Digital Signatures CCA Controller of Certifying Authorities Ministry



![RSA Key pair (including Algorithm identifier) [2048 bit] Private Key 3082 06 d 3 RSA Key pair (including Algorithm identifier) [2048 bit] Private Key 3082 06 d 3](https://slidetodoc.com/presentation_image_h2/3020374d505a346c04887f479ddb85ec/image-11.jpg)
![• Key Generation – Random Numbers – RSA Key Pair [Private/Public Key] • • Key Generation – Random Numbers – RSA Key Pair [Private/Public Key] •](https://slidetodoc.com/presentation_image_h2/3020374d505a346c04887f479ddb85ec/image-14.jpg)















- Slides: 35

Digital Signatures CCA Controller of Certifying Authorities Ministry of Communications & Information Technology

Electronic Record 1. Very easy to make copies 2. Very fast distribution 3. Easy archiving and retrieval 4. Copies are as good as original 5. Easily modifiable 6. Environmental Friendly Because of 4 & 5 together, these lack authenticity

Why Digital Signatures? • To provide Authenticity, Integrity and Nonrepudiation to electronic documents • To use the Internet as the safe and secure medium for e-Commerce and e. Governance

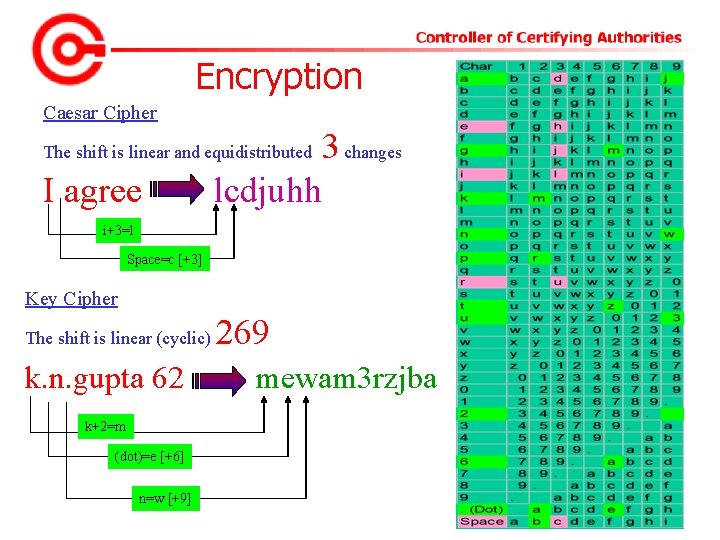
Encryption Caesar Cipher 3 changes lcdjuhh The shift is linear and equidistributed I agree i+3=l Space=c [+3] Key Cipher The shift is linear (cyclic) k. n. gupta 62 k+2=m (dot)=e [+6] n=w [+9] 269 mewam 3 rzjba

