13 IPV 6 and NAT Last Modified 10252021

























- Slides: 49

13: IPV 6 and NAT Last Modified: 10/25/2021 11: 02: 41 AM Adapted from Gordon Chaffee’s slides http: //bmrc. berkeley. edu/people/chaffee/advnet 98/ 4: Network Layer 4 a-1

IPv 6 4: Network Layer 4 a-2

History of IPv 6 r IETF began thinking about the problem of running out of IP addresses in 1991 r Requires changing IP packet format - HUGE deal! r While we’re at it, lets change X too r “NGTrans” (IPv 6 Transition) Working Group of IETF - June 1996 4: Network Layer 4 a-3

IPv 6 Wish List r From “The Case for IPv 6” r Scalable Addressing and Routing r Support for Real Time Services r Support of Autoconfiguration (get your own IP address and domain name to minimize administration r Security Support r Enhanced support for routing to mobile hosts 4: Network Layer 4 a-4

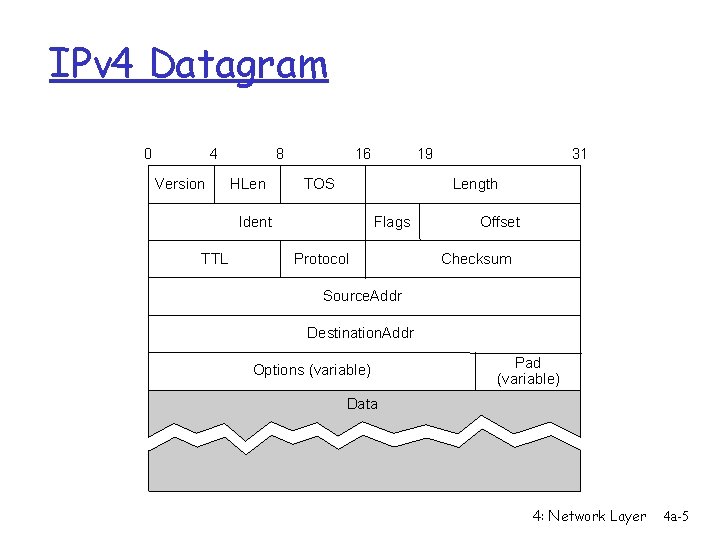
IPv 4 Datagram 0 4 Version 8 HLen 16 TOS 31 Length Ident TTL 19 Flags Protocol Offset Checksum Source. Addr Destination. Addr Options (variable) Pad (variable) Data 4: Network Layer 4 a-5

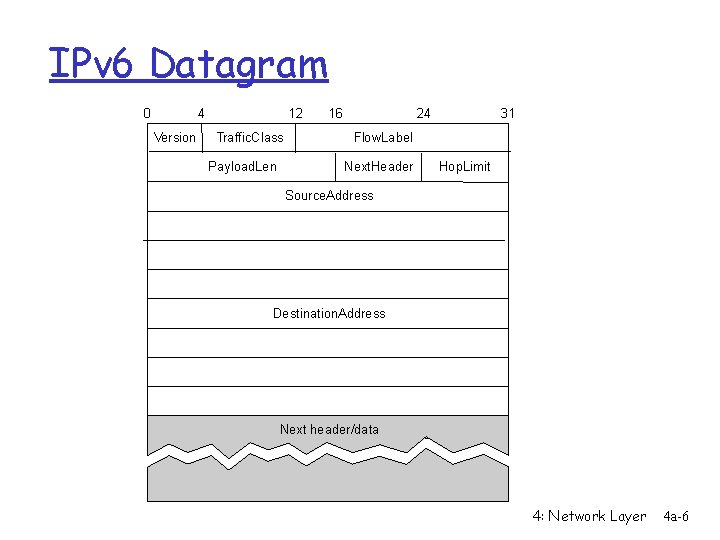
IPv 6 Datagram 0 4 Version 12 Traffic. Class Payload. Len 16 24 31 Flow. Label Next. Header Hop. Limit Source. Address Destination. Address Next header/data 4: Network Layer 4 a-6

