cool smartcard hacks peter honeyman citi university of











































- Slides: 58

cool smartcard hacks peter honeyman citi university of michigan ann arbor

a little bit about citi u center for information technology integration u founded in 1986 as part of information technology division u now in cio office

citi staff u faculty and staff scientists (3) u researchers and programmers (3) u students (13) – – doctoral (4) masters (1) undergraduate (7) high school (1)

a little more about citi u mission: advance umich info tech environment, transfer results to university, government, industry – research and development “skunkworks” for cio – externally funded, primarily by short-term industry contracts

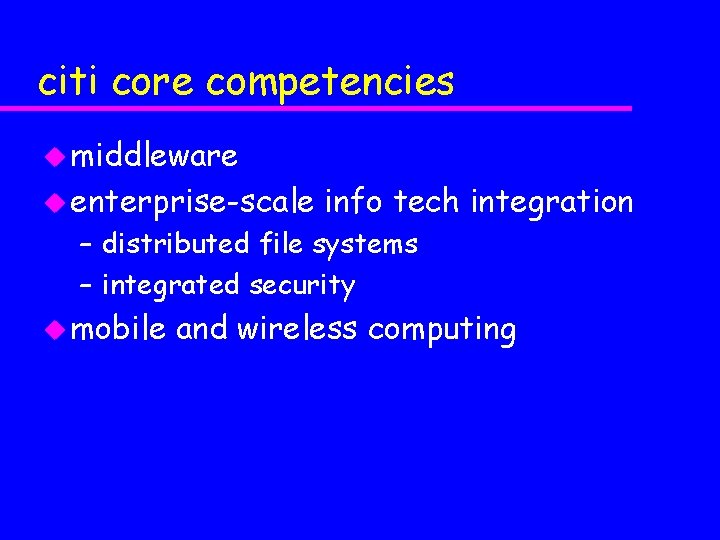
citi core competencies u middleware u enterprise-scale info tech integration – distributed file systems – integrated security u mobile and wireless computing

major advances of the 20 th century u computing u transportation u mobile computing – newton, pilot – superslims – pcs, e. g. , nokia, qualcomm, sprint, etc. u smartcards – a little computing – a lotta mobility

smartcards are cool because u they are tamper resistant u they can do a little crypto u they have a restricted (albeit bizarre) (yet functional) api that can protect secrets u they can store keys – in fact, they have special key files

principal applications u stored value – phone cards – electronic purse u secure identification – challenge/response protocols – gsm phone identity

how smartcards are used u e-purse, e. g. , mcard, visacash, mondex – many spectacular failures u gsm authentication u information control – german healthcard u closed market applications – Do. D card – welfare card

impediments to use u infrastructure requirements u integration with contemporary computing environments – especially security middleware

outline u smartcard ip u kerberos client u smartcard-based file systems u secure booting u palm pilot hacks

ip on smartcard u expand smartcard accessibility to the internet u network protocols on smartcard – network service unmodified u smartcard as a mobile computer – bring your ip address with you

javacard web server u minimal functional server u one connection at a time u minimal state maintenance – tcp port – file name – tcp state

platform u schlumberger u 16 cyberflex access KB eeprom u iso 7816 smartcard u java card 2. 0 u 1. 2 KB ram