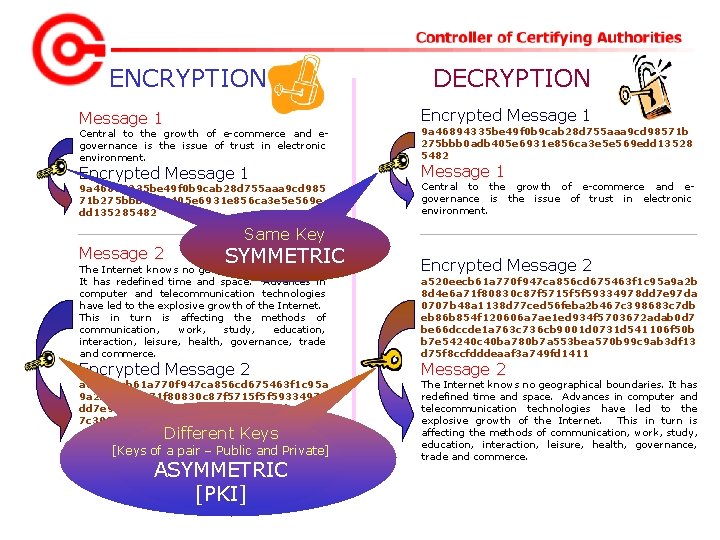
ENCRYPTION DECRYPTION Message 1 Encrypted Message 1 Central to the growth of e-commerce and egovernance is the issue of trust in electronic environment. 9 a 46894335 be 49 f 0 b 9 cab 28 d 755 aaa 9 cd 98571 b 275 bbb 0 adb 405 e 6931 e 856 ca 3 e 5 e 569 edd 13528 5482 9 a 46894335 be 49 f 0 b 9 cab 28 d 755 aaa 9 cd 985 71 b 275 bbb 0 adb 405 e 6931 e 856 ca 3 e 5 e 569 e dd 135285482 Central to the growth of e-commerce and egovernance is the issue of trust in electronic environment. Message 2 Same Key SYMMETRIC The Internet knows no geographical boundaries. It has redefined time and space. Advances in computer and telecommunication technologies have led to the explosive growth of the Internet. This in turn is affecting the methods of communication, work, study, education, interaction, leisure, health, governance, trade and commerce. Encrypted Message 2 a 520 eecb 61 a 770 f 947 ca 856 cd 675463 f 1 c 95 a 9 a 2 b 8 d 4 e 6 a 71 f 80830 c 87 f 5715 f 5 f 59334978 dd 7 e 97 da 0707 b 48 a 1138 d 77 ced 56 feba 2 b 46 7 c 398683 c 7 dbeb 86 b 854 f 120606 a 7 ae 1 ed 93 4 f 5703672 adab 0 d 7 be 66 dccde 1 a 763 c 736 cb 9001 d 0731 d 541106 f 50 bb 7 e 54240 c 40 ba 78 [Keys of a pair – Public and Private] 0 b 7 a 553 bea 570 b 99 c 9 ab 3 df 13 d 75 f 8 ccfddde aaf 3 a 749 fd 1411 Different Keys ASYMMETRIC [PKI] Encrypted Message 2 a 520 eecb 61 a 770 f 947 ca 856 cd 675463 f 1 c 95 a 9 a 2 b 8 d 4 e 6 a 71 f 80830 c 87 f 5715 f 5 f 59334978 dd 7 e 97 da 0707 b 48 a 1138 d 77 ced 56 feba 2 b 467 c 398683 c 7 db eb 86 b 854 f 120606 a 7 ae 1 ed 934 f 5703672 adab 0 d 7 be 66 dccde 1 a 763 c 736 cb 9001 d 0731 d 541106 f 50 b b 7 e 54240 c 40 ba 780 b 7 a 553 bea 570 b 99 c 9 ab 3 df 13 d 75 f 8 ccfdddeaaf 3 a 749 fd 1411 Message 2 The Internet knows no geographical boundaries. It has redefined time and space. Advances in computer and telecommunication technologies have led to the explosive growth of the Internet. This in turn is affecting the methods of communication, work, study, education, interaction, leisure, health, governance, trade and commerce.


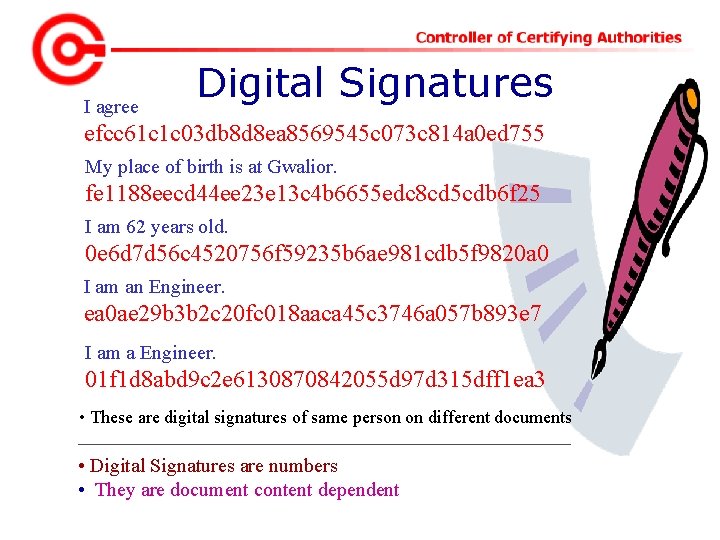
I agree Digital Signatures efcc 61 c 1 c 03 db 8 d 8 ea 8569545 c 073 c 814 a 0 ed 755 My place of birth is at Gwalior. fe 1188 eecd 44 ee 23 e 13 c 4 b 6655 edc 8 cd 5 cdb 6 f 25 I am 62 years old. 0 e 6 d 7 d 56 c 4520756 f 59235 b 6 ae 981 cdb 5 f 9820 a 0 I am an Engineer. ea 0 ae 29 b 3 b 2 c 20 fc 018 aaca 45 c 3746 a 057 b 893 e 7 I am a Engineer. 01 f 1 d 8 abd 9 c 2 e 6130870842055 d 97 d 315 dff 1 ea 3 • These are digital signatures of same person on different documents • Digital Signatures are numbers • They are document content dependent

