Smart Theory Meets Smartcard Practice JeanJacques Quisquater jjqdice










- Slides: 22

Smart Theory Meets Smartcard Practice Jean-Jacques Quisquater jjq@dice. ucl. ac. be Research Director CNRS, France and Université catholique de Louvain, Louvain-la-Neuve, Belgium UCL Crypto Group http: //uclcrypto. org Part of this work done while visiting scientist at MIT-CSAIL © UCL Crypto group – October 2004 – DIMACS - Smart Theory Meets Smartcard Practice

b CONTENTS • Introduction • Smart cards • IBC • Remote integrity • Using bad primitives • Conclusion © UCL Crypto group DIMACS talk - 2004 2

Goal of the talk • Show by examples that thinking with tamperproof and doing crypto with constrained objects is interesting for theoretical and practical purposes. © UCL Crypto group DIMACS talk - 2004 3

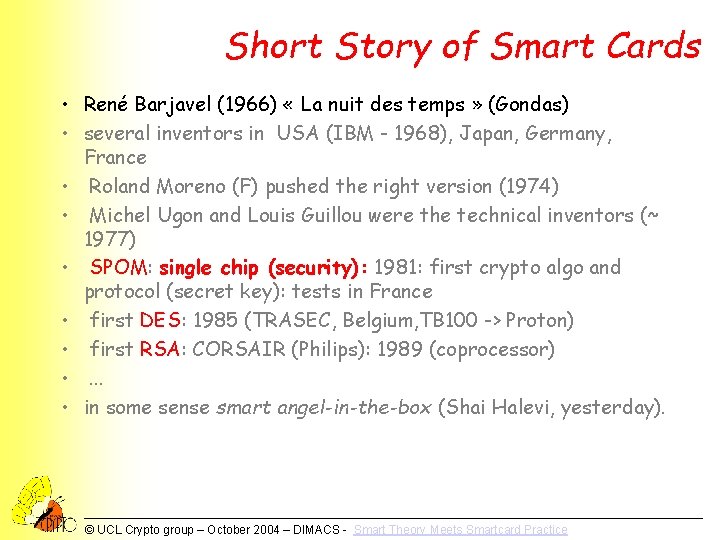
Short Story of Smart Cards • René Barjavel (1966) « La nuit des temps » (Gondas) • several inventors in USA (IBM - 1968), Japan, Germany, France • Roland Moreno (F) pushed the right version (1974) • Michel Ugon and Louis Guillou were the technical inventors (~ 1977) • SPOM: single chip (security): 1981: first crypto algo and protocol (secret key): tests in France • first DES: 1985 (TRASEC, Belgium, TB 100 -> Proton) • first RSA: CORSAIR (Philips): 1989 (coprocessor) • . . . • in some sense smart angel-in-the-box (Shai Halevi, yesterday). © UCL Crypto group – October 2004 – DIMACS - Smart Theory Meets Smartcard Practice

Ring by Moreno (1974) and first smart card (1980) © UCL Crypto group DIMACS talk - 2004 5

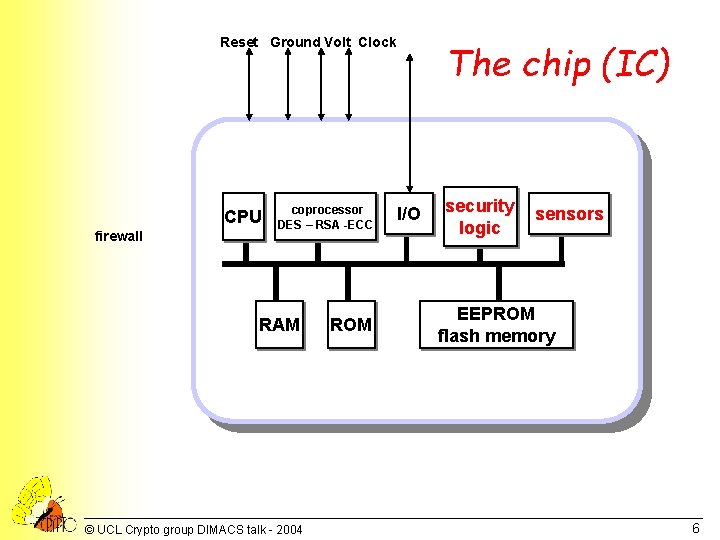
Reset Ground Volt Clock CPU firewall coprocessor DES – RSA -ECC RAM © UCL Crypto group DIMACS talk - 2004 ROM The chip (IC) I/O security logic sensors EEPROM flash memory 6

