Impersonation Attacks Fred Piper Information Security Group Royal















- Slides: 31

Impersonation Attacks Fred Piper Information Security Group Royal Holloway, University of London Egham, Surrey TW 20 0 EX Codes & Ciphers Ltd 12 Duncan Road Richmond, Surrey TW 9 2 JD Crete - 2007 1

Outline • Information security • User recognition – Use of passwords/PINs/cryptogrphic keys – Use of ‘tokens’ • Phishing • Protection against man-in-the-middle attacks • Multi factor or multi channel? • The use of mobile phones as a ‘token’ for user recognition? Crete - 2007 2

What is Information Security? Some features include: • Confidentiality – Protecting information from unauthorised disclosure • Integrity – Protecting information from unauthorised modification, and • ensuring that information can be relied upon and is accurate and complete Availability – Ensuring information is available to authorised users when they need it Crete - 2007 3

Defences and Attacks Defences: • Introduce security mechanism to protect data – Technical – Procedural – Contractual • Introduce strong authentication mechanism Attacks: • Break the technical security mechanism • Impersonate an authorised entity by breaking procedural mechanism Crete - 2007 4

User Recognition (1) 3 factors: 1) Something you know (Password/PIN/Cryptographic 2) 3) Key) Something you own (Token) Personal characteristic (Biometrics) NOTE: Usually one-way authentication Tokens and biometrics often require ‘readers’ ‘Danger’ of false ‘readers’ Cost issues Crete - 2007 5

User Recognition (2) • Many systems rely on more than 1 factor • For multi-factor systems compromise of 1 factor should not enable impersonation • The PIN/magnetic stripe card for ATM networks is an example of a 2 -factor system where each individual factor is ‘weak’ Crete - 2007 6

Something You Know • Password • PIN • Cryptographic key Obvious observations: – A PIN is a password with limited alphabet – A cryptographic key may be regarded as a (secret) password which the user may use but probably not know – Policies for the management of PINs and Passwords are inconsistent Crete - 2007 7

Password Policy It is often recommended that: • Users should adopt a large alphabet (at least alpha- numeric with • • • upper and lower case letters) Passwords should be long (at least 8 characters? ) Passwords should be randomly generated Passwords should be different for each system Passwords should be changed frequently Passwords should not be written down Crete - 2007 8

PINs • Personal identification number • Usually 4 digits (sometimes 6) – Reason: users will not be able to remember longer PINs! NOTE: This is inconsistent with general password policy. Undoubtedly a weak password Crete - 2007 9

Cryptographic Keys • It is the use of a cryptographic key, rather than revealing its value, that identifies a user Crete - 2007 10

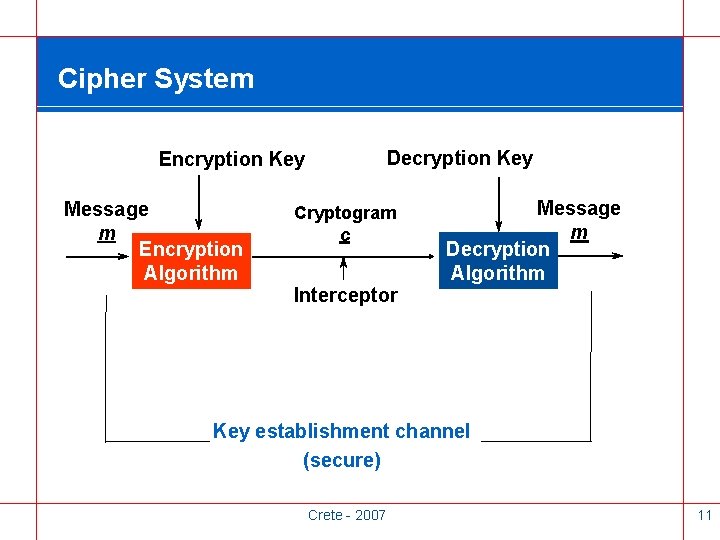
Cipher System Decryption Key Encryption Key Message m Encryption Algorithm Cryptogram c Interceptor Message m Decryption Algorithm Key establishment channel (secure) Crete - 2007 11

