EGov and Security Keren Cummins Digital Signature Trust
























- Slides: 29

E-Gov and Security Keren Cummins Digital Signature Trust Co. Richard Guida Chair, Federal PKI Steering Committee

E-Transaction Landscape • Intra-agency – personnel matters, agency management • Interagency – payments, account reconciliation, litigation • Agency to trading partner – procurement, regulation • Agency to the public

Challenges All Applications Face • • Authentication of Users Non-repudiation for transactions Message integrity Confidentiality (privacy) Liability Interoperability Scalability

Potential Internet Security Solutions • Pin Numbers • Biometrics • Digital Signatures or PKI (Public Key Infrastructure) PKI Viewed by Many as Only Total Solution

A Digital Signature is NOT: • A Digitized Handwritten Signature… • The Typed Name of an Individual • A Secret Code or a Pin Number

A Digital Signature IS: • A Transformation of a Message Using Public Key Cryptography • Virtually Impossible to Forge • Provides a High Level of Security

Basic Principle of Cryptography • All information goes into a computer as a number • One can perform mathematical operations on the information • For Example: Add, subtract, multiply, divide or exponentiate it.

Two Flavors of Cryptography • Symmetric Cryptography – Uses Single Number or Key • Asymmetric or Public Key Cryptography – Uses Two Different Numbers or Key Pair – Key Pair Consists of Two Large Numbers: • One Called a Private Key • One Called a Public Key

What Does Cryptography Really Look Like • Private Key: – 6448072 E 0 AD 8 FD 61 F 78 E 45 FC 0 B 9419 F 9 0 E 1 DD 1 EF • Public Key: – 47 F 126 B 5 74 A 10 BB 1 EB 107322 C 2379439 7 F 7 DD 52 D 6 CB 89 D 3 F 04 A 4 E 434 0 A 09 EE 52 6284271 E E 092 C 592 C 3 CC 4144 5861 CBF 5 E 8696 BFF 85432 ED 1 B 919 A 328 48 B 1 D 9 F 0 • Hash or Message Digest: – 53007 ADB 04851436 F 3 F 3 ACBB F 07 CA 19 D 1 AC 248 EA • DSA Signature: – 571691 CC 0426 C 2 B 5 A 545 D 896 C 620 CB 8 D 76 B 7820 C

What’s a Hash? • Brief series of characters associated with a document • Message digest, or “fingerprint” generated by a mathematical algorithm • Same document will always generate the same hash • A document that has been altered can never generate the original hash

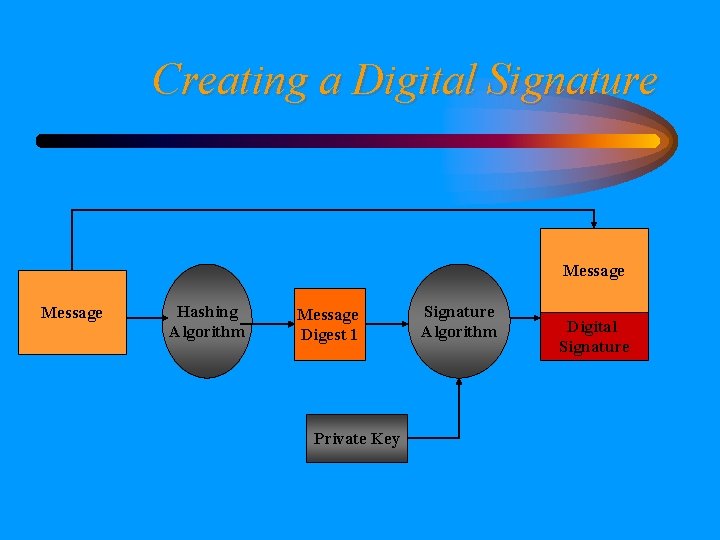
Creating a Digital Signature Message Hashing Algorithm Message Digest 1 Private Key Signature Algorithm Digital Signature

