CS 5103 Software Engineering Lecture 18 Security Issues








![Feed in a valid input Ø Example “username” char[12] buffer Feed in a valid input Ø Example “username” char[12] buffer](https://slidetodoc.com/presentation_image_h2/dbf5e8dd94e3f2793dfaf187332ab84b/image-11.jpg)

















- Slides: 39

CS 5103 Software Engineering Lecture 18 Security Issues in Software Engineering & Final Exam

Last class Ø Ø 2 Delta Debugging Ø Motivation Ø Algorithm Ø In practice Static Bug Detection Ø Common Bugs Ø Find. Bugs

Today’s class Ø Security Issues in Software Engineering Ø Security Threats Ø Requirement Engineering for Security Ø Design for Security Ø Coding for Security Ø Ø 3 Vulnerabilities Testing for Security

Security Threats to Software Ø Ø Undermine usability Ø DOS attacks Ø Peculiar inputs causing crashes, bloats, … Information Leaking Ø Ø Command Control Ø 4 SQL Injection, Cross-site Scripting, unencrypted data, side channels, … OS Injection, Cross-site Scripting, Return Oriented Programming, …

Requirement Engineering for Security Ø Security properties in the specification Ø Users have different privileges for using functionalities? Ø Data should be seen only by certain users? Ø Ø Ø 5 Certain communications and data transfer happens in a safe network or not? Potential source of attacks Ø Any user can use the software? Ø Access to the Internet? Ø The motive of attacking the software? Risk of attacks Ø Estimate the cost if the software is attacked successfully? Ø How important the user data is?

Design for Security Ø The security techniques you choose to protect your software from attacks Ø Ø Ø 6 Input validation: single points, multiple points? Authentication: store and transfer credentials (passwords): where to do the encryption or just store verifier Sensitive data: decide what data needs to be encrypted, minimize the data to be stored Encryption: minimize the length of data flow before they reach the encryption, use known encryption algorithms Auditing and Logging

Coding for security Ø 7 Avoid common vulnerabilities Ø Buffer Overflow Ø Injection Ø Cross-Site Scripting

Buffer Overflow Ø Ø Quite many languages (C, C++) are memory unsafe You define a buffer, and it is your responsibility to keep your data in the buffer char buffer[12]; Ø 8 If you read or write to the place out of a buffer Ø Semantic errors Ø Crashes Ø What else? Anything related to security?

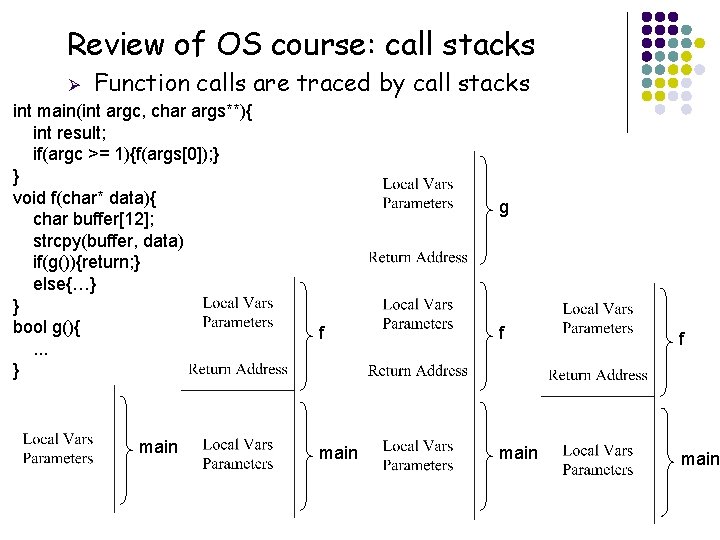
Review of OS course: call stacks Ø Function calls are traced by call stacks int main(int argc, char args**){ int result; if(argc >= 1){f(args[0]); } } void f(char* data){ char buffer[12]; strcpy(buffer, data) if(g()){return; } else{…} } bool g(){. . . } main g f f f main

