1 FINFISHER Fin Spy 3 10 Product Training







































































- Slides: 190

1 FINFISHER: Fin. Spy 3. 10 Product Training

Table of Content 2 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

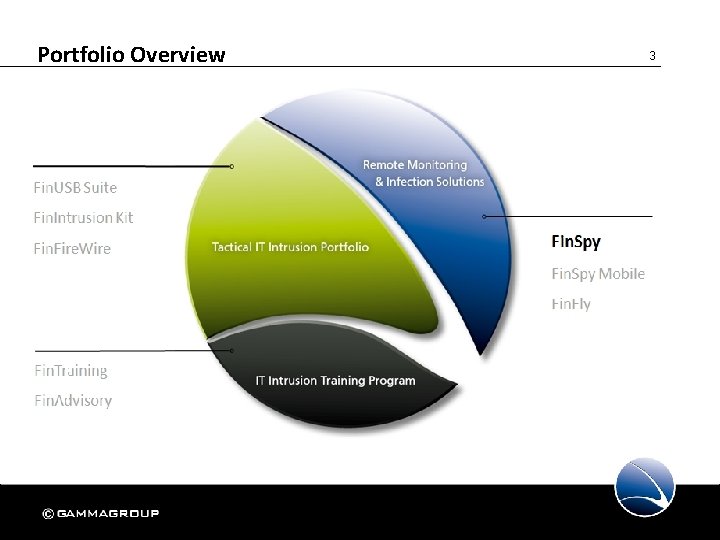
Portfolio Overview 3

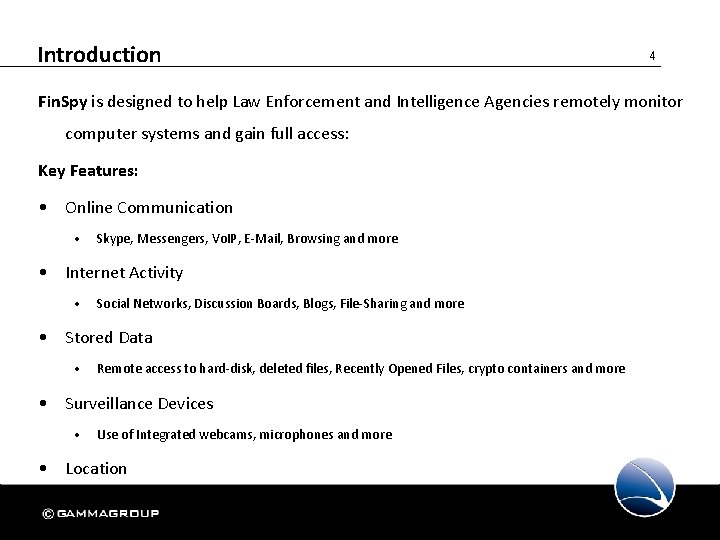
Introduction 4 Fin. Spy is designed to help Law Enforcement and Intelligence Agencies remotely monitor computer systems and gain full access: Key Features: • Online Communication • Skype, Messengers, Vo. IP, E-Mail, Browsing and more • Internet Activity • Social Networks, Discussion Boards, Blogs, File-Sharing and more • Stored Data • Remote access to hard-disk, deleted files, Recently Opened Files, crypto containers and more • Surveillance Devices • Use of Integrated webcams, microphones and more • Location

Introduction Strategic use of the Fin. Spy System: • IT Intrusion System • Internal Monitoring System • Covert Surveillance Device • Remote Control System 5

Fin. Spy – Components 6

Fin. Spy Agent 7 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – Components • Provides Graphical User Interface for Fin. Spy System • Shows Target List • Provides Interface for Target Analysis • Allows Target Configuration • Facilitates Target Updates • Enables Target Trojan Creation • Facilitates Creation of differing Infection Techniques 8

Fin. Spy Agent – Contents • Overview • Target List • Target Options • Evidence Protection • Target Creation • Infection Techniques • Analyses 9

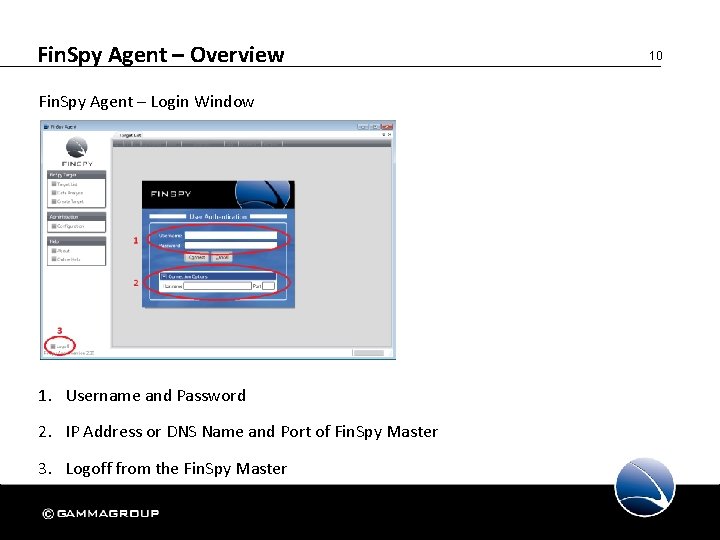
Fin. Spy Agent – Overview Fin. Spy Agent – Login Window 1. Username and Password 2. IP Address or DNS Name and Port of Fin. Spy Master 3. Logoff from the Fin. Spy Master 10

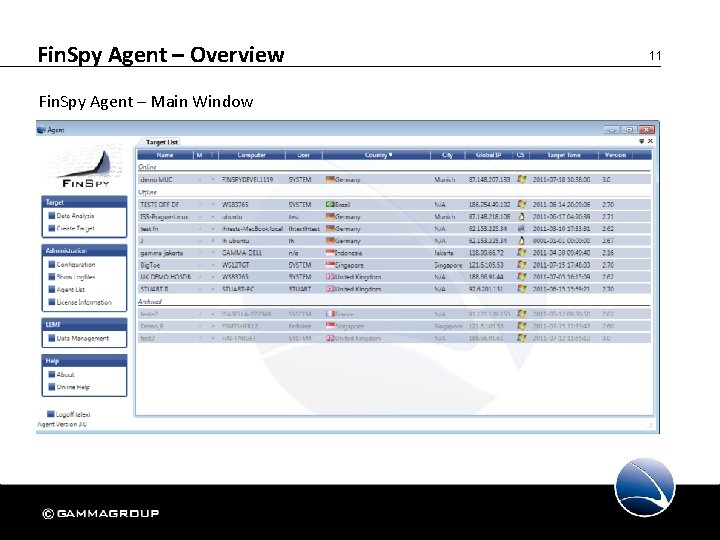
Fin. Spy Agent – Overview Fin. Spy Agent – Main Window 11

Fin. Spy Agent – Overview The Fin. Spy Agent Main Window offers the following functionalities: • Data Analysis – Analysis of selected or multiple Targets • Create Target – Wizard to create a new Target Trojan • Configuration – Basic Settings for Fin. Spy Agent and Fin. Spy Master • Show Logfiles – To view the Logfiles on the Fin. Spy Master • Agent List – To view which Agents are connected to which Target(s) • License Information – To view the actual License and Import one • LEMF – Data Management – To configure the LEMF • About – Shows the Fin. Spy Version and License • Online Help – Visit Support Website • Logoff – Disconnect the Fin. Spy Agent from Fin. Spy Master 12

Fin. Spy Agent 13 1. Introduction 2. Fin. Spy Agent § Target List 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

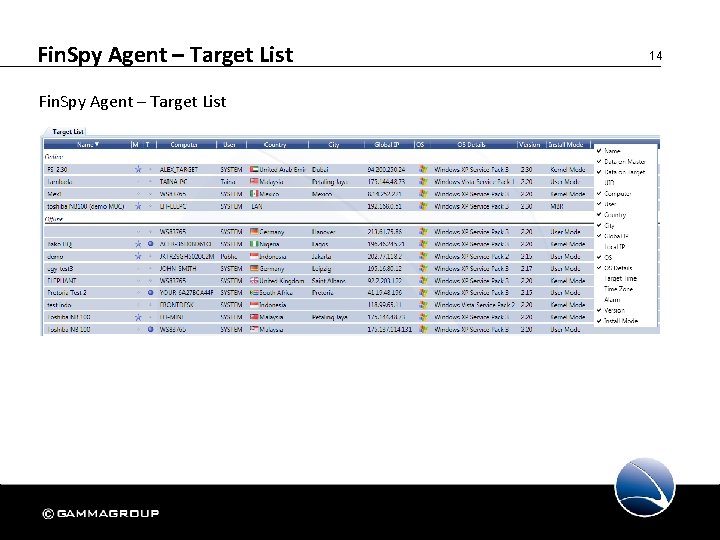
Fin. Spy Agent – Target List 14

Fin. Spy Agent – Target List The Fin. Spy Agent Target List displays information about a Target. • Fin. Spy Target Name • Unique Fin. Spy System Name of Target System • Username under which the Fin. Spy Infection operates • Country & City in which the Fin. Spy Targets ISP Access point is located • Global IP & Public IP address of the Fin. Spy Target • Operating System including Service Pack • Target Time & Target Time Zone • Software Version of the Fin. Spy Target • Install Mode (MBR, Kernel Mode, User Mode) 15

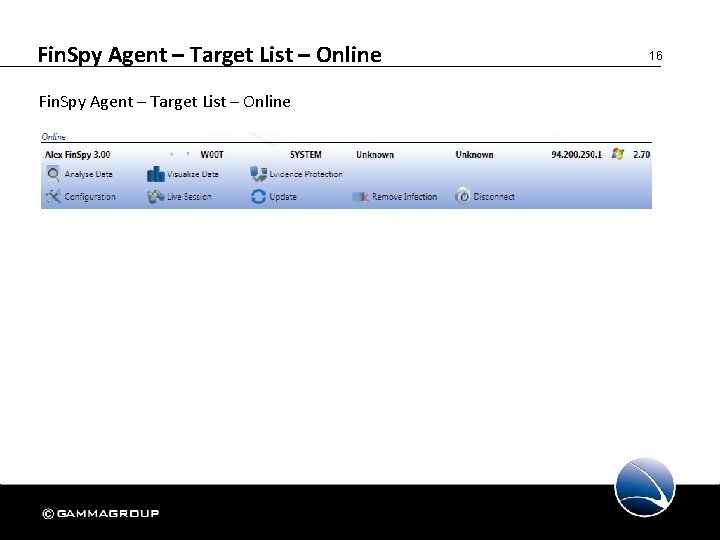
Fin. Spy Agent – Target List – Online 16

Fin. Spy Agent – Target List – Online 17 The Online List of Targets offers the following functionalities to manage, monitor and reconfigure an active Fin. Spy Target: • Analyse Data • Configuration • Visualize Data • Live Session • Evidence Protection • Download Now • Update • Remove Infection • Disconnect

Fin. Spy Agent – Target List – Offline 18

Fin. Spy Agent – Target List – Offline 19 The Offline List of Targets offers the following functionalities to manage and monitor a Fin. Spy Target: • Analyse Data • Visualize Data • Evidence Protection • Configuration • Remove Infection

Fin. Spy Agent – Target List – Archived 20 The Archived List of Targets offers the following functionalities to manage a Fin. Spy Target, where, the infection was removed but data is still on the Fin. Spy Master Server: • Analyse Data • Visualize Data • Evidence Protection • Remove Data

Fin. Spy Agent – Target List – Target Licensing 21 If the maximum number of infection is reached, the Target is unavailable as long as no license is freed an infected Target is uninfected. • First come – first serve principle

Fin. Spy Agent – Target List – Recorded Data Availability 22 Symbols indicate availability of new data 1. Star indicates Data on Fin. Spy Master is available 2. Bullet indicates Data on Fin. Spy Target is available for download to Master Server

Fin. Spy Agent 23 1. Introduction 2. Fin. Spy Agent § Target Analysis 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – Target Analysis • All or Selected recorded data can be shown or replayed • Data is stored on the Fin. Spy Master • Data can be viewed, deleted, exported and commented on 24

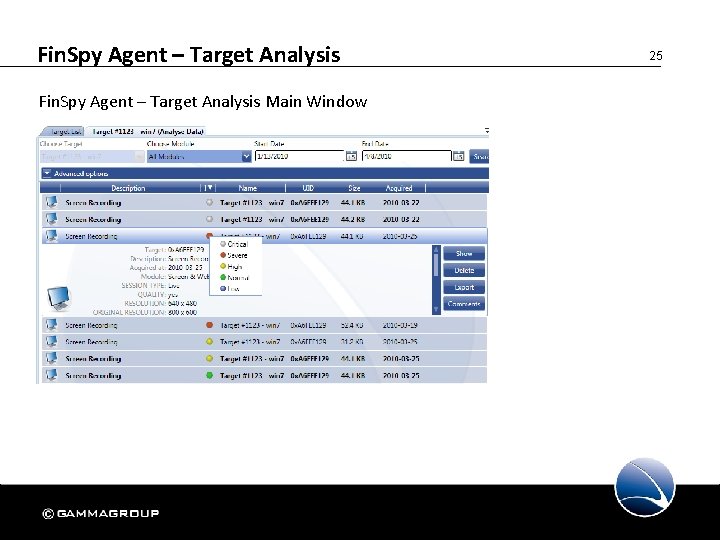
Fin. Spy Agent – Target Analysis Main Window 25

Fin. Spy Agent – Target Analysis The Fin. Spy Agent Target List Main Window shows the following information: • Identifies the Infection module (device/application) • An importance level can be associated with specific stored data • Fin. Spy Target Name • Unique internal Fin. Spy System reference to the Specific Fin. Spy Target • Size of the stored data set in bytes • The date when the data was recorded on the Target PC 26

Fin. Spy Agent – Target Analysis Possible actions each entry: • Opens & shows the recorded data • Deletes the data set from the Fin. Spy Master Server • The data can be exported to the Fin. Spy Agent computer. • Comments to the data can be stored 27

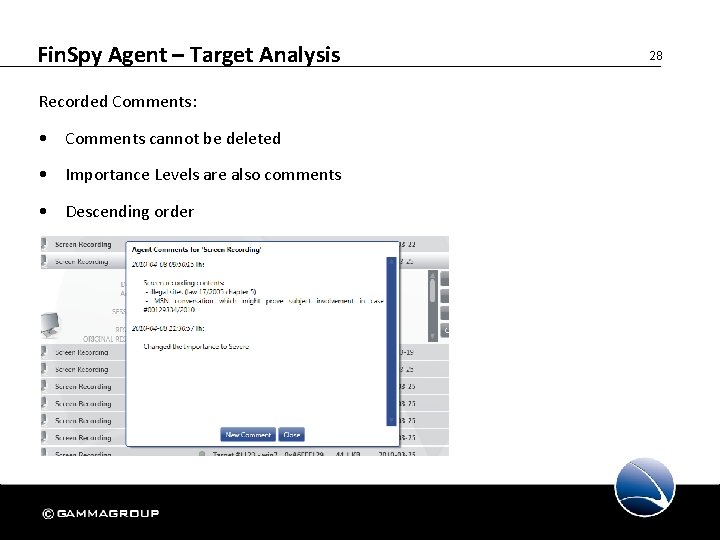
Fin. Spy Agent – Target Analysis Recorded Comments: • Comments cannot be deleted • Importance Levels are also comments • Descending order 28

