VIRUS AND SPY PROTECTION ADMINISTRATION Agenda Main topics














- Slides: 46

VIRUS AND SPY PROTECTION ADMINISTRATION

Agenda Main topics • Administration interface • Local user interface • Administrating scanning remotely • Tips • Updating databases • Handling infections Page 2

ADMINISTRATION INTERFACE

Remote Administration The Policy Manager Console offers two different graphical interfaces • Anti-Virus Mode • Optimized for administering F-Secure Anti-Virus Client Security • Advanced Mode • Used for deeper product configurations • Products other than AVCS have to be administered with this mode • Some settings are only available in this mode! Page 4

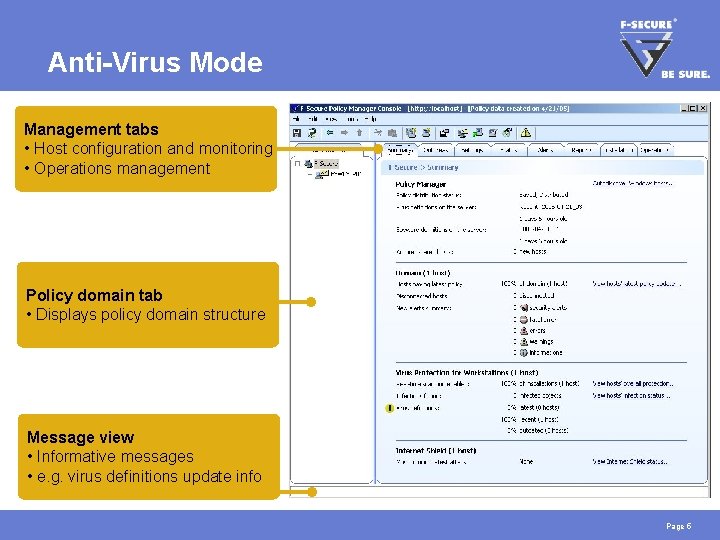
Anti-Virus Mode Management tabs • Host configuration and monitoring • Operations management Policy domain tab • Displays policy domain structure Message view • Informative messages • e. g. virus definitions update info Page 5

Advanced Mode Policy properties pane • Host configuration and monitoring • Operations management Product view pane • Provides most common settings • Functions differ for selected properties tabs (e. g. policy tab) Product help • Field focus help, if policy properties tab selected Message view • Informative messages • e. g. virus definitions update info Page 6

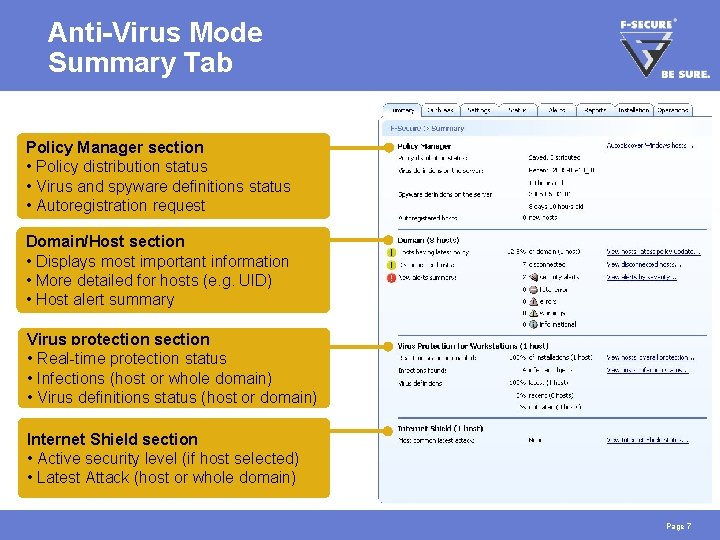
Anti-Virus Mode Summary Tab Policy Manager section • Policy distribution status • Virus and spyware definitions status • Autoregistration request Domain/Host section • Displays most important information • More detailed for hosts (e. g. UID) • Host alert summary Virus protection section • Real-time protection status • Infections (host or whole domain) • Virus definitions status (host or domain) Internet Shield section • Active security level (if host selected) • Latest Attack (host or whole domain) Page 7

Anti-Virus Mode Outbreak Tab Security News • Radar Security News from F-Secure • Shows what definitions needes to protect • Shows if hosts are updated Security News Details • Shows the selected news item in detail • Shows which hosts are connected Page 8

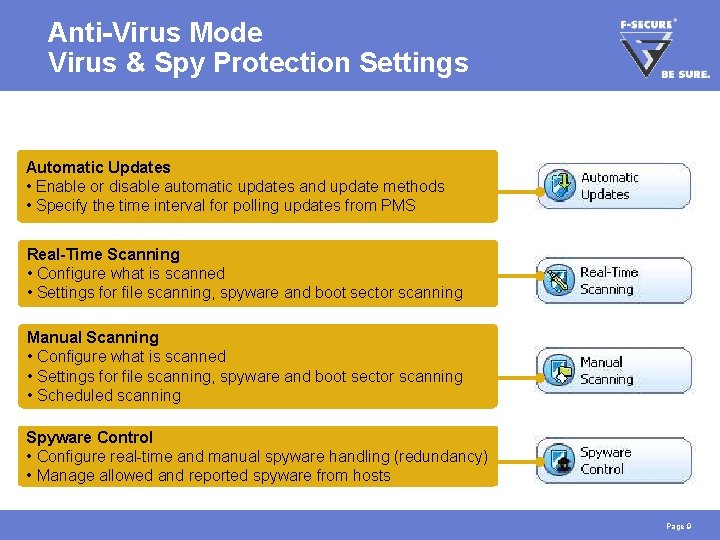
Anti-Virus Mode Virus & Spy Protection Settings Automatic Updates • Enable or disable automatic updates and update methods • Specify the time interval for polling updates from PMS Real-Time Scanning • Configure what is scanned • Settings for file scanning, spyware and boot sector scanning Manual Scanning • Configure what is scanned • Settings for file scanning, spyware and boot sector scanning • Scheduled scanning Spyware Control • Configure real-time and manual spyware handling (redundancy) • Manage allowed and reported spyware from hosts Page 9

