Chapter 18 VirtualCircuit Networks Frame Relay ATM MPLS








- Slides: 73

Chapter 18 Virtual-Circuit Networks: Frame Relay, ATM, MPLS, and VPNs 18. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.

18 -1 FRAME RELAY Frame Relay is a virtual-circuit wide-area network that was designed in response to demands for a new type of WAN in the late 1980 s and early 1990 s. Topics discussed in this section: Architecture Frame Relay Layers Extended Address FRADs VOFR LMI 18. 2

Frame Relay What is so great about frame relay? 1. X. 25, its predecessor, had a max. data rate of 64 kbps 2. X. 25 has extensive flow and error control 3. X. 25 doesn’t fit well into TCP/IP protocol stack (remember the packet layer in X. 25? ) 4. Frame relay can handle bandwidth on demand using SVCs 5. Frame relay can transfer data up to 45 Mbps 6. Frame relay is a layer two protocol 7. Frame relay is reasonably priced and allows 9000 byte payloads 18. 3

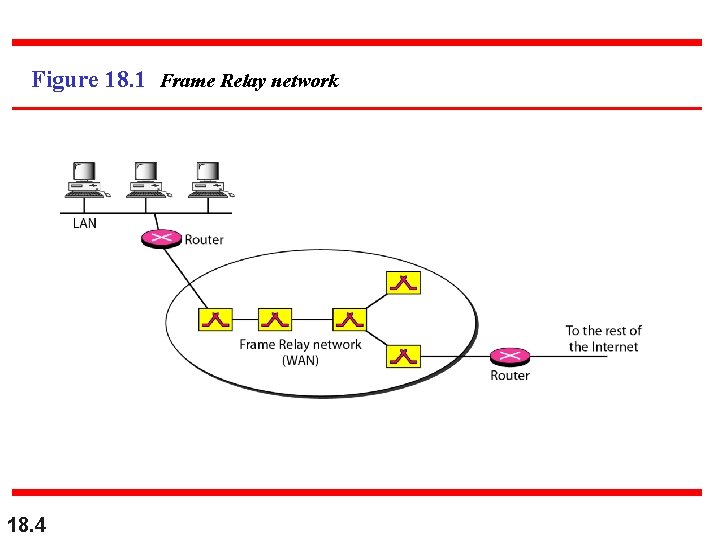
Figure 18. 1 Frame Relay network 18. 4

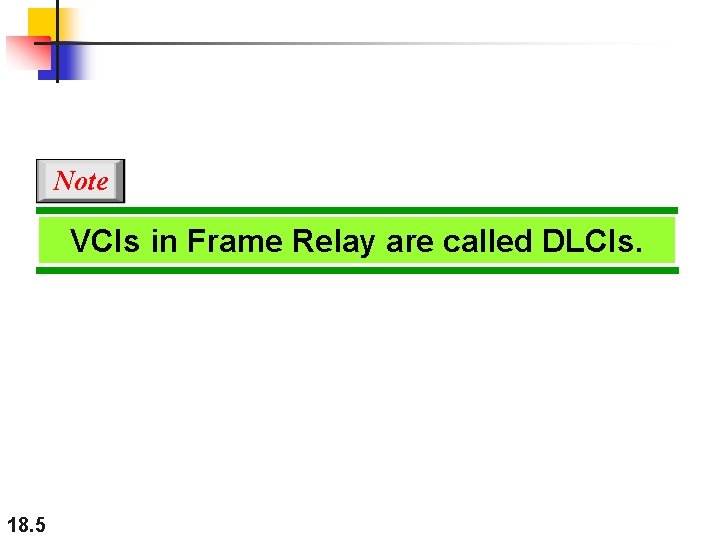
Note VCIs in Frame Relay are called DLCIs. 18. 5

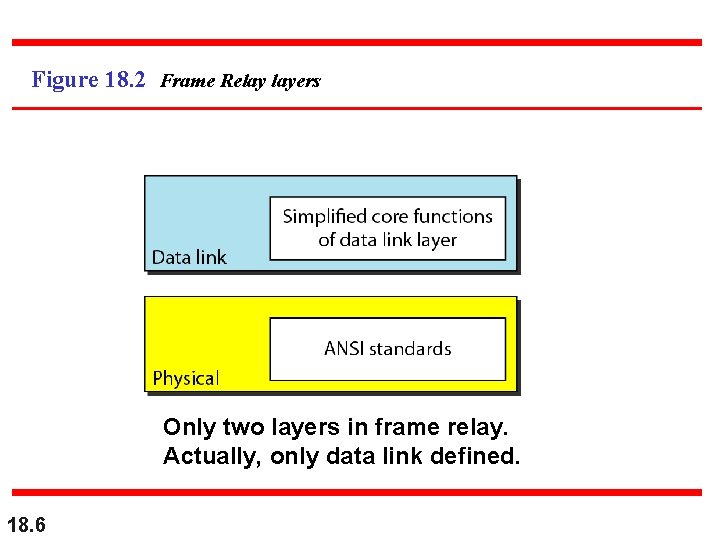
Figure 18. 2 Frame Relay layers Only two layers in frame relay. Actually, only data link defined. 18. 6

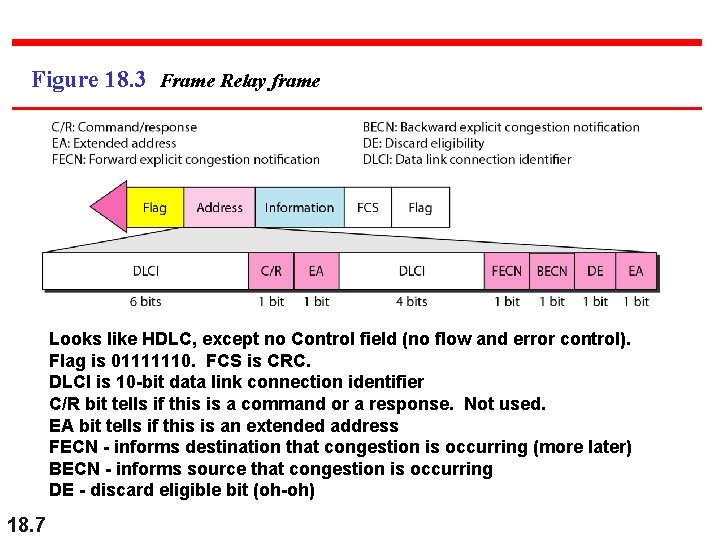
Figure 18. 3 Frame Relay frame Looks like HDLC, except no Control field (no flow and error control). Flag is 01111110. FCS is CRC. DLCI is 10 -bit data link connection identifier C/R bit tells if this is a command or a response. Not used. EA bit tells if this is an extended address FECN - informs destination that congestion is occurring (more later) BECN - informs source that congestion is occurring DE - discard eligible bit (oh-oh) 18. 7

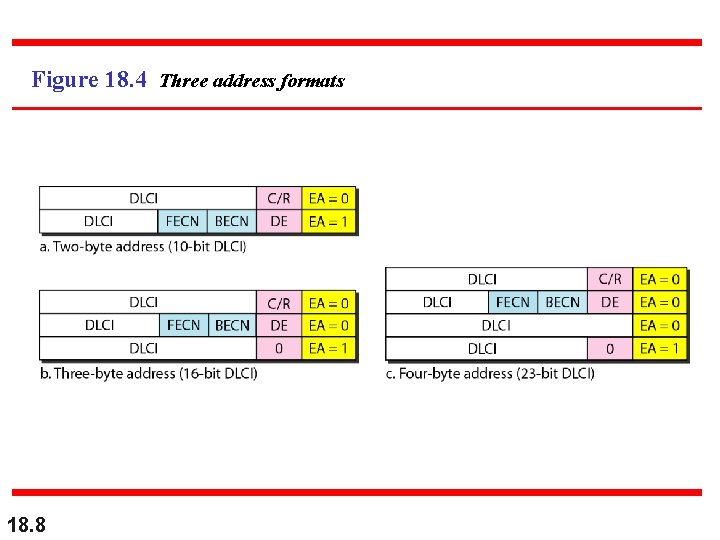
Figure 18. 4 Three address formats 18. 8

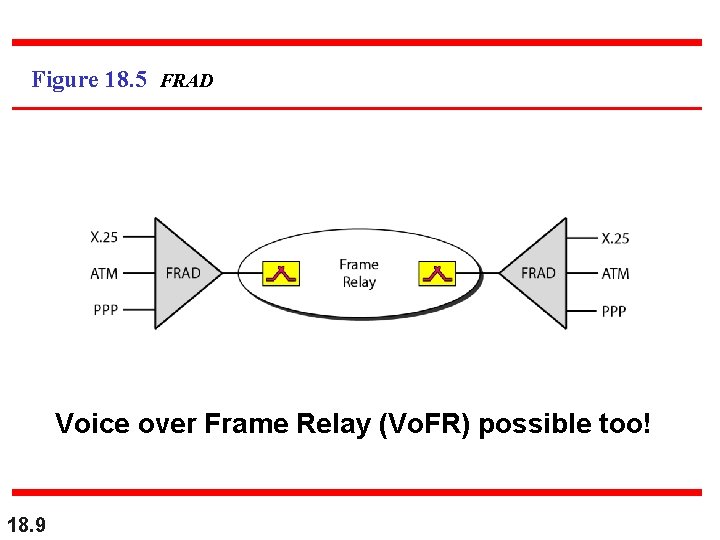
Figure 18. 5 FRAD Voice over Frame Relay (Vo. FR) possible too! 18. 9

