15 744 Computer Networking L14 Network Topology Todays





![Summary Network Topology • Faloutsos 3 [SIGCOMM 99] on Internet topology • Observed many Summary Network Topology • Faloutsos 3 [SIGCOMM 99] on Internet topology • Observed many](https://slidetodoc.com/presentation_image/4795ee8685923d4e3472f3236e119267/image-38.jpg)



![Better Measurements? • Rocketfuel [sigcomm 02] • Better router alias resolution • Detailed maps Better Measurements? • Rocketfuel [sigcomm 02] • Better router alias resolution • Detailed maps](https://slidetodoc.com/presentation_image/4795ee8685923d4e3472f3236e119267/image-51.jpg)

- Slides: 52

15 -744: Computer Networking L-14 Network Topology

Today’s Lecture • • • Structural generators Power laws HOT graphs Graph generators Assigned reading • On Power-Law Relationships of the Internet Topology • A First Principles Approach to Understanding the Internet’s Router-level Topology 2

Outline • Motivation/Background • Power Laws • Optimization Models • Graph Generation 3

Why study topology? • Correctness of network protocols typically independent of topology • Performance of networks critically dependent on topology • e. g. , convergence of route information • Internet impossible to replicate • Modeling of topology needed to generate test topologies 4

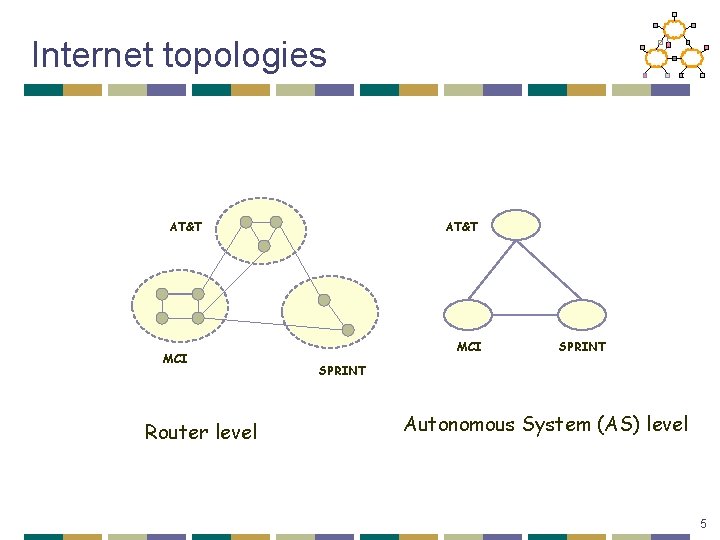
Internet topologies AT&T MCI Router level AT&T MCI SPRINT Autonomous System (AS) level 5

More on topologies. . • Router level topologies reflect physical connectivity between nodes • Inferred from tools like traceroute or well known public measurement projects like Mercator and Skitter • AS graph reflects a peering relationship between two providers/clients • Inferred from inter-domain routers that run BGP and publlic projects like Oregon Route Views • Inferring both is difficult, and often inaccurate 6

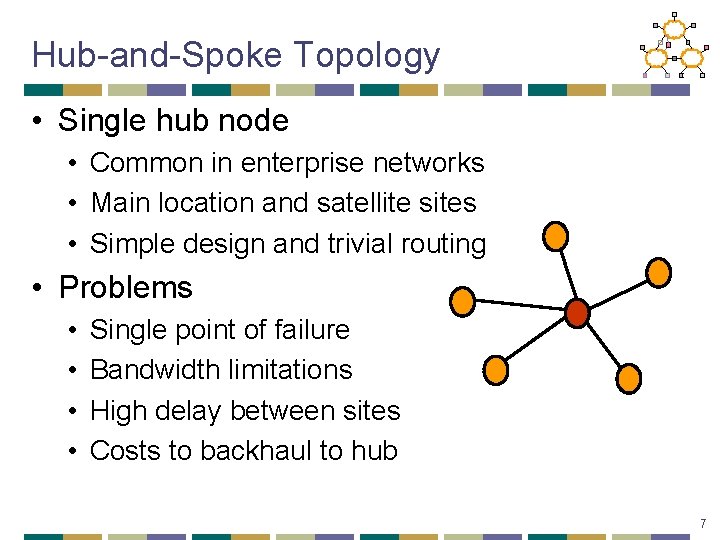
Hub-and-Spoke Topology • Single hub node • Common in enterprise networks • Main location and satellite sites • Simple design and trivial routing • Problems • • Single point of failure Bandwidth limitations High delay between sites Costs to backhaul to hub 7

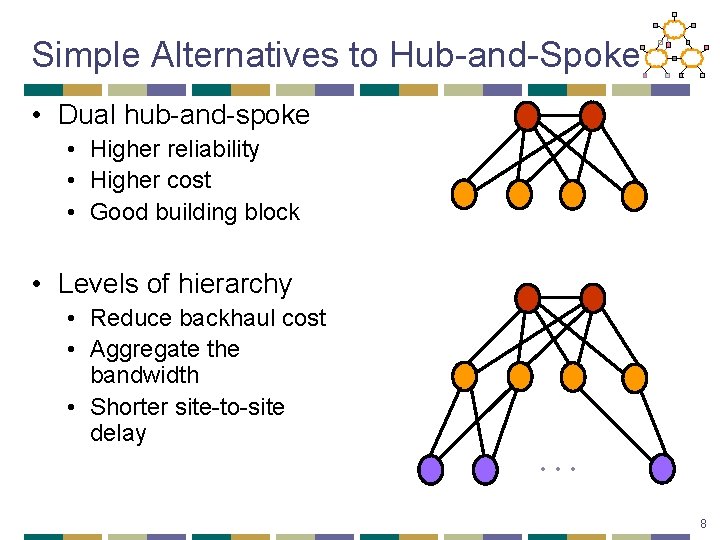
Simple Alternatives to Hub-and-Spoke • Dual hub-and-spoke • Higher reliability • Higher cost • Good building block • Levels of hierarchy • Reduce backhaul cost • Aggregate the bandwidth • Shorter site-to-site delay … 8