http only u subset of http 1. 0 (or higher) u GET method only

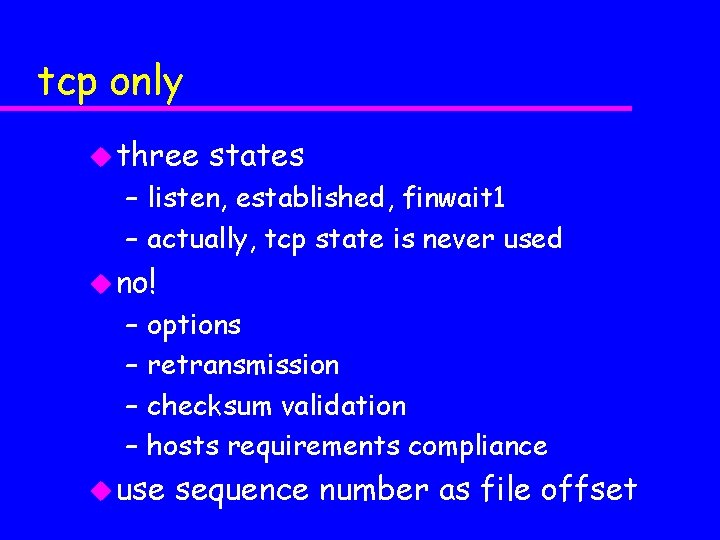
tcp only u three states – listen, established, finwait 1 – actually, tcp state is never used u no! – – options retransmission checksum validation hosts requirements compliance u use sequence number as file offset

ip only u no! – options – reassembly u~ 250 byte mtu

tunnel daemon u “near” side: webcard ip address u “far” side: iso 7816 framing u openbsd implementation

cardlet details u~ 1200 byte codes u leaves about 13 k for content

webcard summary u performance: ~ 130 bytes/sec. u copy content to card with scfs u open source u http: //smarty. citi. umich. edu

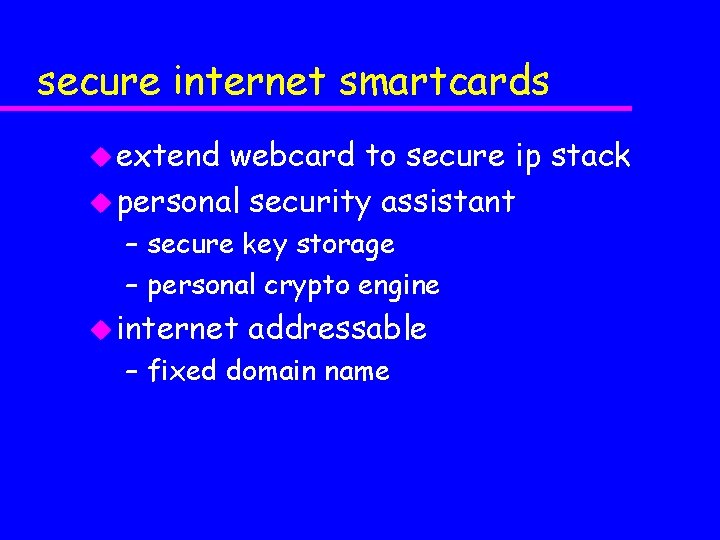
secure internet smartcards u extend webcard to secure ip stack u personal security assistant – secure key storage – personal crypto engine u internet addressable – fixed domain name

why a smartcard on the internet? u convenient – e. g. , one office, many computers, one reader u secure – smartcard has excellent physical security u mobile – you can even sit on it

how? u establish secure, authenticated channel to card – PIN for authentication – session key established with SPEKE

SPEKE u DH + PIN-based common base u DH – A B: gx mod r – B A: gy mod r – K=gxy mod r u SPEKE: g = f(PIN)

