Attack Methods Chapter 4 Panko Corporate Computer and







































- Slides: 65

Attack Methods Chapter 4 Panko, Corporate Computer and Network Security Copyright 2004 Prentice-Hall

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Unobtrusive Information Collection ¡ Do research before sending any packets into the network n Use in social engineering attacks n Use as background for packet attacks ¡ Corporate website ¡ Trade press (often online and searchable) ¡ Securities and Exchange Commission (SEC) web-enabled Internet financial database (Figure 4 -2) 2

Figure 4 -2: Securities and Exchange Commission's Edgar Service 3

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Unobtrusive Information Collection ¡ Whois database (Figure 4 -3) n Information about responsible person n Information about IP addresses of DNS servers, to find firm’s IP address block n Easy if assigned a classful address block (Figure 4 -4) n Difficult is CIDR address block or a block of ISP addresses 4

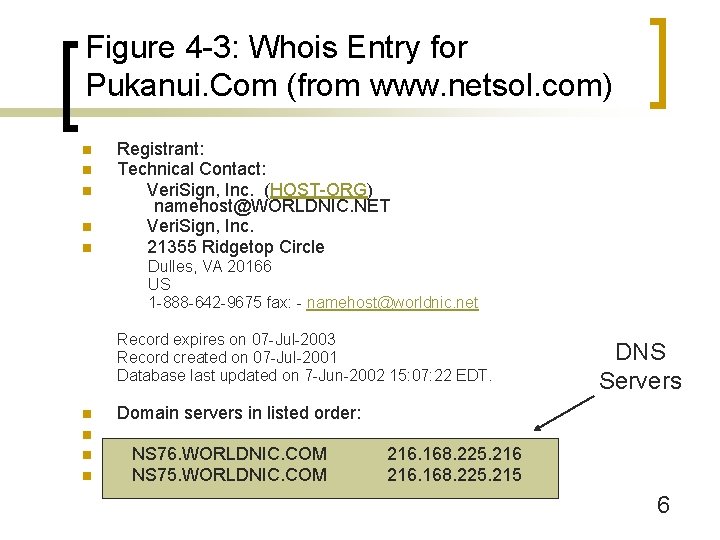
Figure 4 -3: Whois Entry for Pukanui. Com (from www. netsol. com) n Registrant: Panko, Ray (PUKANUI-DOM) 1000 Pukanui St. Honolulu, HI 96821 US n Domain Name: PUKANUI. COM n Administrative Contact: Panko, Ray (RP 17477) n n n Ray@Panko. com n n n 1000 Pukanui St. Honolulu, HI 96821 US (808) 956 -8111 5

Figure 4 -3: Whois Entry for Pukanui. Com (from www. netsol. com) n n n Registrant: Technical Contact: Veri. Sign, Inc. (HOST-ORG) namehost@WORLDNIC. NET Veri. Sign, Inc. 21355 Ridgetop Circle Dulles, VA 20166 US 1 -888 -642 -9675 fax: - namehost@worldnic. net Record expires on 07 -Jul-2003 Record created on 07 -Jul-2001 Database last updated on 7 -Jun-2002 15: 07: 22 EDT. n DNS Servers Domain servers in listed order: n n n NS 76. WORLDNIC. COM NS 75. WORLDNIC. COM 216. 168. 225. 215 6

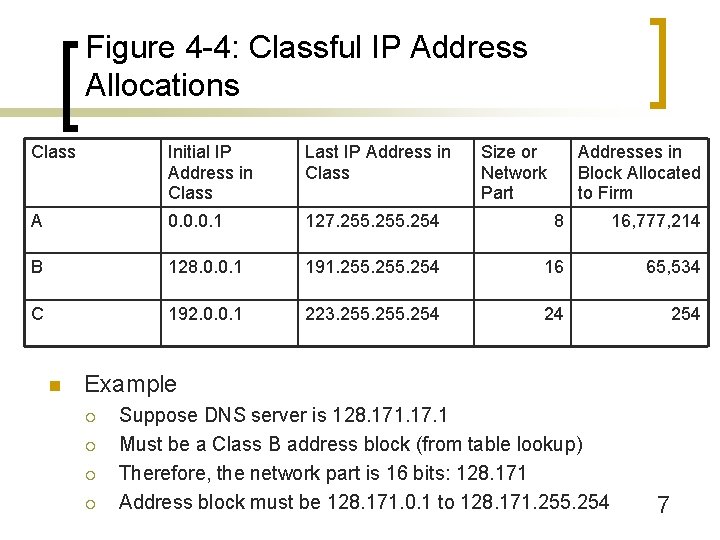
Figure 4 -4: Classful IP Address Allocations Class Initial IP Address in Class Last IP Address in Class A 0. 0. 0. 1 127. 255. 254 8 16, 777, 214 B 128. 0. 0. 1 191. 255. 254 16 65, 534 C 192. 0. 0. 1 223. 255. 254 24 254 n Size or Network Part Addresses in Block Allocated to Firm Example ¡ ¡ Suppose DNS server is 128. 171. 17. 1 Must be a Class B address block (from table lookup) Therefore, the network part is 16 bits: 128. 171 Address block must be 128. 171. 0. 1 to 128. 171. 255. 254 7