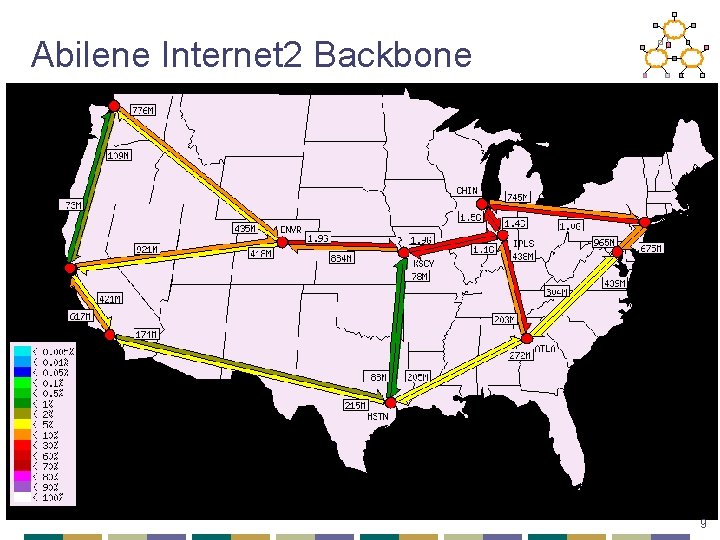
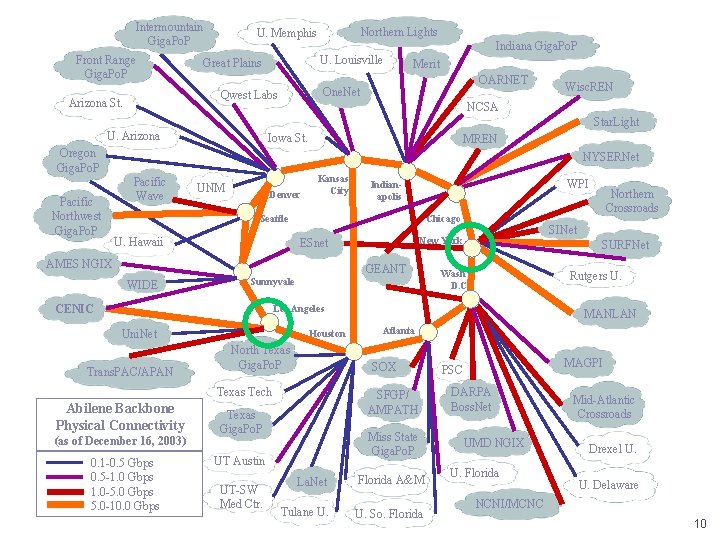
Abilene Internet 2 Backbone 9

Intermountain Giga. Po. P Front Range Giga. Po. P Indiana Giga. Po. P U. Louisville Great Plains Merit OARNET One. Net Qwest Labs Arizona St. Northern Lights U. Memphis Wisc. REN NCSA Star. Light U. Arizona Iowa St. Oregon Giga. Po. P Pacific Northwest Giga. Po. P MREN NYSERNet Pacific Wave UNM Denver Kansas City WPI Indianapolis Chicago Seattle U. Hawaii AMES NGIX WIDE GEANT Sunnyvale CENIC SINet New York ESnet SURFNet Wash D. C. Rutgers U. Los Angeles Uni. Net Trans. PAC/APAN Houston North Texas Giga. Po. P Abilene Backbone Physical Connectivity (as of December 16, 2003) 0. 1 -0. 5 Gbps 0. 5 -1. 0 Gbps 1. 0 -5. 0 Gbps 5. 0 -10. 0 Gbps Atlanta SFGP/ AMPATH Texas Giga. Po. P Miss State Giga. Po. P UT Austin UT-SW Med Ctr. MANLAN SOX Texas Tech Northern Crossroads La. Net Florida A&M Tulane U. So. Florida MAGPI PSC DARPA Boss. Net UMD NGIX U. Florida Mid-Atlantic Crossroads Drexel U. U. Delaware NCNI/MCNC 10

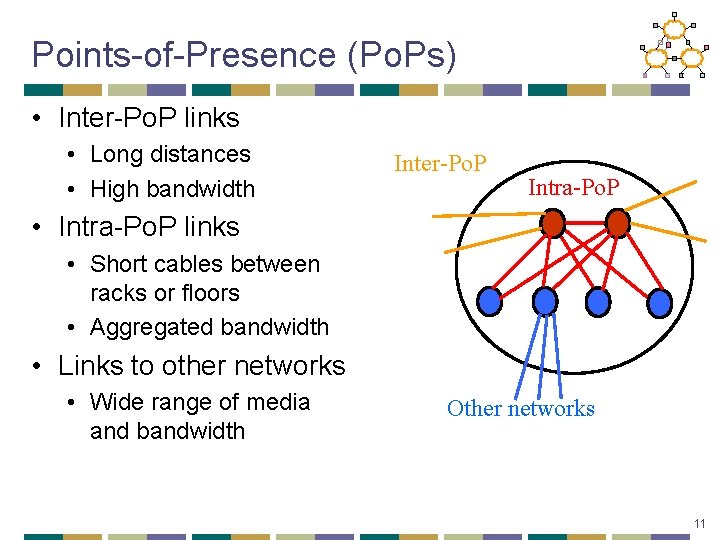
Points-of-Presence (Po. Ps) • Inter-Po. P links • Long distances • High bandwidth Inter-Po. P Intra-Po. P • Intra-Po. P links • Short cables between racks or floors • Aggregated bandwidth • Links to other networks • Wide range of media and bandwidth Other networks 11

Deciding Where to Locate Nodes and Links • Placing Points-of-Presence (Po. Ps) • • Large population of potential customers Other providers or exchange points Cost and availability of real-estate Mostly in major metropolitan areas • Placing links between Po. Ps • Already fiber in the ground • Needed to limit propagation delay • Needed to handle the traffic load 12

