Comp TIA Network N 10 006 Network Performance









- Slides: 36

Comp. TIA Network+ N 10 -006 Network Performance and Monitoring My. Computer. Career. com 1

The Daily üCheck. Briefing your syllabus üfollow the assignments for the day andsuccesses week üExam or appropriately. Career Services eligibility? üNumber of days/Weeks to Certification?

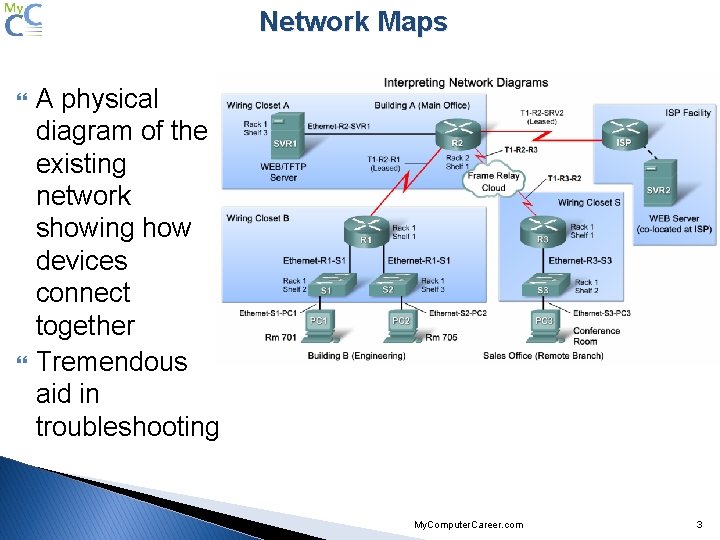
Network Maps A physical diagram of the existing network showing how devices connect together Tremendous aid in troubleshooting My. Computer. Career. com 3

Documentation It is important to document a network as it is created Further, it is important to continuously update documentation as changes are made to a network Any IT position will likely include the requirement to document solutions ◦ No one wants to “recreate the wheel” ◦ If a solution to a problem is found, documenting this in a database allows for the problem to be solved much more quickly when it resurfaces My. Computer. Career. com 4

Cable Management Cable management is crucial to easy maintenance When cabling is organized and documented from the beginning, troubleshooting is much easier later Cables can be organized to the extent that color coding is utilized to identify cables going to different areas in a building My. Computer. Career. com 5

Asset Management Tracking all equipment from receipt to retirement in an organization Proper asset management isn’t just for theft prevention Tracking equipment ensures that new equipment is requested when appropriate and necessary My. Computer. Career. com 6

Establishing a Network Baseline It is important to establish a network baseline once your network has been operational for a short period of time This baseline can then be used later when a network outage occurs to help you quickly locate the problem You will compare your baseline against the current conditions to help you discover the problem Two components that need to be considered when establishing a baseline: - Information about the network design - Expected performance under normal operating conditions

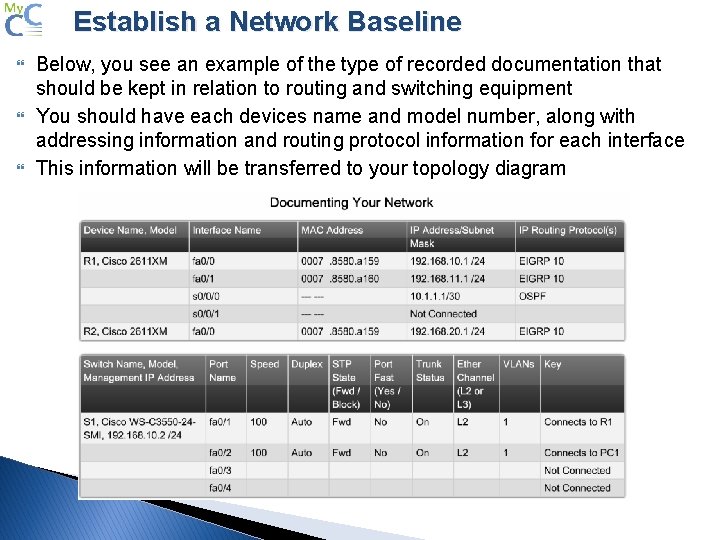
Establish a Network Baseline Below, you see an example of the type of recorded documentation that should be kept in relation to routing and switching equipment You should have each devices name and model number, along with addressing information and routing protocol information for each interface This information will be transferred to your topology diagram