performance

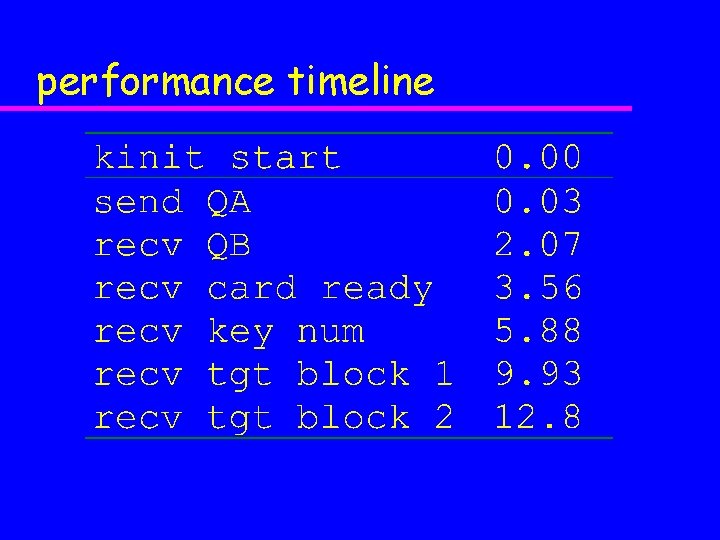
performance timeline

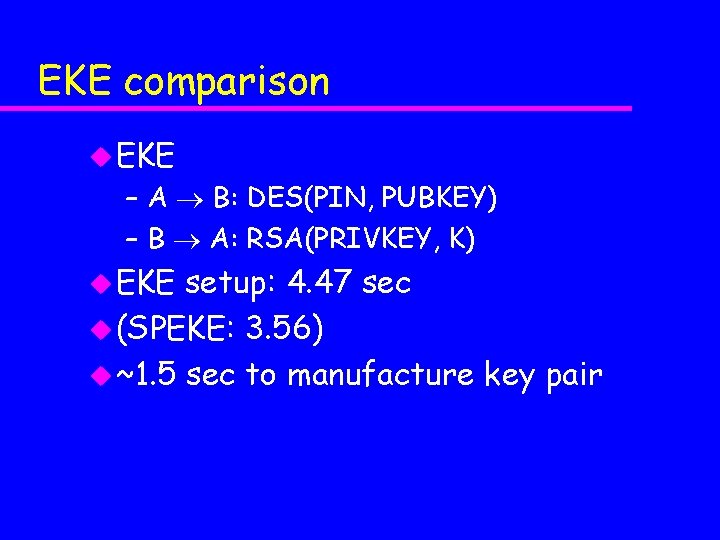
EKE comparison u EKE – A B: DES(PIN, PUBKEY) – B A: RSA(PRIVKEY, K) u EKE setup: 4. 47 sec u (SPEKE: 3. 56) u ~1. 5 sec to manufacture key pair

smartcard integration with kerberos u university of michigan computing environment is protected by kerberos – So are mit, cmu, stanford, cornell, … – product offerings from microsoft, ibm, oracle. . . u public – (yet) key cryptography is not practical u kerberos security limitations: – lacks external encryption device – lacks secure key storage – passwords vulnerable to dictionary attack u smartcards can solve these problems

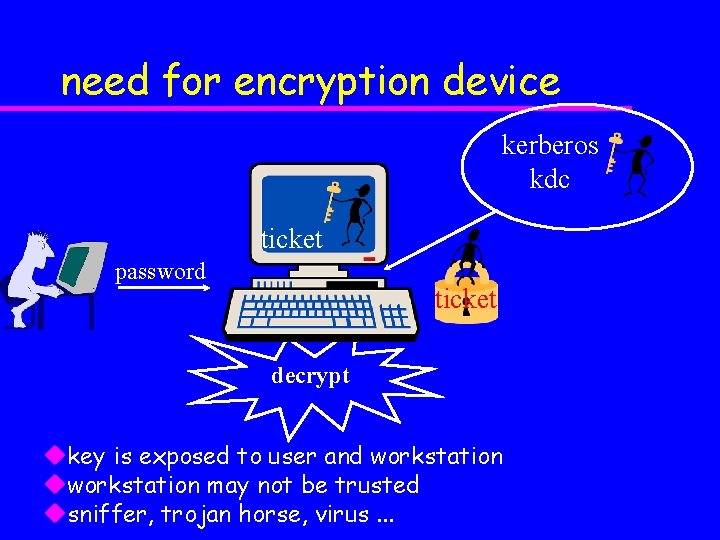
need for encryption device kerberos kdc ticket password ticket decrypt ukey is exposed to user and workstation uworkstation may not be trusted usniffer, trojan horse, virus. . .