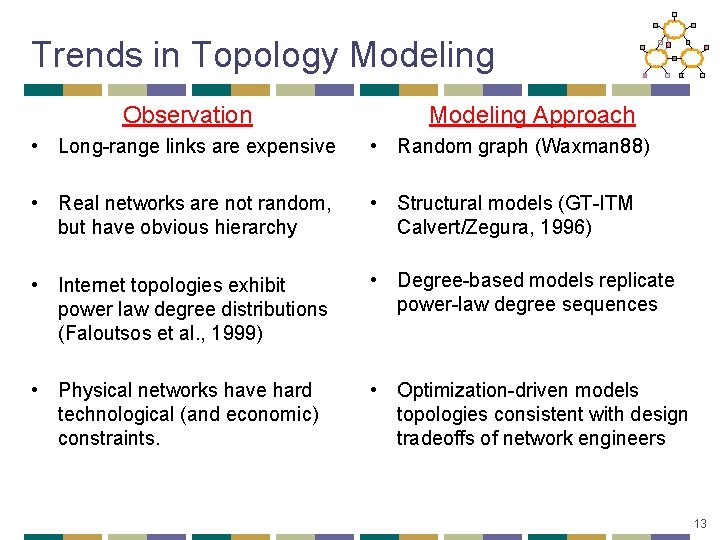
Trends in Topology Modeling Observation Modeling Approach • Long-range links are expensive • Random graph (Waxman 88) • Real networks are not random, but have obvious hierarchy • Structural models (GT-ITM Calvert/Zegura, 1996) • Internet topologies exhibit power law degree distributions (Faloutsos et al. , 1999) • Degree-based models replicate power-law degree sequences • Physical networks have hard technological (and economic) constraints. • Optimization-driven models topologies consistent with design tradeoffs of network engineers 13

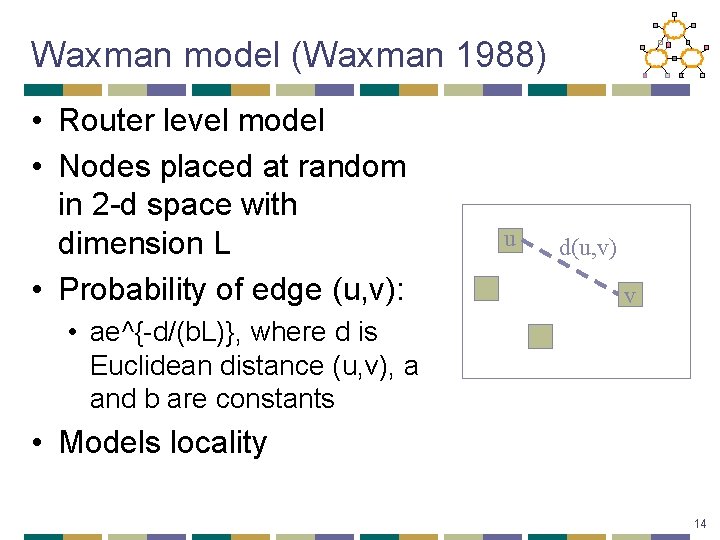
Waxman model (Waxman 1988) • Router level model • Nodes placed at random in 2 -d space with dimension L • Probability of edge (u, v): u d(u, v) v • ae^{-d/(b. L)}, where d is Euclidean distance (u, v), a and b are constants • Models locality 14

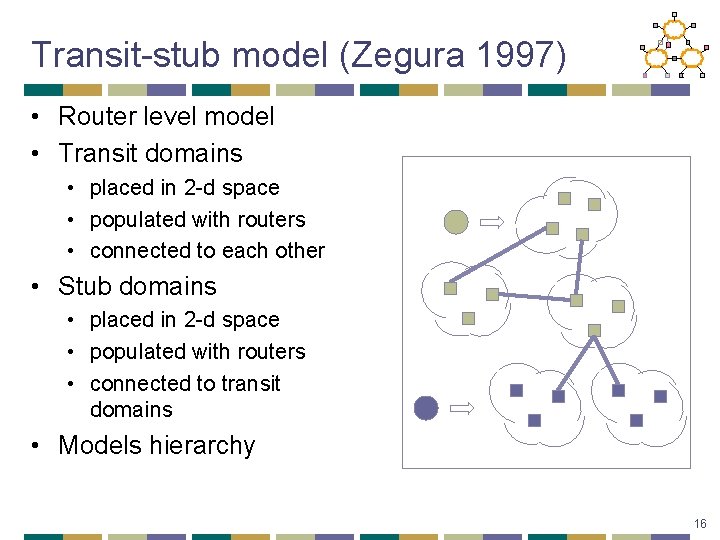
Real world topologies • Real networks exhibit • • Hierarchical structure Specialized nodes (transit, stub. . ) Connectivity requirements Redundancy • Characteristics incorporated into the Georgia Tech Internetwork Topology Models (GT-ITM) simulator (E. Zegura, K. Calvert and M. J. Donahoo, 1995) 15

Transit-stub model (Zegura 1997) • Router level model • Transit domains • placed in 2 -d space • populated with routers • connected to each other • Stub domains • placed in 2 -d space • populated with routers • connected to transit domains • Models hierarchy 16

So…are we done? • No! • In 1999, Faloutsos and Faloutsos published a paper, demonstrating power law relationships in Internet graphs • Specifically, the node degree distribution exhibited power laws That Changed Everything…. . 17

Outline • Motivation/Background • Power Laws • Optimization Models • Graph Generation 18

