Stealth Networks Private and Secure Networking for Critical







- Slides: 10

Stealth Networks. Private and Secure Networking for Critical Assets & Infrastructure July 2014 Ed Koehler - Avaya

Why should you listen? 4 Because folks want to attack you!!! – Critical Business information – Personal and Credit data – Just for the heck of it! 4 These folks are serious and they are well equipped with sophisticated tools – It’s no longer kids looking for kicks or prestige 4 Avaya’s Fabric Connect provides for services that, when properly implemented CANNOT be attacked! 4 This creates a ‘Stealth Shield’ over the network that makes it invisible! © 2012 Avaya Inc. All rights reserved. 2

Privacy in a Virtualized World 4 Network and Service Virtualization have transformed the IT industry – Cloud Services – Software Defined Networking – BYOD and Mobility 4 Security and privacy concerns are being expressed by many risk and security analysts 4 Regulatory compliance in a virtualized environment can be a difficult bar to reach 4 Examples are, PCI Compliance, HIPAA, Process flow and control (SCADA) environments (NERC/CIP), Video Surveillance © 2012 Avaya Inc. All rights reserved. 3

What makes this so difficult? 4 Traditional networking approaches utilize IP as a utility protocol to establish service paths 4 These paths are prone to IP scanning techniques that are used to: – Discover network topology – Identify key attack vectors 4 Using traditional approaches for privacy and separation are costly and complex – Inadvertent Routed Black Holes – Poor resiliency – High Cap/Ex and Op/Ex 4 Using IP as the utility for establishing paths means that they have to be visible. This creates a ‘catch 22’ which in turn creates complexity and cost © 2012 Avaya Inc. All rights reserved. 4

Avaya’s Fabric Connect is truly Stealth! 4 Fabric Connect is not dependent upon IP to establish the service path 4 Service Paths are established by the use of SPB Ethernet Switched Paths within Fabric Connect 4 As a result, path behaviors are established on a completely different plane 4 ESP’s are ‘invisible to IP’ © 2012 Avaya Inc. All rights reserved. 5

The definition of a “Stealth” Network 4 Any network that is enclosed and self contained with no reachability into and/or out of it. It also must be mutable in both services and coverage characteristics 4 Avaya’s Fabric Connect based on IEEE 802. 1 aq provides for fast and nimble private networking circuit based capabilities that are unparalleled in the industry 4 Based on I-SID’s - NOT like MPLS IP VPN or VRF Lite! – Simple not complex 4 “Stealth” Networks are private ‘dark’ networks that are provided as services within the Fabric Connect cloud – L 2 Stealth – A non-IP addressed L 2 VSN environment – L 3 Stealth – A L 3 VSN IP VPN environment © 2012 Avaya Inc. All rights reserved. 6

Data Protection: Segmentation comes first! Dark Reading™ recommendations… 4 Security includes all people, processes and technology 4 Validation on ‘where’ Private Data exists – Trace processes and systems – Develop flow diagrams of interacting systems & Private Data 4 Develop documented penetration testing specific to the Private environment – ‘Hack Attack’ methodologies – Ongoing evaluation of threats/vulnerabilities/risk 4 The more technologies involved in the private environment the more engineering & penetration testing required! 4 Fabric Connect used end to end eliminates most if not all other network technologies! – Fabric Connect (IEEE 802. 1 aq) – Can significantly reduce ACL requirements and enhance data flow validation! – – Firewalls/IDS – are collapsed into a virtualized security demarcation perimeter Servers/Storage – resides in encrypted virtualized storage hidden by stealth services Authentication/Authorization - Identity Engines! Management applications!** Important consideration to ‘lock down’ the management environment. If it manages a system in the private environment. It is part of it! © 2012 Avaya Inc. All rights reserved. 7

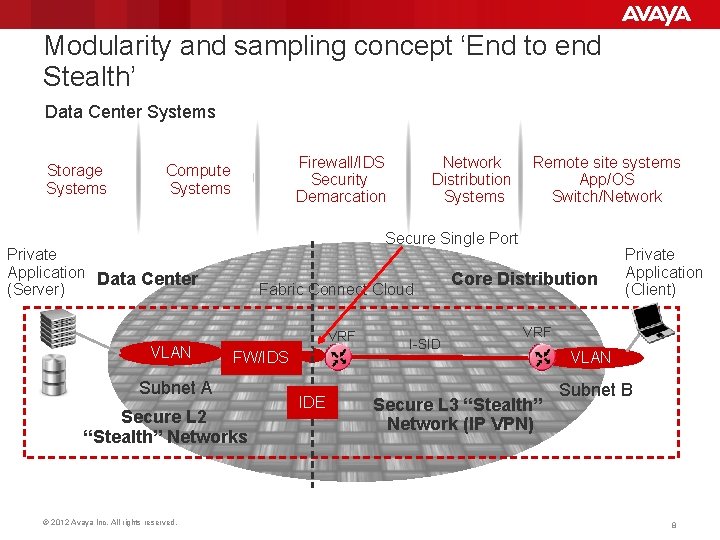
Modularity and sampling concept ‘End to end Stealth’ Data Center Systems Storage Systems Firewall/IDS Security Demarcation Compute Systems Fabric Connect Cloud VRF FW/IDS Subnet A Secure L 2 “Stealth” Networks © 2012 Avaya Inc. All rights reserved. Remote site systems App/OS Switch/Network Secure Single Port Private Application Data Center (Server) VLAN Network Distribution Systems IDE I-SID Core Distribution Private Application (Client) VRF Secure L 3 “Stealth” Network (IP VPN) VLAN Subnet B 8

In Conclusion… 4 While IP Virtual Private Networks are nothing new, Avaya takes the concept to a new level with Fabric Connect 4 Flexible and nimble service extensions lend itself to an incredibly mobile secure networking paradigm – “Stealth” Networking – Fast, nimble and invisible 4 “Stealth” Networks can be used to facilitate traditional privacy concerns such as PCI and HIPAA compliance 4 Next generation private network requirements such as mobility for emergency response, military and/or field based operations 4 Avaya’s Fabric Connect can deliver all modes of secure private connectivity – Layer 2 Stealth requirements – Layer 3 Stealth requirements – Mobile Stealth requirements © 2012 Avaya Inc. All rights reserved. 9
