DIGITAL SIGNATURES Fred Piper Mert zarar Codes Ciphers























- Slides: 34

DIGITAL SIGNATURES Fred Piper & Mert Özarar Codes & Ciphers Ltd 12 Duncan Road Richmond Surrey TW 9 2 JD Information Security Group Royal Holloway, University of London Egham, Surrey TW 20 0 EX Digital Signatures

Outline 1. Brief Introduction to Cryptography 2. Public Key Systems 3. Basic Principles of Digital Signatures 4. Public Key Algorithms 5. Signing Processes 6. Arbitrated Signatures 7. Odds and Ends NOTE: We will not cover all the sections Digital Signatures 2

The Essence of Security – Recognition of those you know – Introduction to those you don’t know – Written signature – Private conversation Digital Signatures 3

The Challenge • Transplant these basic social mechanisms to the telecommunications and/or business environment. Digital Signatures 4

The Security Issues • Sender – Am I happy that the whole world sees this ? – Am I prepared to pay to stop them ? – Am I allowed to stop them ? • Recipient – Do I have confidence in : – the originator – the message contents and message stream – no future repudiation. • Network Manager – Do I allow this user on to the network ? – How do I control their privileges ? Digital Signatures 5

Cryptography is used to provide: 1. Secrecy 2. Data Integrity 3. User Verification 4. Non-Repudiation Digital Signatures 6

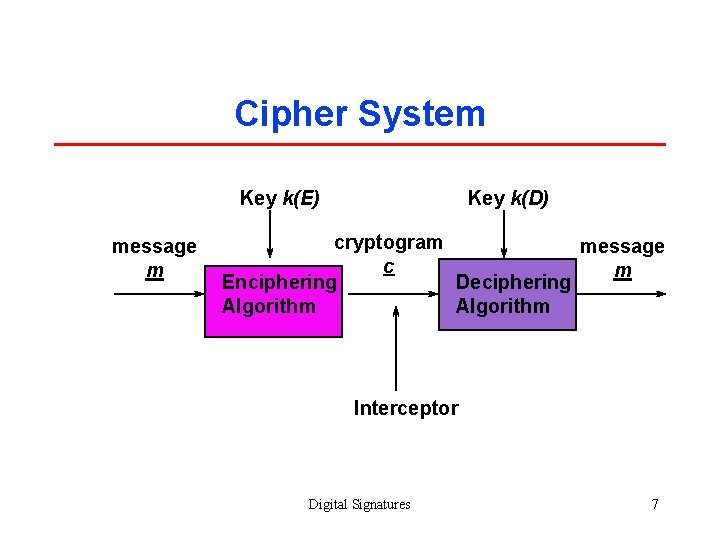
Cipher System Key k(E) message m Key k(D) cryptogram message c m Enciphering Deciphering Algorithm Interceptor Digital Signatures 7

The Attacker’s Perspective Unknown Key k(D) Known c Deciphering Wants m Algorithm Note: k(E) is not needed unless it helps determine k(D) Digital Signatures 8

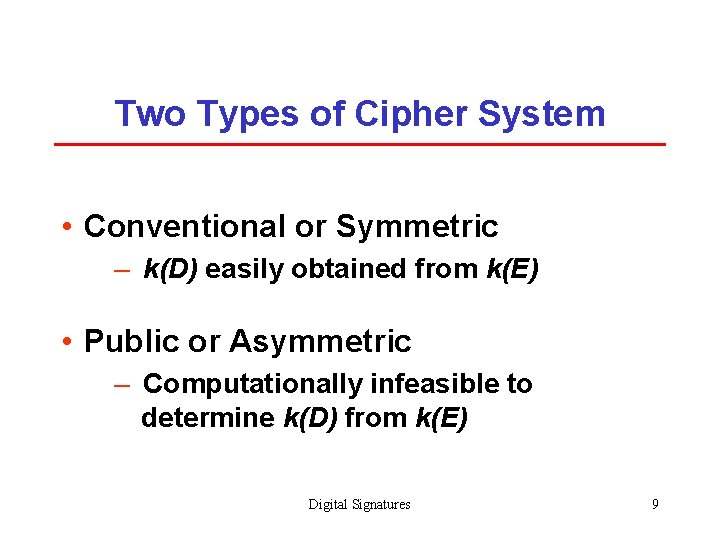
Two Types of Cipher System • Conventional or Symmetric – k(D) easily obtained from k(E) • Public or Asymmetric – Computationally infeasible to determine k(D) from k(E) Digital Signatures 9