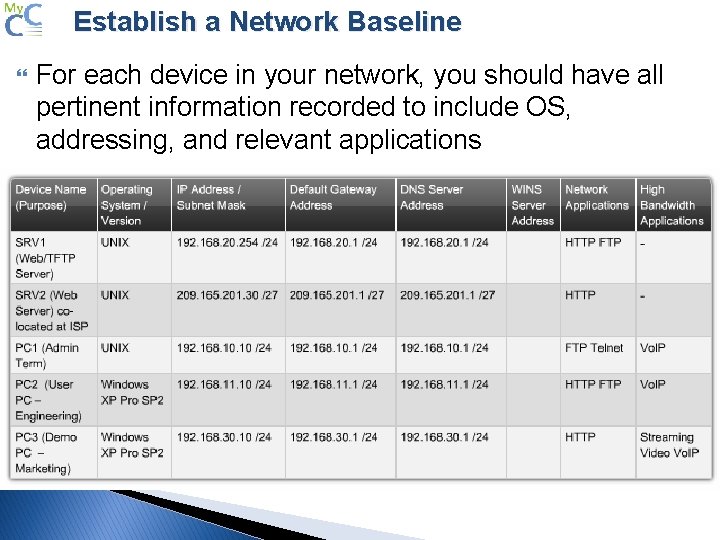
Establish a Network Baseline For each device in your network, you should have all pertinent information recorded to include OS, addressing, and relevant applications

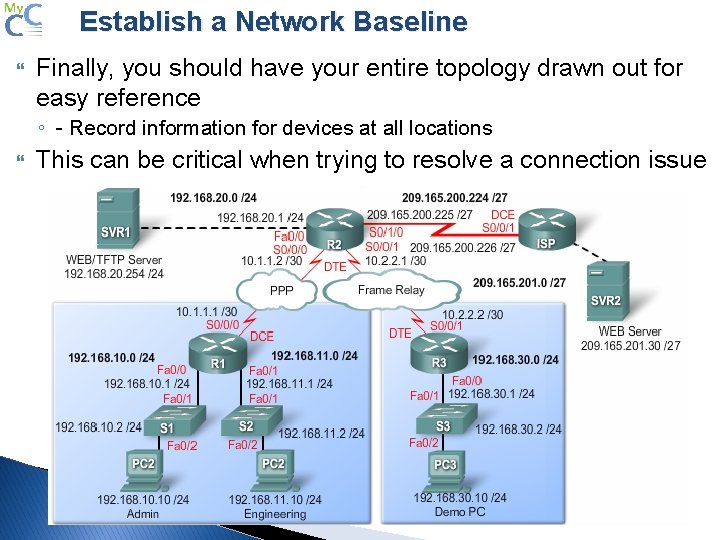
Establish a Network Baseline Finally, you should have your entire topology drawn out for easy reference ◦ - Record information for devices at all locations This can be critical when trying to resolve a connection issue

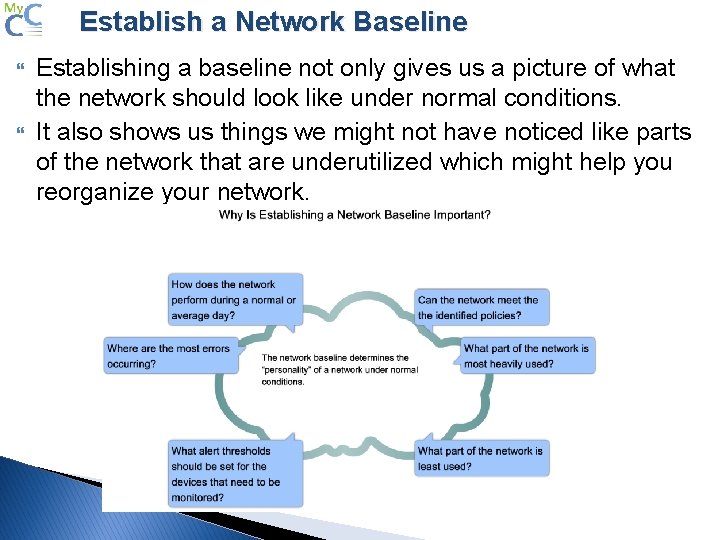
Establish a Network Baseline Establishing a baseline not only gives us a picture of what the network should look like under normal conditions. It also shows us things we might not have noticed like parts of the network that are underutilized which might help you reorganize your network.

