CIS 185 CCNP ROUTE Ch 8 Implementing IPv



![R 2# show ipv 6 route rip R 13: : /64 [120/3] via FE R 2# show ipv 6 route rip R 13: : /64 [120/3] via FE](https://slidetodoc.com/presentation_image/03087a41605c263292e53056315b72d5/image-24.jpg)


![R 1# show ipv 6 route static C C C 13: : /64 [1/0] R 1# show ipv 6 route static C C C 13: : /64 [1/0]](https://slidetodoc.com/presentation_image/03087a41605c263292e53056315b72d5/image-63.jpg)

- Slides: 71

CIS 185 CCNP ROUTE Ch. 8 Implementing IPv 6 – Part 3 Rick Graziani Cabrillo College graziani@cabrillo. edu Last Updated: Fall 2010

Materials l Book: Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide: Foundation learning for the ROUTE 642 -902 Exam By Diane Teare Book ISBN-10: 1 -58705 -882 -0 ISBN-13: 978 -1 -58705 -882 -0 e. Book ISBN-10: 0 -13 -255033 -4 ISBN-13: 978 -0 -13 -255033 -8 2

l Fortunately, the transition from IPv 4 to IPv 6 does not require upgrades on all nodes at the same time l IPv 4 and IPv 6 will coexist for some time. l There are many RFCs that relate to this transition 3

Techniques for the period of transition between IPv 4 and IPv 6: l Dual-stack techniques: Hosts and network devices run both IPv 4 and IPv 6 at the same time. Useful as a temporary transition But has a lot of overhead and uses many resources. l Tunneling techniques: Isolated IPv 6 networks are connected over an IPv 4 infrastructure using tunnels. The edge devices are the only ones that need to be dual-stacked. Scalability may be an issue if many tunnels need to be created. l Translation techniques: A translator converts IPv 6 packets into IPv 4 packets and vise versa Allows IPv 6 -only devices to communicate with IPv 4 -only devices. Scalability may again be an issue because of the resources required on the translator device. 4

Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 5

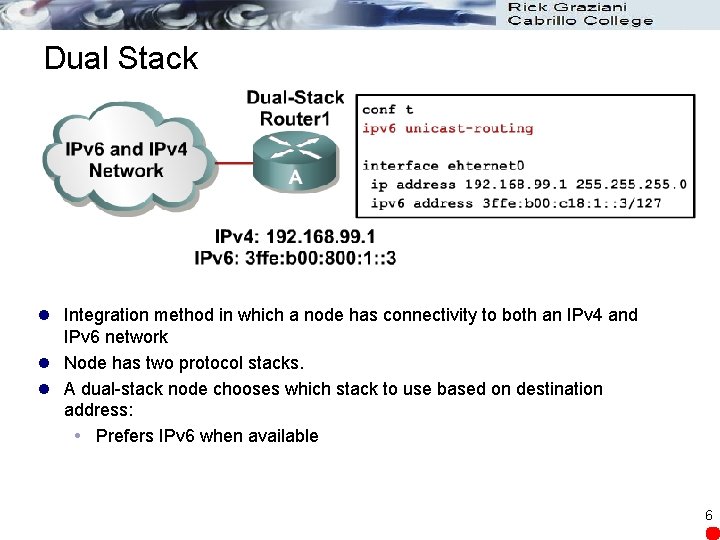
Dual Stack l Integration method in which a node has connectivity to both an IPv 4 and IPv 6 network l Node has two protocol stacks. l A dual-stack node chooses which stack to use based on destination address: Prefers IPv 6 when available 6

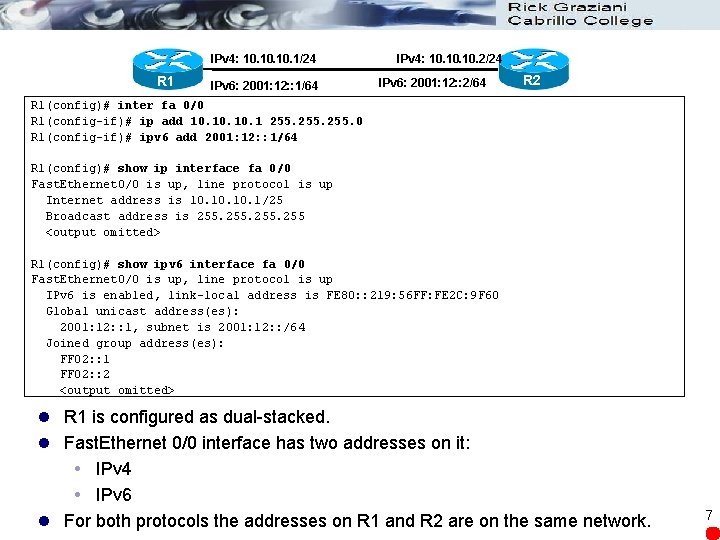
IPv 4: 10. 10. 1/24 R 1 IPv 6: 2001: 12: : 1/64 IPv 4: 10. 10. 2/24 IPv 6: 2001: 12: : 2/64 R 2 R 1(config)# inter fa 0/0 R 1(config-if)# ip add 10. 10. 1 255. 0 R 1(config-if)# ipv 6 add 2001: 12: : 1/64 R 1(config)# show ip interface fa 0/0 Fast. Ethernet 0/0 is up, line protocol is up Internet address is 10. 10. 1/25 Broadcast address is 255 <output omitted> R 1(config)# show ipv 6 interface fa 0/0 Fast. Ethernet 0/0 is up, line protocol is up IPv 6 is enabled, link-local address is FE 80: : 219: 56 FF: FE 2 C: 9 F 60 Global unicast address(es): 2001: 12: : 1, subnet is 2001: 12: : /64 Joined group address(es): FF 02: : 1 FF 02: : 2 <output omitted> l R 1 is configured as dual-stacked. l Fast. Ethernet 0/0 interface has two addresses on it: IPv 4 IPv 6 l For both protocols the addresses on R 1 and R 2 are on the same network. 7

IPv 4: 10. 10. 1/24 R 1 IPv 6: 2001: 12: : 1/64 IPv 4: 10. 10. 2/24 IPv 6: 2001: 12: : 2/64 R 2 l A drawback of dual stacking is the resources required within each device configured with both protocols. l The device must keep dual routing tables, routing protocol topology tables, etc. 8

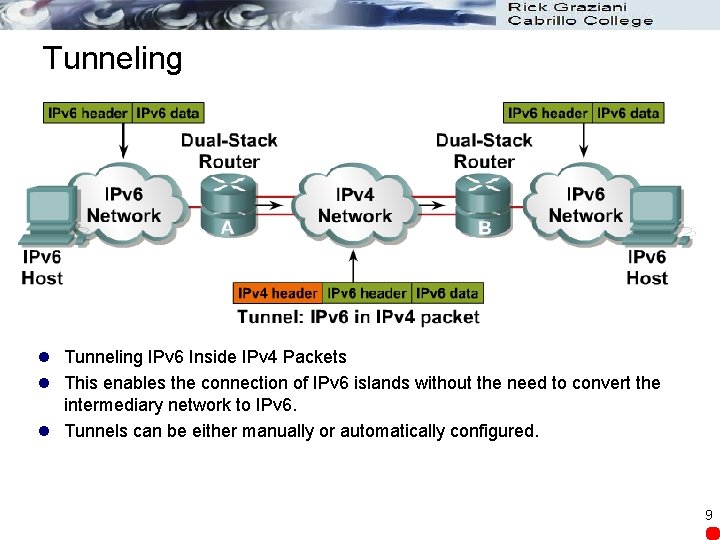
Tunneling l Tunneling IPv 6 Inside IPv 4 Packets l This enables the connection of IPv 6 islands without the need to convert the intermediary network to IPv 6. l Tunnels can be either manually or automatically configured. 9

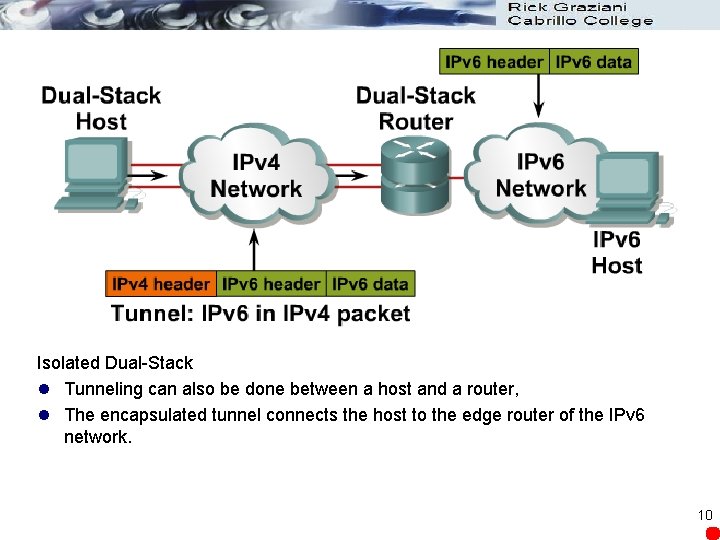
Isolated Dual-Stack l Tunneling can also be done between a host and a router, l The encapsulated tunnel connects the host to the edge router of the IPv 6 network. 10

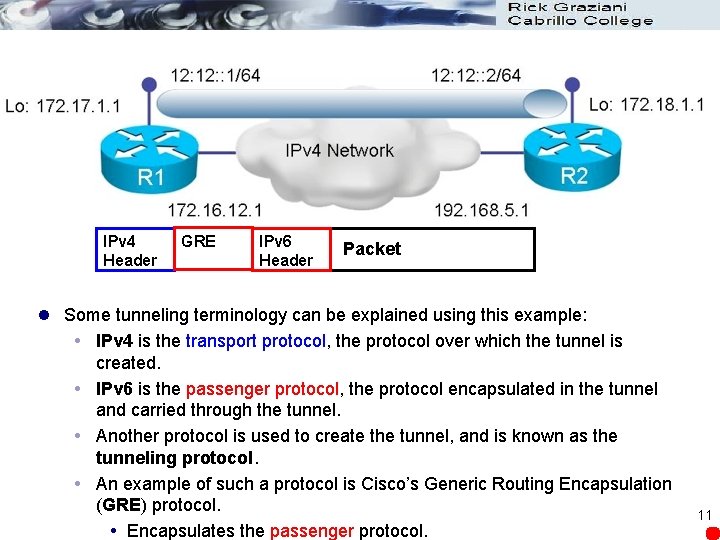
IPv 4 Header GRE IPv 6 Header Packet l Some tunneling terminology can be explained using this example: IPv 4 is the transport protocol, the protocol over which the tunnel is created. IPv 6 is the passenger protocol, the protocol encapsulated in the tunnel and carried through the tunnel. Another protocol is used to create the tunnel, and is known as the tunneling protocol. An example of such a protocol is Cisco’s Generic Routing Encapsulation (GRE) protocol. Encapsulates the passenger protocol. 11

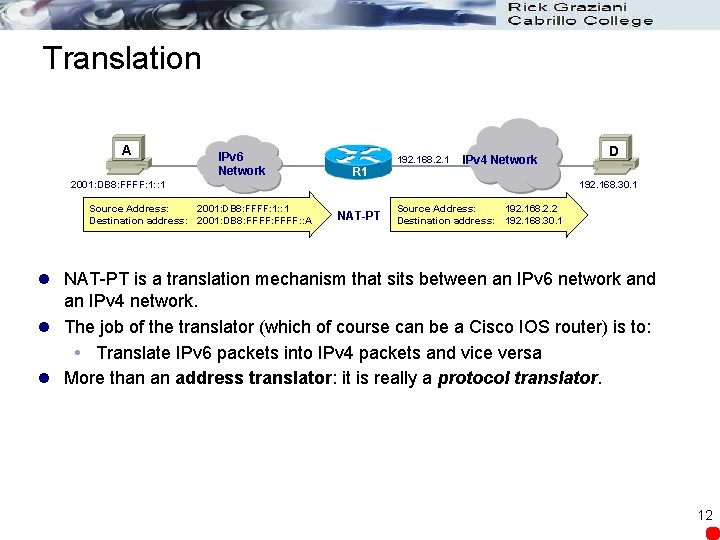
Translation A IPv 6 Network 2001: DB 8: FFFF: 1: : 1 Source Address: 2001: DB 8: FFFF: 1: : 1 Destination address: 2001: DB 8: FFFF: : A 192. 168. 2. 1 R 1 IPv 4 Network D 192. 168. 30. 1 NAT-PT Source Address: 192. 168. 2. 2 Destination address: 192. 168. 30. 1 l NAT-PT is a translation mechanism that sits between an IPv 6 network and an IPv 4 network. l The job of the translator (which of course can be a Cisco IOS router) is to: Translate IPv 6 packets into IPv 4 packets and vice versa l More than an address translator: it is really a protocol translator. 12