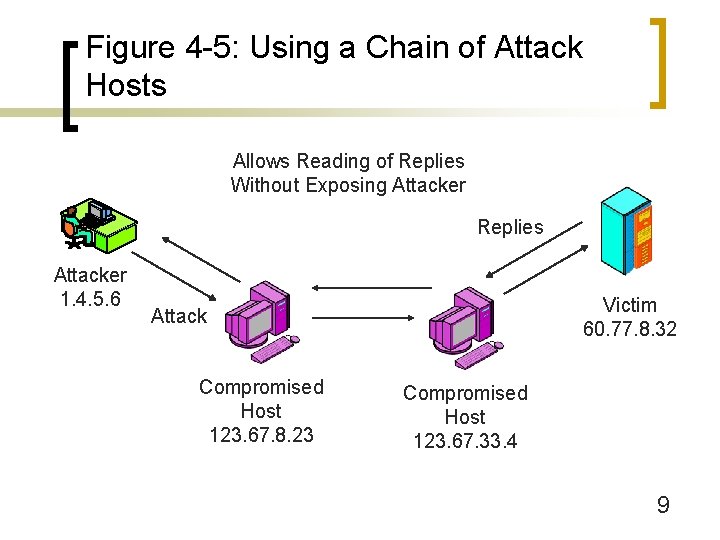
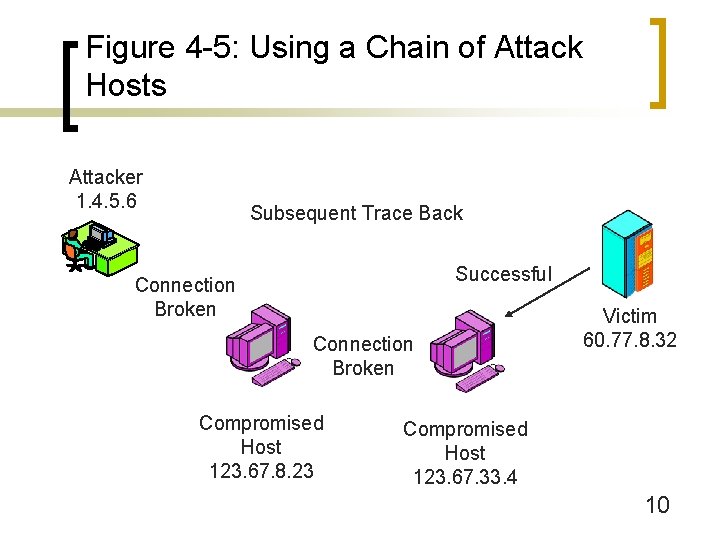
Figure 4 -1: Targeted System Penetration (Break-In Attacks) n IP Address Spoofing (Figure 3 -17) ¡ Put false IP addresses in outgoing attack packets n Attacker is blind to replies ¡ Use series of attack platforms (Figure 4 -5) 8

Figure 4 -5: Using a Chain of Attack Hosts Allows Reading of Replies Without Exposing Attacker Replies Attacker 1. 4. 5. 6 Victim 60. 77. 8. 32 Attack Compromised Host 123. 67. 8. 23 Compromised Host 123. 67. 33. 4 9

Figure 4 -5: Using a Chain of Attack Hosts Attacker 1. 4. 5. 6 Subsequent Trace Back Successful Connection Broken Compromised Host 123. 67. 8. 23 Victim 60. 77. 8. 32 Compromised Host 123. 67. 33. 4 10

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Host Scanning ¡ To identify IP addresses of potential victims ¡ Ping individual hosts (Figure 4 -6) ¡ Ping all IP addresses in block for live IP addresses (Figure 4 -7) 11

