CS 268 Active Networks Overlay Networks Ion Stoica


















![Other Projects § Overcast [Jannotti et al, 2000] - § Single source tree Uses Other Projects § Overcast [Jannotti et al, 2000] - § Single source tree Uses](https://slidetodoc.com/presentation_image_h/0ca50e76db0607f5b2255c4f505f72ff/image-46.jpg)
- Slides: 47

CS 268: Active Networks & Overlay Networks Ion Stoica April 12, 2004 (* Active networks based in part on David Wheterall presentation from SOSP ’ 99) istoica@cs. berkeley. edu

Overview Ø § Active Networks Overlay Networks istoica@cs. berkeley. edu 2

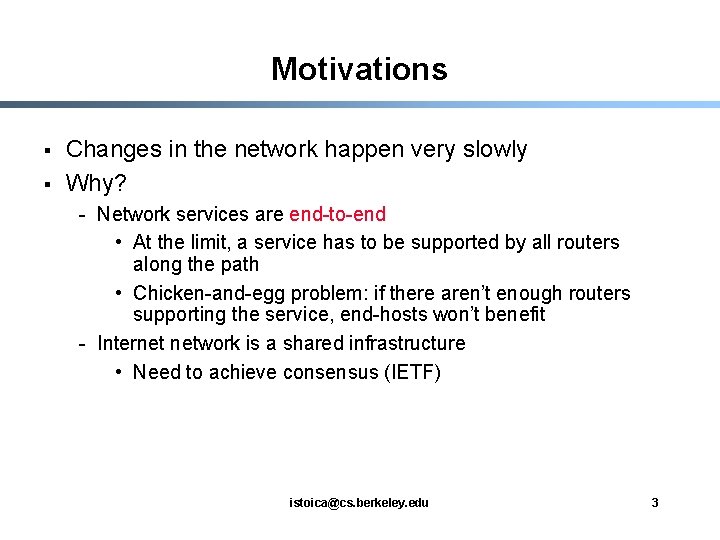
Motivations § § Changes in the network happen very slowly Why? - Network services are end-to-end • At the limit, a service has to be supported by all routers along the path • Chicken-and-egg problem: if there aren’t enough routers supporting the service, end-hosts won’t benefit - Internet network is a shared infrastructure • Need to achieve consensus (IETF) istoica@cs. berkeley. edu 3

Motivations § Proposed changes that haven’t happened yet on a large scale: - IP security (IPSEC ‘ 93) - More addresses (IPv 6 ‘ 91) - Multicast (IP multicast ‘ 90) istoica@cs. berkeley. edu 4

Goals § § Make it easy to deploy new functionalities in the network accelerate the pace of innovation Allow users to customize their services istoica@cs. berkeley. edu 5

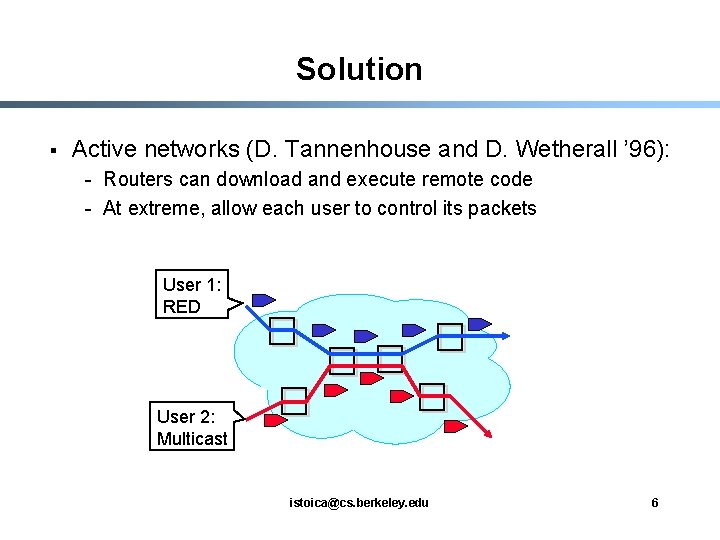
Solution § Active networks (D. Tannenhouse and D. Wetherall ’ 96): - Routers can download and execute remote code - At extreme, allow each user to control its packets User 1: RED User 2: Multicast istoica@cs. berkeley. edu 6