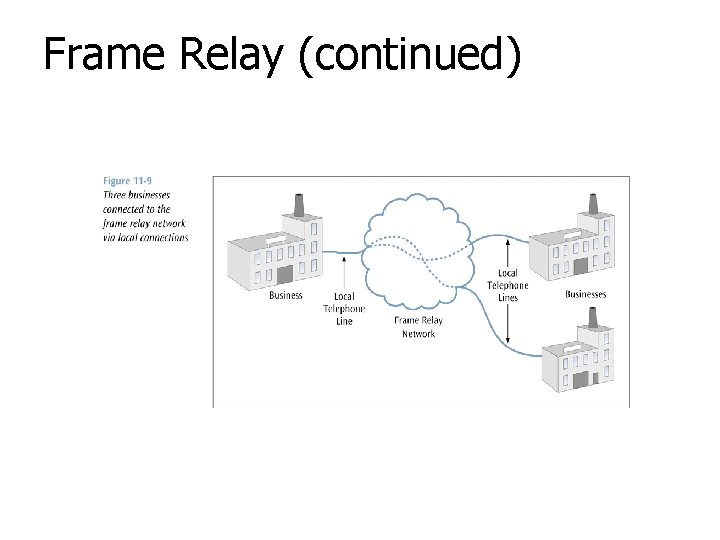
Frame Relay (continued)

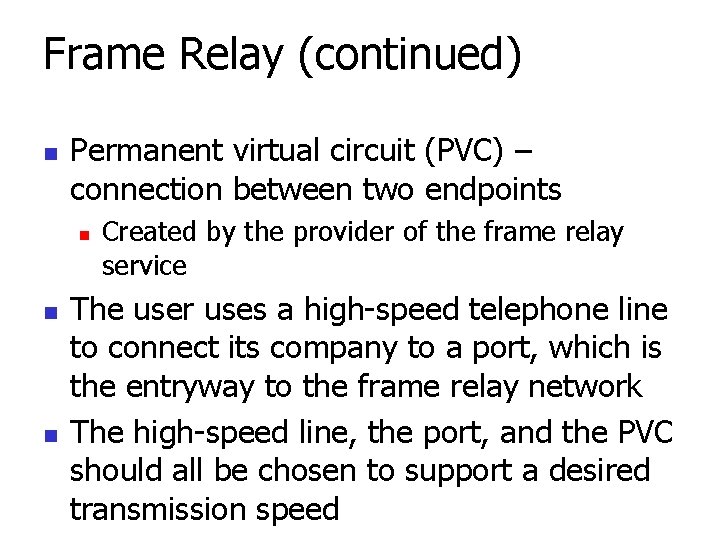
Frame Relay (continued) n Permanent virtual circuit (PVC) – connection between two endpoints n n n Created by the provider of the frame relay service The user uses a high-speed telephone line to connect its company to a port, which is the entryway to the frame relay network The high-speed line, the port, and the PVC should all be chosen to support a desired transmission speed

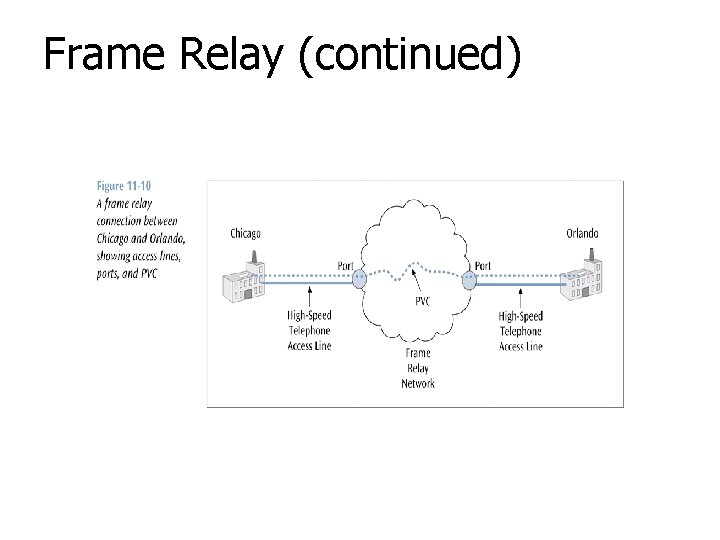
Frame Relay (continued)

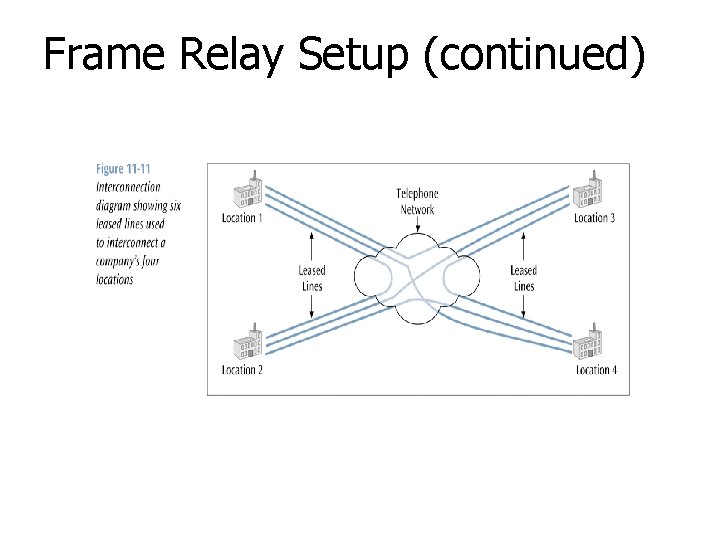
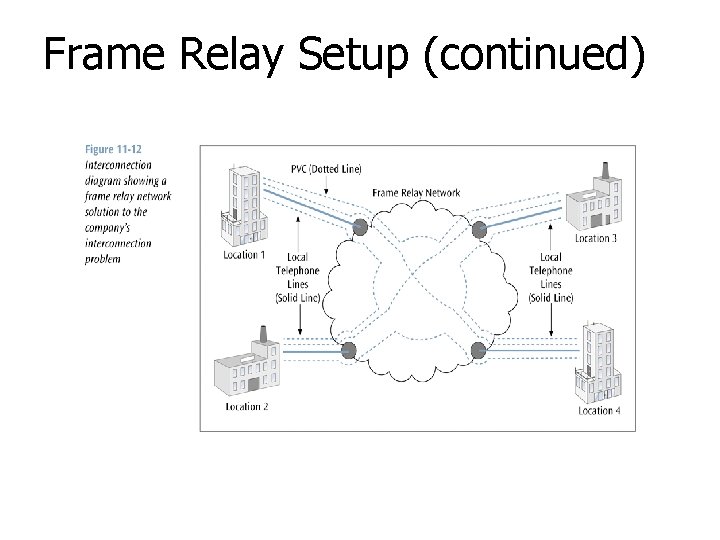
Frame Relay Setup n Consider a company that has four office locations and currently has six leased lines interconnecting the four locations n n To install frame relay, the company would ask for six PVCs in place of the six leased lines The company would also need four highspeed telephone lines and four ports connecting the four locations to the frame relay cloud

Frame Relay Setup (continued)

Frame Relay Setup (continued)

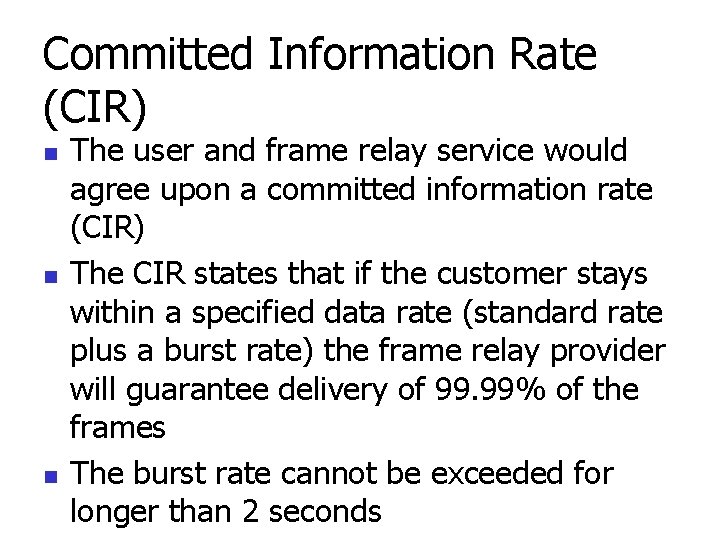
Committed Information Rate (CIR) n n n The user and frame relay service would agree upon a committed information rate (CIR) The CIR states that if the customer stays within a specified data rate (standard rate plus a burst rate) the frame relay provider will guarantee delivery of 99. 99% of the frames The burst rate cannot be exceeded for longer than 2 seconds

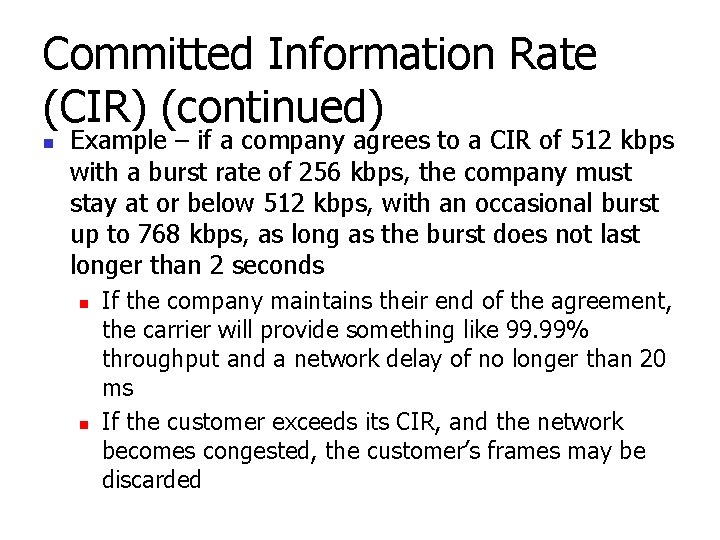
Committed Information Rate (CIR) (continued) n Example – if a company agrees to a CIR of 512 kbps with a burst rate of 256 kbps, the company must stay at or below 512 kbps, with an occasional burst up to 768 kbps, as long as the burst does not last longer than 2 seconds n n If the company maintains their end of the agreement, the carrier will provide something like 99. 99% throughput and a network delay of no longer than 20 ms If the customer exceeds its CIR, and the network becomes congested, the customer’s frames may be discarded