• THE SECURITY OF THE SYSTEM IS DEPENDENT ON THE SECURITY OF THE KEYS Digital Signatures 10

Public Key Systems • Original Concept • For a public key system an enciphering algorithm is agreed and each would-be receiver publishes the key which anyone may use to send a message to him. • Thus for a public key system to be secure it must not be possible to deduce the message from a knowledge of the cryptogram and the enciphering key. Once such a system is set up, a directory of all receivers plus their enciphering keys is published. However, the only person to know any given receiver’s deciphering key is the receiver himself. Digital Signatures 11

Public Key Systems • For a public key system, encipherment must be a ‘one-way function’ which has a ‘trapdoor’. The trapdoor must be a secret known only to the receiver. • A ‘one-way function’ is one which is easy to perform but very difficult to reverse. A ‘trapdoor’ is a trick or another function which makes it easy to reverse the function Digital Signatures 12

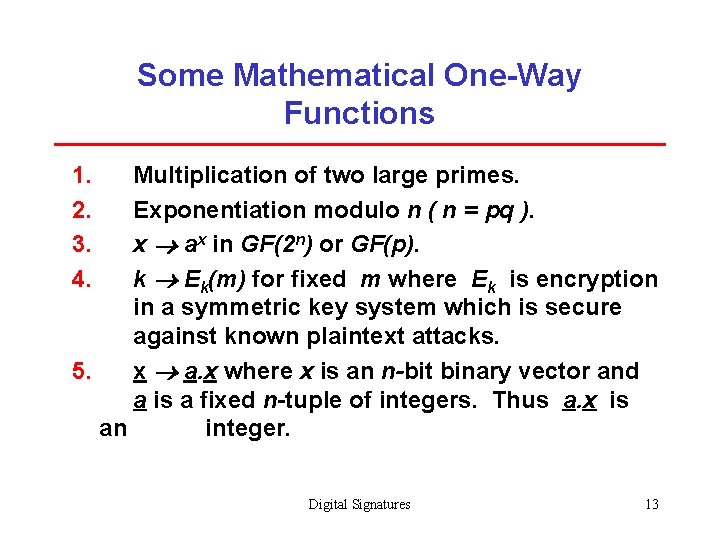
Some Mathematical One-Way Functions 1. 2. 3. 4. Multiplication of two large primes. Exponentiation modulo n ( n = pq ). x ax in GF(2 n) or GF(p). k Ek(m) for fixed m where Ek is encryption in a symmetric key system which is secure against known plaintext attacks. 5. x a. x where x is an n-bit binary vector and a is a fixed n-tuple of integers. Thus a. x is an integer. Digital Signatures 13

Public Key Cryptosystems – Enable secure communications without exchanging secret keys – Enable 3 rd party authentication ( digital signature ) – Use number theoretic techniques – Introduce a whole new set of problems – Are extremely ingenious. Digital Signatures 14

Digital Signatures • According to ISO, the term Digital Signature is used: ‘to indicate a particular authentication technique used to establish the origin of a message in order to settle disputes of what message (if any) was sent’. Digital Signatures 15