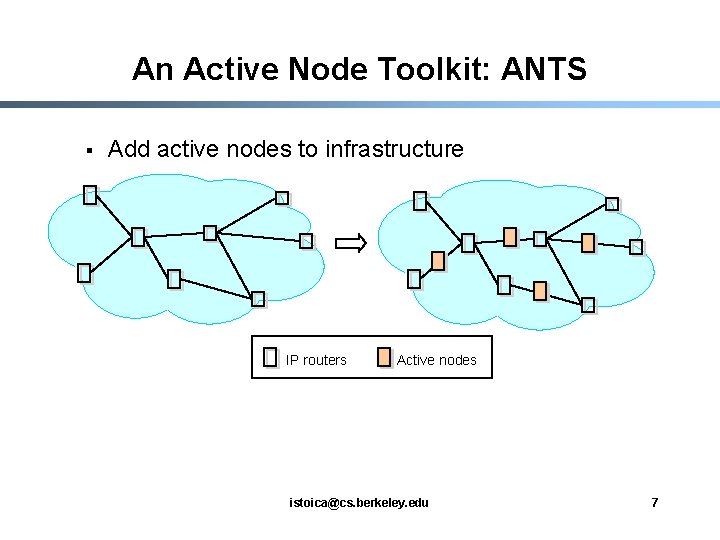
An Active Node Toolkit: ANTS § Add active nodes to infrastructure IP routers Active nodes istoica@cs. berkeley. edu 7

Active Nodes § Provide environment for running service code - Soft-storage, routing, packet manipulation § Ensure safety - Protect state at node; enforce packet invariants § Manage local resources - Bound code runtimes and other resource consumptions istoica@cs. berkeley. edu 8

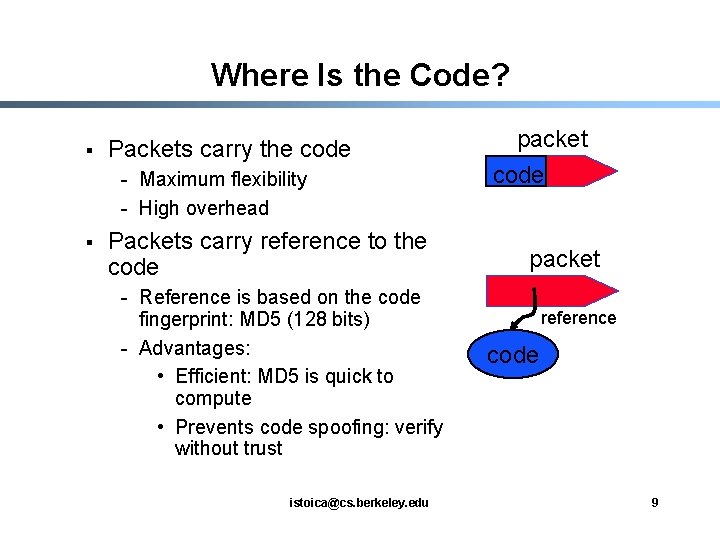
Where Is the Code? § Packets carry the code - Maximum flexibility - High overhead § Packets carry reference to the code - Reference is based on the code fingerprint: MD 5 (128 bits) - Advantages: • Efficient: MD 5 is quick to compute • Prevents code spoofing: verify without trust istoica@cs. berkeley. edu packet code packet reference code 9

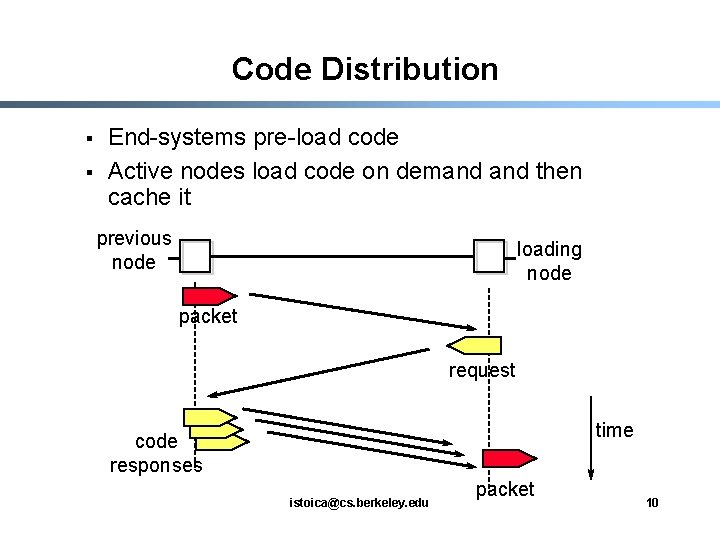
Code Distribution § § End-systems pre-load code Active nodes load code on demand then cache it previous node loading node packet request time code responses istoica@cs. berkeley. edu packet 10

Lesson Learned § § § Applications Performance Security and resource management istoica@cs. berkeley. edu 11

Applications § § Well-suited to implement protocol variations But not to enforce global policies and resource control (e. g. , fire-walls and Qo. S) - Need a central authority to implement these functionalities § Application examples: auctions, reliable multicast, mobility, … istoica@cs. berkeley. edu 12

