Topic 3 Data Encryption Computer Science Encryption Sometimes







- Slides: 18

Topic 3: Data Encryption Computer Science

Encryption • Sometimes, we may want to keep our data hidden from unwanted attention Sending secret messages to someone Keeping private data secure Stopping people online seeing sensitive data (like bank account details or passwords) • Turning data in its original form into something harder to understand is called encryption

Encryption • In encryption, there a few important terms to learn: Plaintext: the data in its original, easily understandable form Cipher text: the data in its encrypted, harder to understand form Cipher: the technique used to encrypt the data (plaintext cipher text) • There are lots of ciphers out there, each involving different steps

Encryption • We will look at four ciphers in total Pigpen Cipher Caesar Cipher Vigenere Fence Rail Fence Cipher • They each vary in terms of complexity Making some ciphers easier to use than others

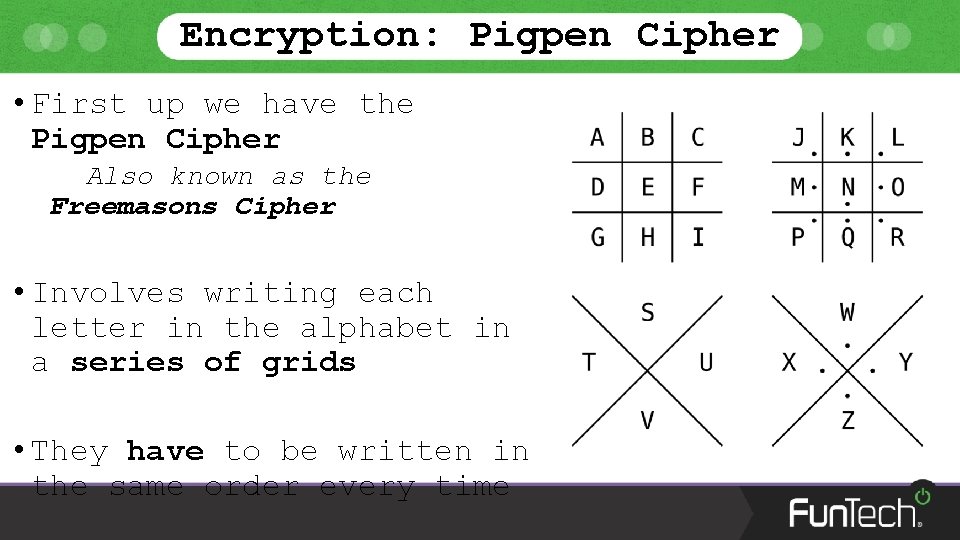
Encryption: Pigpen Cipher • First up we have the Pigpen Cipher Also known as the Freemasons Cipher • Involves writing each letter in the alphabet in a series of grids • They have to be written in the same order every time

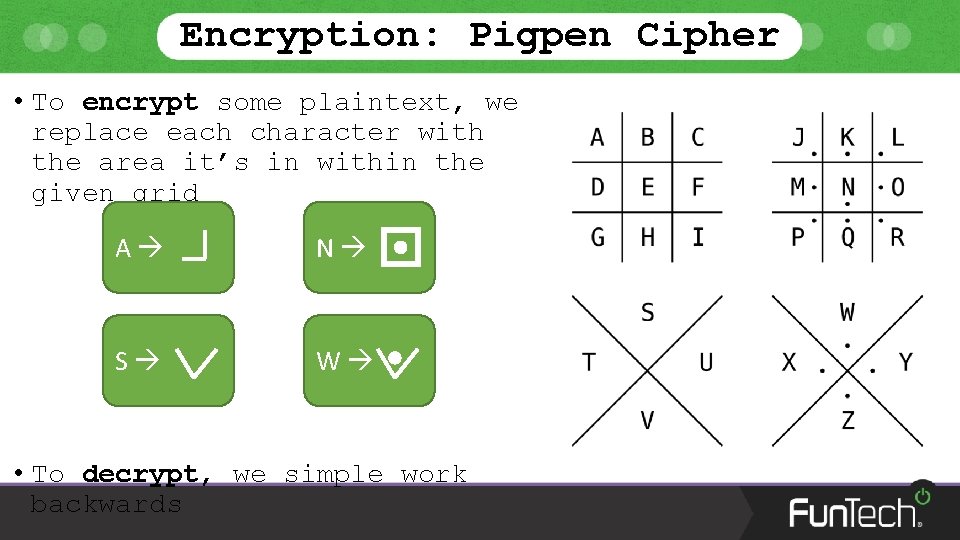
Encryption: Pigpen Cipher • To encrypt some plaintext, we replace each character with the area it’s in within the given grid A N S W • To decrypt, we simple work backwards

