15 744 Computer Networking L1 Intro to Computer






![Second Step: Internet[work] A collection of interconnected networks • Host: network endpoints (computer, PDA, Second Step: Internet[work] A collection of interconnected networks • Host: network endpoints (computer, PDA,](https://slidetodoc.com/presentation_image/296420d4cc304ad1a4a7192db69ca47a/image-23.jpg)







- Slides: 52

15 -744: Computer Networking L-1 Intro to Computer Networks © Srinivasan Seshan, 2001 LH-1; 1 -15 -00

Outline • Administrivia • Whirlwind tour of networking © Srinivasan Seshan, 2002 L -1; 9 -11 -02 2

Who’s Who? • Professor: Srinivasan Seshan • • TA: Amit Manjhi • • • http: //www. cs. cmu. edu/~srini@cmu. edu Office hours: Wed 1: 30 -2: 30 pm manjhi@cs. cmu. edu Office hours: Mon 3: 00 -4: 00 pm Course info • http: //www. cs. cmu. edu/~srini/15 -744/F 02/ © Srinivasan Seshan, 2002 L -1; 9 -11 -02 3

Objectives Understand the state-of-the-art in network protocols, architectures and applications • Understand how networking research is done • • • Teach the typical constraints and thought process for networked systems How is class different from undergraduate networking (15 -441) • Training network programmers vs. training network researchers © Srinivasan Seshan, 2002 L -1; 9 -11 -02 4

Web Page • • • Check regularly!! Course schedule Reading list Lecture notes Announcements Assignments Project ideas Exams Student list © Srinivasan Seshan, 2002 L -1; 9 -11 -02 5

Course Materials • Research papers • • • Links to ps or pdf on Web page Combination of classic and recent work ~40 papers Optional readings Recommended textbook • • For students not familiar with networking Peterson & Davie 2 nd edition • • 2 copies on reserve Kurose & Ross (preferably 2 nd edition) • I have some spare (1 st ed) that I can lend out © Srinivasan Seshan, 2002 L -1; 9 -11 -02 6

Grading • Homework assignments • • Problem sets & hands-on assignments (15%) Hand-ins for readings (10%) Class participation (5%) • 2 person project (30%) • Midterm exam (20%) • Final (2 nd Midterm) exam (not cumulative) (20%) • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 7

Waitlist & HW 0 – due next Thursday in class • If you are trying to add class • • • HW 0 is due on Tuesday in class I will email enrollment decisions by next Friday © Srinivasan Seshan, 2002 L -1; 9 -11 -02 8

Outline • Administrivia • Whirlwind tour of networking © Srinivasan Seshan, 2002 L -1; 9 -11 -02 9

What is the Objective of Networking? Communication between applications on different computers • Must understand application needs/demands • • • Traffic data rate Traffic pattern (bursty or constant bit rate) Traffic target (multipoint or single destination, mobile or fixed) Delay sensitivity Loss sensitivity © Srinivasan Seshan, 2002 L -1; 9 -11 -02 10

Four Steps to Networking • Communicating across a link • Connecting together multiple links (internetworking) • Finding and routing data to nodes on internetwork • Matching application requirements © Srinivasan Seshan, 2002 L -1; 9 -11 -02 11

A First Step Creating a link between nodes • Link: path followed by bits • • Wired or wireless Broadcast or point-to-point (or both) Node: any device connected to a link © Srinivasan Seshan, 2002 L -1; 9 -11 -02 12

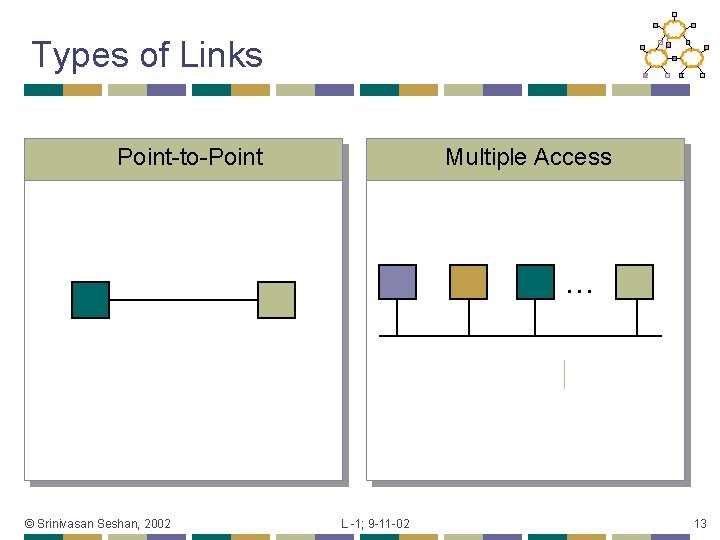
Types of Links Point-to-Point Multiple Access … © Srinivasan Seshan, 2002 L -1; 9 -11 -02 13

