Critical infrastructure protection under imperfect attacker perception Erik



































- Slides: 69

Critical infrastructure protection under imperfect attacker perception Erik Jenelius, Jonas Westin, Åke J. Holmgren Adviser: Frank, Yeong Sung Lin Present by Ying Ju Chen

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 2

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 3

Introduction • This paper considers the problem of allocating finite resources among the elements of a critical infrastructure system in order to protect it from antagonistic attacks. • Previous studies have assumed that the attacker has complete information about the utilities associated with attacks on each element. • This presents a modeling incorporates Ø Itpaper is likely that the attacker’sframework perception that of the system is imperfect attacker perception by introducing random not as precise as the defender’s. observation errors in a previously studied baseline model. • Analyzes how the perceptive ability affects the attack probabilities and the defender’s disutility and optimal resource allocation. 12/09/2021 4

Introduction • Antagonistic threats and game theory Ø Intentional attacks are different from random failures in the sense that the antagonist intentionally chooses the time and place for the attack. Ø Furthermore, the measures applied to protect a system will, most likely, affect the antagonist’s course of action. Ø A strategic interaction between the attacker and the defender. Ø Studies of antagonistic threats embrace a “game” situation rather than a static decision situation. 12/09/2021 5

Introduction • Antagonistic threats and game theory – A number of papers have studied various theoretical aspects of protecting potential targets against antagonistic attacks. Ø Underlying most of the studies is the assumption of a rational and informed attacker. Ø Other studies assume that an attacker chooses one target to attack, possibly randomizing, and the probability that the attack is successful is determined by the resources previously invested in the target by a defender. Ø Substitution effect: an investment by one element increases the probability that the other is attacked. 12/09/2021 6

Introduction • Incomplete information and imperfect observations – The defender may be uncertain about the preferences of the attacker. Ø Bayesian game Some authors model the uncertainty as a probability distribution across possible attacker types; the problem is explicitly framed as a Bayesian game. Ø Scenarios Another approach to handling uncertainty about the nature of the attack when evaluating different protection strategies has been to compare them under a set of plausible 12/09/2021 scenarios. 7

Introduction • Incomplete information and imperfect observations – Less attention has been given to the decision process of the attacker. Ø Bayes’ rule One paper considers a game where the attacker, prior to the defender’s resource allocation, is uncertain about the level of vulnerability of one of the targets. After observing the defender’s investments, the attacker updates his beliefs about the vulnerability. 12/09/2021 8

Introduction • It is unlikely in reality that an antagonist could perceive the precise gains associated with attacking a target as accurately as the defender of the system. • Therefore, its subsequent actions may not necessarily be those that would yield the highest utility given all the information about the system that the defender possesses. However, if there chancedefense that thebudget, attackerassuming chooses aa • • For example, givenisaalimited suboptimal alternative, this strategy could very elements dangerous perfectly perceptive attacker may mean thatbesome if attacks of thesesince elements high should be on leftsome unprotected they would cause be suboptimal disutility forforthethedefender. alternatives attacker. 12/09/2021 9

Introduction • This paper analyzes the impacts if the attacker cannot perfectly observe the utilities associated with attacking elements of an infrastructure system. Ø In particular, examining the implications for the defender’s problem of allocating a limited resource budget in order to protect the system against attack. • As a baseline, this paper uses the model of Powell. Ø Assumes complete information and perfect perception on behalf of both actors. • Include a non attackoption for the antagonist. 12/09/2021 10

Introduction • The analysis highlights a number of important implications of imperfect attacker perception that are not present in the baseline model. Ø An unwise defense investment can increase the expected disutility of the defender even in a zero sum situation. Ø A less perceptive attacker can yield higher expected disutility for the defender even if resources are allocated optimally. 12/09/2021 11

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 12

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 13

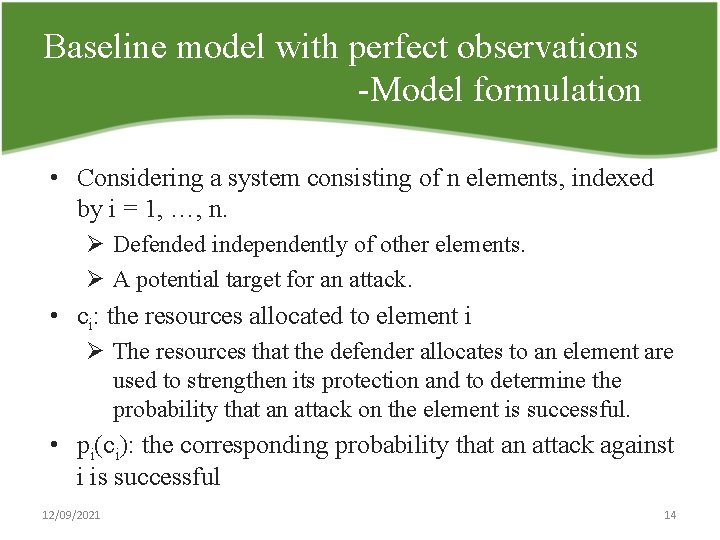
Baseline model with perfect observations Model formulation • Considering a system consisting of n elements, indexed by i = 1, …, n. Ø Defended independently of other elements. Ø A potential target for an attack. • ci: the resources allocated to element i Ø The resources that the defender allocates to an element are used to strengthen its protection and to determine the probability that an attack on the element is successful. • pi(ci): the corresponding probability that an attack against i is successful 12/09/2021 14