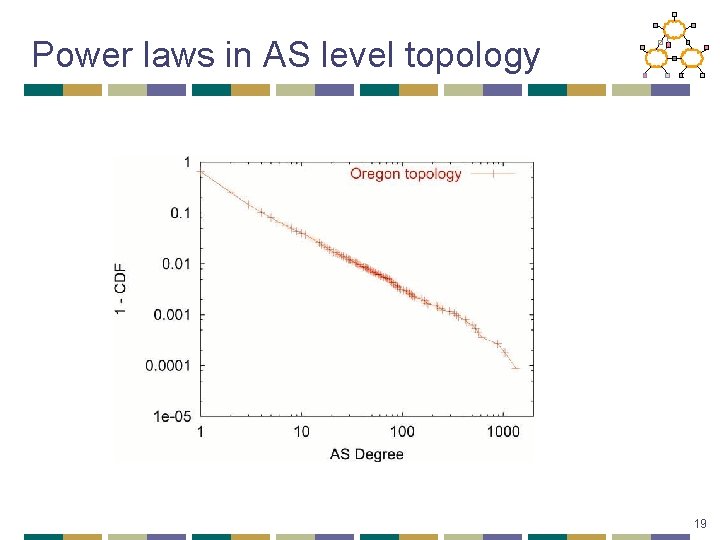
Power laws in AS level topology 19

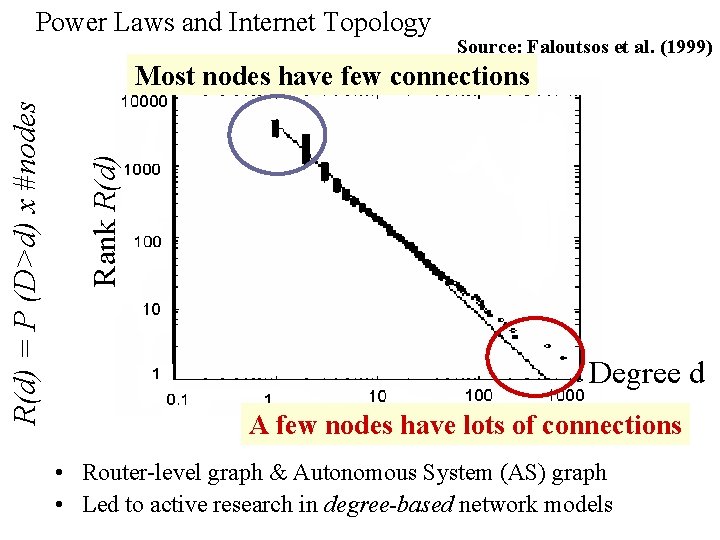
Power Laws and Internet Topology Source: Faloutsos et al. (1999) Rank R(d) = P (D>d) x #nodes Most nodes have few connections Degree d A few nodes have lots of connections • Router-level graph & Autonomous System (AS) graph • Led to active research in degree-based network models

GT-ITM abandoned. . • GT-ITM did not give power law degree graphs • New topology generators and explanation for power law degrees were sought • Focus of generators to match degree distribution of observed graph 21

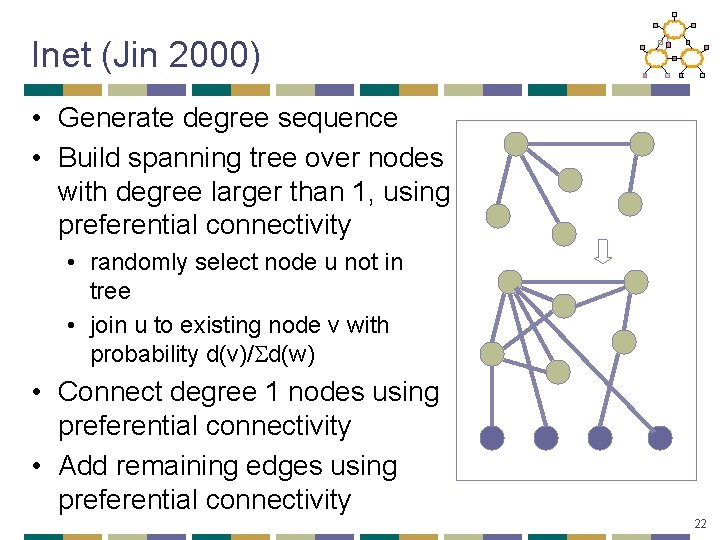
Inet (Jin 2000) • Generate degree sequence • Build spanning tree over nodes with degree larger than 1, using preferential connectivity • randomly select node u not in tree • join u to existing node v with probability d(v)/ d(w) • Connect degree 1 nodes using preferential connectivity • Add remaining edges using preferential connectivity 22

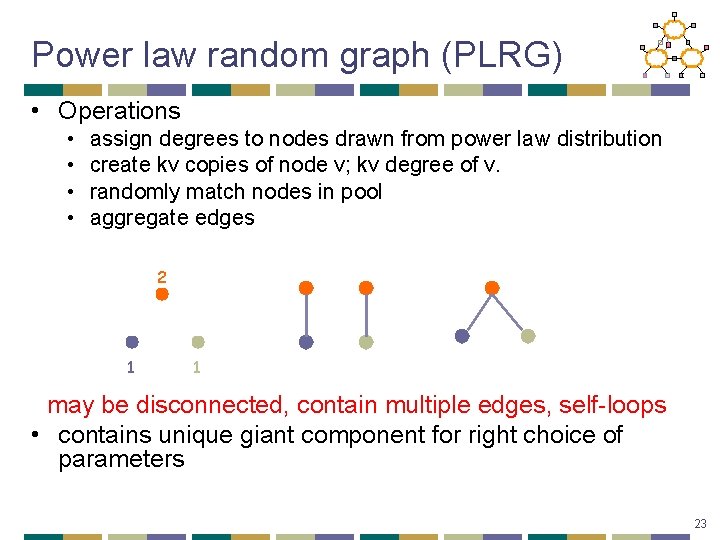
Power law random graph (PLRG) • Operations • • assign degrees to nodes drawn from power law distribution create kv copies of node v; kv degree of v. randomly match nodes in pool aggregate edges 2 1 1 may be disconnected, contain multiple edges, self-loops • contains unique giant component for right choice of parameters 23

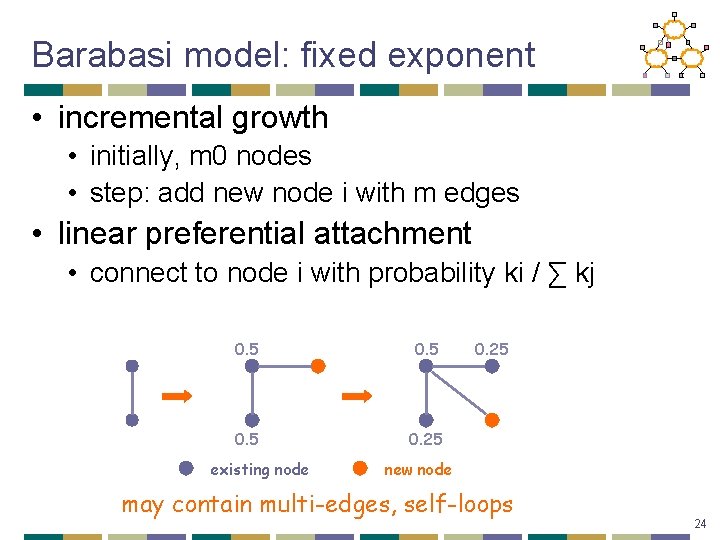
Barabasi model: fixed exponent • incremental growth • initially, m 0 nodes • step: add new node i with m edges • linear preferential attachment • connect to node i with probability ki / ∑ kj 0. 5 0. 25 existing node 0. 25 new node may contain multi-edges, self-loops 24