Frame Relay vs. the Internet n n Frame relay has many advantages over the Internet, including guaranteed throughput and minimum delay, and better security Internet has the advantage of being practically everywhere, cheaper, and simpler to create connections (no PVCs necessary) n And Internet tunnels (VPNs) are attractive

18 -2 ATM Asynchronous Transfer Mode (ATM) is the cell relay protocol designed by the ATM Forum and adopted by the ITU-T. Topics discussed in this section: Design Goals Problems Architecture Switching ATM Layers 18. 19

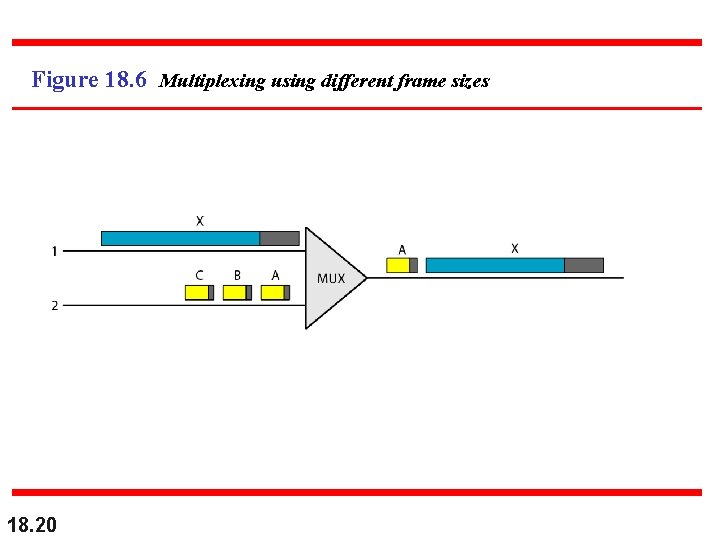
Figure 18. 6 Multiplexing using different frame sizes 18. 20

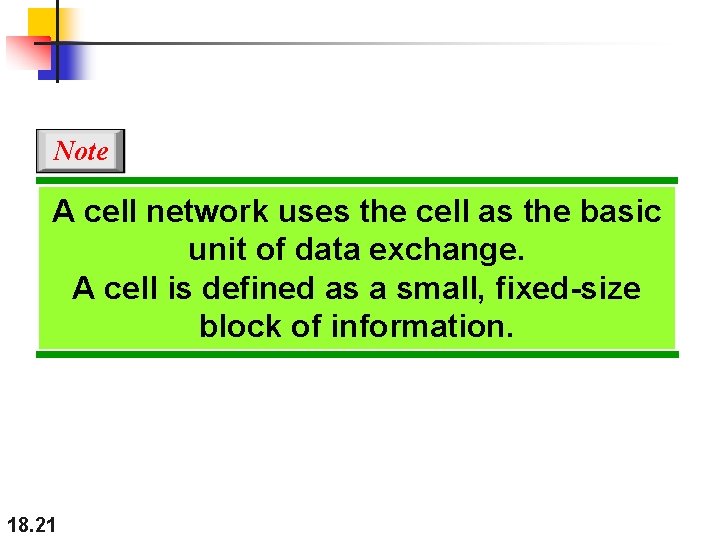
Note A cell network uses the cell as the basic unit of data exchange. A cell is defined as a small, fixed-size block of information. 18. 21

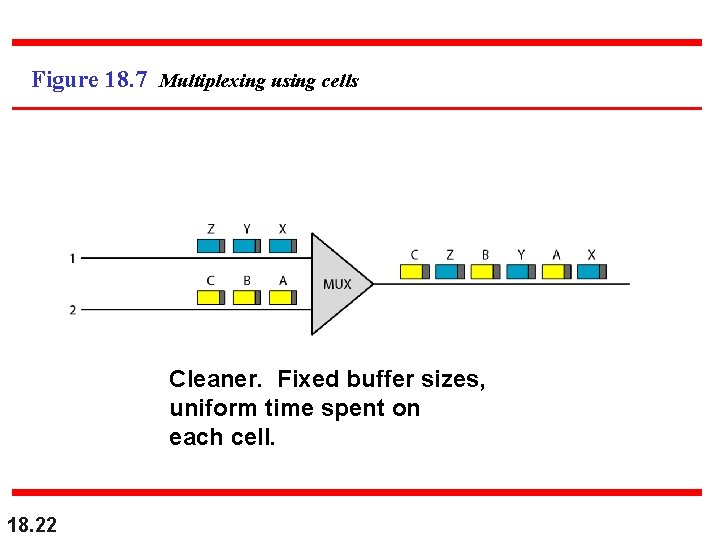
Figure 18. 7 Multiplexing using cells Cleaner. Fixed buffer sizes, uniform time spent on each cell. 18. 22

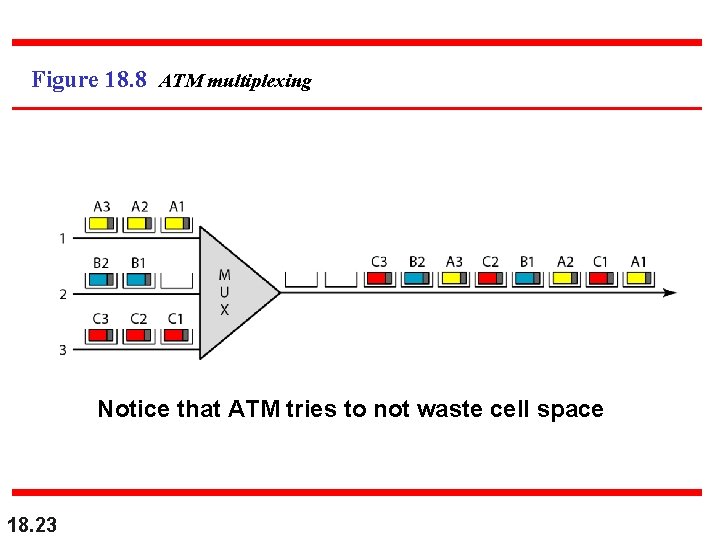
Figure 18. 8 ATM multiplexing Notice that ATM tries to not waste cell space 18. 23

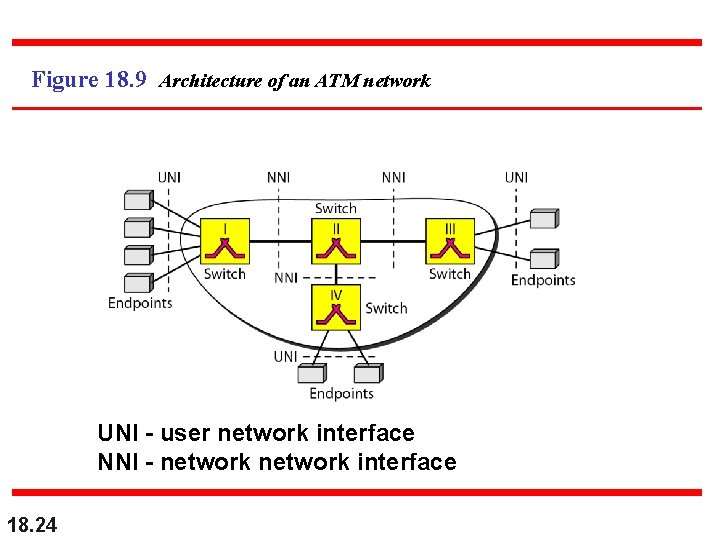
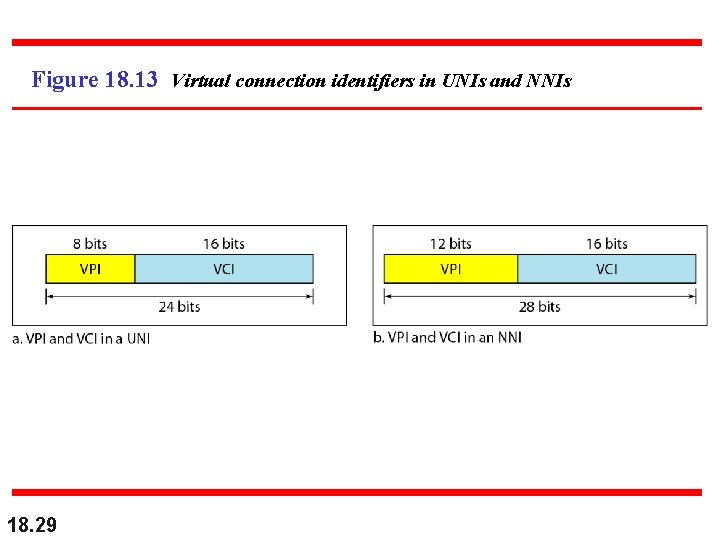
Figure 18. 9 Architecture of an ATM network UNI - user network interface NNI - network interface 18. 24