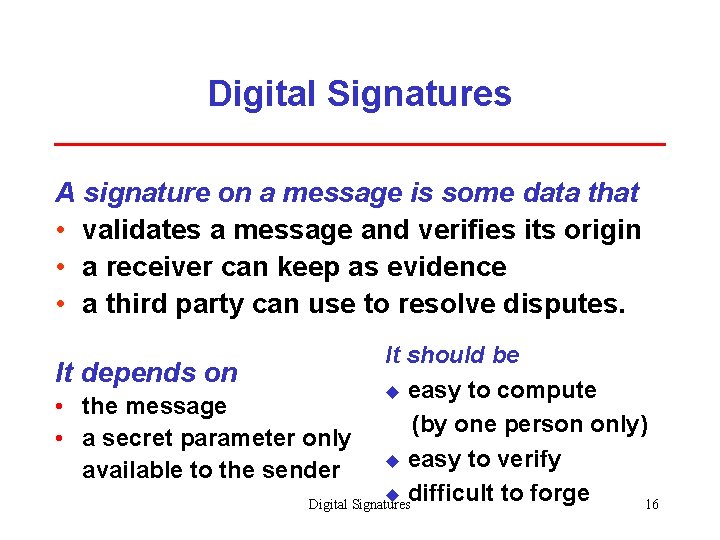
Digital Signatures A signature on a message is some data that • validates a message and verifies its origin • a receiver can keep as evidence • a third party can use to resolve disputes. It should be It depends on u easy to compute • the message (by one person only) • a secret parameter only u easy to verify available to the sender u difficult to forge Digital Signatures 16

Digital Signature • • Cryptographic checksum Identifies sender Provides integrity check for data Can be checked by third party Digital Signatures 17

Hand-Written Signatures • • Intrinsic to signer Same on all documents Physically attached to message Beware plastic cards. Digital Signatures • Use of secret parameter • Message dependent. Digital Signatures 18

Principle of Digital Signatures • • There is a (secret) number which: Only one person can use Is used to identify that person ‘Anyone’ can verify that it has been used NB: Anyone who knows the value of a number can use that number. Digital Signatures 19

Attacks on Digital Signature Schemes To impersonate A, I must either • obtain A’s private key • substitute my public key for A’s NB: Similar attacks if A is receiving secret data encrypted with A’s public key Digital Signatures 20

Obtaining a Private Key · Mathematical attacks · Physical attacks NB: It may be sufficient to obtain a device which contains the key. Knowledge of actual value is not needed. Digital Signatures 21

Certification Authority AIM : To guarantee the authenticity of public keys. METHOD : The Certification Authority guarantees the authenticity by signing a certificate containing user’s identity and public key with its secret key. REQUIREMENT : All users must have an authentic copy of the Certification Authority’s public key. Digital Signatures 22

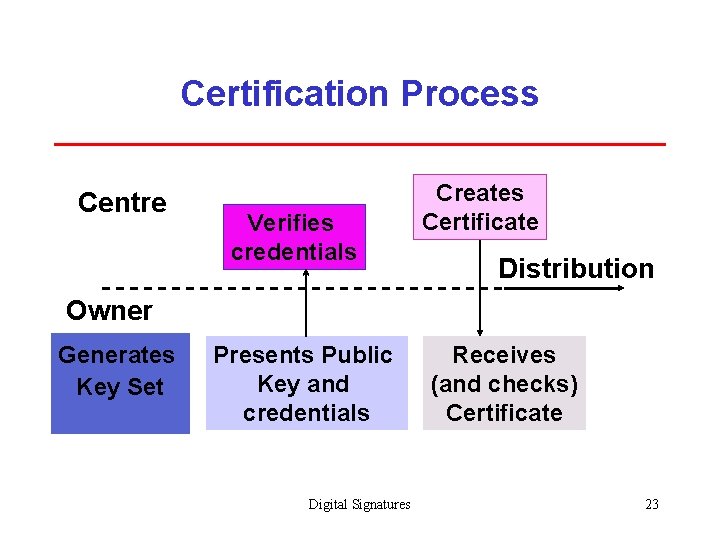
Certification Process Centre Verifies credentials Creates Certificate Distribution Owner Generates Key Set Presents Public Key and credentials Digital Signatures Receives (and checks) Certificate 23