Performances § § ANTS implemented in Java In common case little overhead: - Extra steps over IP (classification, safe eval) run very fast § Enough cycles to run simple programs - e. g. 1 GHz, 1 Gbps, 1000 b packets, 100% 1000 cycles; 10% 10000 cycles istoica@cs. berkeley. edu 13

Security and Resource Mgmt. § Untrusted users need to isolate their actions § Protection: make sure that one program does not corrupt other program - Node level protection - Network level protection istoica@cs. berkeley. edu 14

Node Level Protection § Relatively easy to solve - Allocate resources among users and control their usage • Fair Queueing, per-flow buffer allocation - Use light weight mechanisms: sand-box, safe-type languages, Proof Carrying Code (PCC): • PCC can also provide timeliness guarantees e. g. , can demonstrate that an operation cannot take more time/space than a predifined constant § Note: fundamental trade-off between protection and flexibility - Example: if a node uses FQ to provide bandwidth protection, it will constrain the delays experienced by a user istoica@cs. berkeley. edu 15

Network Level Protection § § § More difficult to achieve Challenge: enforce global behavior of a program only with local checks and control Main problem: programs very flexible. Active nodes can: - Affect routing behavior (e. g. , mobile IP) - Generate new packets (e. g. multicast) istoica@cs. berkeley. edu 16

Examples § § Loops as a result of routing changes Resource wastage as a result of misbehaving multicast programs - Multicast height k, a node can generate up to m copies total number of packets can be O(mk) ! § Local solutions not enough - TTL too weak; unaware about topology - Fair Queueing offers only local protection istoica@cs. berkeley. edu 17

Solution § § Program certification by a central authority Limitations: - Slows innovation, but still better than what we have today - Dealing with a misbehaving node still remains difficult istoica@cs. berkeley. edu 18

Restricting Active Networks § Allow only administrators, or privileged users to inject code - Router plugins, active bridge § Restrict affecting only the control plane increase network manageability - Smart. Packets - Netscript istoica@cs. berkeley. edu 19

Summary § Active networks - A revolutionary paradigm - Explores a significant region of the networking architecture design space § But is the network layer the right level to deploy it? istoica@cs. berkeley. edu 20

Overview § Ø Active Networks Overlay Networks istoica@cs. berkeley. edu 21

Definition § Network - Define addressing, routing, and service model for communication between hosts § Overlay network - A network built on top of one or more existing networks - Add an additional layer of indirection/virtualization - Change properties in one or more areas of underlying network § Alternative - Change an existing network layer istoica@cs. berkeley. edu 22

A Historical Example § Internet is an overlay network - Goal: connect local area networks - Built on local area networks (e. g. , Ethernet), phone lines - Add an Internet Protocol header to all packets istoica@cs. berkeley. edu 23

Benefits § Do not have to deploy new equipment, or modify existing software/protocols - Probably have to deploy new software on top of existing software - E. g. , adding IP on top of Ethernet does not require modifying Ethernet protocol or driver - Allow bootstrapping • Expensive to develop entirely new networking hardware/software • All networks after the telephone have begun as overlay networks istoica@cs. berkeley. edu 24

Benefits § Do not have to deploy at every node - Not every node needs/wants overlay network service all the time • e. g. , Qo. S guarantees for best-effort traffic - Overlay network may be too heavyweight for some nodes • e. g. , consumes too much memory, cycles, or bandwidth - Overlay network may have unclear security properties • e. g. , may be used for service denial attack - Overlay network may not scale • e. g. may require n 2 state or communication istoica@cs. berkeley. edu 25

Costs § Adds overhead - Adds a layer in networking stack • Additional packet headers, processing - Sometimes, additional work is redundant • E. g. , an IP packet contains both Ethernet (48 + 48 bits) and IP addresses (32 + 32 bits) • Eliminate Ethernet addresses from Ethernet header and assume IP header(? ) § Adds complexity - Layering does not eliminate complexity, it only manages it - More layers of functionality more possible unintended interaction between layers - E. g. , corruption drops on wireless interpreted as congestion drops by TCP istoica@cs. berkeley. edu 26

Applications § Mulicast - This lecture § § Mobility Routing Addressing Security istoica@cs. berkeley. edu 27

Problems with IP Multicast § Scales poorly with number of groups - A router must maintain state for every group that traverses it § Supporting higher level functionality is difficult - IP Multicast: best-effort multi-point delivery service - Reliability and congestion control for IP Multicast complicated • Scalable, end-to-end approach for heterogeneous receivers is very difficult • Hop-by-hop approach requires more state and processing in routers § Deployment is difficult and slow - ISP’s reluctant to turn on IP Multicast istoica@cs. berkeley. edu 28