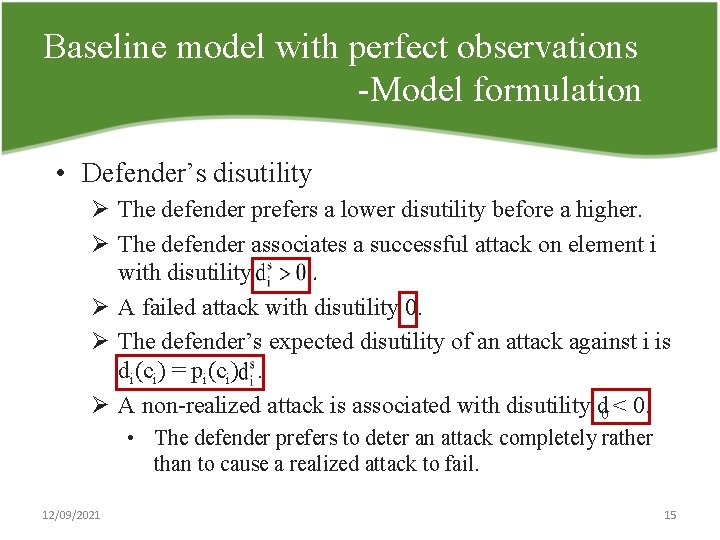
Baseline model with perfect observations Model formulation • Defender’s disutility Ø The defender prefers a lower disutility before a higher. Ø The defender associates a successful attack on element i with disutility. Ø A failed attack with disutility 0. Ø The defender’s expected disutility of an attack against i is di(ci) = pi(ci). Ø A non realized attack is associated with disutility d 0 < 0. • The defender prefers to deter an attack completely rather than to cause a realized attack to fail. 12/09/2021 15

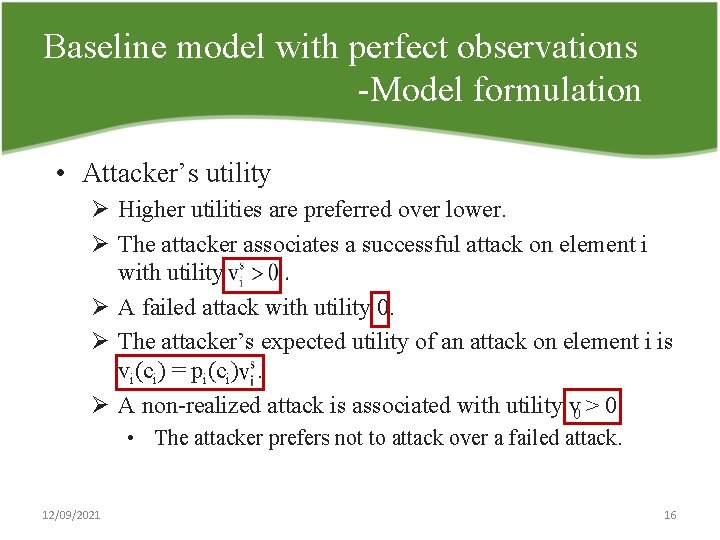
Baseline model with perfect observations Model formulation • Attacker’s utility Ø Higher utilities are preferred over lower. Ø The attacker associates a successful attack on element i with utility. Ø A failed attack with utility 0. Ø The attacker’s expected utility of an attack on element i is vi(ci) = pi(ci). Ø A non realized attack is associated with utility v 0 > 0. • The attacker prefers not to attack over a failed attack. 12/09/2021 16

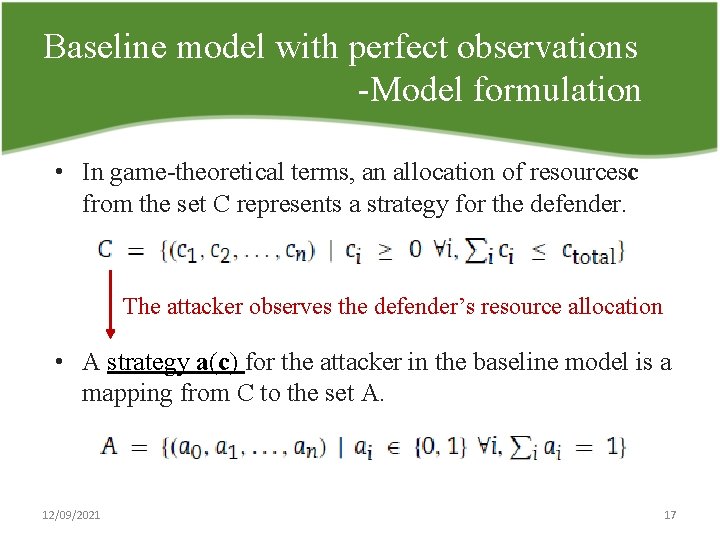
Baseline model with perfect observations Model formulation • In game theoretical terms, an allocation of resourcesc from the set C represents a strategy for the defender. The attacker observes the defender’s resource allocation • A strategy a(c) for the attacker in the baseline model is a mapping from C to the set A. 12/09/2021 17

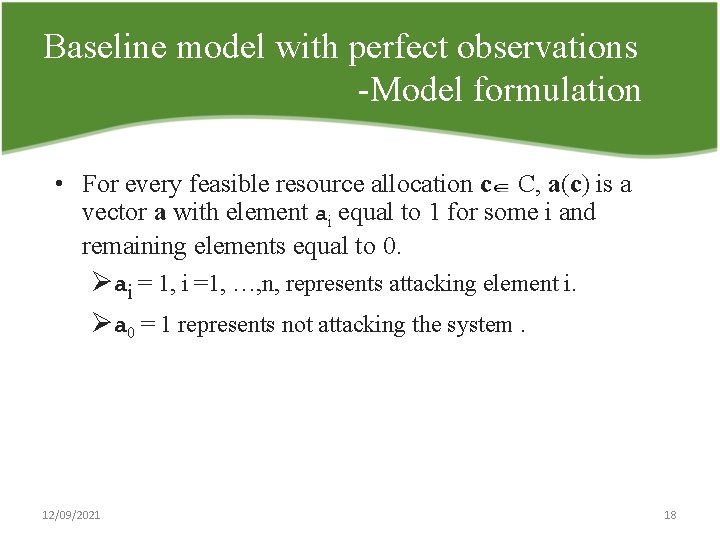
Baseline model with perfect observations Model formulation • For every feasible resource allocation c C, a(c) is a vector a with element ai equal to 1 for some i and remaining elements equal to 0. Øai = 1, i =1, …, n, represents attacking element i. Øa 0 = 1 represents not attacking the system. 12/09/2021 18