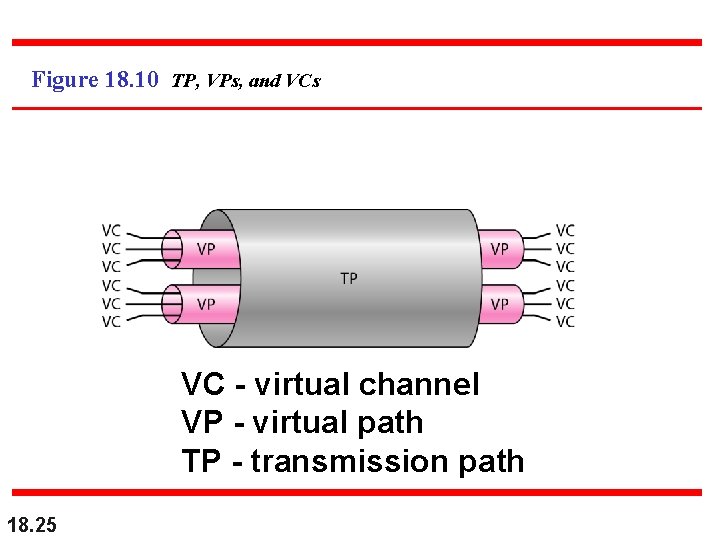
Figure 18. 10 TP, VPs, and VCs VC - virtual channel VP - virtual path TP - transmission path 18. 25

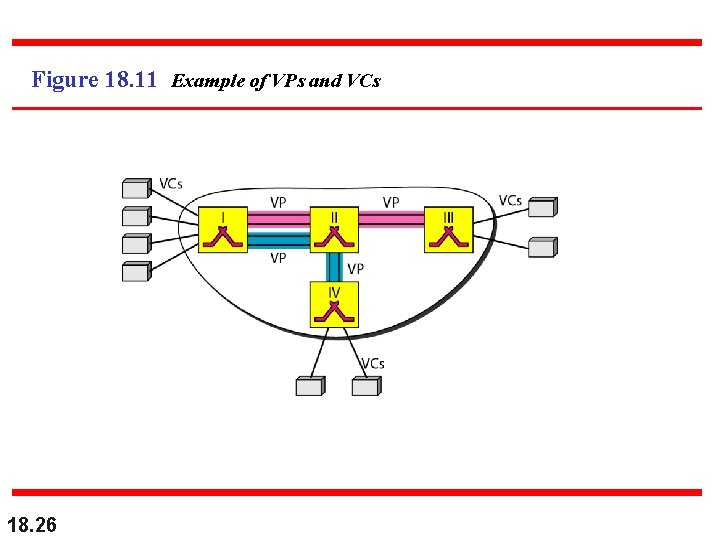
Figure 18. 11 Example of VPs and VCs 18. 26

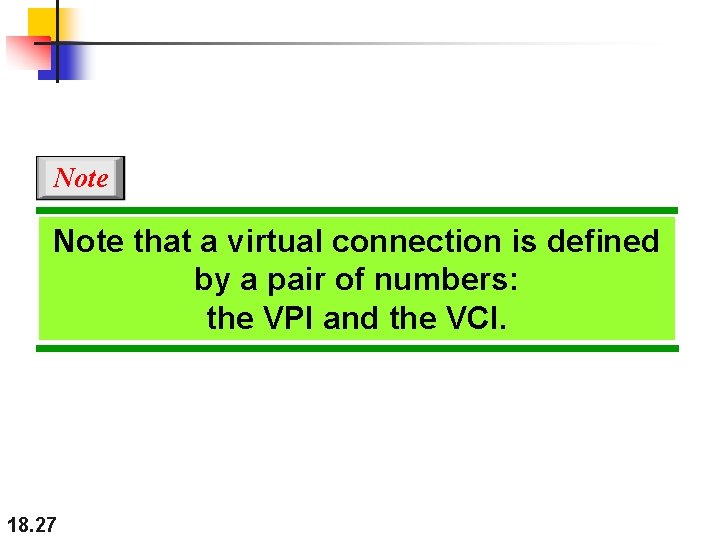
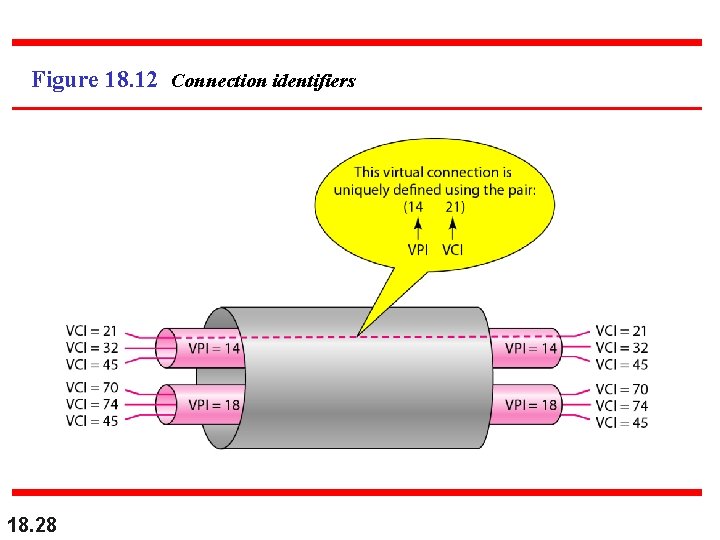
Note that a virtual connection is defined by a pair of numbers: the VPI and the VCI. 18. 27

Figure 18. 12 Connection identifiers 18. 28

Figure 18. 13 Virtual connection identifiers in UNIs and NNIs 18. 29

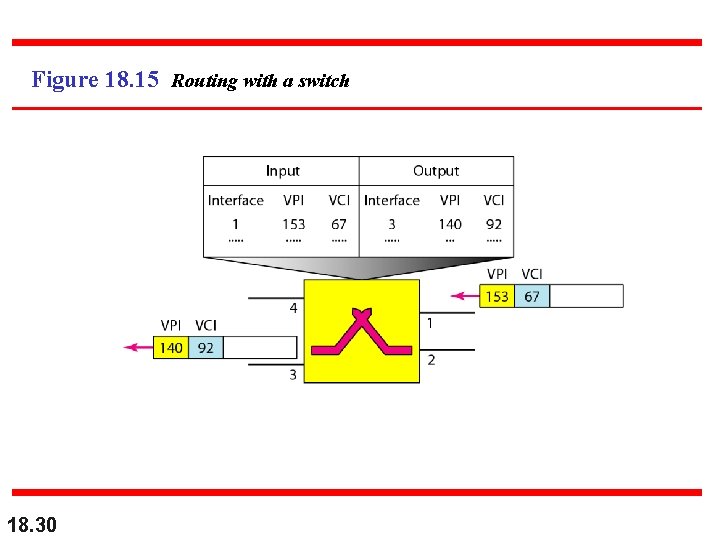
Figure 18. 15 Routing with a switch 18. 30

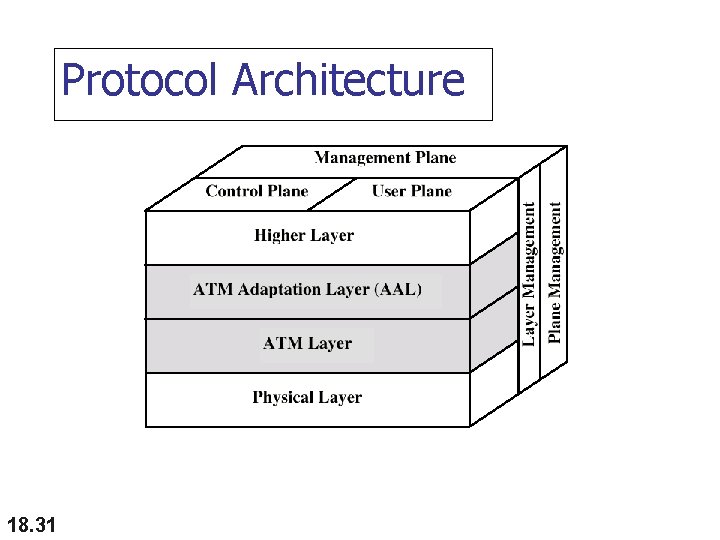
Protocol Architecture 18. 31

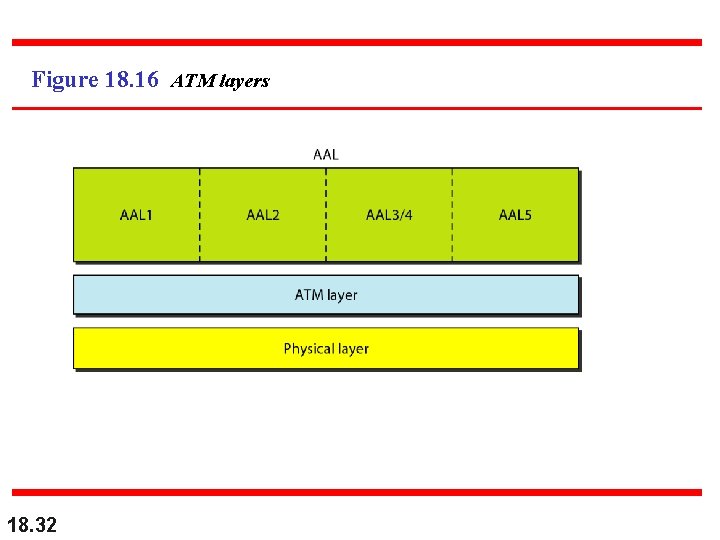
Figure 18. 16 ATM layers 18. 32

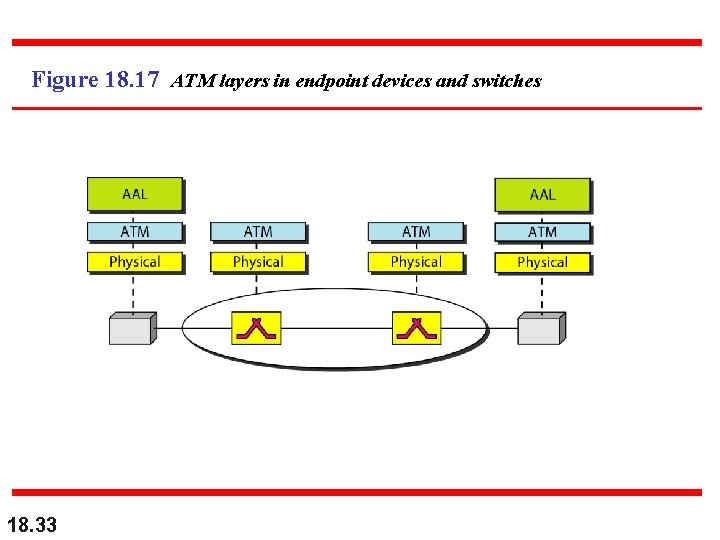
Figure 18. 17 ATM layers in endpoint devices and switches 18. 33

