Practical Security With Smartcards Peter Honeyman CITI University
















- Slides: 24

Practical Security With Smartcards Peter Honeyman CITI University of Michigan Ann Arbor

Smartcards: a pragmatic approach u Build on what we have – Use existing infrastructure (UMCE) » UNIX filesystem; mail, web servers » Kerberos » NT GINA – Use open standards (IETF, ISO) – Add secure hardware: smartcard u Integrate smartcard with infrastructure u Secrets in a smartcard remain safe even if hardware / software is compromised

Experimental approach u Home-brew software, hardware

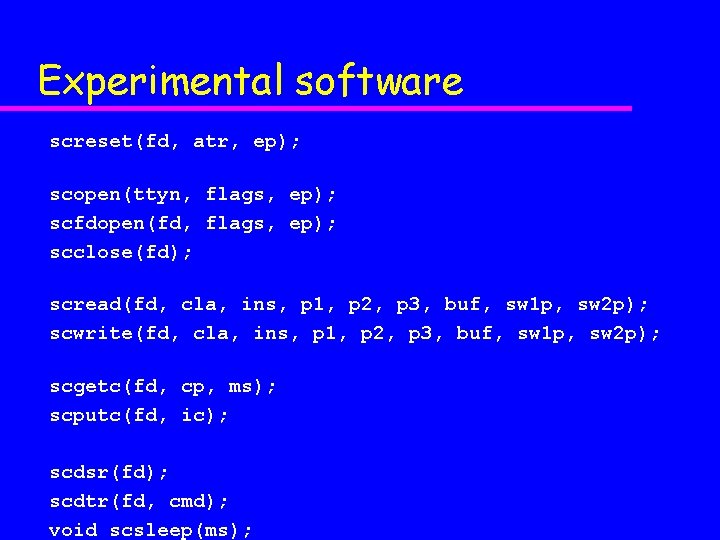
Experimental software screset(fd, atr, ep); scopen(ttyn, flags, ep); scfdopen(fd, flags, ep); scclose(fd); scread(fd, cla, ins, p 1, p 2, p 3, buf, sw 1 p, sw 2 p); scwrite(fd, cla, ins, p 1, p 2, p 3, buf, sw 1 p, sw 2 p); scgetc(fd, cp, ms); scputc(fd, ic); scdsr(fd); scdtr(fd, cmd); void scsleep(ms);

Experimental software (cont’d) u Primary – – – targets: Open. BSD Linux AIX NT Palm. Pilot Java. Card u T=0, T=1

Experimental hardware

Experimental hardware (cont’d)

Experimental Hardware (cont’d)

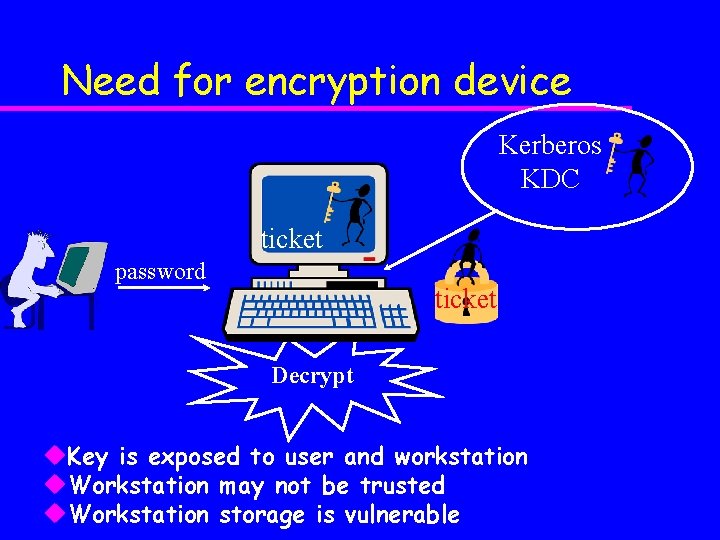
Smartcard integration with Kerberos u University of Michigan computing environment is protected by Kerberos – So are MIT, CMU, Stanford, Cornell, . . . u Public – (yet) key cryptography is not practical u Kerberos security limitations: – Lacks external encryption device – Lacks secure key storage – Passwords vulnerable to dictionary attack u Smartcards can solve these problems

Need for encryption device Kerberos KDC ticket password ticket Decrypt u. Key is exposed to user and workstation u. Workstation may not be trusted u. Workstation storage is vulnerable

Need for secure hardware u Keys stored on hard disk or in memory are vulnerable u Hard disks are not secure – Adversary with administrative rights can access keys – Data in a hard disk may be backed up in an unprotected mass storage device u Memory is not secure – Adversary can scan memory – Data in memory can be paged out to a hard disk

Dictionary attack u Create a list of English words, names, etc. – Also Star Wars, German, Shakespeare, … – thx 1138 is a vulnerable password! : -( u Derive keys from the words in the list u Obtain a <plaintext, ciphertext> pair – Kerberos gives up <plaintext, ciphertext> easily u Decrypt ciphertext with the derived key – If plaintext recovered, password is exposed u UMich: 1997 > 4, 000 vulnerable accounts in