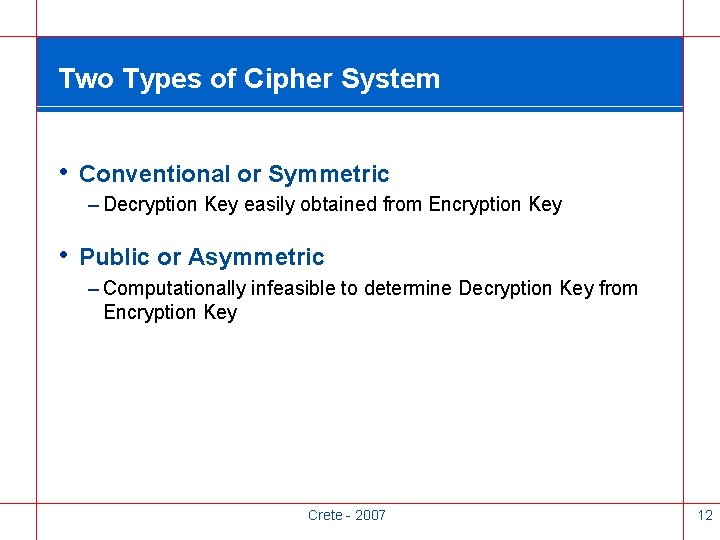
Two Types of Cipher System • Conventional or Symmetric – Decryption Key easily obtained from Encryption Key • Public or Asymmetric – Computationally infeasible to determine Decryption Key from Encryption Key Crete - 2007 12

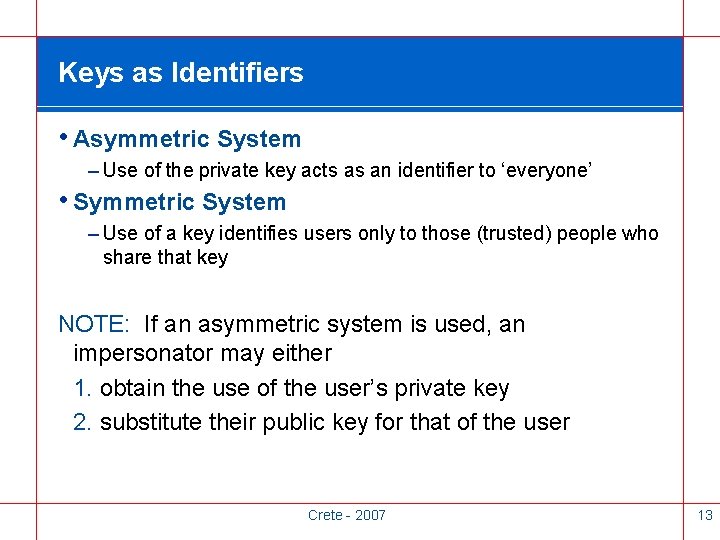
Keys as Identifiers • Asymmetric System – Use of the private key acts as an identifier to ‘everyone’ • Symmetric System – Use of a key identifies users only to those (trusted) people who share that key NOTE: If an asymmetric system is used, an impersonator may either 1. obtain the use of the user’s private key 2. substitute their public key for that of the user Crete - 2007 13

Authentication Using Smart Tokens • Static Password Tokens – Owner authenticates himself to token – Token identified owner to system • Dynamic Password Tokens – Token generates new password – (Owner activates token with PIN) – Owner enters ID plus dynamic password – System knows which dynamic password to accept • Challenge-Response Tokens – System generates challenges – Owner activates token with PIN and enters challenge – Token generates response (probably challenge encrypted with key that is unique to token) – System knows which response to accept Crete - 2007 14

Dynamic Passwords User’s password changes frequently (possibly at each login) Change influenced by at least one of: • Secret information known to user • Intelligent device which is unique to user Crete - 2007 15

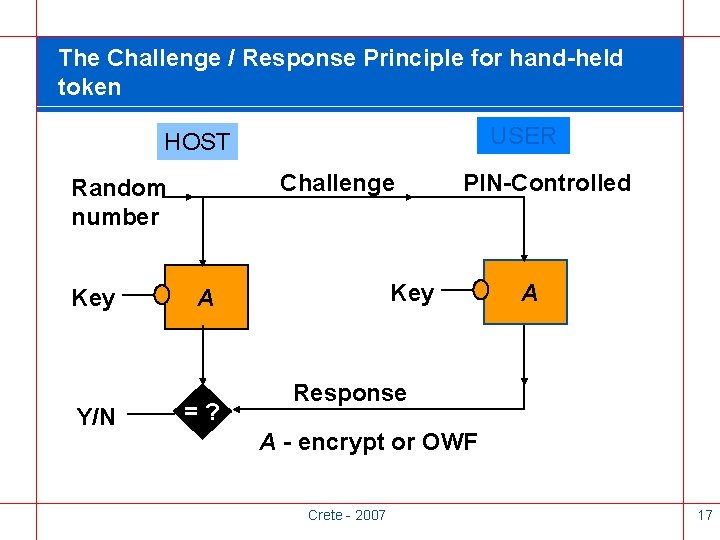
Challenge/Response for Dynamic Password Given an unpredictable challenge, user’s token produces a response which is: • Appropriate to the challenge • Dependent on a user’s token • Dependent on user’s knowledge Crete - 2007 16

The Challenge / Response Principle for hand-held token USER HOST Challenge Random number Key Y/N Key A =? PIN-Controlled A Response A - encrypt or OWF Crete - 2007 17