Tunneling IPv 6 Traffic

Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 14

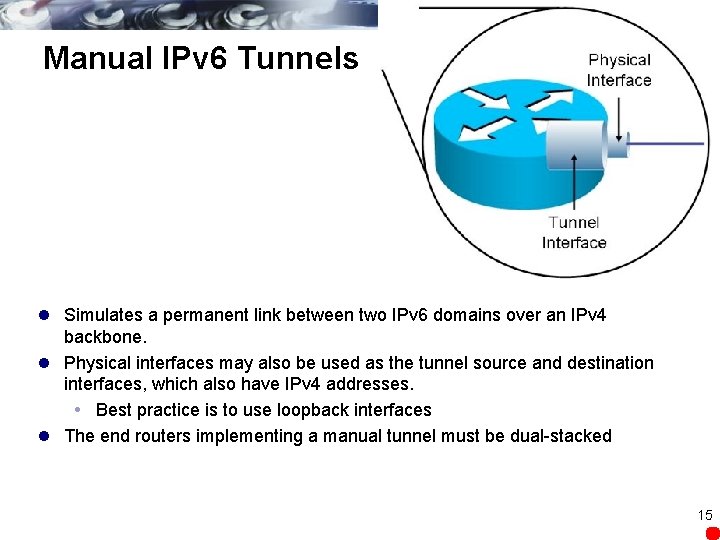
Manual IPv 6 Tunnels l Simulates a permanent link between two IPv 6 domains over an IPv 4 backbone. l Physical interfaces may also be used as the tunnel source and destination interfaces, which also have IPv 4 addresses. Best practice is to use loopback interfaces l The end routers implementing a manual tunnel must be dual-stacked 15

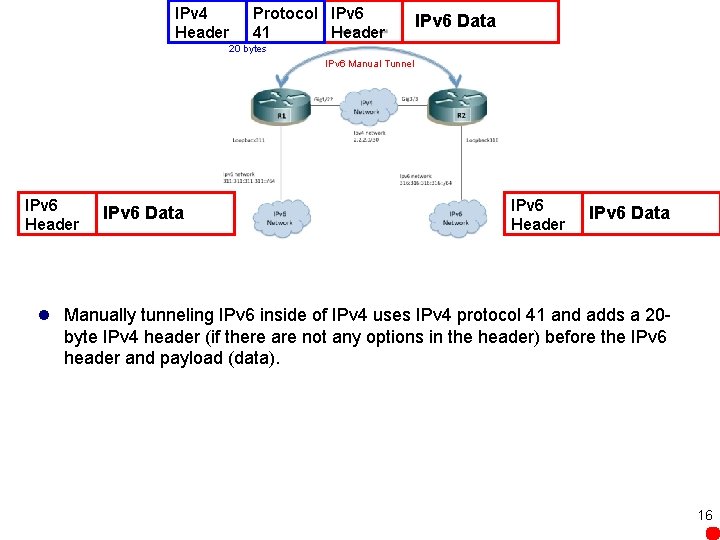
IPv 4 Header Protocol IPv 6 41 Header IPv 6 Data 20 bytes IPv 6 Manual Tunnel IPv 6 Header IPv 6 Data l Manually tunneling IPv 6 inside of IPv 4 uses IPv 4 protocol 41 and adds a 20 byte IPv 4 header (if there are not any options in the header) before the IPv 6 header and payload (data). 16

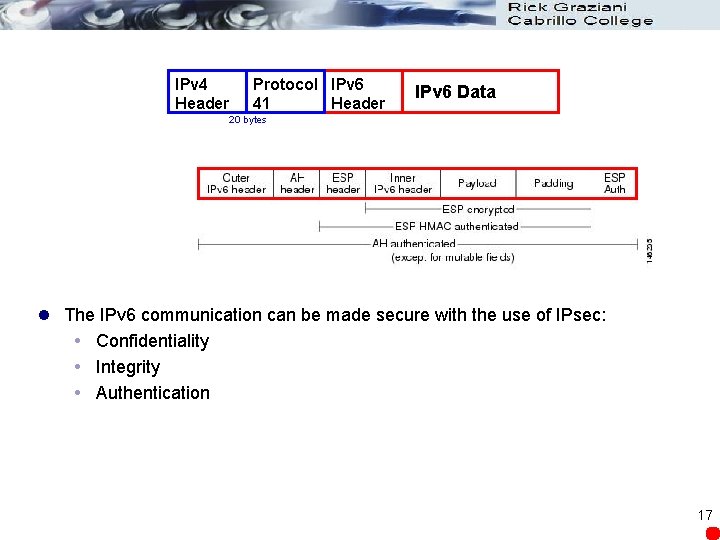
IPv 4 Header Protocol IPv 6 41 Header IPv 6 Data 20 bytes l The IPv 6 communication can be made secure with the use of IPsec: Confidentiality Integrity Authentication 17

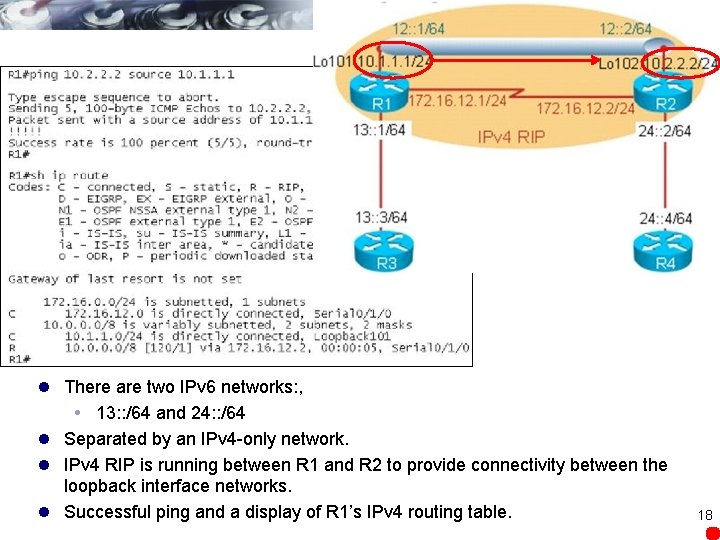
l There are two IPv 6 networks: , 13: : /64 and 24: : /64 l Separated by an IPv 4 -only network. l IPv 4 RIP is running between R 1 and R 2 to provide connectivity between the loopback interface networks. l Successful ping and a display of R 1’s IPv 4 routing table. 18

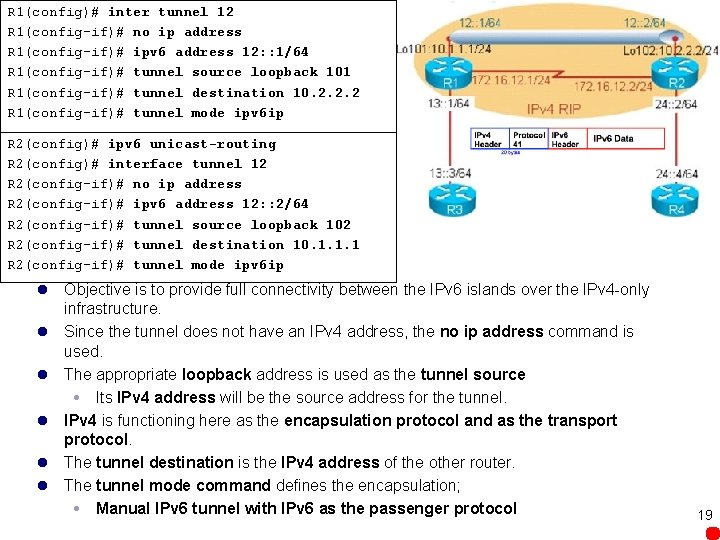
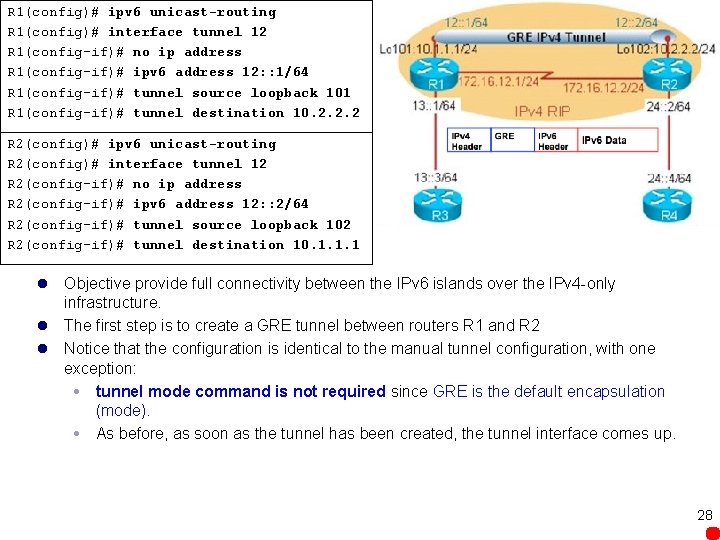
R 1(config)# inter tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : 1/64 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel destination 10. 2. 2. 2 R 1(config-if)# tunnel mode ipv 6 ip R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 12: : 2/64 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination 10. 1. 1. 1 R 2(config-if)# tunnel mode ipv 6 ip l Objective is to provide full connectivity between the IPv 6 islands over the IPv 4 -only infrastructure. l Since the tunnel does not have an IPv 4 address, the no ip address command is used. l The appropriate loopback address is used as the tunnel source Its IPv 4 address will be the source address for the tunnel. l IPv 4 is functioning here as the encapsulation protocol and as the transport protocol. l The tunnel destination is the IPv 4 address of the other router. l The tunnel mode command defines the encapsulation; Manual IPv 6 tunnel with IPv 6 as the passenger protocol 19

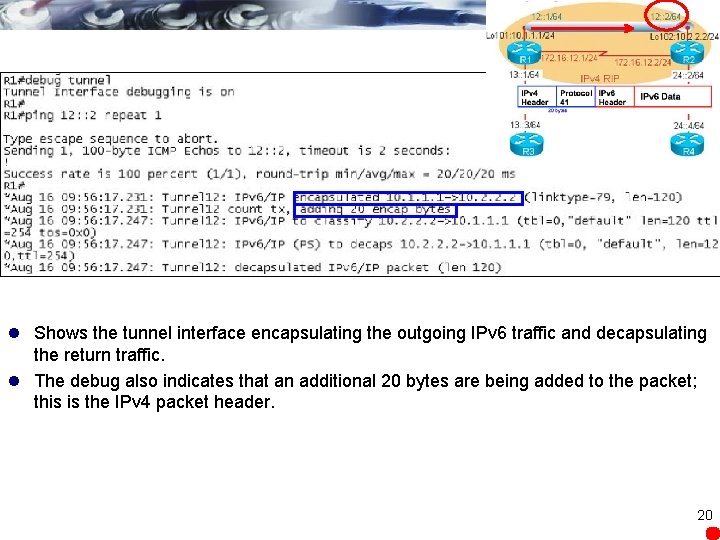
l Shows the tunnel interface encapsulating the outgoing IPv 6 traffic and decapsulating the return traffic. l The debug also indicates that an additional 20 bytes are being added to the packet; this is the IPv 4 packet header. 20