Baseline model with perfect observations Analysis Subgame • A subgame perfect equilibriumof the game is a pair of • 可以表示一種動態的賽局,雙方開始自一完全資訊點 strategies ĉ, â(c) such that: • 不能同時出招 • 第一場子賽局是attacker觀察到defender資源配置之後的賽局 • 第二場子賽局是defender觀察到attacer的行動之後的賽局 Subgame perfect equilibrium • 在每一子賽局中皆是Nash均衡,也就是只要對手的策略確定,就 可以有最適的反應(best response) 12/09/2021 19

Baseline model with perfect observations Analysis • For a given resource allocation c, a rational attacker will only play strategies that involve choosing some alternative that yields the highest utility. Ø Increasing the investment on any element that not yield the highest utility will clearly have no effect. • Since any investment ci in elements that yields the highest utility will reduce di(ci) as well as vi(ci) , it follows that : Ø The defender should allocate the resources in order to reduce the highest utility as much as possible. Ø Adopt a min max strategy. 12/09/2021 20

Baseline model with perfect observations Analysis • It has been shown that, in any subgame perfect equilibrium, the attacker will choose some alternative in elements that with the highest utility and lowest disutility, and the defender will play the min max strategy. 12/09/2021 21

Baseline model with perfect observations Analysis • The baseline model highlights some important aspects of protection against a strategic attacker as opposed to random failures. Ø Rather than investing in elements where the defense can be improved the most efficiently, the defender should invest in the elements that yield the highest utility for the attacker. Ø This principle is robust with regard to the utilities vi and disutilities di of the two actors and hinges only on the fact that an investment in element i will decrease both vi and di. 12/09/2021 22

Baseline model with perfect observations Analysis • The problem of the baseline model Ø The model predicts that no element with utility less than the highest utility will be attacked. Ø Perfect perception implies that an investment will have no deterring effect on the attacker unless its effect is precisely to make v 0 the uniquely largest utility. Ø The model predicts that the expected disutility of the defender is non increasingin the investment on any element, so that an additional investment, ceteris paribus, will not make the situation worse. 12/09/2021 23

Baseline model with perfect observations Analysis • The problem of the baseline model Ø All these properties stem from the fact that the attacker observes the utility of every alternative, given the defender’s resource allocation, perfectly. 12/09/2021 24

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 25

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 26

Model with imperfect observations • Formulation of the attacker’s problem • Formulation of the defender’s problem • Distribution of observation errors 12/09/2021 27

Formulation of the attacker’s problem • The baseline model specifies that the attacker’s actions are directly based on the defender’s strategy, i. e. , the resource allocation c. • In reality, it seems unlikely that the attacker would be able to observe much of the invested amounts directly. • Rather, the attacker would perceive the manifestations of those investments in terms of the risks and potential benefits of executing an attack. 12/09/2021 28

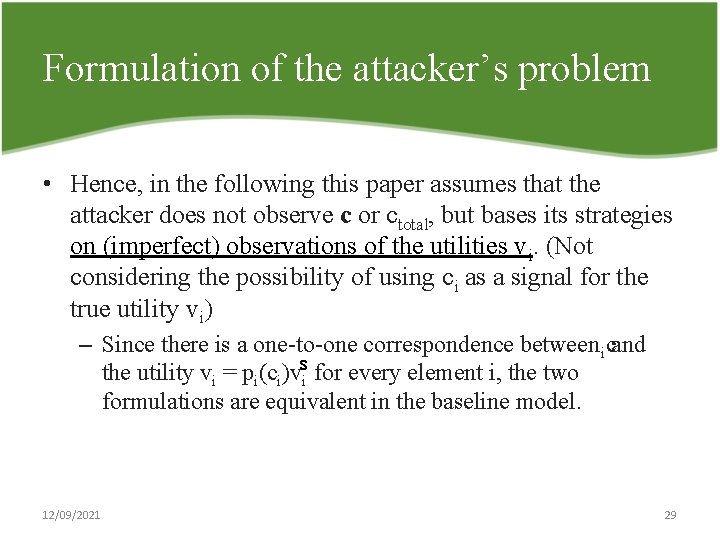
Formulation of the attacker’s problem • Hence, in the following this paper assumes that the attacker does not observe c or ctotal, but bases its strategies on (imperfect) observations of the utilities vi. (Not considering the possibility of using ci as a signal for the true utility vi) – Since there is a one to one correspondence between icand the utility vi = pi(ci)vsi for every element i, the two formulations are equivalent in the baseline model. 12/09/2021 29

Formulation of the attacker’s problem • Assumes the attacker’s observations of the elements are associated with errors, due to an imperfect ability to assess the defender’s protective measures and the outcome of a successful attack(utility). Ø Instead of observing the true utility vi(ci) for each element, the antagonist’s observation or best guess based on its available information is ui. Ø The utility of not attacking, v 0, is observed without error. 12/09/2021 30

Formulation of the attacker’s problem • The observation errors of the attacker are modeled as outcomes of random variables ɛi, so that the observed utility ui is an outcome of the random variable: Ø Assume that every ɛi is continuous on some interval and strictly positive. • Further, this paper assumes that the attacker treats the observed utilities ui as if they were true utilities. 12/09/2021 31