Figure 4 -6: Ping at the Windows Command Prompt 12

Figure 4 -7: Ping Scanning With Ping Sweep 13

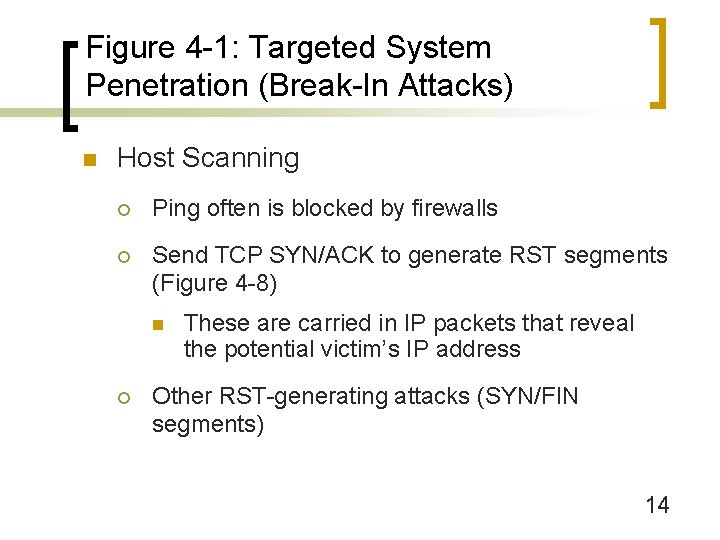
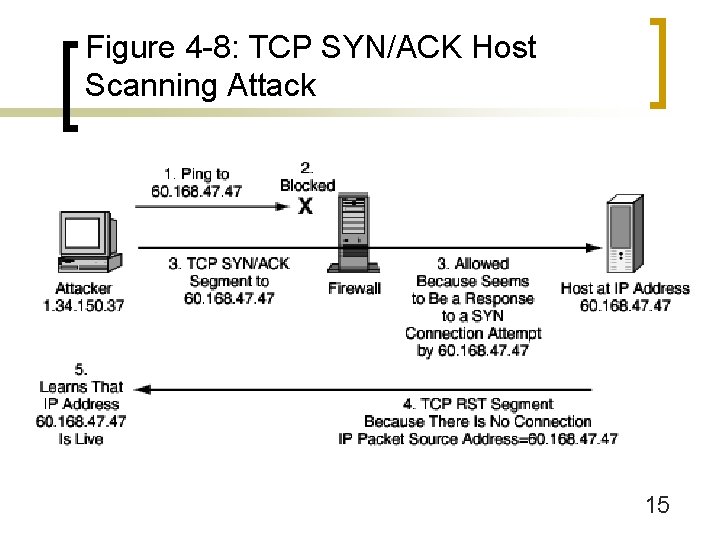
Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Host Scanning ¡ Ping often is blocked by firewalls ¡ Send TCP SYN/ACK to generate RST segments (Figure 4 -8) n ¡ These are carried in IP packets that reveal the potential victim’s IP address Other RST-generating attacks (SYN/FIN segments) 14

Figure 4 -8: TCP SYN/ACK Host Scanning Attack 15

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Network Scanning ¡ To learn about router organization in a network ¡ Send Traceroute messages (Tracert in Windows systems) 16

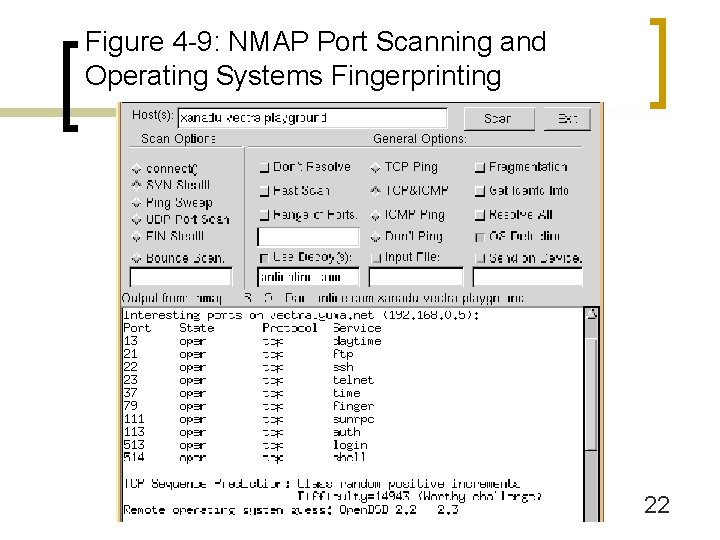
Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Port Scanning ¡ ¡ Most break-ins exploit specific services n For instance, IIS webservers n Services listen for connections on specific TCP or UDP ports (HTTP=80) Scan servers for open ports (Figure 4 -9) n Send SYN segments to a particular port number n Observe SYN/ACK or reset (RST) responses 17