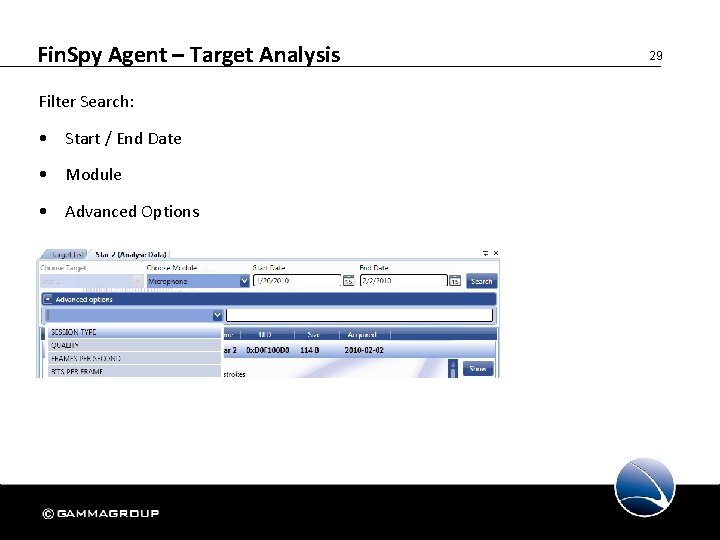
Fin. Spy Agent – Target Analysis Filter Search: • Start / End Date • Module • Advanced Options 29

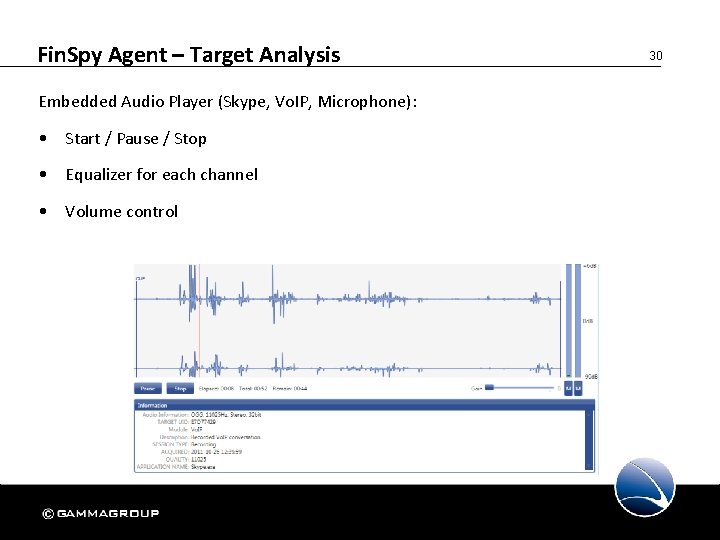
Fin. Spy Agent – Target Analysis Embedded Audio Player (Skype, Vo. IP, Microphone): • Start / Pause / Stop • Equalizer for each channel • Volume control 30

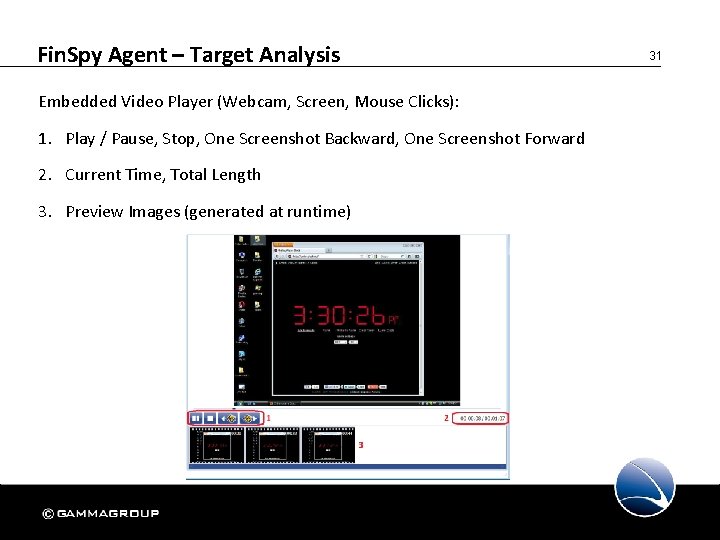
Fin. Spy Agent – Target Analysis Embedded Video Player (Webcam, Screen, Mouse Clicks): 1. Play / Pause, Stop, One Screenshot Backward, One Screenshot Forward 2. Current Time, Total Length 3. Preview Images (generated at runtime) 31

Fin. Spy Agent – Target Analysis – Hands-On: 32

Fin. Spy Agent – Target Analysis – Hands-On: • Select a Target • Search for Microphone Recordings only • Open Microphone Recording • Change Priority Level to High • Write a Comment 33

Fin. Spy Agent 34 1. Introduction 2. Fin. Spy Agent § Visualize Data 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – Visualize Data Analyzing Data on a graphical way. 35

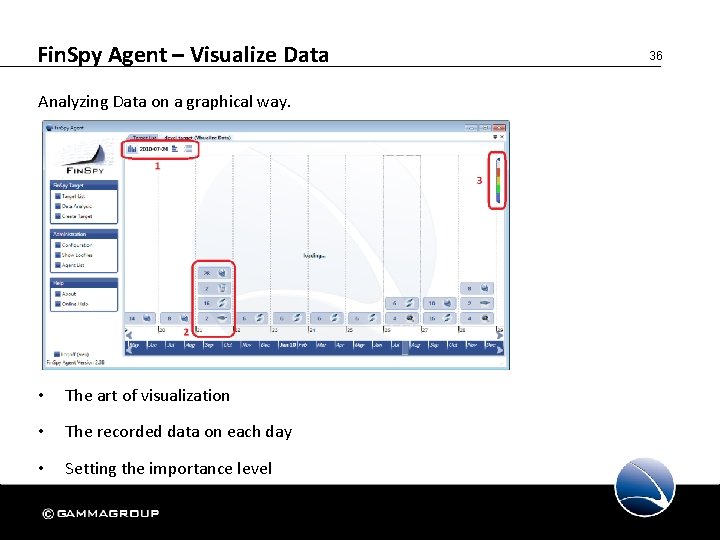
Fin. Spy Agent – Visualize Data Analyzing Data on a graphical way. • The art of visualization • The recorded data on each day • Setting the importance level 36

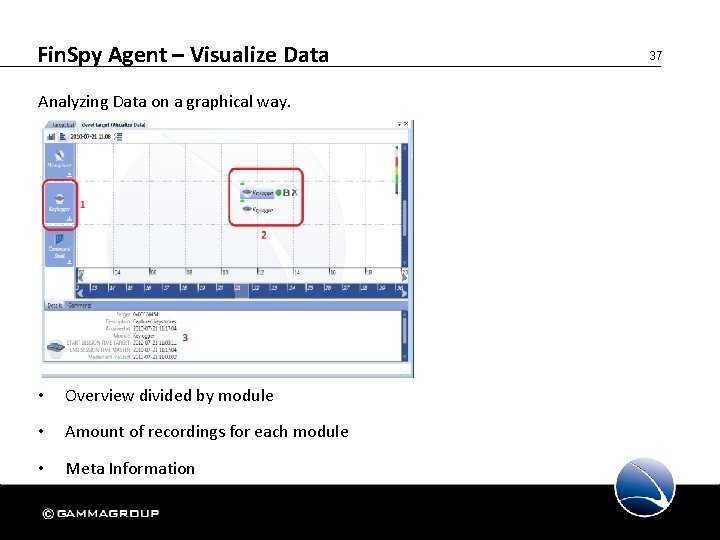
Fin. Spy Agent – Visualize Data Analyzing Data on a graphical way. • Overview divided by module • Amount of recordings for each module • Meta Information 37

Fin. Spy Agent 38 1. Introduction 2. Fin. Spy Agent § Evidence Protection 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

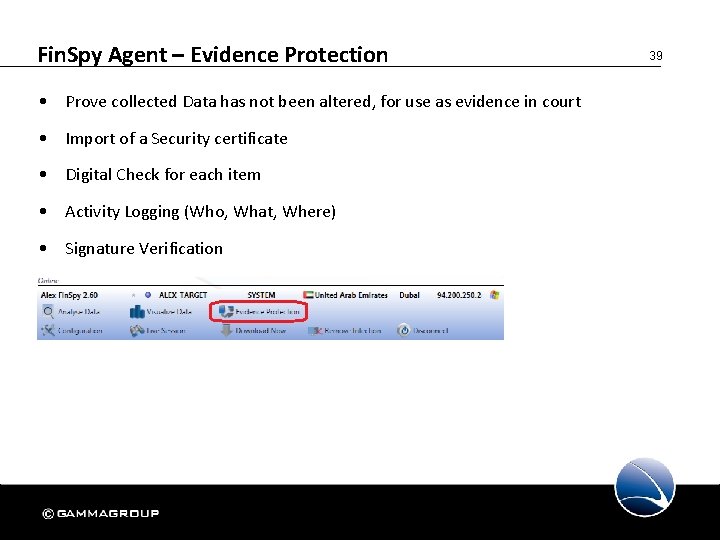
Fin. Spy Agent – Evidence Protection • Prove collected Data has not been altered, for use as evidence in court • Import of a Security certificate • Digital Check for each item • Activity Logging (Who, What, Where) • Signature Verification 39

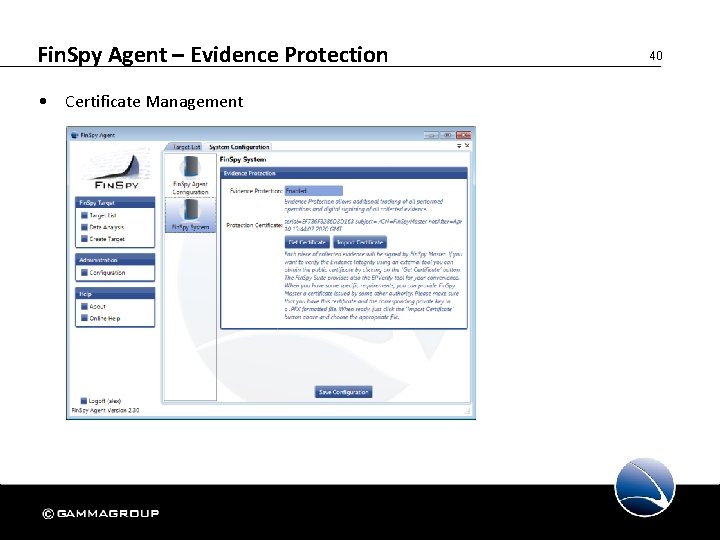
Fin. Spy Agent – Evidence Protection • Certificate Management 40

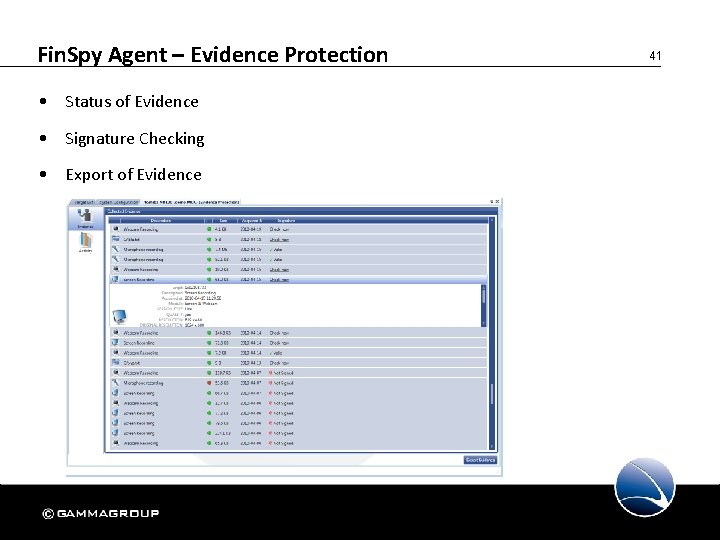
Fin. Spy Agent – Evidence Protection • Status of Evidence • Signature Checking • Export of Evidence 41

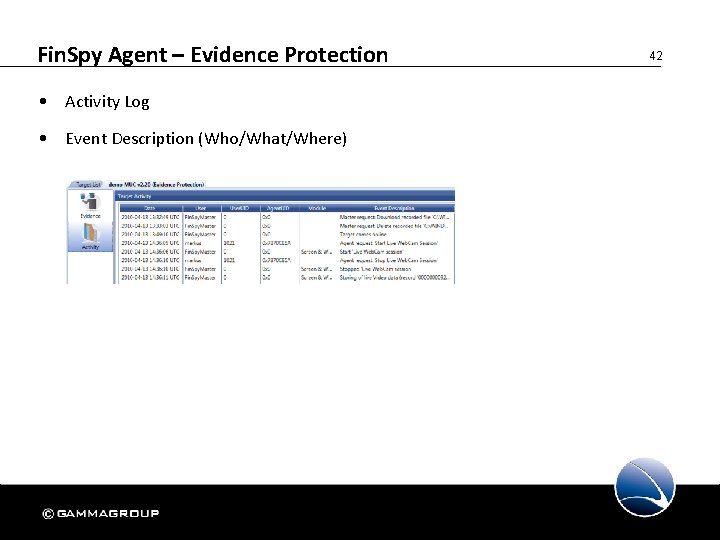
Fin. Spy Agent – Evidence Protection • Activity Log • Event Description (Who/What/Where) 42

Fin. Spy Agent – Evidence Protection • Exported evidence can generate a report 43

Fin. Spy Agent – Evidence Protection • Evidence history can be viewed 44

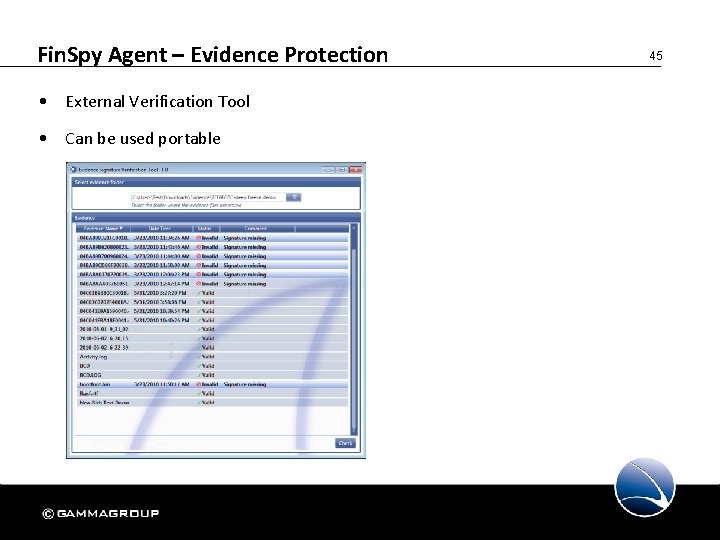
Fin. Spy Agent – Evidence Protection • External Verification Tool • Can be used portable 45

Fin. Spy Agent – Configuration – Hands-On: 46

Fin. Spy Agent – Configuration – Hands-On: • Select a Target • Go to Evidence Protection • Export the Evidence • Use external Evidence Verification Tool • Run the external Evidence Verification Tool 47

Fin. Spy Agent 48 1. Introduction 2. Fin. Spy Agent § Configuration 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