Concepts • A 1024 bits number is a very big number much bigger than the total number of electrons in whole world. • Trillions of pairs of numbers exist in this range with each pair having following property – A message encrypted with one element of the pair can be decrypted ONLY by the other element of the same pair • Two numbers of a pair are called keys, the Public Key & the Private Key. User himself generates his own key pair on his computer • Any message irrespective of its length can be compressed or abridged uniquely into a smaller length message called the Digest or the Hash. • Smallest change in the message will change the Hash value Click for Hash Generation

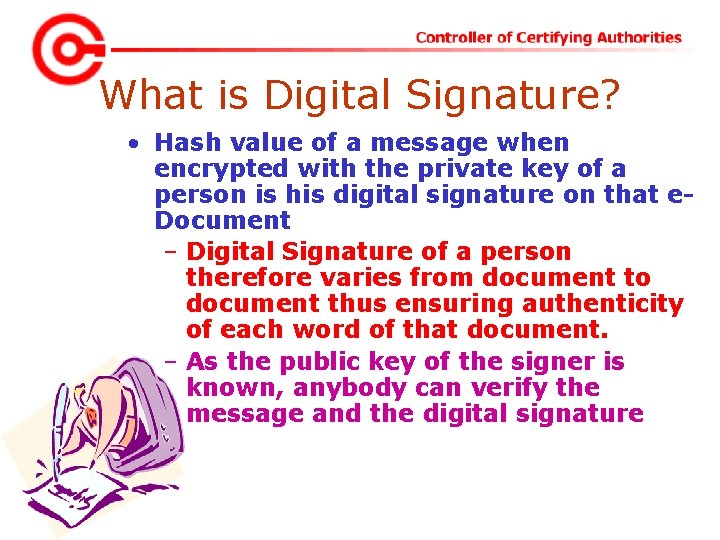
What is Digital Signature? • Hash value of a message when encrypted with the private key of a person is his digital signature on that e. Document – Digital Signature of a person therefore varies from document to document thus ensuring authenticity of each word of that document. – As the public key of the signer is known, anybody can verify the message and the digital signature