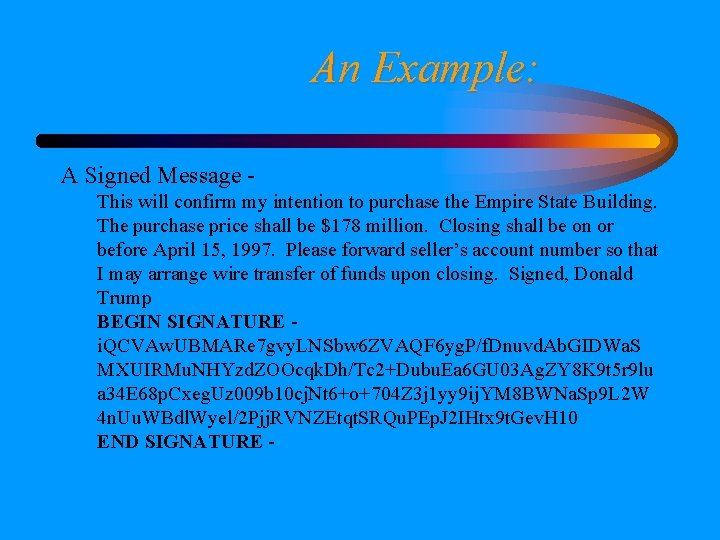
An Example: A Signed Message This will confirm my intention to purchase the Empire State Building. The purchase price shall be $178 million. Closing shall be on or before April 15, 1997. Please forward seller’s account number so that I may arrange wire transfer of funds upon closing. Signed, Donald Trump BEGIN SIGNATURE i. QCVAw. UBMARe 7 gvy. LNSbw 6 ZVAQF 6 yg. P/f. Dnuvd. Ab. GIDWa. S MXUIRMu. NHYzd. ZOOcqk. Dh/Tc 2+Dubu. Ea 6 GU 03 Ag. ZY 8 K 9 t 5 r 9 lu a 34 E 68 p. Cxeg. Uz 009 b 10 cj. Nt 6+o+704 Z 3 j 1 yy 9 ij. YM 8 BWNa. Sp 9 L 2 W 4 n. Uu. WBdl. Wyel/2 Pjj. RVNZEtqt. SRQu. PEp. J 2 IHtx 9 t. Gev. H 10 END SIGNATURE -

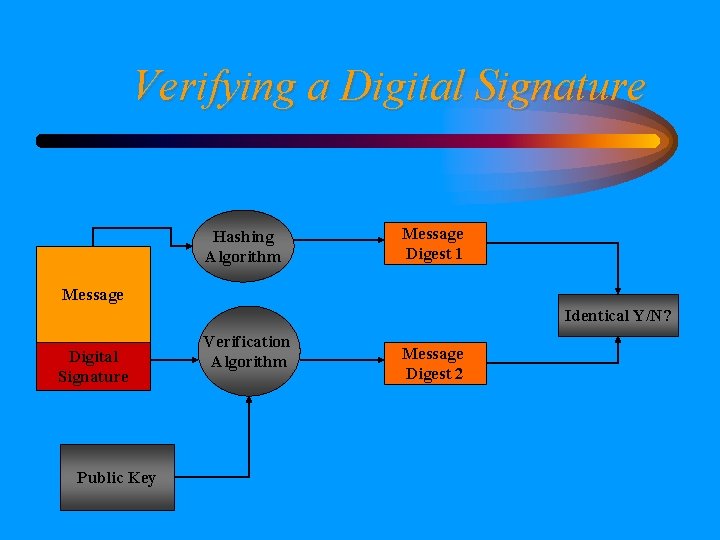
Verifying a Digital Signature Hashing Algorithm Message Digest 1 Message Identical Y/N? Digital Signature Public Key Verification Algorithm Message Digest 2

What’s Missing • Need to Link Individual Identities to Proposed Security Factor • How Do I Know This is Your Password, Fingerprint, or Public Key • Enter “Trusted Third Parties” or TTPs

