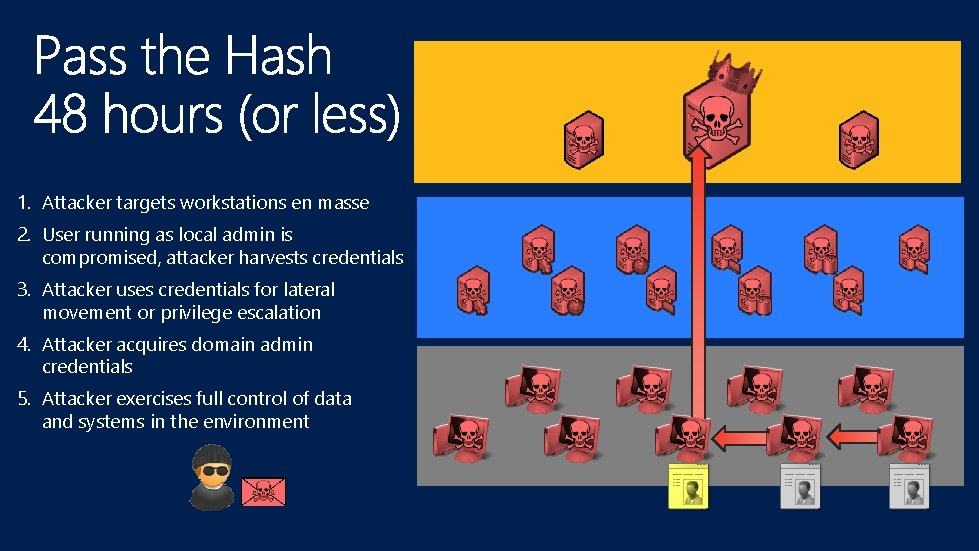
1 Attacker targets workstations en masse 2 User

















- Slides: 32








1. Attacker targets workstations en masse 2. User running as local admin is compromised, attacker harvests credentials 3. Attacker uses credentials for lateral movement or privilege escalation 4. Attacker acquires domain admin credentials 5. Attacker exercises full control of data and systems in the environment

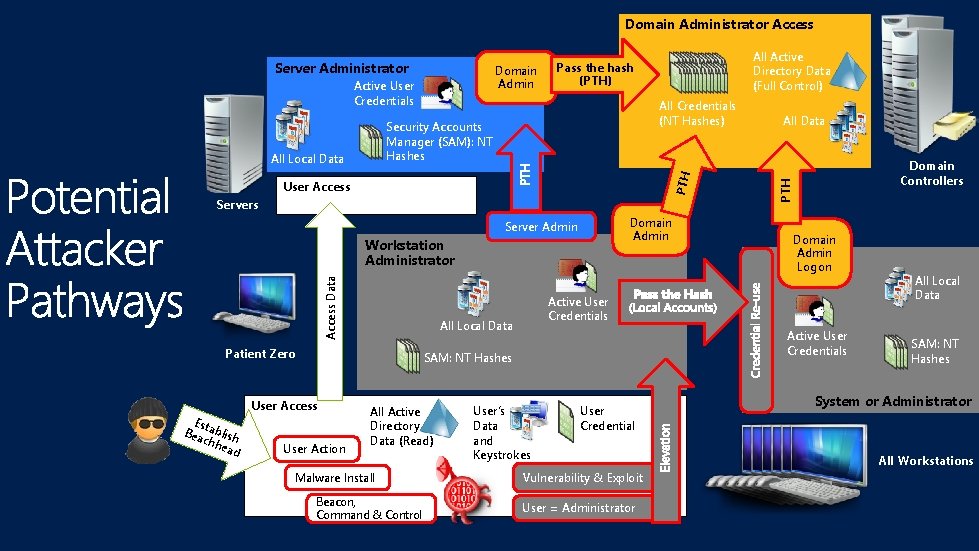
Domain Administrator Access Domain Admin Active User Credentials All Credentials (NT Hashes) Security Accounts Manager (SAM): NT Hashes PTH All Local Data All Active Directory Data (Full Control) Pass the hash (PTH) User Access Servers Domain Admin Server Admin Access Data Workstation Administrator Es Bea tablish chh ead User Action All Active Directory Data (Read) Malware Install Beacon, Command & Control Domain Admin Logon Active User Credentials SAM: NT Hashes User Access Domain Controllers Active User Credentials All Local Data Patient Zero All Data PTH Server Administrator User’s Data and Keystrokes User Credential Vulnerability & Exploit User = Administrator All Local Data SAM: NT Hashes System or Administrator All Workstations

