binary (tcpdump) format; faster. Use –r snort. og to read it back for offline analysis. – -o: change the normal (alert pass log rules) processing order to (pass alert log). – You can use SMB alert. That use smbclient to send Win. Popup alert msg to window machines. – Use –O for (obsuscates) the ip addresses in log file for hiding IP addresses when sharing with others the logs. cs 691 8 chow

/etc/snort. conf Snort read the snort. conf file for the default variables, additional pre/post processing plug-in (if any), output specification (to a mysql for example), and a set of rule files. For example, http: //cs. uccs. edu/~chow/pub/snort. conf output database: log, mysql, user=snort password=xxxx dbname=snort host=localhost include bad-traffic. rules include exploit. rules include scan. rules include finger. rules include ftp. rules include telnet. rules include rpc. rules include rservices. rules include dos. rules include dns. rules n cs 691 9 chow

Snort Rule Syntax Most rules written in single line. If multiple line use Each snort rule has two logical section: rule header and rule options. alert icmp $EXTERNAL_NET any <> $HOME_NET any (msg: "DDOS Stacheldraht agent->handler (skillz)"; content: "skillz"; itype: 0; icmp_id: 6666; reference: url, staff. washington. edu/dittrich/misc/stacheldraht. analysis; classtype: attempted-dos; sid: 1855; rev: 2; ) alert any -> 192. 168. 1. 0/24 any (flags: A; ack: 0; msg: “NMAP TCP ping”; ) # nmap send TCP ACK pkt with ack field set to 0 alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-IIS cmd. exe access"; flow: to_server, established; content: "cmd. exe"; nocase; classtype: web-application-attack; sid: 1002; rev: 5; ) n Rule header contains action, protocol, source (IPaddr/port), direction, destination (IPaddr/port) n Rule option contains alert msgs, info on which parts of packet to be inspected. n -> and <> are the only two direction operators. n n cs 691 10 chow

Snort Rule Syntax n Var: <name> <value> n n n Use $<variable> to reference them later. alert tcp $EXTERNAL_NET any $HOME_LAN any (flags: S; msg: “SYN packet”; ) Rule Actions: l Alert l Log l Pass (ignore the packet) l Activate (alert then turn on another dynamic rule (being phase out) l Dynamic– remain idle until activated by an activeate rule, then act as a log rule. You can also define your own rule types. Then use it as rule actioin. ruletype redalert { type alert output alert_syslog LOG_AUTH LOG_ALERT output database: log, mysql, user=snort dbname=snort host=localhost } n n var: EXTERNAL_NET [128. 198. 160. 0/19, 128. 198. 61. 0/26] var: HOME_LAN [192. 168. 0. 0/24, 10. 1. 1, 0/24] var NON_WIRELESS !128. 198. 61. 128/25 # use ! for negative operator for specifying the CIDR address not within a range. cs 691 11 chow
![Rule option Content content content string n n n It allows the user Rule option: Content content: [!] “<content string>”; n n n It allows the user](https://slidetodoc.com/presentation_image_h/809cb3ee66d15399b7a6b9322039935b/image-12.jpg)
Rule option: Content content: [!] “<content string>”; n n n It allows the user to set rules that search for specific content in packet payload and trigger response based on the data. Case sensitive. Can be mixed text and binary. Use | to specify the byte code (hexadecimal number). ! For negation; nocase to make case-insensitive matching. Examples: l Alert tcp any -> 192. 168. 1. 0/24 143 (content: “|90 CB C 0 FF FFFF|/bin/sh”; msg: “IMAP buffer overflow!”) l Alert tcp any -> 192. 168. 1. 0/24 21 (content: !”GET”; depth: 3; nocase; dsize: >100; msg: “Long Non-Get FTP command!”) l Dsize: payload size. Related IMAP buffer overflow, http: //www. securityfocus. com/bid/130/discussion/ cs 691 12 chow

Rule option: offset and depth n n n Offset: < number> Specify the number of bytes to skip before starting pattern matching. Depth: <number> Set maximum search depth for content pattern match. alert tcp any -> $HLAN 80 (content: “cmd. exe”; offset: 3; depth: 22: msg: “com. exe attack”; ) cs 691 13 chow

Rule option: sid & flow n n n n Sid specifies unique snort rule. <100 reserved for future use. 100 -1, 000 rule included in snort distirbution. >1, 000 for local rule usage. Flow: use in conjunction with TCP stream reassembly. Option: to_server (client request), to client (server response), from_client, from_server. E. g. , alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-IIS cmd. exe access"; flow: to_server, established; content: "cmd. exe"; nocase; classtype: web-applicationattack; sid: 1002; rev: 5; ) cs 691 14 chow