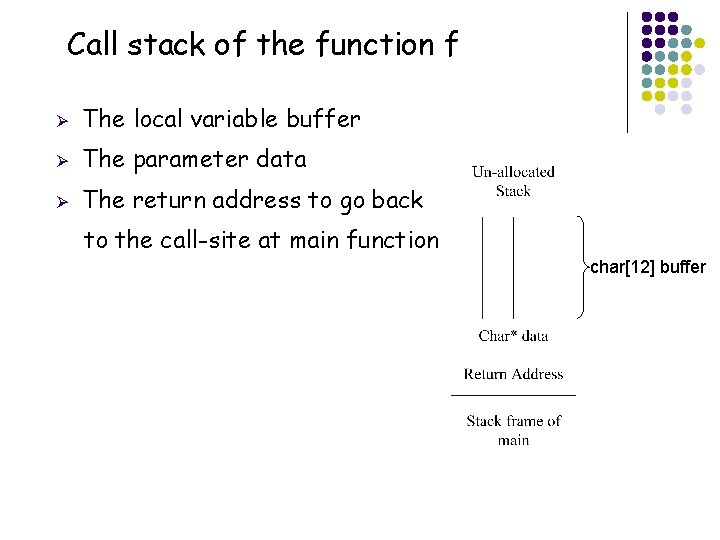
Call stack of the function f Ø The local variable buffer Ø The parameter data Ø The return address to go back to the call-site at main function char[12] buffer
![Feed in a valid input Ø Example username char12 buffer Feed in a valid input Ø Example “username” char[12] buffer](https://slidetodoc.com/presentation_image_h2/dbf5e8dd94e3f2793dfaf187332ab84b/image-11.jpg)
Feed in a valid input Ø Example “username” char[12] buffer

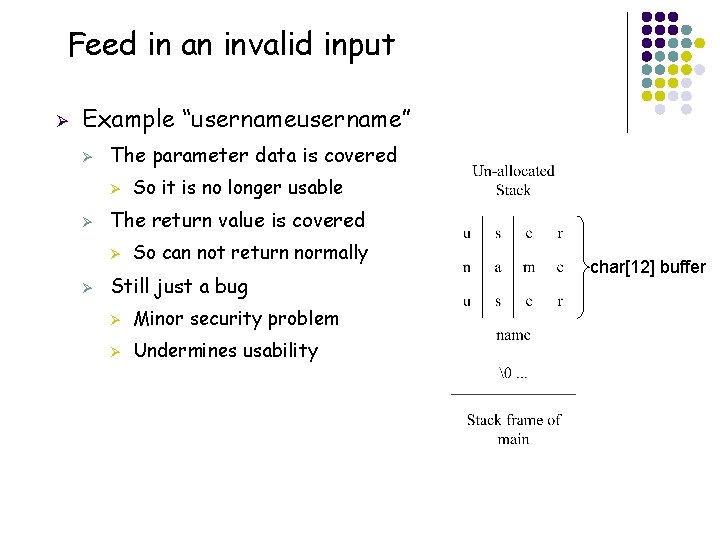
Feed in an invalid input Ø Example “username” Ø The parameter data is covered Ø Ø The return value is covered Ø Ø So it is no longer usable So can not return normally Still just a bug Ø Minor security problem Ø Undermines usability char[12] buffer