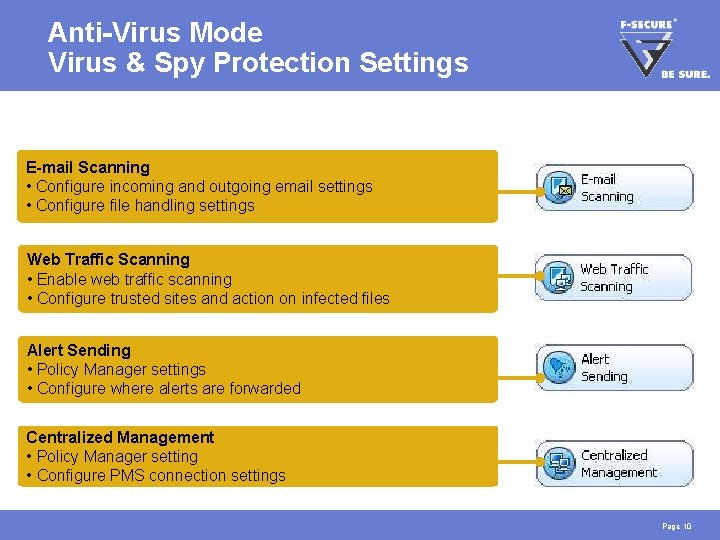
Anti-Virus Mode Virus & Spy Protection Settings E-mail Scanning • Configure incoming and outgoing email settings • Configure file handling settings Web Traffic Scanning • Enable web traffic scanning • Configure trusted sites and action on infected files Alert Sending • Policy Manager settings • Configure where alerts are forwarded Centralized Management • Policy Manager setting • Configure PMS connection settings Page 10

LOCAL USER INTERFACE

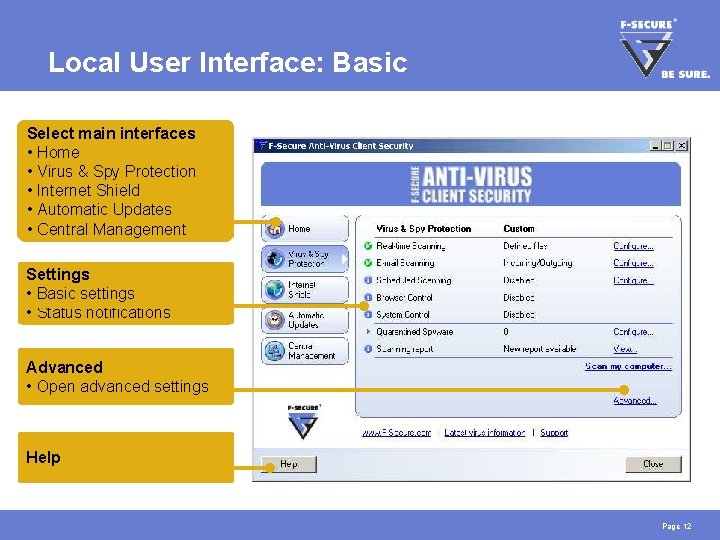
Local User Interface: Basic Select main interfaces • Home • Virus & Spy Protection • Internet Shield • Automatic Updates • Central Management Settings • Basic settings • Status notifications Advanced • Open advanced settings Help Page 12

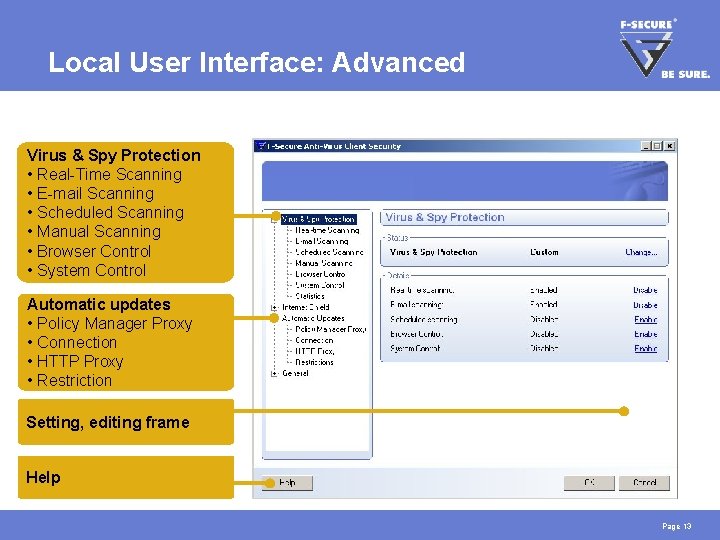
Local User Interface: Advanced Virus & Spy Protection • Real-Time Scanning • E-mail Scanning • Scheduled Scanning • Manual Scanning • Browser Control • System Control Automatic updates • Policy Manager Proxy • Connection • HTTP Proxy • Restriction Setting, editing frame Help Page 13

ADMINISTRATING SCANNING REMOTELY

Adminstering Virus and Spy Protection Finding the right level of security for a corporation is a challenge • In practice the administration is a balancing act between security and usability, as the tighter the security, the more the users and admin need to actively know about all things security related • F-Secure Anti-Virus Client Security and Policy Manager are tools to implement the decision the administrator makes Page 15

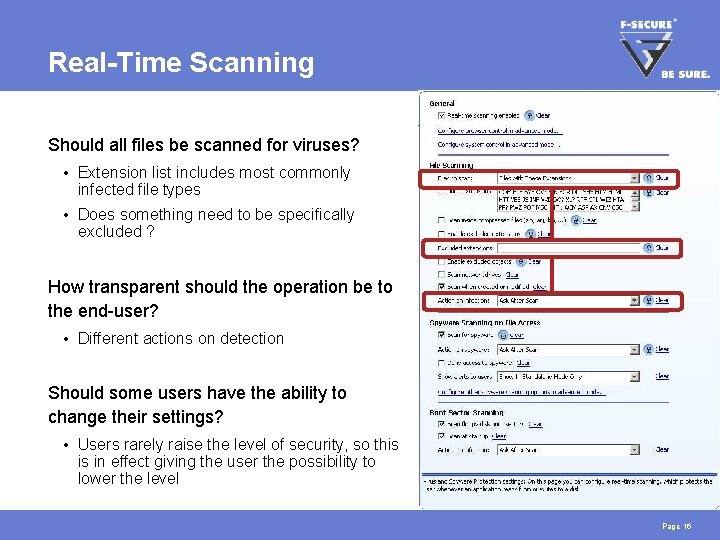
Real-Time Scanning Should all files be scanned for viruses? • Extension list includes most commonly infected file types • Does something need to be specifically excluded ? How transparent should the operation be to the end-user? • Different actions on detection Should some users have the ability to change their settings? • Users rarely raise the level of security, so this is in effect giving the user the possibility to lower the level Page 16