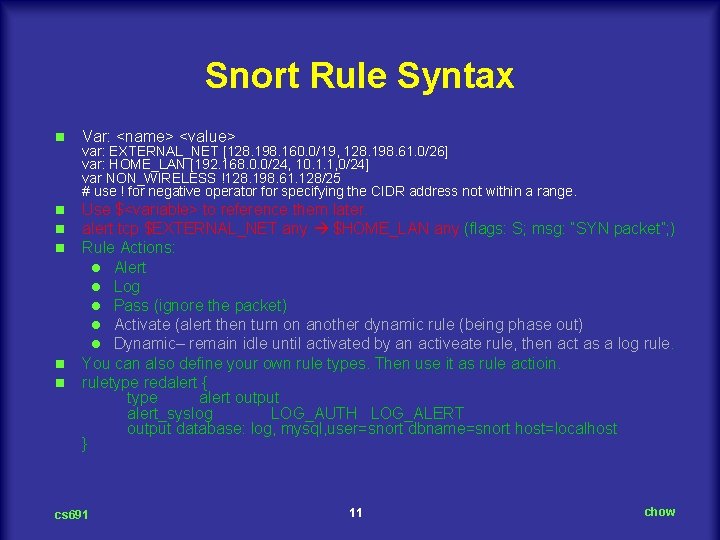
cs 691 15 chow

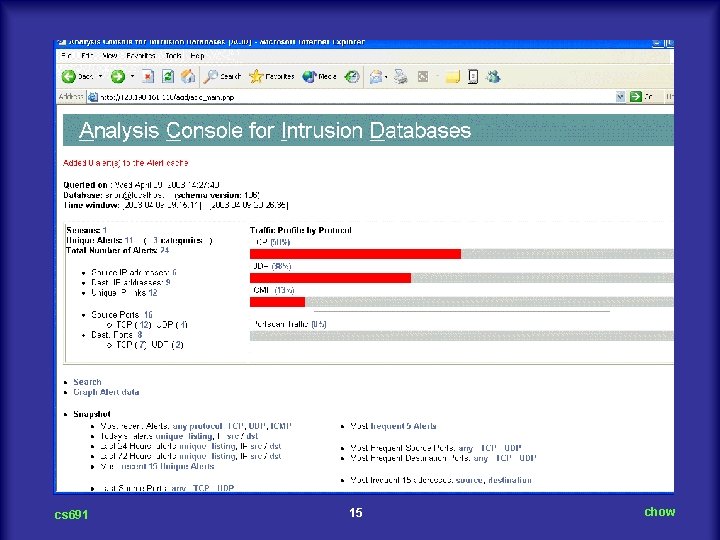
cs 691 16 chow
![Detection Results n 0 3 1 snort WEBIIS cmd exe access 2003 04 14 Detection Results n #0 -(3 -1) [snort] WEB-IIS cmd. exe access 2003 -04 -14](https://slidetodoc.com/presentation_image_h/809cb3ee66d15399b7a6b9322039935b/image-17.jpg)
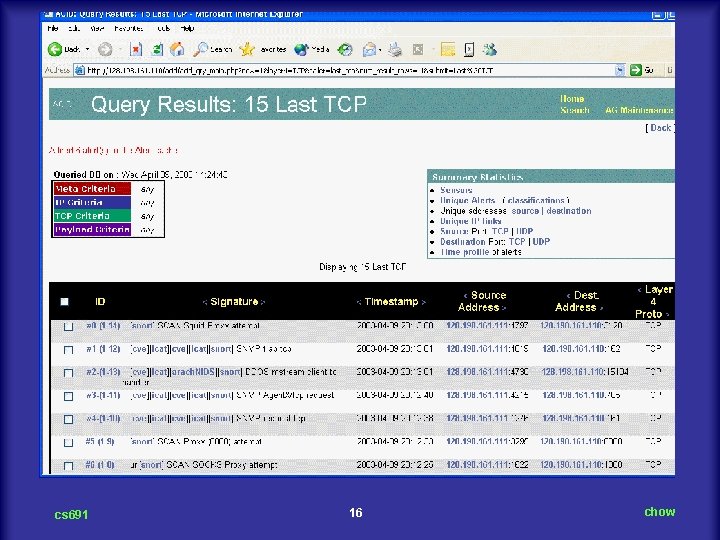
Detection Results n #0 -(3 -1) [snort] WEB-IIS cmd. exe access 2003 -04 -14 21: 14: 00 65. 106. 21. 153: 1541 128. 198. 161. 110: 80 TCP n C: workcucscs 691S 2003>nslookup 65. 106. 21. 153 Server: evans. eas. uccs. edu Address: 128. 198. 160. 66 Name: diahost 153. dia. cnc. net Address: 65. 106. 21. 153 cs 691 17 chow