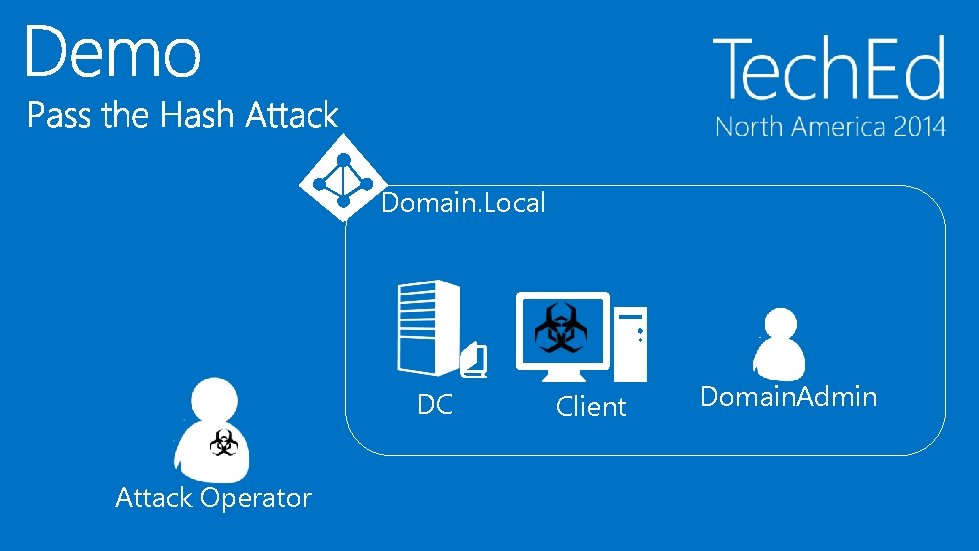
Domain. Local DC Attack Operator Client Domain. Admin


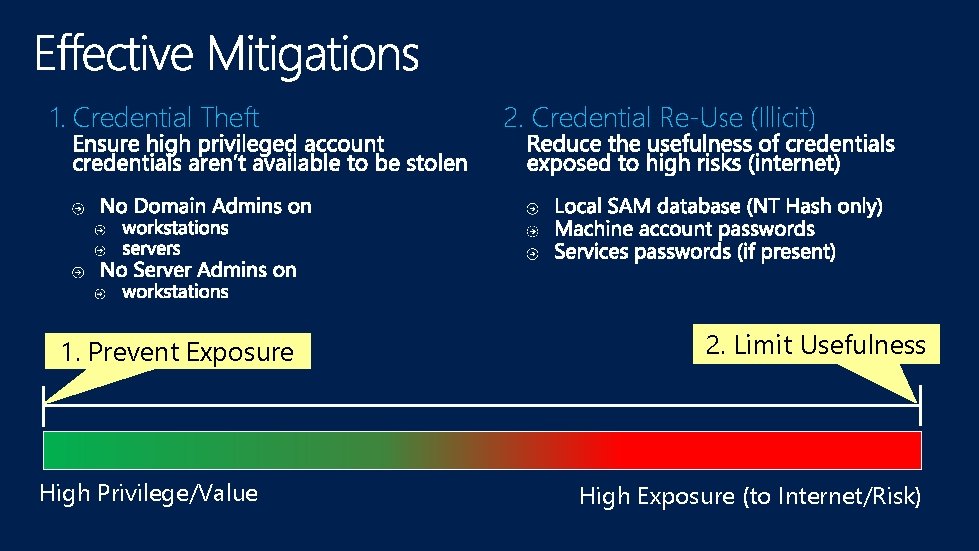
1. Credential Theft 1. Prevent Exposure High Privilege/Value 2. Credential Re-Use (Illicit) 2. Limit Usefulness High Exposure (to Internet/Risk)