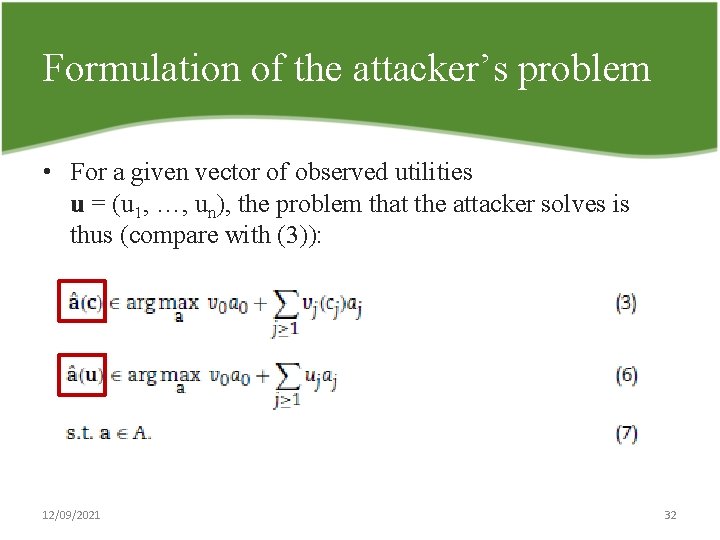
Formulation of the attacker’s problem • For a given vector of observed utilities u = (u 1, …, un), the problem that the attacker solves is thus (compare with (3)): 12/09/2021 32

Formulation of the defender’s problem • Considering the situation when the defender knows the probability distributions of the attacker’s observations Ui = viɛi but not the actual outcomes ui. • Assume that all the ɛi are independent and identically distributed (i. i. d. ). 12/09/2021 33

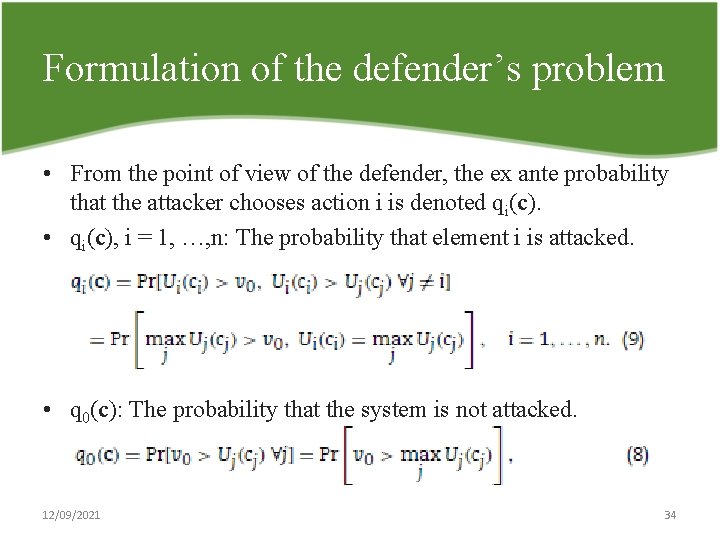
Formulation of the defender’s problem • From the point of view of the defender, the ex ante probability that the attacker chooses action i is denoted qi(c). • qi(c), i = 1, …, n: The probability that element i is attacked. • q 0(c): The probability that the system is not attacked. 12/09/2021 34

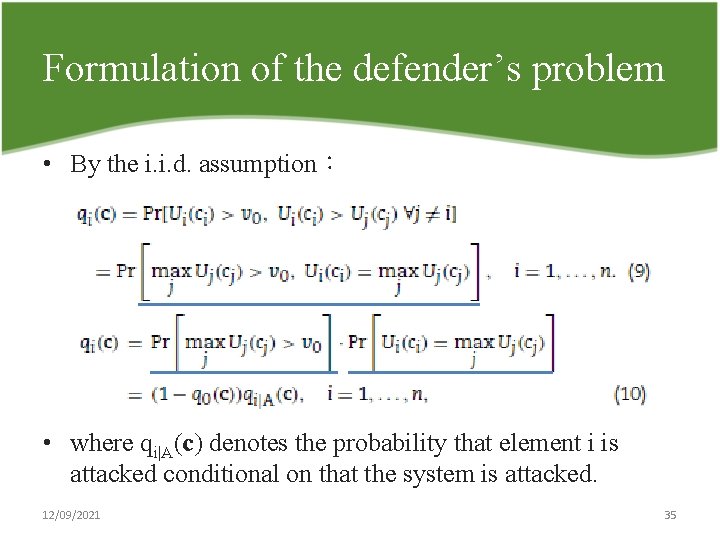
Formulation of the defender’s problem • By the i. i. d. assumption: • where qi|A(c) denotes the probability that element i is attacked conditional on that the system is attacked. 12/09/2021 35

Formulation of the defender’s problem • Conditional on that the system is attacked, the expected disutility of the defender is: • With the non attack alternative, the defender’s expected disutility is (compare with (1)) 12/09/2021 36

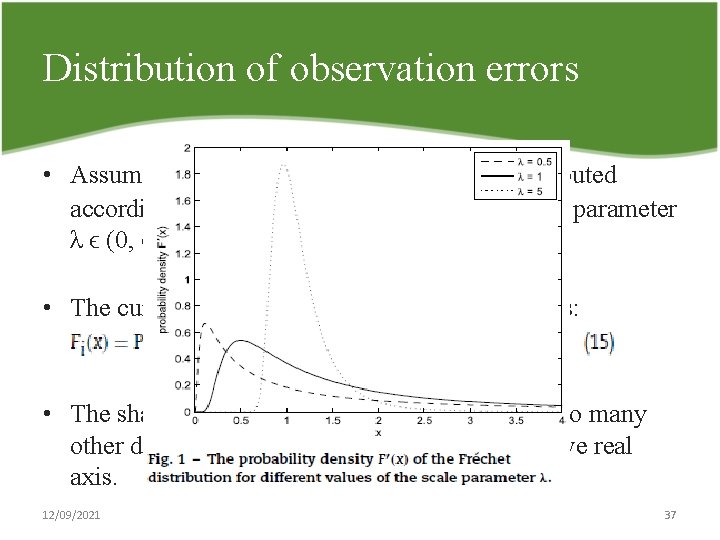
Distribution of observation errors • Assume that every observation error ɛi is distributed according to the Fréchet distribution with shape parameter λ ϵ (0, ∞). • The cumulative distribution function of ɛi is thus: • The shape of the Fréchet distribution is similar to many other distributions that are defined on the positive real axis. 12/09/2021 37