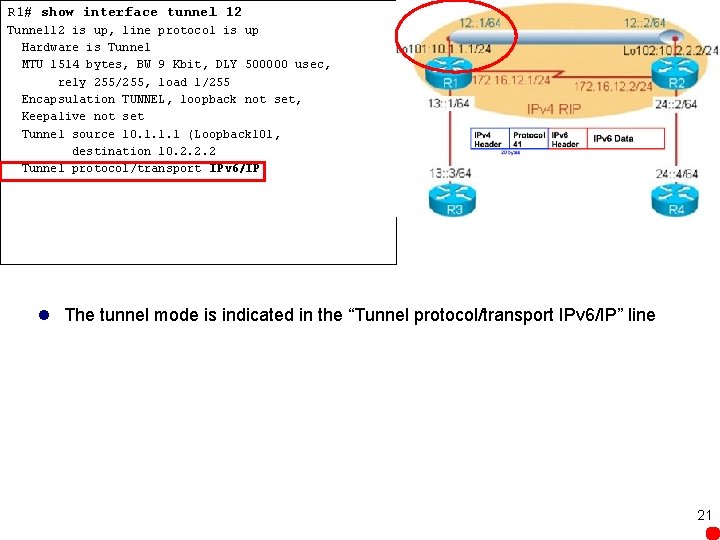
R 1# show interface tunnel 12 Tunnel 12 is up, line protocol is up Hardware is Tunnel MTU 1514 bytes, BW 9 Kbit, DLY 500000 usec, rely 255/255, load 1/255 Encapsulation TUNNEL, loopback not set, Keepalive not set Tunnel source 10. 1. 1. 1 (Loopback 101, destination 10. 2. 2. 2 Tunnel protocol/transport IPv 6/IP l The tunnel mode is indicated in the “Tunnel protocol/transport IPv 6/IP” line 21

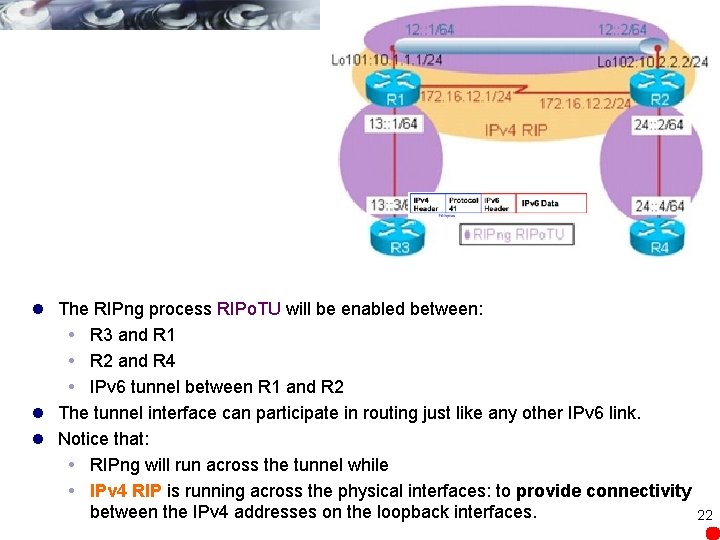
l The RIPng process RIPo. TU will be enabled between: R 3 and R 1 R 2 and R 4 IPv 6 tunnel between R 1 and R 2 l The tunnel interface can participate in routing just like any other IPv 6 link. l Notice that: RIPng will run across the tunnel while IPv 4 RIP is running across the physical interfaces: to provide connectivity between the IPv 4 addresses on the loopback interfaces. 22

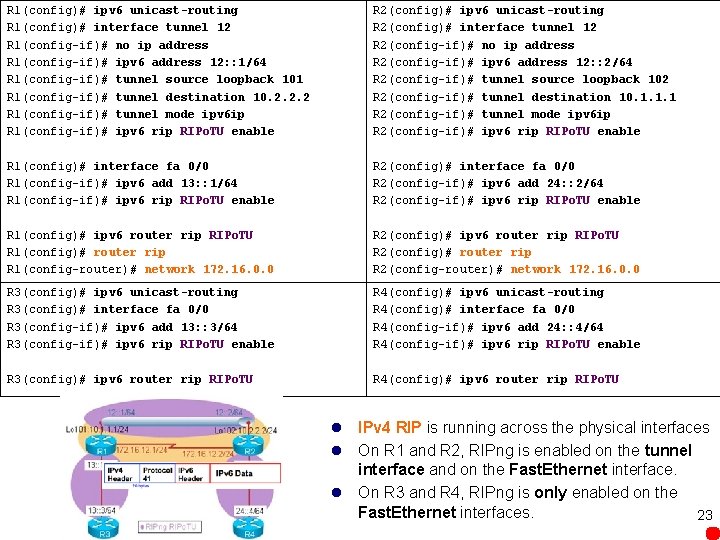
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : 1/64 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel destination 10. 2. 2. 2 R 1(config-if)# tunnel mode ipv 6 ip R 1(config-if)# ipv 6 rip RIPo. TU enable R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 12: : 2/64 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination 10. 1. 1. 1 R 2(config-if)# tunnel mode ipv 6 ip R 2(config-if)# ipv 6 rip RIPo. TU enable R 1(config)# interface fa 0/0 R 1(config-if)# ipv 6 add 13: : 1/64 R 1(config-if)# ipv 6 rip RIPo. TU enable R 2(config)# interface fa 0/0 R 2(config-if)# ipv 6 add 24: : 2/64 R 2(config-if)# ipv 6 rip RIPo. TU enable R 1(config)# ipv 6 router rip RIPo. TU R 1(config)# router rip R 1(config-router)# network 172. 16. 0. 0 R 2(config)# ipv 6 router rip RIPo. TU R 2(config)# router rip R 2(config-router)# network 172. 16. 0. 0 R 3(config)# ipv 6 unicast-routing R 3(config)# interface fa 0/0 R 3(config-if)# ipv 6 add 13: : 3/64 R 3(config-if)# ipv 6 rip RIPo. TU enable R 4(config)# ipv 6 unicast-routing R 4(config)# interface fa 0/0 R 4(config-if)# ipv 6 add 24: : 4/64 R 4(config-if)# ipv 6 rip RIPo. TU enable R 3(config)# ipv 6 router rip RIPo. TU R 4(config)# ipv 6 router rip RIPo. TU l IPv 4 RIP is running across the physical interfaces l On R 1 and R 2, RIPng is enabled on the tunnel interface and on the Fast. Ethernet interface. l On R 3 and R 4, RIPng is only enabled on the Fast. Ethernet interfaces. 23
![R 2 show ipv 6 route rip R 13 64 1203 via FE R 2# show ipv 6 route rip R 13: : /64 [120/3] via FE](https://slidetodoc.com/presentation_image/03087a41605c263292e53056315b72d5/image-24.jpg)
R 2# show ipv 6 route rip R 13: : /64 [120/3] via FE 80: : A 01: 101, Tunnel 12 R 4# show ipv 6 route rip R R 12: : /64 [120/2] via FE 80: : 2, Fast. Ethernet 0/0 13: : /64 [120/3] via FE 80: : 2, Fast. Ethernet 0/0 R 3# ping 24: : 4 !!!!! R 3# l To verify full connectivity across the tunnel, a ping from R 3 to R 4 is performed; as shown in the example it is successful. 24

Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 25

GRE IPv 6 Tunnels l GRE IPv 6 tunnels are very similar to manual tunnels. l GRE tunnels were developed by Cisco; l GRE encapsulation is the default tunneling protocol (configured with the tunnel mode command) on Cisco routers. 26

l The communication can be made secure with the use IPsec. l GRE itself does not provide these security features; it is only an encapsulation protocol. 27

R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : 1/64 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel destination 10. 2. 2. 2 R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 12: : 2/64 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination 10. 1. 1. 1 l Objective provide full connectivity between the IPv 6 islands over the IPv 4 -only infrastructure. l The first step is to create a GRE tunnel between routers R 1 and R 2 l Notice that the configuration is identical to the manual tunnel configuration, with one exception: tunnel mode command is not required since GRE is the default encapsulation (mode). As before, as soon as the tunnel has been created, the tunnel interface comes up. 28

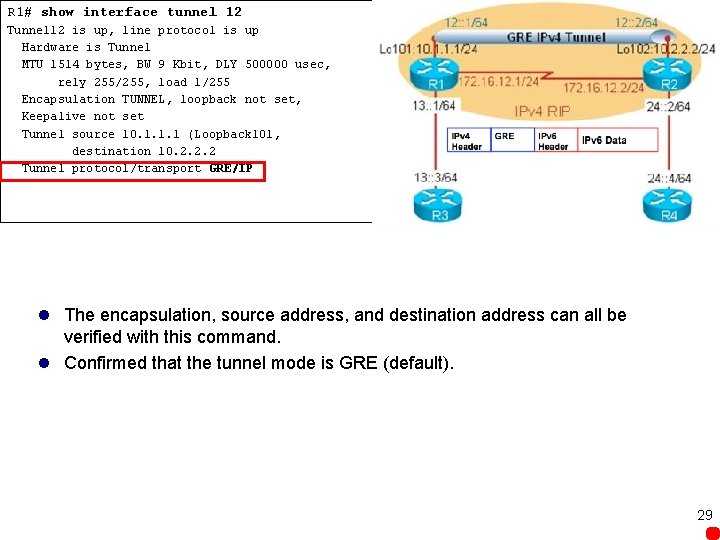
R 1# show interface tunnel 12 Tunnel 12 is up, line protocol is up Hardware is Tunnel MTU 1514 bytes, BW 9 Kbit, DLY 500000 usec, rely 255/255, load 1/255 Encapsulation TUNNEL, loopback not set, Keepalive not set Tunnel source 10. 1. 1. 1 (Loopback 101, destination 10. 2. 2. 2 Tunnel protocol/transport GRE/IP l The encapsulation, source address, and destination address can all be verified with this command. l Confirmed that the tunnel mode is GRE (default). 29

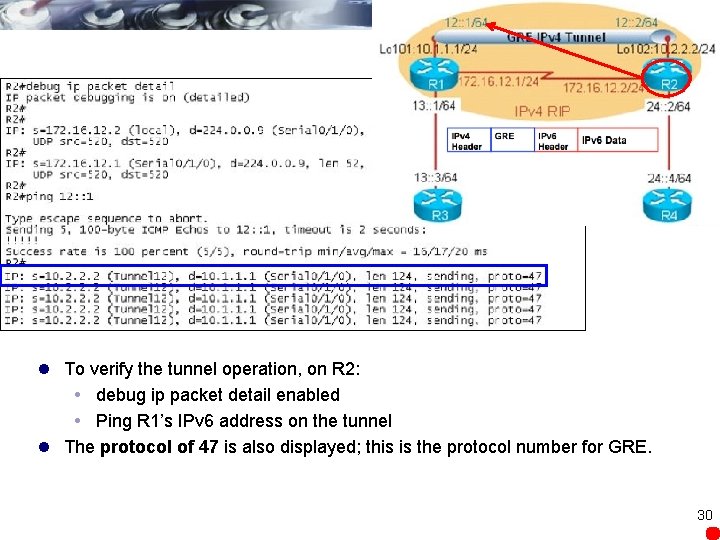
l To verify the tunnel operation, on R 2: debug ip packet detail enabled Ping R 1’s IPv 6 address on the tunnel l The protocol of 47 is also displayed; this is the protocol number for GRE. 30

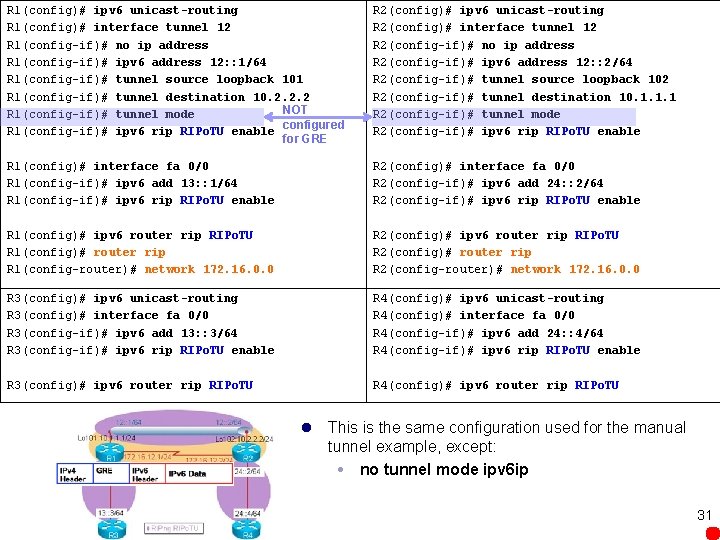
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : 1/64 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel destination 10. 2. 2. 2 NOT R 1(config-if)# tunnel mode configured R 1(config-if)# ipv 6 rip RIPo. TU enable for GRE R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 12: : 2/64 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination 10. 1. 1. 1 R 2(config-if)# tunnel mode R 2(config-if)# ipv 6 rip RIPo. TU enable R 1(config)# interface fa 0/0 R 1(config-if)# ipv 6 add 13: : 1/64 R 1(config-if)# ipv 6 rip RIPo. TU enable R 2(config)# interface fa 0/0 R 2(config-if)# ipv 6 add 24: : 2/64 R 2(config-if)# ipv 6 rip RIPo. TU enable R 1(config)# ipv 6 router rip RIPo. TU R 1(config)# router rip R 1(config-router)# network 172. 16. 0. 0 R 2(config)# ipv 6 router rip RIPo. TU R 2(config)# router rip R 2(config-router)# network 172. 16. 0. 0 R 3(config)# ipv 6 unicast-routing R 3(config)# interface fa 0/0 R 3(config-if)# ipv 6 add 13: : 3/64 R 3(config-if)# ipv 6 rip RIPo. TU enable R 4(config)# ipv 6 unicast-routing R 4(config)# interface fa 0/0 R 4(config-if)# ipv 6 add 24: : 4/64 R 4(config-if)# ipv 6 rip RIPo. TU enable R 3(config)# ipv 6 router rip RIPo. TU R 4(config)# ipv 6 router rip RIPo. TU l This is the same configuration used for the manual tunnel example, except: no tunnel mode ipv 6 ip 31