IPv 6 Base Header Format r VERS = IPv 6 r TRAFFIC CLASS: specifies the routing priority or r r Qo. S requests FLOW LABEL: to be used by applications requesting performance guarantees PAYLOAD LENGTH: like IPv 4’s datagram length, but doesn’t include the header length like IPv 4 NEXT HEADER: indicates the type of the next object in the datagram either type of extension header or type of data HOP LIMIT: like IPv 4’s Time. To. Live field but named correctly NO CHECKSUM (processing efficiency) 4: Network Layer 4 a-7

Address Space r 32 bits versus 128 bits - implications? m 4 billiion vesus 3. 4 X 1038 m 1500 addresses per square foot of the earth surface 4: Network Layer 4 a-8

Addresses r Still divide address into prefix that designates network and suffix that designates host r But no set classes, boundary between suffix and prefix can fall anywhere (CIDR only) r Prefix length associated with each address 4: Network Layer 4 a-9

Addresses Types r Unicast: delivered to a single computer r Multicast: delivered to each of a set of computers (can be anywhere) m Conferencing, subscribing to a broadcast r Anycast: delivered to one of a set of computers that share a common prefix m Deliver to one of a set of machines providing a common servicer 4: Network Layer 4 a-10

Address Notation r Dotted sixteen? m 105. 67. 45. 56. 23. 6. 133. 211. 45. 8. 0. 7. 56. 45. 3. 189. 56 r Colon hexadecimal notation (8 groups) m 69 DC: 8768: 9 A 56: FFFF: 0: 5634: 343 r Or even better with zero compression (replace run of all 0 s with double : : ) r Makes host names look even more attractive huh? 4: Network Layer 4 a-11

Special addresses r Ipv 4 addresses all reserved for compatibility m 96 zeros + IPv 4 address = valid IPv 6 address r Local Use Addresses m Special prefix which means “this needn’t be globally unique” m Allow just to be used locally m Aids in autoconfiguration 4: Network Layer 4 a-12

Datagram Format r Base Header + 0 to N Extension Headers + Data Area 4: Network Layer 4 a-13

Extensible Headers r Why? r Saves Space and Processing Time m Only have to allocate space for and spend time processing headers implementing features you need r Extensibility m When add new feature just add an extension header type - no change to existing headers m For experimental features, only sender and receiver need to understand new header 4: Network Layer 4 a-14

Flow Label r Virtual circuit like behaviour over a datagram network r A sender can request the underlying network to establish a path with certain requirements • Traffic class specifies the general requirements (ex. Delay < 100 msec. ) r If the path can be established, the network returns an identifier that the sender places along with the traffic class in the flow label r Routers use this identifier to route the datagram along the prearranged path 4: Network Layer 4 a-15

ICMPv 6 r New version of ICMP r Additional message types, like “Packet Too Big” r Multicast group management functions 4: Network Layer 4 a-16

Summary like IPv 4 r Connectionless (each datagram contains destination address and is routed seperately) r Best Effort (possibility for virtual circuit behaviour) r Maximum hops field so can avoid datagrams circulating indefinitely 4: Network Layer 4 a-17

Summary New Features r Bigger Address Space (128 bits/address) m CIDR only m Any cast addresses r New Header Format to help speed processing and forwarding m m Checksum: removed entirely to reduce processing time at each hop No fragmentation r Simple Base Header + Extension Headers m Options: allowed, but outside of header, indicated by “Next Header” field r Ability to influence the path a datagram will take through the network (Quality of service) 4: Network Layer 4 a-18