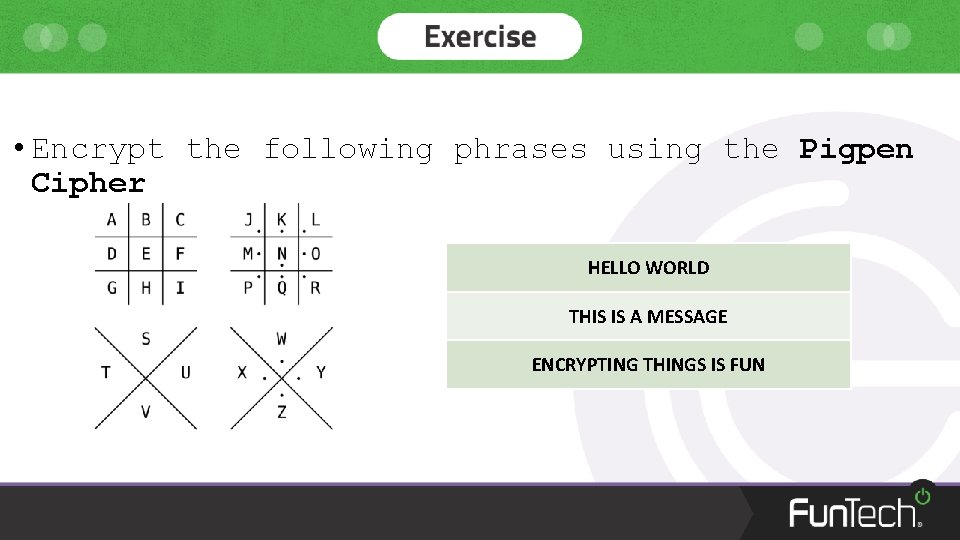
• Encrypt the following phrases using the Pigpen Cipher HELLO WORLD THIS IS A MESSAGE ENCRYPTING THINGS IS FUN

Encryption: Caesar Cipher • Let’s move over to the Caesar Cipher Also known as the shift cipher • Involves moving individual letters so many spaces along Shifting them This creates the cipher text • To decrypt, move the letters in the opposite direction Take a look at this virtual Caesar Cipher Move the same number of spaces • The shift used is called the key wheel!

Encryption: Caesar Cipher Example Plaintext: TIM IS THE COOLEST Cipher Text: XMQ MW XLI GSSPIWX What shift was used here?

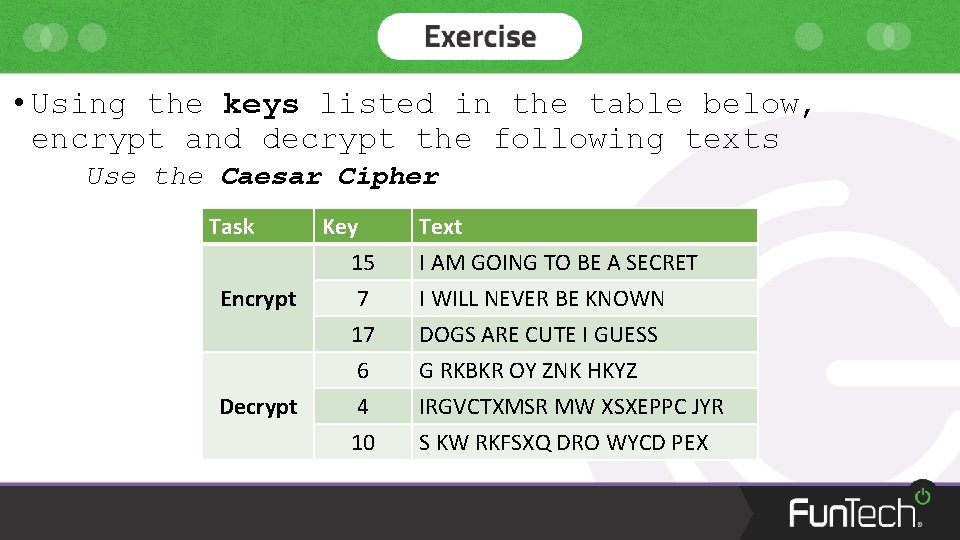
• Using the keys listed in the table below, encrypt and decrypt the following texts Use the Caesar Cipher Task Encrypt Decrypt Key 15 7 17 6 4 10 Text I AM GOING TO BE A SECRET I WILL NEVER BE KNOWN DOGS ARE CUTE I GUESS G RKBKR OY ZNK HKYZ IRGVCTXMSR MW XSXEPPC JYR S KW RKFSXQ DRO WYCD PEX