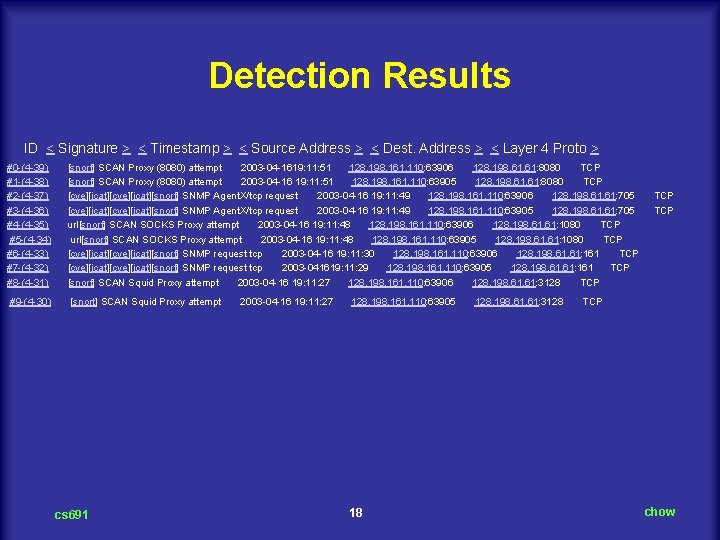
Detection Results ID < Signature > < Timestamp > < Source Address > < Dest. Address > < Layer 4 Proto > #0 -(4 -39) [snort] SCAN Proxy (8080) attempt 2003 -04 -1619: 11: 51 128. 198. 161. 110: 63906 128. 198. 61: 8080 TCP #1 -(4 -38) [snort] SCAN Proxy (8080) attempt 2003 -04 -16 19: 11: 51 128. 198. 161. 110: 63905 128. 198. 61: 8080 TCP #2 -(4 -37) [cve][icat][snort] SNMP Agent. X/tcp request 2003 -04 -16 19: 11: 49 128. 198. 161. 110: 63906 128. 198. 61: 705 TCP #3 -(4 -36) [cve][icat][snort] SNMP Agent. X/tcp request 2003 -04 -16 19: 11: 49 128. 198. 161. 110: 63905 128. 198. 61: 705 TCP #4 -(4 -35) url[snort] SCAN SOCKS Proxy attempt 2003 -04 -16 19: 11: 48 128. 198. 161. 110: 63906 128. 198. 61: 1080 TCP #5 -(4 -34) url[snort] SCAN SOCKS Proxy attempt 2003 -04 -16 19: 11: 48 128. 198. 161. 110: 63905 128. 198. 61: 1080 TCP #6 -(4 -33) [cve][icat][snort] SNMP request tcp 2003 -04 -16 19: 11: 30 128. 198. 161. 110: 63906 128. 198. 61: 161 TCP #7 -(4 -32) [cve][icat][snort] SNMP request tcp 2003 -041619: 11: 29 128. 198. 161. 110: 63905 128. 198. 61: 161 TCP #8 -(4 -31) [snort] SCAN Squid Proxy attempt 2003 -04 -16 19: 11: 27 128. 198. 161. 110: 63906 128. 198. 61: 3128 TCP #9 -(4 -30) [snort] SCAN Squid Proxy attempt 2003 -04 -16 19: 11: 27 128. 198. 161. 110: 63905 128. 198. 61: 3128 TCP cs 691 18 chow

False Positives vs False Negatives False positives: something occurs that causes IDS to incorrectly identify an intrusion when none has occurred. n False negatives: something occurs that causes IDS to incorrectly fail to identify an intrustion when one has in fact occurred. n Accuracy of IDS: reflect the number of false positives. n Completeness: reflect the number of false negatives. n cs 691 19 chow