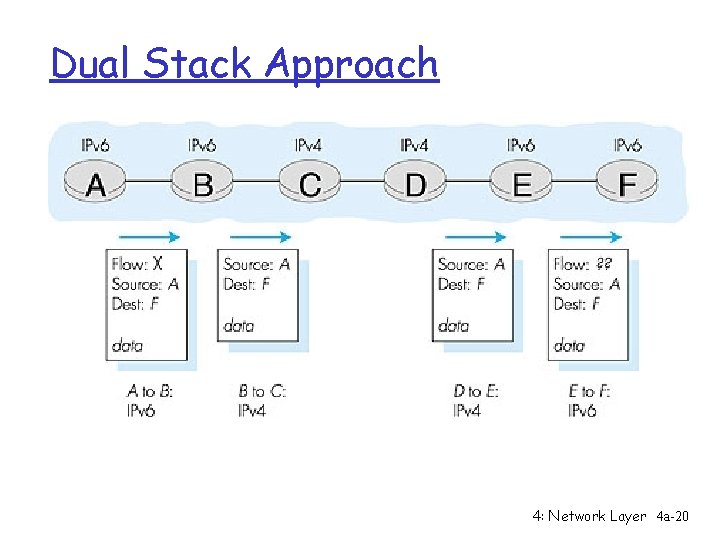
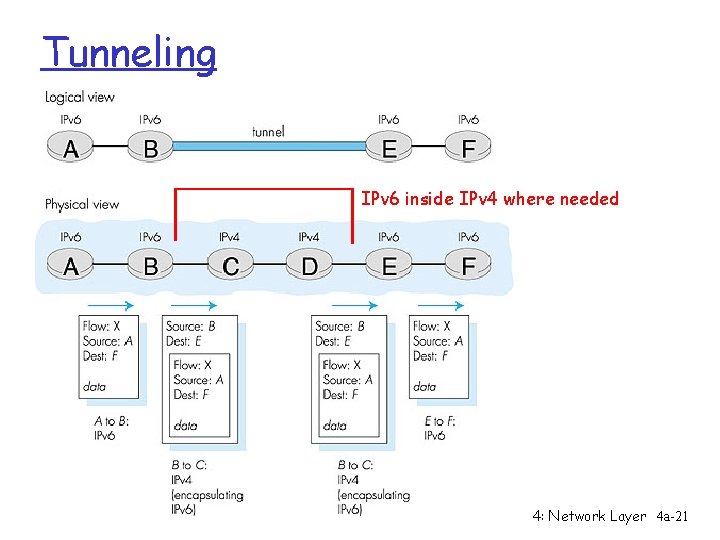
Transition From IPv 4 To IPv 6 r Not all routers can be upgraded simultaneous m no “flag days” m How will the network operate with mixed IPv 4 and IPv 6 routers? r Two proposed approaches: m Dual Stack: some routers with dual stack (v 6, v 4) can “translate” between formats m Tunneling: IPv 6 carried as payload n IPv 4 datagram among IPv 4 routers 4: Network Layer 4 a-19

Dual Stack Approach 4: Network Layer 4 a-20

Tunneling IPv 6 inside IPv 4 where needed 4: Network Layer 4 a-21

History r First blocks of IPv 6 addresses delegated to regional registries - July 1999 r ~2000 - 10 websites in the. com domain that can be reached via an IPv 6 enhanced client via an IPv 6 TCP connection r 2008 - U. S. government agencies required to be IPv 6 compliant to meet an OMB mandate announced in 2005 r 2009/10 – Major websites like Google and Facebook on IPv 6 r Info from Akamai’s State of the Internet 4: Network Layer 4 a-22 report

IPv 5? r New version of IP temporarily named “IP - The Next Generation” or IPng r Many competing proposals; name Ipng became ambiguous r Once specific protocol designed needed a name to distinguish it from other proposals r IPv 5 has been assigned to an experimental protocol ST 4: Network Layer 4 a-23

Network Address Translation (NAT) 4: Network Layer 4 a-24

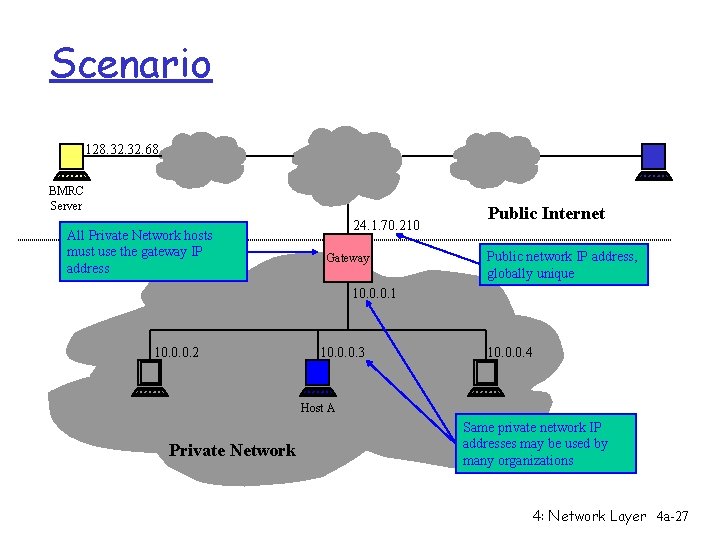
Background r RFC 1918 defines private intranet address ranges for IPv 4 m 10. 0 - 10. 255 (Class A) m 172. 16. 0. 0 - 172. 31. 255 (Class B) m 192. 168. 0. 0 - 192. 168. 255 (Class C) r Addresses reused by many organizations r Addresses cannot be used for communication on Internet 4: Network Layer 4 a-25