need for secure storage u keys stored on hard disk or in memory are vulnerable u hard disks are not secure – adversary with administrative rights can access keys – data in a hard disk may be backed up in an unprotected mass storage device u memory is not secure – adversary can scan memory – data in memory can be paged out to a hard disk

dictionary attack u create a list of english words, names, etc. u derive u obtain keys from the words in the list a <plaintext, ciphertext> pair – Also star wars, german, shakespeare, … – thx 1138 is a vulnerable password! : -( – kerberos gives up <plaintext, ciphertext> easily u decrypt ciphertext with the derived key – if plaintext recovered, password is exposed u umich: 1997 > 4, 000 vulnerable accounts in – 2, 400 in 1999

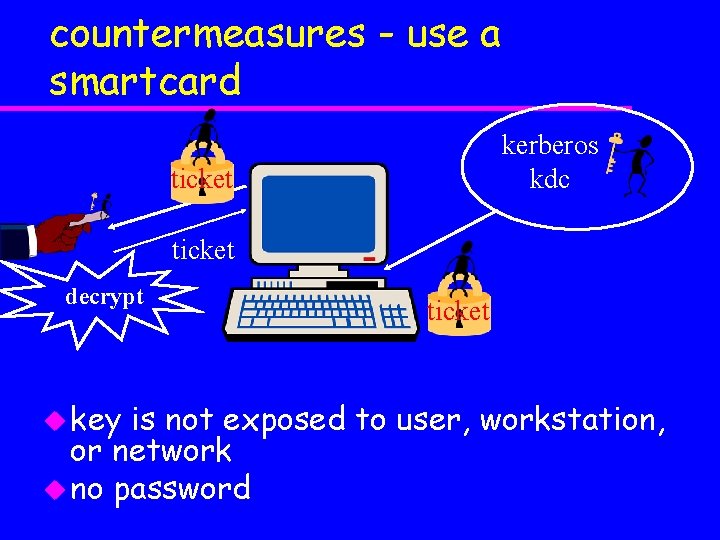
countermeasures - use a smartcard kerberos kdc ticket decrypt u key ticket is not exposed to user, workstation, or network u no password

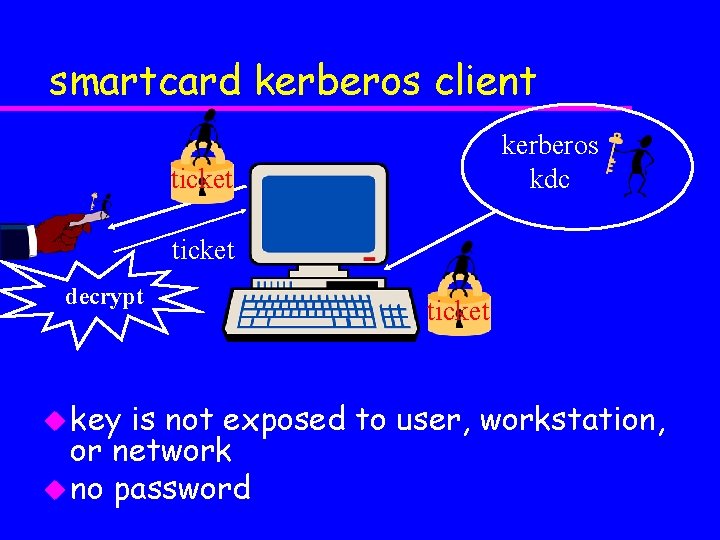
smartcard kerberos client kerberos kdc ticket decrypt u key ticket is not exposed to user, workstation, or network u no password

implementation u starcos v. 2. 1 from giesecke & devrient u cyberflex access from schlumberger u mit kerberos v 5 -1. 0. 5 client u kerberos server unmodified for global interoperability … well, almost – ticket length > 200 bytes, requires cbc – des_cbc_crc method uses key as ivec – modify server to permit des_cbc_md 5