Attack Response Rules n n n n Check on the responses of server for obvious pattern that the system has be attacked/compromised. https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=attack-responses Examples: alert tcp $HTTP_SERVERS $HTTP_PORTS -> $EXTERNAL_NET any (msg: "ATTACK RESPONSES index of /cgi-bin/ response"; flow: from_server, established; content: "Index of /cgi-bin/"; nocase; classtype: badunknown; sid: 1666; rev: 3; ) alert tcp $HOME_NET 22 -> $EXTERNAL_NET any (msg: "ATTACK-RESPONSE successful gobbles ssh exploit (GOBBLE)"; flow: from_server, established; content: "|2 a|GOBBLE|2 a|"; reference: bugtraq, 5093; classtype: successful-admin; sid: 1810; rev: 2; ) http: //www. securityfocus. com/bid/5093 alert tcp $HOME_NET 749 -> $EXTERNAL_NET any (msg: "ATTACK-RESPONSE successful kadmind bufferflow attempt"; flow: established, from_server; content: "*GOBBLE*"; depth: 8; reference: cve, CAN-2002 -1235; reference: url, www. kb. cert. org/vuls/id/875073; classtype: successful-admin; sid: 1900; rev: 1; ) cs 691 20 chow

Back. Door Trojan Try to detect know ports and content of packet that are used and generated by the backdoor trojan. n alert tcp $HOME_NET 6789 -> $EXTERNAL_NET any (msg: "BACKDOOR Doly 2. 0 access"; content: "|57 74 7 a 75 70 20 55 73 65|"; flags: A+; depth: 32; reference: arachnids, 312; sid: 119; classtype: miscactivity; rev: 3; ) n http: //www. whitehats. com/cgi/arach. NIDS/Show? _id=ids 312&view=research n https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=b ackdoor n cs 691 21 chow

DDo. S Rules DDo. S with know protocol/port/content. n https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=ddos n alert icmp $EXTERNAL_NET any <> $HOME_NET any (msg: "DDOS Stacheldraht handler->agent (ficken)"; content: "ficken"; itype: 0; icmp_id: 6667; reference: url, staff. washington. edu/dittrich/misc/stacheldraht. analysi s; classtype: attempted-dos; sid: 1856; rev: 2; ) n alert udp $EXTERNAL_NET any -> $HOME_NET 31335 (msg: "DDOS Trin 00: Daemonto. Master(PONGdetected)"; content: "PONG"; reference: arachnids, 187; classtype: attemptedrecon; sid: 223; rev: 1; ) n cs 691 22 chow

DNS rules Zone transfer, DNS buffer overflow exploit. n https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=dns n alert tcp $EXTERNAL_NET any -> $DNS_SERVERS 53 (msg: "DNS zone transfer TCP"; flow: to_server, established; content: "|00 00 FC|"; offset: 14; reference: cve, CAN-1999 -0532; reference: arachnids, 212; classtype: attempted-recon; sid: 255; rev: 7; ) n alert tcp $EXTERNAL_NET any -> $DNS_SERVERS 53 (msg: "DNS EXPLOIT x 86 linux overflow attempt (ADMv 2)"; flow: to_server, established; content: "|89 f 7 29 c 7 89 f 3 89 f 9 89 f 2 ac 3 c fe|"; classtype: attempted-admin; sid: 265; rev: 3; ) n cs 691 23 chow

Scan rules n n n Scan certain node/ports. (network scan vs port scan) https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=scan alert tcp $EXTERNAL_NET any -> $HOME_NET 3128 (msg: "SCAN Squid Proxy attempt"; flags: S; classtype: attempted-recon; sid: 618; rev: 2; ) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg: "SCAN synscan portscan"; id: 39426; flags: SF; reference: arachnids, 441; classtype: attempted-recon; sid: 630; rev: 1; ) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg: "SCAN nmap TCP"; flags: A; ack: 0; reference: arachnids, 28; classtype: attempted-recon; sid: 628; rev: 1; ) alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg: "SCAN Solar. Winds IP scan attempt"; content: "Solar. Winds. Net"; itype: 8; icode: 0; classtype: network-scan; sid: 1918; rev: 3; ) cs 691 24 chow

WEB-CGI Rules https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=web-cgi alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-CGI perl. exe access"; flow: to_server, established; uricontent: "/perl. exe"; nocase; reference: cve, CAN-1999 -0509; reference: url, www. cert. org/advisories/CA-1996 -11. html; reference: arachnids, 219; reference: nessus, 10173; classtype: attempted-recon; sid: 832; rev: 8; ) n. . (DOT DOT) ATTACK. alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-CGI technote main. cgi file directory traversal attempt"; flow: to_server, established; uricontent: "/technote/main. cgi"; nocase; content: "filename="; nocase; content: ". . /"; reference: cve, CVE-2001 -0075; reference: bugtraq, 2156; classtype: web-application-attack; sid: 1051; rev: 7; ) n n cs 691 25 chow