Encryption: Vigenere Cipher • Now we’re on to the Vigenere Cipher • Similar to the Caesar Cipher • However, uses a phrase (not a key) • This phrase acts as the key for encryption We calculate a number for every letter in the phrase Shift individual letters in the plaintext by that amount Loop back to start of phrase when reaching the end of it

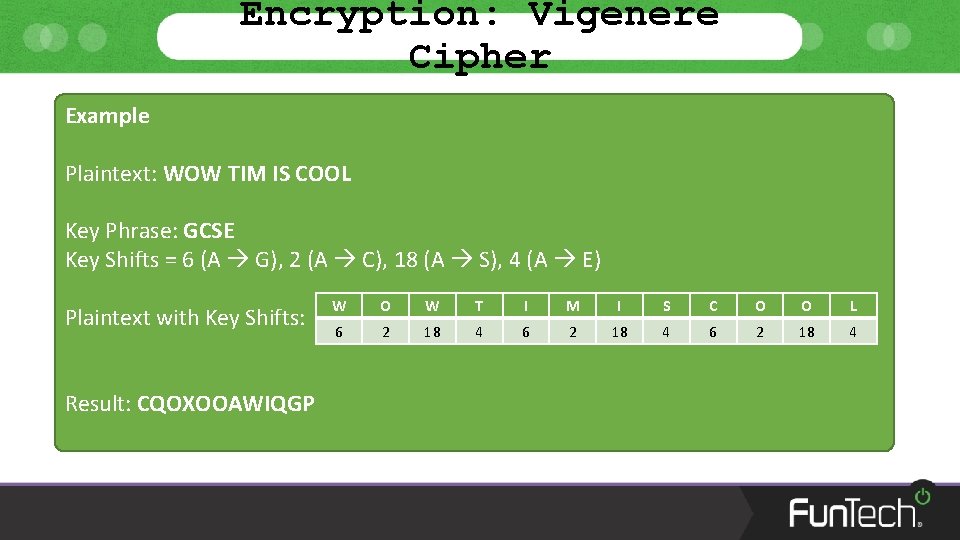
Encryption: Vigenere Cipher Example Plaintext: WOW TIM IS COOL Key Phrase: GCSE Key Shifts = 6 (A G), 2 (A C), 18 (A S), 4 (A E) Plaintext with Key Shifts: Result: CQOXOOAWIQGP W O W T I M I S C O O L 6 2 18 4

• Use this passphrase to encrypt the following plaintext: IGCSE HELLO WORLD THIS IS A MESSAGE ENCRYPTING THINGS IS FUN