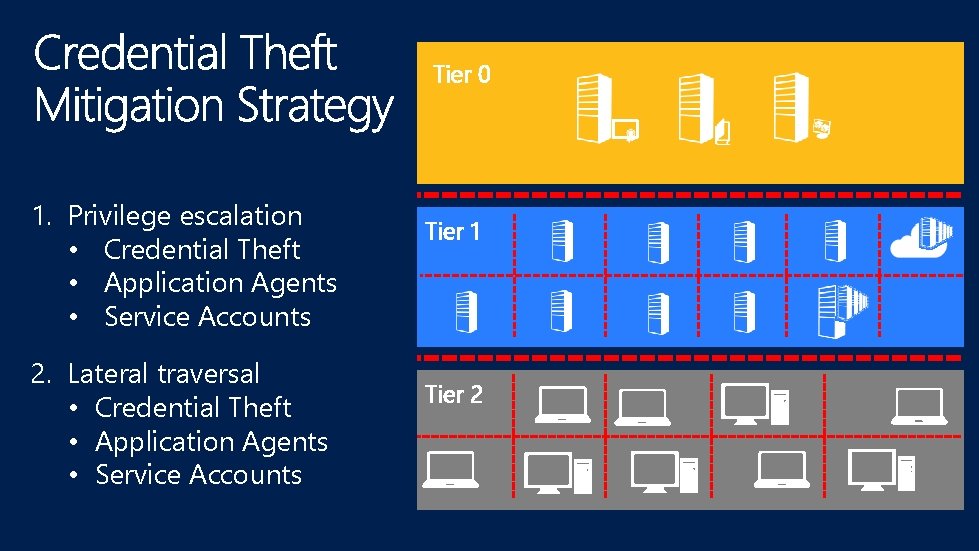
Tier 0 1. Privilege escalation • Credential Theft • Application Agents • Service Accounts 2. Lateral traversal • Credential Theft • Application Agents • Service Accounts Tier 1 Tier 2