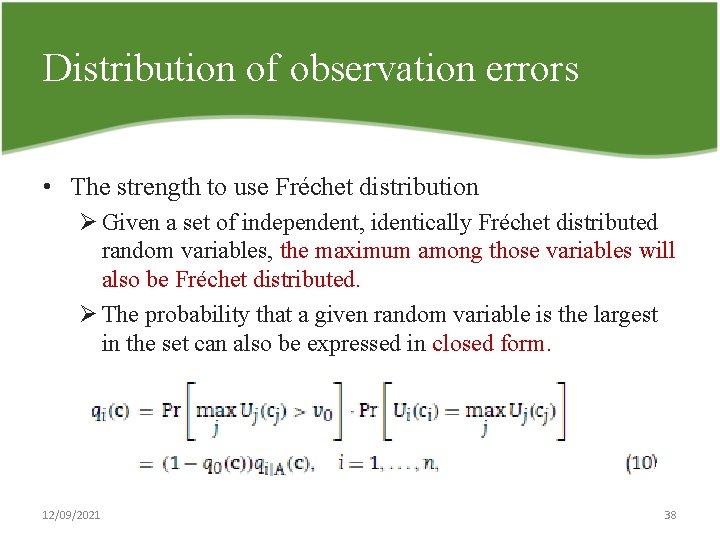
Distribution of observation errors • The strength to use Fréchet distribution Ø Given a set of independent, identically Fréchet distributed random variables, the maximum among those variables will also be Fréchet distributed. Ø The probability that a given random variable is the largest in the set can also be expressed in closed form. 12/09/2021 38

Distribution of observation errors • The variance of ɛi is strictly decreasing in the shape parameter λ, which is used throughout this paper to represent the perceptive ability of the attacker. • λ close to 0 Ø The observation errors completely dominate the true utilities. →The attacker chooses an action largely at random! • Large values of λ Ø The observed utilities are close to the true utilities. → The actions of the attacker tend to those predicted from the baseline model! 12/09/2021 39

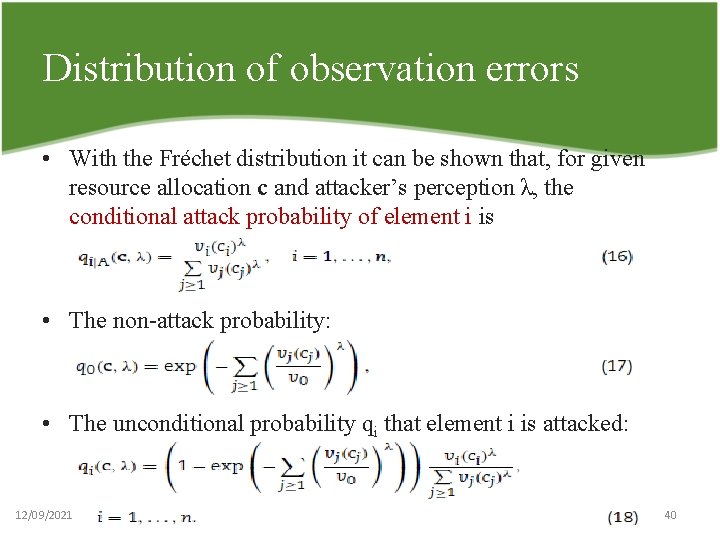
Distribution of observation errors • With the Fréchet distribution it can be shown that, for given resource allocation c and attacker’s perception λ, the conditional attack probability of element i is • The non attack probability: • The unconditional probability qi that element i is attacked: 12/09/2021 40

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 41

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 42

Properties of the model • Effects of attacker perception • Effects of defense resources • Optimal resource allocation 12/09/2021 43

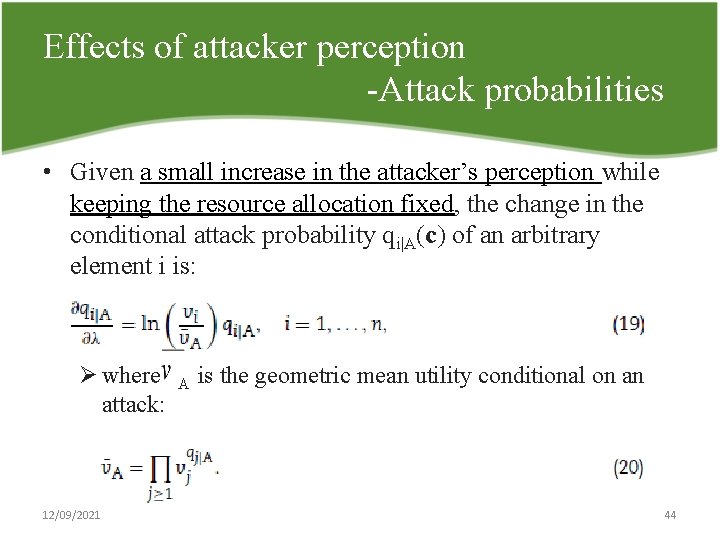
Effects of attacker perception Attack probabilities • Given a small increase in the attacker’s perception while keeping the resource allocation fixed, the change in the conditional attack probability qi|A(c) of an arbitrary element i is: Ø where attack: 12/09/2021 A is the geometric mean utility conditional on an 44

Effects of attacker perception Attack probabilities • The change in the non attack probability q 0 Ø where , which we will callunconditional the deterrenceattack factor, is • All in all, the change in the defined as: q can be written as: probability i Ø 12/09/2021 serves as an adjustment of q 0 due to the fact that the utility of not attacking the system, v 0, is observed without error unlike the other utilities. 45