WEB-IIS Rules https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=w eb-iis n alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-IIS unicode directory traversal attempt"; flow: to_server, established; content: "/. . %c 0%af. . /"; nocase; classtype: webapplication-attack; reference: cve, CVE-2000 -0884; sid: 981; rev: 6; ) n alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg: "WEB-IIS cmd. exe access"; flow: to_server, established; content: "cmd. exe"; nocase; classtype: web-application-attack; sid: 1002; rev: 5; ) n cs 691 26 chow

SMTP Rules SMTP has quite a few buffer overlfow exploit. https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=smtp alert tcp $EXTERNAL_NET any -> $SMTP_SERVERS 25 (msg: "SMTP RCPT TO overflow"; flow: to_server, established; content: "rcpt to|3 a|"; nocase; content: !"|0 a|"; within: 800; reference: cve, CAN-2001 -0260; reference: bugtraq, 2283; classtype: attempted-admin; sid: 654; rev: 7; ) n alert tcp $EXTERNAL_NET any -> $SMTP_SERVERS 25 (msg: "SMTP sendmail 5. 6. 5 exploit"; flow: to_server, established; content: "MAIL FROM|3 a 207 c|/usr/ucb/tail"; nocase; reference: arachnids, 122; classtype: attempted-user; sid: 665; rev: 4; ) n alert tcp $EXTERNAL_NET any -> $SMTP_SERVERS 25 (msg: "SMTP From comment overflow attempt"; flow: to_server, established; content: "From: "; content: "<><><><><><><><><><><>"; distance: 0; content: "("; distance: 1; content: ")"; distance: 1; reference: cve, CAN-2002 -1337; reference: url, www. kb. cert. org/vuls/id/398025; classtype: attempted-admin; sid: 2087; rev: 2; ) n n n cs 691 27 chow

Bad Traffic Bad packet header content n https: //128. 198. 61: 10000/snort/conf_rules. cgi? rule=b ad-traffic n alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg: "BAD TRAFFIC data in TCP SYN packet"; flags: S; dsize: >6; reference: url, www. cert. org/incident_notes/IN 99 -07. html; sid: 526; classtype: misc-activity; rev: 4; ) n alert ip any -> any (msg: "BAD TRAFFIC same SRC/DST"; sameip; reference: cve, CVE-1999 -0016; reference: url, www. cert. org/advisories/CA-1997 -28. html; classtype: bad-unknown; sid: 527; rev: 3; ) n cs 691 28 chow

HIDS: Host-based Intrusion Detection n n n Detect and examine malicious activity (same as network -based intrusion detection. ) Optimize for monitoring individual hosts. Monitor system network activity, file system, log files, user actions. Integrate the finding of several host-based intrusion detection provide unified view of multiple systems in the network. Detect escalation of privileges for a user or system account. (from guest user to have admin privilege). NIDS can not usually see or interpret such actions which takes place on a host. cs 691 29 chow

HIDS’ Advantages over NIDS HIDS can monitor user-specific activity of the system l Check process listing, local log files, system calls. l It is difficult for NIDS to associate packets to specific users (except when content switch-based NIDS is used!) and to determine if the commands in the packets violate specific user’s access privilege. n HIDS sensor can monitor encrypted traffic by tapping in at the connection endpoint such as VPN connection. (NIDS can not check encrypted IPsec/SSL payload. ) n HIDS can help detect attack that evade NIDS detection. For example, attacks encode dangerous commands in nonstandard Unicode encoding. checking for ". ida". An example request would look like: GET /himom. id%u 0061 HTTP/1. 0 n cs 691 30 chow

Tripwire: A Host-based IDS Original version developed at Purdue Univ. 1992 by Dr. Eugene Spafford and Gene Kim, now CTO of Tripwire n http: //www. tripwire. org/downloads/index. php Linux public domain software download. http: //www. tripwire. org/qanda/faq. php n Commercial evaluation version tripwire 3. 0 (with manager and server, run on both Linux/windows) available at http: //www. tripwire. com/downloads/ l Tripwire managers provide gui and unified interface to monitor multiple instances of tripwire program. l Can monitor configuration of routers/switches. l Here is a presentation from tripwire. com. n There is Advanced Intrusion Detection Environment (AIDE) available at http: //www. . cs. tut. fi/~rammer/aide. html. It is actively maintained and developed. Not on windows. Does not encrypt and sign the baseline datagbase. (The tripwire does this). n cs 691 31 chow