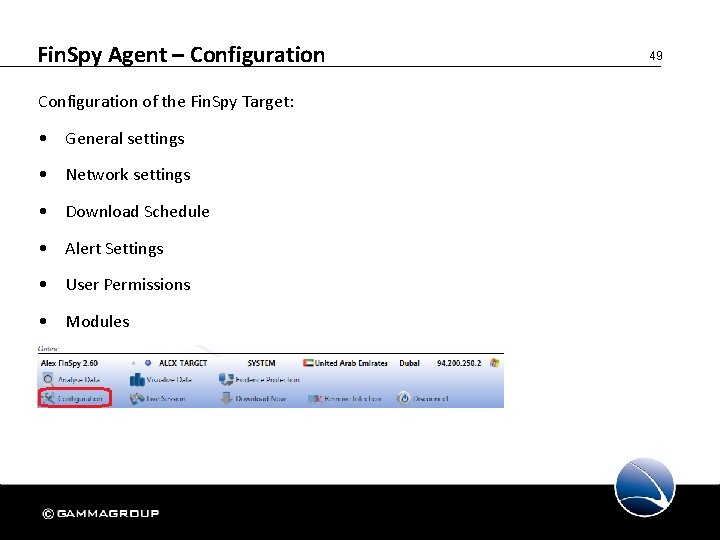
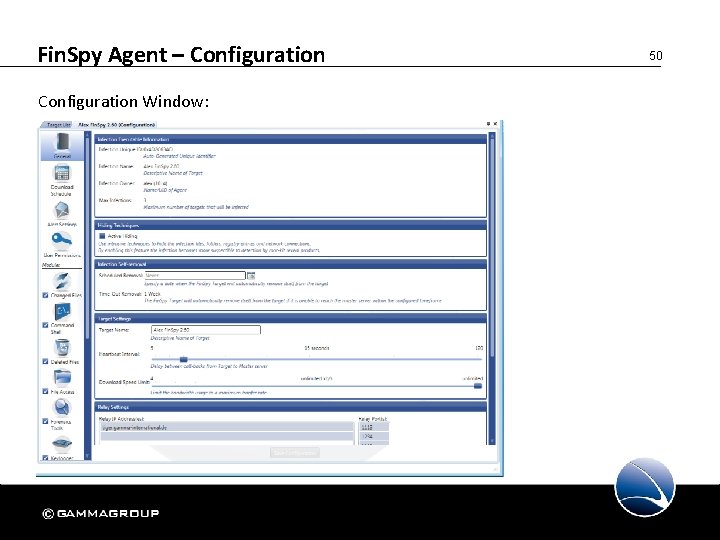
Fin. Spy Agent – Configuration of the Fin. Spy Target: • General settings • Network settings • Download Schedule • Alert Settings • User Permissions • Modules 49

Fin. Spy Agent – Configuration Window: 50

Fin. Spy Agent – Configuration If all modules are installed, the following can be configured: • General – Information on Trojan, Network, Heart-beat and Removal • Download Schedule • Alert Settings • User Permissions • Accessed Files • Changed Files • Command Shell • Deleted Files • File Access • Forensics Tools 51

Fin. Spy Agent – Configuration If all modules are installed, the following can be configured: • Keylogger • Mouse. Clicks • Microphone • Printer • Scheduler • Skype • Screen & Webcam • Vo. IP 52

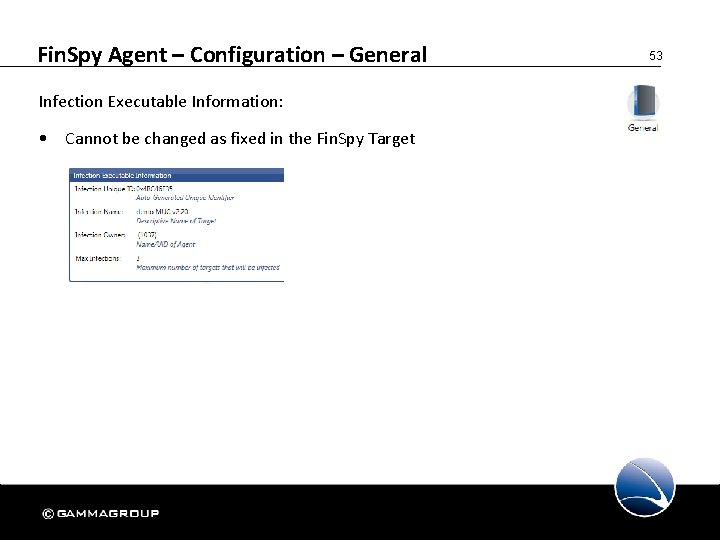
Fin. Spy Agent – Configuration – General Infection Executable Information: • Cannot be changed as fixed in the Fin. Spy Target 53

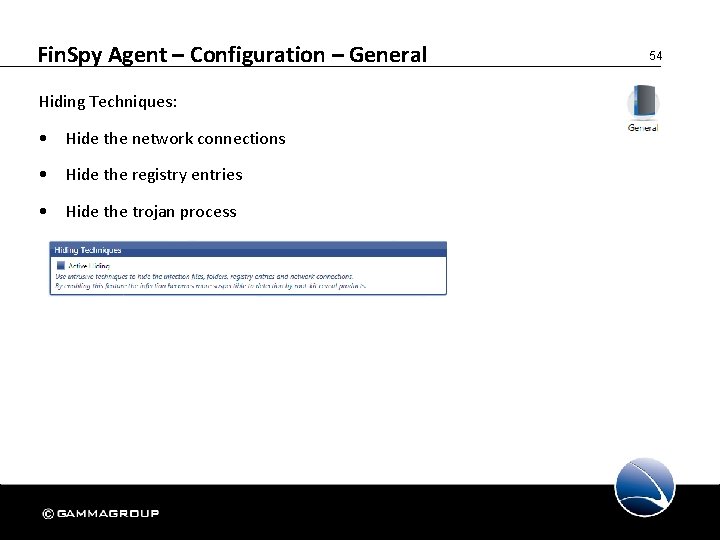
Fin. Spy Agent – Configuration – General Hiding Techniques: • Hide the network connections • Hide the registry entries • Hide the trojan process 54

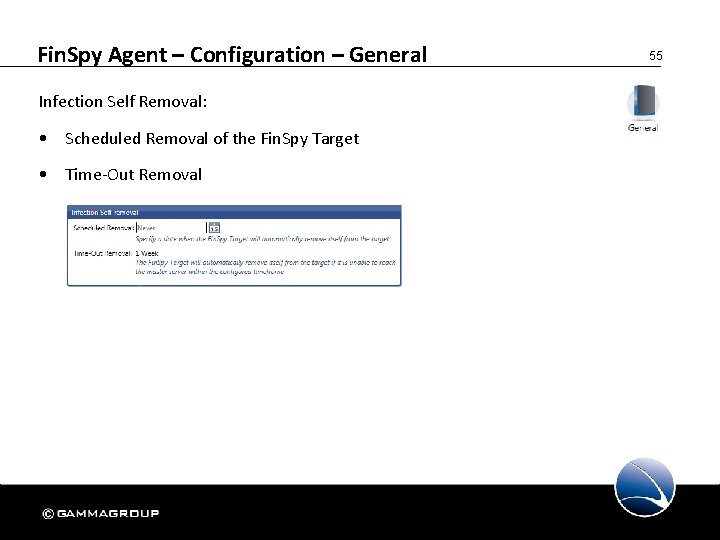
Fin. Spy Agent – Configuration – General Infection Self Removal: • Scheduled Removal of the Fin. Spy Target • Time-Out Removal 55

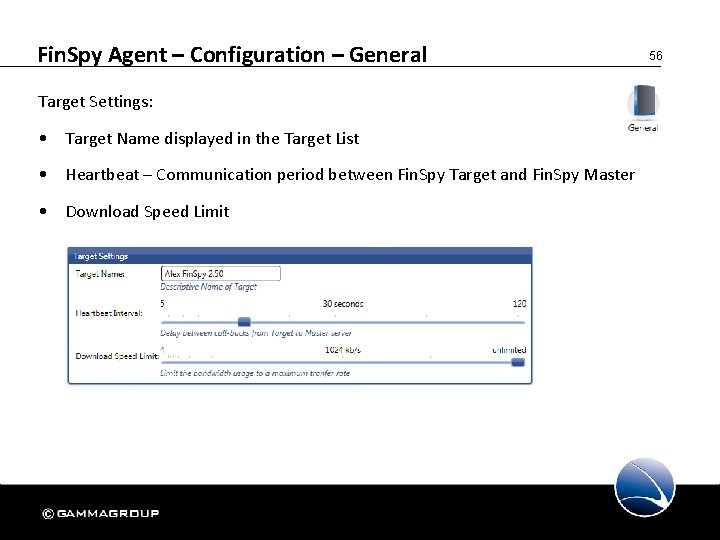
Fin. Spy Agent – Configuration – General Target Settings: • Target Name displayed in the Target List • Heartbeat – Communication period between Fin. Spy Target and Fin. Spy Master • Download Speed Limit 56

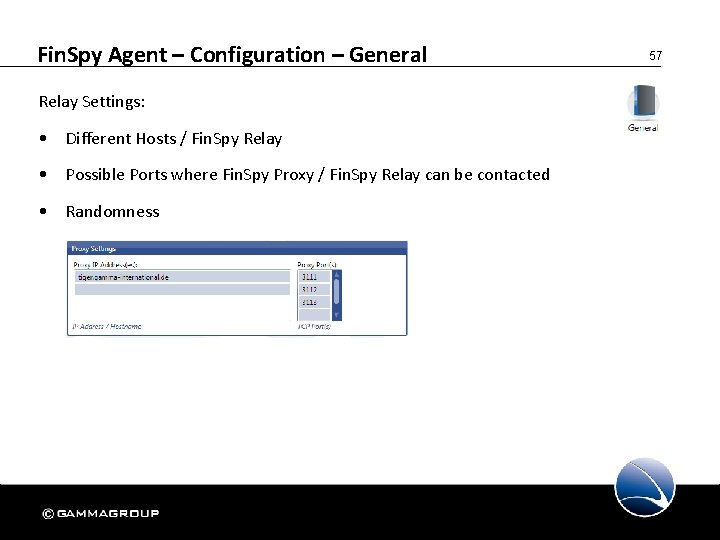
Fin. Spy Agent – Configuration – General Relay Settings: • Different Hosts / Fin. Spy Relay • Possible Ports where Fin. Spy Proxy / Fin. Spy Relay can be contacted • Randomness 57

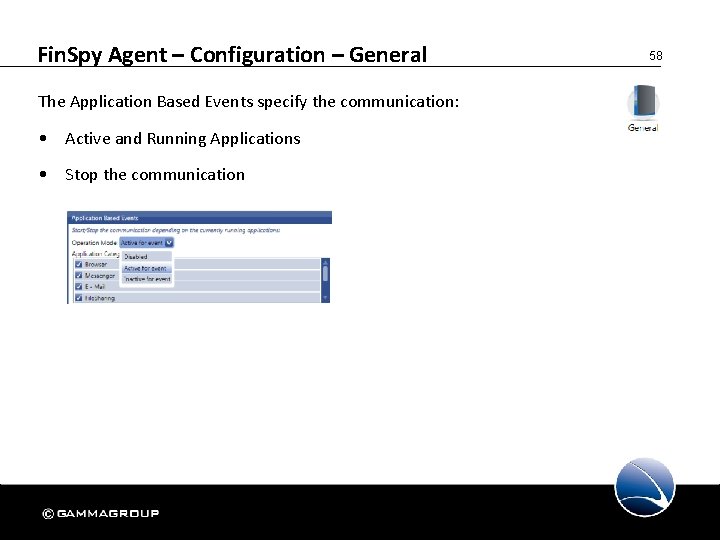
Fin. Spy Agent – Configuration – General The Application Based Events specify the communication: • Active and Running Applications • Stop the communication 58

Fin. Spy Agent – Configuration – Hands-On: 59

Fin. Spy Agent – Configuration – Hands-On: • Select a Target • Configure General Settings • Give Target another Name 60

Fin. Spy Agent 61 1. Introduction 2. Fin. Spy Agent § Download Schedule 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – Configuration – Download Schedule To configure: • Automated Downloads • Time & Date based • Application based 62

Fin. Spy Agent – Configuration – Download Schedule Application Events: • Screensaver Active • Screen Locked • Data Available 63

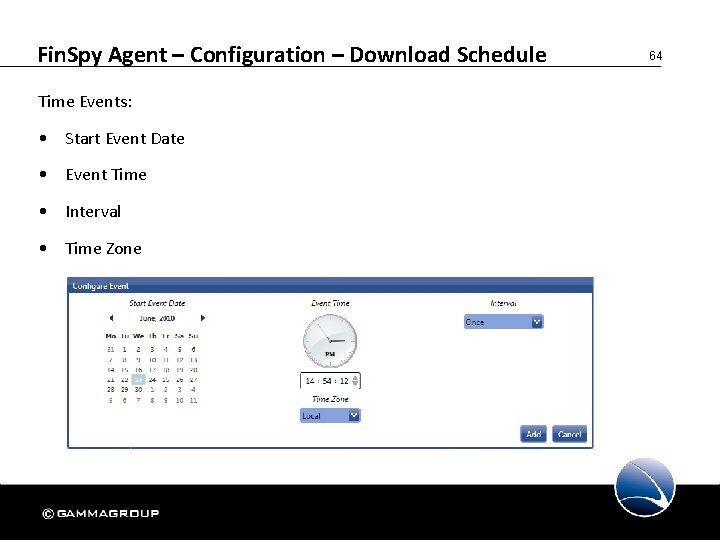
Fin. Spy Agent – Configuration – Download Schedule Time Events: • Start Event Date • Event Time • Interval • Time Zone 64

Fin. Spy Agent – Download Schedule – Hands-On: 65

Fin. Spy Agent – Download Schedule – Hands-On: • Select a Target • Create a Download Schedule • If Screensaver is active • Create a Download Schedule • Every Monday morning at 10 am 66

Fin. Spy Agent 67 1. Introduction 2. Fin. Spy Agent § Alert Settings 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

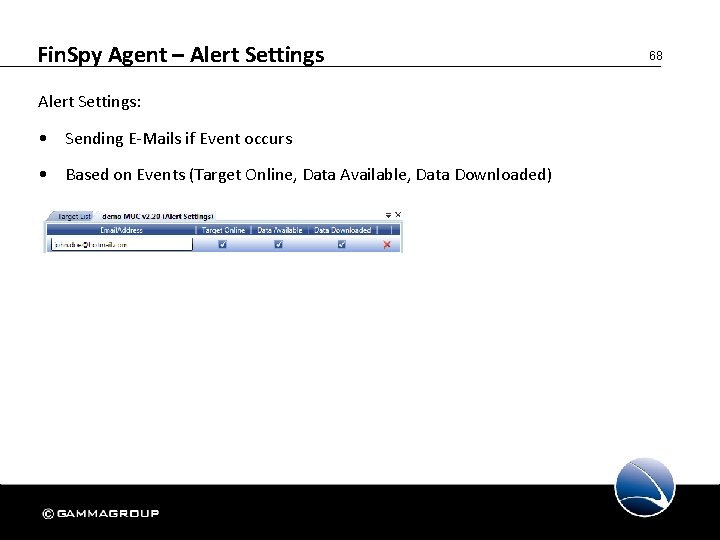
Fin. Spy Agent – Alert Settings: • Sending E-Mails if Event occurs • Based on Events (Target Online, Data Available, Data Downloaded) 68

Fin. Spy Agent – Alert Settings – Hands-On: 69

Fin. Spy Agent – Alert Settings – Hands-On: • Select a Target • Create an Alarm for a certain event • Let the event occur and check your Inbox 70

Fin. Spy Agent 71 1. Introduction 2. Fin. Spy Agent § User Permissions 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – User permissions: • Different users • System Administrator • User • Detailed configuration per user & target • Action allowed / Action not allowed 72

Fin. Spy Agent – User permissions Hands-On: 73

Fin. Spy Agent – User permissions Hands-On: • Select a Target • Choose one user and give him the following rights • Live Session • Configuration • Are the rights correct displayed afterwards? 74

Fin. Spy Agent 75 1. Introduction 2. Fin. Spy Agent § Modules 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

