Anonymizing IPv 6 in PCAPs Challenges and Wins













- Slides: 18

Anonymizing IPv 6 in PCAPs Challenges and Wins Jasper Bongertz Troopers IPv 6 Security Summit 2016

Sanitization in General � Goal: �remove critical stuff �but: keep enough info to stay useful � The original-to-sanitized ratio may vary based on share goal @packetjay

Why PCAP sanitization? � Similar to editing packets for packet replay � Removing sensitive details �User Credentials �Network topology (IP addresses etc. ) �Device & software version information �Vulnerable protocols �Payloads @packetjay

Often, people do this… @packetjay

Sanitization Goal: Analysis � Network analysts �often require to keep packet content only up to the TCP layer �look at packet loss, timings, TCP being messed up by obscure middle boxes �sometimes need higher layer details like FQDNs or URLs @packetjay

Sanitization Goals: Malware � Security Analysts/Researchers �usually don't care that much about Ethernet / ARP / IPv 4 / TCP / UDP headers �Need to keep the malware / exploit delivery process intact: FQDNs, URLs, binary payloads @packetjay

Selected Tools – Manual Editing � Hex Editors � Wireshark Edit Feature �only in GTK at this time � Wire. Edit �can do bulk search/replace @packetjay If you choose manual editing, better be stuck in a time loop to get things done. . .

General Challenges � Balance between removing details and remaining usefulness � One packet vs. many � Protocol complexity � Procotol dependencies � Defensive Transformation @packetjay

Selected Tools – Batch Edit � bittwiste, tcprewrite � pktanon �http: //www. tm. uka. de/software/pktanon/ � pcaplib �http: //sourceforge. net/projects/pcaplib/ � Trace. Wrangler �https: //www. tracewrangler. com @packetjay

How to sanitize correctly � Parse/Dissect all packet layers �from layer 2 up � Sanitize extracted values � Rebuild the packet layer by layer using sanitized values only! �from the top layer down @packetjay

33 00 5 a 00 00 00 33 00 ff 01 00 10 ff 00 fe ff 00 5 a 02 20 aa 02 00 aa 6 e 3 a 20 6 e 00 20 a 5 ff a 2 a 5 00 a 2 00 fe ff 87 02 10 80 02 00 60 5 a 00 00 0 f 97 aa 00 00 35 ff 20 00 00 00 fe a 2 00 00 00 02 86 00 00 00 6 e Ethernet Details parsed: Destination MAC: Source MAC: Ether. Type: @packetjay 33 33 ff 02 6 e a 5 00 10 5 a aa 20 a 2 86 dd dd 00 00 00 a 5 60 02 00 fe 01 00 10 00 80 01

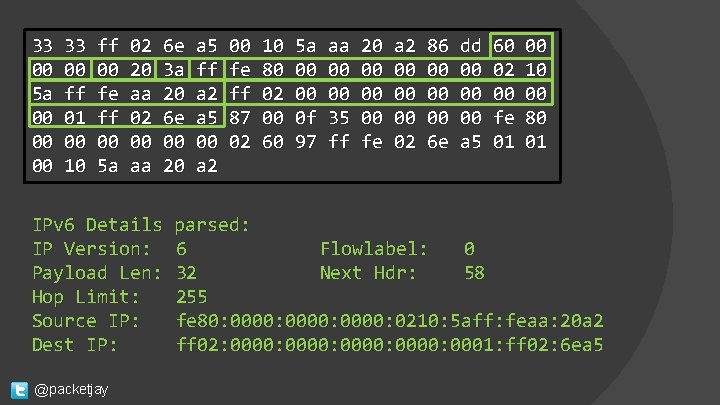
33 00 5 a 00 00 00 33 00 ff 01 00 10 ff 00 fe ff 00 5 a 02 20 aa 02 00 aa 6 e 3 a 20 6 e 00 20 IPv 6 Details IP Version: Payload Len: Hop Limit: Source IP: Dest IP: @packetjay a 5 ff a 2 a 5 00 a 2 00 fe ff 87 02 10 80 02 00 60 5 a 00 00 0 f 97 aa 00 00 35 ff 20 00 00 00 fe a 2 00 00 00 02 86 00 00 00 6 e dd 00 00 00 a 5 60 02 00 fe 01 00 10 00 80 01 parsed: 6 Flowlabel: 0 32 Next Hdr: 58 255 fe 80: 0000: 0210: 5 aff: feaa: 20 a 2 ff 02: 0000: 0001: ff 02: 6 ea 5

The IPv 6 Prefix Win � With IPv 4, subnets are a problem �can‘t tell from a PCAP what the masks are �is 192. 168. 1. 1 in the same subnet as 192. 168. 20? � Prefix for IPv 6 makes it much easier: �same original prefix, same replacement prefix @packetjay

IP Address Replacement � Some possible rules: �black marker (zero out all bytes) �Full IP address randomization (prefix + ID) �original: replacement preset �Prefix aware replacement ○ randomize Interface ID ○ keep Interface ID @packetjay

IP Replacement Challenges � Handling special IP addresses �All Zero �Loopback �Multicast � Documentation IPs � Mapping different original IPs to same replacement IP @packetjay the

IPv 6 Protocol challenges � Address dependencies: �MAC �IPv 6 �Multicast � Checksums @packetjay

Demo

Thanks! Questions? � Mail: jasper@packet-foo. com � Web: blog. packet-foo. com � Twitter: @packetjay