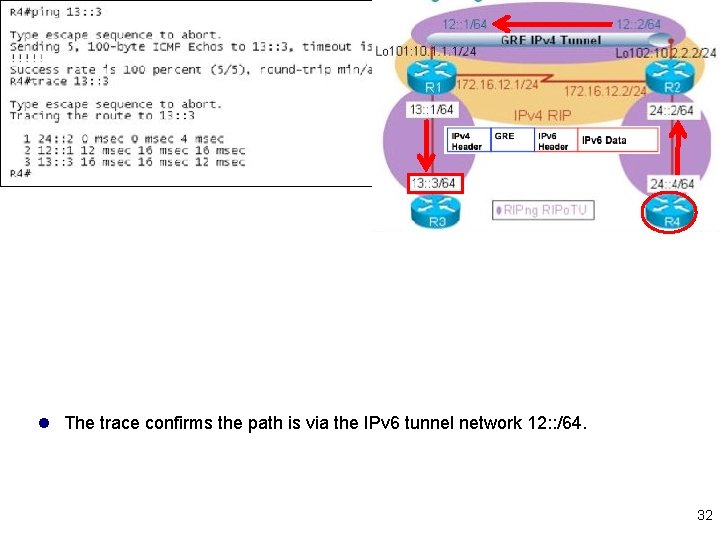
l The trace confirms the path is via the IPv 6 tunnel network 12: : /64. 32

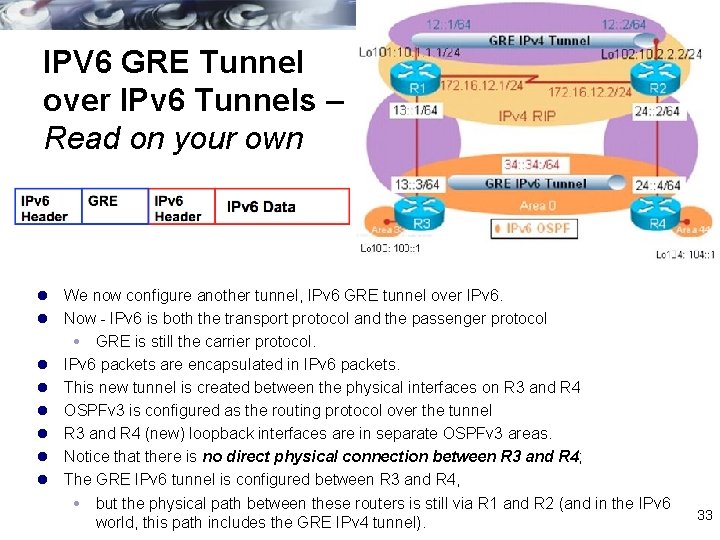
IPV 6 GRE Tunnel over IPv 6 Tunnels – Read on your own l We now configure another tunnel, IPv 6 GRE tunnel over IPv 6. l Now - IPv 6 is both the transport protocol and the passenger protocol GRE is still the carrier protocol. l IPv 6 packets are encapsulated in IPv 6 packets. l This new tunnel is created between the physical interfaces on R 3 and R 4 l OSPFv 3 is configured as the routing protocol over the tunnel l R 3 and R 4 (new) loopback interfaces are in separate OSPFv 3 areas. l Notice that there is no direct physical connection between R 3 and R 4; l The GRE IPv 6 tunnel is configured between R 3 and R 4, but the physical path between these routers is still via R 1 and R 2 (and in the IPv 6 world, this path includes the GRE IPv 4 tunnel). 33

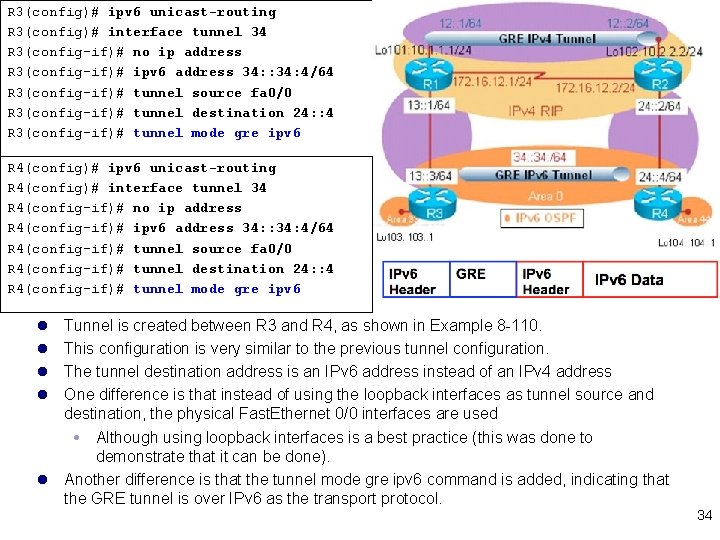
R 3(config)# ipv 6 unicast-routing R 3(config)# interface tunnel 34 R 3(config-if)# no ip address R 3(config-if)# ipv 6 address 34: : 34: 4/64 R 3(config-if)# tunnel source fa 0/0 R 3(config-if)# tunnel destination 24: : 4 R 3(config-if)# tunnel mode gre ipv 6 R 4(config)# ipv 6 unicast-routing R 4(config)# interface tunnel 34 R 4(config-if)# no ip address R 4(config-if)# ipv 6 address 34: : 34: 4/64 R 4(config-if)# tunnel source fa 0/0 R 4(config-if)# tunnel destination 24: : 4 R 4(config-if)# tunnel mode gre ipv 6 l l Tunnel is created between R 3 and R 4, as shown in Example 8 -110. This configuration is very similar to the previous tunnel configuration. The tunnel destination address is an IPv 6 address instead of an IPv 4 address One difference is that instead of using the loopback interfaces as tunnel source and destination, the physical Fast. Ethernet 0/0 interfaces are used Although using loopback interfaces is a best practice (this was done to demonstrate that it can be done). l Another difference is that the tunnel mode gre ipv 6 command is added, indicating that the GRE tunnel is over IPv 6 as the transport protocol. 34

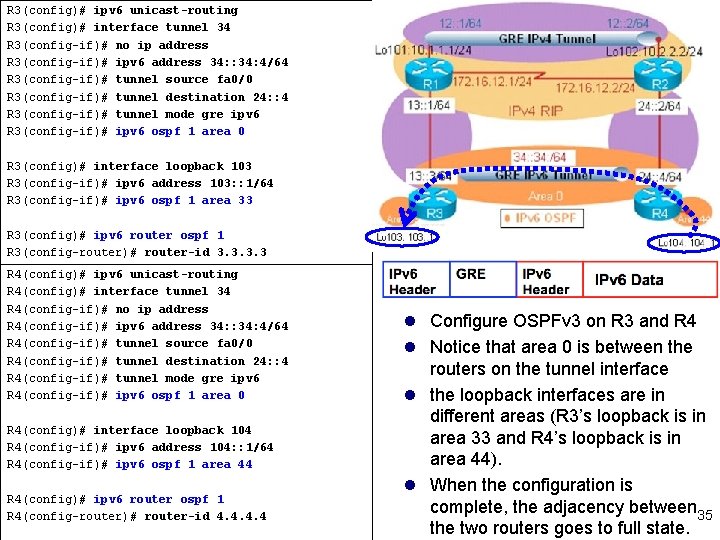
R 3(config)# ipv 6 unicast-routing R 3(config)# interface tunnel 34 R 3(config-if)# no ip address R 3(config-if)# ipv 6 address 34: : 34: 4/64 R 3(config-if)# tunnel source fa 0/0 R 3(config-if)# tunnel destination 24: : 4 R 3(config-if)# tunnel mode gre ipv 6 R 3(config-if)# ipv 6 ospf 1 area 0 R 3(config)# interface loopback 103 R 3(config-if)# ipv 6 address 103: : 1/64 R 3(config-if)# ipv 6 ospf 1 area 33 R 3(config)# ipv 6 router ospf 1 R 3(config-router)# router-id 3. 3 R 4(config)# ipv 6 unicast-routing R 4(config)# interface tunnel 34 R 4(config-if)# no ip address R 4(config-if)# ipv 6 address 34: : 34: 4/64 R 4(config-if)# tunnel source fa 0/0 R 4(config-if)# tunnel destination 24: : 4 R 4(config-if)# tunnel mode gre ipv 6 R 4(config-if)# ipv 6 ospf 1 area 0 R 4(config)# interface loopback 104 R 4(config-if)# ipv 6 address 104: : 1/64 R 4(config-if)# ipv 6 ospf 1 area 44 R 4(config)# ipv 6 router ospf 1 R 4(config-router)# router-id 4. 4 l Configure OSPFv 3 on R 3 and R 4 l Notice that area 0 is between the routers on the tunnel interface l the loopback interfaces are in different areas (R 3’s loopback is in area 33 and R 4’s loopback is in area 44). l When the configuration is complete, the adjacency between 35 the two routers goes to full state.

Transition methods between IPv 4 and IPv 6 Please read about Translation at the end of this chapter l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel – Suggested Lab IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 36

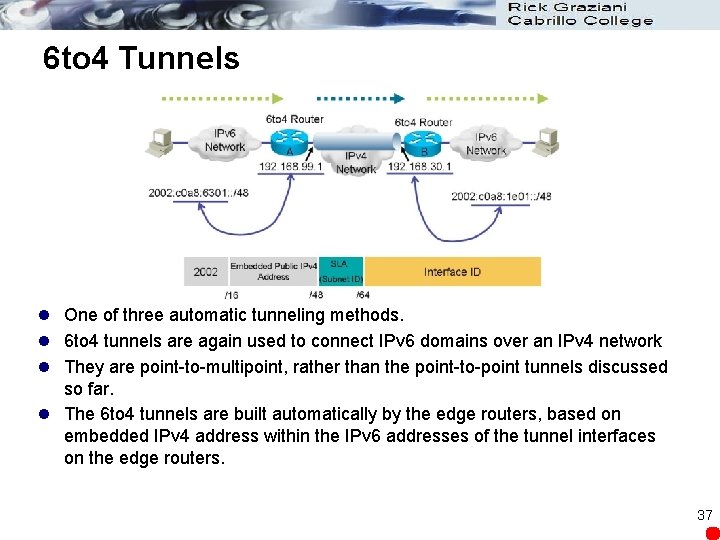
6 to 4 Tunnels l One of three automatic tunneling methods. l 6 to 4 tunnels are again used to connect IPv 6 domains over an IPv 4 network l They are point-to-multipoint, rather than the point-to-point tunnels discussed so far. l The 6 to 4 tunnels are built automatically by the edge routers, based on embedded IPv 4 address within the IPv 6 addresses of the tunnel interfaces on the edge routers. 37