Problem Discussion r Hosts on private IP networks need to access public Internet r All traffic travels through a gateway to/from public Internet r Traffic needs to use IP address of gateway r Conserves IPv 4 address space m Private IP addresses mapped into fewer public IP addresses 4: Network Layer 4 a-26

Scenario 128. 32. 68 BMRC Server All Private Network hosts must use the gateway IP address 24. 1. 70. 210 Gateway Public Internet Public network IP address, globally unique 10. 0. 0. 1 10. 0. 0. 2 10. 0. 0. 3 10. 0. 0. 4 Host A Private Network Same private network IP addresses may be used by many organizations 4: Network Layer 4 a-27

Network Address Translation Solution r Special function on gateway m IP source and destination addresses are translated m Internal hosts need no changes r TCP based protocols work well r Non-TCP based protocols more difficult r Changes required to applications that embed IP addresses? FTP? Others? r Provides some security m m Hosts behind gateway difficult to reach Possibly vulnerable to IP level attacks 4: Network Layer 4 a-28

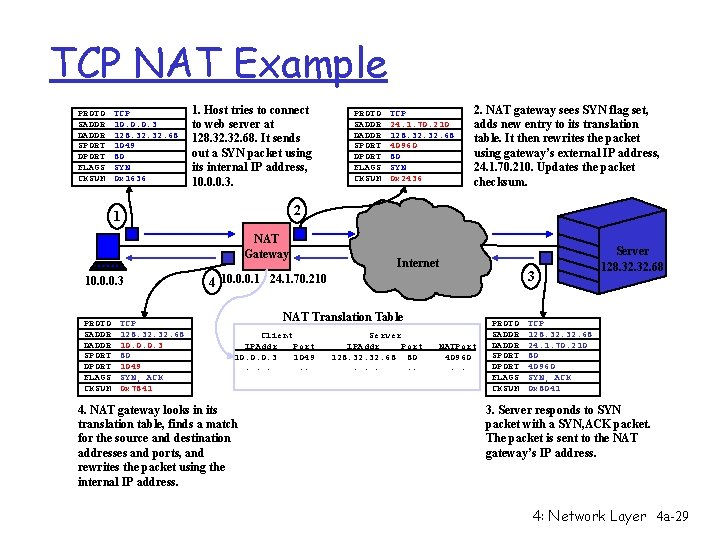
TCP NAT Example PROTO SADDR DADDR SPORT DPORT FLAGS CKSUM TCP 10. 0. 0. 3 128. 32. 68 1049 80 SYN 0 x 1636 1. Host tries to connect to web server at 128. 32. 68. It sends out a SYN packet using its internal IP address, 10. 0. 0. 3. NAT Gateway PROTO SADDR DADDR SPORT DPORT FLAGS CKSUM TCP 128. 32. 68 10. 0. 0. 3 80 1049 SYN, ACK 0 x 7841 TCP 24. 1. 70. 210 128. 32. 68 40960 80 SYN 0 x 2436 2. NAT gateway sees SYN flag set, adds new entry to its translation table. It then rewrites the packet using gateway’s external IP address, 24. 1. 70. 210. Updates the packet checksum. 2 1 10. 0. 0. 3 PROTO SADDR DADDR SPORT DPORT FLAGS CKSUM Internet 3 4 10. 0. 0. 1 24. 1. 70. 210 NAT Translation Table Client IPAddr Port 10. 0. 0. 3 1049. . . 4. NAT gateway looks in its translation table, finds a match for the source and destination addresses and ports, and rewrites the packet using the internal IP address. Server IPAddr Port 128. 32. 68 80. . . NATPort 40960. . PROTO SADDR DADDR SPORT DPORT FLAGS CKSUM Server 128. 32. 68 TCP 128. 32. 68 24. 1. 70. 210 80 40960 SYN, ACK 0 x 8041 3. Server responds to SYN packet with a SYN, ACK packet. The packet is sent to the NAT gateway’s IP address. 4: Network Layer 4 a-29