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Port Scanning ¡ May scan for all well-known TCP ports (1024) and all well-known UDP ports (1024) ¡ Or may scan more selectively ¡ Scan clients for Windows file sharing ports (135139) 18

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Fingerprinting ¡ ¡ Identify a particular operating system or application program and (if possible) version n For example, Microsoft Windows 2000 Server n For example, BSD LINUX 4. 2 n For example, Microsoft IIS 5. 0 Useful because most exploits are specific to particular programs or versions 19

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Fingerprinting ¡ Active fingerprinting n Send odd messages and observe replies n Different operating systems and application programs respond differently n Odd packets may set off alarms 20

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Fingerprinting ¡ Passive fingerprinting n n Read packets and look at parameters (TTL, window size, etc. ) ¡ If TTL is 113, probably originally 128. Windows 9 X, NT 4. 0, 2000, or Novell Net. Ware ¡ Window size field is 18, 000. Must be Windows 2000 Server Less precise than active fingerprinting 21

Figure 4 -9: NMAP Port Scanning and Operating Systems Fingerprinting 22

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n Stealth scanning ¡ Scan fewer systems and ports and/or scan more slowly to avoid detection 23

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n The Break-In ¡ Password Guessing n Seldom works because attacker is locked our after a few guesses ¡ Exploits that take advantage of known vulnerabilities that have not been patched n Exploits are easy to use n Frequently effective n The most common break-in approach today 24

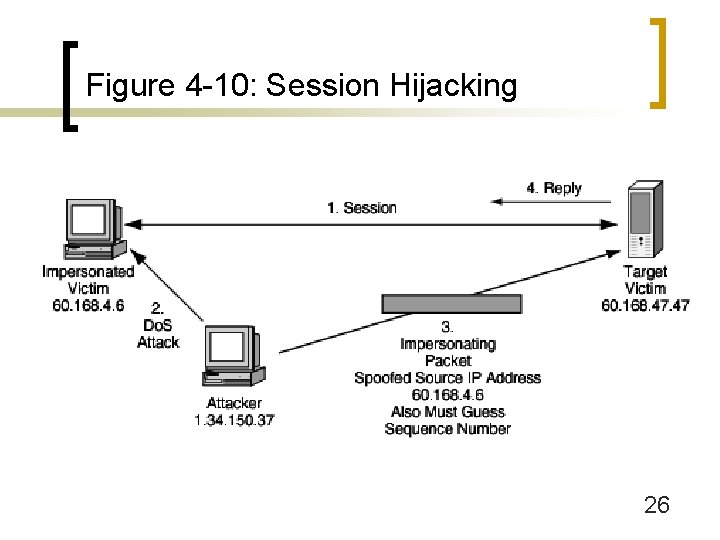
Figure 4 -1: Targeted System Penetration (Break-In Attacks) n The Break-In ¡ Session hijacking (Figure 4 -10) n Take over an existing TCP communication session n Difficult to do (must guess TCP sequence numbers), so not commonly done 25

Figure 4 -10: Session Hijacking 26

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n After the Break-In ¡ Install rootkit n Usually downloaded through trivial file transfer protocol (TFTP) ¡ Erase audit logs ¡ Create backdoors for reentry if original hacking vulnerability is fixed n Backdoor accounts n Trojanized programs that permit reentry 27

Figure 4 -1: Targeted System Penetration (Break-In Attacks) n After the Break-In ¡ Weaken security ¡ Unfettered access to steal information, do damage ¡ Install victimization software n Keystroke capture programs n Spyware n Remote Administration Trojans (RATs) n Attack software to use against other hosts n Spam relay New 28

Figure 4 -11: Denial-of-Service (Do. S) Attacks n n Introduction ¡ Attack on availability ¡ Act of vandalism Single-Message Do. S Attacks ¡ Crash a host with a single attack packet ¡ Examples: Ping-of-Death, Teardrop, and LAND ¡ Send unusual combination for which developers did not test 29