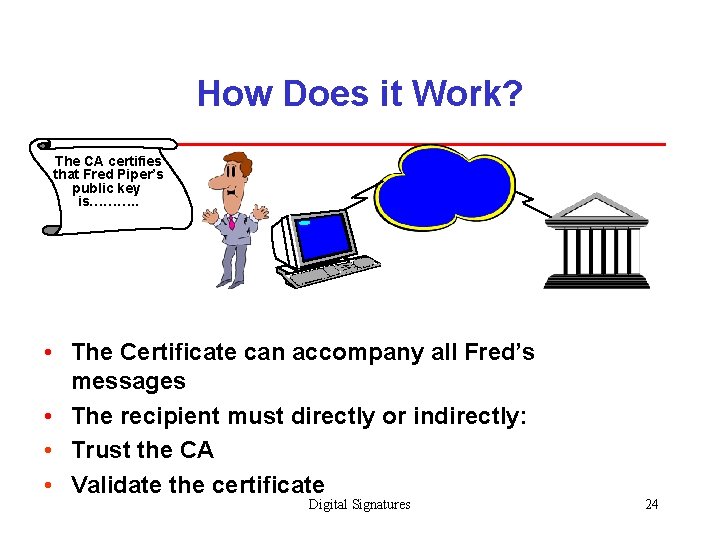
How Does it Work? The CA certifies that Fred Piper’s public key is………. . Electronically signed by the CA • The Certificate can accompany all Fred’s messages • The recipient must directly or indirectly: • Trust the CA • Validate the certificate Digital Signatures 24

User Authentication Certificates • Ownership of certificate does not establish identity • Need protocols establishing use of corresponding secret keys Digital Signatures 25

WARNING • Identity Theft • You ‘are’ your private key • You ‘are’ the private key corresponding to the public key in your certificiate Digital Signatures 26

Certification Authorities • • • Problems/Questions Who generates users’ keys? How is identity established? How can certificates be cancelled? Any others? Digital Signatures 27

Fundamental Requirement Internal infrastructure to support secure technological implementation Digital Signatures 28

Is everything OK? Announcement in Microsoft Security Bulletin MS 01 -017 “Veri. Sign Inc recently advised Microsoft that on January 29 -30 2001 it issued two Veri. Sign Class 3 codesigning digital certificates to an individual who fraudulently claimed to be a Microsoft employee. ” Digital Signatures 29

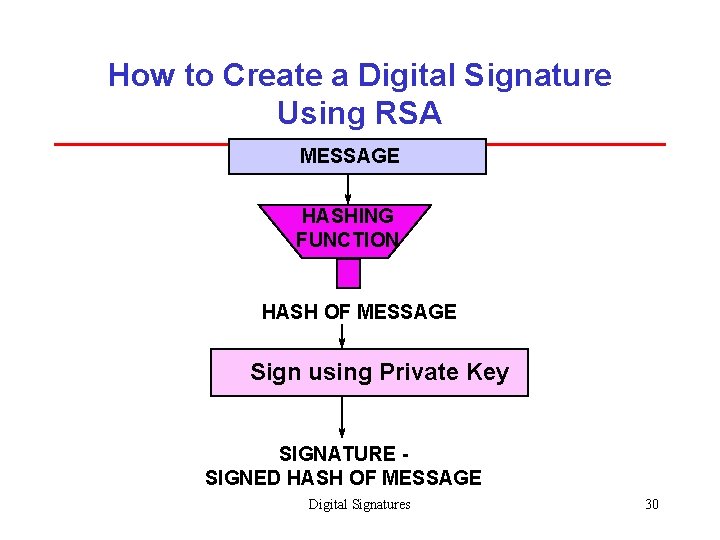
How to Create a Digital Signature Using RSA MESSAGE HASHING FUNCTION HASH OF MESSAGE Sign using Private Key SIGNATURE SIGNED HASH OF MESSAGE Digital Signatures 30

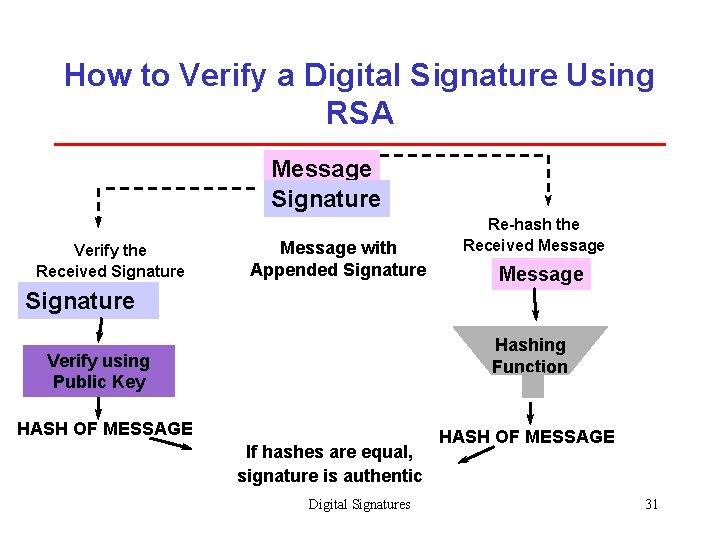
How to Verify a Digital Signature Using RSA Message Signature Verify the Received Signature Message with Appended Signature Re-hash the Received Message Signature Hashing Function Verify using Public Key HASH OF MESSAGE If hashes are equal, signature is authentic Digital Signatures HASH OF MESSAGE 31