Digital Signatures Each individual generates his own key pair [Public key known to everyone & Private key only to the owner] Private Key – Used for making digital signature Public Key – Used to verify the digital signature
![RSA Key pair including Algorithm identifier 2048 bit Private Key 3082 06 d 3 RSA Key pair (including Algorithm identifier) [2048 bit] Private Key 3082 06 d 3](https://slidetodoc.com/presentation_image_h2/3020374d505a346c04887f479ddb85ec/image-11.jpg)
RSA Key pair (including Algorithm identifier) [2048 bit] Private Key 3082 06 d 3 d 854 463 d b 35 f cf 42 6 c 89 b 4 f 8 04 e 3 010 a 0 d 59 0 aa 5 1 ef 0 5 a 22 b 2 f 0 2 aca cdf 9 459 e 0282 bd 3 e 2586 b 92 c 97 ec 1 cd 5 da 33 f 400 a 146 0101 c 1 ce 94 ed 345 f 199 b 5 ffb 1379 84 b 6 2840 00 b 1 4367 6356 8 c 7 c c 105 6 bed c 255 5742 8102 d 311 018 a ff 70 4 c 08 68 fd 6856 8 ced 859 d 0301 e 079 21 a 8 6 ca 3 299 d e 6 b 7 7 b 39 9 cbb 32 a 8 0001 5543 efbc a 119 4055 a 991 2 c 72 f 2 cb f 92 a 0708 ccd 0 d 278 eb 3 c 942 c 38 b 0 5 b 10 54 fb 4 ccb a 2 cc be 68 7 d 83 e 478 ee 93 f 82 e ff 78 0542 b 055 2 a 44 deb 5 4824 a 9 d 3 6135 41 bc 00 e 2 9653 5 e 2 f f 0 f 7 1 a 25 7 b 77 c 629 bd 71 0 d 83 8466 cfcc 8 a 83 193 a 3 ceb 4 c 2 a 28 f 4 Public Key 3082 0673 d 8 b 4 463 d b 35 f cf 42 6 c 89 b 4 f 8 04 de 01 e 4 0 d 59 0 aa 5 1 df 0 5 a 22 b 250 2 aca cdf 9 45 de f 267 bf 3 e 2586 b 92 c 97 ec 1 cd 5 da 33 f 400 af 46 0142 c 1 ce 94 ed 345 f 199 b 5 ffb 1379 84 b 6 2240 0 f 61 4367 6356 8 c 7 c c 105 6 bed c 255 5742 8410 dd 12 012 a ff 70 4 c 08 68 fd 6856 8 ced 859 d 02 f 1 e 089 11 a 8 6 ca 3 299 d e 6 b 7 7 b 39 9 cbb 32 a 8 0001 5547 efbc a 119 4055 a 991 2 c 72 f 2 cb f 92 a 0 f 08 ccd 0 d 278 eb 3 c 942 c 38 b 0 5 b 10 54 fb 4 ccb a 2 cc be 68 7 d 83 e 478 ee 93 f 82 e ff 78 0542 b 055 2 a 44 deb 5 4824 a 9 d 3 6135 41 bc 00 e 2 9653 5 e 2 f f 0 f 7 1 a 25 7 b 77 c 629 bd 71 0 d 83 8466 cfcc 8 a 83 193 a 3 ceb 4 c 2 a 28 f 4 463 d 0500 185 e 0 ea 1 eb 95 7103 d 02 a bb 90 e 493 da 44 47 bc 4 cb 4 9 c 39 a 938 63 d 1 bcff bab 6 4980 3 ab 1 3 aa 5 0 a 8 a 4 a 16 6559 9634

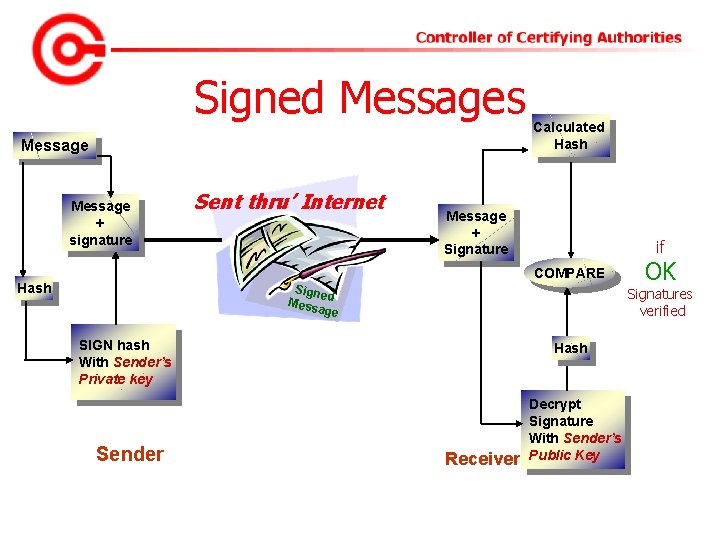
Signed Messages Message + signature Sent thru’ Internet Calculated Hash Message + Signature if COMPARE Hash Signe Mess d age Signatures verified SIGN hash With Sender’s Private key Sender OK Hash Receiver Decrypt Signature With Sender’s Public Key