Manual Scanning Should manual scans be performed inside archives? • Archives cannot be disinfected! • If the scanning operation is configured transparent, the secondary action will be applied automatically (remove or delete archive) • Scanning archives has a performance impact! It is very important to run regular manual virus and spyware scans on all hosts! • For example through PMC operations • Scheduled scans include no spyware scanning! Page 17

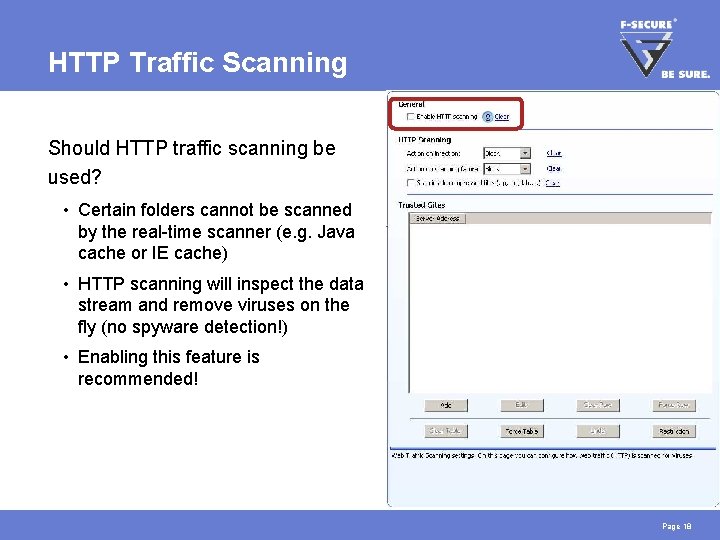
HTTP Traffic Scanning Should HTTP traffic scanning be used? • Certain folders cannot be scanned by the real-time scanner (e. g. Java cache or IE cache) • HTTP scanning will inspect the data stream and remove viruses on the fly (no spyware detection!) • Enabling this feature is recommended! Page 18

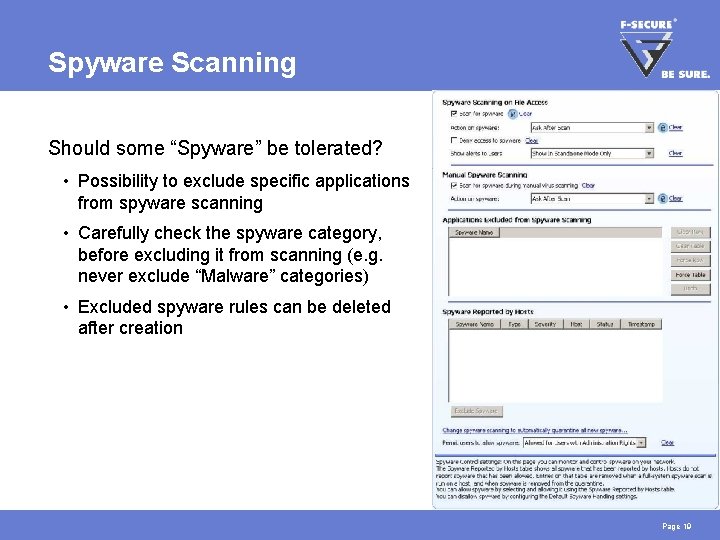
Spyware Scanning Should some “Spyware” be tolerated? • Possibility to exclude specific applications from spyware scanning • Carefully check the spyware category, before excluding it from scanning (e. g. never exclude “Malware” categories) • Excluded spyware rules can be deleted after creation Page 19

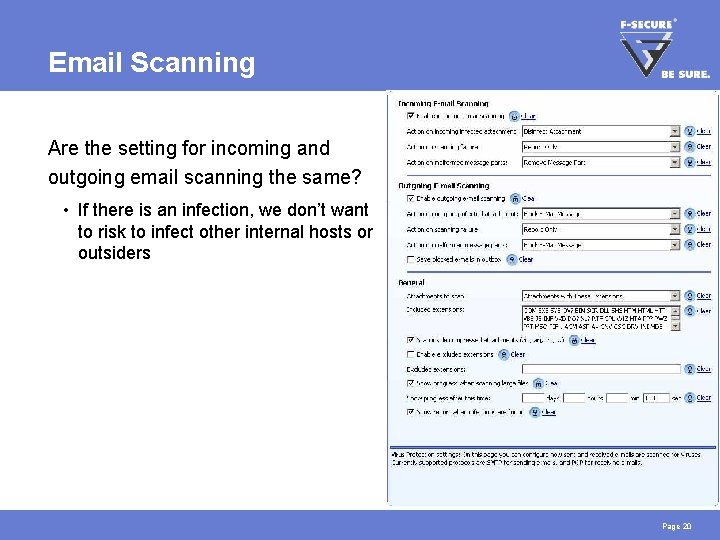
Email Scanning Are the setting for incoming and outgoing email scanning the same? • If there is an infection, we don’t want to risk to infect other internal hosts or outsiders Page 20

Monitoring Hosts: Status The Administrator has a number of different ways to follow what is happening on the hosts The Status leaf on Policy Manager Console shows the latest infection date, infection name, infected object, action taken for each host as well as the number of all time infections Page 21