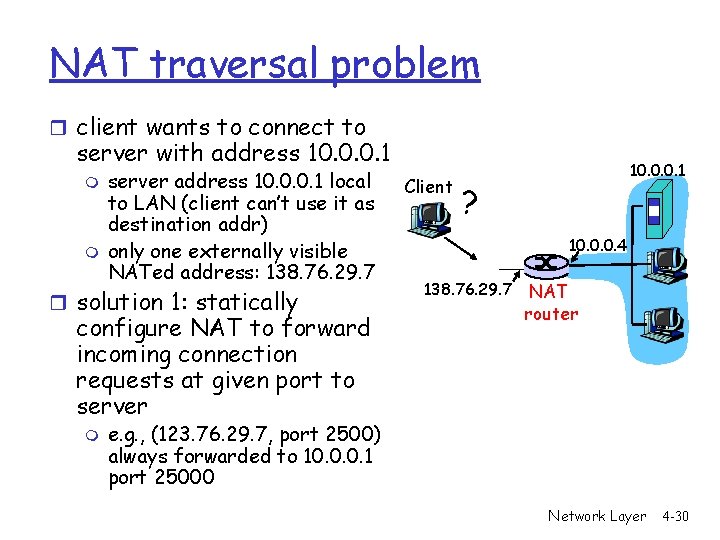
NAT traversal problem r client wants to connect to server with address 10. 0. 0. 1 m m server address 10. 0. 0. 1 local to LAN (client can’t use it as destination addr) only one externally visible NATed address: 138. 76. 29. 7 r solution 1: statically configure NAT to forward incoming connection requests at given port to server m Client 10. 0. 0. 1 ? 10. 0. 0. 4 138. 76. 29. 7 NAT router e. g. , (123. 76. 29. 7, port 2500) always forwarded to 10. 0. 0. 1 port 25000 Network Layer 4 -30

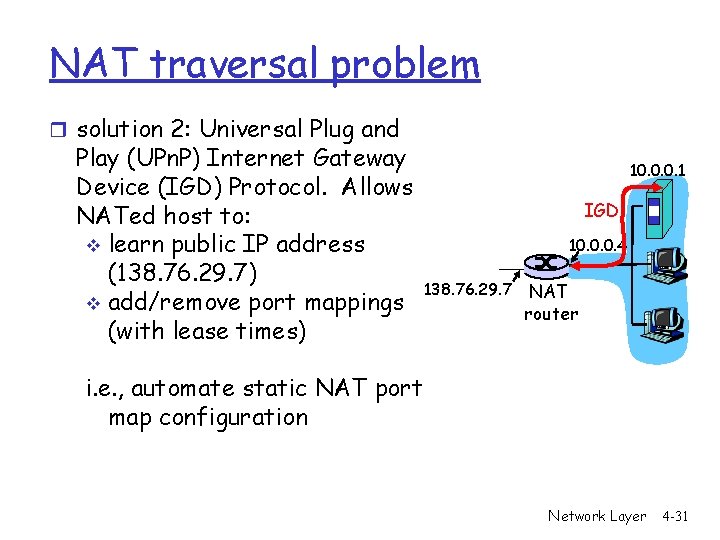
NAT traversal problem r solution 2: Universal Plug and Play (UPn. P) Internet Gateway Device (IGD) Protocol. Allows NATed host to: v learn public IP address (138. 76. 29. 7) v add/remove port mappings (with lease times) 10. 0. 0. 1 IGD 10. 0. 0. 4 138. 76. 29. 7 NAT router i. e. , automate static NAT port map configuration Network Layer 4 -31