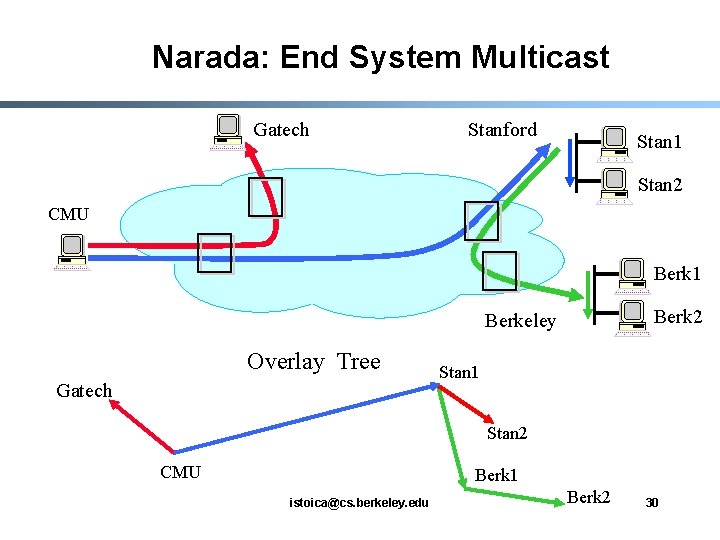
Overlay Multicast § § § Provide multicast functionality above the IP layer, overlay or application level multicast Challenge: do this efficiently Narada [Yang-hua et al, 2000] - Multi-source multicast Involves only end hosts Small group sizes <= hundreds of nodes Typical application: chat istoica@cs. berkeley. edu 29

Narada: End System Multicast Gatech Stanford Stan 1 Stan 2 CMU Berk 1 Berk 2 Berkeley Overlay Tree Gatech Stan 1 Stan 2 CMU Berk 1 istoica@cs. berkeley. edu Berk 2 30

Potential Benefits § Scalability - Routers do not maintain per-group state - End systems do, but they participate in very few groups § Easier to deploy - Only requires adding software to end hosts § Potentially simplifies support for higher level functionality - Use hop-by-hop approach, but end hosts are routers - Leverage computation and storage of end systems - E. g. , packet buffering, transcoding of media streams, ACK aggregation - Leverage solutions for unicast congestion control and reliability istoica@cs. berkeley. edu 31

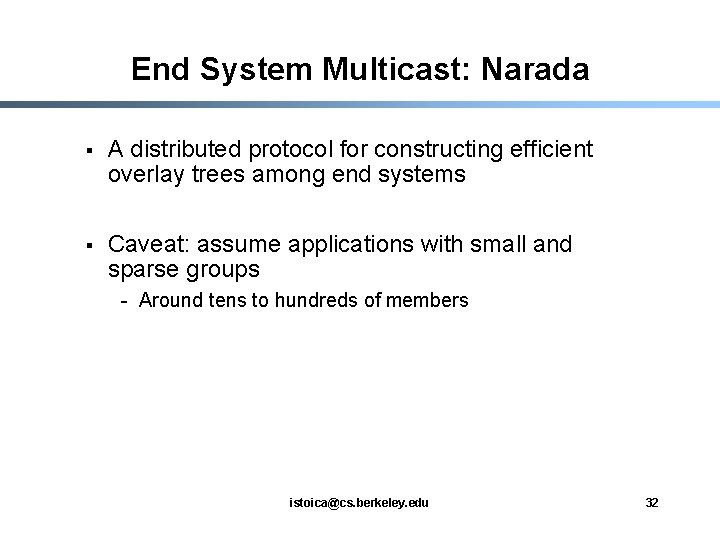
End System Multicast: Narada § A distributed protocol for constructing efficient overlay trees among end systems § Caveat: assume applications with small and sparse groups - Around tens to hundreds of members istoica@cs. berkeley. edu 32

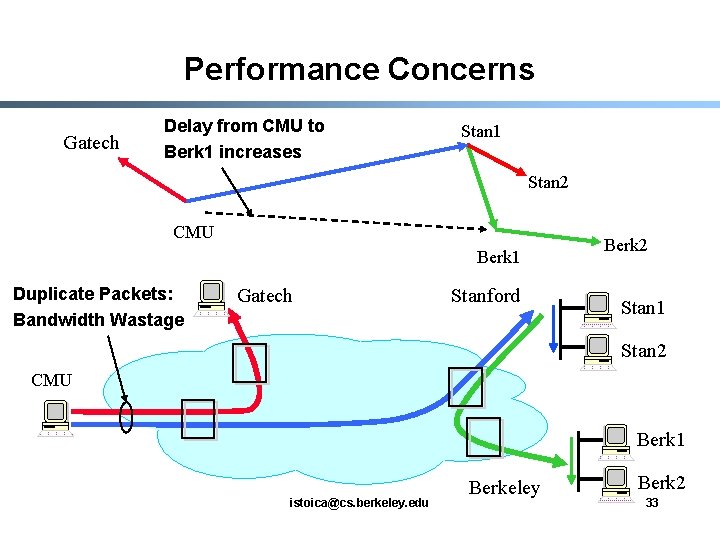
Performance Concerns Gatech Delay from CMU to Berk 1 increases Stan 1 Stan 2 CMU Berk 1 Duplicate Packets: Bandwidth Wastage Gatech Stanford Berk 2 Stan 1 Stan 2 CMU Berk 1 istoica@cs. berkeley. edu Berkeley Berk 2 33