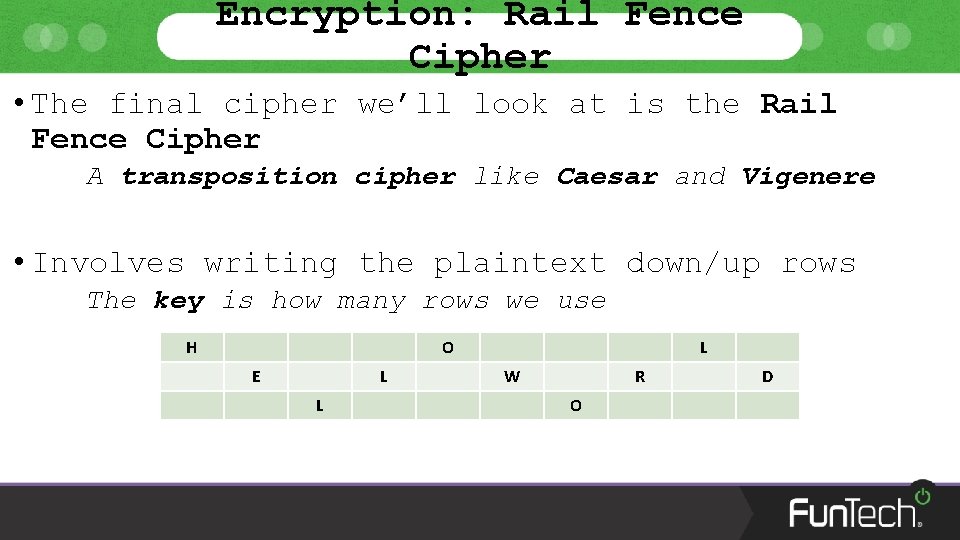
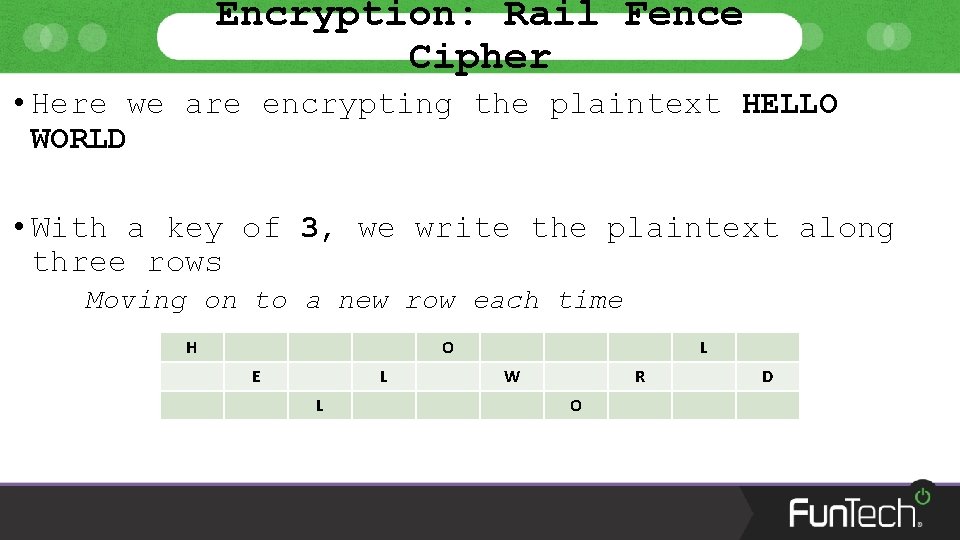
Encryption: Rail Fence Cipher • The final cipher we’ll look at is the Rail Fence Cipher A transposition cipher like Caesar and Vigenere • Involves writing the plaintext down/up rows The key is how many rows we use H O E L L L W R O D

Encryption: Rail Fence Cipher • Here we are encrypting the plaintext HELLO WORLD • With a key of 3, we write the plaintext along three rows Moving on to a new row each time H O E L L L W R O D

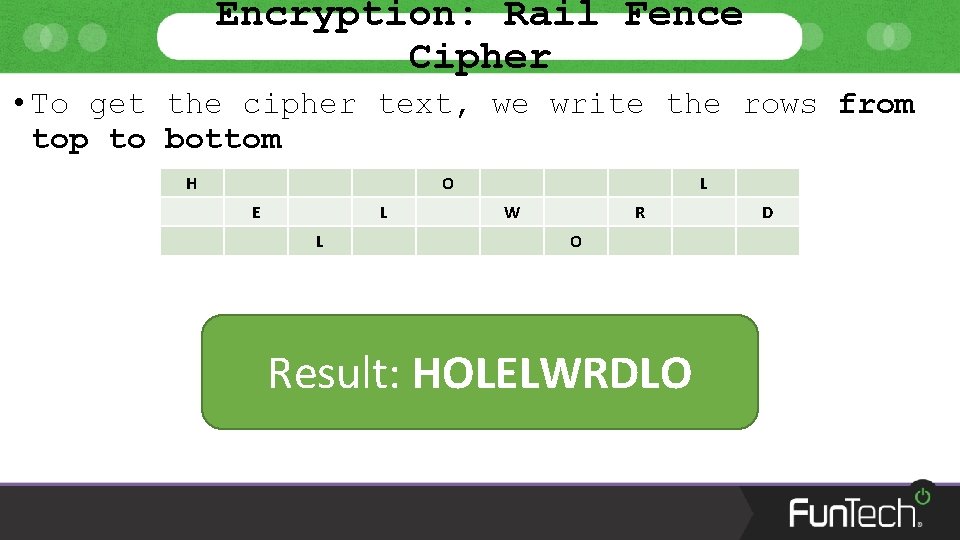
Encryption: Rail Fence Cipher • To get the cipher text, we write the rows from top to bottom H O E L L L W R O Result: HOLELWRDLO D

• Use a key of 4 (and the Rail Fence Cipher) to encrypt the following phrases: HELLO WORLD THIS IS A MESSAGE ENCRYPTING THINGS IS FUN