Protocol Architecture n User plane n n Control plane n n Provides for user information transfer along with flow control and error control Performs call and connection control functions Management plane n Plane management n n Layer management n 18. 34 Management functions related to system as a whole; make sure the various planes coordinate their activities properly Provides operations, administration, and maintenance (OAM) services thru info packets that switches exchange to keep system running effectively

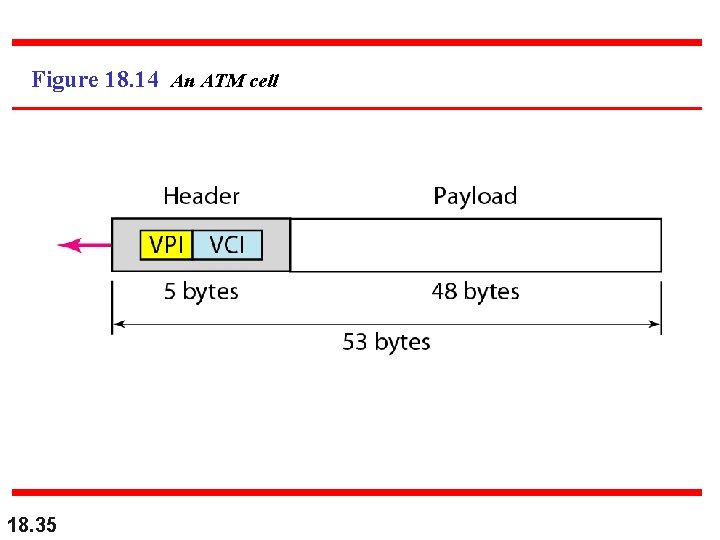
Figure 18. 14 An ATM cell 18. 35

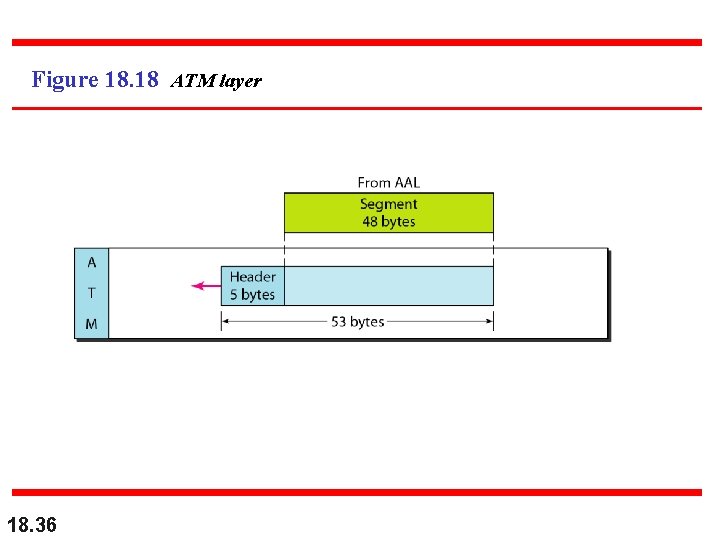
Figure 18. 18 ATM layer 18. 36

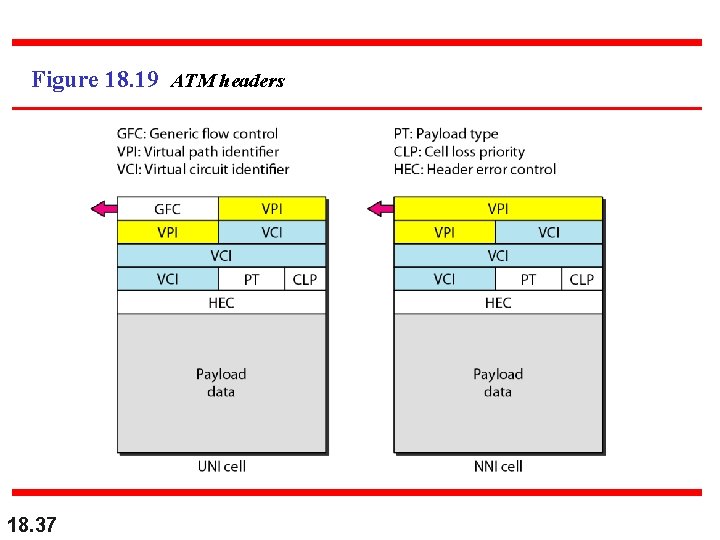
Figure 18. 19 ATM headers 18. 37

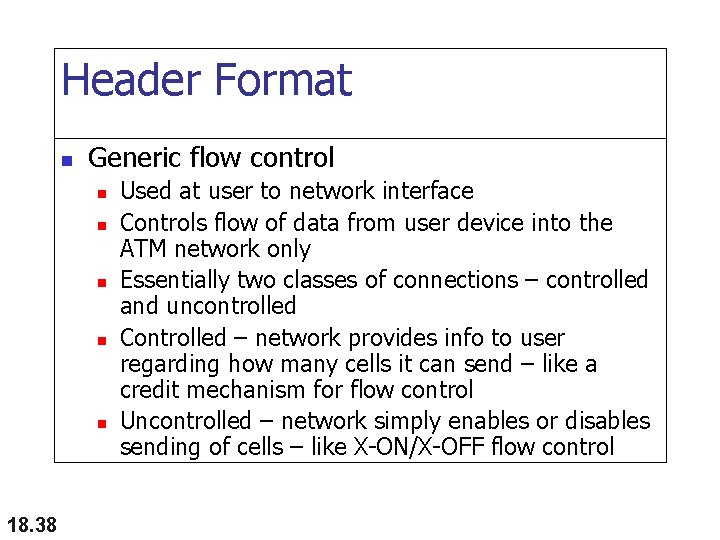
Header Format n Generic flow control n n n 18. 38 Used at user to network interface Controls flow of data from user device into the ATM network only Essentially two classes of connections – controlled and uncontrolled Controlled – network provides info to user regarding how many cells it can send – like a credit mechanism for flow control Uncontrolled – network simply enables or disables sending of cells – like X-ON/X-OFF flow control

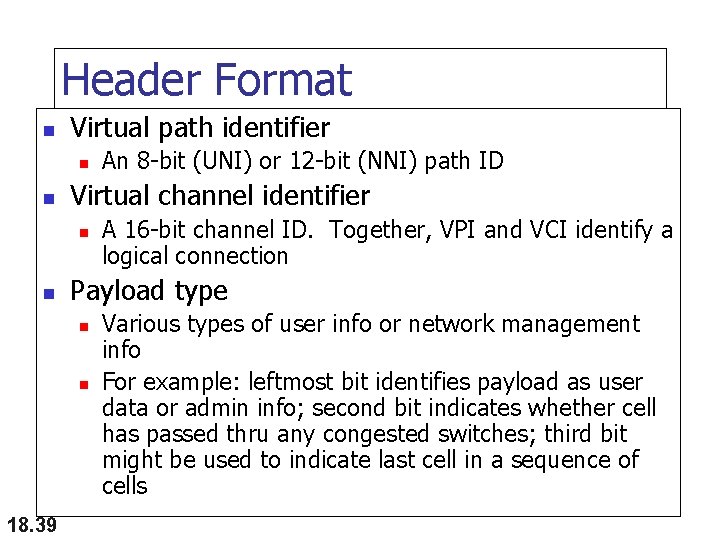
Header Format n Virtual path identifier n n Virtual channel identifier n n A 16 -bit channel ID. Together, VPI and VCI identify a logical connection Payload type n n 18. 39 An 8 -bit (UNI) or 12 -bit (NNI) path ID Various types of user info or network management info For example: leftmost bit identifies payload as user data or admin info; second bit indicates whether cell has passed thru any congested switches; third bit might be used to indicate last cell in a sequence of cells

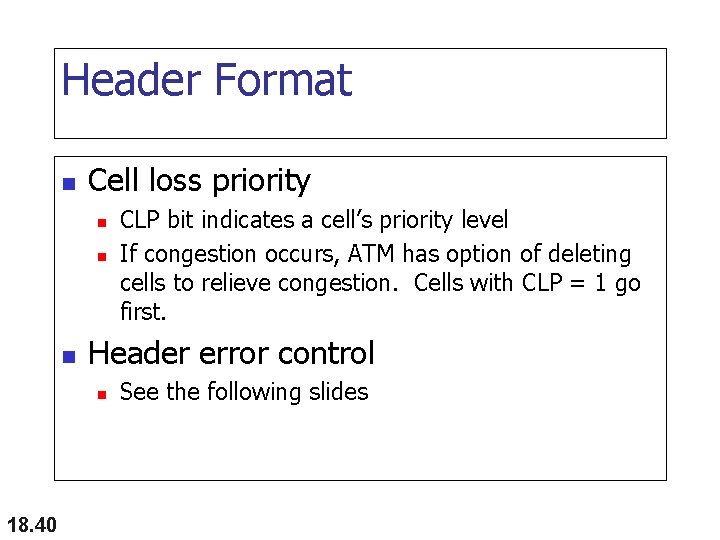
Header Format n Cell loss priority n n n Header error control n 18. 40 CLP bit indicates a cell’s priority level If congestion occurs, ATM has option of deleting cells to relieve congestion. Cells with CLP = 1 go first. See the following slides