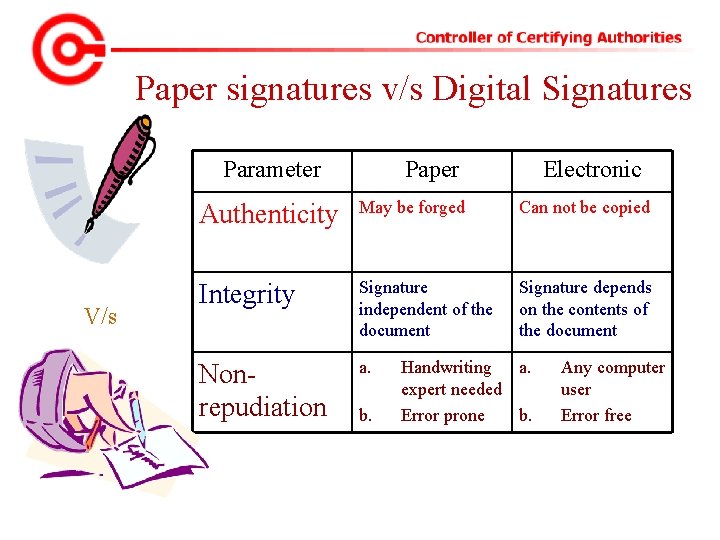
Paper signatures v/s Digital Signatures Parameter V/s Paper Electronic Authenticity May be forged Can not be copied Integrity Signature independent of the document Signature depends on the contents of the document Nonrepudiation a. b. Handwriting a. expert needed Error prone b. Any computer user Error free
![Key Generation Random Numbers RSA Key Pair PrivatePublic Key • Key Generation – Random Numbers – RSA Key Pair [Private/Public Key] •](https://slidetodoc.com/presentation_image_h2/3020374d505a346c04887f479ddb85ec/image-14.jpg)
• Key Generation – Random Numbers – RSA Key Pair [Private/Public Key] • Digital Signature – Generate Message Digest [SHA 1] – Encrypting Digest using Private Key [Signatures] – Attaching the Signatures to the message. • Verification of Signatures – Run the test for Authentication, Integrity and Non repudiation. • Digital Signature Certificate – ITU X. 509 v 3

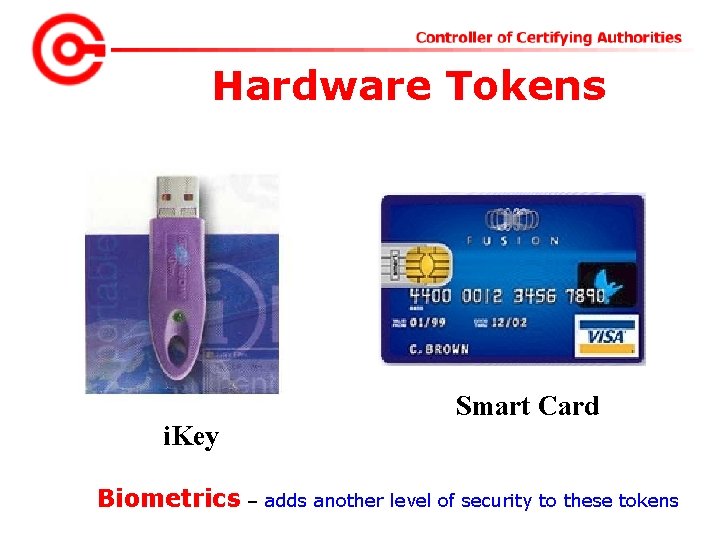
Private key protection • The Private key generated is to be protected and kept secret. The responsibility of the secrecy of the key lies with the owner. • The key is secured using – PIN Protected soft token – Smart Cards – Hardware Tokens

PIN protected soft tokens • • The Private key is encrypted and kept on the Hard Disk in a file, this file is password protected. This forms the lowest level of security in protecting the key, as – The key is highly reachable. – PIN can be easily known or cracked. • Soft tokens are also not preferred because – The key becomes static and machine dependent. – The key is in known file format.

Smart Cards • • The Private key is generated in the crypto module residing in the smart card. The key is kept in the memory of the smart card. The key is highly secured as it doesn’t leave the card, the message digest is sent inside the card for signing, and the signatures leave the card. The card gives mobility to the key and signing can be done on any system. (Having smart card reader)

Hardware Tokens • They are similar to smart cards in functionality as – Key is generated inside the token. – Key is highly secured as it doesn’t leave the token. – Highly portable. – Machine Independent. • i. KEY is one of the most commonly used token as it doesn’t need a special reader and can be connected to the system using USB port.