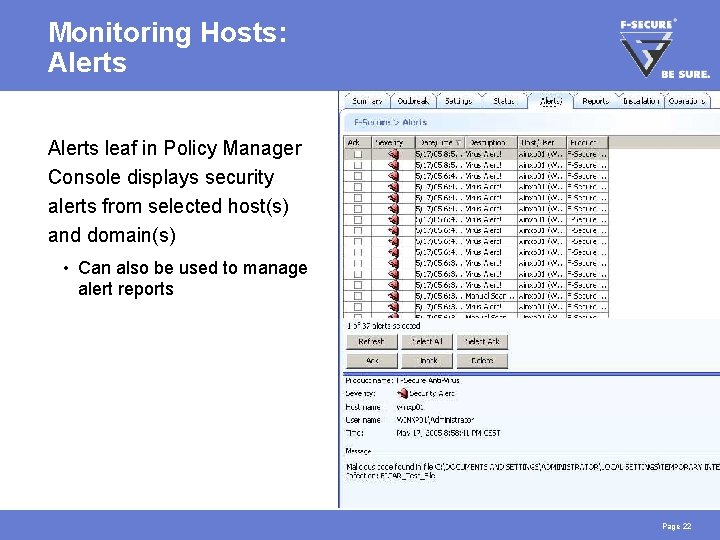
Monitoring Hosts: Alerts leaf in Policy Manager Console displays security alerts from selected host(s) and domain(s) • Can also be used to manage alert reports Page 22

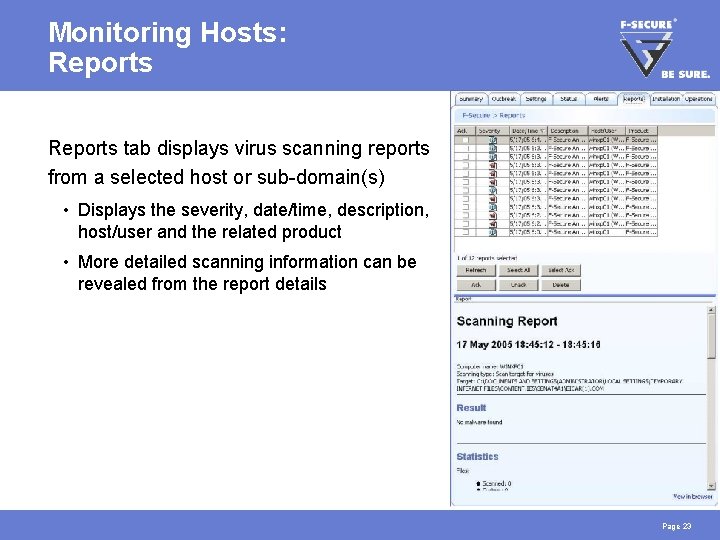
Monitoring Hosts: Reports tab displays virus scanning reports from a selected host or sub-domain(s) • Displays the severity, date/time, description, host/user and the related product • More detailed scanning information can be revealed from the report details Page 23

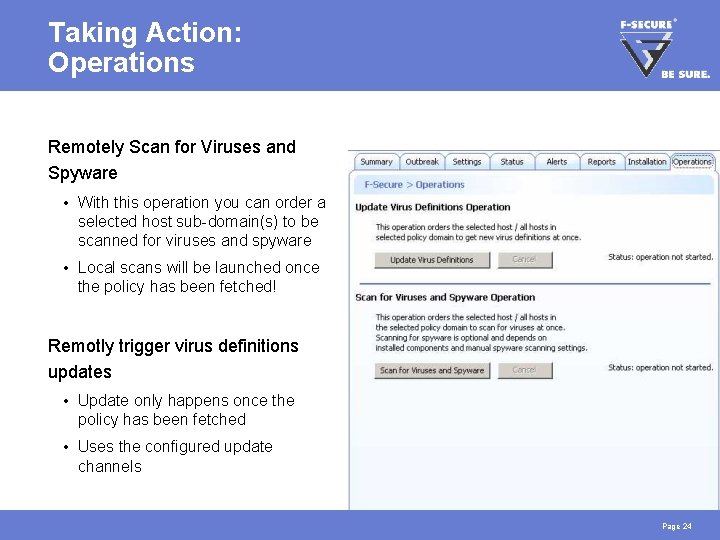
Taking Action: Operations Remotely Scan for Viruses and Spyware • With this operation you can order a selected host sub-domain(s) to be scanned for viruses and spyware • Local scans will be launched once the policy has been fetched! Remotly trigger virus definitions updates • Update only happens once the policy has been fetched • Uses the configured update channels Page 24

TIPS

Tips: Enabling HTTP Traffic Scanning HTTP traffic scanning is disabled by default • Enabling is easy Page 26

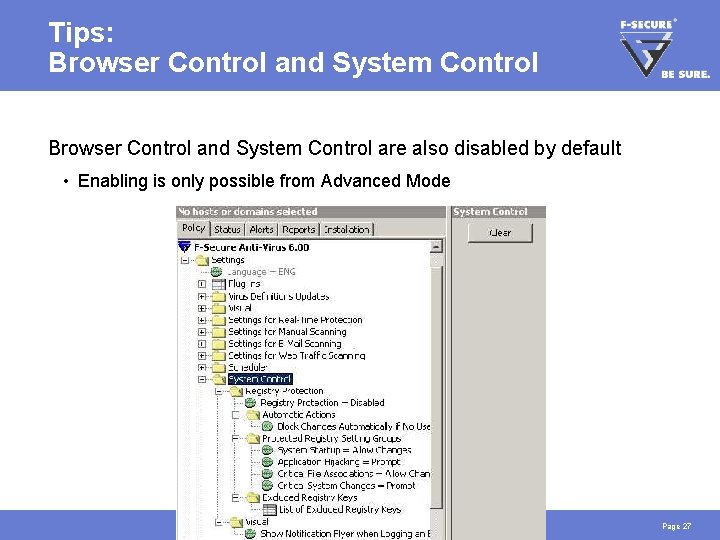
Tips: Browser Control and System Control are also disabled by default • Enabling is only possible from Advanced Mode Page 27