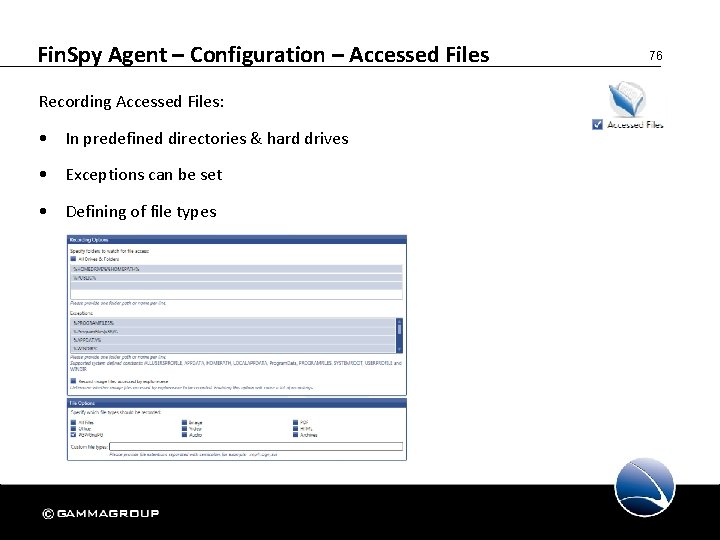
Fin. Spy Agent – Configuration – Accessed Files Recording Accessed Files: • In predefined directories & hard drives • Exceptions can be set • Defining of file types 76

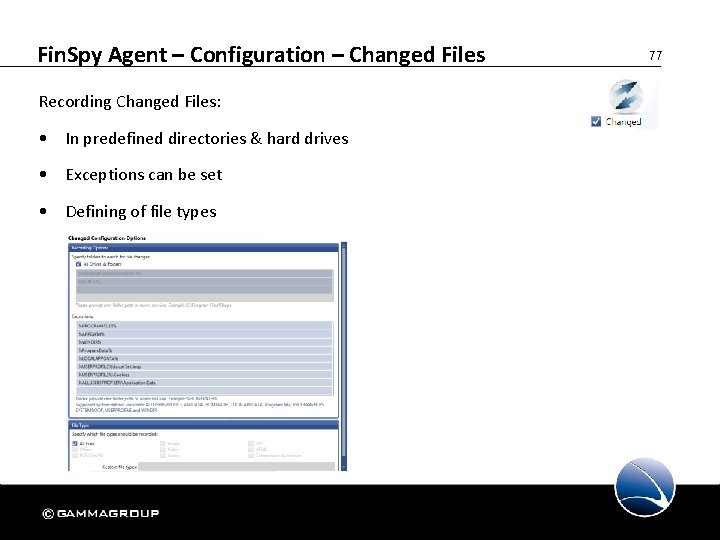
Fin. Spy Agent – Configuration – Changed Files Recording Changed Files: • In predefined directories & hard drives • Exceptions can be set • Defining of file types 77

Fin. Spy Agent – Configuration – Deleted Files Recording Deleted Files: • In predefined directories & hard drives • Exceptions can be set • Defining of file types 78

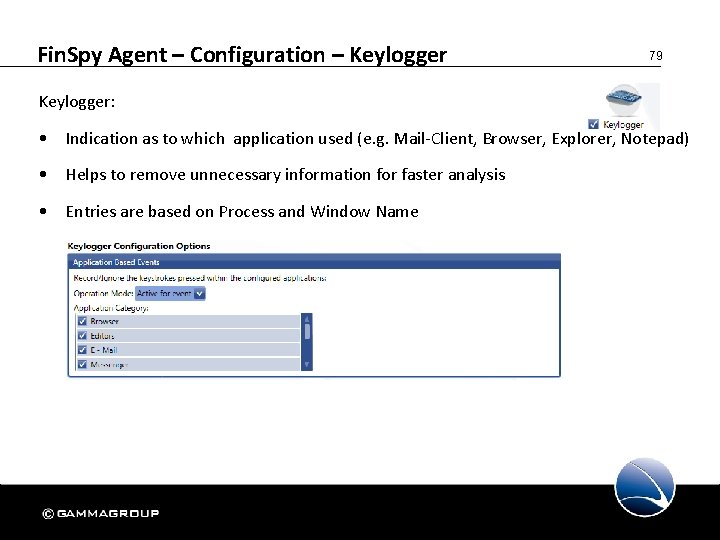
Fin. Spy Agent – Configuration – Keylogger 79 Keylogger: • Indication as to which application used (e. g. Mail-Client, Browser, Explorer, Notepad) • Helps to remove unnecessary information for faster analysis • Entries are based on Process and Window Name

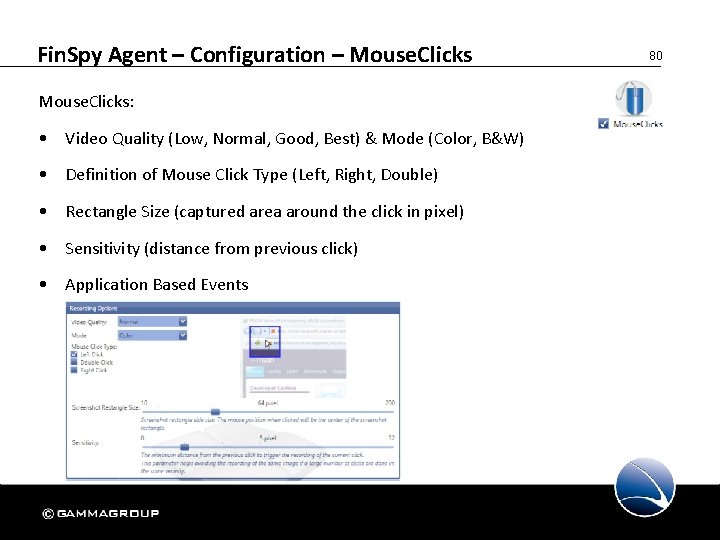
Fin. Spy Agent – Configuration – Mouse. Clicks: • Video Quality (Low, Normal, Good, Best) & Mode (Color, B&W) • Definition of Mouse Click Type (Left, Right, Double) • Rectangle Size (captured area around the click in pixel) • Sensitivity (distance from previous click) • Application Based Events 80

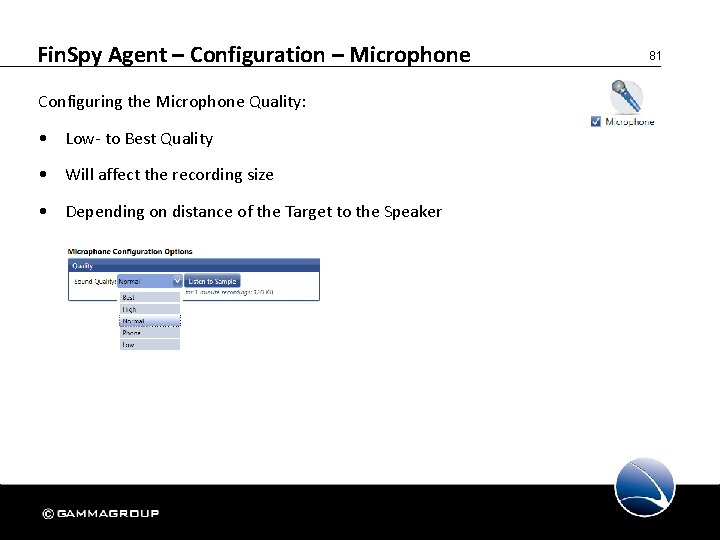
Fin. Spy Agent – Configuration – Microphone Configuring the Microphone Quality: • Low- to Best Quality • Will affect the recording size • Depending on distance of the Target to the Speaker 81

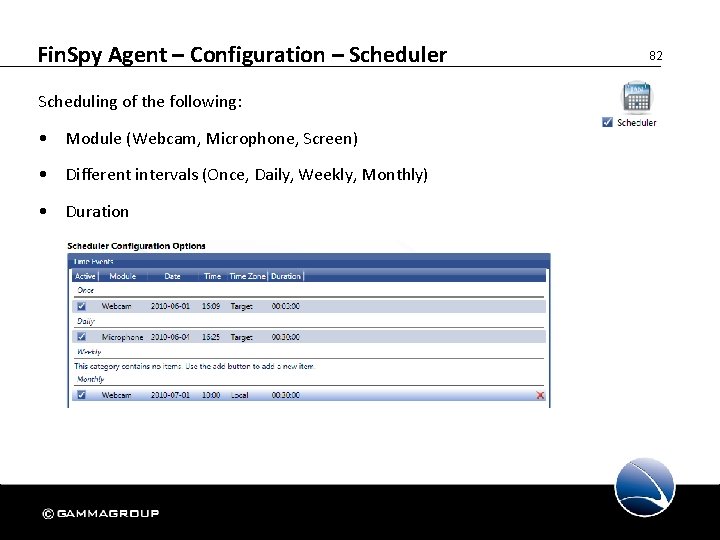
Fin. Spy Agent – Configuration – Scheduler Scheduling of the following: • Module (Webcam, Microphone, Screen) • Different intervals (Once, Daily, Weekly, Monthly) • Duration 82

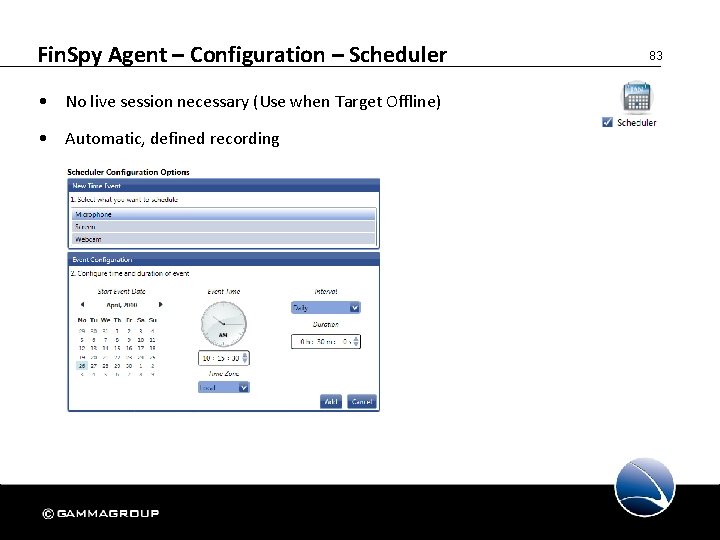
Fin. Spy Agent – Configuration – Scheduler • No live session necessary (Use when Target Offline) • Automatic, defined recording 83

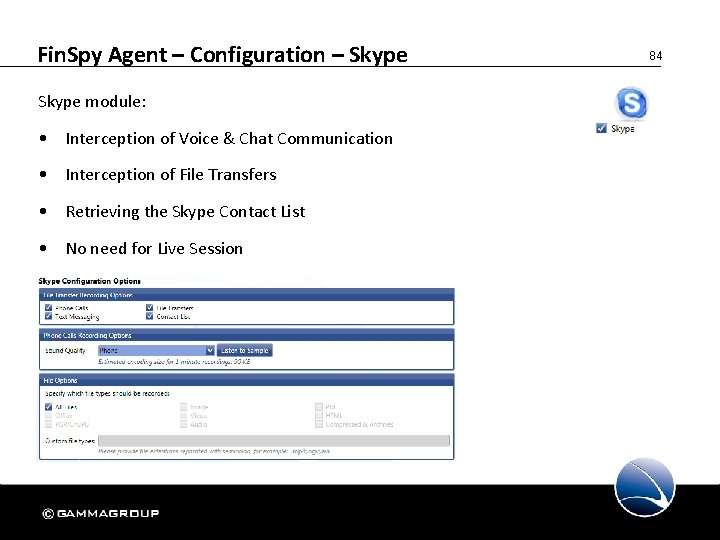
Fin. Spy Agent – Configuration – Skype module: • Interception of Voice & Chat Communication • Interception of File Transfers • Retrieving the Skype Contact List • No need for Live Session 84

Fin. Spy Agent – Configuration – Screen & Webcam • Quality & Size can be defined • Useful for indication of Disk space on the Target Computer • Automatic Recording of the Screen if certain applications are running 85

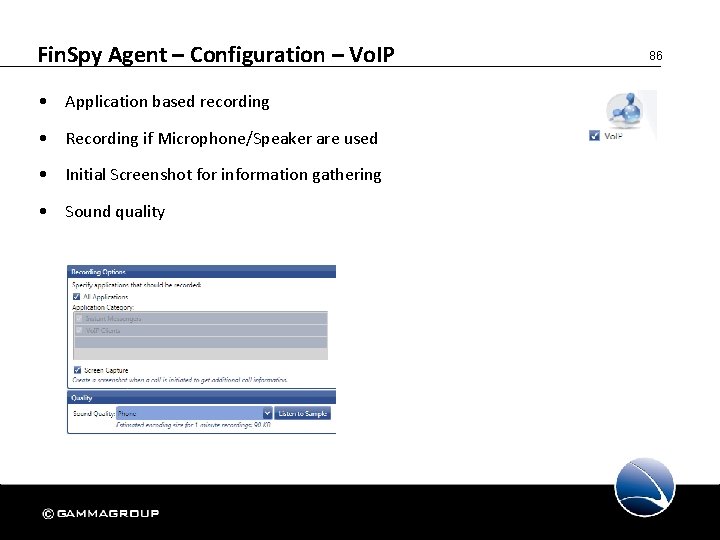
Fin. Spy Agent – Configuration – Vo. IP • Application based recording • Recording if Microphone/Speaker are used • Initial Screenshot for information gathering • Sound quality 86

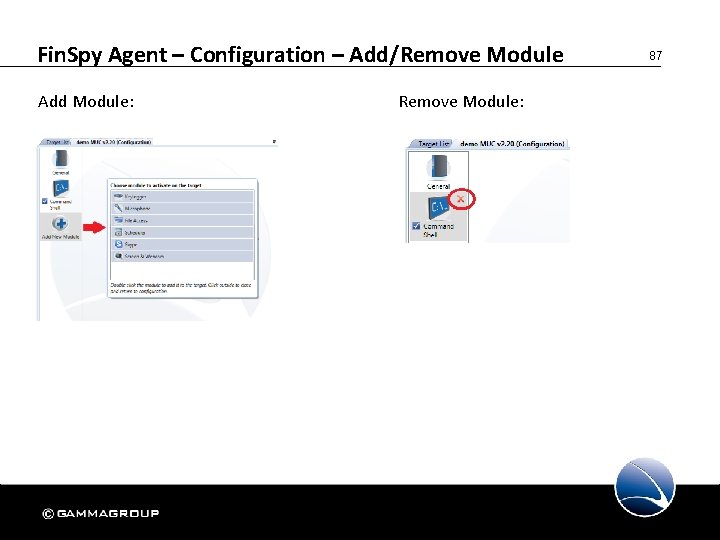
Fin. Spy Agent – Configuration – Add/Remove Module Add Module: Remove Module: 87

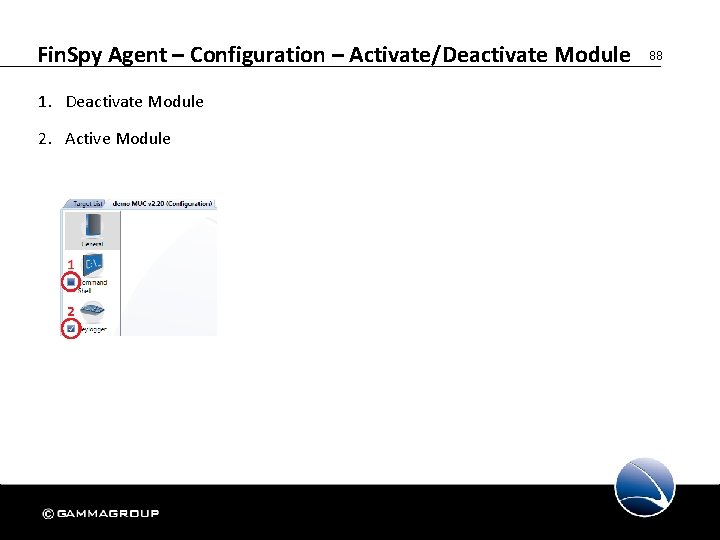
Fin. Spy Agent – Configuration – Activate/Deactivate Module 1. Deactivate Module 2. Active Module 88