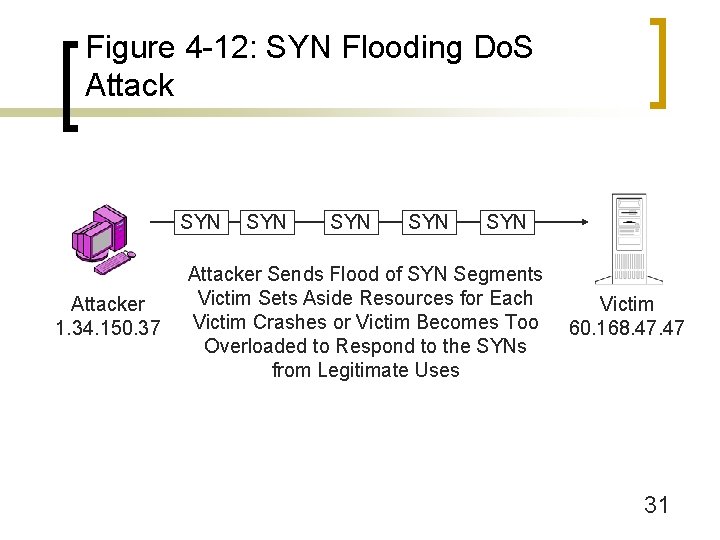
Figure 4 -11: Denial-of-Service (Do. S) Attacks n Flooding Denial-of-Service Attacks ¡ SYN flooding (Figure 4 -12) n Try to open many connections with SYN segments n Victim must prepare to work with many connections n Victim crashes if runs out of resources; at least slows down n More expensive for the victim than the attacker 30

Figure 4 -12: SYN Flooding Do. S Attack SYN Attacker 1. 34. 150. 37 SYN SYN Attacker Sends Flood of SYN Segments Victim Sets Aside Resources for Each Victim Crashes or Victim Becomes Too Overloaded to Respond to the SYNs from Legitimate Uses Victim 60. 168. 47 31

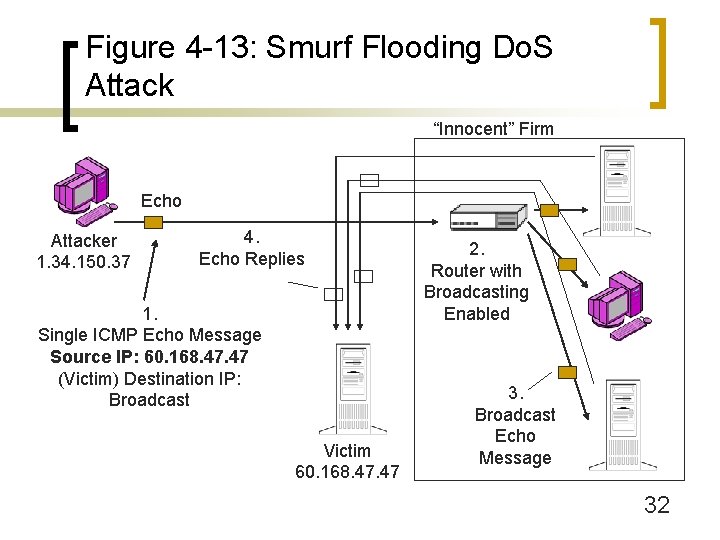
Figure 4 -13: Smurf Flooding Do. S Attack “Innocent” Firm Echo Attacker 1. 34. 150. 37 4. Echo Replies 1. Single ICMP Echo Message Source IP: 60. 168. 47 (Victim) Destination IP: Broadcast Victim 60. 168. 47 2. Router with Broadcasting Enabled 3. Broadcast Echo Message 32

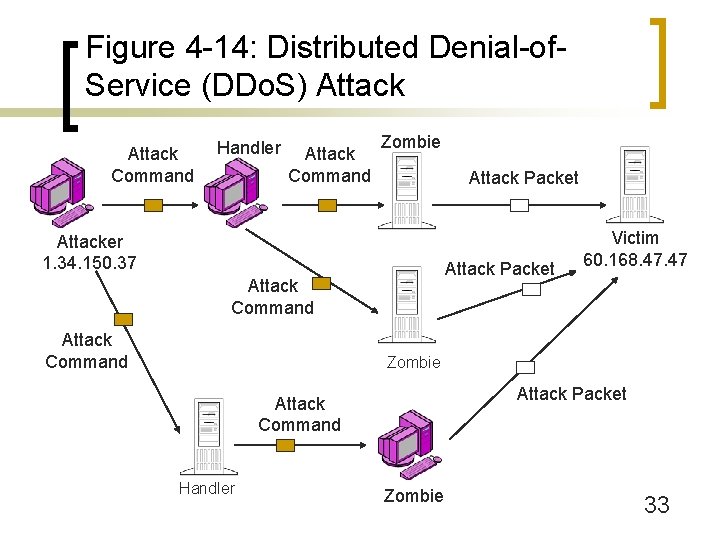
Figure 4 -14: Distributed Denial-of. Service (DDo. S) Attack Command Handler Attack Command Zombie Attack Packet Attacker 1. 34. 150. 37 Attack Packet Attack Command Victim 60. 168. 47 Zombie Attack Packet Attack Command Handler Zombie 33