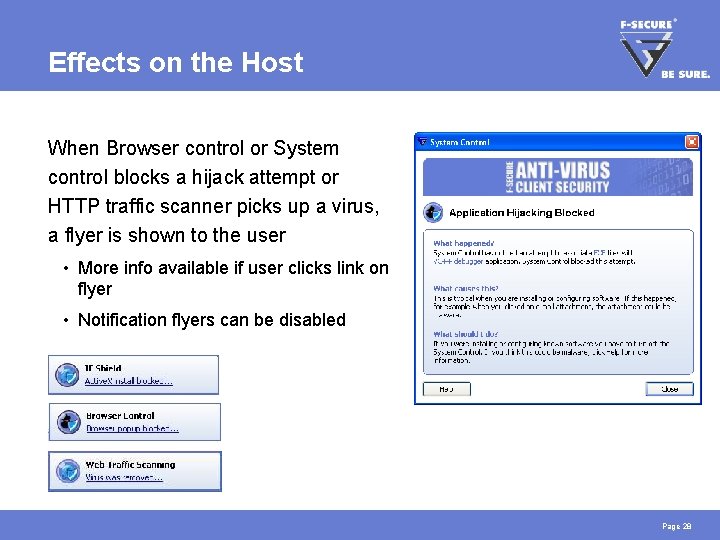
Effects on the Host When Browser control or System control blocks a hijack attempt or HTTP traffic scanner picks up a virus, a flyer is shown to the user • More info available if user clicks link on flyer • Notification flyers can be disabled Page 28

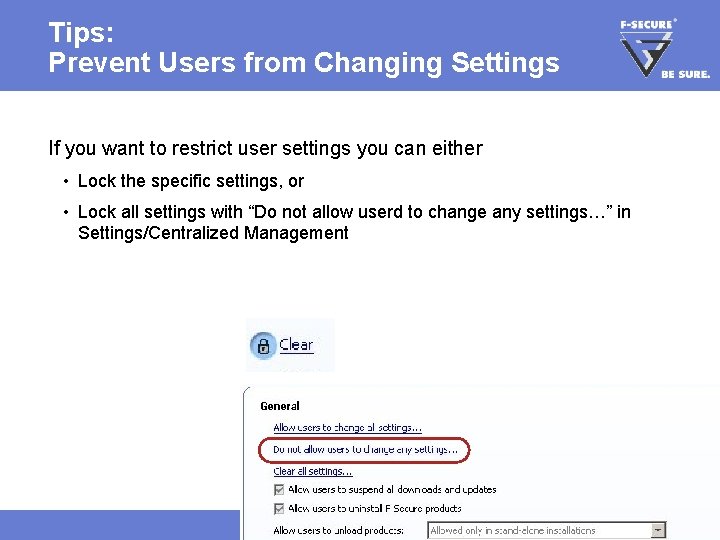
Tips: Prevent Users from Changing Settings If you want to restrict user settings you can either • Lock the specific settings, or • Lock all settings with “Do not allow userd to change any settings…” in Settings/Centralized Management Page 29

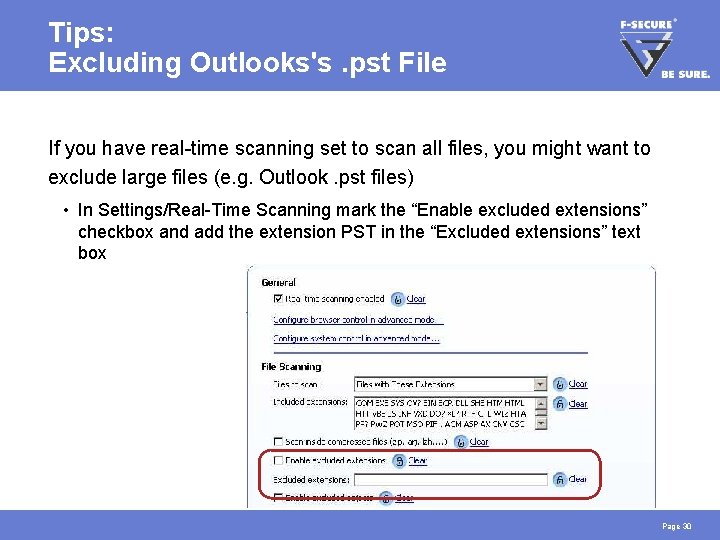
Tips: Excluding Outlooks's. pst File If you have real-time scanning set to scan all files, you might want to exclude large files (e. g. Outlook. pst files) • In Settings/Real-Time Scanning mark the “Enable excluded extensions” checkbox and add the extension PST in the “Excluded extensions” text box Page 30

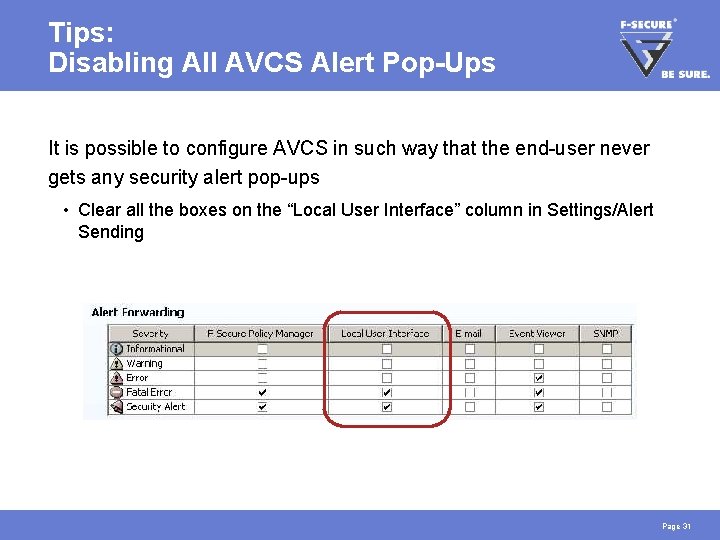
Tips: Disabling All AVCS Alert Pop-Ups It is possible to configure AVCS in such way that the end-user never gets any security alert pop-ups • Clear all the boxes on the “Local User Interface” column in Settings/Alert Sending Page 31