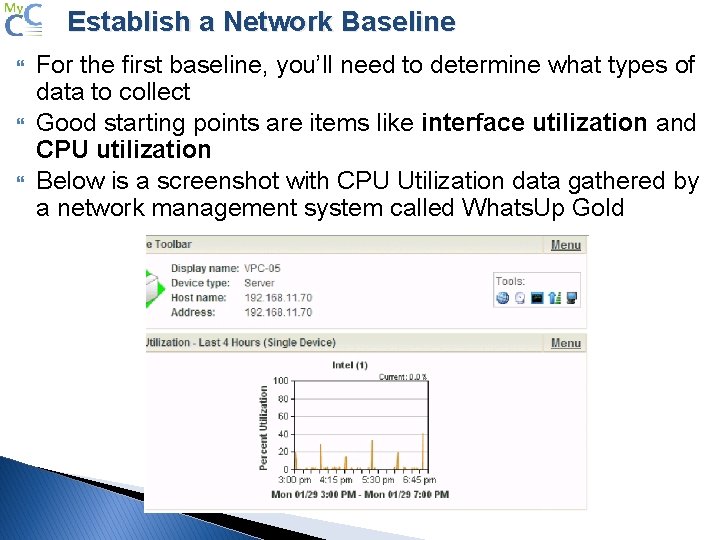
Establish a Network Baseline For the first baseline, you’ll need to determine what types of data to collect Good starting points are items like interface utilization and CPU utilization Below is a screenshot with CPU Utilization data gathered by a network management system called Whats. Up Gold

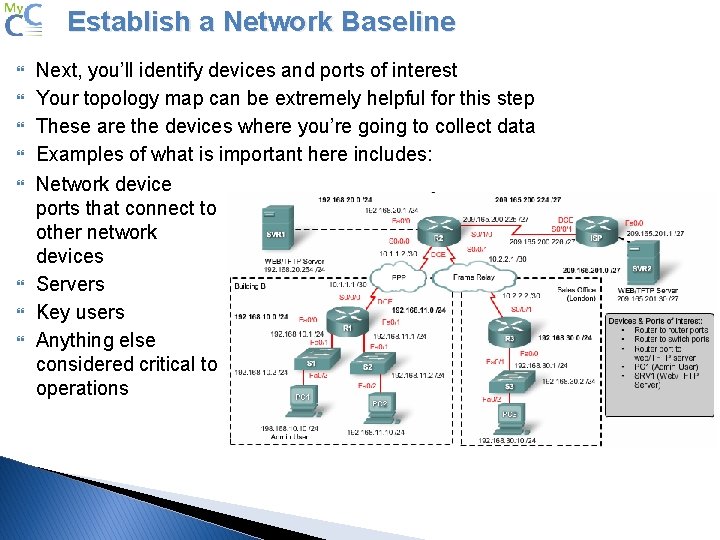
Establish a Network Baseline Next, you’ll identify devices and ports of interest Your topology map can be extremely helpful for this step These are the devices where you’re going to collect data Examples of what is important here includes: Network device ports that connect to other network devices Servers Key users Anything else considered critical to operations