Figure 4 -11: Denial-of-Service (Do. S) Attacks n Stopping Do. S Attacks ¡ Ingress filtering to stop attack packets (Figure 414) ¡ Limited ability of ingress filtering because link to ISP might become overloaded ¡ Egress filtering by attacker’s company or ISP ¡ Requires cooperating from attacker’s company or ISP ¡ Requires a community response; victim cannot do it alone 34

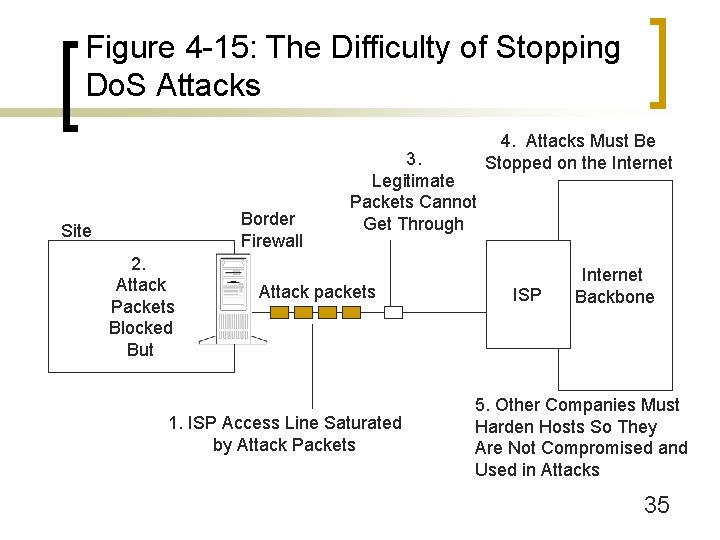
Figure 4 -15: The Difficulty of Stopping Do. S Attacks Border Firewall Site 2. Attack Packets Blocked But 3. Legitimate Packets Cannot Get Through Attack packets 1. ISP Access Line Saturated by Attack Packets 4. Attacks Must Be Stopped on the Internet ISP Internet Backbone 5. Other Companies Must Harden Hosts So They Are Not Compromised and Used in Attacks 35

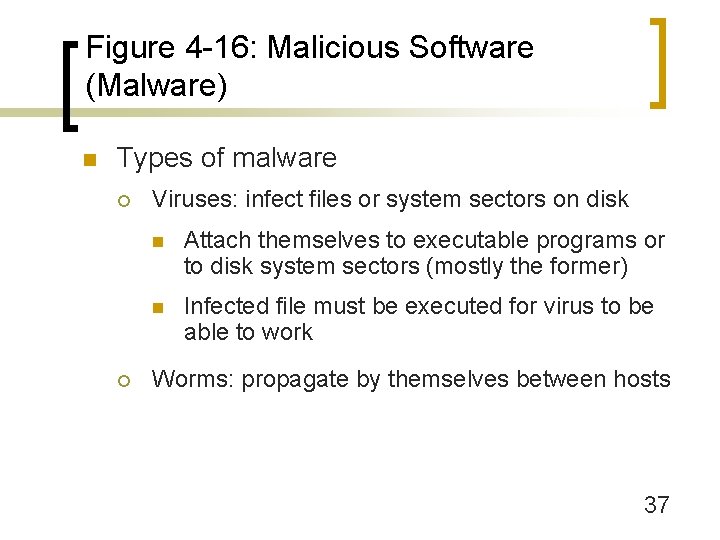
Figure 4 -16: Malicious Software (Malware) n Malware: Malicious software n Essentially an automated attack robot capable of doing much damage n Usually target-of-opportunity attacks 36