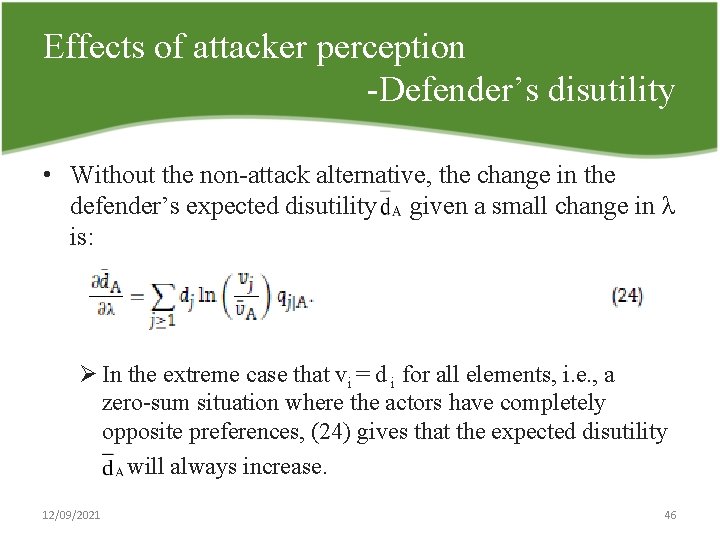
Effects of attacker perception Defender’s disutility • Without the non attack alternative, the change in the defender’s expected disutility given a small change in λ is: Ø In the extreme case that vi = d i for all elements, i. e. , a zero sum situation where the actors have completely opposite preferences, (24) gives that the expected disutility will always increase. 12/09/2021 46

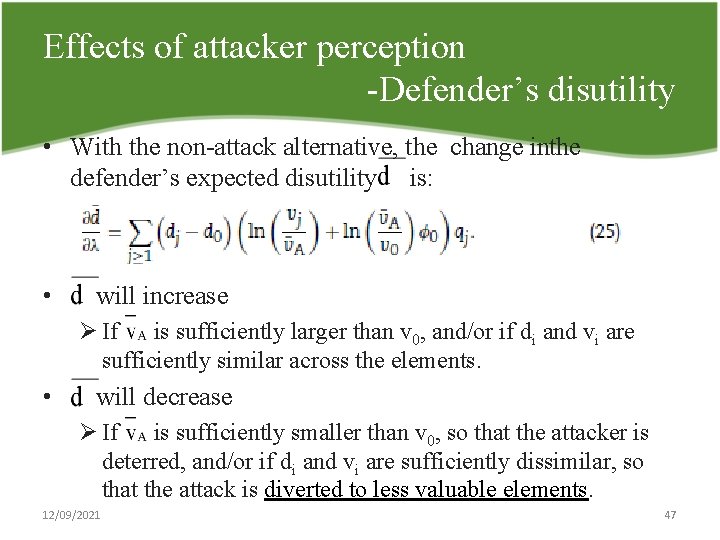
Effects of attacker perception Defender’s disutility • With the non attack alternative, the change inthe defender’s expected disutility is: • will increase Ø If is sufficiently larger than v 0, and/or if di and vi are sufficiently similar across the elements. • will decrease Ø If is sufficiently smaller than v 0, so that the attacker is deterred, and/or if di and vi are sufficiently dissimilar, so that the attack is diverted to less valuable elements. 12/09/2021 47

Effects of attacker perception Defender’s disutility • The results show that a less perceptive attacker can cause higher disutility for the defender. • This means that a perfectly perceptive attacker need not represent a “worst case” attackscenario against the system. Ø Such an interpretation only holds if the valuation of the defender and the attacker are sufficiently similar or the attacker’s gain from attacking the system is sufficiently high. 12/09/2021 48

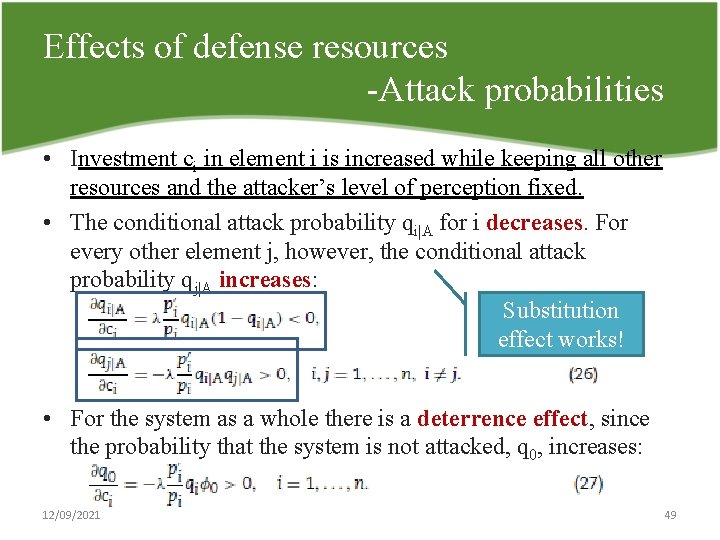
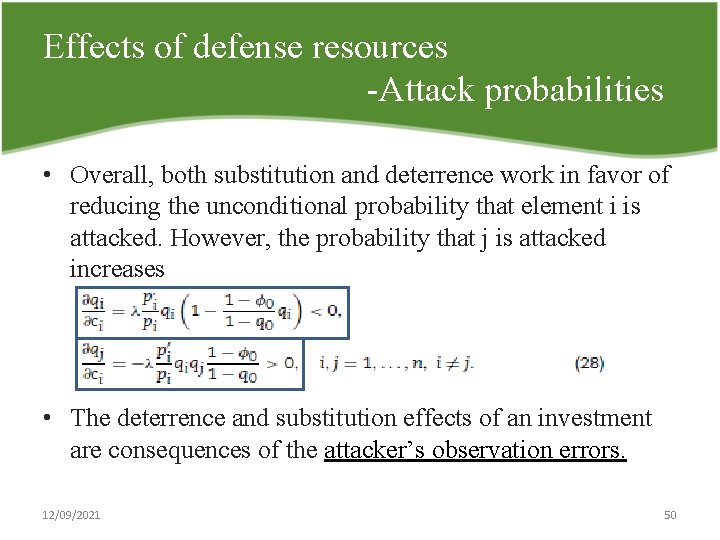
Effects of defense resources Attack probabilities • Investment ci in element i is increased while keeping all other resources and the attacker’s level of perception fixed. • The conditional attack probability qi|A for i decreases. For every other element j, however, the conditional attack probability qj|A increases: Substitution effect works! • For the system as a whole there is a deterrence effect, since the probability that the system is not attacked, q 0, increases: 12/09/2021 49