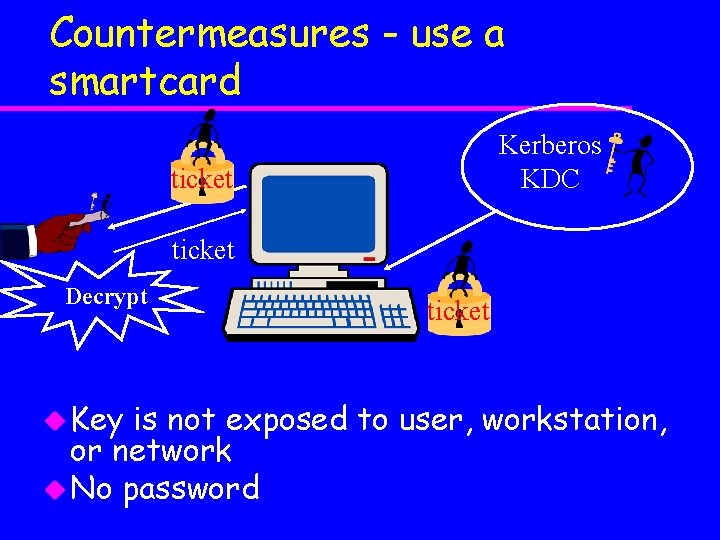
Countermeasures - use a smartcard Kerberos KDC ticket Decrypt u Key ticket is not exposed to user, workstation, or network u No password

Implementation u STARCOS v. 2. 1 from Giesecke & Devrient u Modify MIT Kerberos v 5 -1. 0. 5 client u Kerberos server unmodified for global interoperability – Well, almost … – des_cbc_crc method uses key as ivec – Modify server to allow des_cbc_md 5

Kerberos+smartcard performance kinit start card reset 0 0. 06 u Ticket – – start decryption 0. 34 end decryption time in sec. decrypt time: 1. 26 sec. 1. 32 Native STARCOS CBC Two rounds Obviates 27 round host ECB: 2. 09 sec Communication cost @ 9600 bps: ~ half kinit finish 1. 54

Kerberos+smartcard conclusion u Practical smartcard authentication method u Addresses major weakness of Kerberos u Fairly fast … room to improve u Future work: store ticket on smartcard

Smartcard filesystem (SCFS) u ISO-7816 – Standard smartcard interface – Primitive message framing protocol » Too primitive to be useful – Many vendor dependencies u Smartcard programming toolkits – IBM MFC, Microsoft PC/SC, Open. Card framework, EMV’ 96, PKCS#11, Java. Card … – Smartcard-specific everything: language, API, toolkit, library, application, etc. – Hassle learning toolkit after toolkit – API dependencies

SCFS goals and policies u Integrate a smartcard with UNIX – VFS: UNIX filesystem API u Take advantage of UNIX environment – Allows sophisticated UNIX commands – Access through symlinks u Any ISO-7816 smartcard u Easy integration with applications – – Netscape cookies PGP private keyring Kerberos tickets SSH private key

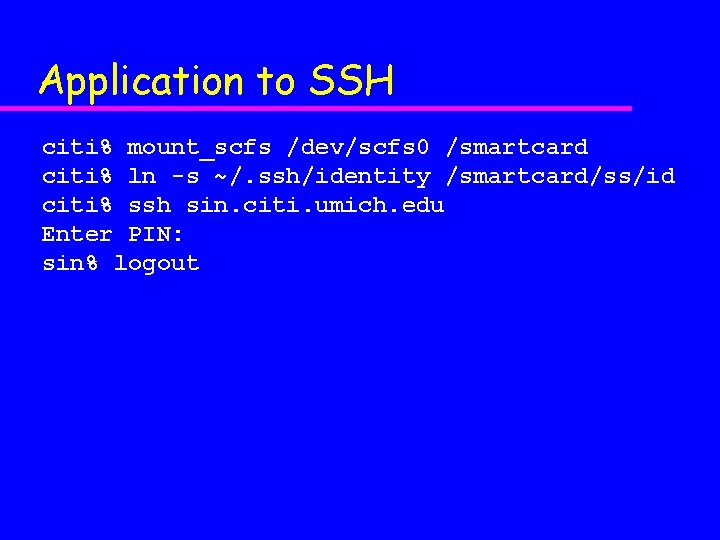
Application to SSH citi% mount_scfs /dev/scfs 0 /smartcard citi% ln -s ~/. ssh/identity /smartcard/ss/id citi% ssh sin. citi. umich. edu Enter PIN: sin% logout

