FEAL 1 FEAL Fast data Encryption ALgorithm q





















- Slides: 30

FEAL 1

FEAL Fast data Encryption ALgorithm q Invented, promoted by NTT in 1987 q o Japanese telecommunications monopoly Designed as replacement for DES q And to be fast and efficient q o With modest security q Original version (FEAL-4) found to be weak o Many “improved” versions followed o All are flawed to some degree FEAL 2

FEAL-4 q Here, we consider FEAL-4 q Important in history of cryptanalysis q Differential cryptanalysis developed to attack FEAL-4 o Powerful method to analyze block ciphers q We present differential and linear attacks on FEAL-4 FEAL 3

Differential and Linear Attacks q Differential and linear attacks are usually only of theoretical interest o Large chosen (known) plaintext requirement FEAL-4 is an exception q Both differential and linear attacks on FEAL-4 are practical q o So these attacks fit theme of the book o And introduce important cryptanalysis methods FEAL 4

FEAL-4 Cipher q FEAL-4 is a 4 -round Feistel cipher with a 64 -bit block and 64 -bit key q Several different (but equivalent) ways to describe the cipher q Description for differential attack o 64 -bit key six 32 -bit subkeys o Round function F maps 32 bits to 32 bits FEAL 5

FEAL-4 Cipher q Plaintext: P q Ciphertext: C q Round function: F q 32 -bit subkeys: K 0, K 1, …, K 6 q XOR: q Very simple cipher! FEAL 6

FEAL-4 Round Function Define G 0(a, b) = (a + b (mod 256)) <<< 2 G 1(a, b) = (a + b + 1 (mod 256)) <<< 2 q Where “<<<” is left cyclic shift (rotation) q Then F(x 0, x 1, x 2, x 3) = (y 0, y 1, y 2, y 3) where q y 1 = G 1(x 0 x 1, x 2 x 3) y 2 = G 1(y 1, x 2 x 3) FEAL y 0 = G 0(x 0, y 1) y 3 = G 1(y 2, x 3) 7

FEAL-4 Round Function q Schematic of FEAL-4 round function o Note the XORs Differential attack: “difference” is XOR q By considering differences, the cipher is simplified q FEAL 8

FEAL-4 Differential Attack A chosen plaintext attack q Two plaintexts, specified difference q o Difference is known as a characteristic For example if X is the characteristic, P 0 P 1 = X q Note, we can choose P 0 at random and let P 1 = P 0 X q Are there any useful characteristics? q FEAL 9

FEAL-4 Differential Attack q Note: A 0 A 1 = 0 implies F(A 0) = F(A 1) q Easy to show that if A 0 A 1 = 0 x 80800000 then for round function F we have F(A 0) F(A 1) = 0 x 02000000 q And it holds with probability 1 q Differential attack based on this… FEAL 10

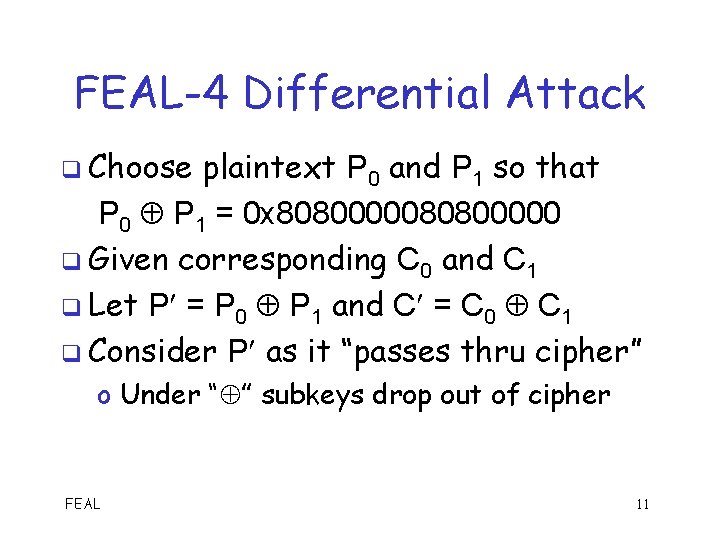
FEAL-4 Differential Attack q Choose plaintext P 0 and P 1 so that P 0 P 1 = 0 x 80800000 q Given corresponding C 0 and C 1 q Let P = P 0 P 1 and C = C 0 C 1 q Consider P as it “passes thru cipher” o Under “ ” subkeys drop out of cipher FEAL 11