Fin. Spy Agent 89 1. Introduction 2. Fin. Spy Agent § Live Session 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Agent – Live Session The Live Session gives the possibility of the following options: • Establishing a live session to the Target’s Display • Establishing a live session to the Target’s Webcam • Establishing a live session to the Target’s Microphone • Will show a live session of the Target’s keys pressed • Commands can be entered at the Target’s command shell • Will show a live File Browser for the Target’s file system • Execute Applications on Target’s system 90

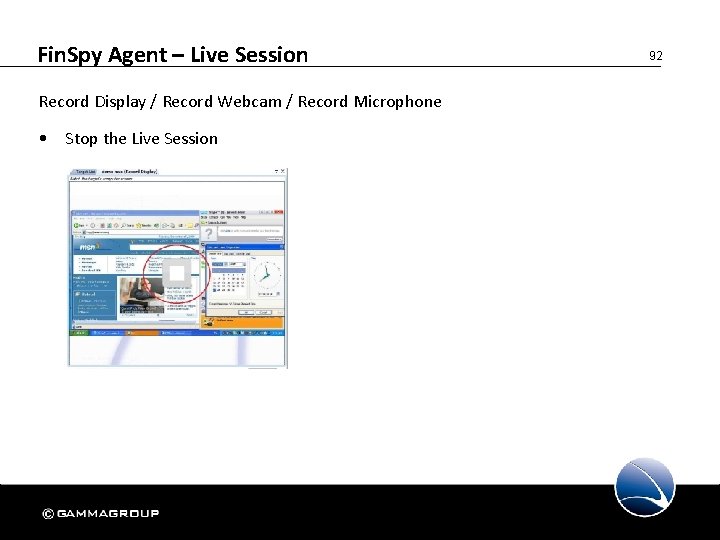
Fin. Spy Agent – Live Session Record Display / Record Webcam / Record Microphone • Start the Live Session 91

Fin. Spy Agent – Live Session Record Display / Record Webcam / Record Microphone • Stop the Live Session 92

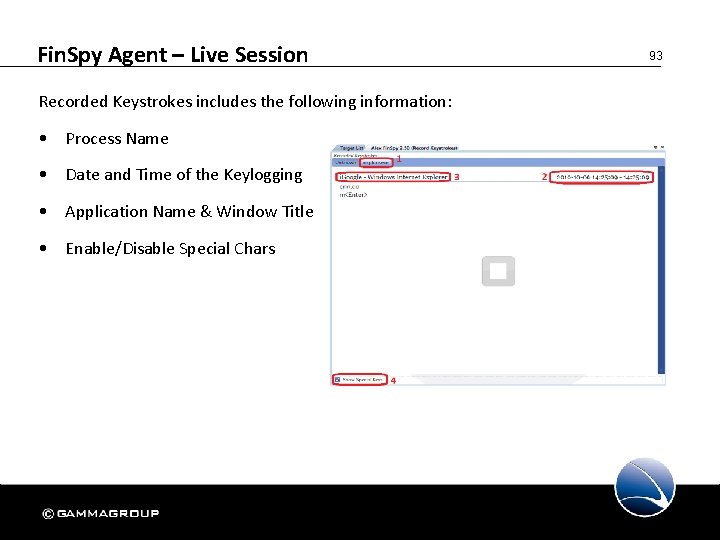
Fin. Spy Agent – Live Session Recorded Keystrokes includes the following information: • Process Name • Date and Time of the Keylogging • Application Name & Window Title • Enable/Disable Special Chars 93

Fin. Spy Agent – Live Session Command Shell offers - • Shutting down the Fin. Spy Target • Creating Files • Executing Files • Creating Accounts • Accessing Other Computers • Uploading Data • Access to Powershell • And many more 94

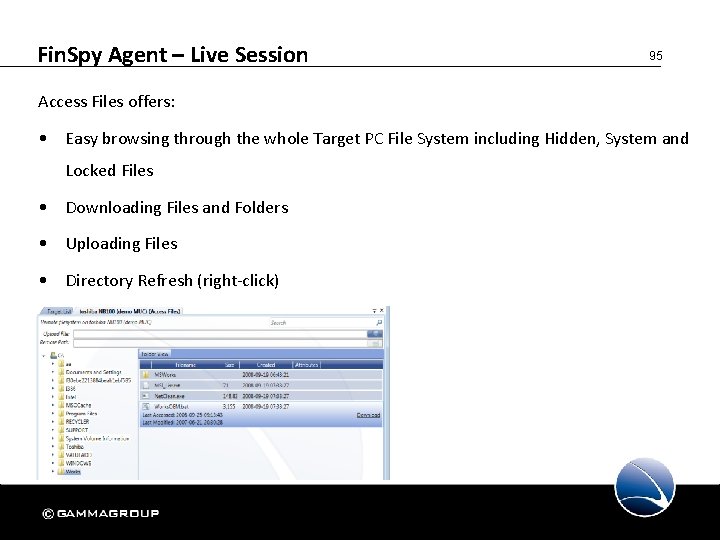
Fin. Spy Agent – Live Session 95 Access Files offers: • Easy browsing through the whole Target PC File System including Hidden, System and Locked Files • Downloading Files and Folders • Uploading Files • Directory Refresh (right-click)

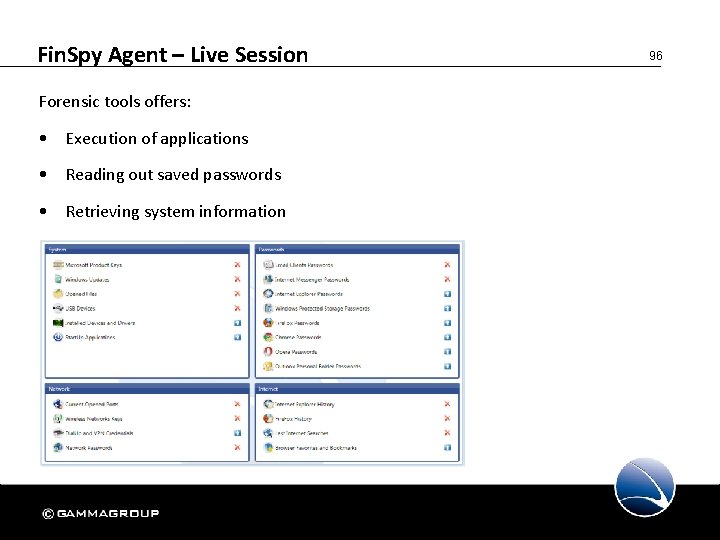
Fin. Spy Agent – Live Session Forensic tools offers: • Execution of applications • Reading out saved passwords • Retrieving system information 96

Fin. Spy Agent – Live Session – Hands-On: 97

Fin. Spy Agent – Live Session – Hands-On – 1: • Select a Target • Establish two Live Sessions • Watch the Screen • Browse Files • Upload a File 98

Fin. Spy Agent – Live Session – Hands-On – 2: • Select a Target • Establish Forensic Tools Live Session • Upload & Execute Application to Fin. Spy Target • View the Data • Remove the Application from Fin. Spy Target 99

Fin. Spy Agent 100 1. Introduction 2. Fin. Spy Agent § Download Data 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

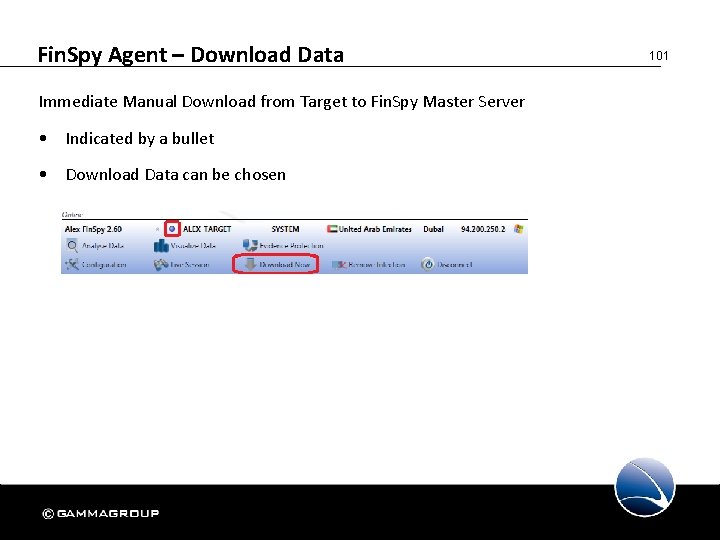
Fin. Spy Agent – Download Data Immediate Manual Download from Target to Fin. Spy Master Server • Indicated by a bullet • Download Data can be chosen 101

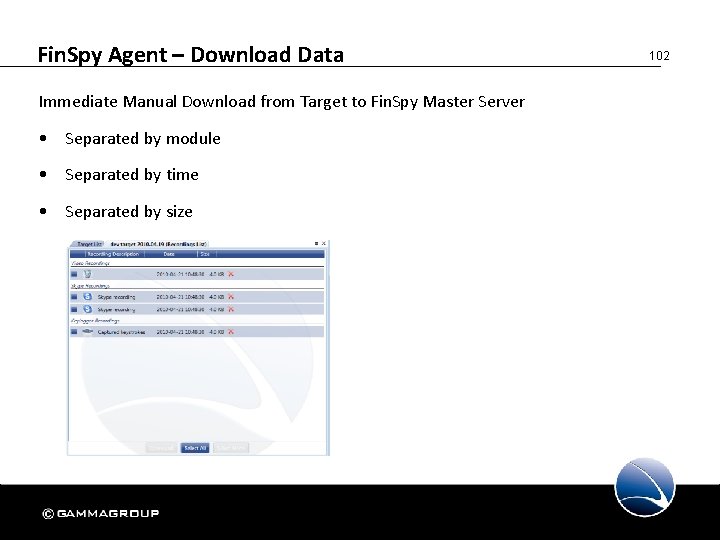
Fin. Spy Agent – Download Data Immediate Manual Download from Target to Fin. Spy Master Server • Separated by module • Separated by time • Separated by size 102

Fin. Spy Agent 103 1. Introduction 2. Fin. Spy Agent § Update Modules 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

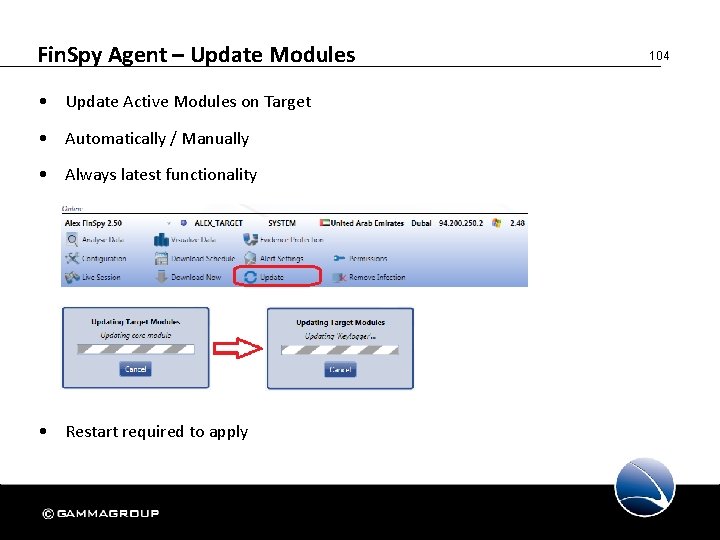
Fin. Spy Agent – Update Modules • Update Active Modules on Target • Automatically / Manually • Always latest functionality • Restart required to apply 104

Fin. Spy Agent 105 1. Introduction 2. Fin. Spy Agent § Remove Data 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

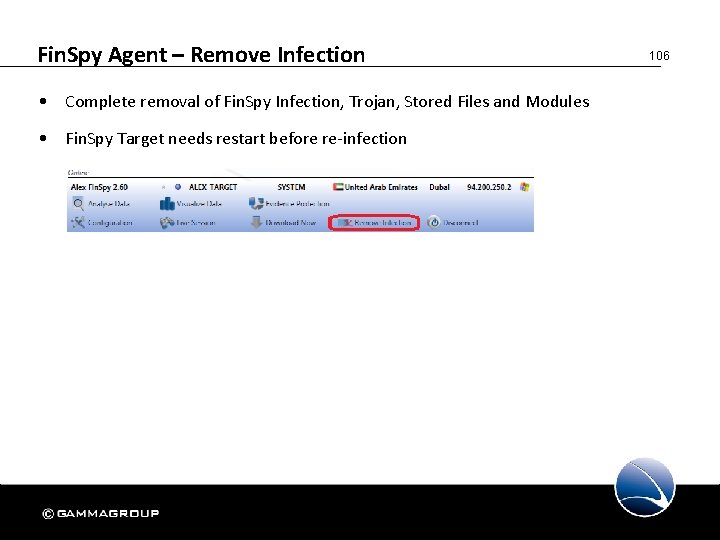
Fin. Spy Agent – Remove Infection • Complete removal of Fin. Spy Infection, Trojan, Stored Files and Modules • Fin. Spy Target needs restart before re-infection 106

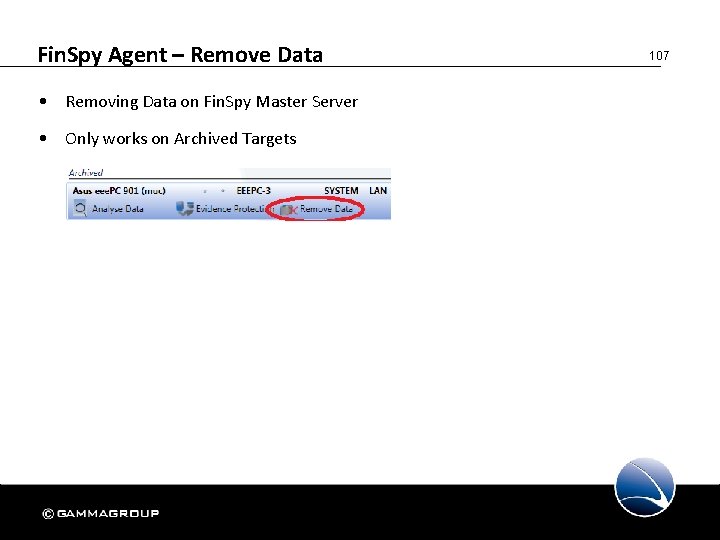
Fin. Spy Agent – Remove Data • Removing Data on Fin. Spy Master Server • Only works on Archived Targets 107

Fin. Spy Agent 108 1. Introduction 2. Fin. Spy Agent § Create Target 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

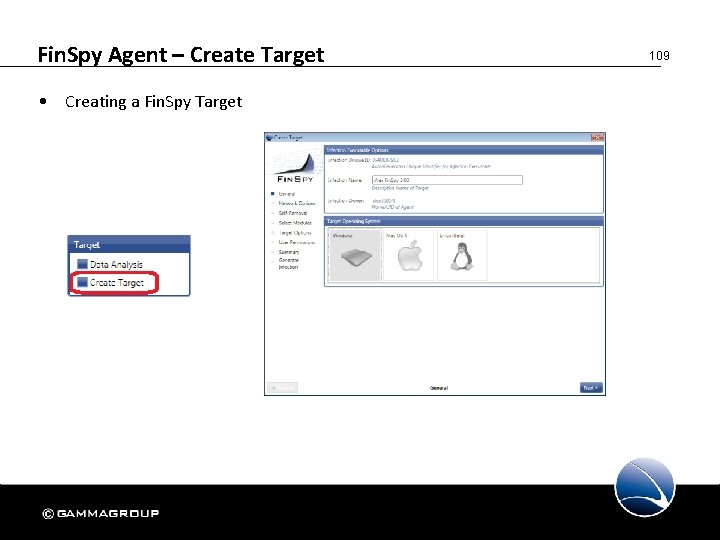
Fin. Spy Agent – Create Target • Creating a Fin. Spy Target 109