Effects of defense resources Attack probabilities • Overall, both substitution and deterrence work in favor of reducing the unconditional probability that element i is attacked. However, the probability that j is attacked increases • The deterrence and substitution effects of an investment are consequences of the attacker’s observation errors. 12/09/2021 50

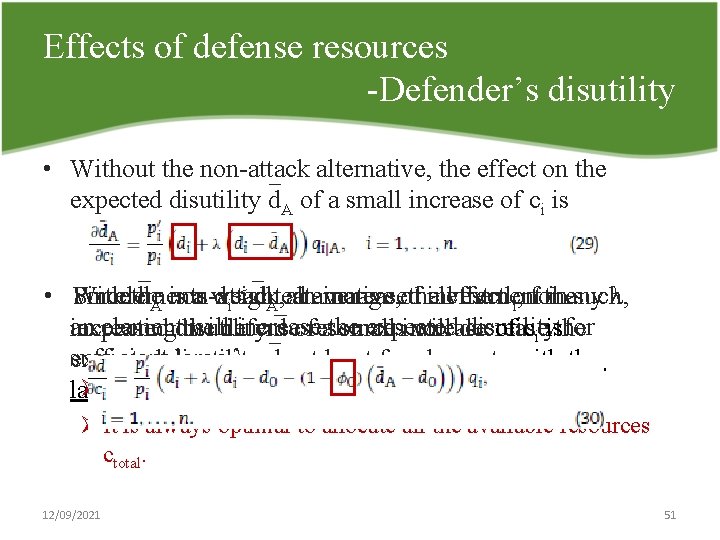
Effects of defense resources Defender’s disutility • Without the non attack alternative, the effect on the expected disutility d. A of a small increase of ci is di< d. A, alternative, anaverage increased inany suchλ, • For Withelements Since the d. A is non attack a weighted of theinvestment alleffect the dion , for the an elementdisutility willdefense increase expected disutility for increasing expected the d ofresources athe small increase will decrease of ci isthe sufficient large λ. d. A at least for elements with the expected disutility ØSpending more resources on an element can actually largest utility. the situation Ømake It is always optimalworse. to allocate all the available resources ctotal. 12/09/2021 51

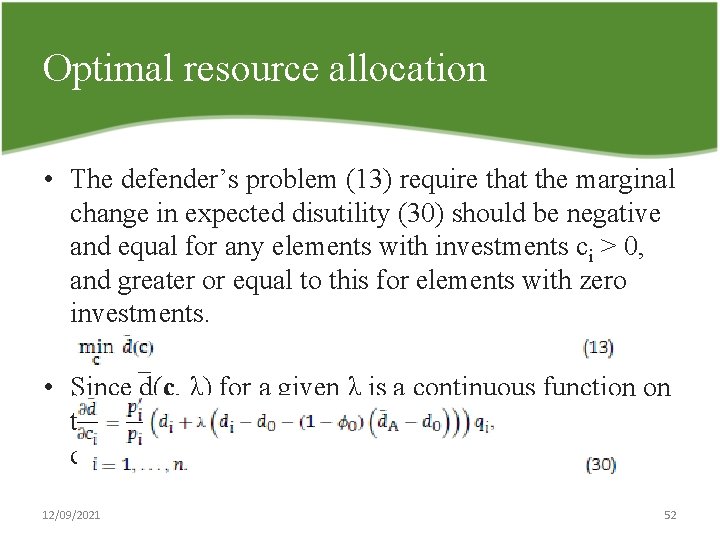
Optimal resource allocation • The defender’s problem (13) require that the marginal change in expected disutility (30) should be negative and equal for any elements with investments ci > 0, and greater or equal to this for elements with zero investments. • Since d(c, λ) for a given λ is a continuous function on the closed, bounded domain defined by C, the defender’s problem has an optimal solution. 12/09/2021 52

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 53

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 54

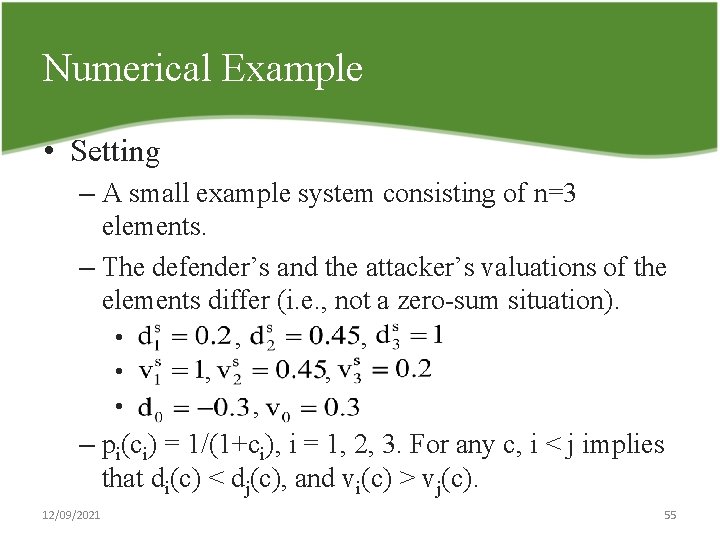
Numerical Example • Setting – A small example system consisting of n=3 elements. – The defender’s and the attacker’s valuations of the elements differ (i. e. , not a zero sum situation). • • • , , , – pi(ci) = 1/(1+ci), i = 1, 2, 3. For any c, i < j implies that di(c) < dj(c), and vi(c) > vj(c). 12/09/2021 55

Numerical Example • Influence of attacker perception ØHow the optimal resource allocation varies with the antagonist’s level of perception λ? ØAssume here that the size of the defense budget is ctotal = 1. 12/09/2021 56