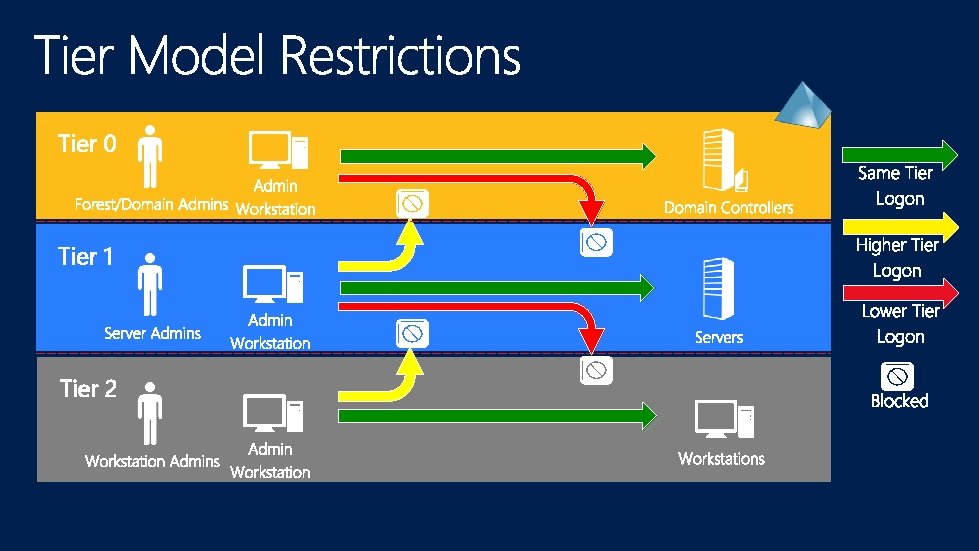
Tier 0 Tier 1 Tier 2

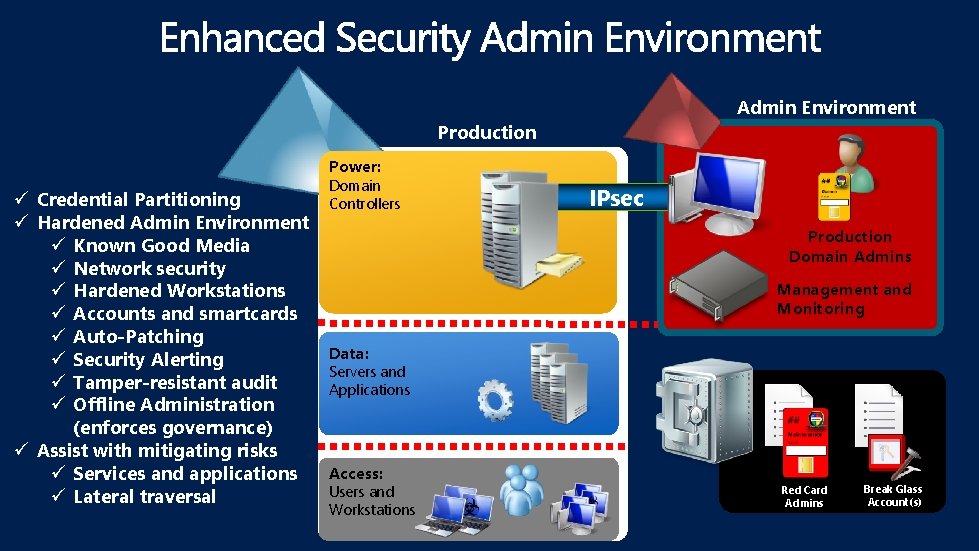
Admin Environment Production Power: ü Credential Partitioning ü Hardened Admin Environment ü Known Good Media ü Network security ü Hardened Workstations ü Accounts and smartcards ü Auto-Patching ü Security Alerting ü Tamper-resistant audit ü Offline Administration (enforces governance) ü Assist with mitigating risks ü Services and applications ü Lateral traversal Domain Controllers IPsec Production Domain Admins Management and Monitoring Data: Servers and Applications Access: Users and Workstations Red Card Admins Break Glass Account(s)


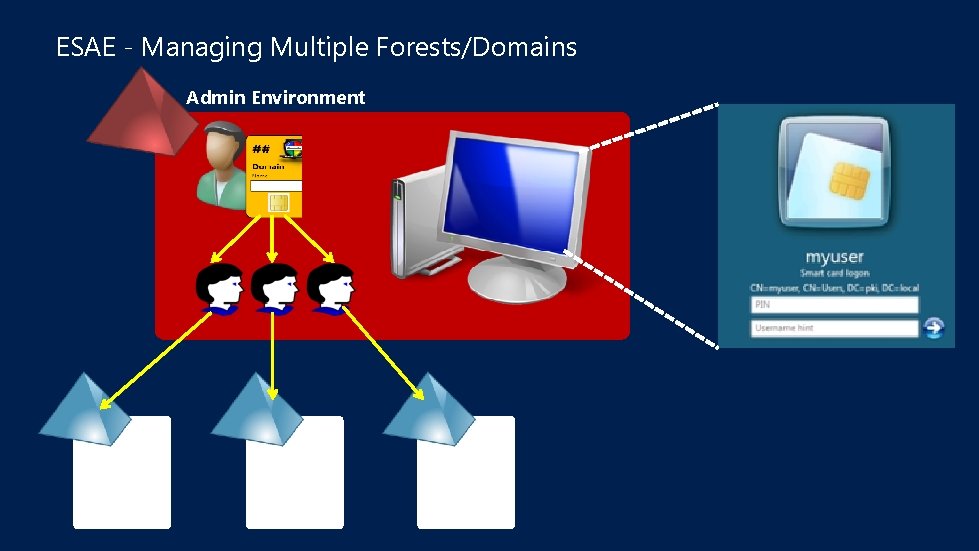
ESAE - Managing Multiple Forests/Domains Admin Environment