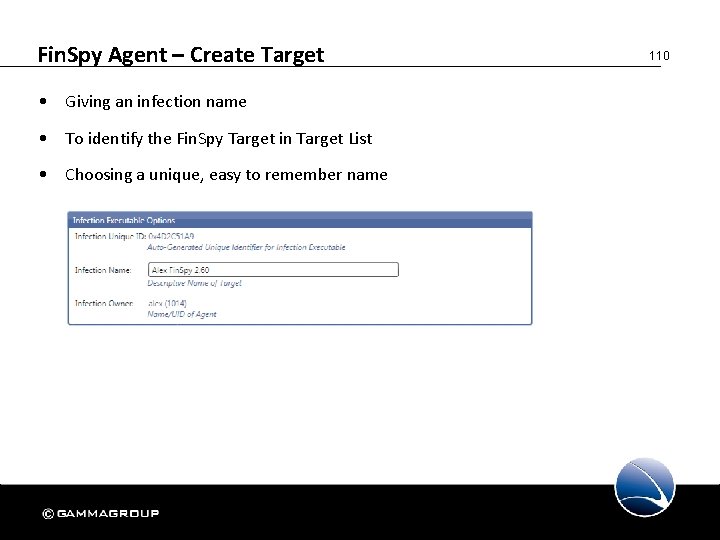
Fin. Spy Agent – Create Target • Giving an infection name • To identify the Fin. Spy Target in Target List • Choosing a unique, easy to remember name 110

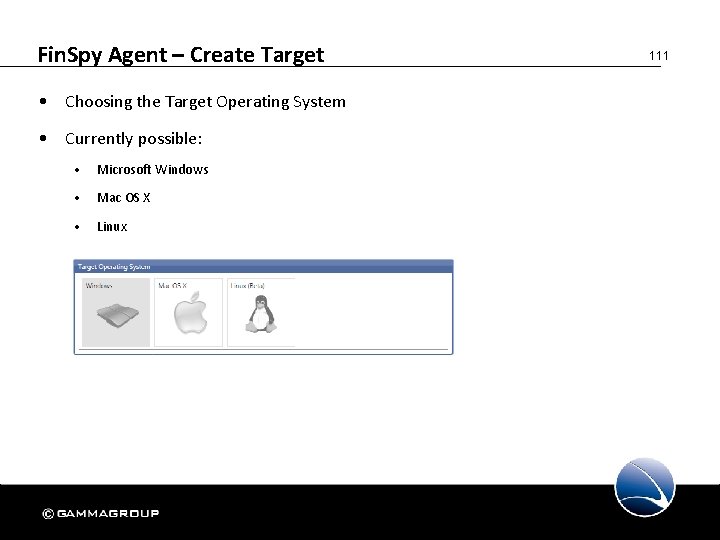
Fin. Spy Agent – Create Target • Choosing the Target Operating System • Currently possible: • Microsoft Windows • Mac OS X • Linux 111

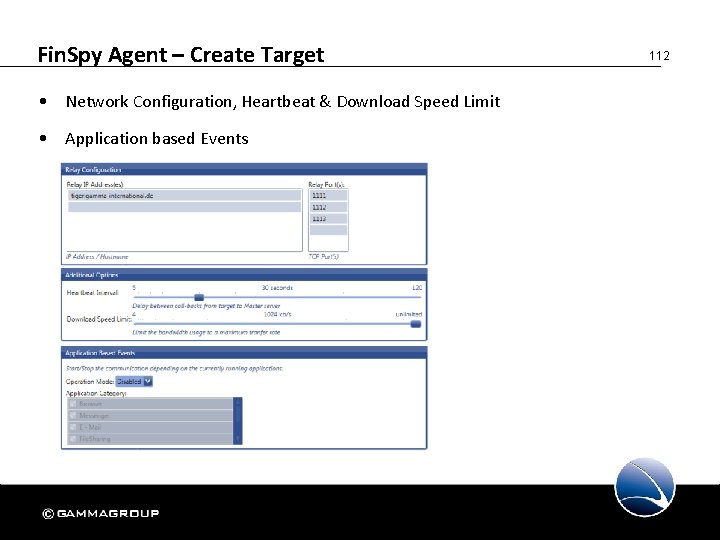
Fin. Spy Agent – Create Target • Network Configuration, Heartbeat & Download Speed Limit • Application based Events 112

Fin. Spy Agent – Create Target 113 • Self Removal • Max Infection • Avoid accidental Mass Infections and wasting of license limits • Scheduled Removal • On given date the Fin. Spy Target removes itself • Time-Out Removal • After being out of Communication with the Finspy Master for a given time, Fin. Spy Target removes itself

Fin. Spy Agent – Create Target • Module Selection 114

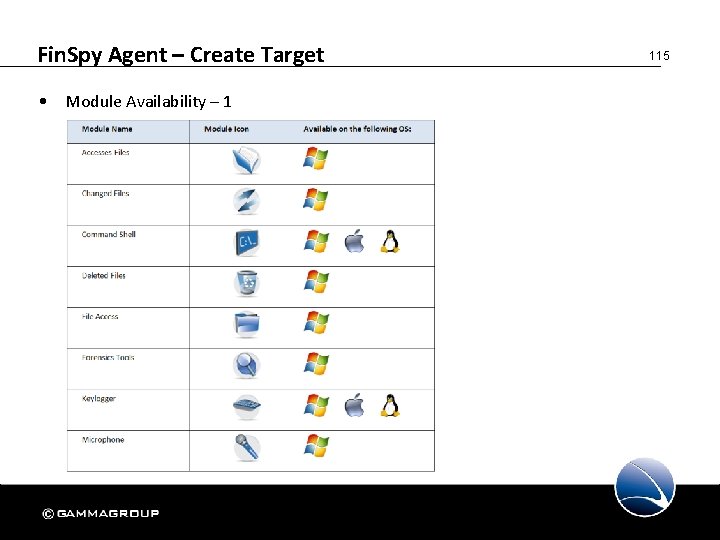
Fin. Spy Agent – Create Target • Module Availability – 1 115

Fin. Spy Agent – Create Target • Module Availability – 2 116

Fin. Spy Agent – Create Target 117 • Modules can be selected • Recommendation for Physical and Remote Infection • Use no modules - Fin. Spy Installer at minimum and lack of activity of modules does not attract attention from Antivirus/Antispyware upon initial installation. • Minimum size: ~ 590 KB (no modules) • Maximum size: ~ 1. 8 MB (all modules)

Fin. Spy Agent – Create Target Options • Installing into Master Boot Record • Vista and Windows 7 infection (UAC Popup) • More hidden infection! 118

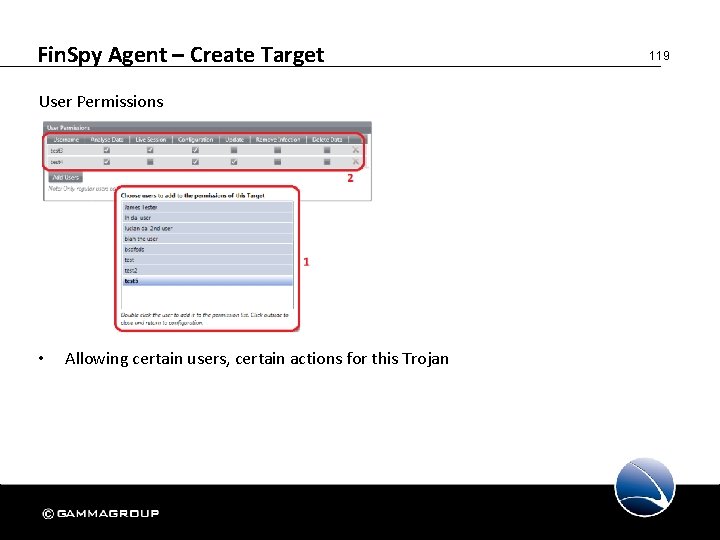
Fin. Spy Agent – Create Target User Permissions • Allowing certain users, certain actions for this Trojan 119

Fin. Spy Agent – Create Target Summary of created Fin. Spy Target • Name • Operating System • Network Information • Modules • Etc. 120

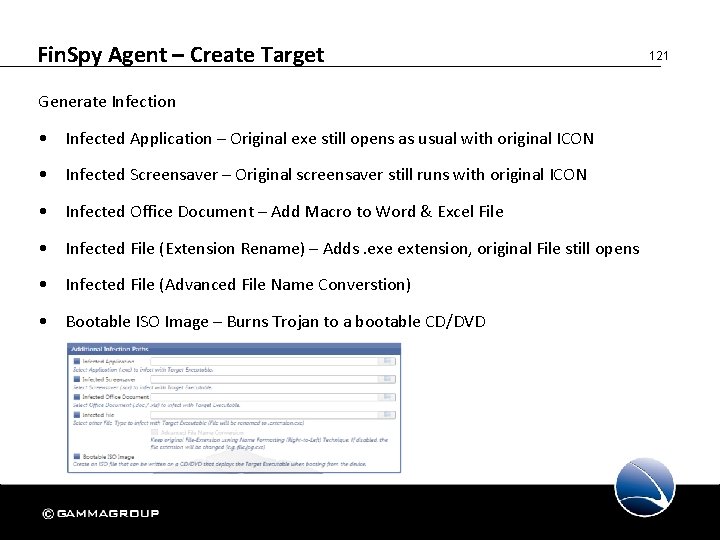
Fin. Spy Agent – Create Target Generate Infection • Infected Application – Original exe still opens as usual with original ICON • Infected Screensaver – Original screensaver still runs with original ICON • Infected Office Document – Add Macro to Word & Excel File • Infected File (Extension Rename) – Adds. exe extension, original File still opens • Infected File (Advanced File Name Converstion) • Bootable ISO Image – Burns Trojan to a bootable CD/DVD 121

Fin. Spy Agent – Create Target Generate Infection • Bootable Infection Dongle – Install Trojan on a bootable USB device • For infection of Harddrive encrypted systems (True. Crypt, PGP, etc. ) • Runtime Infection Dongle • For infection of running systems via Autorun 122

Fin. Spy Agent – Configuration – Hands-On: 123

Fin. Spy Agent – Configuration – Hands-On: • Create a Target • Following Modules: • Microphone, Keylogger, Skype • Choose MBR Infection • Any Infection Path • How big is the file size of the Target? • Useful for which kind of distribution? 124

Fin. Spy Agent 125 1. Introduction 2. Fin. Spy Agent § Infection Techniques 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

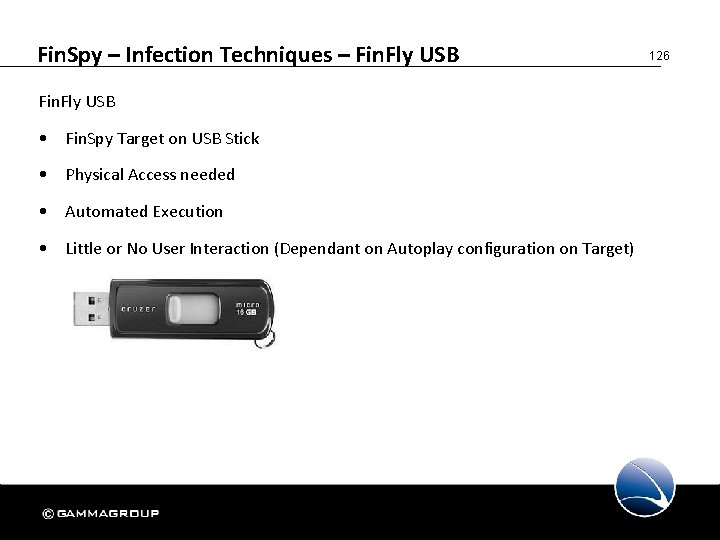
Fin. Spy – Infection Techniques – Fin. Fly USB • Fin. Spy Target on USB Stick • Physical Access needed • Automated Execution • Little or No User Interaction (Dependant on Autoplay configuration on Target) 126

Fin. Spy – Infection Techniques – Fin. Fly USB • Created through Fin. Spy Agent 127

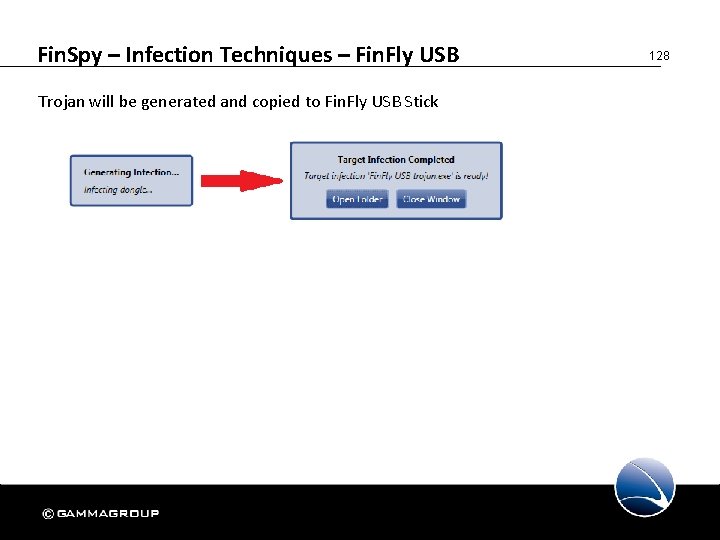
Fin. Spy – Infection Techniques – Fin. Fly USB Trojan will be generated and copied to Fin. Fly USB Stick 128

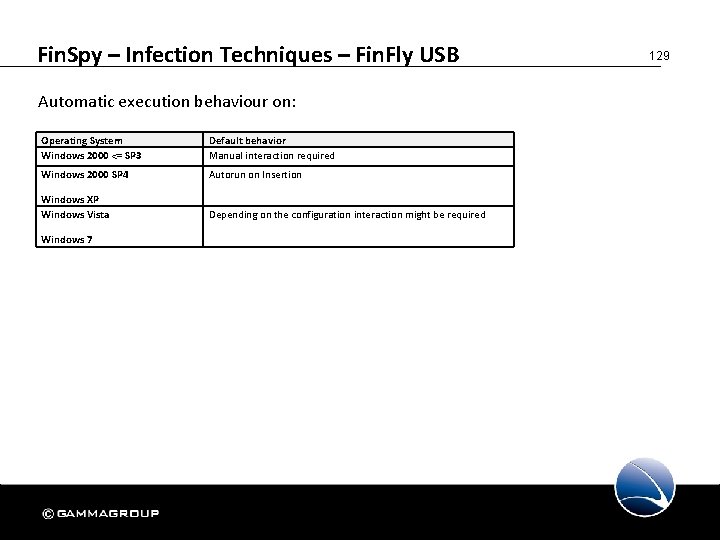
Fin. Spy – Infection Techniques – Fin. Fly USB Automatic execution behaviour on: Operating System Windows 2000 <= SP 3 Default behavior Manual interaction required Windows 2000 SP 4 Autorun on Insertion Windows XP Windows Vista Depending on the configuration interaction might be required Windows 7 129

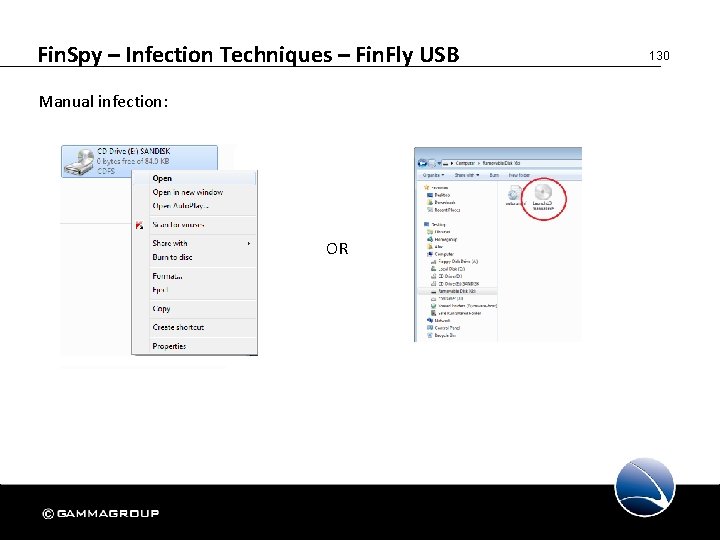
Fin. Spy – Infection Techniques – Fin. Fly USB Manual infection: OR 130