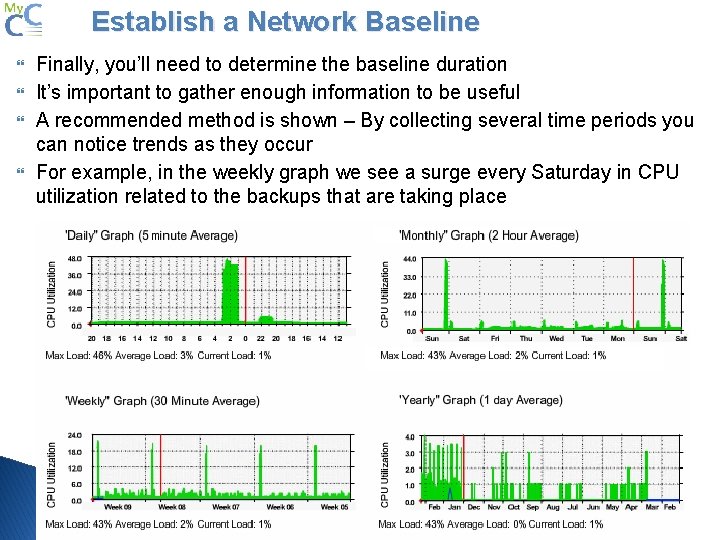
Establish a Network Baseline Finally, you’ll need to determine the baseline duration It’s important to gather enough information to be useful A recommended method is shown – By collecting several time periods you can notice trends as they occur For example, in the weekly graph we see a surge every Saturday in CPU utilization related to the backups that are taking place

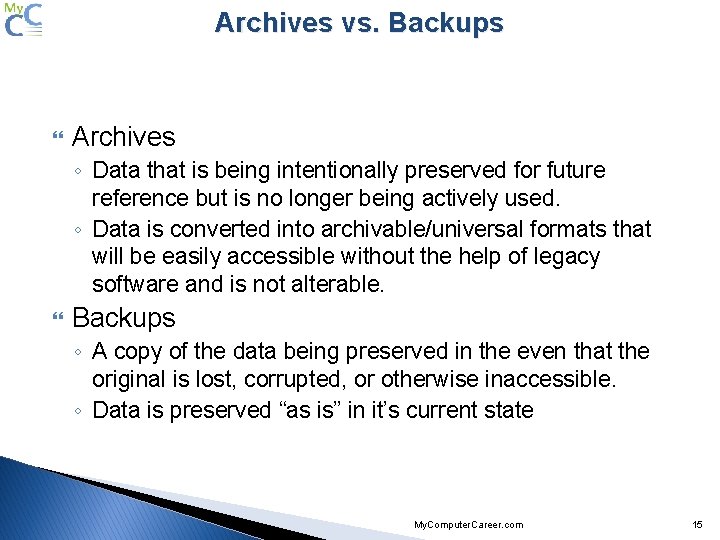
Archives vs. Backups Archives ◦ Data that is being intentionally preserved for future reference but is no longer being actively used. ◦ Data is converted into archivable/universal formats that will be easily accessible without the help of legacy software and is not alterable. Backups ◦ A copy of the data being preserved in the even that the original is lost, corrupted, or otherwise inaccessible. ◦ Data is preserved “as is” in it’s current state My. Computer. Career. com 15

Network Optimization Working to increase uptime Ensuring that latency sensitive applications are able to function ◦ VOIP ◦ Video ◦ Streaming Media Provide support for high bandwidth applications ◦ High-Definition Telepresence – Like being in the same room while videoconferencing 50 millisecond latency and 24 Mbps up and down ◦ Real-Time Data Backup 10 millisecond latency and 2 Mbps up and down My. Computer. Career. com 16

Quality of Service (Qo. S) Providing priority to specific network traffic Class of Service (Co. S) – Parameter used in the Ethernet Header to differentiate the types of payloads in the packet being transmitted ◦ Voice over IP (Vo. IP) and Video need to be given special consideration compared to traditional network traffic ◦ If the phone call or video has too much latency, it impacts the quality of the communication ◦ The router or switch can look at the parameter and identify that a voice packet has a higher priority versus a data packet when this has been configured ◦ MPLS will use Co. S Differentiated Services Code Point (DSCP) – A field in the IPv 4 and IPv 6 header Backwards compatible with the original Type of Service (TOS) field in IPv 4 Used to identify traffic in the IP header My. Computer. Career. com 17