Role of Trusted Third Parties (TTPs) • Link Security Factor to Individual Identity (PKI Uses Digital Certificates) • Stand Behind Linkage • Demonstrate Sufficient Institutional Stature as to Promote Trust in Linkage • Issue a Digital Certificate Binding Signer’s Identity to Signer’s Public Key

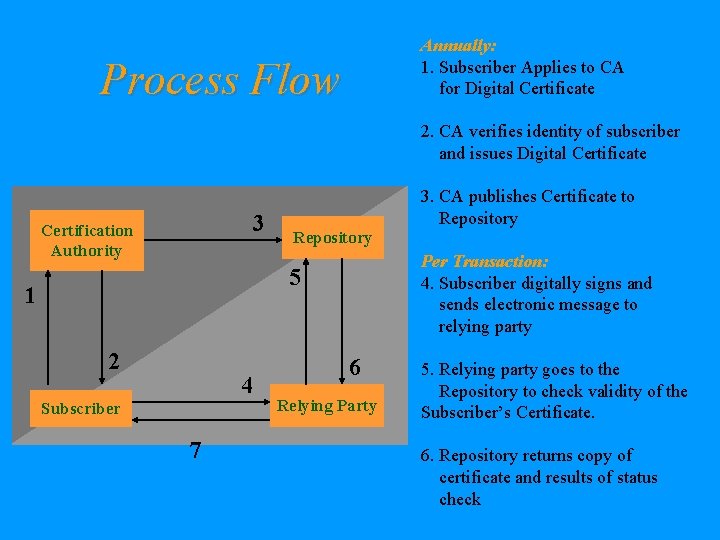
Annually: 1. Subscriber Applies to CA for Digital Certificate Process Flow 2. CA verifies identity of subscriber and issues Digital Certificate 3 Certification Authority 3. CA publishes Certificate to Repository Per Transaction: 4. Subscriber digitally signs and sends electronic message to relying party 5 1 2 4 Subscriber 7 6 Relying Party 5. Relying party goes to the Repository to check validity of the Subscriber’s Certificate. 6. Repository returns copy of certificate and results of status check

Likely Candidates for “TTP” Role • Government Agencies • Financial Institutions • Employers (In their own COI )

Legal Framework • Government Paperwork Elimination Act (GPEA) – supports the use of electronic signatures for transactions with the Federal government – Enacted October 1998 – Covers user authentication and persistent electronic signatures

GPEA Background • With some qualifications, GPEA requires agencies by October 2003 to: – Accept forms (>50 K copies/year) electronically – Accept electronic signatures on forms and documents • Encourages electronic filing and electronic recordkeeping, particularly by employers

GPEA Background (continued) • Gives electronic signatures full legal effect • Technology neutral - agencies select based on specifics of applications (e. g. , risk) – But recognizes that technology neutrality does NOT mean all technologies are created equally • Focus: transactions with Federal agencies • Draft OMB Guidance 3/99; final 5/00

Electronic Signatures Under GPEA Guidance • OMB GPEA guidance recognizes several ways to effect “electronic signature” – – PINs/passwords Digitized signatures Biometrics Digital signatures • Each approach has advantages and disadvantages, some more acute than others

PINs/Passwords • Advantages: – Simple – Used ubiquitously, no “learning curve” • Disadvantages: – – – Shared secret means other party can compromise Hard to achieve non-repudiation Does not scale well - PINs/passwords proliferate Can be very susceptible to remote attack Parties must know each other beforehand

Digitized Signatures • Advantages: – Closest in appearance to “wet signature” • Disadvantages: – – – Form of shared secret No open standards, templates are usually proprietary Can be vulnerable to replay attack No cryptographic binding of identity to document Hard to achieve non-repudiation Requires additional hardware (stylus/pad)

Biometrics • Advantages: – Fingerprints, iris images impossible to “forget” • Disadvantages: – – – Form of shared secret No open standards, templates are usually proprietary Can be vulnerable to replay attack No cryptographic binding of identity to document Requires additional hardware (camera, pad) Can be hard to revoke old identity and issue new one