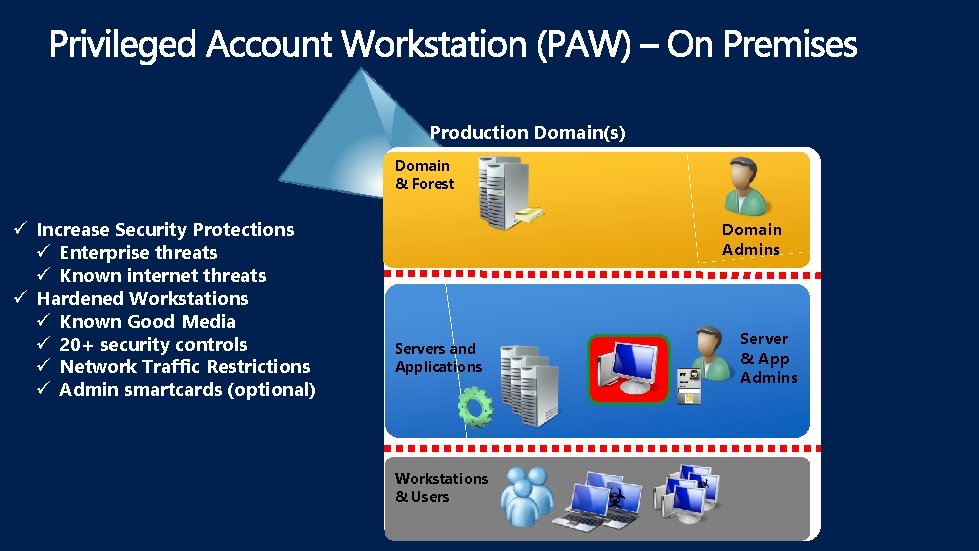
Production Domain(s) Domain & Forest ü Increase Security Protections ü Enterprise threats ü Known internet threats ü Hardened Workstations ü Known Good Media ü 20+ security controls ü Network Traffic Restrictions ü Admin smartcards (optional) Domain Admins Servers and Applications Workstations & Users Server & App Admins

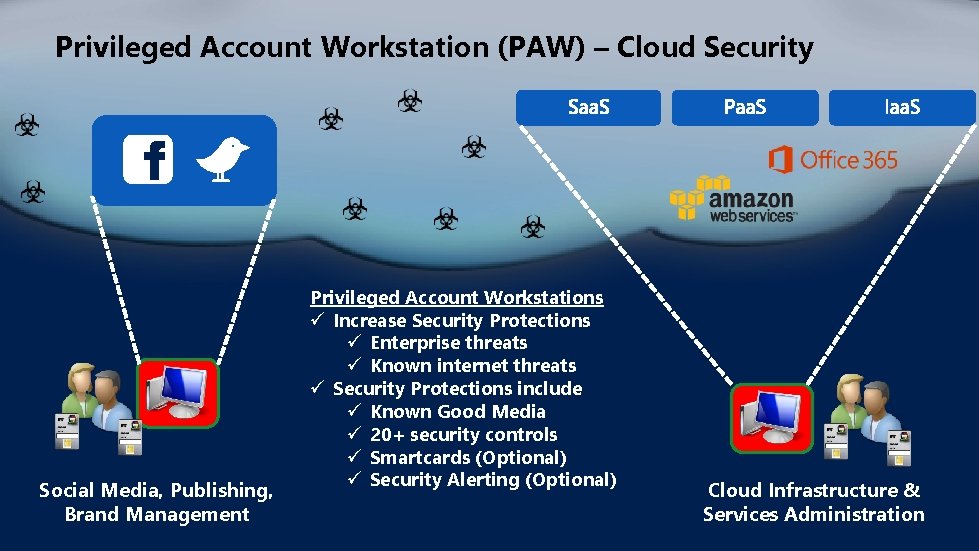
Privileged Account Workstation (PAW) – Cloud Security Social Media, Publishing, Brand Management Privileged Account Workstations ü Increase Security Protections ü Enterprise threats ü Known internet threats ü Security Protections include ü Known Good Media ü 20+ security controls ü Smartcards (Optional) ü Security Alerting (Optional) Cloud Infrastructure & Services Administration