Figure 4 -16: Malicious Software (Malware) n Types of malware ¡ ¡ Viruses: infect files or system sectors on disk n Attach themselves to executable programs or to disk system sectors (mostly the former) n Infected file must be executed for virus to be able to work Worms: propagate by themselves between hosts 37

Figure 4 -16: Malicious Software (Malware) n Types of malware ¡ Payloads n Malicious: designed to do damage n “Benign” may do damage accidentally 38

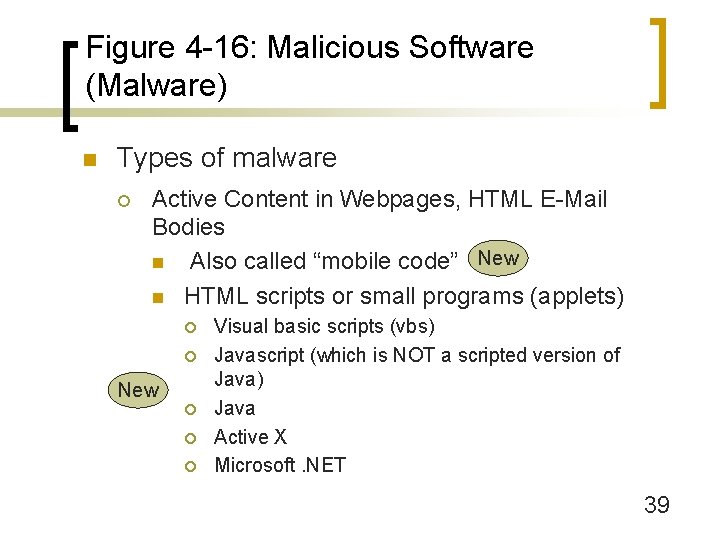
Figure 4 -16: Malicious Software (Malware) n Types of malware ¡ Active Content in Webpages, HTML E-Mail Bodies n Also called “mobile code” New n HTML scripts or small programs (applets) ¡ ¡ New ¡ ¡ ¡ Visual basic scripts (vbs) Javascript (which is NOT a scripted version of Java) Java Active X Microsoft. NET 39

Figure 4 -16: Malicious Software (Malware) n Types of malware ¡ Active Content in Webpages, HTML E-Mail Bodies (also called “mobile code”) New n Attack directly when clicked on or download a malicious program n User can turn off active content execution, but webpage functionality will be reduced ¡ Non-mobile malware n Trojan horses, etc. 40

Figure 4 -16: Malicious Software (Malware) n Types of malware ¡ Blended threats combine attack vectors and after-attack damage tools n Propagate in multiple ways: as viruses, worms and active content n Afterward, do damage directly, and download non-mobile attack programs 41

Figure 4 -16: Malicious Software (Malware) n Viruses ¡ Executable versus macro viruses n Executable viruses attach to executable programs (traditional) n Macro viruses attach as macros (series of commands) to data file; executed when file is opened 42

Figure 4 -16: Malicious Software (Malware) n Viruses ¡ Propagation vectors n Exchange floppy disks (rare) n E-mail attachments ¡ E-mail offers easy attachment delivery ¡ 90% of viruses spread via e-mail attachments today 43

Figure 4 -16: Malicious Software (Malware) n Viruses ¡ Propagation vectors n E-mail attachments ¡ An epidemic: virus in every 200 to 400 email messages ¡ Some users open attachments from people they trust 44

Figure 4 -16: Malicious Software (Malware) n Viruses ¡ Propagation vectors n E-mail attachments ¡ But good people get viruses ¡ Viruses send e-mail pretending to be coming from victim ¡ Should open e-mail attachments only if specifically expected and still scan with updated virus program ¡ HTML bodies may execute malware automatically 45

Figure 4 -16: Malicious Software (Malware) n Viruses ¡ Propagation vectors n IRC and instant messaging (IM) n FTP and website downloads 46

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Location for Filtering n On clients (often disabled by users) n On mail servers (does not require user compliance) n Outsourced e-mail scanning outside the firm (advantages of scale and experience) 47

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Scanning Method n Signature scanning (characteristic sequence of commands for a particular virus) ¡ n Dominant scanning method today Behavioral scanning (what the virus tries to do, for instance reformat the hard drive) ¡ Can stop new viruses and worms ¡ Many false alarms and misses 48

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Two nightmares for antivirus professionals n Flash viruses that spread too rapidly for signatures to be developed ¡ Not a theoretical concern. In 2001, Nimda became the most widespread Internet virus/worm within 22 minutes! ¡ Behavioral scanning and outsourcing firms that see many instances quickly will become important 49