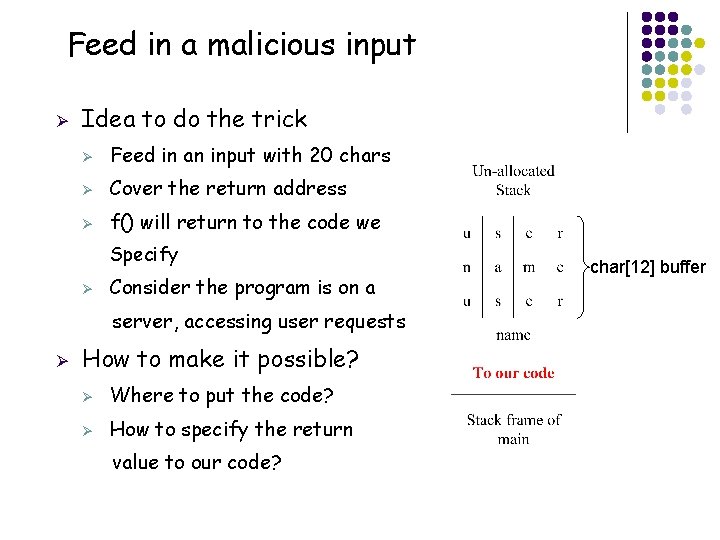
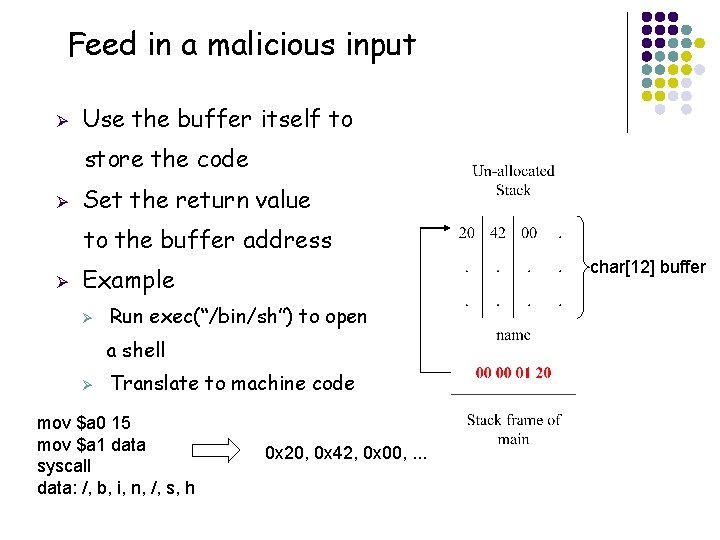
Feed in a malicious input Ø Idea to do the trick Ø Feed in an input with 20 chars Ø Cover the return address Ø f() will return to the code we Specify Ø Consider the program is on a server, accessing user requests Ø How to make it possible? Ø Where to put the code? Ø How to specify the return value to our code? char[12] buffer

Feed in a malicious input Ø Use the buffer itself to store the code Ø Set the return value to the buffer address Ø char[12] buffer Example Ø Run exec(“/bin/sh”) to open a shell Ø Translate to machine code mov $a 0 15 mov $a 1 data syscall data: /, b, i, n, /, s, h 0 x 20, 0 x 42, 0 x 00, . . .

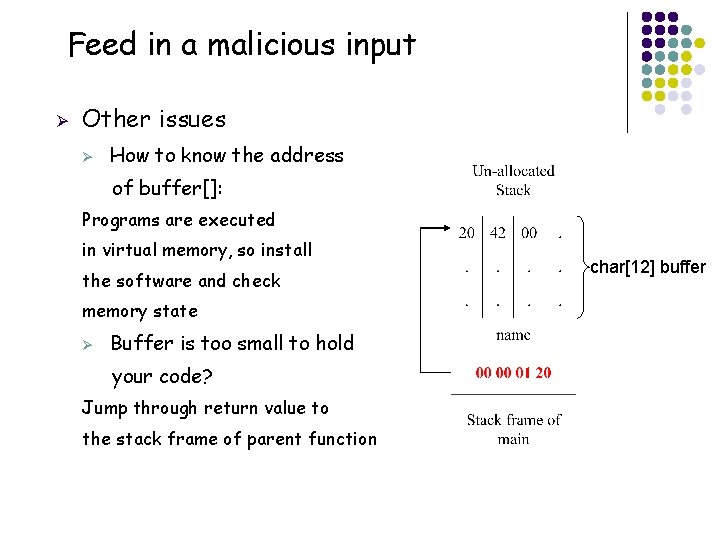
Feed in a malicious input Ø Other issues Ø How to know the address of buffer[]: Programs are executed in virtual memory, so install the software and check memory state Ø Buffer is too small to hold your code? Jump through return value to the stack frame of parent function char[12] buffer