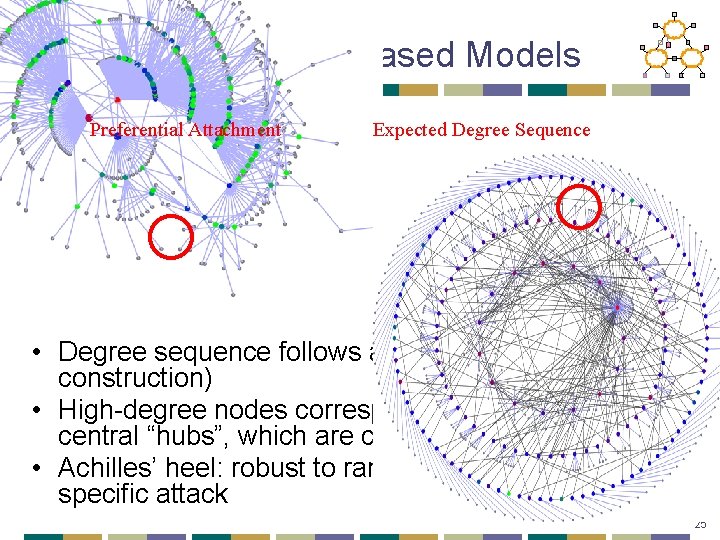
Features of Degree-Based Models Preferential Attachment Expected Degree Sequence • Degree sequence follows a power law (by construction) • High-degree nodes correspond to highly connected central “hubs”, which are crucial to the system • Achilles’ heel: robust to random failure, fragile to specific attack 25

Does Internet graph have these properties? • No…(There is no Memphis!) • Emphasis on degree distribution - structure ignored • Real Internet very structured • Evolution of graph is highly constrained 26

Problem With Power Law • . . . but they're descriptive models! • No correct physical explanation, need an understanding of: • the driving force behind deployment • the driving force behind growth 27

Outline • Motivation/Background • Power Laws • Optimization Models • Graph Generation 28

Li et al. • Consider the explicit design of the Internet • Annotated network graphs (capacity, bandwidth) • Technological and economic limitations • Network performance • Seek a theory for Internet topology that is explanatory and not merely descriptive. • Explain high variability in network connectivity • Ability to match large scale statistics (e. g. power laws) is only secondary evidence 29

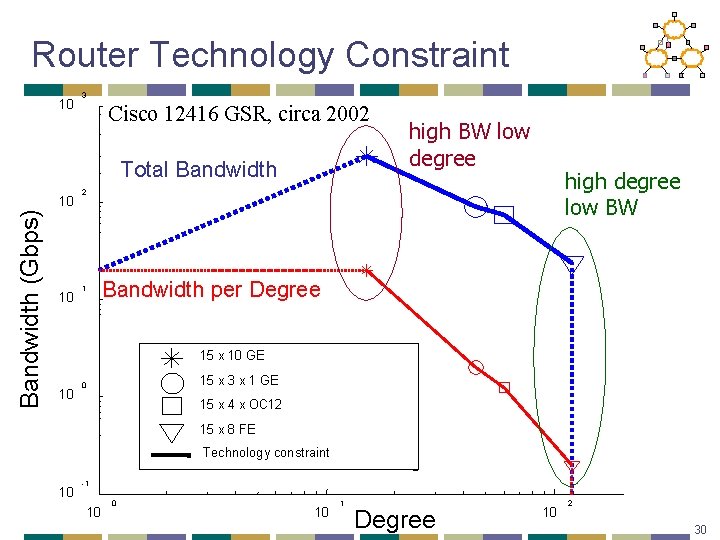
Router Technology Constraint 10 3 Cisco 12416 GSR, circa 2002 Total Bandwidth (Gbps) 10 10 high BW low degree high degree low BW 2 1 Bandwidth per Degree 15 x 10 GE 10 15 x 3 x 1 GE 0 15 x 4 x OC 12 15 x 8 FE Technology constraint 10 -1 10 0 10 1 Degree 10 2 30

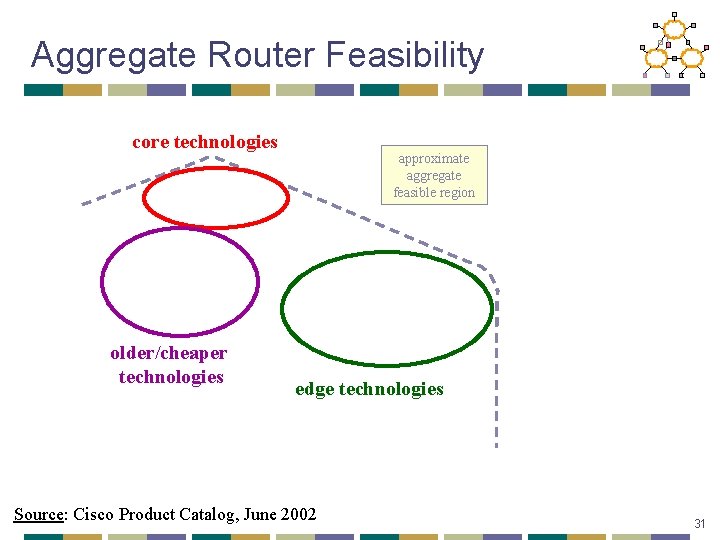
Aggregate Router Feasibility core technologies older/cheaper technologies approximate aggregate feasible region edge technologies Source: Cisco Product Catalog, June 2002 31