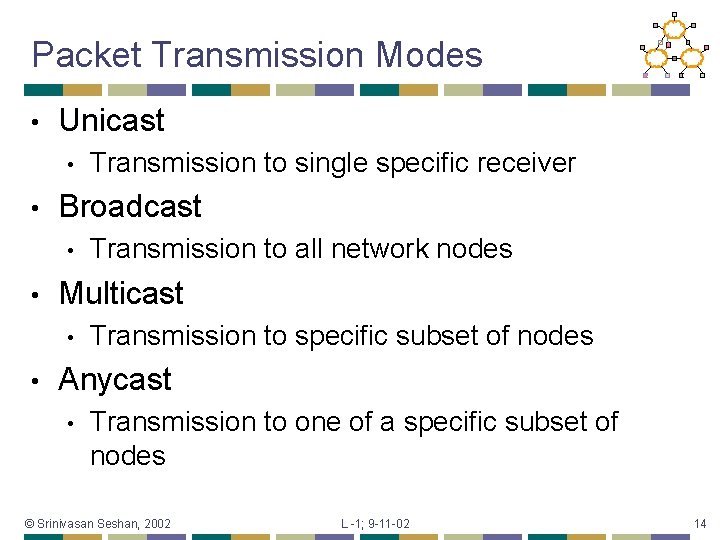
Packet Transmission Modes • Unicast • • Broadcast • • Transmission to all network nodes Multicast • • Transmission to single specific receiver Transmission to specific subset of nodes Anycast • Transmission to one of a specific subset of nodes © Srinivasan Seshan, 2002 L -1; 9 -11 -02 14

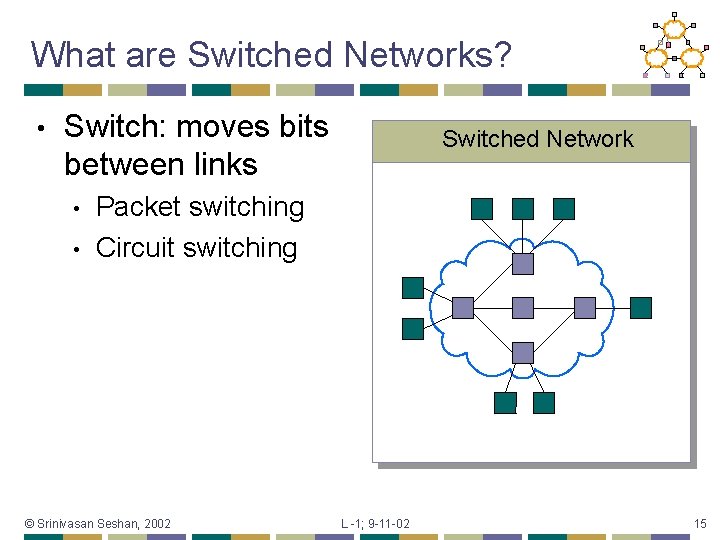
What are Switched Networks? • Switch: moves bits between links • • Switched Network Packet switching Circuit switching © Srinivasan Seshan, 2002 L -1; 9 -11 -02 15

Back in the Old Days… © Srinivasan Seshan, 2002 L -1; 9 -11 -02 16

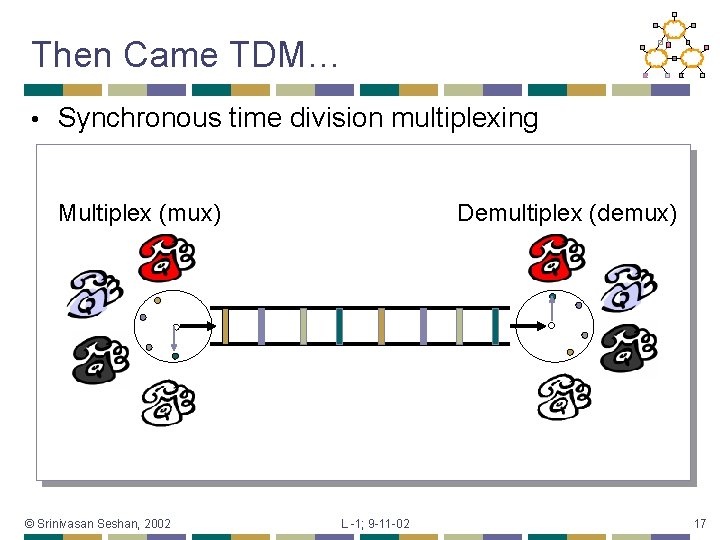
Then Came TDM… • Synchronous time division multiplexing Multiplex (mux) © Srinivasan Seshan, 2002 Demultiplex (demux) L -1; 9 -11 -02 17

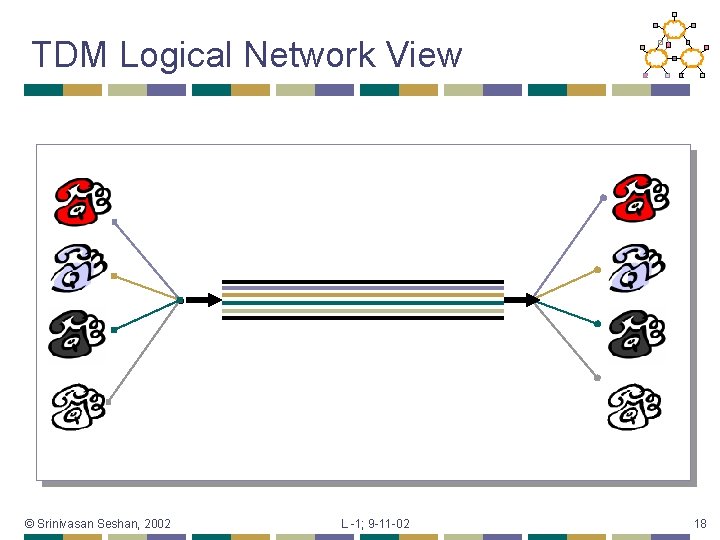
TDM Logical Network View © Srinivasan Seshan, 2002 L -1; 9 -11 -02 18