Some slides temporarily removed 38

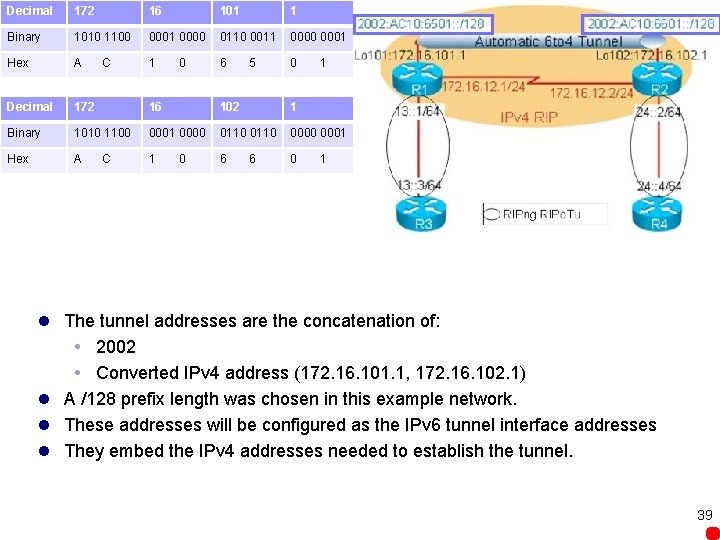
Decimal 172 16 101 1 Binary 1010 1100 0001 0000 0110 0011 0000 0001 Hex A C 1 0 6 5 0 1 Decimal 172 16 102 1 Binary 1010 1100 0001 0000 0110 0001 Hex A C 1 0 6 6 0 1 l The tunnel addresses are the concatenation of: 2002 Converted IPv 4 address (172. 16. 101. 1, 172. 16. 102. 1) l A /128 prefix length was chosen in this example network. l These addresses will be configured as the IPv 6 tunnel interface addresses l They embed the IPv 4 addresses needed to establish the tunnel. 39

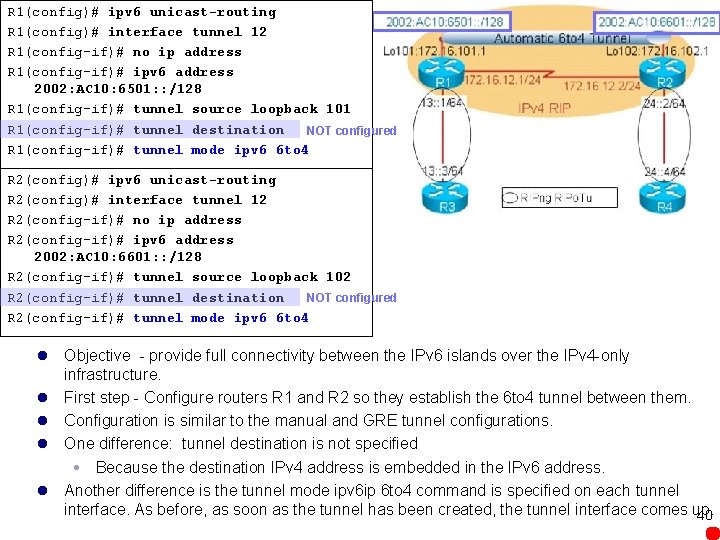
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 2002: AC 10: 6501: : /128 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel destination NOT configured R 1(config-if)# tunnel mode ipv 6 6 to 4 R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 2002: AC 10: 6601: : /128 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination NOT configured R 2(config-if)# tunnel mode ipv 6 6 to 4 l Objective - provide full connectivity between the IPv 6 islands over the IPv 4 -only infrastructure. l First step - Configure routers R 1 and R 2 so they establish the 6 to 4 tunnel between them. l Configuration is similar to the manual and GRE tunnel configurations. l One difference: tunnel destination is not specified Because the destination IPv 4 address is embedded in the IPv 6 address. l Another difference is the tunnel mode ipv 6 ip 6 to 4 command is specified on each tunnel interface. As before, as soon as the tunnel has been created, the tunnel interface comes up. 40

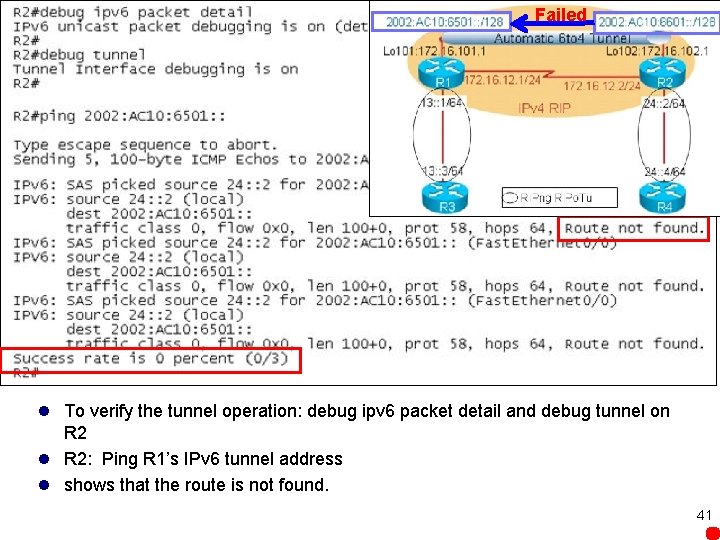
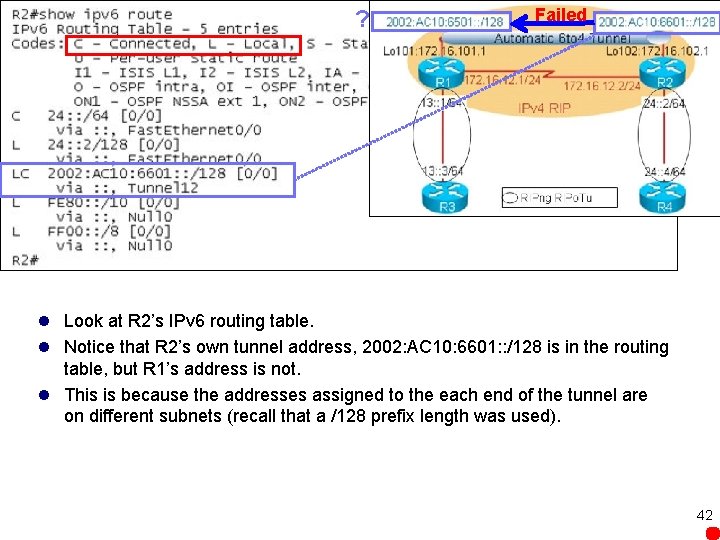
Failed l To verify the tunnel operation: debug ipv 6 packet detail and debug tunnel on R 2 l R 2: Ping R 1’s IPv 6 tunnel address l shows that the route is not found. 41

? Failed l Look at R 2’s IPv 6 routing table. l Notice that R 2’s own tunnel address, 2002: AC 10: 6601: : /128 is in the routing table, but R 1’s address is not. l This is because the addresses assigned to the each end of the tunnel are on different subnets (recall that a /128 prefix length was used). 42

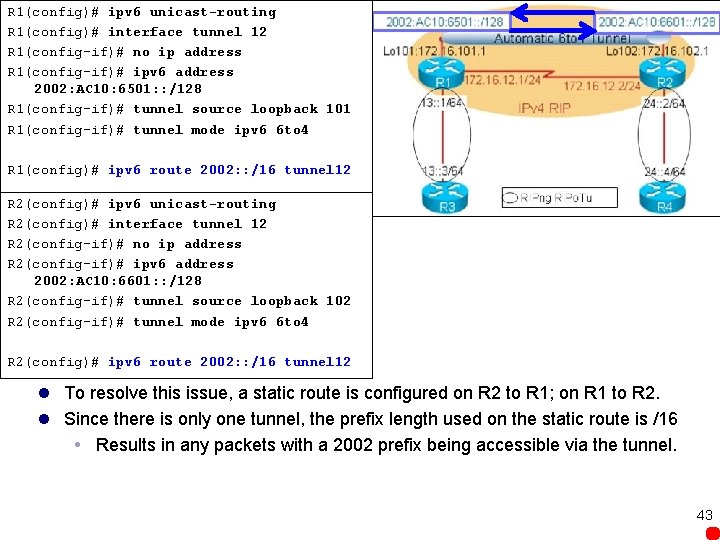
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 2002: AC 10: 6501: : /128 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel mode ipv 6 6 to 4 R 1(config)# ipv 6 route 2002: : /16 tunnel 12 R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 2002: AC 10: 6601: : /128 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel mode ipv 6 6 to 4 R 2(config)# ipv 6 route 2002: : /16 tunnel 12 l To resolve this issue, a static route is configured on R 2 to R 1; on R 1 to R 2. l Since there is only one tunnel, the prefix length used on the static route is /16 Results in any packets with a 2002 prefix being accessible via the tunnel. 43

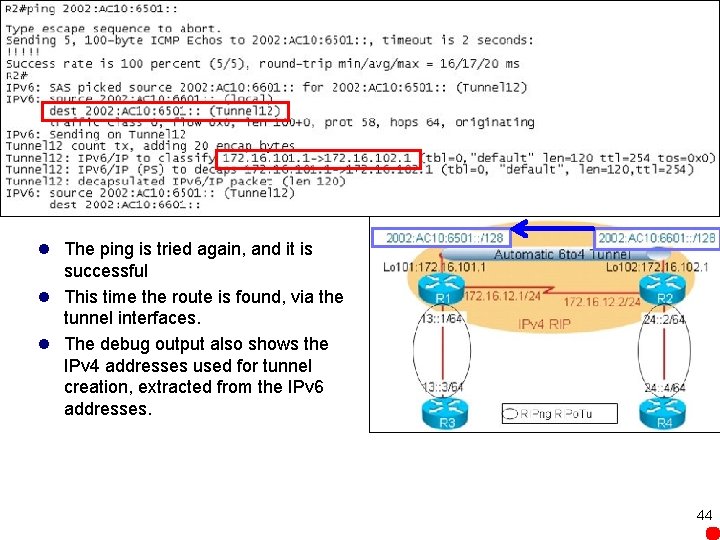
l The ping is tried again, and it is successful l This time the route is found, via the tunnel interfaces. l The debug output also shows the IPv 4 addresses used for tunnel creation, extracted from the IPv 6 addresses. 44

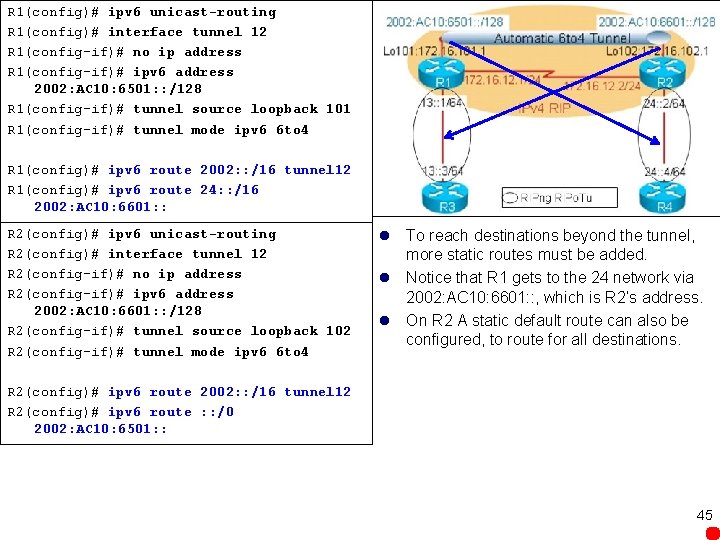
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 2002: AC 10: 6501: : /128 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel mode ipv 6 6 to 4 R 1(config)# ipv 6 route 2002: : /16 tunnel 12 R 1(config)# ipv 6 route 24: : /16 2002: AC 10: 6601: : R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 2002: AC 10: 6601: : /128 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel mode ipv 6 6 to 4 l To reach destinations beyond the tunnel, more static routes must be added. l Notice that R 1 gets to the 24 network via 2002: AC 10: 6601: : , which is R 2’s address. l On R 2 A static default route can also be configured, to route for all destinations. R 2(config)# ipv 6 route 2002: : /16 tunnel 12 R 2(config)# ipv 6 route : : /0 2002: AC 10: 6501: : 45