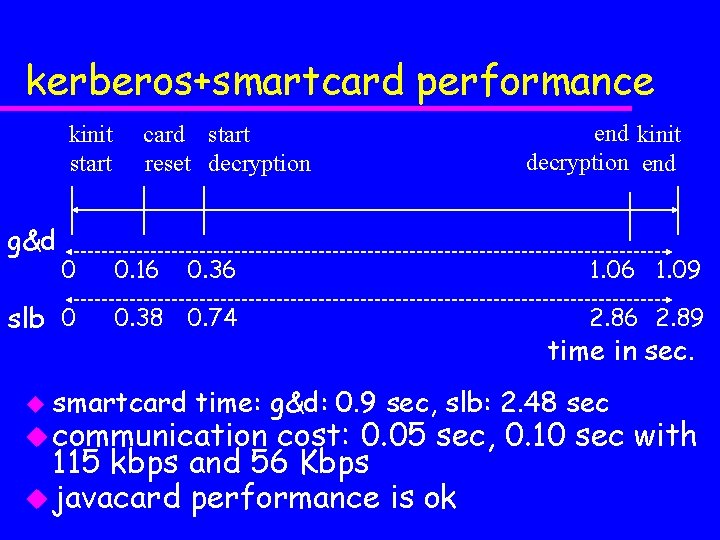
kerberos+smartcard performance kinit start g&d 0 slb 0 card start reset decryption 0. 16 end kinit decryption end 0. 36 1. 09 0. 38 0. 74 2. 86 2. 89 u smartcard time in sec. time: g&d: 0. 9 sec, slb: 2. 48 sec u communication cost: 0. 05 sec, 0. 10 sec with 115 kbps and 56 Kbps u javacard performance is ok

kerberos+smartcard w-i-p u udp/ip implementation u store ticket on smartcard u pc/sc library for interoperability u server ticket generation – using ibm 4758 secure pci 486

smartcard filesystem (scfs) u iso-7816 – standard smartcard interface – message framing protocol (too primitive to be usable) – many vendor dependencies u smartcard programming toolkits – ibm mfc, microsoft pc/sc, opencard framework, emv’ 96, pkcs#11, … – smartcard-specific everything: language, api, toolkit, library, application, etc. – hassle learning toolkit after toolkit – api dependencies

scfs goals and policies u integrate a smartcard with unix – vfs: unix filesystem api u take advantage of unix environment – allows sophisticated unix commands (cd, ls, cat. . . ) and systems calls (open, close, read, write …) – access through symlinks u any iso-7816 smartcard u easy integration with applications – – netscape cookies pgp private keyring kerberos tickets ssh private key

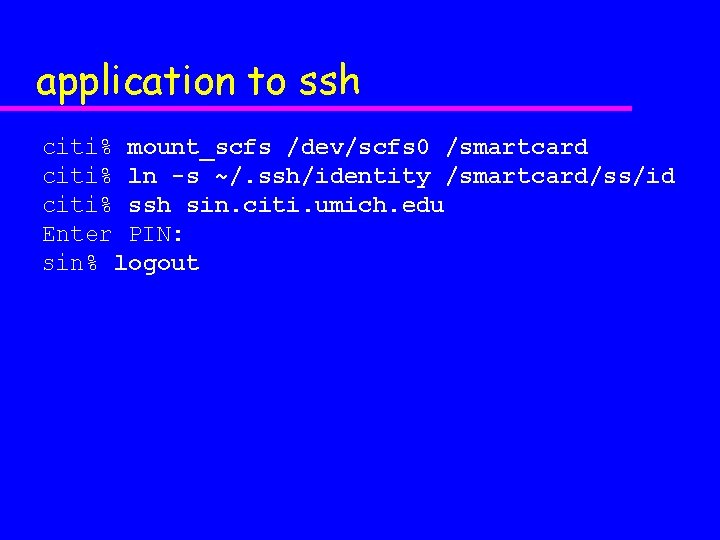
application to ssh citi% mount_scfs /dev/scfs 0 /smartcard citi% ln -s ~/. ssh/identity /smartcard/ss/id citi% ssh sin. citi. umich. edu Enter PIN: sin% logout