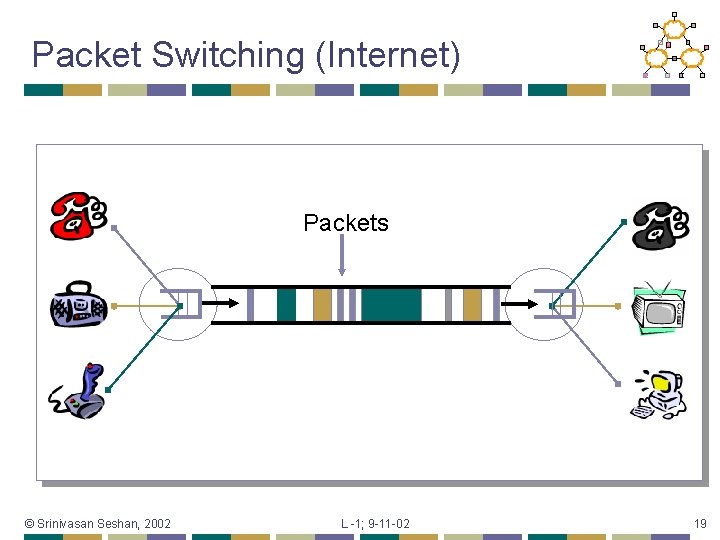
Packet Switching (Internet) Packets © Srinivasan Seshan, 2002 L -1; 9 -11 -02 19

Packet Switching Interleave packets from different sources • Efficient: resources used on demand • • • General • • Statistical multiplexing Multiple types of applications Accommodates bursty traffic • Addition of queues © Srinivasan Seshan, 2002 L -1; 9 -11 -02 20

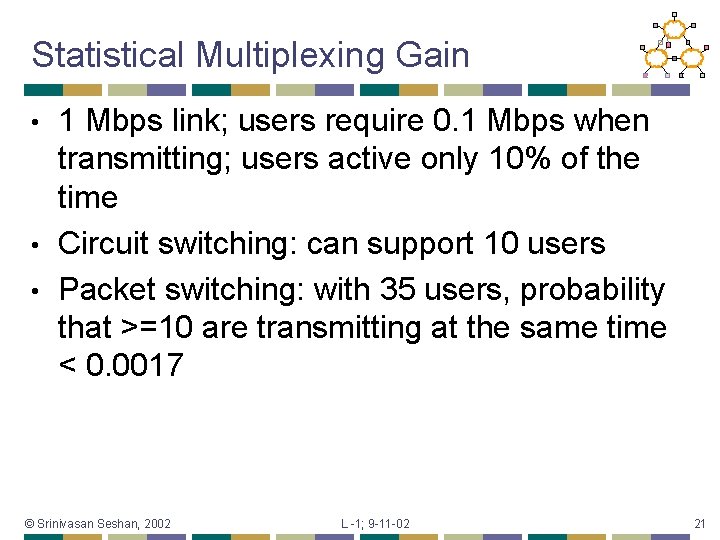
Statistical Multiplexing Gain 1 Mbps link; users require 0. 1 Mbps when transmitting; users active only 10% of the time • Circuit switching: can support 10 users • Packet switching: with 35 users, probability that >=10 are transmitting at the same time < 0. 0017 • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 21

Characteristics of Packet Switching • Store and forward • • • Packets are self contained units Can use alternate paths – reordering Contention • • Congestion Delay © Srinivasan Seshan, 2002 L -1; 9 -11 -02 22
![Second Step Internetwork A collection of interconnected networks Host network endpoints computer PDA Second Step: Internet[work] A collection of interconnected networks • Host: network endpoints (computer, PDA,](https://slidetodoc.com/presentation_image/296420d4cc304ad1a4a7192db69ca47a/image-23.jpg)
Second Step: Internet[work] A collection of interconnected networks • Host: network endpoints (computer, PDA, light switch, …) • Router: node that connects networks • Internet vs. internet • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 Internet[work] 23

Challenge • Many differences between networks • • • Address formats Performance – bandwidth/latency Packet size Loss rate/pattern/handling Routing How to translate between various network technologies © Srinivasan Seshan, 2002 L -1; 9 -11 -02 24

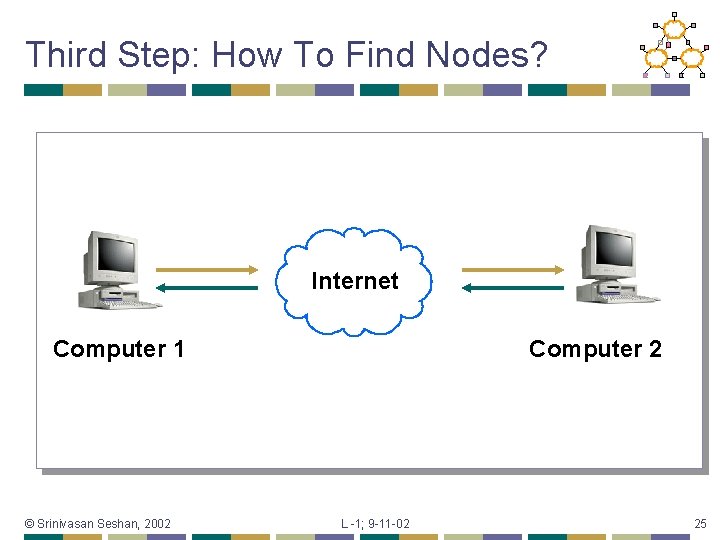
Third Step: How To Find Nodes? Internet Computer 1 © Srinivasan Seshan, 2002 Computer 2 L -1; 9 -11 -02 25