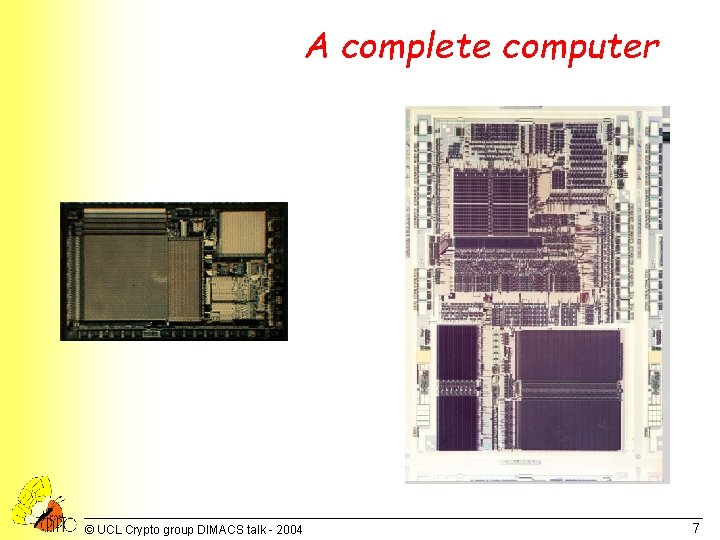
A complete computer © UCL Crypto group DIMACS talk - 2004 7

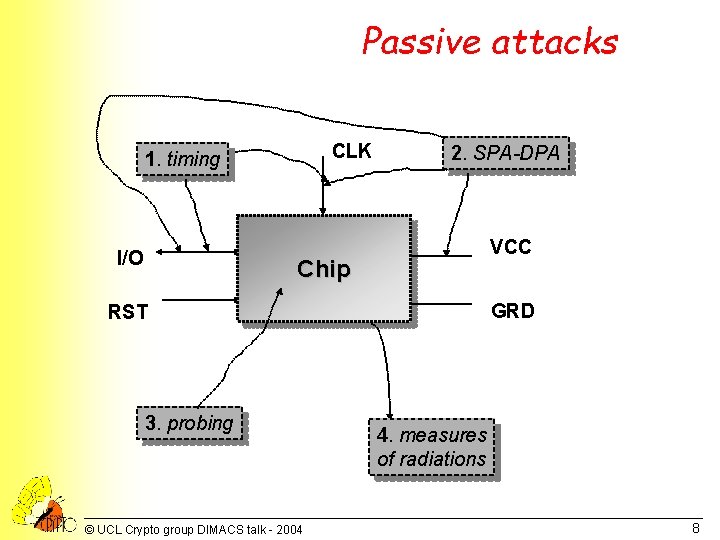
Passive attacks CLK 1. timing I/O 2. SPA-DPA VCC Chip GRD RST 3. probing © UCL Crypto group DIMACS talk - 2004 4. measures of radiations 8

Active fault attacks (Bellcore attack) Key=1010110. . . © UCL Crypto group DIMACS talk - 2004 9