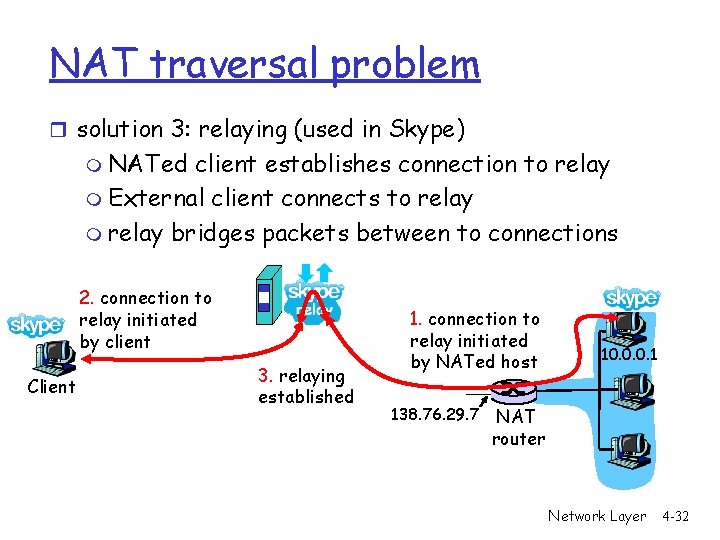
NAT traversal problem r solution 3: relaying (used in Skype) m NATed client establishes connection to relay m External client connects to relay m relay bridges packets between to connections 2. connection to relay initiated by client Client 3. relaying established 1. connection to relay initiated by NATed host 138. 76. 29. 7 10. 0. 0. 1 NAT router Network Layer 4 -32

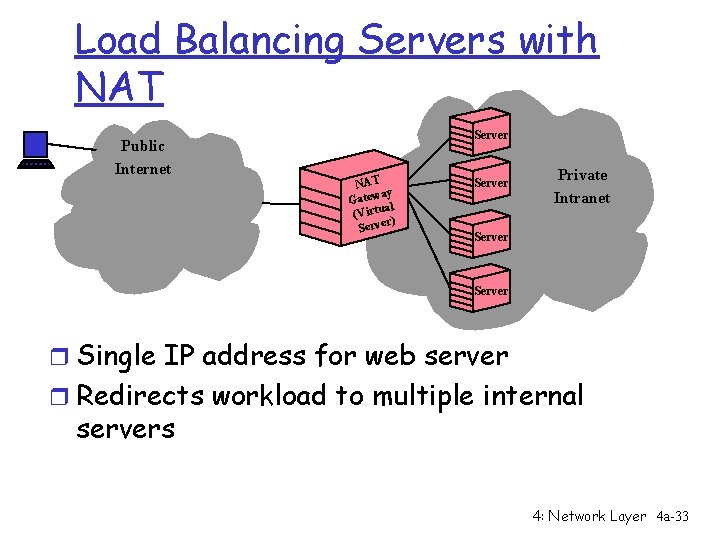
Load Balancing Servers with NAT Public Internet Server NAT ay Gatew l a (Virtu r) Server Private Intranet Server r Single IP address for web server r Redirects workload to multiple internal servers 4: Network Layer 4 a-33

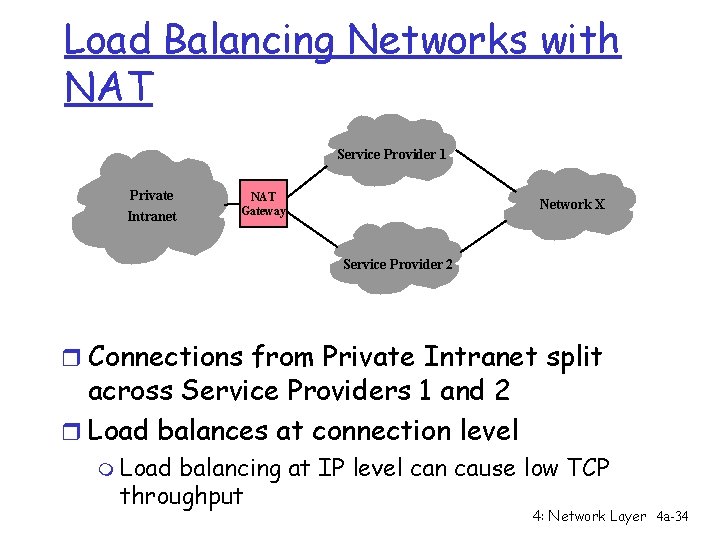
Load Balancing Networks with NAT Service Provider 1 Private Intranet NAT Gateway Network X Service Provider 2 r Connections from Private Intranet split across Service Providers 1 and 2 r Load balances at connection level m Load balancing at IP level can cause low TCP throughput 4: Network Layer 4 a-34

