What Happens When You Scam a Hackers Grandma




















- Slides: 33

What Happens When You Scam a Hackers Grandma? . Weston Hecker Principal Application Security Engineer NCR Twitter @Westonhecker Linked-IN

A Little About Me. • About myself: 33 - Work for NCR - Live in North Dakota • Defcon 22, 23, 24 and 25 Blackhat 2016, Hardwear. io, ICS security 2016, Enterprise Connect 2016, ISC 2 -Security Congress, SC-Congress Toronto, BSIDESBoston, HOPE 11 (50+ other talks) • 13 years Pentesting has 14 years of Experience Doing Security Research and Programming. • Hacking ATMs, POS, Hotel, Cars and Several IOT projects Hacking Oilwells. • Reverse Engineering Malware – Building Hardware • DARPA/DHS/S&T The contract titled “DDo. S Resilient Emergency Dispatch Center” • Projects Hacking Vehicle Systems/802. 11 p WAVE V 2 V Attack Surface. • This was a side project that was done on free time. Nothing to do with work.

Past Projects to Stop the Bad Guys.

Present Background: What Lead To This.

Filter Names Based On Age. • Who here still has a pots line? • Targeting the elderly • Change there landline Don’t port to cell phone.

Lists of Phone Numbers. • They look for names that match old people Gladis, Agatha, Marleen. • Once Apon a Time they used to list addresses and phone numbers. • How many people in here have land lines that are not for business. • How many of the hands raised are under 48 ? Statistically 6% • They target people with mental health from old age as they did my grandmother. • My grandma was not using craigslist. They used this method or the mail. • There are lists of elderly people with numbers for sale on the darkweb.

How Does the Scam Normally Work. • • • They contact you in broken English. They say the need the item shipped or it will be picked up. They make a story that makes you think there a nice person. They make it look like they are going to send you a check plus shipping and extra for your time. They over night a check from a stolen account. The check clears the bank for 2 -4 days fraud is count and disputed. You loose all the money. And the item if you sent it. They have two ways of bouncing checks from banks. Or the account is a fresh stolen account. They draft 20+ checks from each account.

The Start of it • Got an Ipad for a prize from work. • Listed it on craigslist. • Got the scam email. • Laughed at the bad spelling…… • I laughed at there bad spelling I probably used the wrong version of there Their ? • English is not my strong suit. • Thought these guys are DI%^bags and deserve a taste of there own medicine.

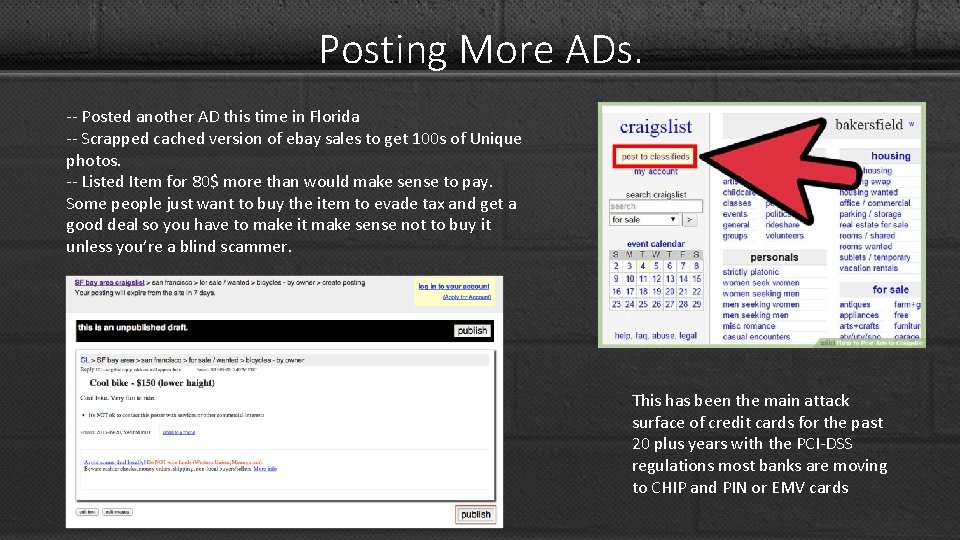
Posting More ADs. -- Posted another AD this time in Florida -- Scrapped cached version of ebay sales to get 100 s of Unique photos. -- Listed Item for 80$ more than would make sense to pay. Some people just want to buy the item to evade tax and get a good deal so you have to make it make sense not to buy it unless you’re a blind scammer. This has been the main attack surface of credit cards for the past 20 plus years with the PCI-DSS regulations most banks are moving to CHIP and PIN or EMV cards

Bots for E-mail Addresses. • Most addresses that proxies use are black flagged had to use DHCP loophole on VPS for burnable IPV 6 Addresses. • Luckily I was also setting up burner phones to validate the information. • Used to TXT input script I made for a Defcon talk at Defcon 22. • Scripted the making of 500 email accounts and bounced external interface with each creation. • Made bot tool to close accounts and send emails back and forth. • All email accounts closed now.