Requirements for Hash Function h (H 1) condenses message M of arbitrary length into a fixed length ‘digest’ h(M) (H 2) is one-way (H 3) is collision free - it is computationally infeasible to construct messages M, M' with h(M) = h(M') H 3 implies a restriction on the size of h(M). Digital Signatures 32

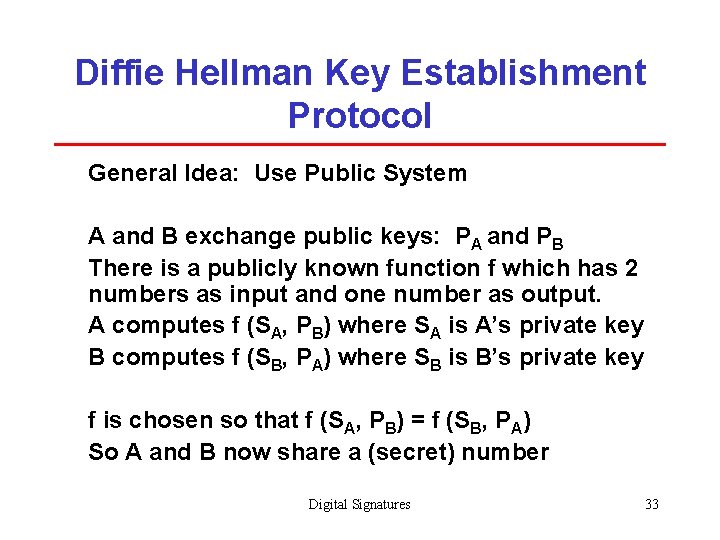
Diffie Hellman Key Establishment Protocol General Idea: Use Public System A and B exchange public keys: PA and PB There is a publicly known function f which has 2 numbers as input and one number as output. A computes f (SA, PB) where SA is A’s private key B computes f (SB, PA) where SB is B’s private key f is chosen so that f (SA, PB) = f (SB, PA) So A and B now share a (secret) number Digital Signatures 33

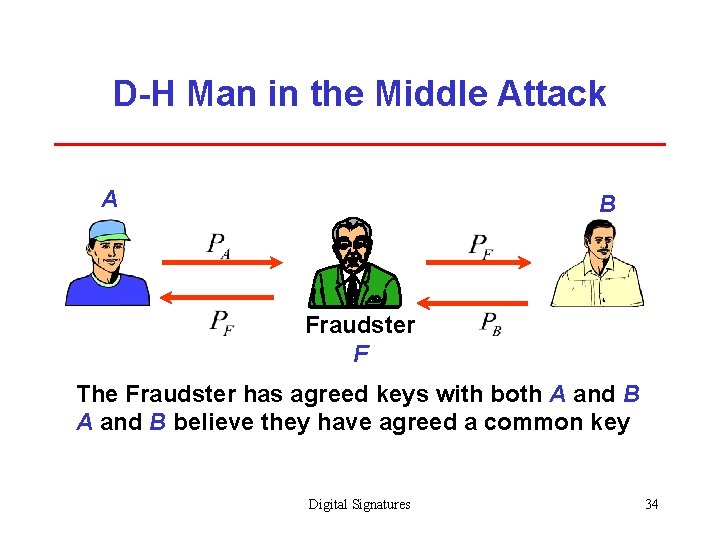
D-H Man in the Middle Attack A B Fraudster F The Fraudster has agreed keys with both A and B believe they have agreed a common key Digital Signatures 34