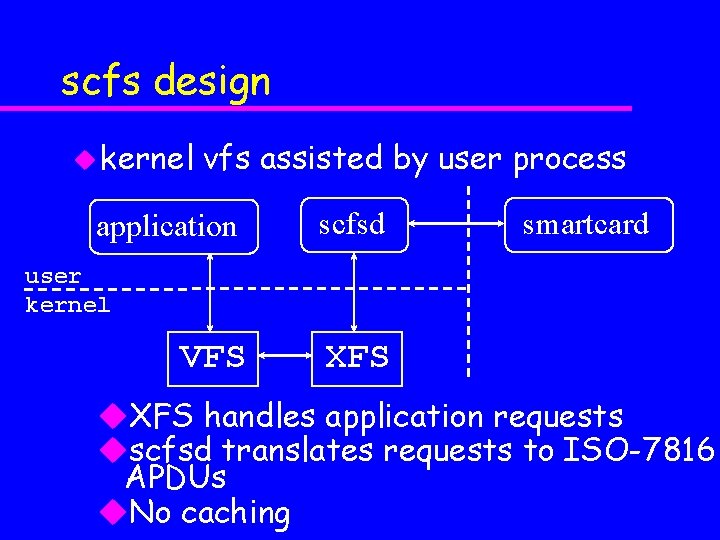
scfs design u kernel vfs assisted by user process application scfsd smartcard user kernel VFS XFS u. XFS handles application requests uscfsd translates requests to ISO-7816 APDUs u. No caching

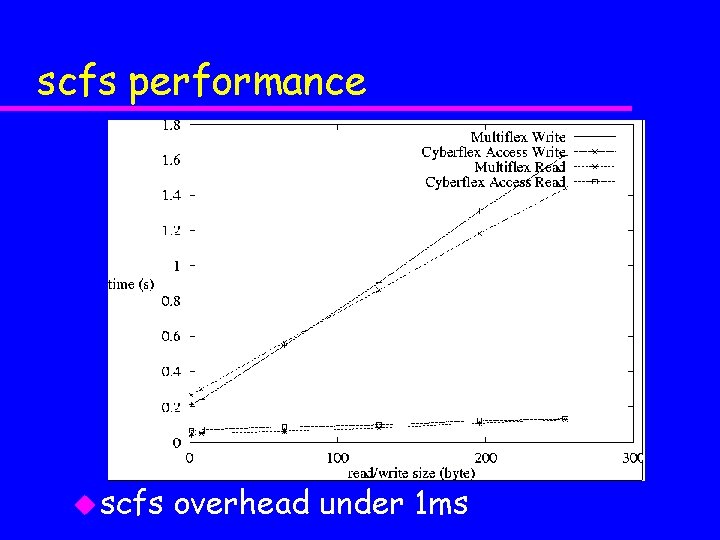
scfs performance u scfs overhead under 1 ms

scfs problem areas u order of remove u directories and metadata

directory entry file u iso-7816 does not have the right metadata – file type, size, age u required for ls, cat u Hack: “. i” in every directory

abstraction mismatch u some iso-7816 -4 features do not fit the unix filesystem abstraction u creat(), mkdir() need size u crypto commands (authentication, verify key, …) u hack: ioctl()