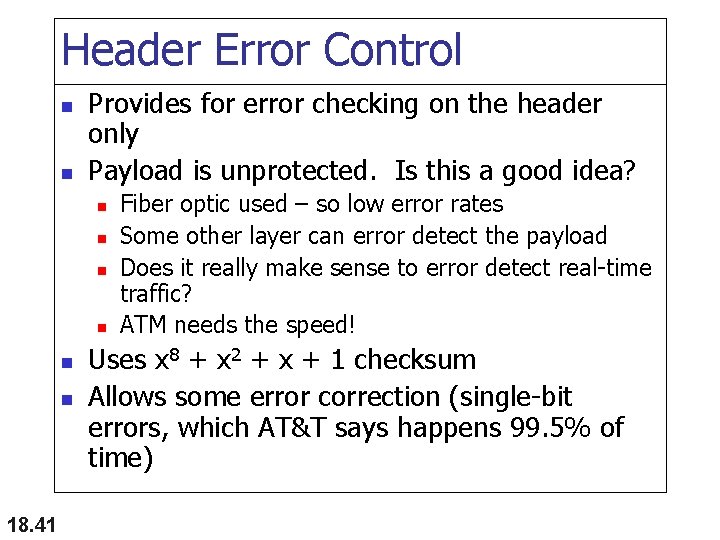
Header Error Control n n Provides for error checking on the header only Payload is unprotected. Is this a good idea? n n n 18. 41 Fiber optic used – so low error rates Some other layer can error detect the payload Does it really make sense to error detect real-time traffic? ATM needs the speed! Uses x 8 + x 2 + x + 1 checksum Allows some error correction (single-bit errors, which AT&T says happens 99. 5% of time)

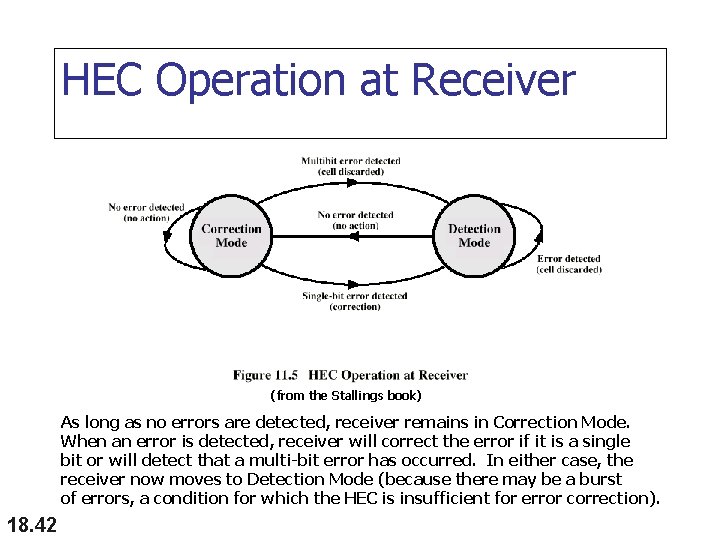
HEC Operation at Receiver (from the Stallings book) As long as no errors are detected, receiver remains in Correction Mode. When an error is detected, receiver will correct the error if it is a single bit or will detect that a multi-bit error has occurred. In either case, the receiver now moves to Detection Mode (because there may be a burst of errors, a condition for which the HEC is insufficient for error correction). 18. 42

Header Error Control n HEC can also be used for providing synchronization n n 18. 43 Apply error-checking method using 40 consecutive bits. If it does not generate a result consistent with the last 8 bits, shift one bit and try again. Repeat above step until a consistent result is found. Could it be a coincidence? Try it three more times. All four succeed? You are in sync.

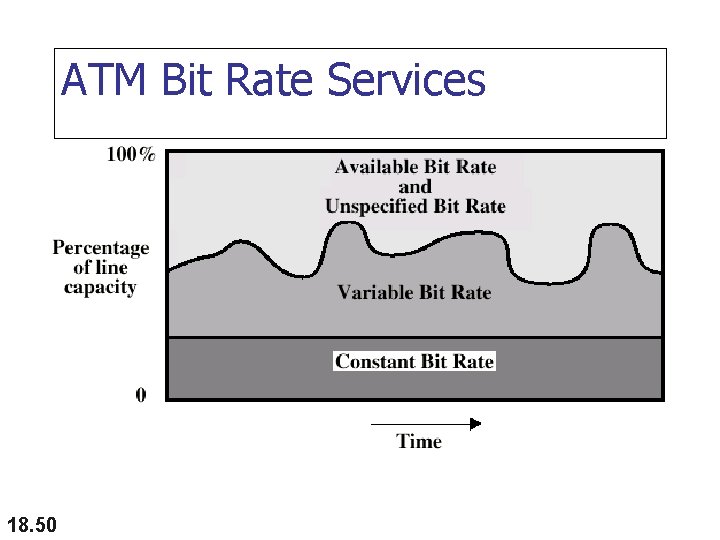
ATM Service Categories n n An ATM network can support many types of traffic: Real time n n n Non-real time n n n 18. 44 Constant bit rate (CBR) Real time variable bit rate (rt-VBR) Non-real time variable bit rate (nrt-VBR) Available bit rate (ABR) Unspecified bit rate (UBR)

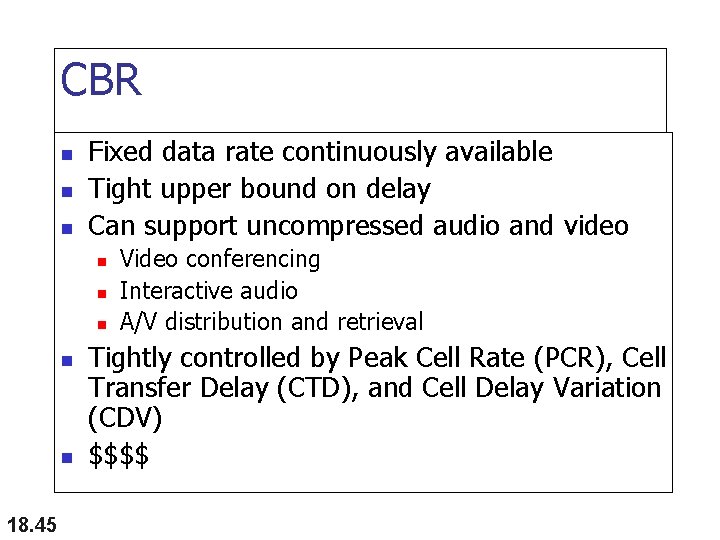
CBR n n n Fixed data rate continuously available Tight upper bound on delay Can support uncompressed audio and video n n n 18. 45 Video conferencing Interactive audio A/V distribution and retrieval Tightly controlled by Peak Cell Rate (PCR), Cell Transfer Delay (CTD), and Cell Delay Variation (CDV) $$$$

rt-VBR n Time sensitive application n n n 18. 46 Tightly constrained delay and delay variation rt-VBR applications transmit at a rate that varies with time Examples include bursty voice and video Can statistically multiplex connections Parameters include Peak Cell Rate, Sustainable Cell Rate, and Maximum Burst Size $$$

nrt-VBR n n n 18. 47 Non-real time VBR Intended for bursty traffic with no tight constraints on delay and delay variation Examples include airline reservations, banking transactions Parameters include Peak Cell Rate, Sustainable Cell Rate, Maximum Burst Size, Cell Loss Ratio, Cell Transfer Delay $$$

ABR n n n 18. 48 Application specifies Peak Cell Rate (PCR) and Minimum Cell Rate (MCR) Resources allocated to give at least MCR Spare capacity shared among all ABR sources Examples include LAN interconnection and basic critical data transfer systems such as banking, defense information (flying standby) $$

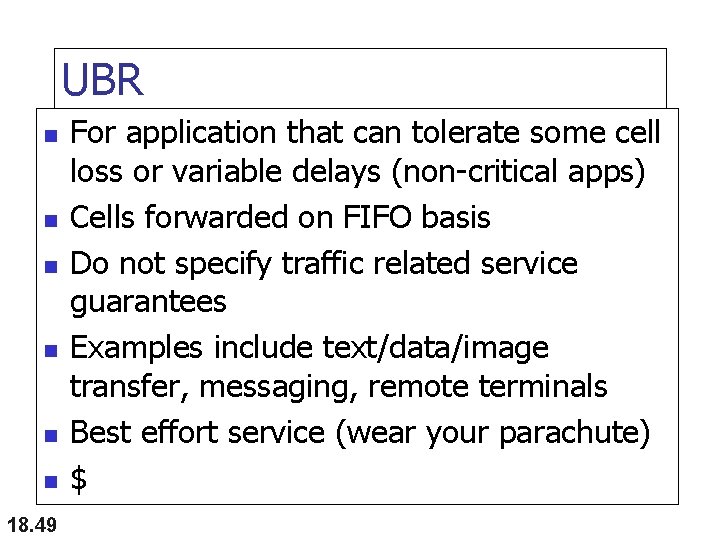
UBR n n n 18. 49 For application that can tolerate some cell loss or variable delays (non-critical apps) Cells forwarded on FIFO basis Do not specify traffic related service guarantees Examples include text/data/image transfer, messaging, remote terminals Best effort service (wear your parachute) $