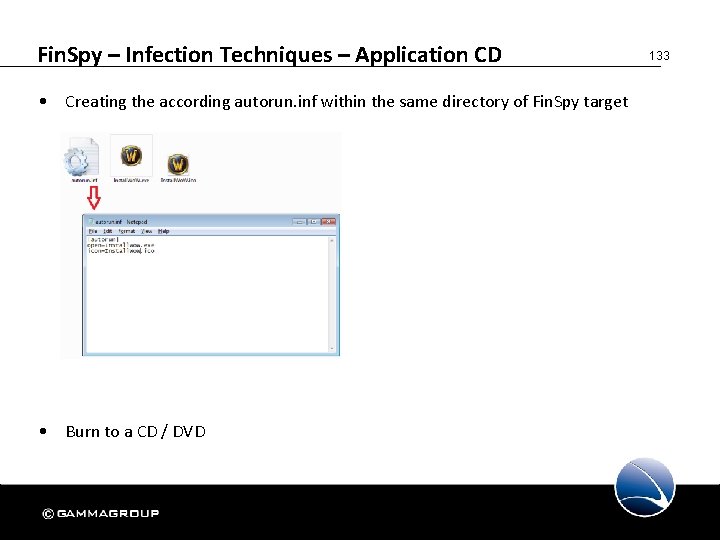
Fin. Spy – Infection Techniques – Application CD Create an Autorun CD with Infected Installer of: • Games (World of Warcraft) • DVD (Video Player) • Etc. 131

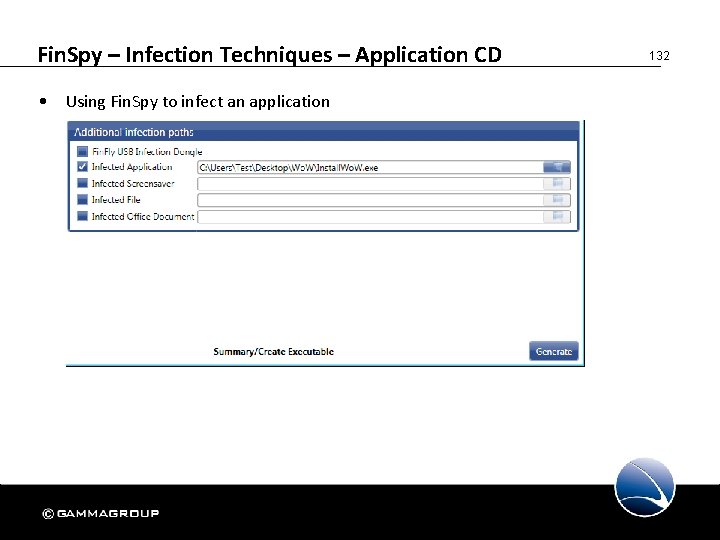
Fin. Spy – Infection Techniques – Application CD • Using Fin. Spy to infect an application 132

Fin. Spy – Infection Techniques – Application CD • Creating the according autorun. inf within the same directory of Fin. Spy target • Burn to a CD / DVD 133

Fin. Spy – Infection Techniques – Application CD Distribute to the following locations: • Mailbox of the Target • Internet Cafes • Business Centres • Offices 134

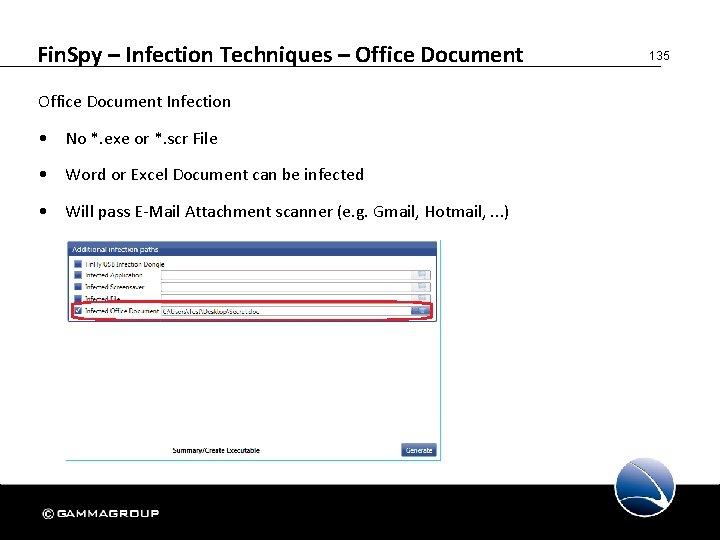
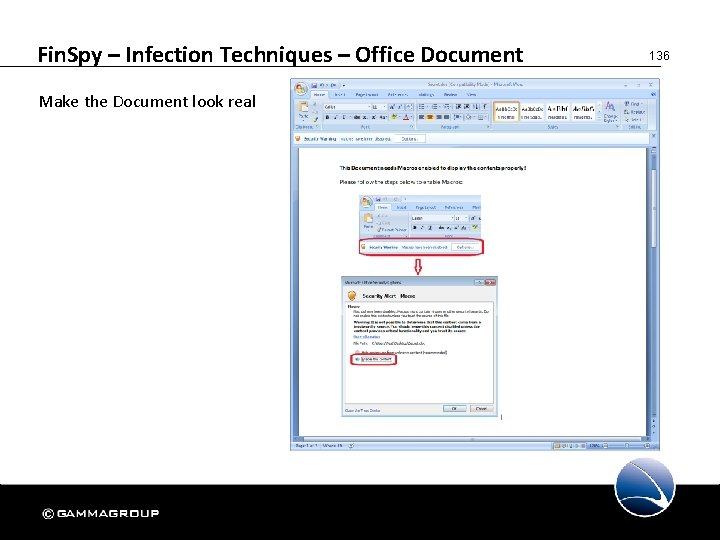
Fin. Spy – Infection Techniques – Office Document Infection • No *. exe or *. scr File • Word or Excel Document can be infected • Will pass E-Mail Attachment scanner (e. g. Gmail, Hotmail, . . . ) 135

Fin. Spy – Infection Techniques – Office Document Make the Document look real 136

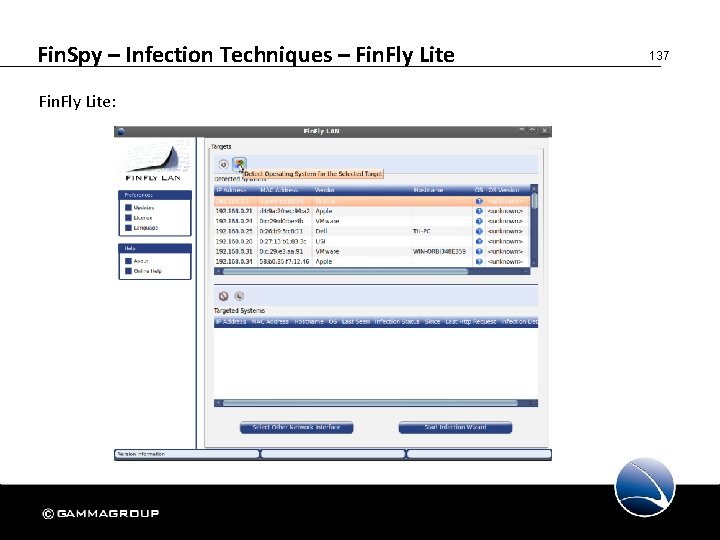
Fin. Spy – Infection Techniques – Fin. Fly Lite: 137

Fin. Spy – Infection Techniques – Fin. Fly Lite 138 Key Features: • Binary Infection: • Downloads of Executables or Screensavers will be infected with the pre-configured “payloads” • Update Injection: • Several Client-Software can be forced to update and install the configured software when checking for updates • Website Infection • Infect Target Systems through Websites which install the software by using the Web-browser module functionalities • Custom Payloads: • The software that will be injected can be uploaded and configured and is not bound to any other product • Traffic Inspection: • Identify Target Systems by IP Address or Radius username

Fin. Spy – Infection Techniques – Fin. Fly Web Example with IFrame Injection: 139

Fin. Spy – Infection Techniques – Fin. Fly Web Key Features: • Different Infection Modules • • Multiple Browser support • • Internet Explorer, Mozilla Firefox, Sea. Monkey, Safari, Google Chrome, Opera Multiple Operation System support • • Java. Script / IFrame / Sun Java / XPI Plugin / Active. X Windows 2000, Windows XP, Windows Vista, Windows 7, Mac. OS Snow Leopard Implementation into Standard Websites 140

Fin. Spy Administration 141 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Administration offers: • Fin. Spy Configuration through the Fin. Spy Agent • Configuration of Fin. Spy Master • Logfile Viewer of Fin. Spy Master • Fin. Spy Agent Connection Viewer • Viewing License Information 142

Fin. Spy Administration 143 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration § Configuration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Administration – Configuration Inside the Configuration Options, the following can be configured: • Configuration of the Fin. Spy Agent Data Download/Export • Fin. Spy Master Internal/External Network Interfaces • Connection configuration for the Fin. Spy Target • Configuring E-Mail Settings for Alerts • Fin. Spy Master and Fin. Spy Target Updates • Certificates, Activity Logging & Functionality • Database Integration of a LEMF • Target Modules Definition 144

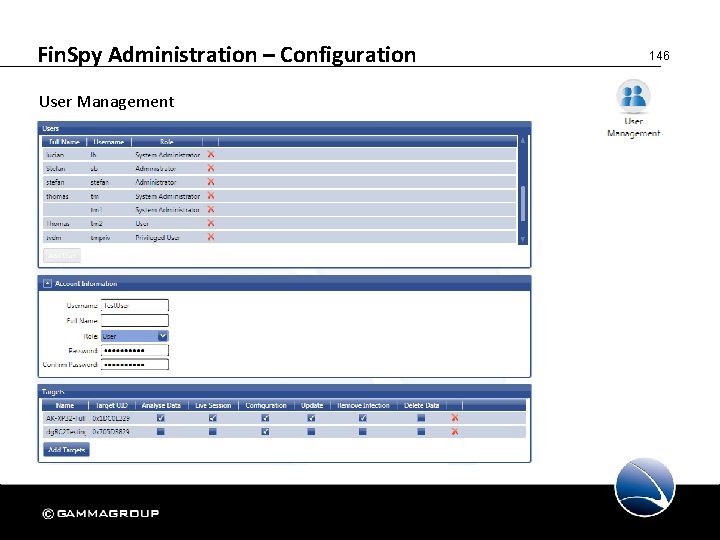
Fin. Spy Administration – Configuration User Management • Users can be added, changed or deleted • Four different user roles • User • Privileged User • Administrator • System Administrator 145

Fin. Spy Administration – Configuration User Management 146

Fin. Spy Administration – Configuration Agent Configuration • Download Data Folder • Created Targets will be placed here • Exported Evidence • Updated Installer Files 147

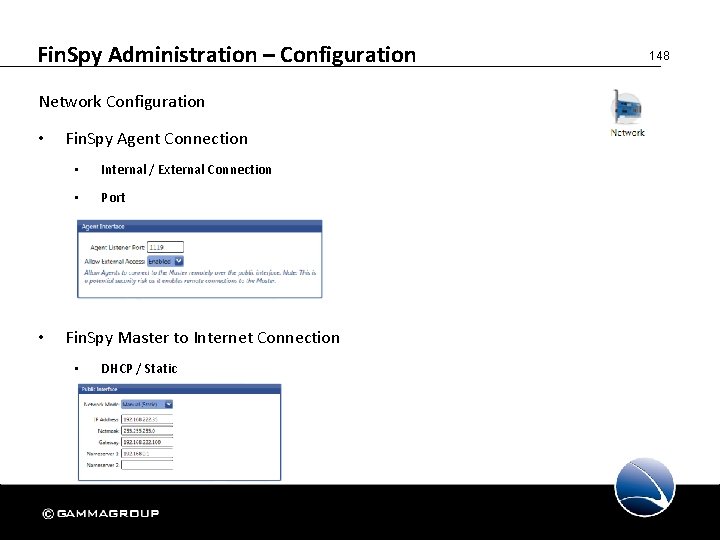
Fin. Spy Administration – Configuration Network Configuration • • Fin. Spy Agent Connection • Internal / External Connection • Port Fin. Spy Master to Internet Connection • DHCP / Static 148

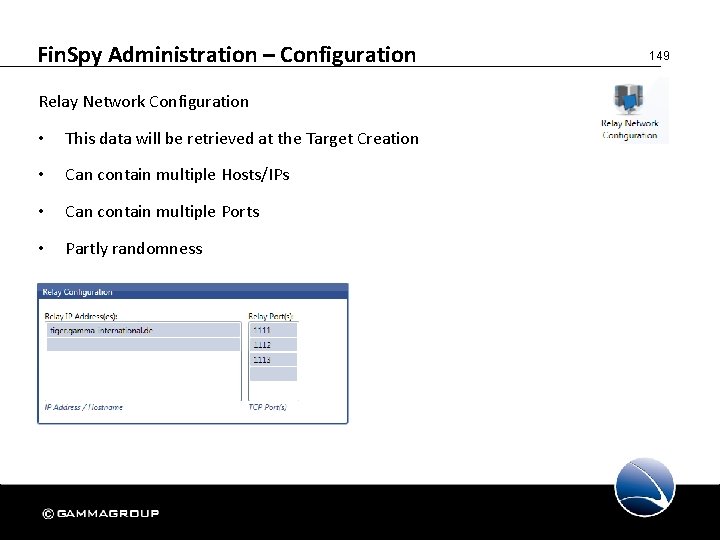
Fin. Spy Administration – Configuration Relay Network Configuration • This data will be retrieved at the Target Creation • Can contain multiple Hosts/IPs • Can contain multiple Ports • Partly randomness 149

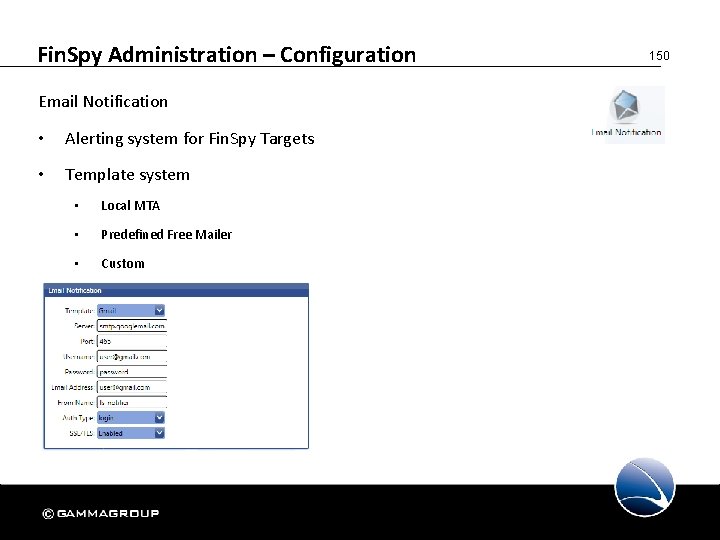
Fin. Spy Administration – Configuration Email Notification • Alerting system for Fin. Spy Targets • Template system • Local MTA • Predefined Free Mailer • Custom 150