Hardware Tokens i. Key Smart Card Biometrics – adds another level of security to these tokens


Public Key Infrastructure (PKI) • Some Trusted Agency is required which certifies the association of an individual with the key pair. Certifying Authority (CA) • This association is done by issuing a certificate to the user by the CA Public key certificate (PKC) • All public key certificates are digitally signed by the CA

Certifying Authority • • Must be widely known and trusted • • Must have well defined Identification process before issuing the certificate issuing • • Provides online access to all the certificates issued • • Provides online access to to the list of of certificates revoked • • Displays online the license issued by by the Controller • • Displays online approved Certification Practice Statement (CPS) • • Must adhere to to IT IT Act/Rules/Regulations and Guidelines

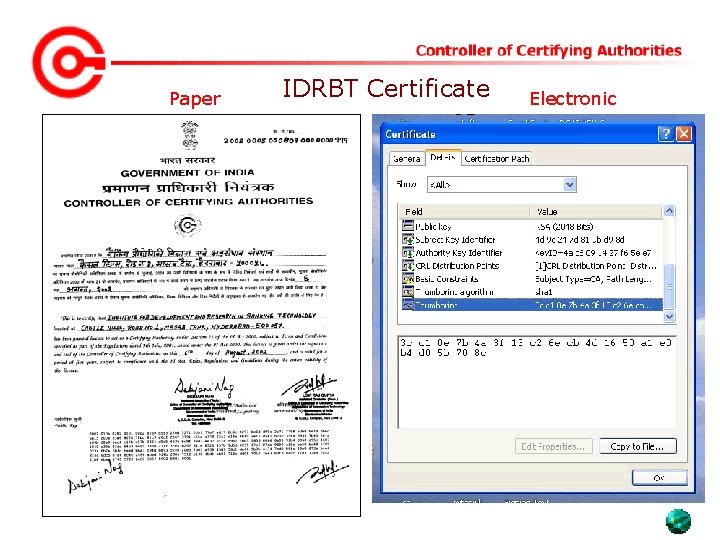
Paper IDRBT Certificate Electronic

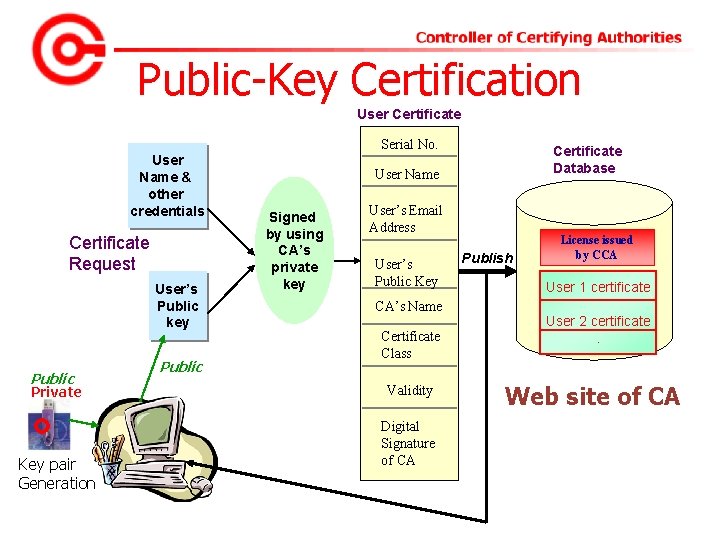
Public-Key Certification User Certificate Serial No. User Name & other credentials Certificate Request User’s Public key Public Private Key pair Generation Public Certificate Database User Name Signed by using CA’s private key User’s Email Address User’s Public Key CA’s Name Certificate Class Validity Digital Signature of CA Publish License issued by CCA User 1 certificate User 2 certificate. Web site of CA

Private key of CA or CCA require highest level of security Hardware Security Module (HSM) is used for storing the Private Key More than one person are required for signing HSM is housed in a strong room with video surveillance on 24 x 7 basis. Click for certificate generation demo

Trust Path • Controller is the Root certifying authority responsible for regulating Certifying Authorities (CAs) • Controller certifies the association of CA with his public key • Certifying Authority (CA) is the trusted authority responsible for creating or certifying identities. • CA certifies the association of an individual with his public key

Role of controller Controller of Certifying Authorities as the “Root” Authority certifies the technologies, infrastructure and practices of all the Certifying Authorities licensed to issue Digital Signature Certificates

Summary • Each individual has a pair of keys • Public key of each individual is certified by a CA (Certifying Authority) • Public keys of CAs are certified by the Controller • Public key of the Controller is self certified • Public keys of everyone are known to all concerned and are also available on the web • Certification Practice Statement is displayed on the web site

Applications in Judiciary 1. Instant posting of judgment on the web. 2. Secured electronic communications within judiciary 3. Authentic archiving of Judicial records 4. Submission of affidavits 5. Giving certified copies of the Judgment