© UCL Crypto group DIMACS talk - 2004 10

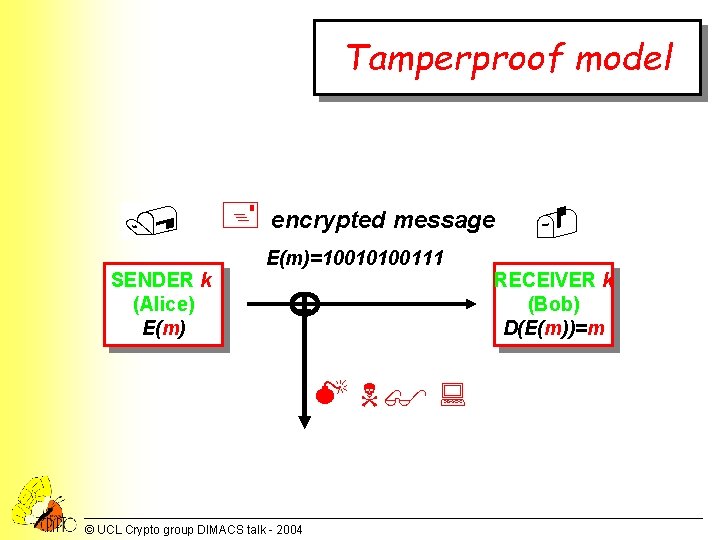
Tamperproof model / + encrypted message E(m)=10010100111 SENDER k (Alice) E(m) RECEIVER k (Bob) D(E(m))=m M N$ : © UCL Crypto group DIMACS talk - 2004

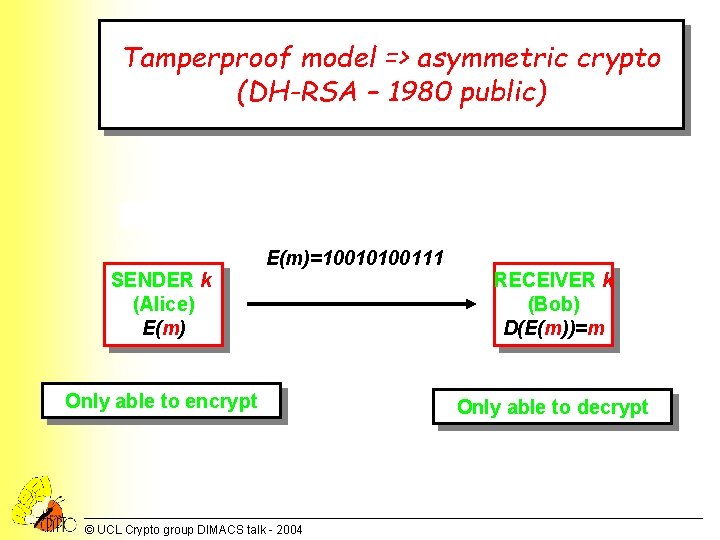
Tamperproof model => asymmetric crypto (DH-RSA – 1980 public) E(m)=10010100111 SENDER k (Alice) E(m) RECEIVER k (Bob) D(E(m))=m Only able to encrypt Only able to decrypt © UCL Crypto group DIMACS talk - 2004

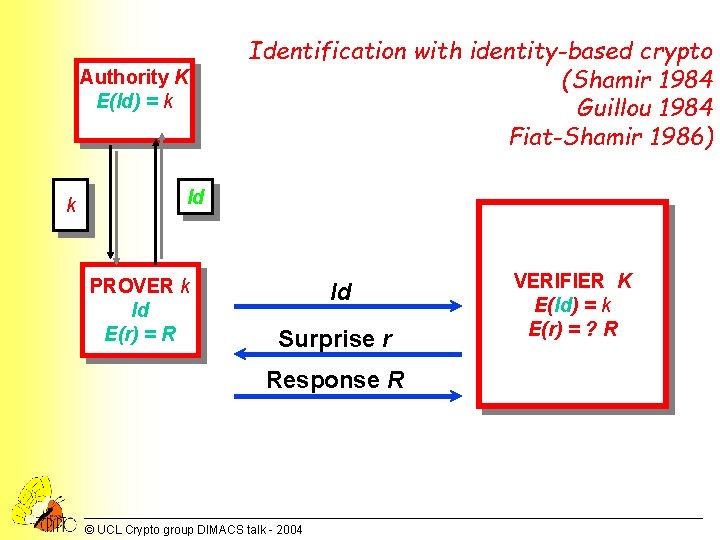
Authority K E(Id) = k k Identification with identity-based crypto (Shamir 1984 Guillou 1984 Fiat-Shamir 1986) Id PROVER k Id E(r) = R Id Surprise r Response R © UCL Crypto group DIMACS talk - 2004 VERIFIER K E(Id) = k E(r) = ? R