FEAL-4 Differential Attack q Characteristic for P gets us half way thru q Can then work backwards from C q Try to meet in middle o Note L , R are known FEAL 12

FEAL-4 Differential Attack q We have L = 0 x 02000000 Z q Which give us Z q Also, Y = 0 x 80800000 X q Note: For C = (L, R) we have Y = L R q Now we can solve for subkey K 3 o Next slide… FEAL 13

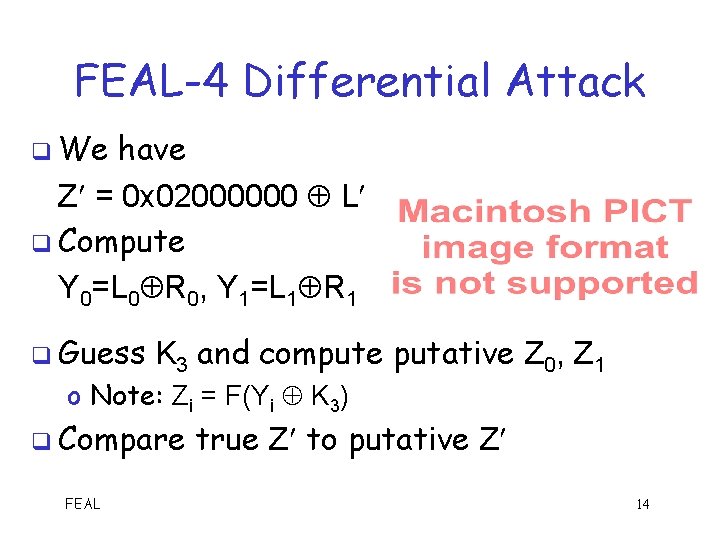
FEAL-4 Differential Attack q We have Z = 0 x 02000000 L q Compute Y 0=L 0 R 0, Y 1=L 1 R 1 q Guess K 3 and compute putative Z 0, Z 1 o Note: Zi = F(Yi K 3) q Compare FEAL true Z to putative Z 14

FEAL-4 Differential Attack q Using 4 chosen plaintext pairs o Work is of order 232 o Expect one K 3 to survive q Good divide and conquer strategy q But it is possible to do better! o Can reduce work to about 217 q Relies on structure of F function o See next slide… FEAL 15

FEAL-4 Differential Attack q For 32 -bit word A=(a 0, a 1, a 2, a 3), define M(A) = (z, a 0 a 1, a 2 a 3, z) where z is all-zero byte q For all possible A=(z, a 0, a 1, z), compute Q 0 = F(M(Y 0) A) and Q 1 = F(M(Y 1) A) q Can be used to find 16 bits of K 3 FEAL 16

FEAL-4 Differential Attack q For all A = (z, a 0, a 1, z), compute Q 0 = F(M(Y 0) A) and Q 1 = F(M(Y 1) A) q When A = M(K 3) by defn of F, we have Q 0 Q 1 8… 23 = Z 8… 23 where X i…j is bits i thru j of X q Can recover K 3 with about 217 work FEAL 17

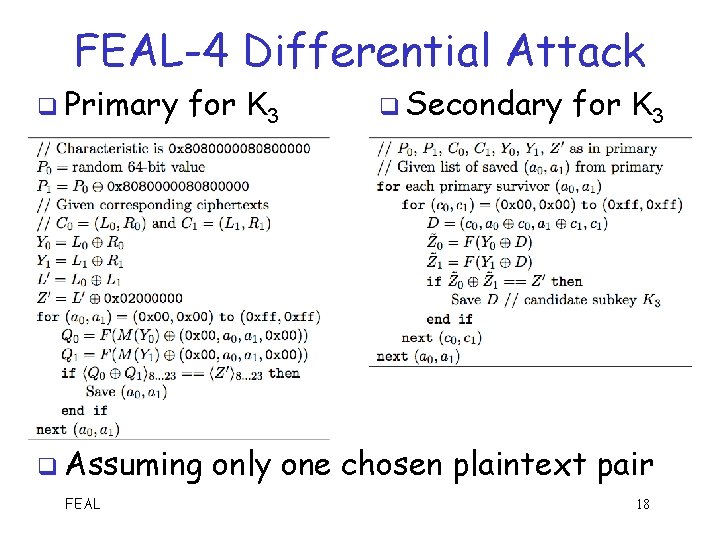
FEAL-4 Differential Attack q Primary for K 3 q Assuming FEAL q Secondary for K 3 only one chosen plaintext pair 18