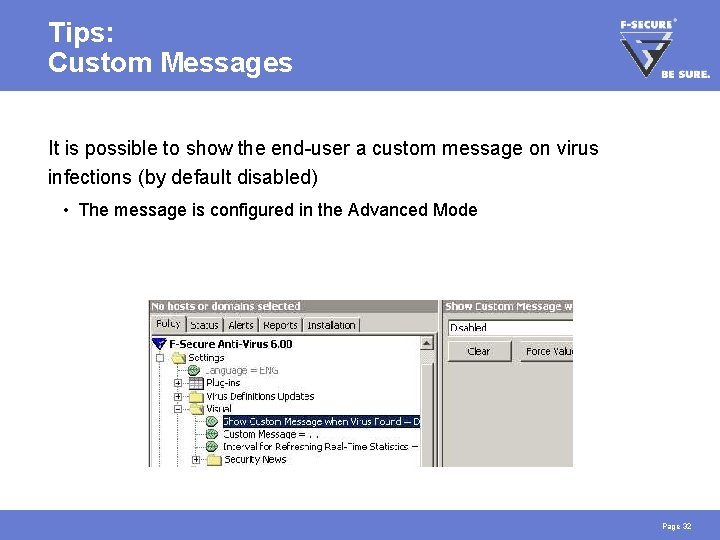
Tips: Custom Messages It is possible to show the end-user a custom message on virus infections (by default disabled) • The message is configured in the Advanced Mode Page 32

Tips: Testing Anti-Virus with eicar. com To test whether F-Secure Anti-Virus Client Security operates correctly, download a special test file that is detected by F-Secure Anti-Virus Client Security as though it were a real virus • http: //www. europe. f-secure. com/virus-info/eicar_test_file. shtml Page 33

UPDATING DATABASES

Database Updates Numerous methods to update virus definitions updates • Update changes in Anti-Virus Client Security 6! • FSMA no longer responsible for virus updates Components in the updating infrastructure • F-Secure Root Update Server • F-Secure Automatic Update Agent • If on PMS, connects to the Root Server on hourly bases and downloads the update differentially • If on host, connects to the PMS regularly – and if that fails, connects direcly to FSecure Root Update Server • F-Secure Automatic Update Server Page 35

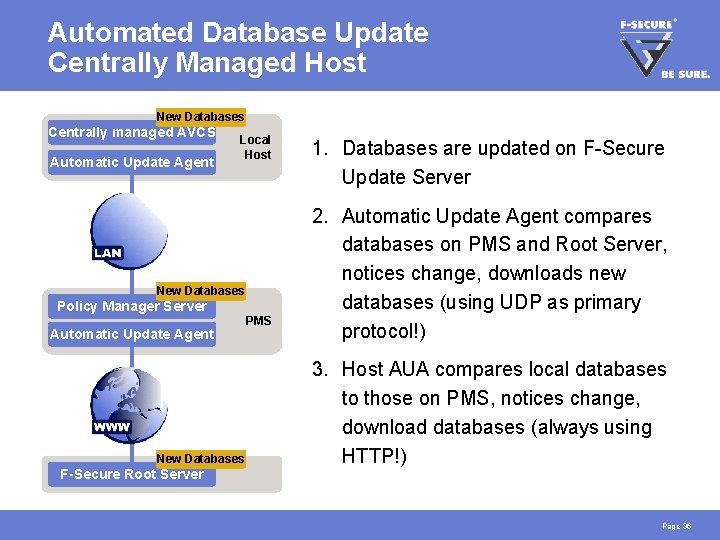
Automated Database Update Centrally Managed Host New Old Databases Centrally managed AVCS Automatic Update Agent Local Host New Old Databases Policy Manager Server Automatic Update Agent New Old Databases F-Secure Root Server PMS 1. Databases are updated on F-Secure Update Server 2. Automatic Update Agent compares databases on PMS and Root Server, notices change, downloads new databases (using UDP as primary protocol!) 3. Host AUA compares local databases to those on PMS, notices change, download databases (always using HTTP!) Page 36

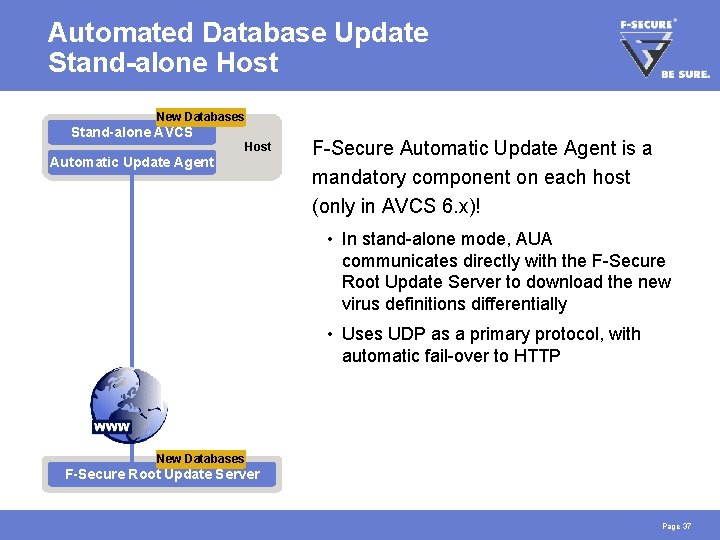
Automated Database Update Stand-alone Host New Old Databases Stand-alone AVCS Host Automatic Update Agent F-Secure Automatic Update Agent is a mandatory component on each host (only in AVCS 6. x)! • In stand-alone mode, AUA communicates directly with the F-Secure Root Update Server to download the new virus definitions differentially • Uses UDP as a primary protocol, with automatic fail-over to HTTP New Old Databases F-Secure Root Update Server Page 37