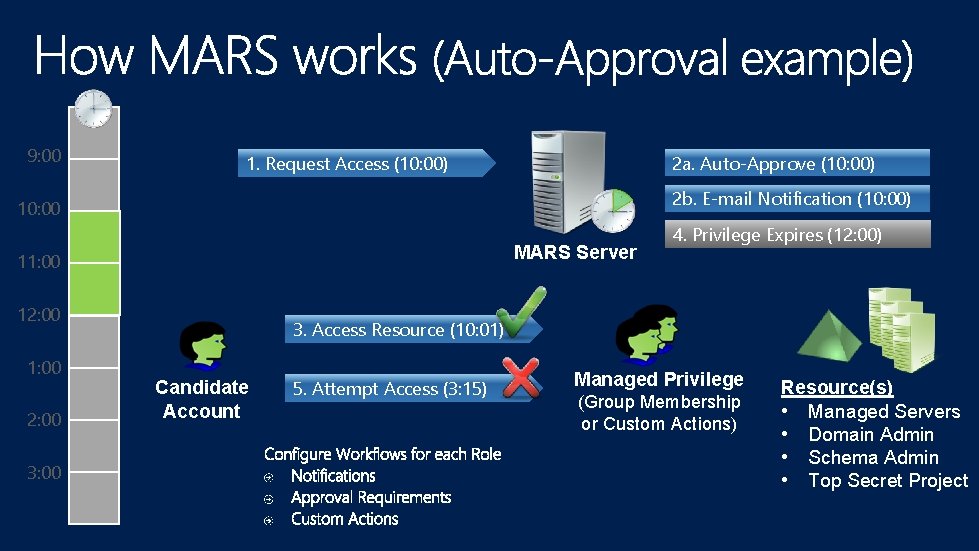
9: 00 1. Request Access (10: 00) 2 a. Auto-Approve (10: 00) 2 b. E-mail Notification (10: 00) 10: 00 MARS Server 11: 00 12: 00 1: 00 2: 00 3: 00 4. Privilege Expires (12: 00) 3. Access Resource (10: 01) Candidate Account 5. Attempt Access (3: 15) Managed Privilege (Group Membership or Custom Actions) Resource(s) • Managed Servers • Domain Admin • Schema Admin • Top Secret Project


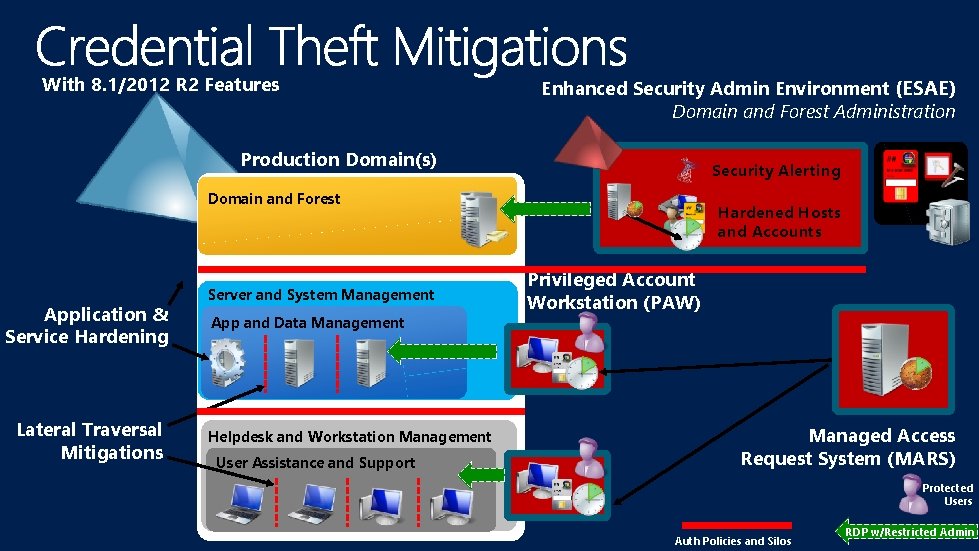
With 8. 1/2012 R 2 Features Enhanced Security Admin Environment (ESAE) Domain and Forest Administration Production Domain(s) Security Alerting Domain and Forest Application & Service Hardening Lateral Traversal Mitigations Server and System Management App and Data Management Helpdesk and Workstation Management User Assistance and Support Hardened Hosts and Accounts Privileged Account Workstation (PAW) Managed Access Request System (MARS) Protected Users Auth Policies and Silos RDP w/Restricted Admin