Making of a bot. • How do you post 50 Ipads in 50 states ? • Java and python that’s how. • How Does CL stop this. They are used to scamming tools. • Do Ads get taken down. Nope cause they are posted with a fresh IP • Clean proxies…… Nah used the same Loophole with VPS • Once again used (local jump machine List) Used scammers tools against them. • Scammers use these portals to make local orders online. So if you want to scam a STOREX in Wisconsin you can rent a local IP to do so.

Ready to go? • So with the bots now ready I posted 50 adds for a month. • Bounced ads and changed description every few days to get new item numbers and reinitiate contact with scammers. • Scrapped the email. And started building flags for common layout of scam emails. • Let the reverse scamming begin. • First one was manually done.

Spreading out to other sites (Just to see) • Checked out scamming on other sites also. Pretty much any specialized non-Escro’ed • Checked out other Items also to see what they were most interested in. • Trying to think like they did.

Filtering the information key words response. Broken English misspelled word. Obvious Item description paste. Weird Salutation (Dear Friend) Things like that. Generic reference to ITEM, electronic. DO YOU STILL HAVE X With more and more emails I was able to build on an open source context and chat engine. Not as creepy as the recent Facebook example……. . Was able to plug into the Burner phone API and Bluetooth gateway to make my own multi-number SMS gateway with DID filters. Also made sure based on context of conversation I did not use same number on the same scammer crew. Each number was used roughly 5 -6 times before it was burned.

How Did You Filter Out Real Buyers ? • I would like to buy your (IPAD 128 GB) There was a 7% real human detected (which they were informed that it sold) • Overpriced Item. Even Minus Tax (Would be dumb to buy) • Bad spellers and other information was taken into consideration. • No BS story or shipping. • My original AD had Local buyers only.

SMS gateways. SMS gateway was burner phone API and keyboard pushes to a Smartphone I had. Texts were filtered into bot with email coloration. Based on staggered dollar amount. Or agreed apon price.

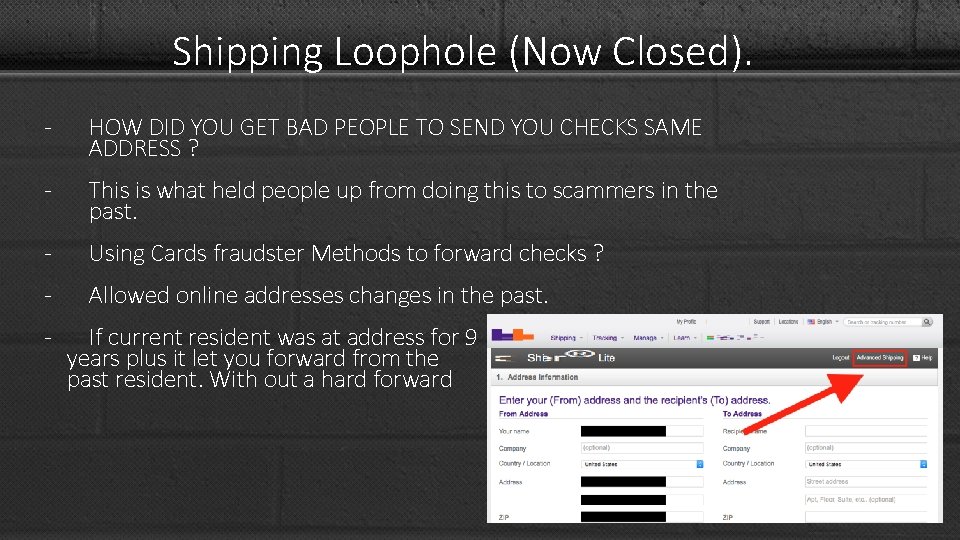
Shipping Loophole (Now Closed). - HOW DID YOU GET BAD PEOPLE TO SEND YOU CHECKS SAME ADDRESS ? - This is what held people up from doing this to scammers in the past. - Using Cards fraudster Methods to forward checks ? - Allowed online addresses changes in the past. - If current resident was at address for 9 years plus it let you forward from the past resident. With out a hard forward

When a Check is received • Scanning routing numbers parsing stolen accounts • Reporting to fraud @Bankurl. com (Same Generated E-mail Accounts) • Found a BIN (Bank Identification) style list online for Routing numbers. • Taking routing numbers and building a bank report list. • Every morning at around 10 I would get 8 to 15 checks • It was like Christmas every day. • How would you feel getting 20, 000 a day

What did the Mail Guy think I was doing ? • I have an office I work out of cause I am a remote worker. • I asked him he assumed I was an important business man. • And they were contracts. • I was WEARING A FALLOUT 4 HOODY…. • I sold him a unicorn and he left.