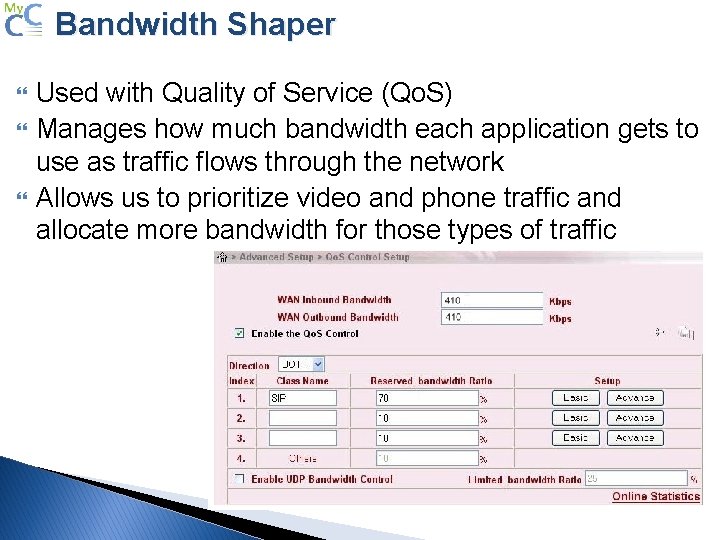
Bandwidth Shaper Used with Quality of Service (Qo. S) Manages how much bandwidth each application gets to use as traffic flows through the network Allows us to prioritize video and phone traffic and allocate more bandwidth for those types of traffic

High Availability Many people think that 99% is a valid number Actually, we use the five 9’s as a standard ◦ 99. 999% of the time the network is up Fault tolerance will take care of this ◦ Multiple routers and multiple switches Doesn’t include our downtime for maintenance ◦ Planned outage vs unplanned downtime My. Computer. Career. com 19

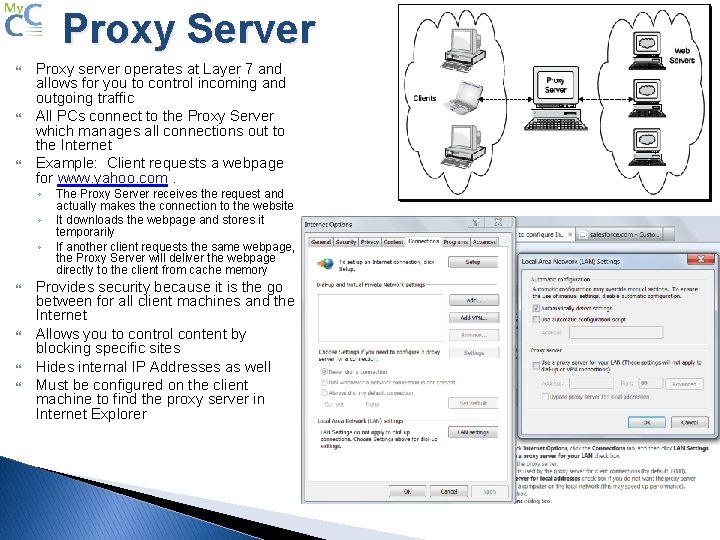
Proxy Server Proxy server operates at Layer 7 and allows for you to control incoming and outgoing traffic All PCs connect to the Proxy Server which manages all connections out to the Internet Example: Client requests a webpage for www. yahoo. com. ◦ ◦ ◦ The Proxy Server receives the request and actually makes the connection to the website It downloads the webpage and stores it temporarily If another client requests the same webpage, the Proxy Server will deliver the webpage directly to the client from cache memory Provides security because it is the go between for all client machines and the Internet Allows you to control content by blocking specific sites Hides internal IP Addresses as well Must be configured on the client machine to find the proxy server in Internet Explorer

