spys tool tiger what is spy spionage or








- Slides: 9

spy's tool tiger

what is spy? spionage or spying involves a government or individual obtaining information considered secret or confidential without the permission of the holder of the information. [1] Espionage is inherently clandestine, as it is taken for granted that it is unwelcome and, in many cases illegal and punishable by law. It is a subset of intelligence gathering, which otherwise may be conducted from public sources and using perfectly legal and ethical means. It is crucial to distinguish espionage from intelligence gathering, as the latter does not necessarily involve espionage, but often collates open-source information. Espionage is often part of an institutional effort by a government or commercial concern. However, the term is generally associated with state spying on potential or actual enemies primarily for military purposes. Spying involving corporations is known as industrial espionage.

what is spy? One of the most effective ways to gather data and information about the enemy (or potential enemy) is by infiltrating the enemy's ranks. This is the job of the spy (espionage agent). Spies can bring back all sorts of information concerning the size and strength of an enemy army. They can also find dissidents within the enemy's forces and influence them to defect. In times of crisis, spies can also be used to steal technology and to sabotage the enemy in various ways. Counterintelligence operatives can feed false information to enemy spies, protecting important domestic secrets, and preventing attempts at subversion. Nearly every country has very strict laws concerning espionage, and the penalty for being caught is often severe. However, the benefits that can be gained through espionage are generally great enough that most governments and many large corporations make use of it to varying degrees. Further information on clandestine HUMINT (human intelligence) information collection techniques is available, including discussions of operational techniques, asset recruiting, and the tradecraft used to collect this information.

famous spys

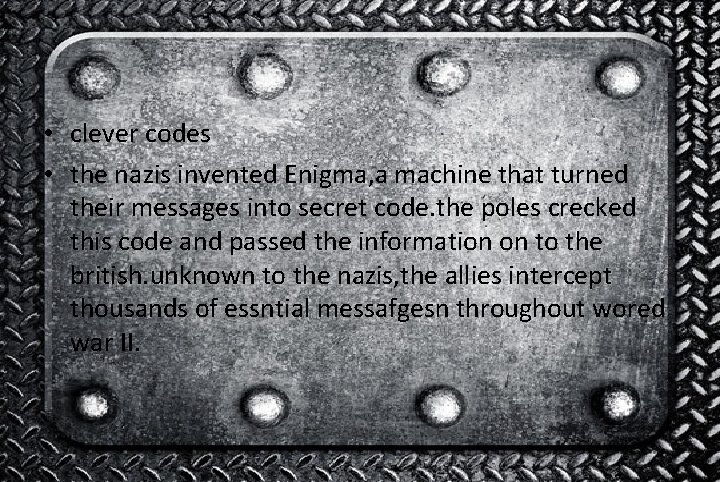
• clever codes • the nazis invented Enigma, a machine that turned their messages into secret code. the poles crecked this code and passed the information on to the british. unknown to the nazis, the allies intercept thousands of essntial messafgesn throughout wored war II.

• dangerous messages • this mark II radio set was used by a secret agent to transmit messages to the allies. this method ofcommunication was very dangerous for the agent, because the enemy could trace the signal back to the radio and its opertor.

• spy purse • working from behind enemy lines, radio opertor yvonne cormeau anged to send more than 400 coded messages to the allies between 1943 and the end of the war. she used a secret compartment in her purse to hide her code sheets.

Present • today's spies agents as they are often known, still gather top-secret information, but they ues very dofferent technoiogy. on the ground, they communicate using the smallest concealed radios. In the air, they use surveillance planes and satellites to monitor what is happening around the world. •

• mini communications • since world war II, communications technology has tiny become more sophisticated. the circuits of radios transmitters are now tiny enough to be concealed inside a working pen.