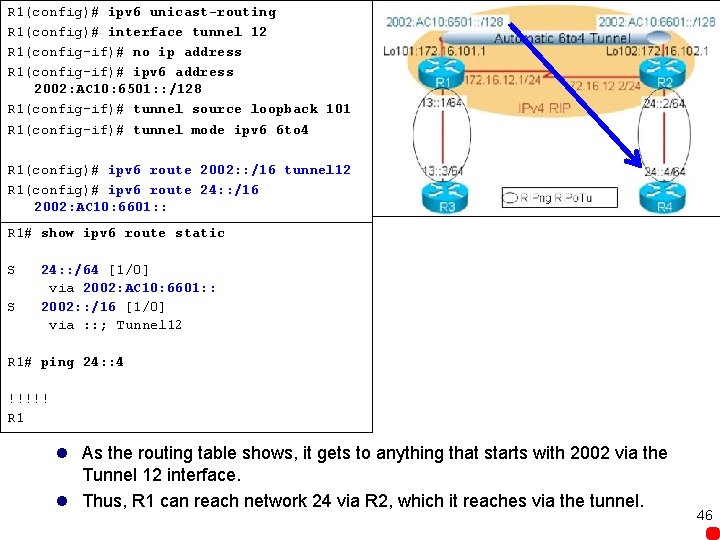
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 2002: AC 10: 6501: : /128 R 1(config-if)# tunnel source loopback 101 R 1(config-if)# tunnel mode ipv 6 6 to 4 R 1(config)# ipv 6 route 2002: : /16 tunnel 12 R 1(config)# ipv 6 route 24: : /16 2002: AC 10: 6601: : R 1# show ipv 6 route static S S 24: : /64 [1/0] via 2002: AC 10: 6601: : 2002: : /16 [1/0] via : : ; Tunnel 12 R 1# ping 24: : 4 !!!!! R 1 l As the routing table shows, it gets to anything that starts with 2002 via the Tunnel 12 interface. l Thus, R 1 can reach network 24 via R 2, which it reaches via the tunnel. 46

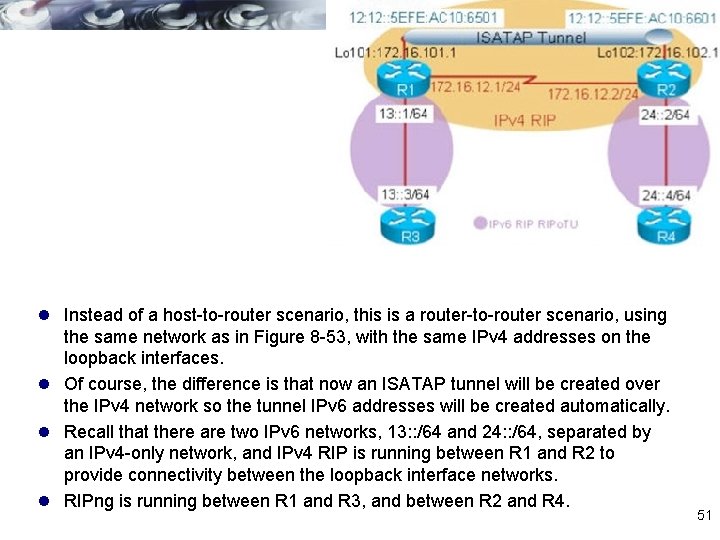
Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 47

Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 48

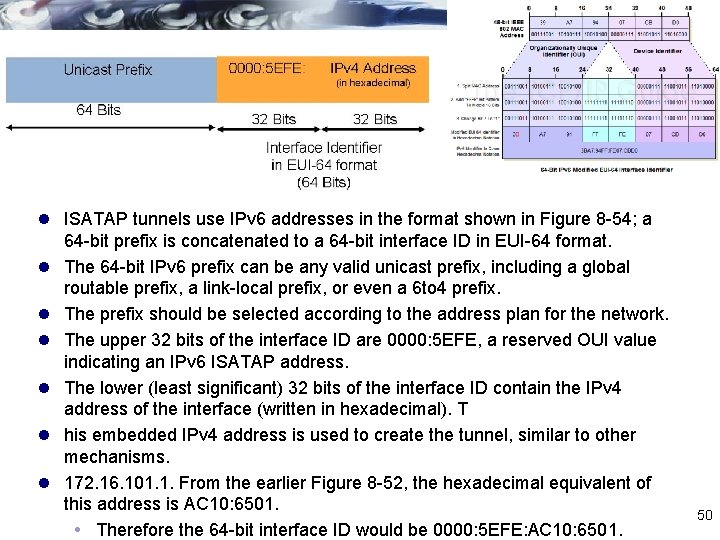
ISATAP Tunnels l ISATAP tunnels are very similar to 6 to 4 and IPv 4 -compatible IPv 6 tunnels: l they all are used to connect IPv 6 domains over an IPv 4 network, l all embed an IPv 4 address within the IPv 6 address so that the tunnel destination IPv 4 address is easily obtained by the devices at the end of the tunnel and it can therefore automatically create the tunnel. l ISATAP was designed to transport IPv 6 packets within a site (hence the “intra-site” part of its name); it can still be used between sites, but its purpose is within sites. l The main limitation of ISATAP is that it does not support IPv 6 multicast. This is not an issue for static routing or BGP (like 6 to 4 tunnels) 49

l ISATAP tunnels use IPv 6 addresses in the format shown in Figure 8 -54; a 64 -bit prefix is concatenated to a 64 -bit interface ID in EUI-64 format. l The 64 -bit IPv 6 prefix can be any valid unicast prefix, including a global routable prefix, a link-local prefix, or even a 6 to 4 prefix. l The prefix should be selected according to the address plan for the network. l The upper 32 bits of the interface ID are 0000: 5 EFE, a reserved OUI value indicating an IPv 6 ISATAP address. l The lower (least significant) 32 bits of the interface ID contain the IPv 4 address of the interface (written in hexadecimal). T l his embedded IPv 4 address is used to create the tunnel, similar to other mechanisms. l 172. 16. 101. 1. From the earlier Figure 8 -52, the hexadecimal equivalent of this address is AC 10: 6501. Therefore the 64 -bit interface ID would be 0000: 5 EFE: AC 10: 6501. 50

l Instead of a host-to-router scenario, this is a router-to-router scenario, using the same network as in Figure 8 -53, with the same IPv 4 addresses on the loopback interfaces. l Of course, the difference is that now an ISATAP tunnel will be created over the IPv 4 network so the tunnel IPv 6 addresses will be created automatically. l Recall that there are two IPv 6 networks, 13: : /64 and 24: : /64, separated by an IPv 4 -only network, and IPv 4 RIP is running between R 1 and R 2 to provide connectivity between the loopback interface networks. l RIPng is running between R 1 and R 3, and between R 2 and R 4. 51

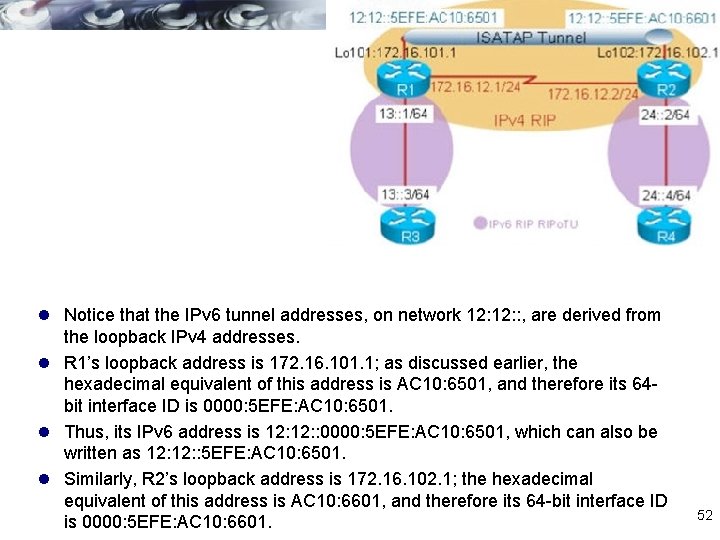
l Notice that the IPv 6 tunnel addresses, on network 12: : , are derived from the loopback IPv 4 addresses. l R 1’s loopback address is 172. 16. 101. 1; as discussed earlier, the hexadecimal equivalent of this address is AC 10: 6501, and therefore its 64 bit interface ID is 0000: 5 EFE: AC 10: 6501. l Thus, its IPv 6 address is 12: : 0000: 5 EFE: AC 10: 6501, which can also be written as 12: : 5 EFE: AC 10: 6501. l Similarly, R 2’s loopback address is 172. 16. 102. 1; the hexadecimal equivalent of this address is AC 10: 6601, and therefore its 64 -bit interface ID is 0000: 5 EFE: AC 10: 6601. 52

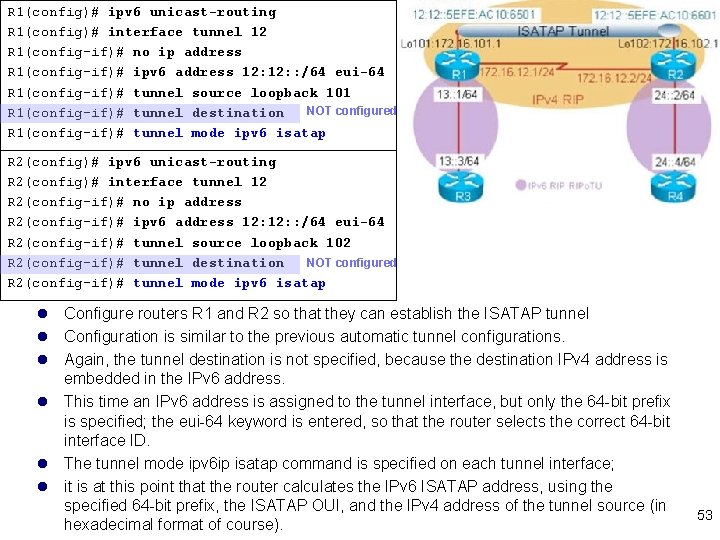
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : /64 eui-64 R 1(config-if)# tunnel source loopback 101 NOT configured R 1(config-if)# tunnel destination R 1(config-if)# tunnel mode ipv 6 isatap R 2(config)# ipv 6 unicast-routing R 2(config)# interface tunnel 12 R 2(config-if)# no ip address R 2(config-if)# ipv 6 address 12: : /64 eui-64 R 2(config-if)# tunnel source loopback 102 R 2(config-if)# tunnel destination NOT configured R 2(config-if)# tunnel mode ipv 6 isatap l Configure routers R 1 and R 2 so that they can establish the ISATAP tunnel l Configuration is similar to the previous automatic tunnel configurations. l Again, the tunnel destination is not specified, because the destination IPv 4 address is embedded in the IPv 6 address. l This time an IPv 6 address is assigned to the tunnel interface, but only the 64 -bit prefix is specified; the eui-64 keyword is entered, so that the router selects the correct 64 -bit interface ID. l The tunnel mode ipv 6 ip isatap command is specified on each tunnel interface; l it is at this point that the router calculates the IPv 6 ISATAP address, using the specified 64 -bit prefix, the ISATAP OUI, and the IPv 4 address of the tunnel source (in hexadecimal format of course). 53

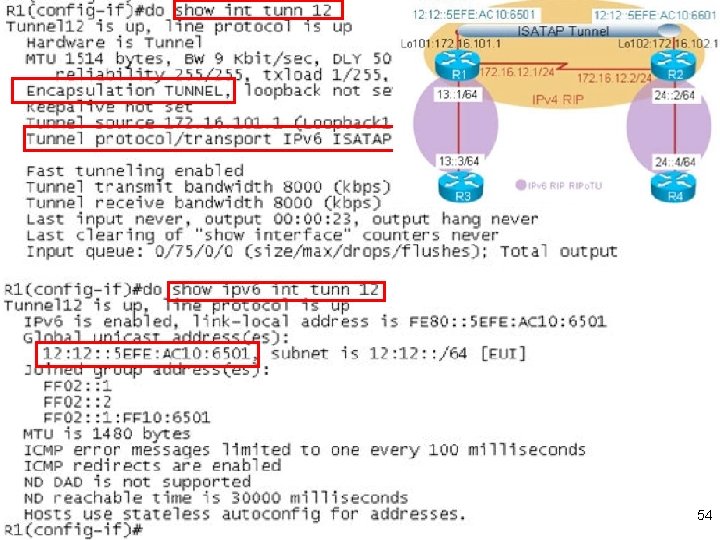
54

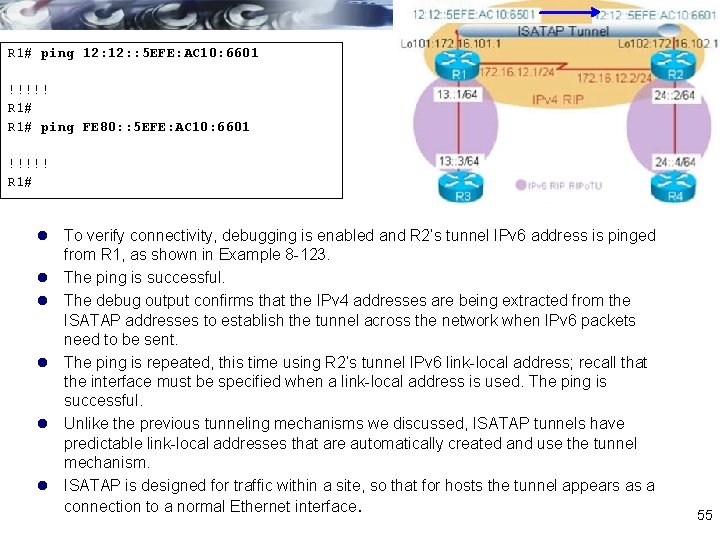
R 1# ping 12: : 5 EFE: AC 10: 6601 !!!!! R 1# ping FE 80: : 5 EFE: AC 10: 6601 !!!!! R 1# l To verify connectivity, debugging is enabled and R 2’s tunnel IPv 6 address is pinged from R 1, as shown in Example 8 -123. l The ping is successful. l The debug output confirms that the IPv 4 addresses are being extracted from the ISATAP addresses to establish the tunnel across the network when IPv 6 packets need to be sent. l The ping is repeated, this time using R 2’s tunnel IPv 6 link-local address; recall that the interface must be specified when a link-local address is used. The ping is successful. l Unlike the previous tunneling mechanisms we discussed, ISATAP tunnels have predictable link-local addresses that are automatically created and use the tunnel mechanism. l ISATAP is designed for traffic within a site, so that for hosts the tunnel appears as a connection to a normal Ethernet interface. 55