FEAL-4 Differential Attack q Once K 3 is known, can successively recover K 2, K 1, K 0 and finally K 4, K 5 o Attack is similar in each case o Some require different characteristics o There a few subtle points q See FEAL the homework problems! 19

Differential Attacks In FEAL-4, differential for K 3 holds with probability 1 q In most differential attacks, probability is small, which q o Increases chosen plaintext requirement o Increases work factor Differential cryptanalysis seldom practical q Usually only a theoretical tool q FEAL 20

FEAL-4 Linear Attack q Consider this equivalent form of FEAL-4 q Known plaintext attack… FEAL 21

FEAL-4 Linear Attack Let X be 32 -bit word, X = (x 0, x 1, …, x 31) q Define Si, j(X) = xi xj and Si(X) = xi q o Also extends to sum of more than 2 bits Attack uses fact that for bytes a and b, S 7(a b) = S 7(a + b (mod 256)) q Recall G 0(a, b) = (a + b (mod 256)) <<< 2, so that S 5 G 0(a, b) = S 7(a b) q Also, S 5 G 1(a, b) = S 7(a b) 1 q FEAL 22

FEAL-4 Linear Attack Have S 5 G 0(a, b) = S 7(a b) q And S 5 G 1(a, b) = S 7(a b) 1 q Let Y = F(X), where X, Y are 32 -bit words q Then it can be shown that S 13(Y) = S 7, 15, 23, 31(X) 1 S 5(Y) = S 15(Y) S 7(X) S 15(Y) = S 21(Y) S 23, 31(X) S 23(Y) = S 29(Y) S 31(X) 1 q FEAL 23

FEAL-4 Linear Attack q Label FEAL-4 intermediate steps q Use formulas on previous slide… FEAL 24

FEAL-4 Linear Attack q It can be shown that a = S 23, 29(L 0 R 0 L 4) S 31(L 0 L 4 R 4) S 31 F(L 0 R 0 K 0) q Where a = S 31(K 1 K 3 K 4 K 5) S 23, 29(K 4) Treat a as unknown, but constant q Exhaust over all choices for K 0 q o Test all known plaintext/ciphertext pairs o If a is not constant, putative K 0 is incorrect FEAL 25

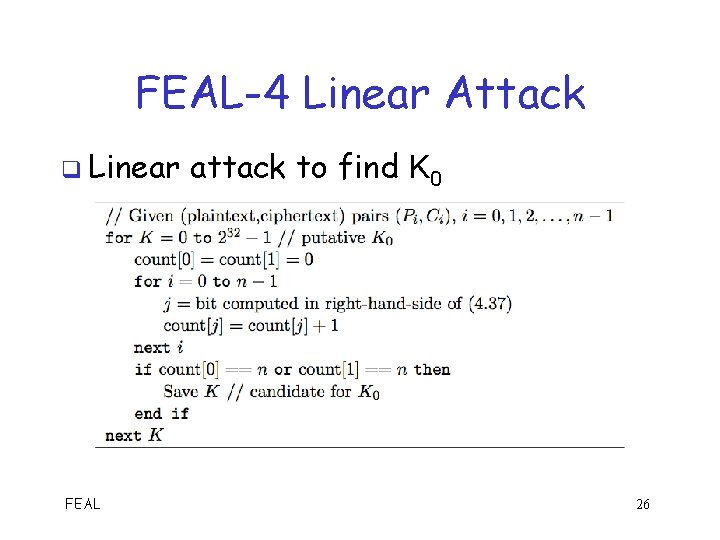
FEAL-4 Linear Attack q Linear FEAL attack to find K 0 26

FEAL-4 Linear Attack q Possible to improve on linear attack of previous slide o Exhaust for 12 bits of K 0 first, then… o Work is much less than 232 (see text) q Can extend this attack to recover other subkeys FEAL 27

Confusion and Diffusion Modern block ciphers employ both confusion and diffusion q FEAL-4 is a Feistel cipher q o With round function F(X Ki) o Diffusion: shift bytes in F and bits in G 0, G 1 o Confusion: XOR of Ki and addition q FEAL-4: diffusion and confusion are weak FEAL 28

FEAL-4 Conclusion Weak block cipher q Important in modern cryptanalysis q o Many variants in FEAL cipher family o All broken Differential cryptanalysis developed for FEAL q Good example to illustrate both linear and differential attacks q FEAL 29

Linear and Differential Attacks q Important tools to analyze ciphers o Used in block cipher design q Seldom practical methods of attack for block ciphers q Will see again with hash functions o In particular, differential attacks FEAL 30