cs 691 32 chow

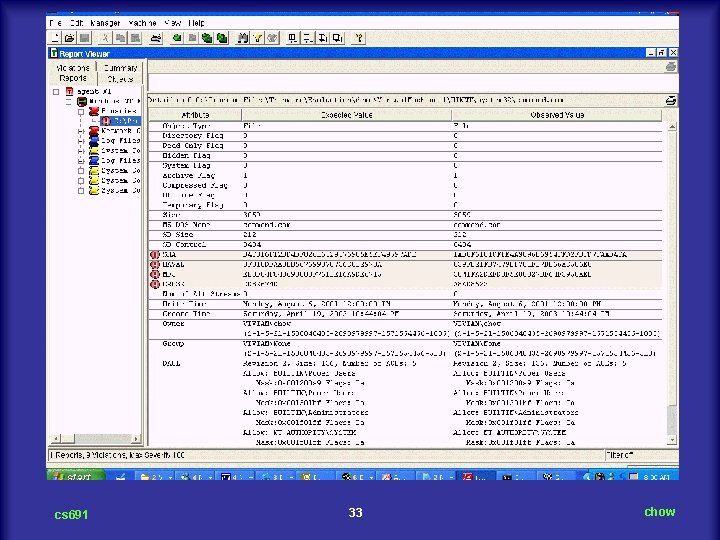
cs 691 33 chow

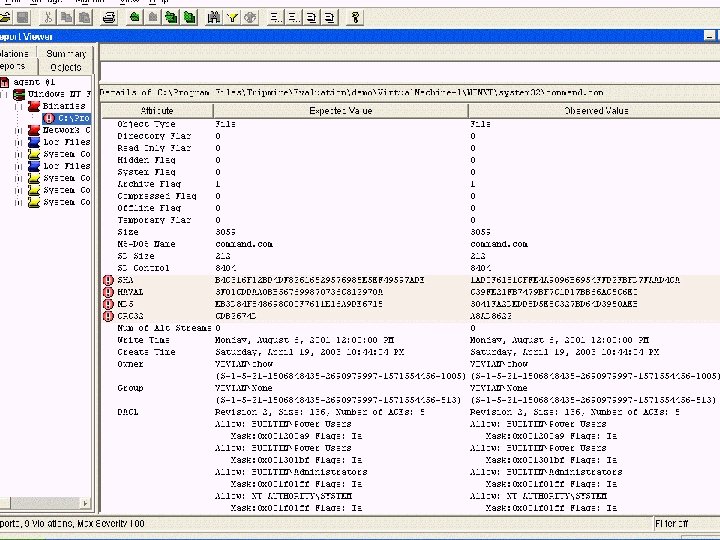
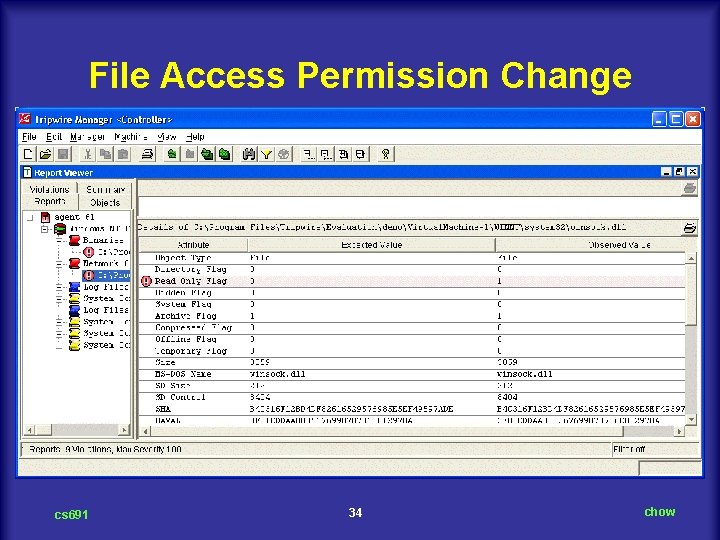
File Access Permission Change cs 691 34 chow

Example of Policy File For windows systems, http: //cs. uccs. edu/~cs 691/tripwire/windows/Policy/twpol. txt n For linux, http: //cs. uccs. edu/~cs 691/tripwire/linux/Policy/twpol. txt n http: //cs. uccs. edu/~cs 691/tripwire/windows/Documents/r eference_guide. pdf page 25. n Rule: object -> properties; n cs 691 35 chow