How Does this Hurt the Scammers? • 26 Dollars to overnight • The stolen bank accounts cost them 18 -50$ • So when other checks got cashed at banks they got declined or flagged. • This cost them 318 x$25 In account attrition. $7, 950 • 488 x$26 shipping. $12, 688 • Assuming they use each account 10 times Making $800 each scam. • 318 x 10 = 3180 x 800 = $2, 544, 000 Money Lost • That’s 2 and half million less in sex trafficking, guns and drugs. • At very least that’s two less Bugatti Veyron in Nigeria

Finding out Mules and state side Operators • Other pages led to other scams !!! Go figure • Indian reservation • How do they find mules ? • Fake job listings (Just cash checks and keep half wire rest to X) • How do they make money ? Have people in the USA to cash checks at post office or bank accounts and then they • Do they know what there doing ? Some did the 4 that I came across seemed to have the same handler.

Turning over American Mule Addresses • Names for Store to store money Transfers If I got a name like Nathan Smith or X it was reported. • I even called one dude and talked to him. It scared him he denied it. I was like Im not even mad man just tell me how the bad guys approached you. • Anything that happened state side was reported. • Checks were all shredded never intended to cash them. Marked void on them the moment I opened them.

What is the likelihood of these 5 crews being the one That scammed grandma ? ? • Don’t care it was fun !!!!!! • Cost terrible people copious amounts of money saved a few old people from getting scammed. • The crews that call people and scam seem to be mostly based out of Jamaica 419 scams lottery and “your grandson is in jail” • How often do computer guys get to go full Liam Nelson on People.

Did they ever catch on ? • Tried out selling cars • Tried apartments rooms for rent. • Tried DVDs small ticket items. • Pointless or dumb things. • Heavy electronics. • Guns – They had back stories of closed FFLs • Services. (To many emails)

LIL Wayne for A Day • Shredding 400, 000 dollars worth of fake checks. • Yes it was as fun as it sounds.

There Vo. Ip Google Voice Setup. • They had several Different numbers 4 numbers for most of the crews. • Some of the crews used the same numbers for 2 weeks in some cases. • Yea most of them just used online voice services. • They called on Hacked or Frauded Google Voice accounts.

How complex of operation did they seem to have ? • Team Edward – This guy spoke perfect English and sounded like a vampire. • The A-team – What I imagine was 4 guys in tent some where. • Nigerian MIT – These guys had technical skills. • Mr. Cleo – Jamaican based sheer numbers. • 6 x Other scammers with different MO or inconsistent templates.

Why Did You Stop? • Attention span of a Ferret. • This cost me 12 -24 c per reverse scam. About 87 Dollars and 22 hours of time. • They were evolving. • They closed Shipping Loophole was using to forward checks. • End of quarter busy at work. • Quit while ahead. • It started to feel like work.

How to Protect yourself and loved ones. • Switching there numbers out of the phone book. • Fill them in on these scams. • SCAMBLOCKER – Raspberry PI with a USB to cat-4 cable. • Make there Ads for them. • Get them a burner App. • Keep in better touch.

Cost to the criminals ? • 2. 5 Million Dollars • Hours of there time. • Frustration of failed scams. • Caused friction from there source for stolen accounts.

What else could I have done? • I could have had them reissue checks saying they did not work. • They would in some cases cut communication after this. • Email them proof I did transfer with malicious attachments. • Found out that some scammers have the ability to scrap web pages and images for phone numbers. • The numbers I listed got scam calls 5 -60 min after listing them on AD • Kept better data on which crews responded to what kind of ads

Other Research Projects. • Working on hacking WAVE systems • Hacking cellular backends. • Still hacking ATMs. • Still hacking POS. • Still Pentesting. • Mushrooms Bio. Hacking • Have any questions let me know.

Thanks to • My Work • My Wife Kids. • Jesus • My Uncle Stacy. (Gave me first Zenith EZ PC - 17 Mhz of Glory) • For Having Me Speak. its an honor. • Audience for Listening to my talk and giving me feedback. Twitter: @Westonhecker Linked IN