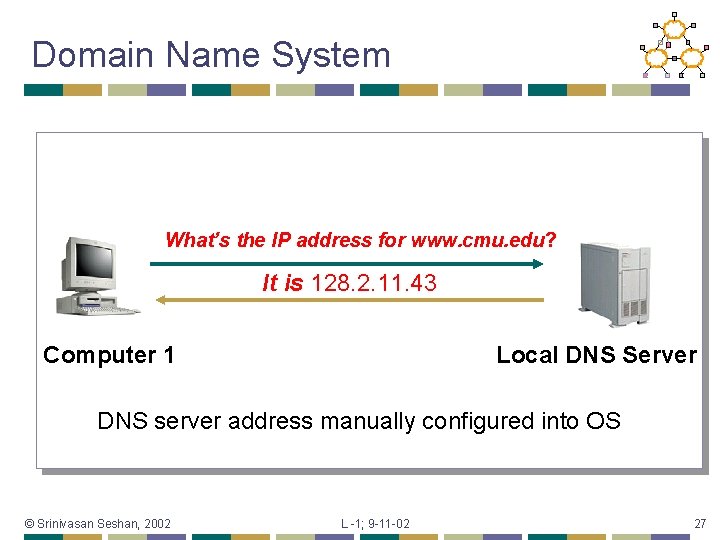
Naming • Humans use readable host names • • • E. g. www. cmu. edu Globally unique (can correspond to multiple hosts) Naming system translates to physical address • • E. g. DNS translates name to IP Address (e. g. 128. 2. 11. 43) Address reflects location in network © Srinivasan Seshan, 2002 L -1; 9 -11 -02 26

Domain Name System What’s the IP address for www. cmu. edu? It is 128. 2. 11. 43 Computer 1 Local DNS Server DNS server address manually configured into OS © Srinivasan Seshan, 2002 L -1; 9 -11 -02 27

Packet Routing/Delivery Each network technology has different local delivery methods • Address resolution provides delivery information within network • • E. g. , ARP maps IP addresses to Ethernet addresses Local, works only on a particular network Routing protocol provides path through an internetwork © Srinivasan Seshan, 2002 L -1; 9 -11 -02 28

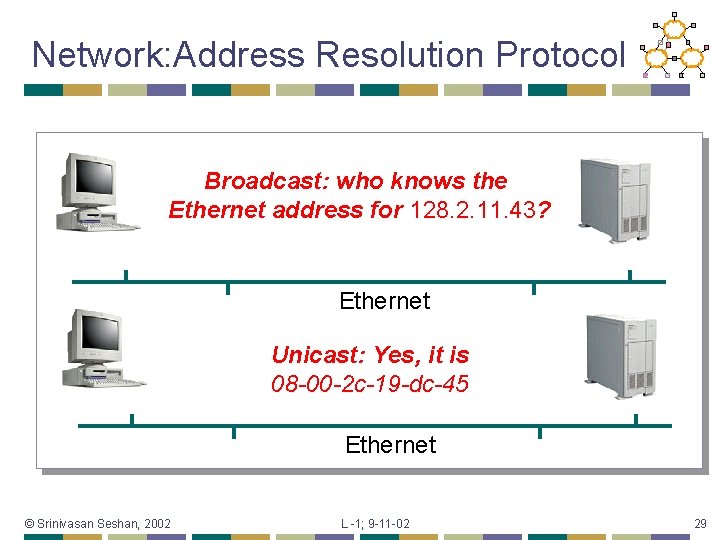
Network: Address Resolution Protocol Broadcast: who knows the Ethernet address for 128. 2. 11. 43? Ethernet Unicast: Yes, it is 08 -00 -2 c-19 -dc-45 Ethernet © Srinivasan Seshan, 2002 L -1; 9 -11 -02 29

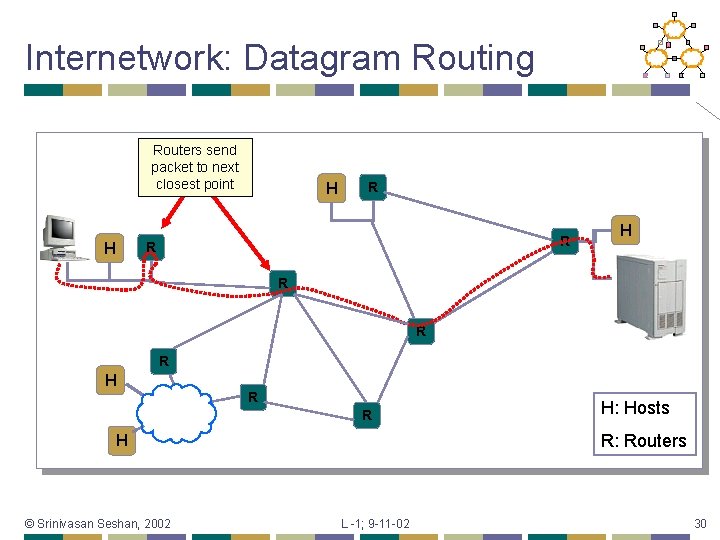
Internetwork: Datagram Routing Routers send packet to next closest point H R R R: Routers H © Srinivasan Seshan, 2002 H: Hosts L -1; 9 -11 -02 30