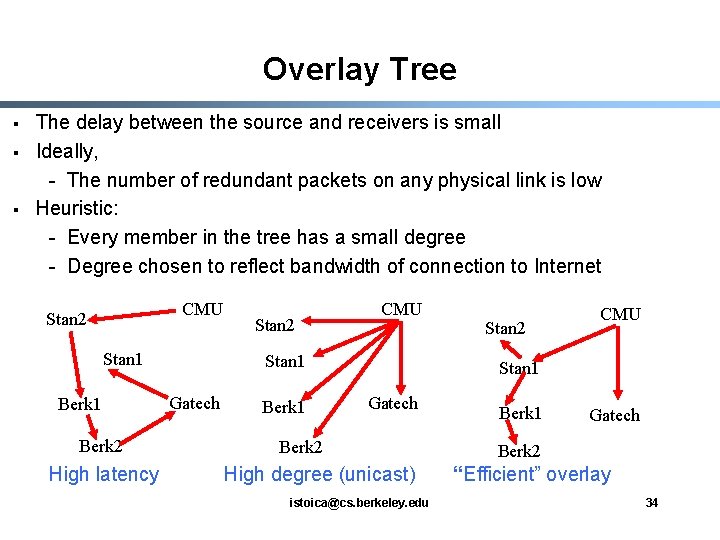
Overlay Tree § § § The delay between the source and receivers is small Ideally, - The number of redundant packets on any physical link is low Heuristic: - Every member in the tree has a small degree - Degree chosen to reflect bandwidth of connection to Internet CMU Stan 2 Stan 1 Berk 2 High latency Stan 2 CMU Stan 1 Gatech Berk 1 Stan 2 CMU Stan 1 Gatech Berk 2 High degree (unicast) istoica@cs. berkeley. edu Berk 1 Gatech Berk 2 “Efficient” overlay 34

Overlay Construction Problems § Dynamic changes in group membership - Members may join and leave dynamically - Members may die § Dynamic changes in network conditions and topology - Delay between members may vary over time due to congestion, routing changes § Knowledge of network conditions is member specific - Each member must determine network conditions for itself istoica@cs. berkeley. edu 35

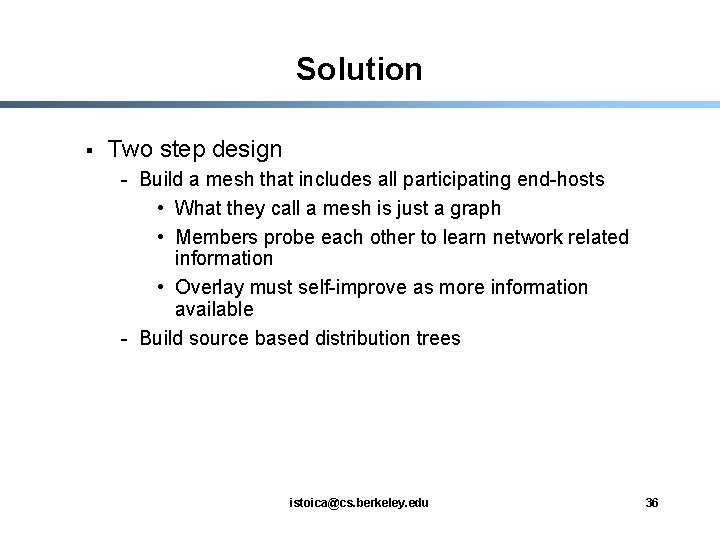
Solution § Two step design - Build a mesh that includes all participating end-hosts • What they call a mesh is just a graph • Members probe each other to learn network related information • Overlay must self-improve as more information available - Build source based distribution trees istoica@cs. berkeley. edu 36