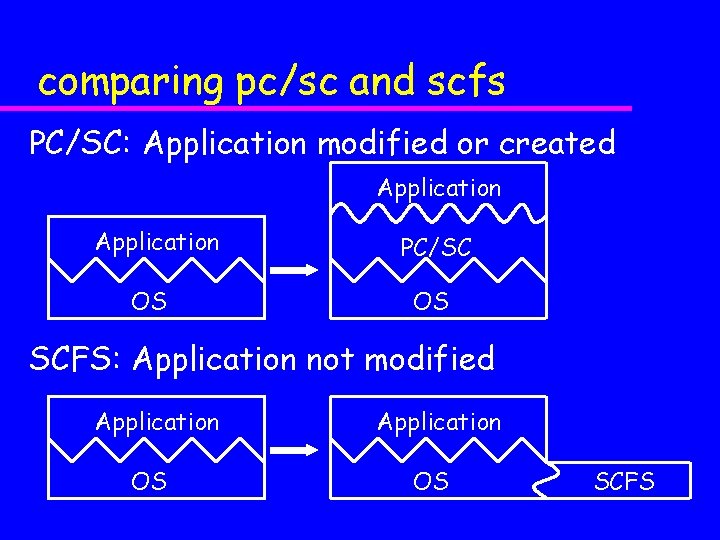
comparing pc/sc and scfs PC/SC: Application modified or created Application OS PC/SC OS SCFS: Application not modified Application OS SCFS

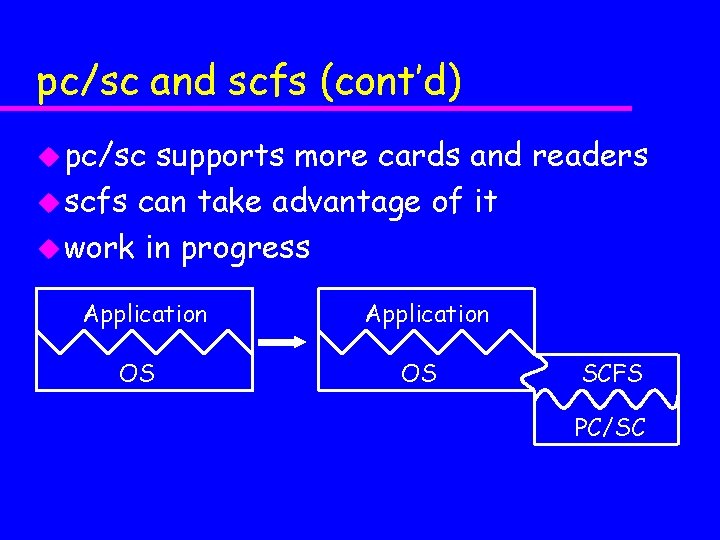
pc/sc and scfs (cont’d) u pc/sc supports more cards and readers u scfs can take advantage of it u work in progress Application OS SCFS PC/SC

scfs extensions u encrypted file system u key per file, derived from smartcard master key u 300 msec. overhead to derive key – caching keys helps

scfs conclusion u powerful, flexible api u overhead is small u useful as a low-level development – ls, cd, pwd, emacs, etc. u secure tool storage for user profiles, web cookies, kerberos tickets, private keys, etc.

secure booting with smartcard u netboot aegis from to load an integrity -checked specialized os u os checks macs stored on a smartcard u so check the kernel image integrity u and boot u check integrity of important applications (kerberos kdc, databases, etc. ) with the smartcard u can boot linux, openbsd, win 9 x, …

secure bootstrap with smartcard u signed executables for software integrity check u hardware-based solutions – secure coprocessor, aegis (from upenn) – secure, but hard to configure u software-based solutions – tripwire, authenticode – but is os trusted?

code signing with smartcard u use aegis to boot a specialized os (boot os) u store macs in a smartcard u check the kernel integrity (second os) with the smartcard u check integrity of important applications (kerberos kdc, databases, etc. ) with the smartcard

secure booting summary u multi-level bootstrap, with assurance at each level u can boot linux, openbsd, win 9 x

palm pilot hacks u palmreader, software tools u smartcard explorer u blaze rke cipher – appropriate cipher for length-preserving file encryption using smartcard u s/key calculator u value checker (mcard, visacash, mondex) – and transfer? u encrypted beam?