Routing Forwarding tables at each router populated by routing protocols. • Original Internet: manually updated • Routing protocols update tables based on “cost” • • • Exchange tables with neighbors or everyone Use neighbor leading to shortest path © Srinivasan Seshan, 2002 L -1; 9 -11 -02 31

Fourth Step: Application Demands • Reliability • • Corruption Lost packets Flow and congestion control • Fragmentation • In-order delivery • Etc… • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 32

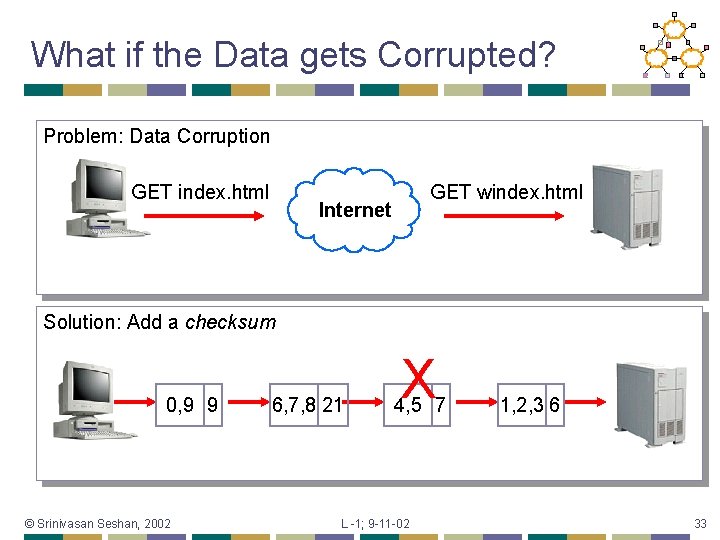
What if the Data gets Corrupted? Problem: Data Corruption GET index. html GET windex. html Internet Solution: Add a checksum 0, 9 9 © Srinivasan Seshan, 2002 6, 7, 8 21 X 4, 5 7 L -1; 9 -11 -02 1, 2, 3 6 33

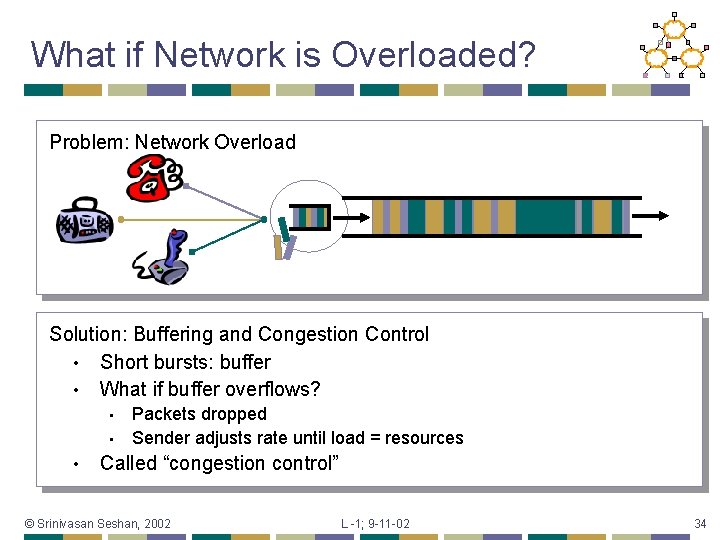
What if Network is Overloaded? Problem: Network Overload Solution: Buffering and Congestion Control • Short bursts: buffer • What if buffer overflows? • • • Packets dropped Sender adjusts rate until load = resources Called “congestion control” © Srinivasan Seshan, 2002 L -1; 9 -11 -02 34

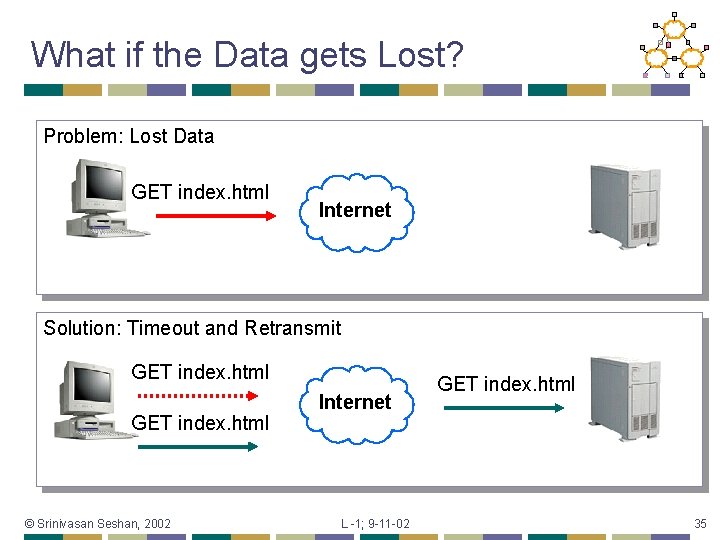
What if the Data gets Lost? Problem: Lost Data GET index. html Internet Solution: Timeout and Retransmit GET index. html © Srinivasan Seshan, 2002 Internet L -1; 9 -11 -02 GET index. html 35