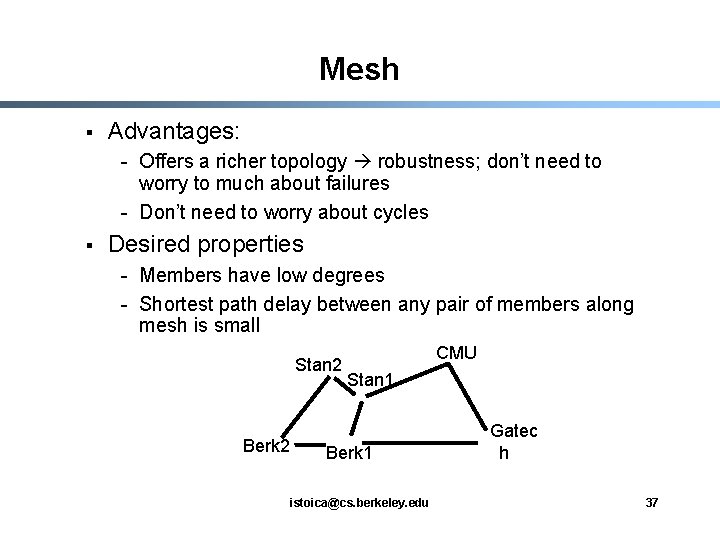
Mesh § Advantages: - Offers a richer topology robustness; don’t need to worry to much about failures - Don’t need to worry about cycles § Desired properties - Members have low degrees - Shortest path delay between any pair of members along mesh is small Stan 2 Berk 2 CMU Stan 1 Berk 1 istoica@cs. berkeley. edu Gatec h 37

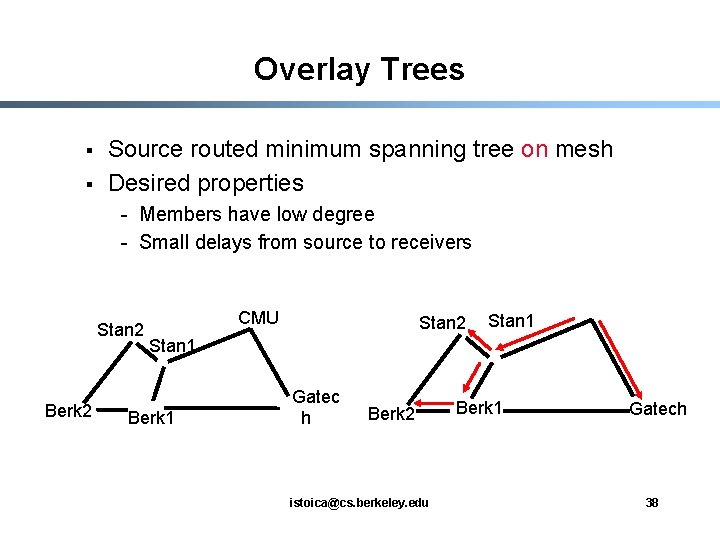
Overlay Trees § § Source routed minimum spanning tree on mesh Desired properties - Members have low degree - Small delays from source to receivers Stan 2 Berk 2 CMU Stan 2 Stan 1 Berk 1 Gatec h Berk 2 istoica@cs. berkeley. edu Berk 1 Gatech 38

Narada Components/Techniques § Mesh Management: - Ensures mesh remains connected in face of membership changes § Mesh Optimization: - Distributed heuristics for ensuring shortest path delay between members along the mesh is small § Tree construction: - Routing algorithms for constructing data-delivery trees - Distance vector routing, and reverse path forwarding istoica@cs. berkeley. edu 39

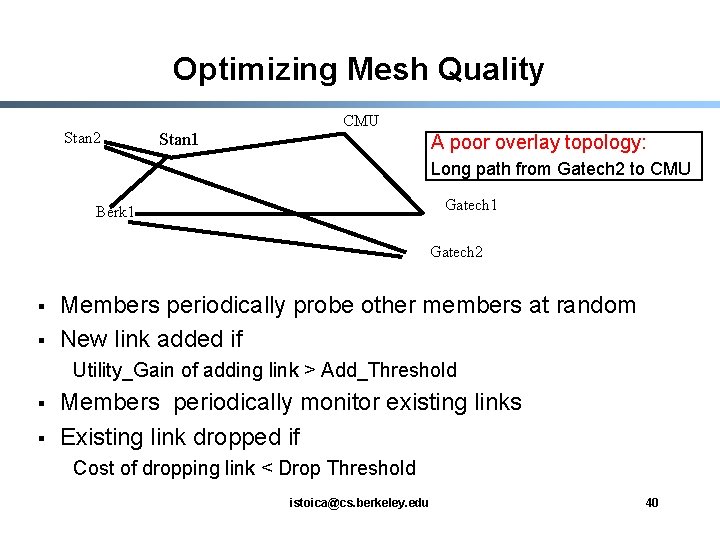
Optimizing Mesh Quality Stan 2 Stan 1 CMU A poor overlay topology: Long path from Gatech 2 to CMU Gatech 1 Berk 1 Gatech 2 § § Members periodically probe other members at random New link added if Utility_Gain of adding link > Add_Threshold § § Members periodically monitor existing links Existing link dropped if Cost of dropping link < Drop Threshold istoica@cs. berkeley. edu 40