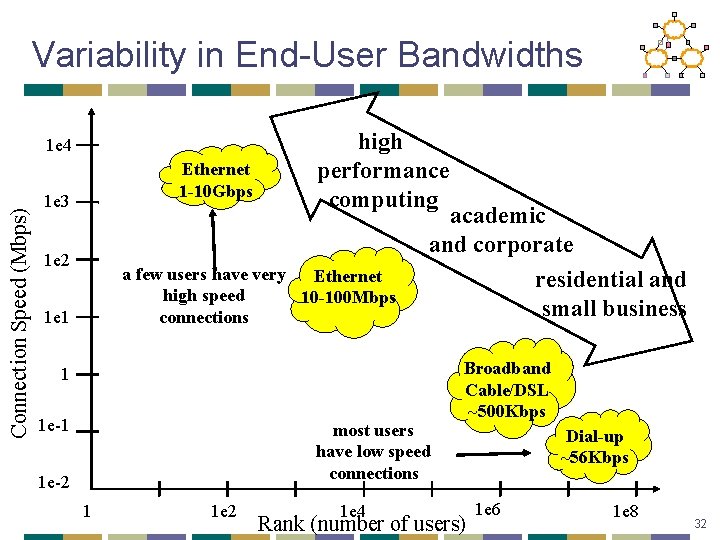
Variability in End-User Bandwidths Connection Speed (Mbps) 1 e 4 Ethernet 1 -10 Gbps 1 e 3 1 e 2 high performance computing a few users have very Ethernet high speed 10 -100 Mbps connections 1 e 1 academic and corporate residential and small business 1 1 e-1 most users have low speed connections 1 e-2 1 1 e 2 1 e 4 Broadband Cable/DSL ~500 Kbps Rank (number of users) Dial-up ~56 Kbps 1 e 6 1 e 8 32

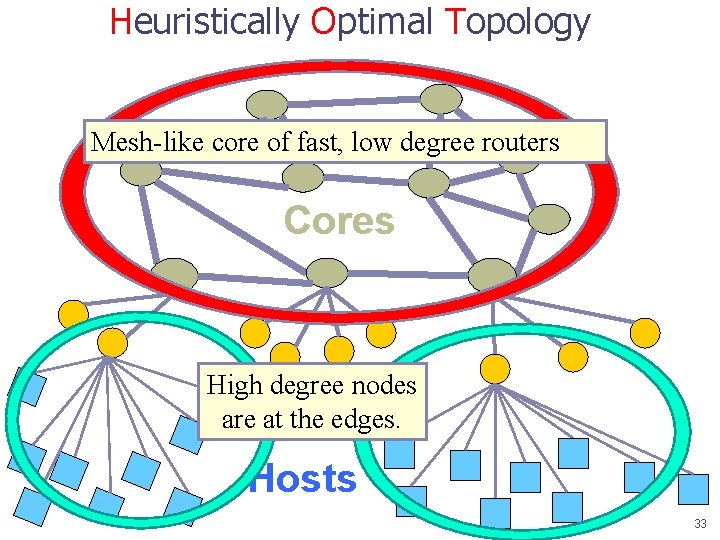
Heuristically Optimal Topology Mesh-like core of fast, low degree routers Cores High degree nodes are at. Edges the edges. Hosts 33

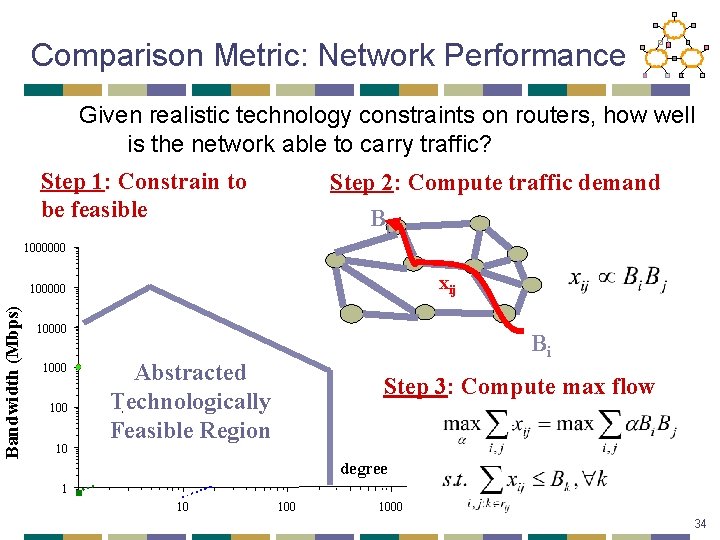
Comparison Metric: Network Performance Given realistic technology constraints on routers, how well is the network able to carry traffic? Step 1: Constrain to be feasible Step 2: Compute traffic demand Bj 1000000 xij Bandwidth (Mbps) 100000 1000 10 Bi Abstracted Technologically Feasible Region Step 3: Compute max flow degree 1 10 1000 34

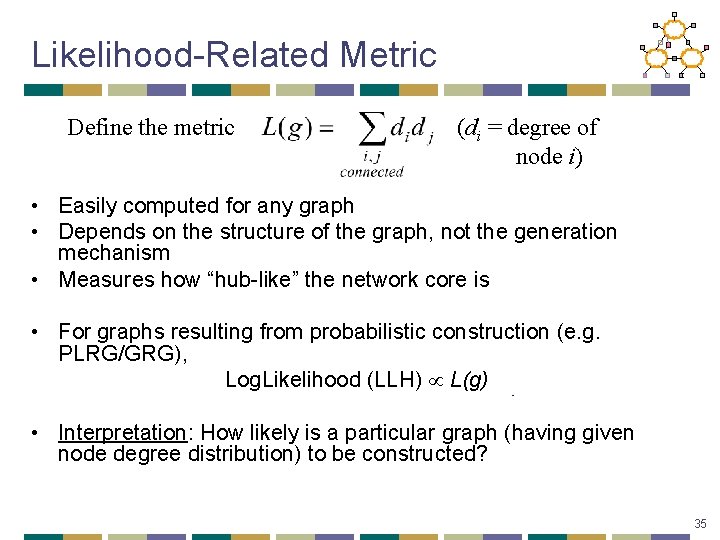
Likelihood-Related Metric Define the metric (di = degree of node i) • Easily computed for any graph • Depends on the structure of the graph, not the generation mechanism • Measures how “hub-like” the network core is • For graphs resulting from probabilistic construction (e. g. PLRG/GRG), Log. Likelihood (LLH) L(g) • Interpretation: How likely is a particular graph (having given node degree distribution) to be constructed? 35