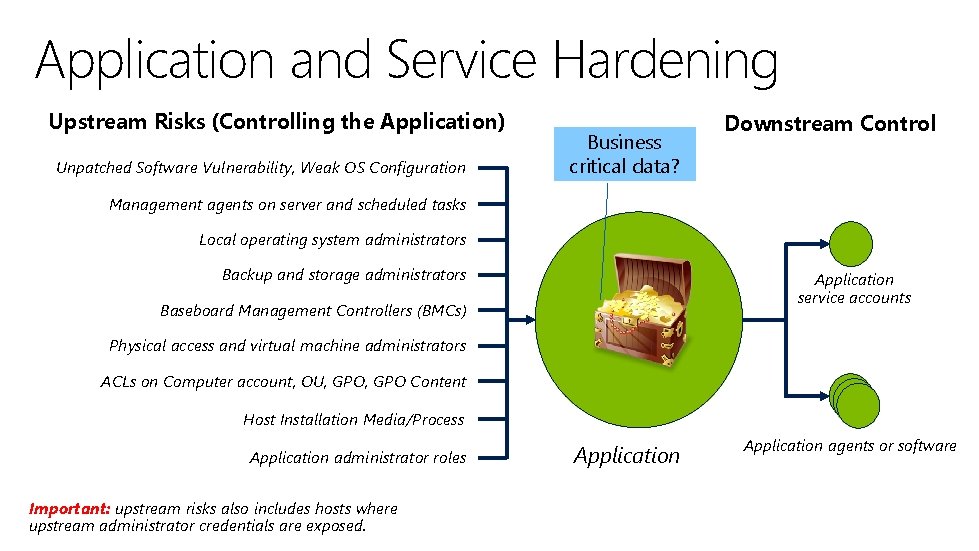
Application and Service Hardening Upstream Risks (Controlling the Application) Unpatched Software Vulnerability, Weak OS Configuration Business critical data? Downstream Control Management agents on server and scheduled tasks Local operating system administrators Backup and storage administrators Application service accounts Baseboard Management Controllers (BMCs) Physical access and virtual machine administrators ACLs on Computer account, OU, GPO Content Host Installation Media/Process Application administrator roles Important: upstream risks also includes hosts where upstream administrator credentials are exposed. Application agents or software Application 24




For More Information Windows Server 2012 R 2 http: //technet. microsoft. com/en-US/evalcenter/dn 205286 System Center 2012 R 2 http: //technet. microsoft. com/en-US/evalcenter/dn 205295 Azure Pack http: //www. microsoft. com/en-us/servercloud/products/windows-azure-pack Microsoft Azure http: //azure. microsoft. com/en-us/ Come Visit Us in the Microsoft Solutions Experience! Look for Datacenter and Infrastructure Management Tech. Expo Level 1 Hall CD

http: //channel 9. msdn. com/Events/Tech. Ed www. microsoft. com/learning http: //microsoft. com/technet http: //microsoft. com/msdn