Applications in Telecommunications A. Subscribers Ø Subscriber’s services management • STD/ISD, Opening, Closing, Initializing Password Ø Shifting of telephones, Accessories (Clip, Cordless) Ø Small Payments through telephones bills • Books, gifts, Internet purchases Ø Mobile Authentication of SMS • Share market trading, Intra/Inter office instructions Ø Mobile Phones as Credit cards • Mobile operator can venture into credit card business

Applications in Telecommunications (contd. ) B. Internal Ø Intra/Inter offices authentic communications • OBs, approvals, Instructions, requests Ø Procurement of material • Calling/Receiving bids, Purchase orders, Payment instructions Ø Network Management functions • Change of configuration, Blocking/unblocking routes

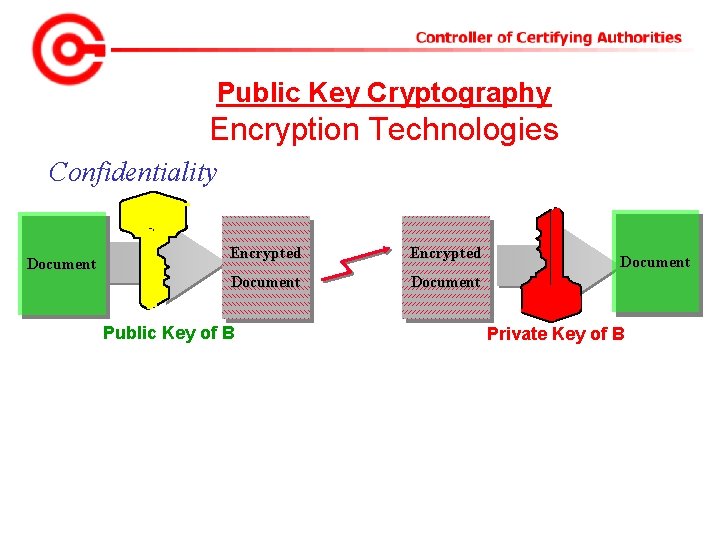
Public Key Cryptography Encryption Technologies Confidentiality Document Encrypted Document Public Key of B Document Private Key of B

E-Governance • Empowering Citizens a) b) c) d) Transparency Accountability Elimination of Intermediatory Encouraging Citizens to exercise their Rights

Government Online 1. Issuing forms and licences 2. Filing tax returns online 3. Online Government orders/treasury orders 4. Registration 5. Online file movement system 6. Public information records 7. E-voting 8. Railway reservations & ticketing 9. E-education 10. Online money orders

Thank You
 Death confirmation geeky medics
Death confirmation geeky medics Digital signature
Digital signature Order of sharps
Order of sharps Exchange 2007 signatures
Exchange 2007 signatures Uncitral model law on international commercial arbitration
Uncitral model law on international commercial arbitration Parallel key signatures
Parallel key signatures Uncitral model law on electronic signatures
Uncitral model law on electronic signatures Ocaml signatures
Ocaml signatures Spectral signatures
Spectral signatures Intruders use virus signatures fabricate
Intruders use virus signatures fabricate Martin kreitman
Martin kreitman Compact multi-signatures for smaller blockchains
Compact multi-signatures for smaller blockchains Digital logic controller
Digital logic controller State feedback controller design example
State feedback controller design example True digital controller
True digital controller Importance of lok adalat
Importance of lok adalat Clarisse is jailed by the authorities for her beliefs.
Clarisse is jailed by the authorities for her beliefs. Lds general authorities seniority
Lds general authorities seniority Types of authority
Types of authority Fthun
Fthun Authorities refers to
Authorities refers to Code of ethics for professional teachers article 7
Code of ethics for professional teachers article 7 Asia pacific privacy authorities
Asia pacific privacy authorities Hubs and authorities
Hubs and authorities Ahj authority having jurisdiction
Ahj authority having jurisdiction American society of agronomy cca
American society of agronomy cca Cisco sbcs
Cisco sbcs Cca
Cca Cca grading
Cca grading Cca
Cca Cca
Cca Boon lay garden primary school
Boon lay garden primary school Greendale secondary school cca
Greendale secondary school cca Depreciation tax shield formula
Depreciation tax shield formula Cca ipn
Cca ipn Cca csn review
Cca csn review