Identity-Based Encryption • Adi Shamir: Identity-Based Cryptosystems and Signature Schemes. CRYPTO 1984: 47 -53. • Yvo Desmedt, Q. : Public-Key Systems Based on the Difficulty of Tampering (Is There a Difference Between DES and RSA? ). CRYPTO 1986: 111 -117. • Dan Boneh, Matthew K. Franklin: Identity-Based Encryption from the Weil Pairing. CRYPTO 2001: 213 -229. • Clifford Cocks: An Identity Based Encryption Scheme Based on Quadratic Residues Source LNCS, Proc. of the 8 th IMA Intern. Conf. on Cryptography and Coding 2001: 360 -363. © UCL Crypto group DIMACS talk - 2004 14

Hierarchical IBC? • Was done also in 1984 • The easy way: you iterate the process with cards being mother, daughter, granddaughter, aso. © UCL Crypto group DIMACS talk - 2004 15

Tamperproof model useful? • Sometimes proof of concept • Sometimes useful to simulate publickey crypto in closed systems • Yes, but we don’t know how to translate tamperproof into trapdoor in a crypto function. © UCL Crypto group DIMACS talk - 2004 16

First smart card (1980) © UCL Crypto group DIMACS talk - 2004 17

Security with two chips or with a unsecure server? • One chip is tamperproof but slow, • The other one is a unsecure memory or a fast unsecure processor, … • Philippe Béguin, Q. : Secure Acceleration of DSS Signatures Using Insecure Server. ASIACRYPT 1994: 249 -259 • Possible for El gamal signatures with small memory • RSA? • See Philippe Béguin, Q. : Fast Server-Aided RSA Signatures Secure Against Active Attacks. CRYPTO 1995: 57 -69 • but parameters need to be changed due to an attack by Nguyen–Stern (Asiacrypt 1998). Better? • Work in progress © UCL Crypto group DIMACS talk - 2004 18

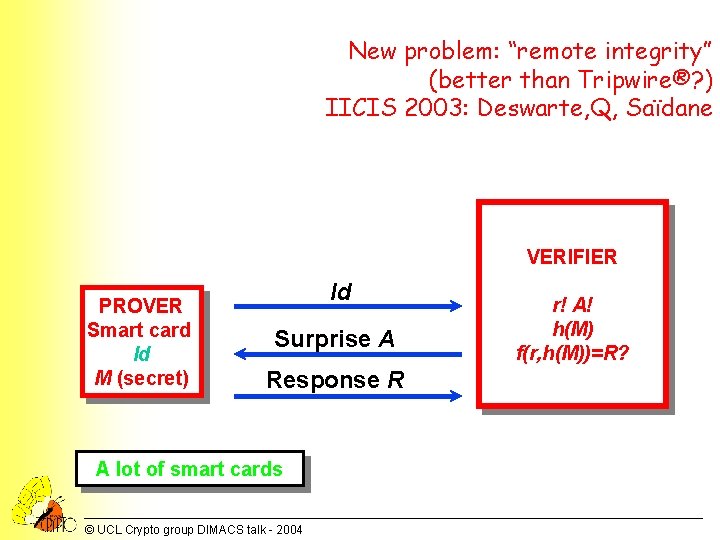
New problem: “remote integrity” (better than Tripwire®? ) IICIS 2003: Deswarte, Q, Saïdane VERIFIER PROVER Smart card Id M (secret) Id Surprise A Response R A lot of smart cards © UCL Crypto group DIMACS talk - 2004 r! A! h(M) f(r, h(M))=R?