Definitions § Utility gain of adding a link based on - The number of members to which routing delay improves - How significant the improvement in delay to each member is § Cost of dropping a link based on - The number of members to which routing delay increases, for either neighbor § Add/Drop Thresholds are functions of: - Member’s estimation of group size - Current and maximum degree of member in the mesh istoica@cs. berkeley. edu 41

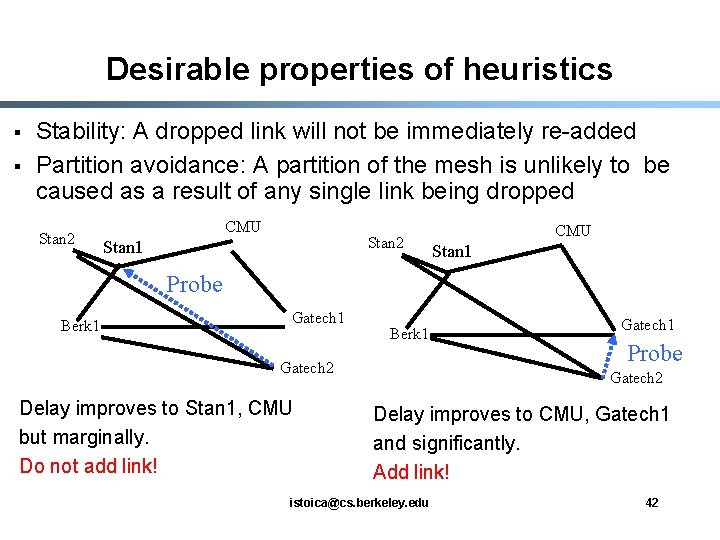
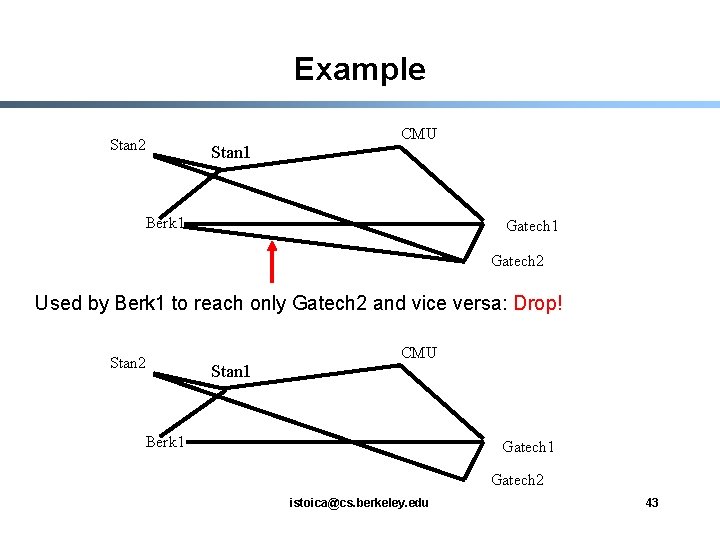
Desirable properties of heuristics § § Stability: A dropped link will not be immediately re-added Partition avoidance: A partition of the mesh is unlikely to be caused as a result of any single link being dropped Stan 2 CMU Stan 2 Stan 1 CMU Stan 1 Probe Berk 1 Gatech 1 Berk 1 Gatech 2 Delay improves to Stan 1, CMU but marginally. Do not add link! Gatech 1 Probe Gatech 2 Delay improves to CMU, Gatech 1 and significantly. Add link! istoica@cs. berkeley. edu 42

Example Stan 2 Stan 1 CMU Berk 1 Gatech 2 Used by Berk 1 to reach only Gatech 2 and vice versa: Drop! Stan 2 Stan 1 CMU Berk 1 Gatech 2 istoica@cs. berkeley. edu 43

Simulation Results § Simulations - Group of 128 members - Delay between 90% pairs < 4 times the unicast delay - No link caries more than 9 copies § Experiments - Group of 13 members - Delay between 90% pairs < 1. 5 times the unicast delay istoica@cs. berkeley. edu 44