ATM Bit Rate Services 18. 50

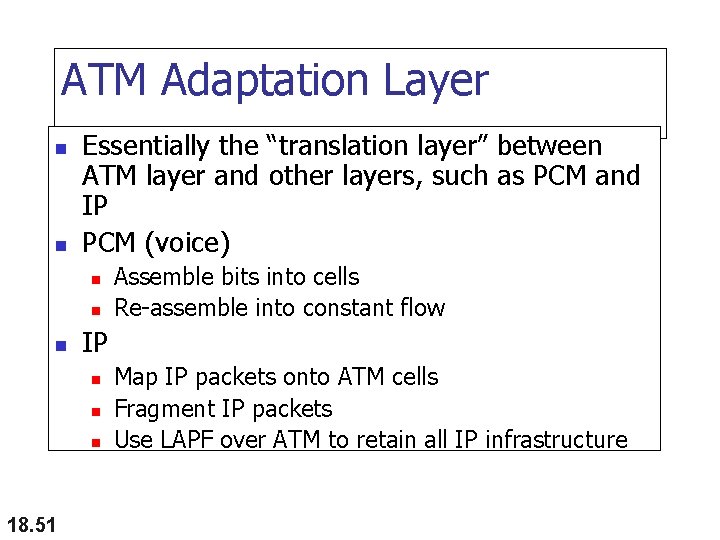
ATM Adaptation Layer n n Essentially the “translation layer” between ATM layer and other layers, such as PCM and IP PCM (voice) n n n IP n n n 18. 51 Assemble bits into cells Re-assemble into constant flow Map IP packets onto ATM cells Fragment IP packets Use LAPF over ATM to retain all IP infrastructure

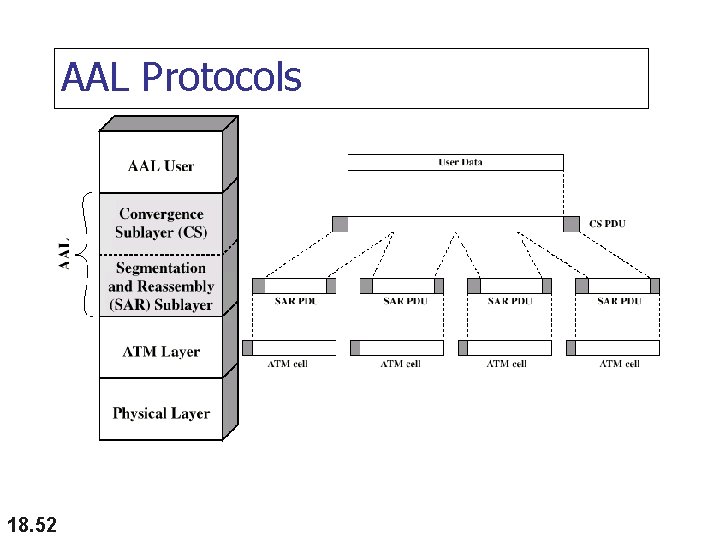
AAL Protocols 18. 52

Adaptation Layer Services n n n 18. 53 Handle transmission errors Segmentation and re-assembly To enable larger blocks of data to be carried in the information field of ATM cells Handle lost and misinserted cells (cells routed the wrong way) Perform flow control and timing control

Supported Application types n n n 18. 54 Four AAL protocols defined: AAL 1: CBR traffic, e. g. circuit emulation (T-1 over ATM), voice over ATM, real-time video AAL 2: rt-VBR traffic, e. g. MPEG voice and video AAL 3/4: nrt-VBR traffic, e. g. general data service (not really used by anyone) AAL 5 (successor to AAL 3/4): e. g. nrt-VBR: voice on demand; nrt-VBR: frame relay, ATM; UBR: IP over ATM

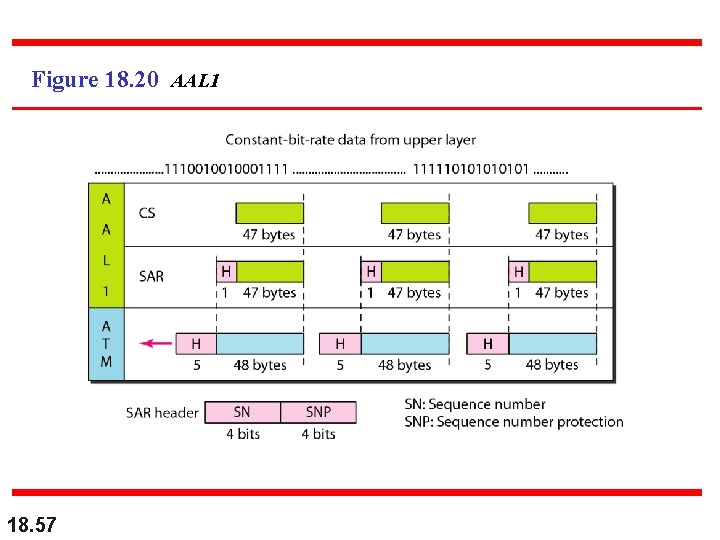
AAL 1 n n 18. 55 AAL 1 is the interface between a realtime uncompressed byte stream and ATM Got to be fast! No convergence sublayer, only SAR sublayer AAL 1 takes 46 or 47 bytes of data and puts a one or two byte header on front

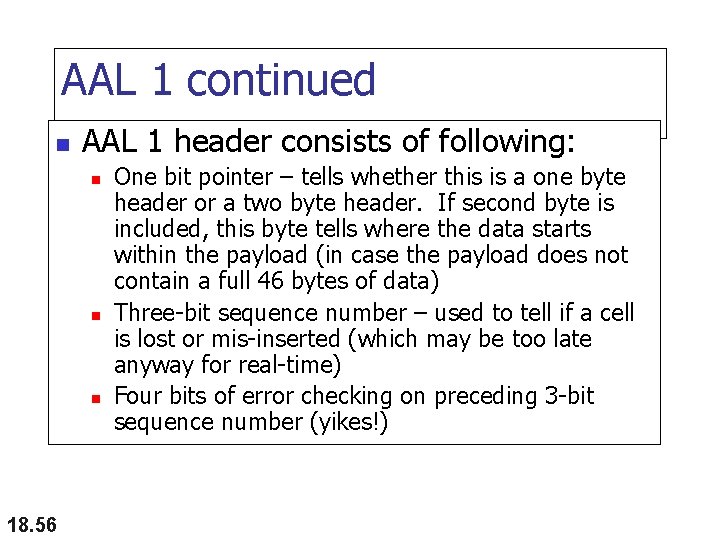
AAL 1 continued n AAL 1 header consists of following: n n n 18. 56 One bit pointer – tells whether this is a one byte header or a two byte header. If second byte is included, this byte tells where the data starts within the payload (in case the payload does not contain a full 46 bytes of data) Three-bit sequence number – used to tell if a cell is lost or mis-inserted (which may be too late anyway for real-time) Four bits of error checking on preceding 3 -bit sequence number (yikes!)

Figure 18. 20 AAL 1 18. 57

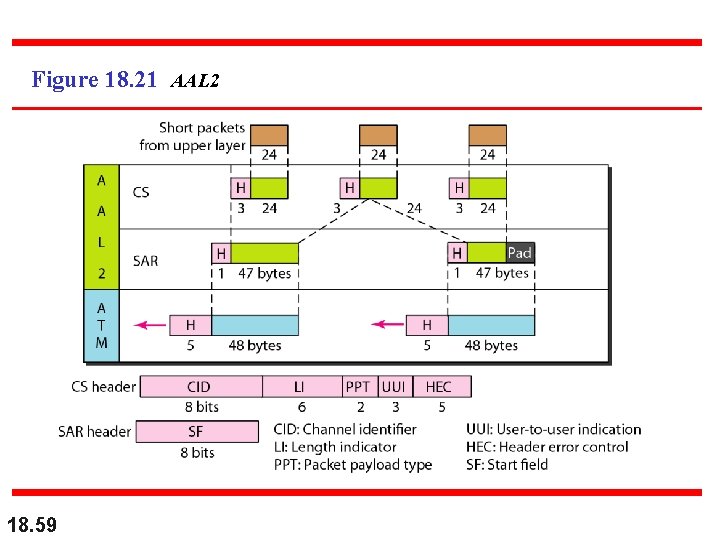
AAL 2 n 18. 58 AAL 2 format is used for compressed data (MPEG voice and video), so ATM needs to indicate where each frame of compressed data ends and begins

Figure 18. 21 AAL 2 18. 59

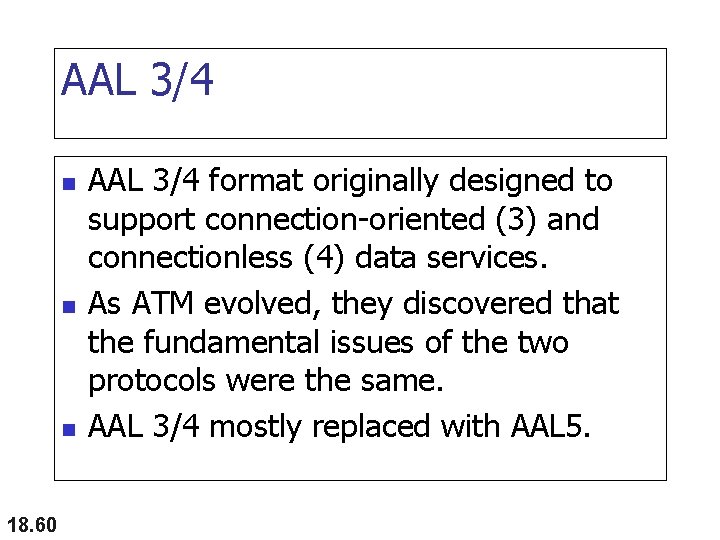
AAL 3/4 n n n 18. 60 AAL 3/4 format originally designed to support connection-oriented (3) and connectionless (4) data services. As ATM evolved, they discovered that the fundamental issues of the two protocols were the same. AAL 3/4 mostly replaced with AAL 5.