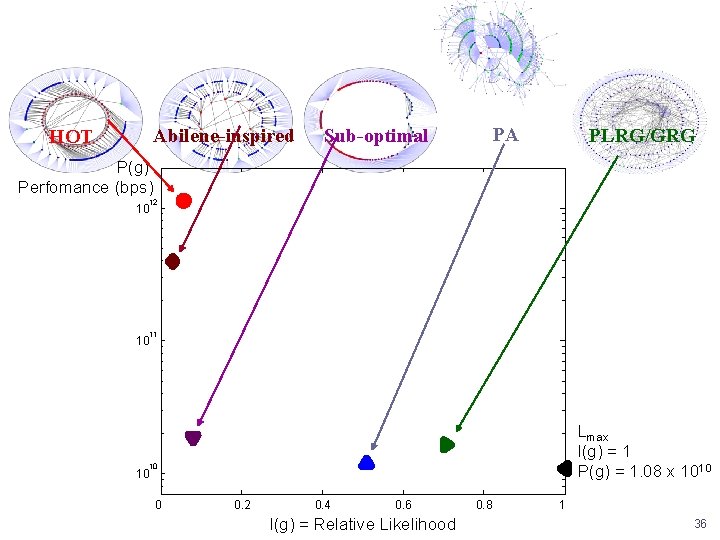
Abilene-inspired HOT PA Sub-optimal PLRG/GRG P(g) Perfomance (bps) 12 10 11 10 Lmax l(g) = 1 P(g) = 1. 08 x 1010 10 10 0 0. 2 0. 4 0. 6 l(g) = Relative Likelihood 0. 8 1 36

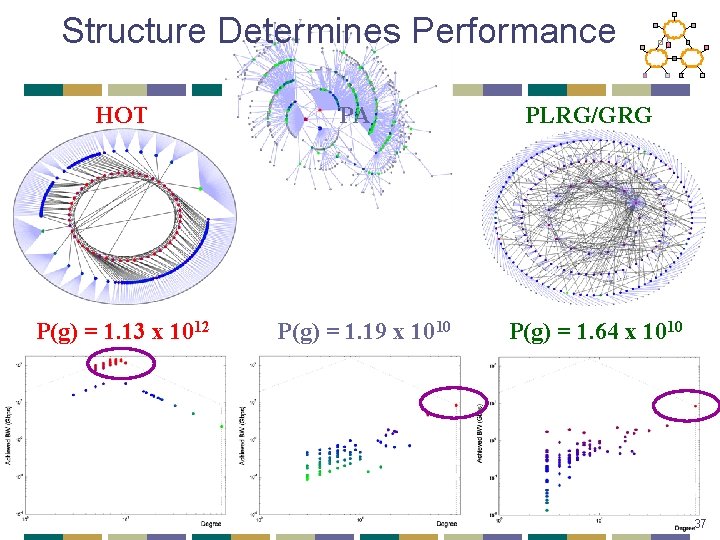
Structure Determines Performance HOT P(g) = 1. 13 x 1012 PA P(g) = 1. 19 x 1010 PLRG/GRG P(g) = 1. 64 x 1010 37
![Summary Network Topology Faloutsos 3 SIGCOMM 99 on Internet topology Observed many Summary Network Topology • Faloutsos 3 [SIGCOMM 99] on Internet topology • Observed many](https://slidetodoc.com/presentation_image/4795ee8685923d4e3472f3236e119267/image-38.jpg)
Summary Network Topology • Faloutsos 3 [SIGCOMM 99] on Internet topology • Observed many “power laws” in the Internet structure • Router level connections, AS-level connections, neighborhood sizes • Power law observation refuted later, Lakhina [INFOCOM 00] • Inspired many degree-based topology generators • Compared properties of generated graphs with those of measured graphs to validate generator • What is wrong with these topologies? Li et al [SIGCOMM 04] • Many graphs with similar distribution have different properties • Random graph generation models don’t have network-intrinsic meaning • Should look at fundamental trade-offs to understand topology • Technology constraints and economic trade-offs • Graphs arising out of such generation better explain topology and its properties, but are unlikely to be generated by random processes! 38

Outline • Motivation/Background • Power Laws • Optimization Models • Graph Generation 39

Graph Generation • Many important topology metrics • • Spectrum Distance distribution Degree distribution Clustering… • No way to reproduce most of the important metrics • No guarantee there will not be any other/new metric found important 40

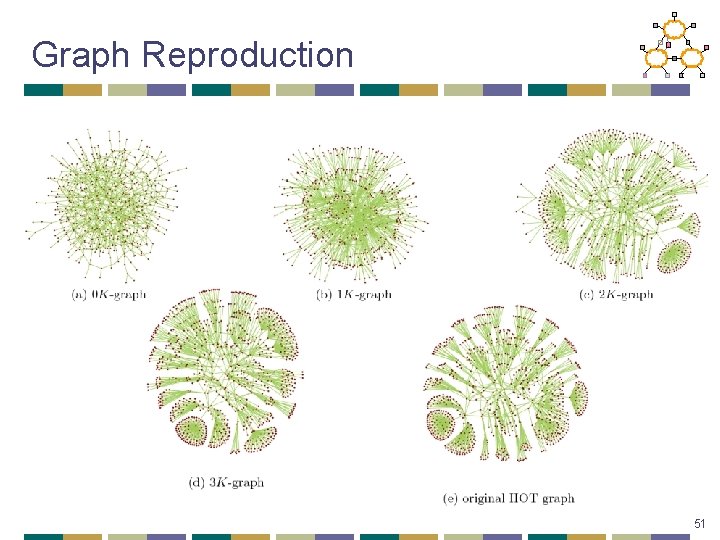
d. K-series approach • Look at inter-dependencies among topology characteristics • See if by reproducing most basic, simple, but not necessarily practically relevant characteristics, we can also reproduce (capture) all other characteristics, including practically important • Try to find the one(s) defining all others • d. K-distributions are degree correlations within simple connected graphs of size d