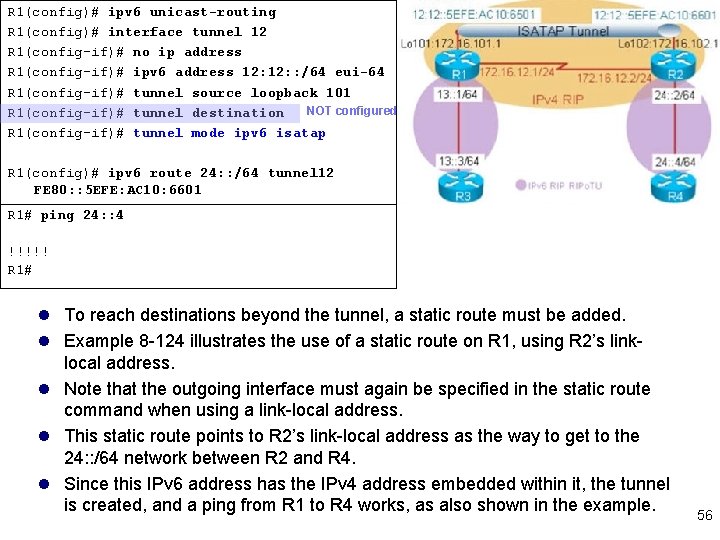
R 1(config)# ipv 6 unicast-routing R 1(config)# interface tunnel 12 R 1(config-if)# no ip address R 1(config-if)# ipv 6 address 12: : /64 eui-64 R 1(config-if)# tunnel source loopback 101 NOT configured R 1(config-if)# tunnel destination R 1(config-if)# tunnel mode ipv 6 isatap R 1(config)# ipv 6 route 24: : /64 tunnel 12 FE 80: : 5 EFE: AC 10: 6601 R 1# ping 24: : 4 !!!!! R 1# l To reach destinations beyond the tunnel, a static route must be added. l Example 8 -124 illustrates the use of a static route on R 1, using R 2’s linklocal address. l Note that the outgoing interface must again be specified in the static route command when using a link-local address. l This static route points to R 2’s link-local address as the way to get to the 24: : /64 network between R 2 and R 4. l Since this IPv 6 address has the IPv 4 address embedded within it, the tunnel is created, and a ping from R 1 to R 4 works, as also shown in the example. 56

Transition methods between IPv 4 and IPv 6 l Dual-stack l Tunneling Manual IPv 6 Tunnel GRE IPv 6 Tunnel Dynamic 6 to 4 Tunnel IPv 4 -Compatible IPv 6 Tunnel (deprecated) ISATAP Tunnel l Translation Static NAT-PT for IPv 6 Dynamic NAT-PT for IPv 6 57

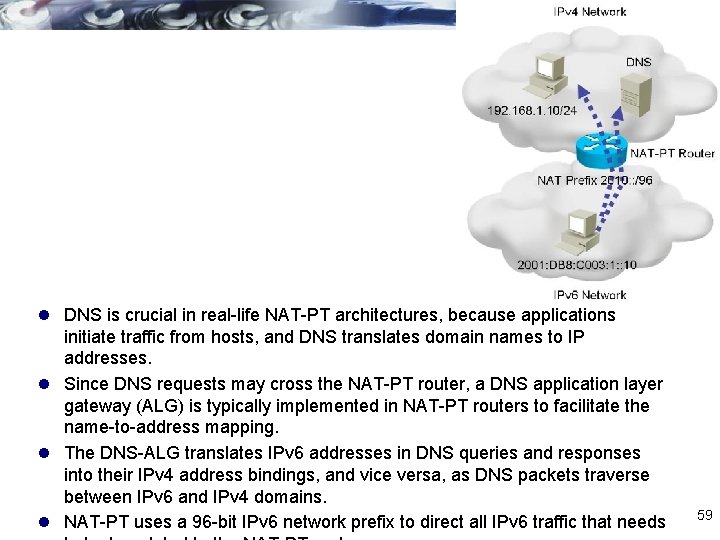
l NAT-PT is another powerful transition technique, but is not a replacement for the other techniques, such as dual-stack and tunneling, discussed so far in this chapter. l Used in situations where direct communication between IPv 6 -only and IPv 4 only networks is desired. l It would not be appropriate in situations where connectivity between two IPv 6 networks is required, since two points of translation would be necessary, which would not be efficient or effective. l With NAT-PT, all configuration and translation is performed on the NAT-PT router; the other devices in the network are not aware of the existence of the 58

l DNS is crucial in real-life NAT-PT architectures, because applications initiate traffic from hosts, and DNS translates domain names to IP addresses. l Since DNS requests may cross the NAT-PT router, a DNS application layer gateway (ALG) is typically implemented in NAT-PT routers to facilitate the name-to-address mapping. l The DNS-ALG translates IPv 6 addresses in DNS queries and responses into their IPv 4 address bindings, and vice versa, as DNS packets traverse between IPv 6 and IPv 4 domains. l NAT-PT uses a 96 -bit IPv 6 network prefix to direct all IPv 6 traffic that needs 59

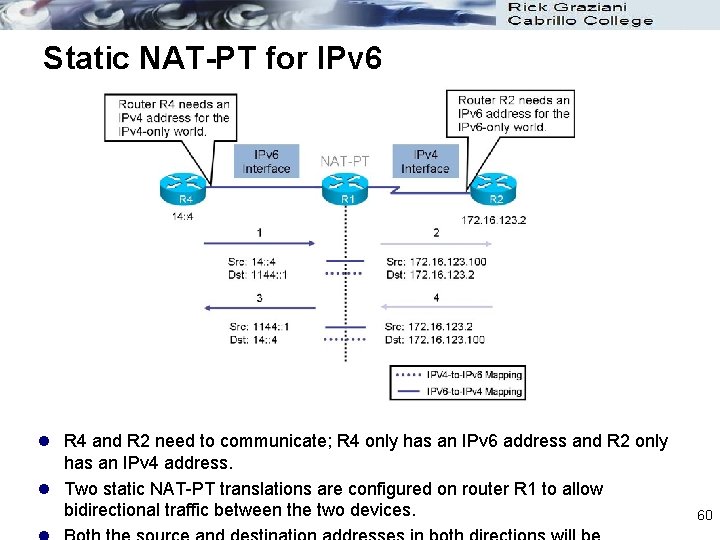
Static NAT-PT for IPv 6 l R 4 and R 2 need to communicate; R 4 only has an IPv 6 address and R 2 only has an IPv 4 address. l Two static NAT-PT translations are configured on router R 1 to allow bidirectional traffic between the two devices. 60

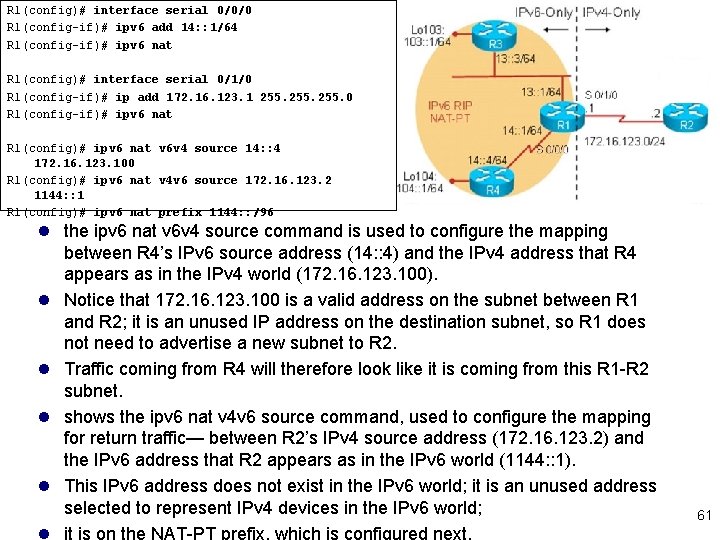
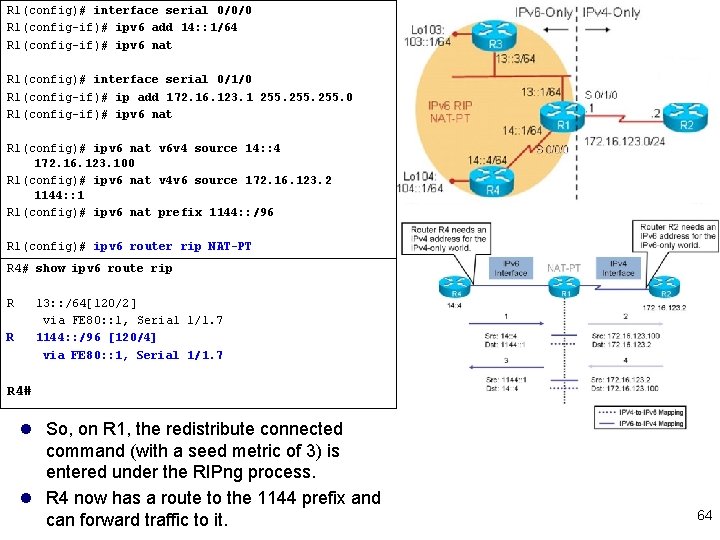
R 1(config)# interface serial 0/0/0 R 1(config-if)# ipv 6 add 14: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/1/0 R 1(config-if)# ip add 172. 16. 123. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# ipv 6 nat v 6 v 4 source 14: : 4 172. 16. 123. 100 R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 123. 2 1144: : 1 R 1(config)# ipv 6 nat prefix 1144: : /96 l the ipv 6 nat v 6 v 4 source command is used to configure the mapping between R 4’s IPv 6 source address (14: : 4) and the IPv 4 address that R 4 appears as in the IPv 4 world (172. 16. 123. 100). l Notice that 172. 16. 123. 100 is a valid address on the subnet between R 1 and R 2; it is an unused IP address on the destination subnet, so R 1 does not need to advertise a new subnet to R 2. l Traffic coming from R 4 will therefore look like it is coming from this R 1 -R 2 subnet. l shows the ipv 6 nat v 4 v 6 source command, used to configure the mapping for return traffic— between R 2’s IPv 4 source address (172. 16. 123. 2) and the IPv 6 address that R 2 appears as in the IPv 6 world (1144: : 1). l This IPv 6 address does not exist in the IPv 6 world; it is an unused address selected to represent IPv 4 devices in the IPv 6 world; l it is on the NAT-PT prefix, which is configured next. 61