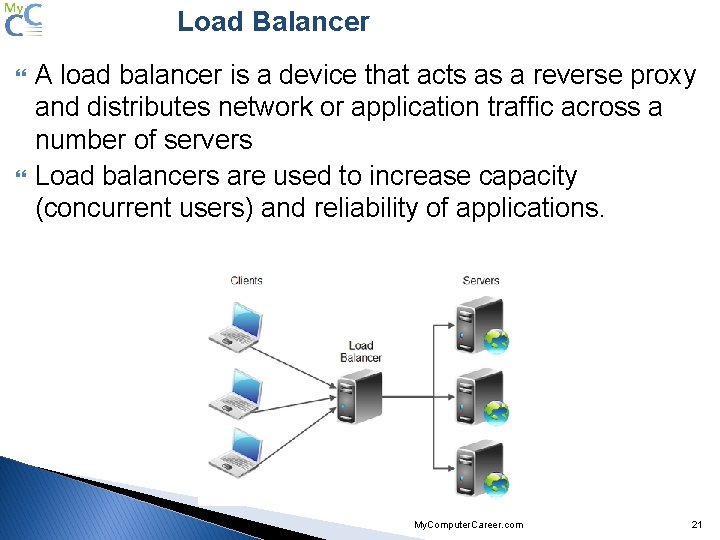
Load Balancer A load balancer is a device that acts as a reverse proxy and distributes network or application traffic across a number of servers Load balancers are used to increase capacity (concurrent users) and reliability of applications. My. Computer. Career. com 21

VPN Concentrator A VPN concentrator primarily adds the capabilities of a VPN router by adding advanced data and network security to the communications. It has the ability to create and manage a large quantity of VPN tunnels. A VPN concentrator is typically used for creating site-tosite VPN architectures. It can: ◦ ◦ ◦ Establish and configure tunnels Authenticate users Assign tunnel/IP addresses to users Encrypt and decrypt data Ensure end-to-end delivery of data My. Computer. Career. com 22

Unified Voice Services Taking all voice services and combining them together resulting in a seamless communications platform ◦ Having one single phone number and people can reach you through that number ◦ Call your office phone that also rings your cell ◦ They send a fax to that number and it arrives in your e-mail inbox ◦ They leave a voicemail and it is translated into text sent to your phone as a text message ◦ Example – You start a text to someone, click a button and you join a video conference. You then move the video conference to your desktop. Record the video conference and review it later from your cell phone while you wait for your kids at school. ◦ The overall idea is one platform combining all of our current technologies equaling business on the go! My. Computer. Career. com 23

Common Address Redundancy Protocol (CARP) Allows multiple hosts to share the same IP address Great for load balancing to Web Servers as an example The servers have to hold identical content, but it allows for the web requests coming in to be addressed to one IP address ◦ It doesn’t matter which web server actually sends back the requested web page ◦ Requests are handled via Round Robin so that each server gets the equivalent amount of usage My. Computer. Career. com 24

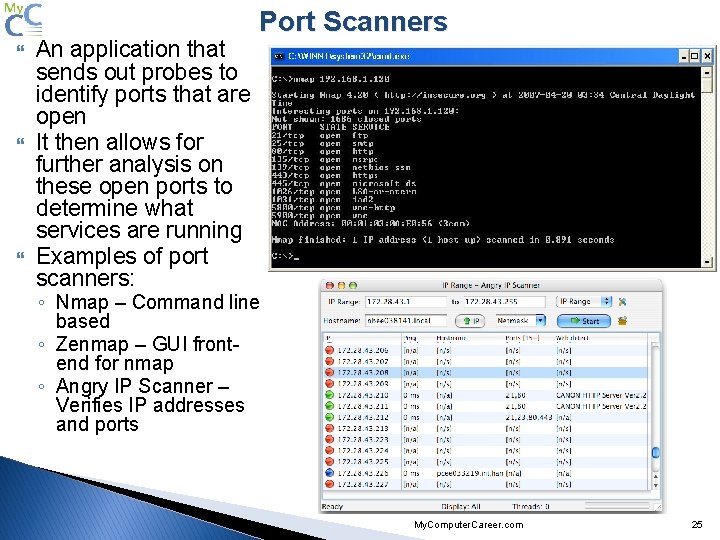
An application that sends out probes to identify ports that are open It then allows for further analysis on these open ports to determine what services are running Examples of port scanners: Port Scanners ◦ Nmap – Command line based ◦ Zenmap – GUI frontend for nmap ◦ Angry IP Scanner – Verifies IP addresses and ports My. Computer. Career. com 25