NAT Discussion r NAT works best with TCP connections r NAT breaks End-to-End Principle by modifying packets r Problems m Connectionless UDP (Real Audio) m ICMP (Ping) m Multicast m Applications use IP addresses within data stream (FTP) r Need to watch/modify data packets 4: Network Layer 4 a-35

IP addresses: how to get one? One more time r Hard-coded by system admin in a file m Long with subnet mask, default gateway and DNS server r DHCP: Dynamic Host Configuration Protocol: dynamically get network identity and neighborhood info dynamically, “plug-and-play” 4: Network Layer 4 a-36

DHCP r Automated configuration of IP addresses r DHCP server hands out IP addresses to hosts in a administrative domain r Relieves burdens of system administrators - major factor in lifetime cost of computer systems! r Runs over UDP (ports 67 and 68) r RFC 2131 4: Network Layer 4 a-37

Finding the DHCP server? r Wouldn’t be big improvement if had to configure each host with address of DHCP server! m. A little better because at least every machine in a local network gets same info r Hosts send special DHCPDISCOVER message to the special IP address 255 m This is a special IP broadcast address and all other nodes on that network will receive m We’ll see more about special addresses like this 4: Network Layer 4 a-38

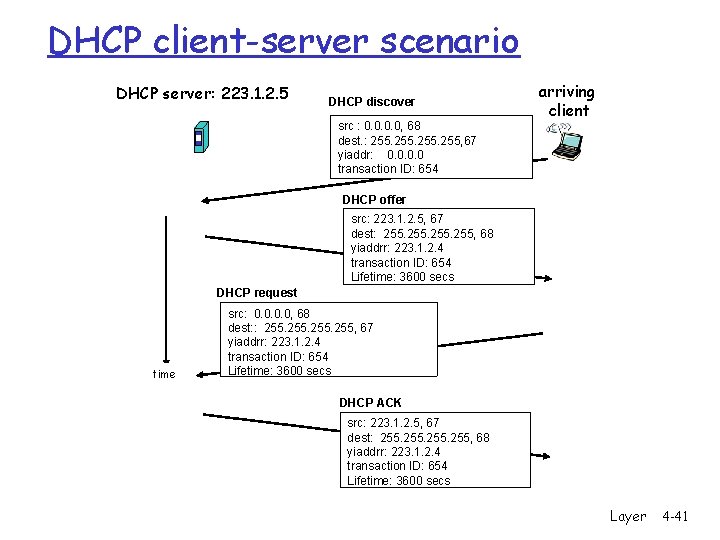
DHCP Discover/Offer r Host broadcasts “DHCP discover” msg m Sent to 255 from 0. 0 m Contains a client ID to uniquely identify the client in that network m Usually use MAC address m DHCP server can be configured with a “registered list” of MAC addresses to accept r DHCP server responds with “DHCP offer” msg m Sent from IP address of DHCP server to 255 m Includes ip address, subnet mask, DNS servers, default gateway, length of lease 4: Network Layer 4 a-39

DHCP Request/Ack r Host sends “DHCP request” msg directly to server m Sent to DHCP Server’s IP address m Requests the address and other info offered with DHCP offer or could be requesting the address it was offered last time ( ie before it expires) m Still sent from 0. 0 r DHCP server responds with “DHCP ack” msg m Sent from IP address of DHCP server to 255 m Final confirmation of the ip address, subnet mask, DNS servers, default gateway, length of lease 4: Network Layer 4 a-40

DHCP client-server scenario DHCP server: 223. 1. 2. 5 DHCP discover src : 0. 0, 68 dest. : 255, 67 yiaddr: 0. 0 transaction ID: 654 arriving client DHCP offer src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs DHCP request time src: 0. 0, 68 dest: : 255, 67 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs DHCP ACK src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs Network Layer 4 -41

DHCP server on every network? r If there is a DHCP server on the local network to receive the broadcast, then it can respond the host with its IP address, its default router, etc. r Alternatively, can have a DHCP relay agent on each network that knows the address of the DHCP server and will forward the DHCPDISCOVER message 4: Network Layer 4 a-42