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Two nightmares for antivirus professionals n Metamorphic viruses ¡ Instead of placing their code at the end of the infected file, they place it throughout the file ¡ Might make signature detection inaccurate ¡ Might make signature detection too slow to be workable 50

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Recovery n Detection and Identification n Repair ¡ Go to the antivirus vendor’s website ¡ Malware-specific repair program or manual procedure 51

Figure 4 -16: Malicious Software (Malware) n Antivirus Protection ¡ Recovery n Repair ¡ Often, infected programs must be reinstalledsometimes the entire operating system ¡ Some or all data since the last backup might be lost ¡ If damage to data files took place over a period of time, a company might not know when its last clean backup was ¡ Extremely time consuming 52

Figure 4 -16: Malicious Software (Malware) n Nimda Worm of 2001 ¡ Highly sophisticated blended threat ¡ Spread by infected clients infecting other clients n Spread by sending e-mail in client’s name (often accepted because receivers recognize and trust the name) n Spread by open file shares on client 53

Figure 4 -16: Malicious Software (Malware) n Nimda Worm of 2001 ¡ Spread by infected clients infecting webservers n Client scanning for IIS webservers almost constitutes a Do. S attack n Client infects IIS webserver through backdoors left by previous viruses and worm n Client infects IIS webserver through unpatched directory traversal vulnerability 54

Figure 4 -16: Malicious Software (Malware) n Nimda Worm ¡ Spread by IIS webserver infecting clients with malicious links, often executed automatically when the page is downloaded ¡ Trojanizes various files so they are difficult to find and clean out ¡ Multiple propagation vectors allowed Nimda to become the Internet’s most widespread virus/worm within 22 minutes 55

Topics Covered n n Unobtrusive Data Collection ¡ From public sites ¡ Whois database Sending Scanning Packets ¡ IP address spoofing to hide identity ¡ Using a chain of attack hosts when there must be a legitimate IP address 56

Topics Covered n n Host Scanning ¡ To identify possible victims ¡ Ping range of IP addresses or use alternative scanning messages Network Scanning ¡ To learn a network’s structure (routers, subnets, etc. ) ¡ Tracert shows all routers along the route to a destination host 57

Topics Covered n Port Scanning ¡ n n Once a host is identified, scan all ports to find out if it is a server and what type it is Fingerprinting ¡ Learn a victim’s operating system and version and applications and versions if possible ¡ Passive (listen) versus active (send probes) fingerprinting Nmap does all major scanning methods 58

Topics Covered n The Break-In ¡ Password guessing ¡ Take advantage of unpatched vulnerabilities n The most effective form of break-in today ¡ Session hijacking 59

Topics Covered n After the Break-In ¡ Delete log files ¡ Create backdoor account or program ¡ Download rootkit to the victim host ¡ Weaken security ¡ Unfettered access to steal information, do damage ¡ Install victimization software (keystroke capture program, RAT, Do. S zombie, spam relay, etc. ) 60

Topics Covered n Denial-of-Service (Do. S) Attacks ¡ Attacks on availability ¡ SYN flooding attacks overload a host or network with connection attempts n Distributed Do. S attacks use many zombies to do the flooding ¡ Stopping Do. S attacks is very hard n May require the cooperation of the ISP, zombie owners 61

Topics Covered n Malware ¡ Malicious software n Essentially an automated attack robot n Usually target-of-opportunity attacks ¡ Viruses and worms n Some worms can propagate on their own n Payloads: malicious or “benign” ¡ Active Content (Mobile Code) in Webpages, etc. Non-mobile malware (Trojan horses, etc. ) Blended threats combine several forms of malware 62 ¡ ¡

Topics Covered n Viruses ¡ Infect programs or data files (macro viruses) ¡ Propagate by e-mail attachment (90%), floppy disk, etc. ¡ Must train users to not open attachments except under specific circumstances 63

Topics Covered n Viruses ¡ Location of e-mail and webpage filtering n Clients often turn off their programs or fail to maintain their subscription and database n On server, users cannot interfere n Outsourcing firms can scan before the mail reaches the firm ¡ Nightmare scenario n Flash viruses n Metamorphic viruses 64

Topics Covered n Viruses ¡ n Recovery n Detection and identification n Repair Nimda ¡ Blended threat: spread in several ways ¡ This allowed it to spread very rapidly ¡ Became the most widespread infection within 22 minutes 65