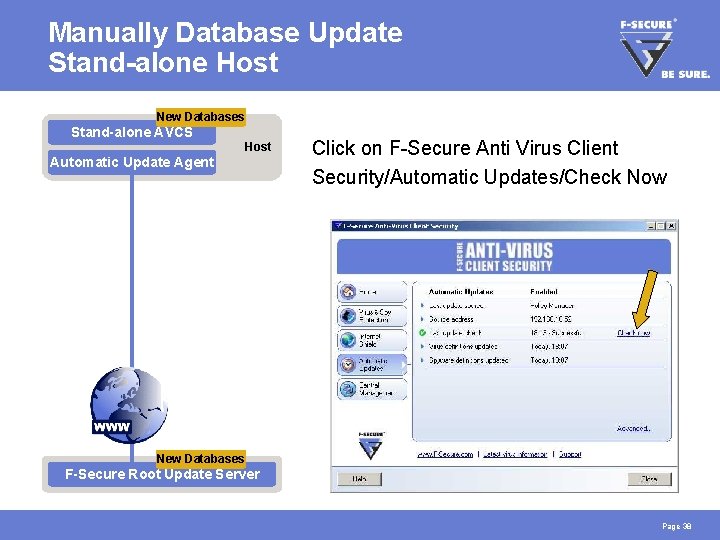
Manually Database Update Stand-alone Host New Old Databases Stand-alone AVCS Host Automatic Update Agent Click on F-Secure Anti Virus Client Security/Automatic Updates/Check Now New Old Databases F-Secure Root Update Server Page 38

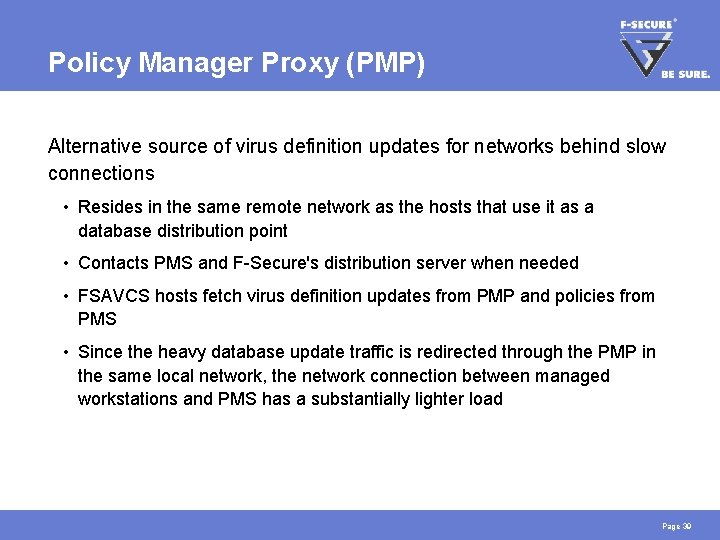
Policy Manager Proxy (PMP) Alternative source of virus definition updates for networks behind slow connections • Resides in the same remote network as the hosts that use it as a database distribution point • Contacts PMS and F-Secure's distribution server when needed • FSAVCS hosts fetch virus definition updates from PMP and policies from PMS • Since the heavy database update traffic is redirected through the PMP in the same local network, the network connection between managed workstations and PMS has a substantially lighter load Page 39

HANDLING INFECTIONS

Virus Outbreaks Monitor the global situation (on a daily basis) • http: //www. f-secure. com/weblog/ • http: //www. f-secure. com/virus-info/virus-news/ Update your knowledge on the latest threat, read virus descriptions from F-Secure website • Type of malware • Detection • Behavior • Removal Page 41

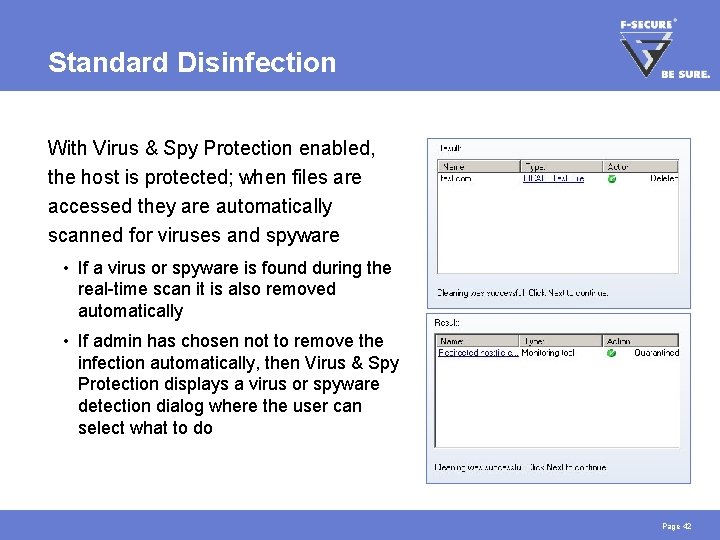
Standard Disinfection With Virus & Spy Protection enabled, the host is protected; when files are accessed they are automatically scanned for viruses and spyware • If a virus or spyware is found during the real-time scan it is also removed automatically • If admin has chosen not to remove the infection automatically, then Virus & Spy Protection displays a virus or spyware detection dialog where the user can select what to do Page 42

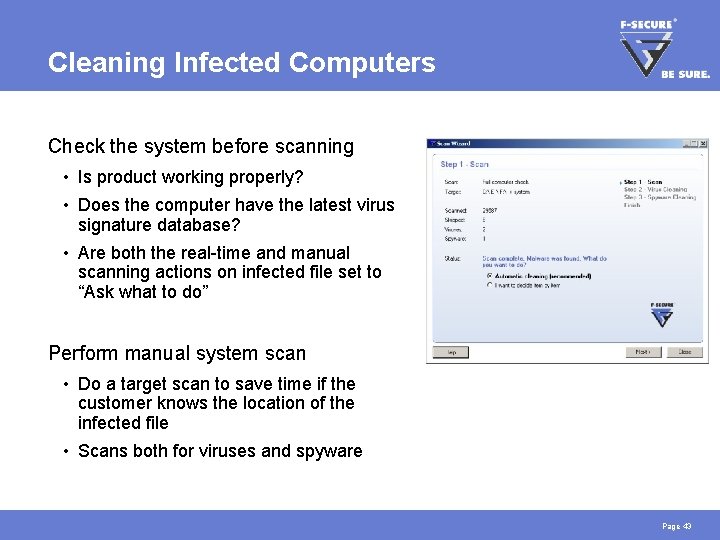
Cleaning Infected Computers Check the system before scanning • Is product working properly? • Does the computer have the latest virus signature database? • Are both the real-time and manual scanning actions on infected file set to “Ask what to do” Perform manual system scan • Do a target scan to save time if the customer knows the location of the infected file • Scans both for viruses and spyware Page 43