Leases r DHCP doesn’t *give* each client an IP address, just lease them for a while m IP addresses aren’t reserved by clients not currently connected to the network r Clients can keep their address by renewing their leases m m Some DHCP servers will hand out new address each time (especially to prevent customers running servers) Dynamic DNS? r Clients typically start renewing ½ way through lease period r Internet wide DHCP to enforce efficient CIDR? 4: Network Layer 4 a-43

Renew lease r Host requests IP address: “DHCP request” msg m Once know the IP address of the DHCP server then just send a request message directly to them r DHCP server sends address: “DHCP ack” msg m Contains same info as an offer 4: Network Layer 4 a-44

DHCP other r DHCP servers and DNS r DHCP servers and routers m What if some machine choose their own IP address in the proper range? Doesn’t stop data from flowing to them (see ARP later) m Unless routers or switches keep list of valid MACs r DHCP and BOOTP r Security problem – attach to network and act like DHCP server – give out all duplicate IPs 4: Network Layer 4 a-45

Outtakes 4: Network Layer 4 a-46

6 Bone r The 6 Bone: an IPv 6 testbed r Started as a virtual network using IPv 6 over IPv 4 tunneling/encapsulation r Slowly migrated to native links for IPv 6 transport r RFC 2471 r Abandoned 2006 4: Network Layer 4 a-47

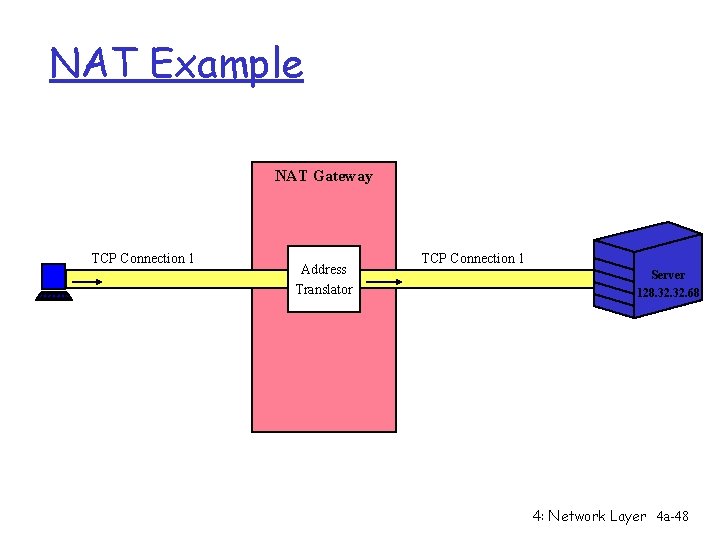
NAT Example NAT Gateway TCP Connection 1 Address Translator TCP Connection 1 Server 128. 32. 68 4: Network Layer 4 a-48

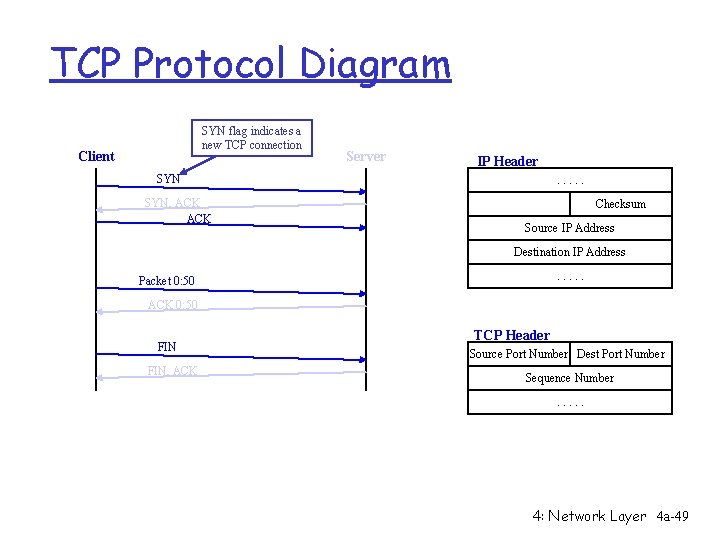
TCP Protocol Diagram SYN flag indicates a new TCP connection Client Server IP Header SYN, ACK . . . Checksum Source IP Address Destination IP Address. . . Packet 0: 50 ACK 0: 50 FIN, ACK TCP Header Source Port Number Dest Port Number Sequence Number. . . 4: Network Layer 4 a-49