NARADA Summary § End-system multicast (NARADA) : aimed to small -sized groups - Application example: chat § § § Multi source multicast model No need for infrastructure Properties - low performance penalty compared to IP Multicast - potential to simplify support for higher layer functionality - allows for application-specific customizations istoica@cs. berkeley. edu 45
![Other Projects Overcast Jannotti et al 2000 Single source tree Uses Other Projects § Overcast [Jannotti et al, 2000] - § Single source tree Uses](https://slidetodoc.com/presentation_image_h/0ca50e76db0607f5b2255c4f505f72ff/image-46.jpg)
Other Projects § Overcast [Jannotti et al, 2000] - § Single source tree Uses an infrastructure; end hosts are not part of multicast tree Large groups ~ millions of nodes Typical application: content distribution Scattercast (Chawathe et al, UC Berkeley) - Emphasis on infrastructural support and proxy-based multicast - Uses a mesh like Narada, but differences in protocol details § Yoid (Paul Francis, Cornell) - Uses a shared tree among participating members - Distributed heuristics for managing and optimizing tree constructions istoica@cs. berkeley. edu 46

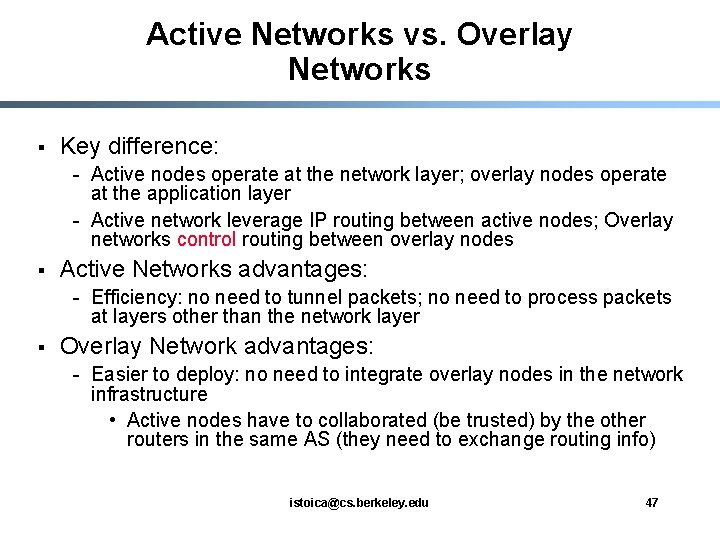
Active Networks vs. Overlay Networks § Key difference: - Active nodes operate at the network layer; overlay nodes operate at the application layer - Active network leverage IP routing between active nodes; Overlay networks control routing between overlay nodes § Active Networks advantages: - Efficiency: no need to tunnel packets; no need to process packets at layers other than the network layer § Overlay Network advantages: - Easier to deploy: no need to integrate overlay nodes in the network infrastructure • Active nodes have to collaborated (be trusted) by the other routers in the same AS (they need to exchange routing info) istoica@cs. berkeley. edu 47
 Ee 122 berkeley
Ee 122 berkeley Ion stoica
Ion stoica Overlay networks in distributed systems
Overlay networks in distributed systems Emilia ion procuror
Emilia ion procuror Monica stoica
Monica stoica Emilia stoica
Emilia stoica Adrian stoica jpl
Adrian stoica jpl Beatrice stoica
Beatrice stoica London dispersion forces diagram
London dispersion forces diagram Ion dipolo
Ion dipolo Qumica
Qumica Fuerzas dipolo-dipolo ejemplos
Fuerzas dipolo-dipolo ejemplos Iso tc268
Iso tc268 Round 268 to the nearest hundred
Round 268 to the nearest hundred Opwekking 268
Opwekking 268 Opwekking 268
Opwekking 268 Px 268
Px 268 Cs 268
Cs 268 Cs 268
Cs 268 Odo 268 swiss medical
Odo 268 swiss medical Suipacha 268
Suipacha 268 Iso/tc 268
Iso/tc 268 268/33
268/33 Are ion channels passive or active
Are ion channels passive or active Vector overlay operations
Vector overlay operations Absolute loader advantages and disadvantages
Absolute loader advantages and disadvantages Polyester concrete overlay
Polyester concrete overlay Triggered overlay
Triggered overlay Definition of spatial analysis
Definition of spatial analysis Overlay network
Overlay network Seo specialist punto rojo
Seo specialist punto rojo Porofessor overlay
Porofessor overlay Interpret?
Interpret? Skoring pada poligon
Skoring pada poligon Hfw map
Hfw map Rapid overlay of chemical structures
Rapid overlay of chemical structures Nvo agenda
Nvo agenda Map overlay usmc
Map overlay usmc Skype overlay
Skype overlay Old map overlay
Old map overlay Overlay-netzwerk
Overlay-netzwerk Pc weld overlay
Pc weld overlay Nexio touch screen
Nexio touch screen What colour overlay is best for dyslexia
What colour overlay is best for dyslexia Edge platform
Edge platform Configuring otv
Configuring otv Homing overlay experiment
Homing overlay experiment Overlay oam
Overlay oam