Impersonation Attacks • 1 -way authentication – – Steal and/or copy token Guess or ‘observe’ password/PIN/cryptographic key Con the user into divulging password/PIN eg phishing Gain access to device using key • 2 -way authentication – Man-in-the-middle Crete - 2007 18

Phishing Attacks (1) • Social engineering • Attacker discovers secret ‘information known’ • Banking customers have been ‘prime’ targets via email messages and fake websites Crete - 2007 19

Phishing Attacks (2) Countermeasures • User education/awareness • Use of 2 or 3 factor systems so that compromise of 1 factor has limited impact Crete - 2007 20

Identification over the Internet • Many applications use 2 -factor systems that allow ‘card not present’ transactions • Effectively a physical token is replaced by a virtual token which is nothing more than a card number • This is a 1 -factor system • In Singapore the FA mandates use of genuine 2 -factor authentication • In UK banks are starting to issue customers with Chip and PIN ‘readers’ Crete - 2007 21

Phishing • Browsers starting to try to detect fake websites – Google Safe Browsing for Firefox browser – Microsoft’s Internet Explorer 7 • Anti-Phishing War Group (APWG) – Forum to discuss phishing issues and share best practices – www. antiphishing. org Crete - 2007 22

Phishing Attacks Summary • • • Enable attacks to discover secret ‘information known’ ‘Best’ countermeasure is user education/awareness Effectiveness of attack decreases for 2 or 3 factor systems Use of conventional 2 or 3 factors often expensive and needs special hardware Introduction of ‘one-time’ PINs such as ITANs for some German ebanking systems helps Crete - 2007 23

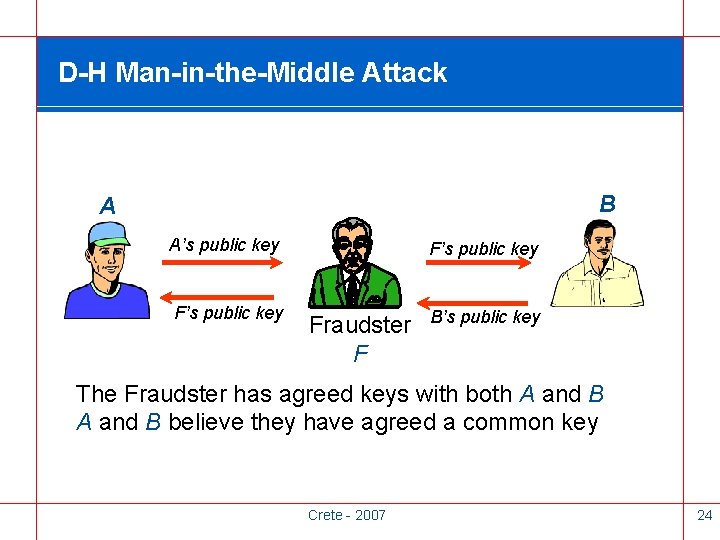
D-H Man-in-the-Middle Attack B A A’s public key F’s public key Fraudster F B’s public key The Fraudster has agreed keys with both A and B believe they have agreed a common key Crete - 2007 24

Protection Against Man-in-the-Middle Attack • Rely on TTP to establish key management infrastructure (eg PKI) • Use second (independent) communications channel to confirm key between A and B (Over) Simple Example: – D-H protocol establishes 1024 shared bits – AES key is 128 bits from agreed positions – Users exchange different 32 -bit sequences from the 1024 bits over second (possibly insecure) channel Crete - 2007 25

OOB (Out of Band) Authentication Requirement • A user claims an identity over a computer network • Host wants to use a second channel to confirm it is the genuine user • Neither party is willing to pay for ‘extra hardware’ Crete - 2007 26

Use of Two Channels • Prior to PK crypto, most cryptographic systems needed a second (secure) channel for initial key establishment • One motivation for introduction of PK crypto Crete - 2007 27

OOB Communications • Symmetric cryptography – Use secure second channel to enable secure communications over an insecure primary channel • Authentication – Use second (possibly insecure) channel to confirm that the communications over the primary channel are secure NOTE: In this context an insecure channel is one where interception is possible. Crete - 2007 28

Communications How does ‘token’ communicate with host: • One channel or two channel system? • One-way or two-way authentication? • What is the interface? – The user? – A reader that is part of the network? – Other? Crete - 2007 29

Mobile Phones • There is a move towards systems where the mobile phone is ‘something you own’ • No reader required • No extra cost (in the sense that most people have them) • Use their own channel • Security implications? Crete - 2007 30

Question • Are there situations where using the mobile phone as a token in a 2 -factor system and using a second communication channel can decrease the chance of successful impersonation attacks? Crete - 2007 31