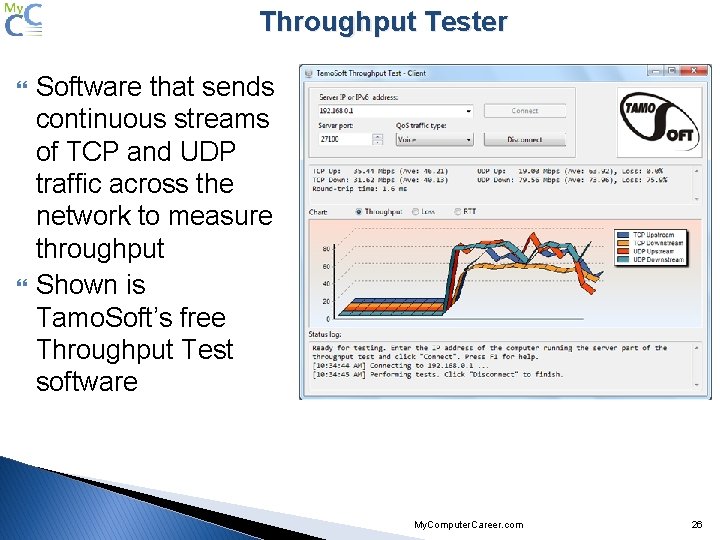
Throughput Tester Software that sends continuous streams of TCP and UDP traffic across the network to measure throughput Shown is Tamo. Soft’s free Throughput Test software My. Computer. Career. com 26

Traffic Analysis Not only gathering data like we do with a packet sniffer or port scanner, but actually using the data to analyze traffic in order to make improvements Used for the following: ◦ Troubleshooting Failed communication between two routers and you can analyze the information the routers exchange to identify the problem and restore communication ◦ Performance Analysis Identify that there is a bottleneck occurring in one part of the network Engineering has started transferring massive files back and forth regularly that is slowing down the rest of the network Place Engineering on its own subnet so it no longer interferes with the rest of the network My. Computer. Career. com 27

Virtual Switches A software program that allows one virtual machine (VM) to communicate with another Virtual. Box and Hyper. V have software built in that allows for the VMs to communicate directly with one another Allows each virtual server its own unique connection out of the physical server My. Computer. Career. com 28

Virtual Router Software-based routing framework that allows the host machine to perform as a typical hardware router over a LAN A computer / server could then serve as a router via a software application Microsoft Routing and Remote Access (RRAS) is an example of being able to use a server as a router through software My. Computer. Career. com 29

Virtual Firewall A service or appliance running entirely within a virtualized environment that provides the usual packet filtering and monitoring provided via a physical network firewall Virtual firewall could protect multiple virtual machines running virtual services in a virtual server environment My. Computer. Career. com 30

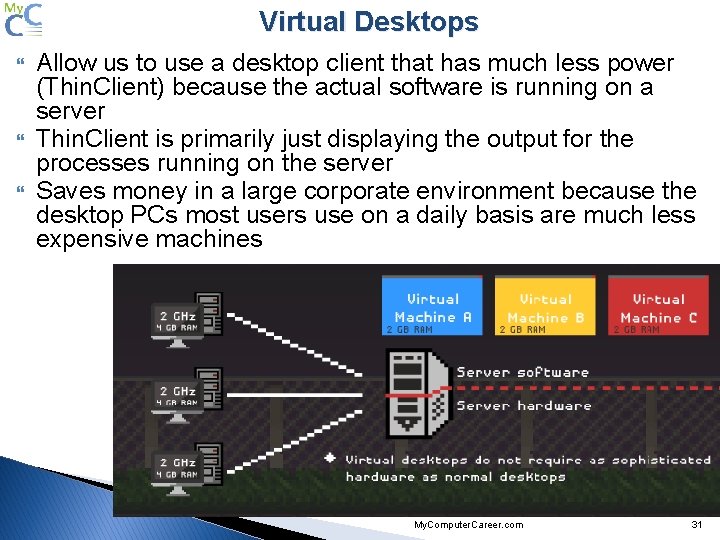
Virtual Desktops Allow us to use a desktop client that has much less power (Thin. Client) because the actual software is running on a server Thin. Client is primarily just displaying the output for the processes running on the server Saves money in a large corporate environment because the desktop PCs most users use on a daily basis are much less expensive machines My. Computer. Career. com 31