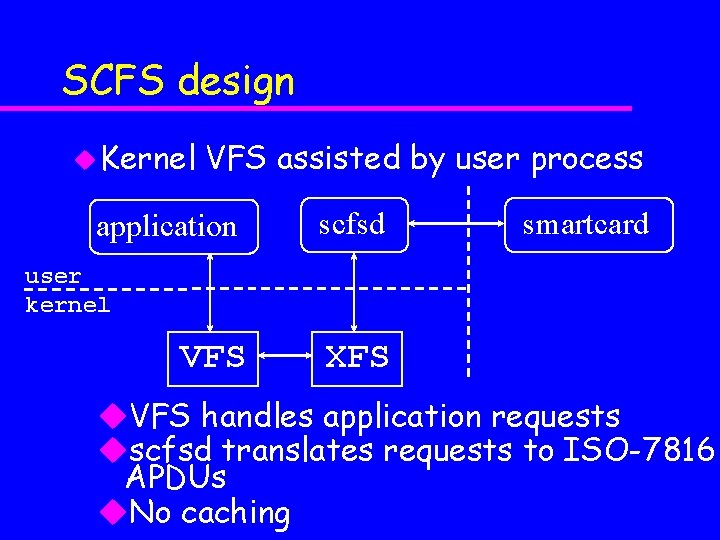
SCFS design u Kernel VFS assisted by user process application scfsd smartcard user kernel VFS XFS u. VFS handles application requests uscfsd translates requests to ISO-7816 APDUs u. No caching

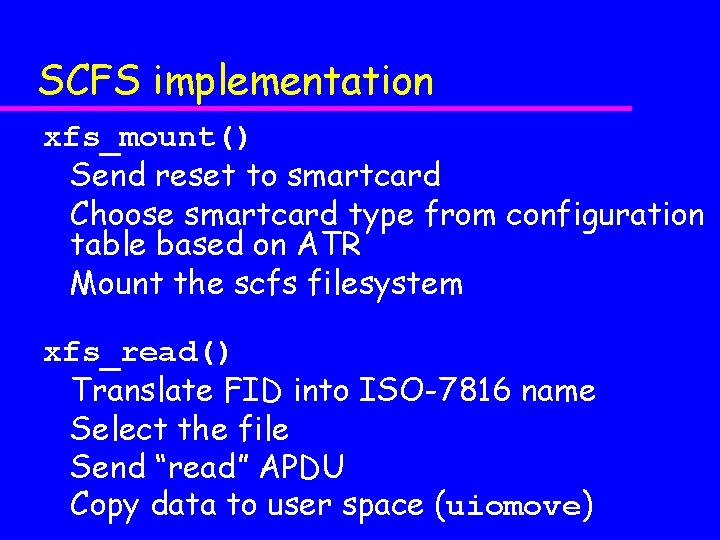
SCFS implementation xfs_mount() Send reset to smartcard Choose smartcard type from configuration table based on ATR Mount the scfs filesystem xfs_read() Translate FID into ISO-7816 name Select the file Send “read” APDU Copy data to user space (uiomove)

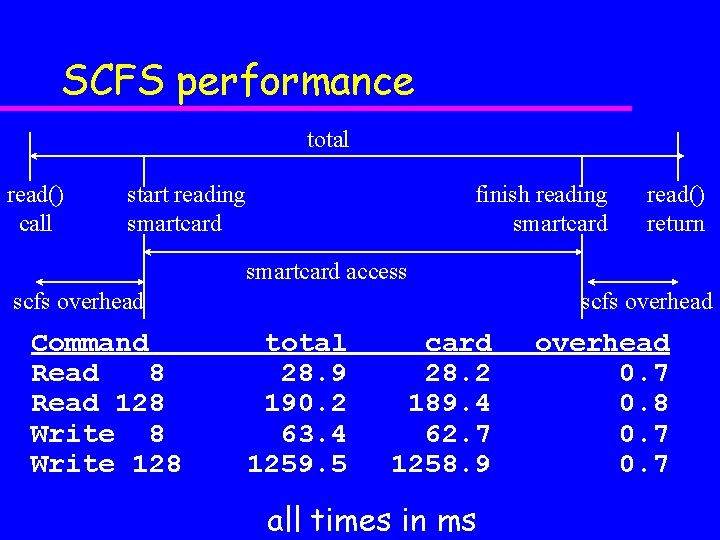
SCFS performance total read() call start reading smartcard finish reading smartcard read() return smartcard access scfs overhead Command Read 8 Read 128 Write 128 scfs overhead total 28. 9 190. 2 63. 4 1259. 5 card 28. 2 189. 4 62. 7 1258. 9 all times in ms overhead 0. 7 0. 8 0. 7

SCFS conclusion u Flexible API u Overhead is small u Useful as a low-level development tool – ls, cd, pwd, make, etc. u Secure storage for user profiles, web cookies, Kerberos tickets, private keys, etc. u Problems – Readdir is broken in ISO-7816 – Must preconfigure for each card – File length is troublesome

Future directions u Smartcard filesystem – Complete missing vnodeops – Porting to other operating systems u Authentication – Secure Kerberos ticket generation – Smartcard public key integration u IP for smartcard – honey. mcard. umich. edu – Secure network storage, service provider