Numerical Example Influence of attacker perception 12/09/2021 57

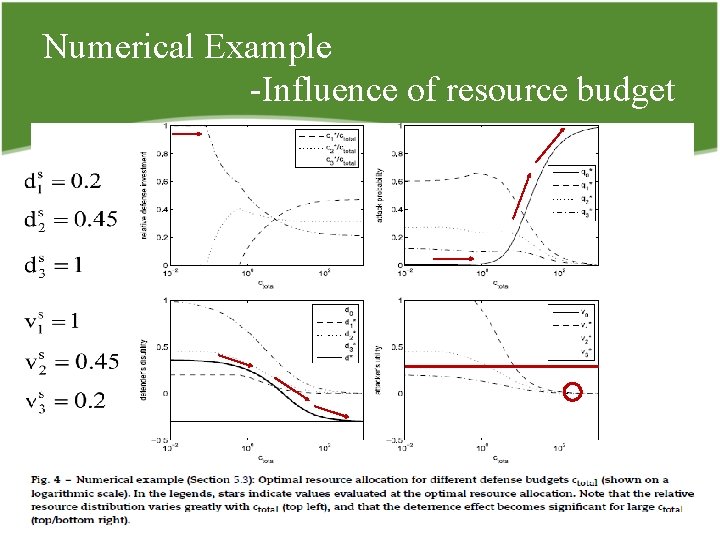
Numerical Example • Influence of resource budget ØHow the optimal resource allocation depends on the size of the defense budget ctotal? ØAssume that λ = 1 represents a relatively unperceptive antagonist. 12/09/2021 58

Numerical Example Influence of resource budget 12/09/2021 59

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 60

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 61

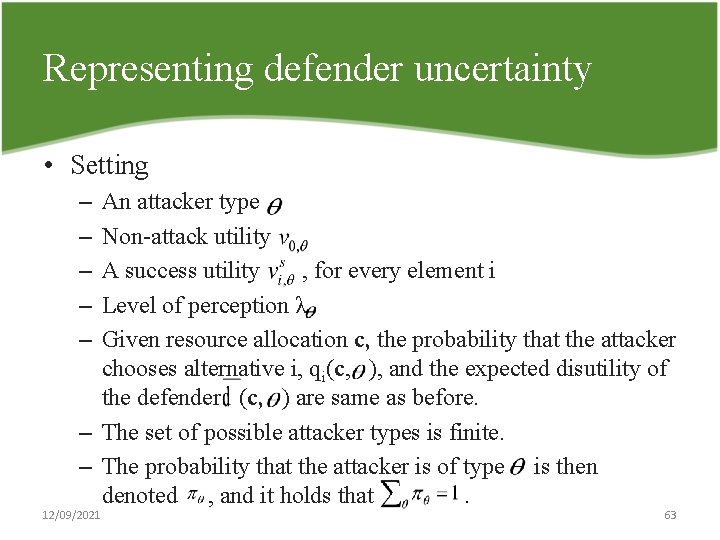
Representing defender uncertainty • This paper has assumed that the defender has complete information about the attacker’s characteristics, except for the actual outcomes ui of the attacker’s observed utilities. • If the defender’s uncertainty can be represented as a probability distribution across possible attacker characteristics or “types”, we can model the situation as a Bayesian game. 12/09/2021 62

Representing defender uncertainty • Setting – – – An attacker type Non attack utility A success utility , for every element i Level of perception λ Given resource allocation c, the probability that the attacker chooses alternative i, qi(c, ), and the expected disutility of the defender (c, ) are same as before. – The set of possible attacker types is finite. – The probability that the attacker is of type is then denoted , and it holds that. 12/09/2021 63

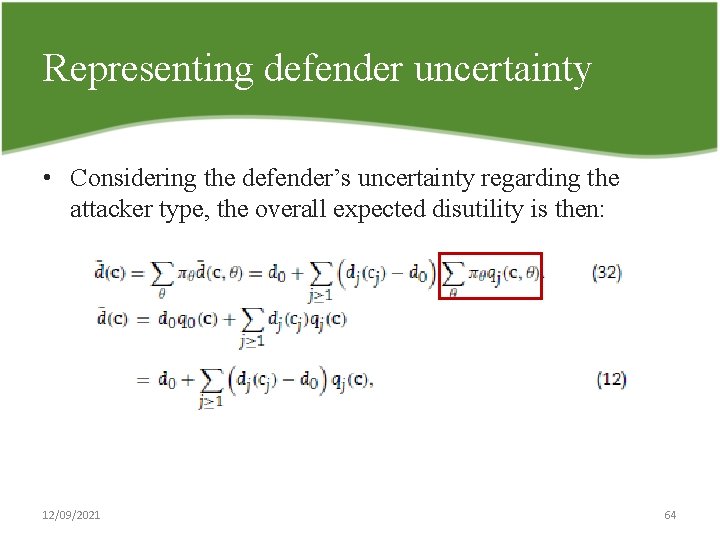
Representing defender uncertainty • Considering the defender’s uncertainty regarding the attacker type, the overall expected disutility is then: 12/09/2021 64

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 65

Agenda • • Introduction Baseline model with perfect observations Model with imperfect observations Properties of the model Numerical example Representing defender uncertainty Conclusion 12/09/2021 66

Conclusion • The proposed modeling framework extends a previous game theoretic model with complete information by introducing random observation errors on behalf of the attacker. • A perfectly perceptive attacker need not represent a worst case scenario, i. e. , a less perceptive attacker can cause greater disutility for the defender. • Spending more resources on an element is not necessarily better, since this may redirect the attack to more critical elements, causing the expected disutility for the overall system to rise. • However, if the defense is distributed optimally among targets, 12/09/2021 it is optimal to spend all defense resources. 67

Conclusion • If an attacker has imperfect perception of a system, then one should in general consider a larger number of targets to be in need of protection. • By focusing the defense too narrowly on the optimal scenario, the results show it may be providing a higher chance of success for the antagonist. • An area for further research is to investigate the consequences of imperfect information on behalf of the defender and of optimizing the defense against the “wrong” set of beliefs. 12/09/2021 68

Thanks so much for your listening. � 12/09/2021 69