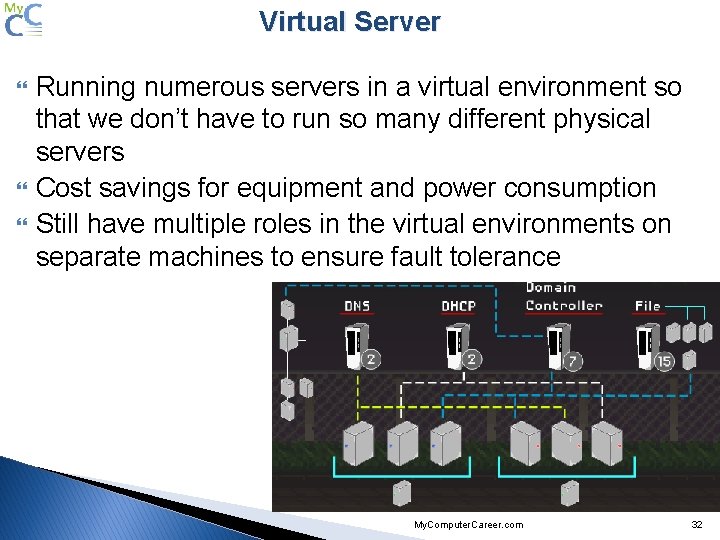
Virtual Server Running numerous servers in a virtual environment so that we don’t have to run so many different physical servers Cost savings for equipment and power consumption Still have multiple roles in the virtual environments on separate machines to ensure fault tolerance My. Computer. Career. com 32

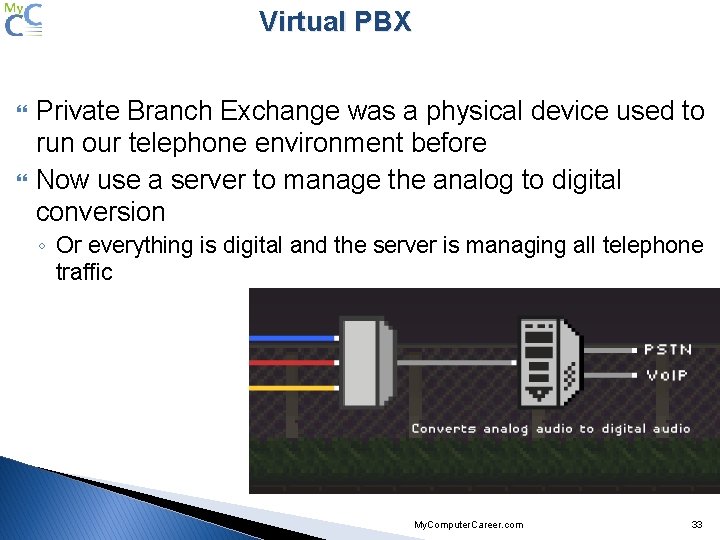
Virtual PBX Private Branch Exchange was a physical device used to run our telephone environment before Now use a server to manage the analog to digital conversion ◦ Or everything is digital and the server is managing all telephone traffic My. Computer. Career. com 33

Virtual NIC A virtual NIC is a NIC setting used in a virtual environment ◦ Depending on the setting you can do different things Create a bridge to the host NIC to gain access to the external network Create a virtual connection inside of the virtual space on the host machine to provide resources to another virtual machine on the host My. Computer. Career. com 34

Network as a Service (Naa. S) Management of the network is outsourced For example, Wireless Access Points or security systems are managed through the Vendor providing the service You still have the ability to connect to the Vendor providing this service to you through software allowing you to change settings Naa. S Onsite – The client’s company manages all of the network components Naa. S Offsite – The client’s company only manages local connections ◦ Vendor manages all network services offsite My. Computer. Career. com 35

My. Computer. Career. com 36