Protocol for remote integrity • GENERAL INIT: Let M = (content of the file), integer n = pq (RSA modulus, 1024 bits) public: factorisation is secret a = a random number, 1 <a <n-1, secret (chosen by verifier) • INIT for ONE FILE: h = a. M mod n precomputed by verifier • Verifier generates a random number r and computes challenge A = ar mod n • Smart card computes response: R = AM mod n and send R (or a part of it) • Verifier computes C = hr mod n and checks if R = C = a. Mr mod n • Diffie-Hellman protocol • Problem: Proof! • Work in progress (optimisations) © UCL Crypto group DIMACS talk - 2004 20

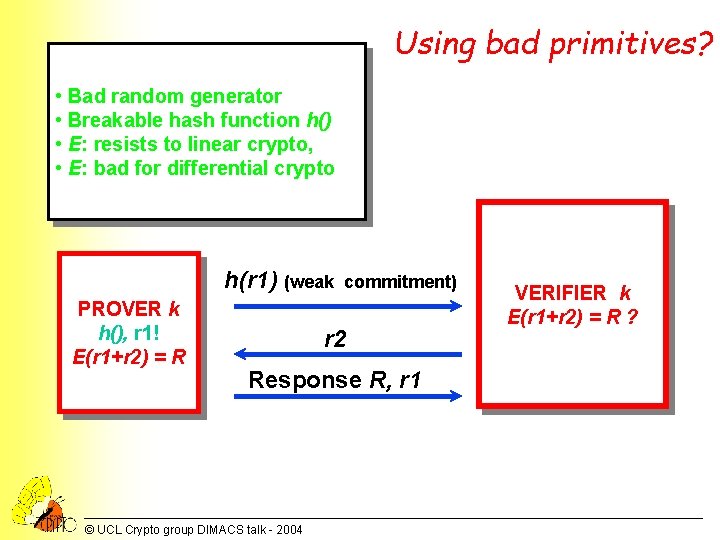
Using bad primitives? • Bad random generator • Breakable hash function h() • E: resists to linear crypto, • E: bad for differential crypto h(r 1) (weak PROVER k h(), r 1! E(r 1+r 2) = R commitment) r 2 Response R, r 1 © UCL Crypto group DIMACS talk - 2004 VERIFIER k E(r 1+r 2) = R ?

General conclusion Thinking theoretically with strongly constrained objects set interesting problems with practical results. Many open problems. UCL© © UCL Crypto group DIMACS talk - 2004 22
 Mondex smartcard
Mondex smartcard Mondex motorola
Mondex motorola Street smarts vs book smarts
Street smarts vs book smarts Smart two men are
Smart two men are It's not how smart you are it's how you are smart
It's not how smart you are it's how you are smart Jeopardy smart
Jeopardy smart It's not how smart you are
It's not how smart you are Street smart vs book smart quotes
Street smart vs book smart quotes Street smart vs book smart quotes
Street smart vs book smart quotes One smart man he felt smart
One smart man he felt smart Where tradition meets tomorrow
Where tradition meets tomorrow Approaches meets masters
Approaches meets masters Piaget meets santa
Piaget meets santa Approaches meets masters
Approaches meets masters Metes and bounds
Metes and bounds Newton meets buzz and woody
Newton meets buzz and woody Macbeth meets the witches
Macbeth meets the witches Approaches meets masters
Approaches meets masters Gatsby chapter 3 questions
Gatsby chapter 3 questions Congress of vienna meets
Congress of vienna meets Narrow band where the ocean meets land
Narrow band where the ocean meets land Jack and jill psychosexual fixation
Jack and jill psychosexual fixation Generally restful like the horizon where the sky meets land
Generally restful like the horizon where the sky meets land