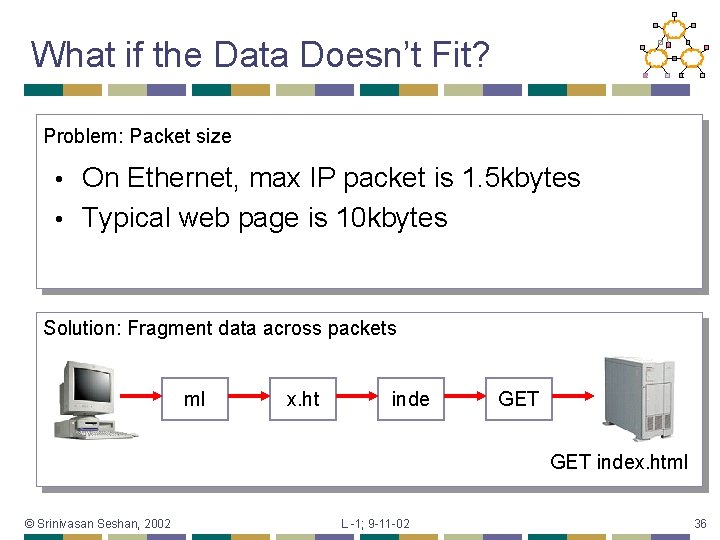
What if the Data Doesn’t Fit? Problem: Packet size On Ethernet, max IP packet is 1. 5 kbytes • Typical web page is 10 kbytes • Solution: Fragment data across packets ml x. ht inde GET index. html © Srinivasan Seshan, 2002 L -1; 9 -11 -02 36

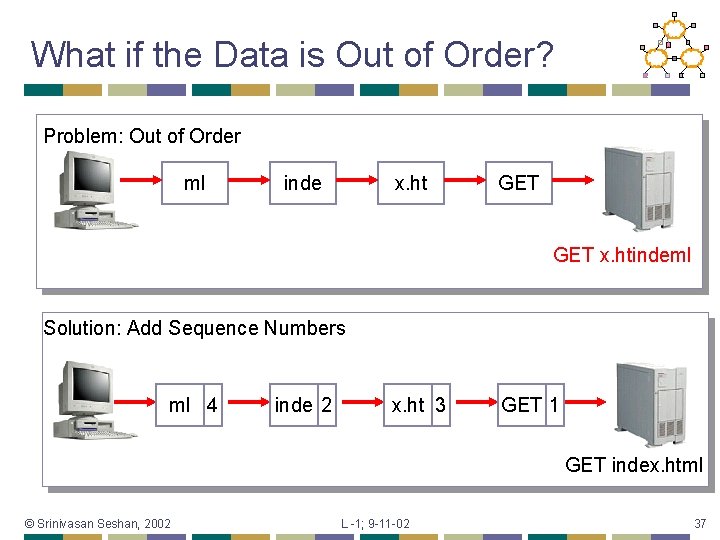
What if the Data is Out of Order? Problem: Out of Order ml inde x. ht GET x. htindeml Solution: Add Sequence Numbers ml 4 inde 2 x. ht 3 GET 1 GET index. html © Srinivasan Seshan, 2002 L -1; 9 -11 -02 37

Network Functionality Summary • • Link Multiplexing Routing Addressing/naming (locating peers) Reliability Flow control Fragmentation Etc…. © Srinivasan Seshan, 2002 L -1; 9 -11 -02 38

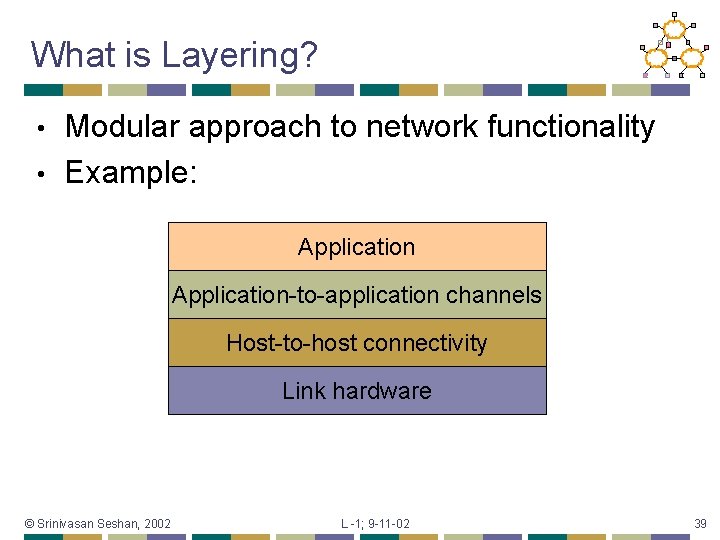
What is Layering? Modular approach to network functionality • Example: • Application-to-application channels Host-to-host connectivity Link hardware © Srinivasan Seshan, 2002 L -1; 9 -11 -02 39