Digital Signatures • Advantages: – No shared secrets between remote parties – Cryptographic binding between identity and document – Scales well, interoperates reasonably well • Disadvantages: – Requires infrastructure (PKI) – Is more complex than PINs/passwords – Can require additional hardware (if smartcards are used)

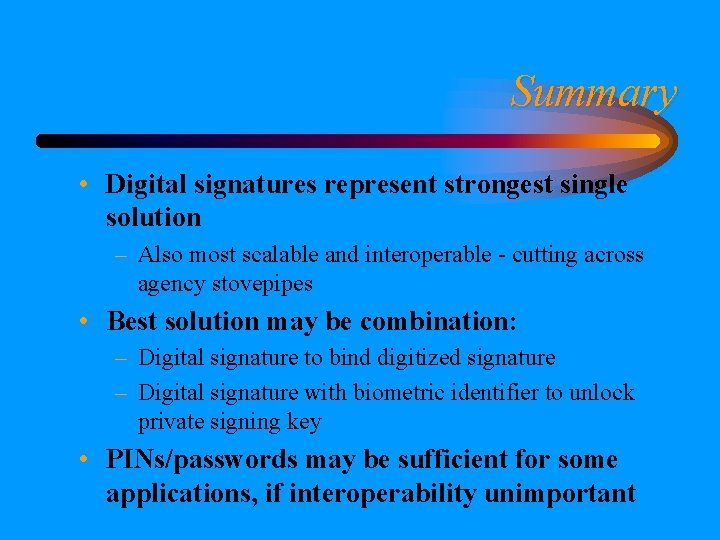
Summary • Digital signatures represent strongest single solution – Also most scalable and interoperable - cutting across agency stovepipes • Best solution may be combination: – Digital signature to bind digitized signature – Digital signature with biometric identifier to unlock private signing key • PINs/passwords may be sufficient for some applications, if interoperability unimportant

Privacy/ Disclosure: Basic Principles • Electronic authentication should only be required where needed • Tailor authentication needs to the transaction and the participants • Avoid collecting information that is more detailed than required • Inform participants that information will be managed pursuant to the Privacy Act, Computer Security Act, and other laws.

Legal Effect and Validity Electronic records submitted or maintained in accordance with procedures developed under this title, or electronic signatures or other forms of electronic authentication used in accordance with such procedures, shall not be denied legal effect, validity, or enforceability because such records are in electronic form. -GPEA, section 1707

Additional Legal Considerations • “Intent” at time of signing critical – Need for banners or other indicia • Need to capture entire document with signature - not just HTML “tags” • Need to retain ability to validate signature at later date (either directly or through “digital notary” • Electronic records management big issue - with or without electronic signatures
 Dsa in network security
Dsa in network security Egov.ba.it
Egov.ba.it Modalits
Modalits Forms.sc.egov.usda
Forms.sc.egov.usda Chinabank egov
Chinabank egov Egov kuwait
Egov kuwait Private securty
Private securty Cipher based message authentication code
Cipher based message authentication code Dashboard excel laporan keuangan
Dashboard excel laporan keuangan Nama kelompok matematika yang keren
Nama kelompok matematika yang keren Nama kelompok tugas
Nama kelompok tugas Nama kelompok fisika keren
Nama kelompok fisika keren Nama kelompok yang bagus
Nama kelompok yang bagus Nama kelompok fisika keren
Nama kelompok fisika keren Volume tabung
Volume tabung Ilil keren
Ilil keren Background ppt keren
Background ppt keren Nama kelompok matematika yang keren
Nama kelompok matematika yang keren Keren lasker
Keren lasker Nama ff keren smb
Nama ff keren smb Message authentication code
Message authentication code Dsa vs rsa digital signature
Dsa vs rsa digital signature Pfms digital signature
Pfms digital signature Diffie hellman digital signature
Diffie hellman digital signature Properties of digital signature
Properties of digital signature Rsa digital signature
Rsa digital signature Digital signature
Digital signature Digital signature authentication protocol
Digital signature authentication protocol Digital signature authentication protocol
Digital signature authentication protocol Digital signature forgery
Digital signature forgery