projects under incubation u extend ip stack – sun rpc on smartcard (rmi wrapper? shrpc? ) u ldap server on ip smartcard u pki based user authentication u ssl between smartcard and web server (to send data securely), or ssl between client and smartcard web server u cyberflex simera. (ip over sms? ) u new os for javacard

summary: citi’s focus u secure – – computing secure storage authentication secure booting application integration u convenient use of smartcard – operating system extensions – internet access – pda integration

publications u u u N. Itoi and P. Honeyman, “Practical Security Solutions with Smartcards, ” in Proc. 7 th IEEE Workshop on Hot Topics in Operating Systems, Rio Rico, AZ (March 1999) N. Itoi and P. Honeyman, "Smartcard Integration with Kerberos V 5, " in Proc. USENIX Workshop on Smartcard Technology, Chicago (May 1999) N. Itoi, P. Honeyman, and J. Rees, "SCFS: A UNIX Filesystem for Smartcards, ” in Proc. USENIX Workshop on Smartcard Technology, Chicago (May 1999)

publications u u N. Itoi, "Secure Coprocessor Integration with Kerberos V 5, ” in Proc. USENIX Security'2000, Denver (July 2000). ] N. Itoi, P. Honeyman, and T. Fukuzawa, “Secure Internet Smartcards, ” in Proc. Java Card Workshop, Cannes (September 2000). J. Rees and P. Honeyman, "Webcard: a Java Card web server, " in Proc. IFIP CARDIS 2000, Bristol, UK (September 2000) P. Honeyman, “New I/O Models for Smartcards” (in preparation).

any questions? http: //www. citi. umich. edu/
 [email protected]
[email protected] Mondex smartcard
Mondex smartcard Mondex motorola
Mondex motorola Andrew honeyman
Andrew honeyman She hacks purple
She hacks purple Savvas hacks
Savvas hacks The hacks
The hacks Art teacher hacks
Art teacher hacks Search engine hacks
Search engine hacks Asian hackz
Asian hackz Mushrooms hoax. stop hacks
Mushrooms hoax. stop hacks Damian gordon
Damian gordon Ddo hacks
Ddo hacks Citi linus torvalds
Citi linus torvalds Drexel citi training
Drexel citi training Uvm citi training
Uvm citi training Wvu citi training
Wvu citi training Citi commercial cards
Citi commercial cards Autonomn
Autonomn Citi mission statement
Citi mission statement Ohsu citi
Ohsu citi Citi training drexel
Citi training drexel Citi apache cassandra
Citi apache cassandra Ub click irb
Ub click irb Citi training purdue
Citi training purdue Cmu citi training
Cmu citi training Citi linus torvalds
Citi linus torvalds Iu citi
Iu citi Citi bike data analysis
Citi bike data analysis Precizează timpul verbelor din text cunosc au suit
Precizează timpul verbelor din text cunosc au suit Citi training flashcards
Citi training flashcards Uc davis irb
Uc davis irb Corsair society uga
Corsair society uga David ingram citi
David ingram citi Citi ufpe
Citi ufpe Citigroup transaction services
Citigroup transaction services Autonomn
Autonomn Usf irb
Usf irb Citi training ucf
Citi training ucf Citi training uci
Citi training uci Irb pitt
Irb pitt Unl nugrant
Unl nugrant Citi gtcc
Citi gtcc Unm hrpo
Unm hrpo Ucla webirb
Ucla webirb Msu click irb
Msu click irb Usc citi training
Usc citi training What is pain
What is pain Citi training penn state
Citi training penn state Wfu irb
Wfu irb Citi global transaction services
Citi global transaction services Benjamin fontes
Benjamin fontes Balcon authorization citi
Balcon authorization citi 沈榮麟
沈榮麟 Cool chilly cold freezing
Cool chilly cold freezing Cool rap rhymes
Cool rap rhymes We real cool poem meaning
We real cool poem meaning Cold cool
Cold cool Tundra unique facts
Tundra unique facts