The state of practice Ø Ø 16 Buffer overflow is very common in C / C++ programs About 50% of new attacks are related to buffer overflow Memory safe languages such as Java do not have the problem, why we still have the problem? Known bugs are being exploited from time to time

How to deal with buffer overflow Ø Ø 17 Boundary check for input-reachable buffers Ø Not so easy in practice Ø Check too many places: slow the software down Ø Check too few places: buffer overflow risk Automatic supports Ø Buffer Overflow Detection: libsafe, stackguard, … Ø Runtime protection: weak memory safe Ø Runtime protection: split stack

Injection Ø Directly inject user input into code to be executed Ø SQL Injection Ø Ø OS Injection Ø 18 Inject code to SQL queries Inject code to OS commands

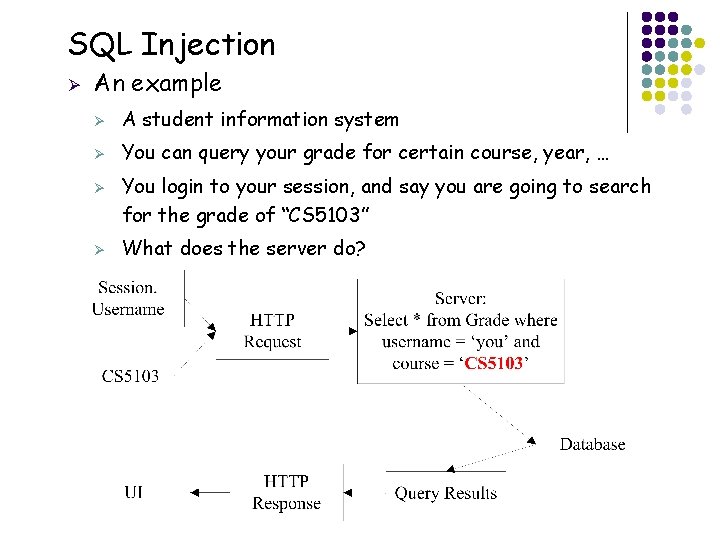
SQL Injection Ø An example Ø A student information system Ø You can query your grade for certain course, year, … Ø Ø 19 You login to your session, and say you are going to search for the grade of “CS 5103” What does the server do?

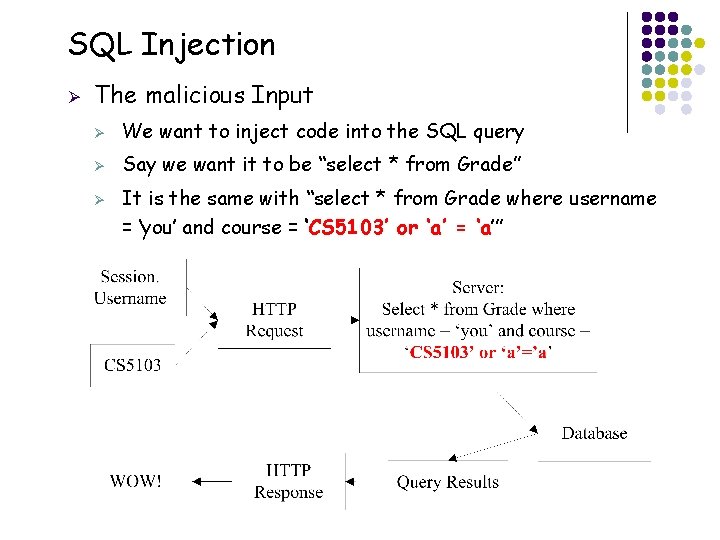
SQL Injection Ø The malicious Input Ø We want to inject code into the SQL query Ø Say we want it to be “select * from Grade” Ø 20 It is the same with “select * from Grade where username = ‘you’ and course = ‘CS 5103’ or ‘a’ = ‘a’”

OS Injection Ø Quite Similar Ø Ø Consider a server is going to make a dir for you as a new user, and it will execute exec(“mkdir path/to/” + username) What username you should make up? An example: Haha. Gotyou | binsh 21