0 K Average degree <k>

1 K Degree distribution P(k)

2 K Joint degree distribution P(k 1, k 2)

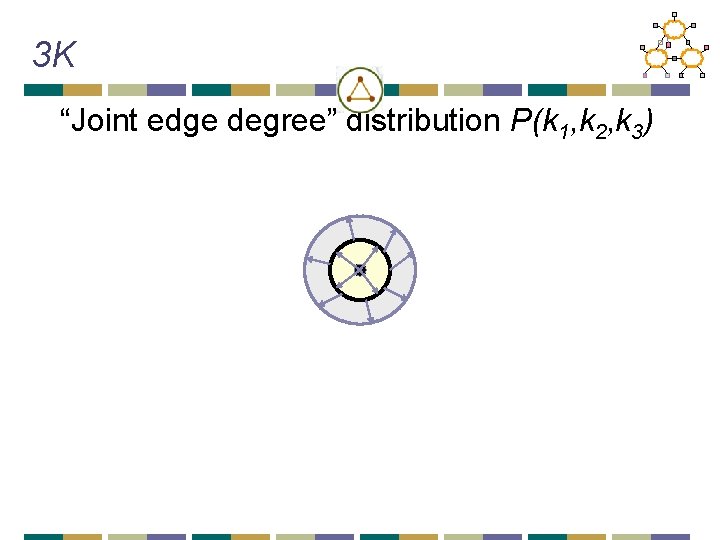
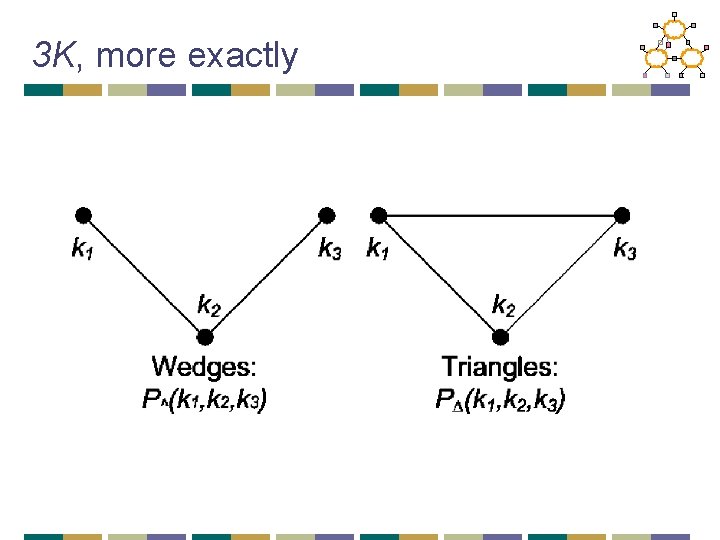
3 K “Joint edge degree” distribution P(k 1, k 2, k 3)

3 K, more exactly

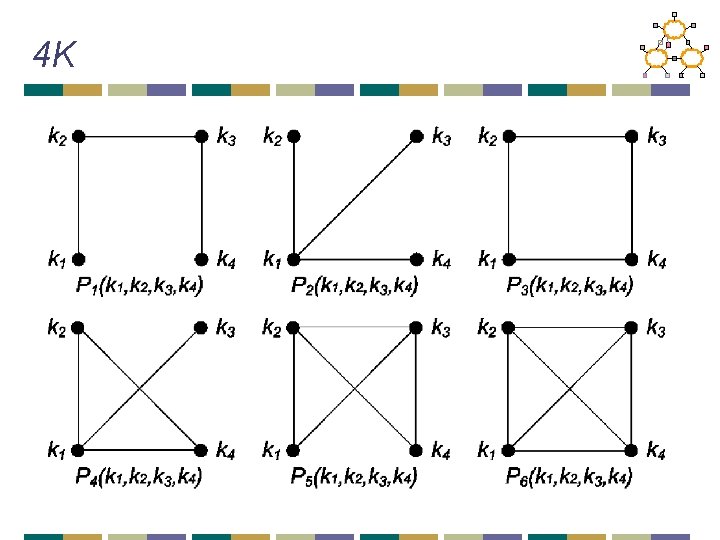
4 K

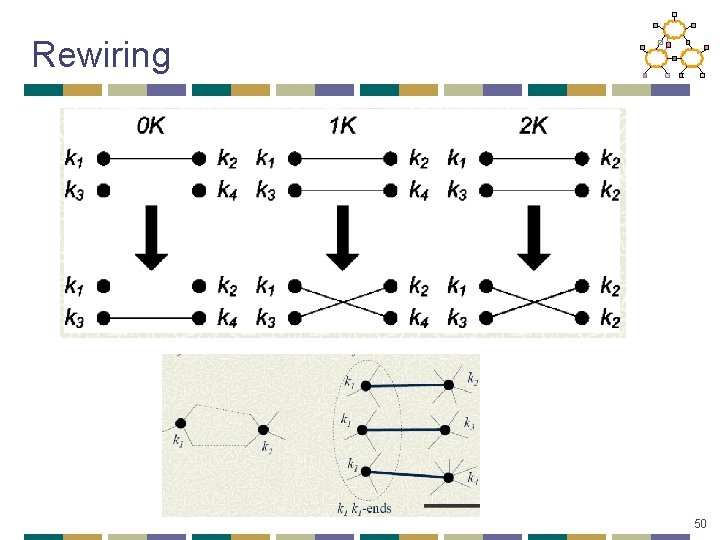
Rewiring 50

Graph Reproduction 51

The elephant in the room… • How good is the underlying data on which these studies are based? • E. g. , sampling bias traceroute of shortest paths on random graph can produce powerlaw distribution [Lakhina 03] • Similar issues with AS-level view • Router level data is very noisy 52
![Better Measurements Rocketfuel sigcomm 02 Better router alias resolution Detailed maps Better Measurements? • Rocketfuel [sigcomm 02] • Better router alias resolution • Detailed maps](https://slidetodoc.com/presentation_image/4795ee8685923d4e3472f3236e119267/image-51.jpg)
Better Measurements? • Rocketfuel [sigcomm 02] • Better router alias resolution • Detailed maps based on multiple viewpoints • Reverse traceroute [nsdi 10] • Improves ability to view peer-to-peer links • Route. Views and BGP collection efforts 53

Next Lecture • Overlay networks • Challenges in deploying new protocols • Required readings: • Active network vision and reality: lessons from a capsule-based system • Optional readings: • Resilient Overlay Networks • Future Internet Architecture: Clean-Slate Versus Evolutionary Research 54