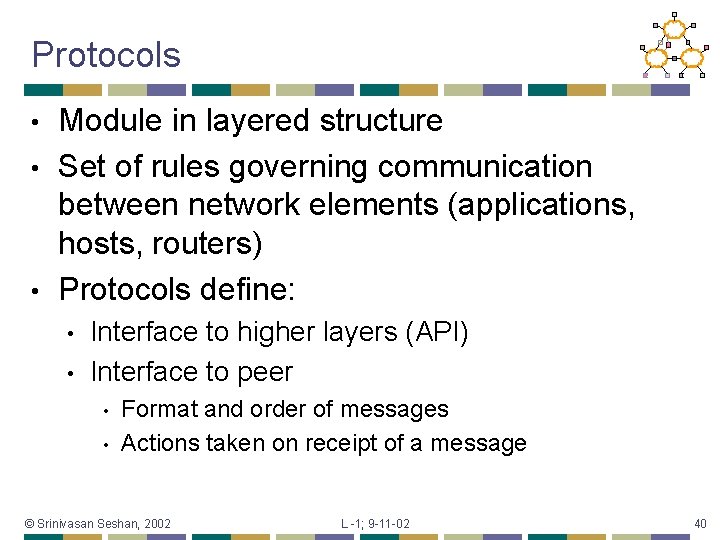
Protocols Module in layered structure • Set of rules governing communication between network elements (applications, hosts, routers) • Protocols define: • • • Interface to higher layers (API) Interface to peer • • Format and order of messages Actions taken on receipt of a message © Srinivasan Seshan, 2002 L -1; 9 -11 -02 40

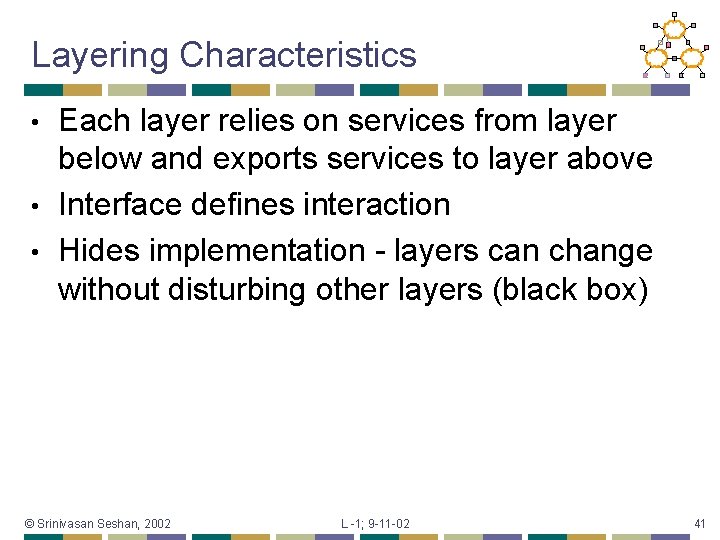
Layering Characteristics Each layer relies on services from layer below and exports services to layer above • Interface defines interaction • Hides implementation - layers can change without disturbing other layers (black box) • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 41

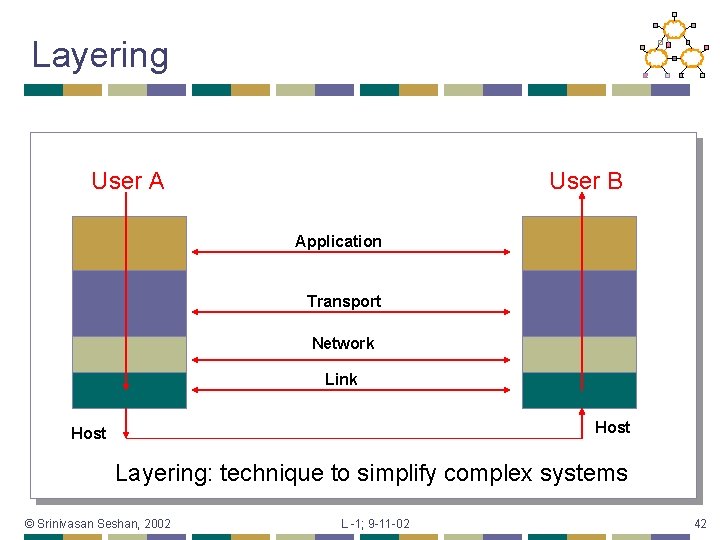
Layering User A User B Application Transport Network Link Host Layering: technique to simplify complex systems © Srinivasan Seshan, 2002 L -1; 9 -11 -02 42

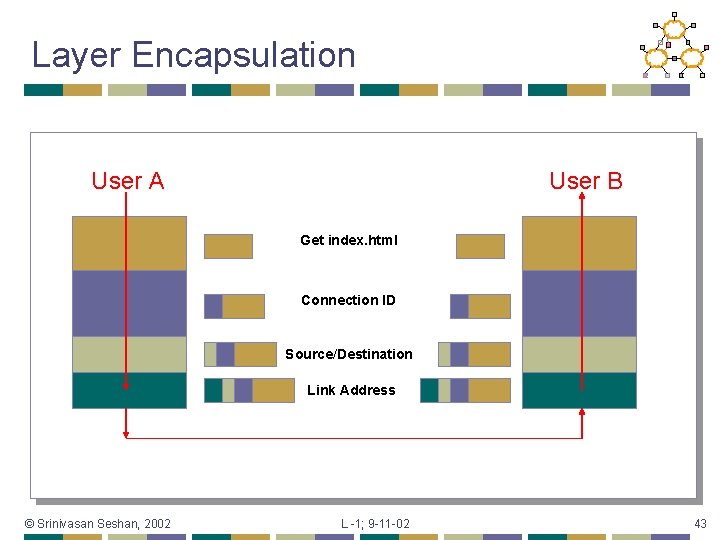
Layer Encapsulation User A User B Get index. html Connection ID Source/Destination Link Address © Srinivasan Seshan, 2002 L -1; 9 -11 -02 43