Injection Protection Ø Ø Injection works by passing user inputs into backend engines Can we simply cut off the path? Ø Definitely NO Ø We have to do some filtering Ø We are going to work on the example: select * from Grade where username = ‘you’ and course = ‘CS 5103’ or ‘a’ = ‘a’ 22

User Input Filtering select * from Grade where username = ‘you’ and course = ‘CS 5103’ or ‘a’ = ‘a’ Ø What to filter? Ø or ? => “oorr” can bypass it Ø Space? => use /**/ can bypass it Ø Quotes? A little bit difficult, we can search by year, and use year = 2009 or 1=1 Ø Want more? Ø See http: //websec. wordpress. com/2010/03/19/exploiting-hard-filtered-sql-injections/ 23

Final Exam Ø Time: Dec 18 th 6: 00 pm to 8: 30 pm Ø Location: FLN 3. 02. 07 Ø Form: closed book exam Ø 100 points total Ø Account for 30% for the course grade Ø 15 multiple choice questions * 3 points each: single answer Ø Ø 24 5 multiple choice questions * 4 points each: multiple answers 3 -4 Question & Answer, 35 points in total

Covered Course Contents Ø Must * Ø Ø May ? Ø Ø This knowledge point may be covered in the final exam Not mentioned in this outline Ø 25 It is for sure that this knowledge point will be covered in the final exam The final exam will not cover this knowledge point

Software process models Ø Features of Waterfall model ? Ø Features of Iterative model ? Ø 26 Features of Agile software development & Extreme programming * Ø Major difference between these models * Ø Usage Scenario of different models ?

Requirement Engineering Ø Find Stake Holders ? Ø Type of Requirements * Ø Major requirement elicitation approaches ? Ø Ø Natural Language Specifications and find problems in the specifications * Use case diagram ? Ø 27 Actors and Relationship between use cases ?

System Modeling Ø Class Diagram* Ø Draw Class Diagrams * Ø Relationship between classes * Ø Ø 28 Generalization, Aggregation, Composition, Association and their difference * Multiplicity and Role Names ?

Software Architecture Ø 29 Major software architecture styles* Ø Pipe and Filter ? Ø Layered ? Ø There differences and usage scenarios *

Software Design Ø 30 Design Patterns * Ø Structure and Types ? Ø Composite Pattern ? Ø Factory Pattern ? Ø Visitor Pattern ?

Versioning Ø Ø Diff * Ø Know what a diff between two files should look like ? Ø Know how applying a diff works ? Ø Know what diff to apply for pull / update ? Conflict ? Ø Ø 31 Know how to detect conflict ? Branch * Ø Know how to merge branches by applying diffs ? Ø Branch strategies and their pros / cons ?

Software licences Ø Know major software licenses ? Ø Ø Ø 32 GPL, LGPL, Apache, BSD, … Know the difference between permissive licenses and copyleft licenses * Know the main idea of GPL and its difference with LGPL ?

Coding Styles Ø Ø Ø 33 Coding style rules for all levels * Ø Identifier / constant ? Ø Expression ? Ø Statements ? Ø Blocks ? Ø Comments ? Finding coding style errors in given code * Understand the goal and concept of software refactoring ?

Software Testing Ø Concepts and terms in software testing * Ø Ø 34 Test case, Test suite, Test oracle, … Unit Testing * Ø Working process of JUnit ? Ø What are good ways to write assertions ? Ø What are good ways to do the tearing down ?

Software Testing Ø Test coverage * Ø Ø Ø 35 Understand statement coverage, branch coverage and path coverage, and calculate coverage for a given test case and code* Understand input combination coverage, and calculate coverage for a given model and test case* Understand mutations and mutation coverage ?

Software Testing Ø Regression Testing ? Ø Ø 36 Know the ways to reduce testing effort in regression testing ? Understand what is APFD, and know how total and additional strategy works ?

Software Debugging Ø Delta debugging* Ø Ø Ø 37 Understand how basic delta debugging works ? Know how to handle interference and multiple interference ? Understand the limitations of delta debugging ?

Software Security Issues Ø 38 Major software vulnerabilities * Ø Injection ? Ø Buffer Overflow *

Thanks! 39