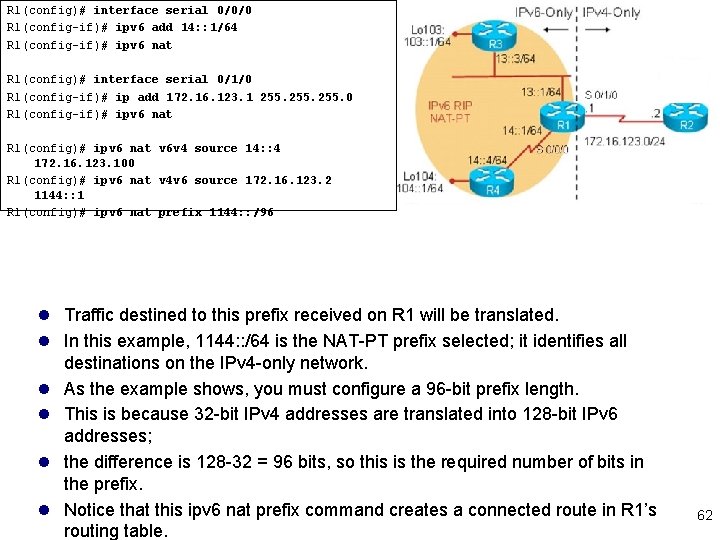
R 1(config)# interface serial 0/0/0 R 1(config-if)# ipv 6 add 14: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/1/0 R 1(config-if)# ip add 172. 16. 123. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# ipv 6 nat v 6 v 4 source 14: : 4 172. 16. 123. 100 R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 123. 2 1144: : 1 R 1(config)# ipv 6 nat prefix 1144: : /96 l Traffic destined to this prefix received on R 1 will be translated. l In this example, 1144: : /64 is the NAT-PT prefix selected; it identifies all destinations on the IPv 4 -only network. l As the example shows, you must configure a 96 -bit prefix length. l This is because 32 -bit IPv 4 addresses are translated into 128 -bit IPv 6 addresses; l the difference is 128 -32 = 96 bits, so this is the required number of bits in the prefix. l Notice that this ipv 6 nat prefix command creates a connected route in R 1’s routing table. 62
![R 1 show ipv 6 route static C C C 13 64 10 R 1# show ipv 6 route static C C C 13: : /64 [1/0]](https://slidetodoc.com/presentation_image/03087a41605c263292e53056315b72d5/image-63.jpg)
R 1# show ipv 6 route static C C C 13: : /64 [1/0] via Fast. Ethernet 0/0, directly connected 14: : /64 [1/0] via Serial 0/0/0, directly connected 1144: : /96 [0/0] via NV 10, directly connected R 1# l displays the output of the show ipv 6 route connected command, confirming that the NAT-PT 96 -bit prefix is there. l Notice that this prefix is directly connected to the interface NVI 0; l NVI is a NAT virtual interface and exists to allow NAT traffic flows. 63

R 1(config)# interface serial 0/0/0 R 1(config-if)# ipv 6 add 14: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/1/0 R 1(config-if)# ip add 172. 16. 123. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# ipv 6 nat v 6 v 4 source 14: : 4 172. 16. 123. 100 R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 123. 2 1144: : 1 R 1(config)# ipv 6 nat prefix 1144: : /96 R 1(config)# ipv 6 router rip NAT-PT R 1(config-rtr)# redistribute connected metric 3 R 4# show ipv 6 route rip R 13: : /64[120/2] via FE 80: : 1, Serial 1/1. 7 1144: : /96 [120/4] via FE 80: : 1, Serial 1/1. 7 R R 4# l So, on R 1, the redistribute connected command (with a seed metric of 3) is entered under the RIPng process. l R 4 now has a route to the 1144 prefix and can forward traffic to it. 64

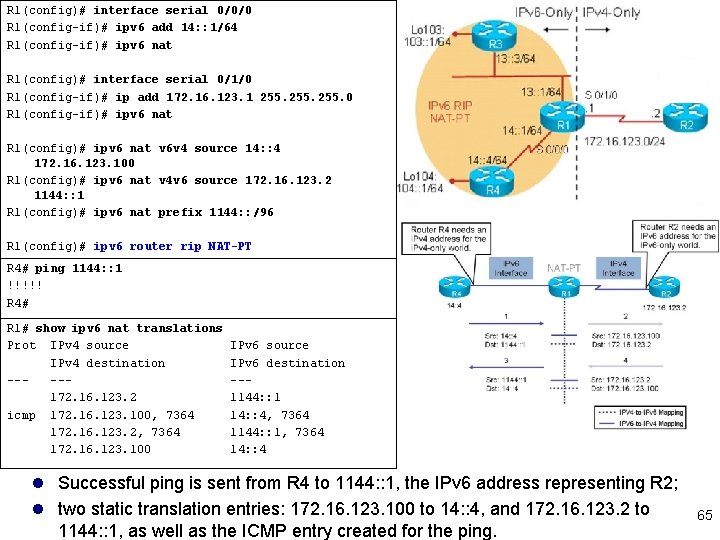
R 1(config)# interface serial 0/0/0 R 1(config-if)# ipv 6 add 14: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/1/0 R 1(config-if)# ip add 172. 16. 123. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# ipv 6 nat v 6 v 4 source 14: : 4 172. 16. 123. 100 R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 123. 2 1144: : 1 R 1(config)# ipv 6 nat prefix 1144: : /96 R 1(config)# ipv 6 router rip NAT-PT R 1(config-rtr)# R 4# ping 1144: : 1 redistribute connected metric 3 !!!!! R 4# R 1# show ipv 6 nat translations Prot IPv 4 source IPv 4 destination ----172. 16. 123. 2 icmp 172. 16. 123. 100, 7364 172. 16. 123. 2, 7364 172. 16. 123. 100 IPv 6 source IPv 6 destination --1144: : 1 14: : 4, 7364 1144: : 1, 7364 14: : 4 l Successful ping is sent from R 4 to 1144: : 1, the IPv 6 address representing R 2; l two static translation entries: 172. 16. 123. 100 to 14: : 4, and 172. 16. 123. 2 to 1144: : 1, as well as the ICMP entry created for the ping. 65

Dynamic NAT-PT for IPv 6 l With dynamic NAT-PT, addresses are allocated from an address pool, the same as is done with IPv 4 dynamic NAT. l And again, the commands have similar syntax to their IPv 4 NAT counterparts. l With dynamic NAT-PT, the NAT-PT router receives, for example, a packet with an IPv 6 destination address of an arbitrarily assigned 96 -bit prefix (the NAT-PT prefix), the same as it did with static NAT-PT. l This time though, instead of translating this to an IPv 4 address that was statically configured, the NAT-PT router translates it to an IPv 4 address from an address pool. 66

67

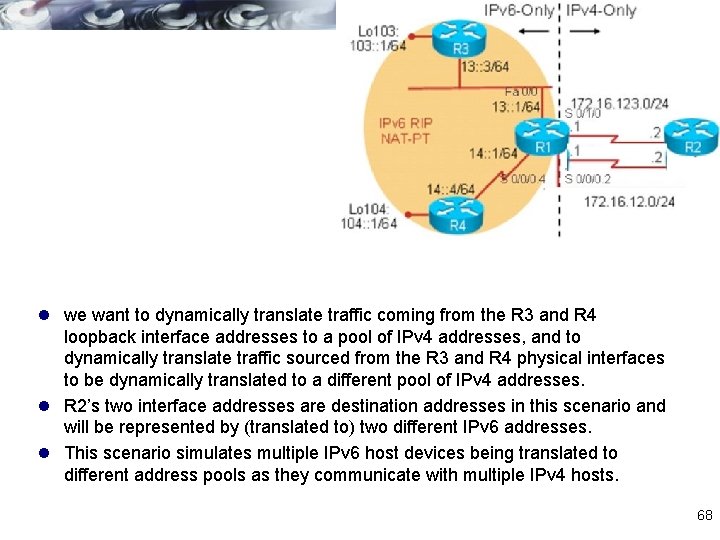
l we want to dynamically translate traffic coming from the R 3 and R 4 loopback interface addresses to a pool of IPv 4 addresses, and to dynamically translate traffic sourced from the R 3 and R 4 physical interfaces to be dynamically translated to a different pool of IPv 4 addresses. l R 2’s two interface addresses are destination addresses in this scenario and will be represented by (translated to) two different IPv 6 addresses. l This scenario simulates multiple IPv 6 host devices being translated to different address pools as they communicate with multiple IPv 4 hosts. 68

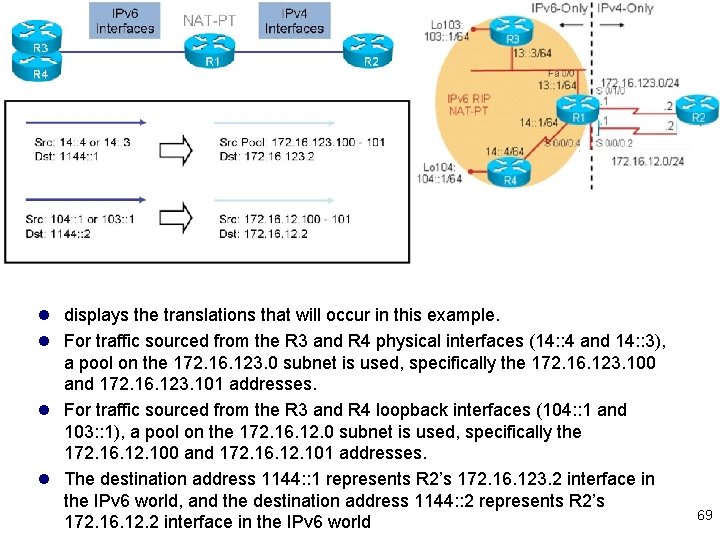
l displays the translations that will occur in this example. l For traffic sourced from the R 3 and R 4 physical interfaces (14: : 4 and 14: : 3), a pool on the 172. 16. 123. 0 subnet is used, specifically the 172. 16. 123. 100 and 172. 16. 123. 101 addresses. l For traffic sourced from the R 3 and R 4 loopback interfaces (104: : 1 and 103: : 1), a pool on the 172. 16. 12. 0 subnet is used, specifically the 172. 16. 12. 100 and 172. 16. 12. 101 addresses. l The destination address 1144: : 1 represents R 2’s 172. 16. 123. 2 interface in the IPv 6 world, and the destination address 1144: : 2 represents R 2’s 172. 16. 12. 2 interface in the IPv 6 world 69

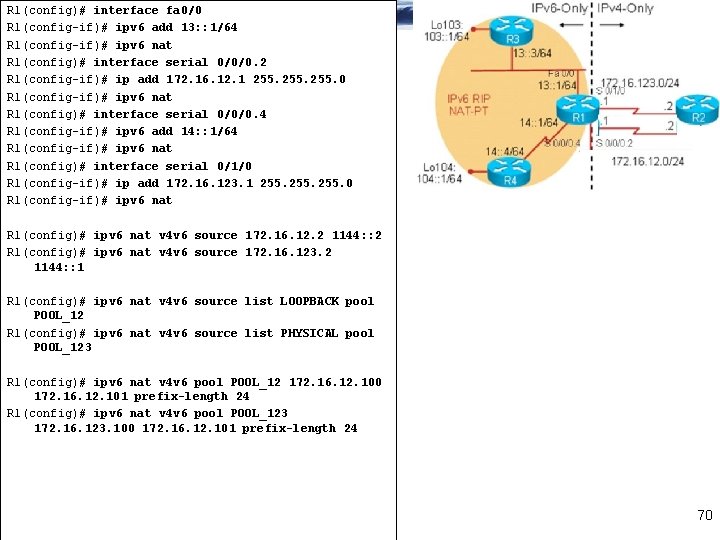
R 1(config)# interface fa 0/0 R 1(config-if)# ipv 6 add 13: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/0/0. 2 R 1(config-if)# ip add 172. 16. 12. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/0/0. 4 R 1(config-if)# ipv 6 add 14: : 1/64 R 1(config-if)# ipv 6 nat R 1(config)# interface serial 0/1/0 R 1(config-if)# ip add 172. 16. 123. 1 255. 0 R 1(config-if)# ipv 6 nat R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 12. 2 1144: : 2 R 1(config)# ipv 6 nat v 4 v 6 source 172. 16. 123. 2 1144: : 1 R 1(config)# ipv 6 nat v 4 v 6 source list LOOPBACK pool POOL_12 R 1(config)# ipv 6 nat v 4 v 6 source list PHYSICAL pool POOL_123 R 1(config)# ipv 6 nat v 4 v 6 pool POOL_12 172. 16. 12. 100 172. 16. 12. 101 prefix-length 24 R 1(config)# ipv 6 nat v 4 v 6 pool POOL_123 172. 16. 123. 100 172. 16. 12. 101 prefix-length 24 70

CIS 185 CCNP ROUTE Ch. 8 Implementing IPv 6 – Part 3 Rick Graziani Cabrillo College graziani@cabrillo. edu Last Updated: Fall 2010