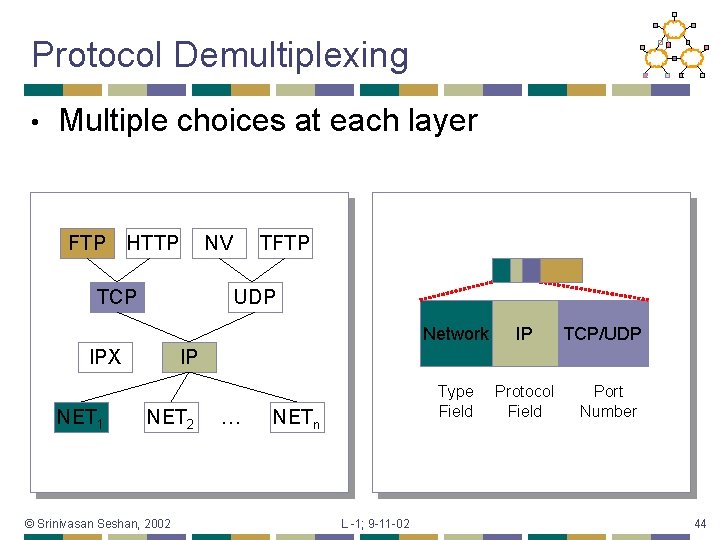
Protocol Demultiplexing • Multiple choices at each layer FTP HTTP NV TCP UDP IPX NET 1 TFTP Network IP Type Field Protocol Field TCP/UDP IP NET 2 © Srinivasan Seshan, 2002 … NETn L -1; 9 -11 -02 Port Number 44

E. g. : OSI Model: 7 Protocol Layers • • Physical: how to transmit bits Data link: how to transmit frames Network: how to route packets Transport: how to send packets end 2 end Session: how to tie flows together Presentation: byte ordering, security Application: everything else © Srinivasan Seshan, 2002 L -1; 9 -11 -02 45

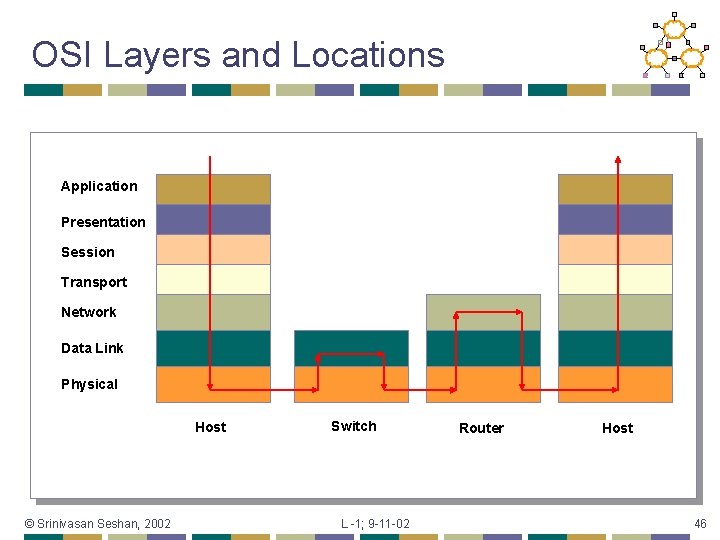
OSI Layers and Locations Application Presentation Session Transport Network Data Link Physical Host © Srinivasan Seshan, 2002 Switch L -1; 9 -11 -02 Router Host 46

Example: Transport Layer First end-to-end layer • End-to-end state • May provide reliability, flow and congestion control • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 47

Example: Network Layer Point-to-point communication • Network and host addressing • Routing • © Srinivasan Seshan, 2002 L -1; 9 -11 -02 48

Is Layering Harmful? • Sometimes. . • • • Layer N may duplicate lower level functionality (e. g. , error recovery) Layers may need same info (timestamp, MTU) Strict adherence to layering may hurt performance © Srinivasan Seshan, 2002 L -1; 9 -11 -02 49

Class Coverage • No coverage of physical and data link layer • Students expected to know this Focus on network to application layer • We will deal with: • • Protocol rules and algorithms Investigate protocol trade-offs Why this way and not another? © Srinivasan Seshan, 2002 L -1; 9 -11 -02 50

Lecture Topics • • • Traditional Layering Internet architecture Routing (IP) Transport (TCP) Queue management (FQ, RED) Naming (DNS) • • © Srinivasan Seshan, 2002 Recent Topics Multicast Mobility Active networks QOS Security Network measurement Overlay networks P 2 P applications L -1; 9 -11 -02 51

Next Lecture: Design Considerations • How to determine split of functionality • • • Across protocol layers Across network nodes Assigned Reading • • • [Cla 88] Design Philosophy of the DARPA Internet Protocols [SRC 84] End-to-end Arguments in System Design [Cla 02] Tussle in Cyberspace: Defining Tomorrow’s Internet © Srinivasan Seshan, 2002 L -1; 9 -11 -02 52