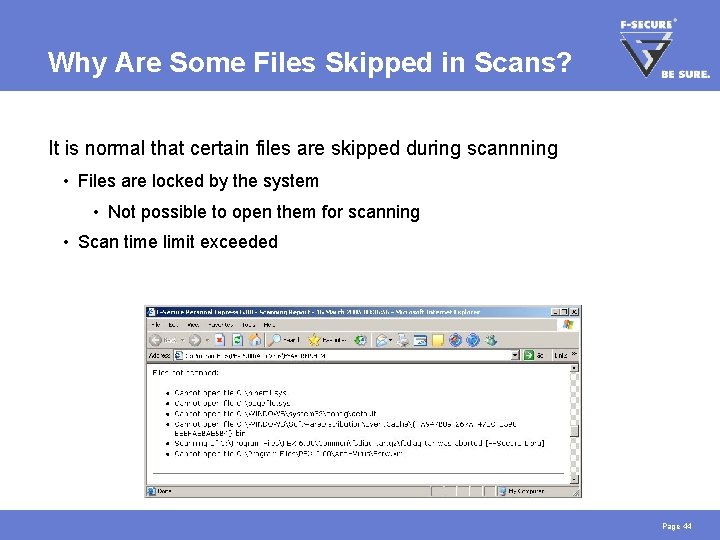
Why Are Some Files Skipped in Scans? It is normal that certain files are skipped during scannning • Files are locked by the system • Not possible to open them for scanning • Scan time limit exceeded Page 44

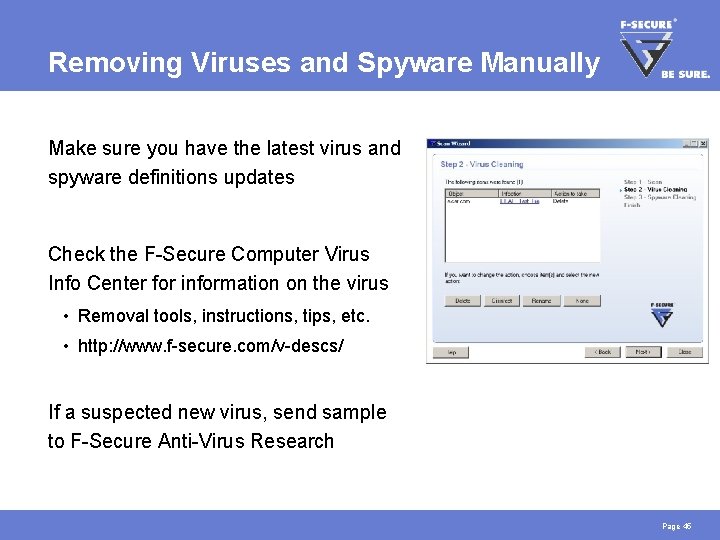
Removing Viruses and Spyware Manually Make sure you have the latest virus and spyware definitions updates Check the F-Secure Computer Virus Info Center for information on the virus • Removal tools, instructions, tips, etc. • http: //www. f-secure. com/v-descs/ If a suspected new virus, send sample to F-Secure Anti-Virus Research Page 45

Summary Main topics • Administration interface • Local user interface • Administrating Scanning remotely • Updating databases • Handling infections Page 46
 Spy vs spy font
Spy vs spy font Hr meeting agenda topics
Hr meeting agenda topics Agenda sistemica y agenda institucional
Agenda sistemica y agenda institucional U-2 incident cartoon
U-2 incident cartoon Walter todd wick
Walter todd wick Spy - card party game взлом
Spy - card party game взлом Anstrack spy tool
Anstrack spy tool Finfisher download
Finfisher download They say he is spy rewrite in the other voice
They say he is spy rewrite in the other voice I spy simple machines
I spy simple machines Spy aware
Spy aware Samuel townsend
Samuel townsend Spy hansen
Spy hansen Spy addon
Spy addon Si spy net work, big fedjaw iog link kyxogy
Si spy net work, big fedjaw iog link kyxogy Opc data spy
Opc data spy Types of main idea
Types of main idea Future will
Future will Void main int main
Void main int main Measles and mumps virus
Measles and mumps virus Bacteria virus fungi and parasites
Bacteria virus fungi and parasites Structure of bacteria and virus
Structure of bacteria and virus Virus and related threats
Virus and related threats Surprising reversal strategy
Surprising reversal strategy Research topics and objectives
Research topics and objectives Classification and division
Classification and division Advanced topics in software engineering
Advanced topics in software engineering Cause and effect essays topics
Cause and effect essays topics Phrases for advantages and disadvantages essay
Phrases for advantages and disadvantages essay Quantitative research problem
Quantitative research problem Computer and society topics
Computer and society topics International trade and finance topics
International trade and finance topics Ib sports science topic 4
Ib sports science topic 4 Ib sports exercise and health science
Ib sports exercise and health science Factor isolating question examples
Factor isolating question examples Global citizenship education topics and learning objectives
Global citizenship education topics and learning objectives Meaning of wages and salary
Meaning of wages and salary Vietnam meteorological and hydrological administration
Vietnam meteorological and hydrological administration Difference between administration and management
Difference between administration and management Linux operation and administration chapter 8
Linux operation and administration chapter 8 Public and private administration
Public and private administration Sapna suri
Sapna suri Intravenous medication administration pretest
Intravenous medication administration pretest According to kimball richman and copen administration is
According to kimball richman and copen administration is Institute of public administration and management
Institute of public administration and management Concept of wage and salary administration
Concept of wage and salary administration Principles of organization and administration of guidance
Principles of organization and administration of guidance