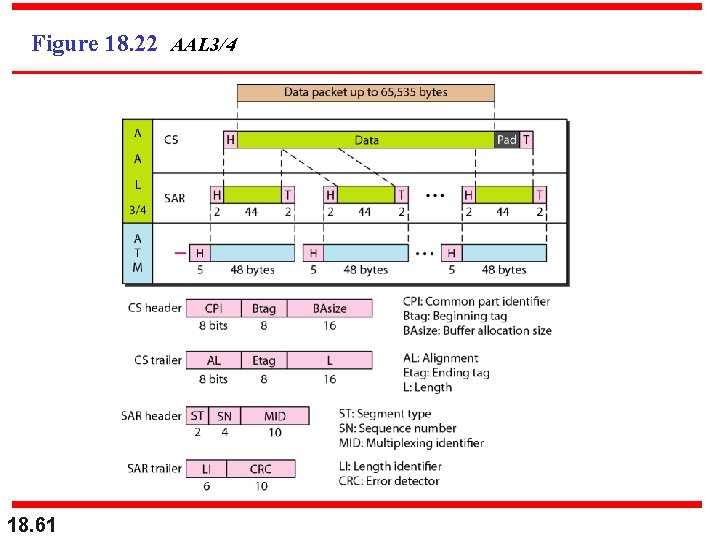
Figure 18. 22 AAL 3/4 18. 61

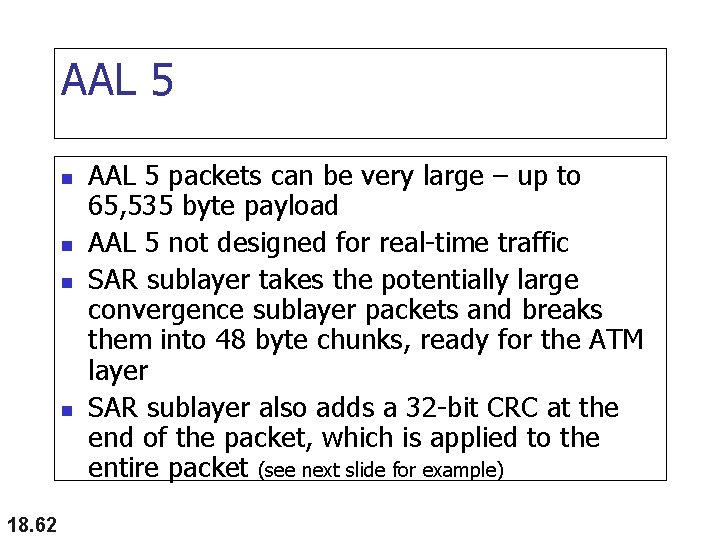
AAL 5 n n 18. 62 AAL 5 packets can be very large – up to 65, 535 byte payload AAL 5 not designed for real-time traffic SAR sublayer takes the potentially large convergence sublayer packets and breaks them into 48 byte chunks, ready for the ATM layer SAR sublayer also adds a 32 -bit CRC at the end of the packet, which is applied to the entire packet (see next slide for example)

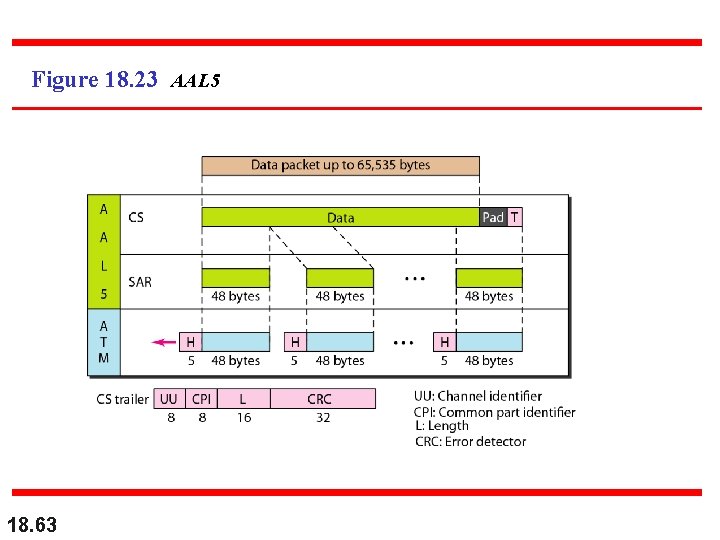
Figure 18. 23 AAL 5 18. 63

In Summary n Frame relay n n n ATM n n n 18. 64 Up to 45 Mbps but usually slower Local and long distance Cloud computing Being replaced by IP and MPLS Fast! Different classes of service! Small cells

A Transition n Use of Frame Relay is dropping off quickly ATM is starting to die off too(? ) What is replacing these protocols? n n MPLS VPN 65

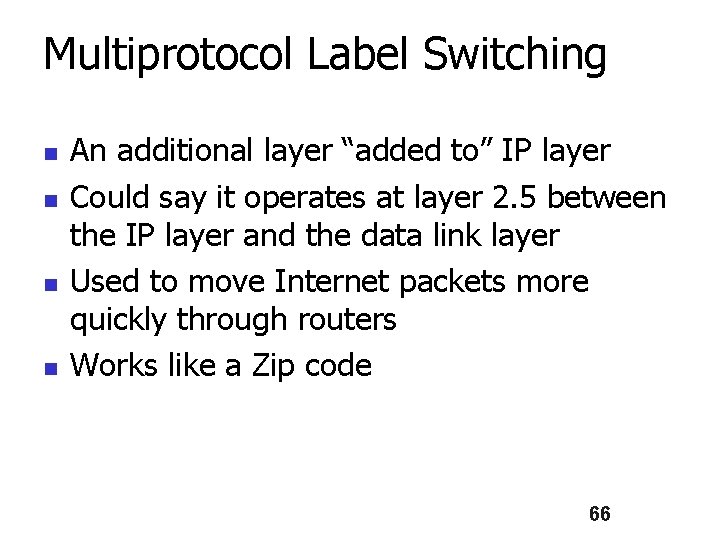
Multiprotocol Label Switching n n An additional layer “added to” IP layer Could say it operates at layer 2. 5 between the IP layer and the data link layer Used to move Internet packets more quickly through routers Works like a Zip code 66

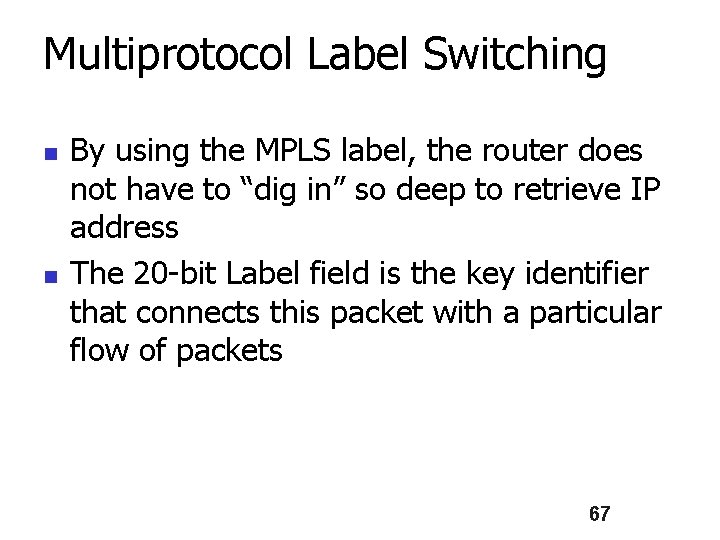
Multiprotocol Label Switching n n By using the MPLS label, the router does not have to “dig in” so deep to retrieve IP address The 20 -bit Label field is the key identifier that connects this packet with a particular flow of packets 67

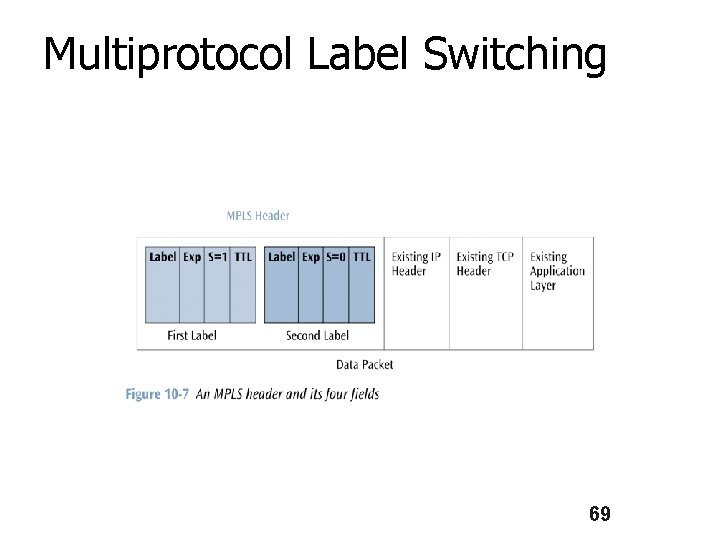
Multiprotocol Label Switching n Four fields in an MPLS header: n n Label (as we saw on previous slide) 3 -bit Traffic Class for Qo. S and congestion notification 1 -bit bottom of stack identifier 8 -bit TTL field 68

Multiprotocol Label Switching 69

Multiprotocol Label Switching n n When a packet with no MPLS header arrives at a Label Edge Router (LER), the LER creates a label with appropriate address – the address chosen can be based upon more than just an IP address (Qo. S too!) Routers that simply route based on MPLS label number are called Label Switch Routers (LSR) 70

VPN (Virtual Private Network) n Many types of VPNs n n Trusted VPNs use non-cryptographic tunneling protocols over a single-provider network, such as MPLS, L 2 TP (layer 2 tunneling protocol), and Microsoft’s PPTP (point to point tunneling protocol) Secure VPNs use cryptographic tunneling protocols, such as IPsec, Microsoft’s SSTP (secure sockets tunneling protocol), and Cisco VPN and their DTLS 71

VPN (Virtual Private Network) n n For example, IPsec provides encrypted transmission of packets over the IP layer (similar to SSL-Secure Sockets Layer and SSH - Secure SHell at the transport layer) Applies a header (Authentication Header) directly on top of the IP layer 72

In Conclusion n There a number of ways to provide a “tunnel” through a network n n n Virtual LANs Frame relay ATM MPLS VPN 73