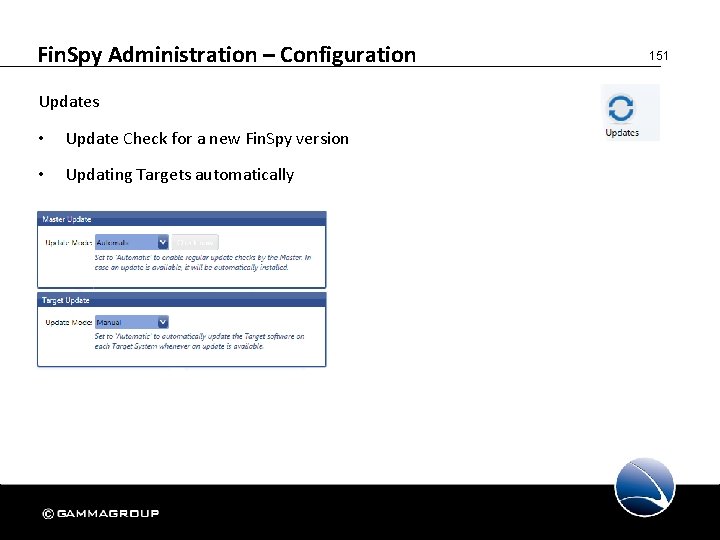
Fin. Spy Administration – Configuration Updates • Update Check for a new Fin. Spy version • Updating Targets automatically 151

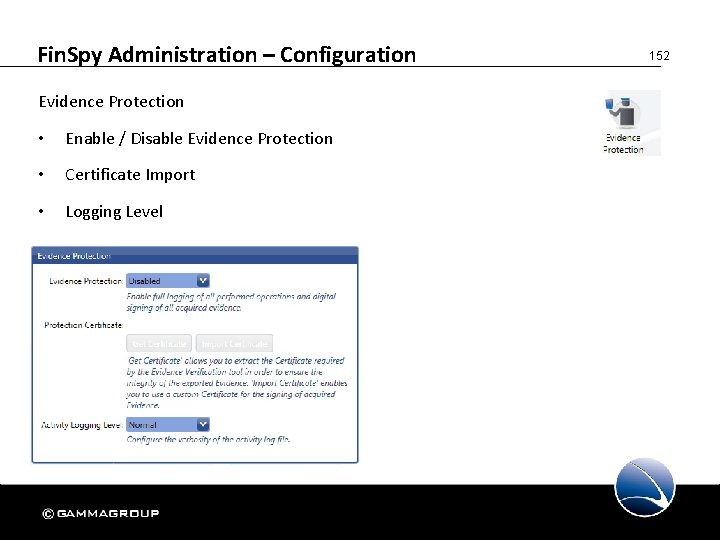
Fin. Spy Administration – Configuration Evidence Protection • Enable / Disable Evidence Protection • Certificate Import • Logging Level 152

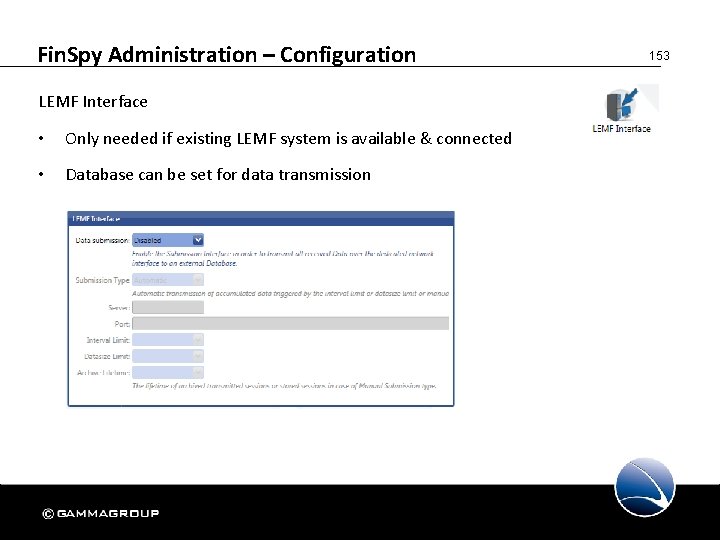
Fin. Spy Administration – Configuration LEMF Interface • Only needed if existing LEMF system is available & connected • Database can be set for data transmission 153

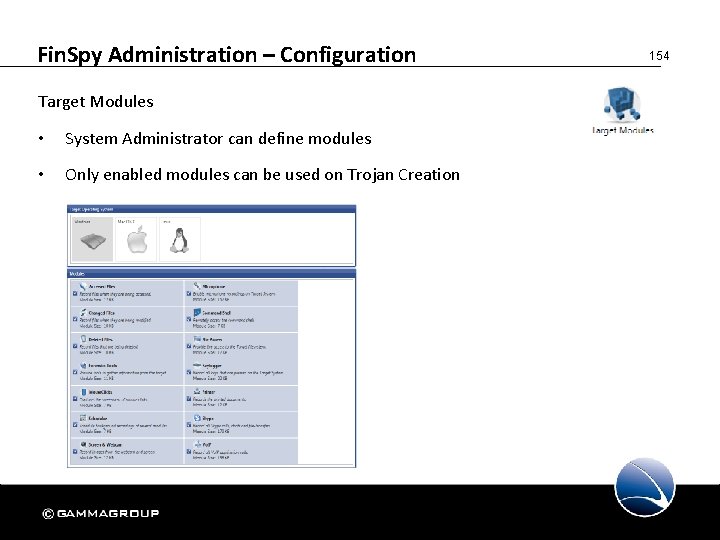
Fin. Spy Administration – Configuration Target Modules • System Administrator can define modules • Only enabled modules can be used on Trojan Creation 154

Fin. Spy Administration 155 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration § Show Logfiles 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

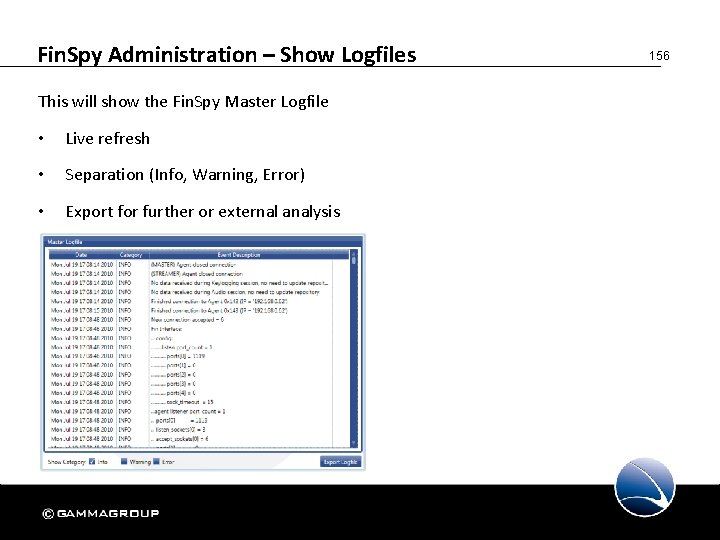
Fin. Spy Administration – Show Logfiles This will show the Fin. Spy Master Logfile • Live refresh • Separation (Info, Warning, Error) • Export for further or external analysis 156

Fin. Spy Administration 157 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration § Agent List 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Administration – Agent List Overview of all configured User Accounts / Fin. Spy Agents • When did what Fin. Spy Agent Login? • From where is the Fin. Spy Agent connecting? • Where is the Fin. Spy Agent connected to? 158

Fin. Spy Administration 159 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration § License Information 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Administration – Agent List Overview of current License Information • Number of Agents / Targets • Validity • Import of a new License 160

Fin. Spy Master 161 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Master – Components Software: • Fin. Spy Master • Fin. Spy Proxy Hardware: • Fin. Spy Master Server • Fin. Spy Master Spare Server • KVM Console • Switch • UPS • Ruggedized Box 162

Fin. Spy Master – Contents 1. Overview 2. Brief Linux Command Instructions 3. Master & Proxy Configuration 4. Monitoring 5. Port Forwarding 6. Dynamic DNS 163

Fin. Spy Master – Overview • One Server with Software • Different Networks • Own File-based Database • Hardened Kernel and Operating System based on Debian • Massive and Robust Space for Data (RAID 6, 1. 6 TB) 164

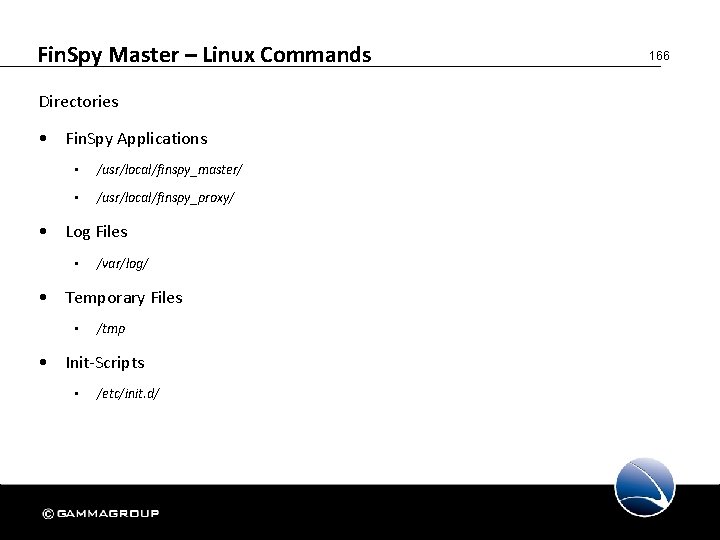
Fin. Spy Master 165 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master § Linux Commands 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Master – Linux Commands Directories • Fin. Spy Applications • /usr/local/finspy_master/ • /usr/local/finspy_proxy/ • Log Files • /var/log/ • Temporary Files • /tmp • Init-Scripts • /etc/init. d/ 166

Fin. Spy Master – Linux Commands • Super User Rights • sudo command • Changing Directories • cd /usr/local/finspy_master/ • Rename File • mv finspy_master. cfg_template finspy_master. cfg • Edit & Read (Configuration File) with Console Text Editor • nano /usr/local/finspy_master/data/finspy_master. cfg • Show latest Entries (of Logfile) • tail –f /var/log/finspy_proxy. log • Show Network Config • ifconfig 167

Fin. Spy Master – Linux Commands • Remove Files • rm filename • Remove Directories • rm –r directoryname • Copy File • cp finspy_master. cfg_template finspy_master. cfg • Show content of file (Version of Fin. Spy Master) • cat /usr/local/finspy_master/data/version 168

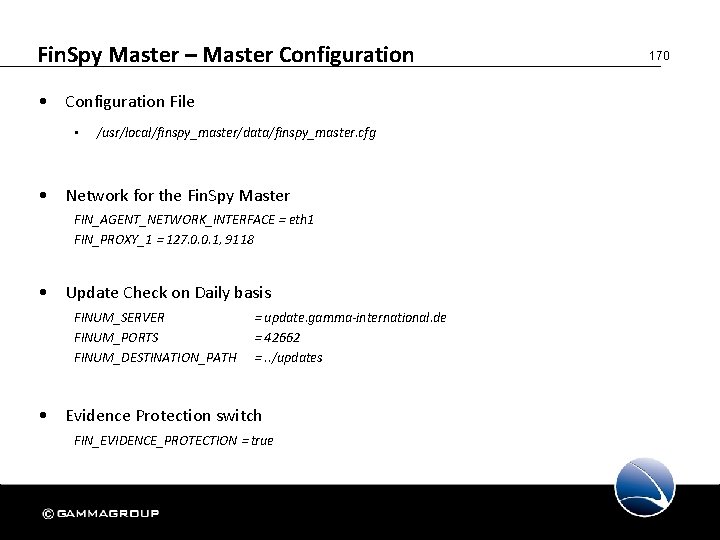
Fin. Spy Master 169 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master § Master Configuration 5. Fin. Spy Relay 6. Troubleshooting

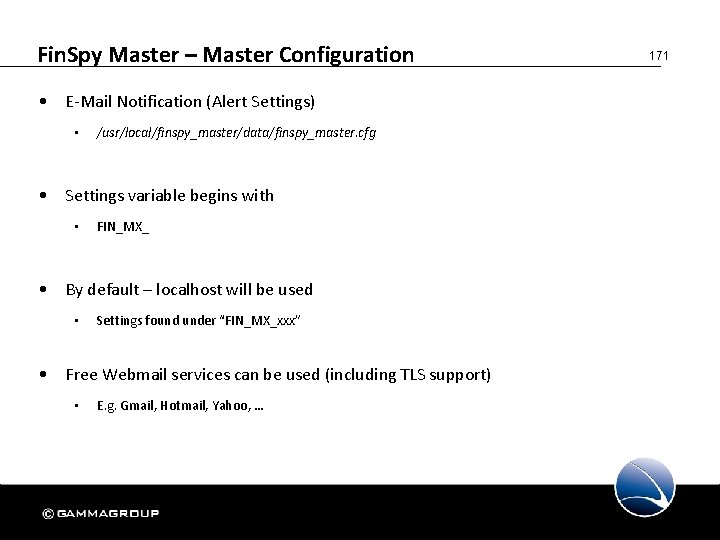
Fin. Spy Master – Master Configuration • Configuration File • /usr/local/finspy_master/data/finspy_master. cfg • Network for the Fin. Spy Master FIN_AGENT_NETWORK_INTERFACE = eth 1 FIN_PROXY_1 = 127. 0. 0. 1, 9118 • Update Check on Daily basis FINUM_SERVER FINUM_PORTS FINUM_DESTINATION_PATH = update. gamma-international. de = 42662 =. . /updates • Evidence Protection switch FIN_EVIDENCE_PROTECTION = true 170

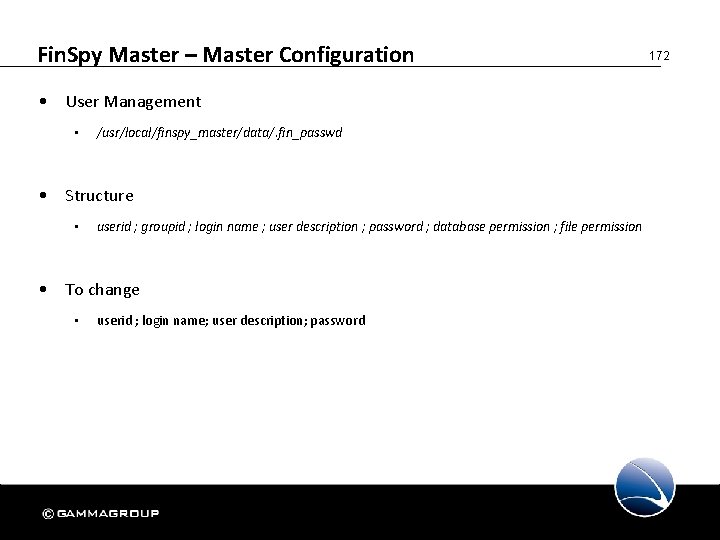
Fin. Spy Master – Master Configuration • E-Mail Notification (Alert Settings) • /usr/local/finspy_master/data/finspy_master. cfg • Settings variable begins with • FIN_MX_ • By default – localhost will be used • Settings found under “FIN_MX_xxx” • Free Webmail services can be used (including TLS support) • E. g. Gmail, Hotmail, Yahoo, … 171

Fin. Spy Master – Master Configuration • User Management • /usr/local/finspy_master/data/. fin_passwd • Structure • userid ; groupid ; login name ; user description ; password ; database permission ; file permission • To change • userid ; login name; user description; password 172

Fin. Spy Master 173 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master § Proxy Configuration 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Master – Proxy Configuration • Configuration File • /usr/local/finspy_master/data/finspy_master. cfg • Network for the Fin. Spy Master FIN_AGENT_NETWORK_INTERFACE = eth 1 FIN_PROXY_1 = 127. 0. 0. 1, 9118 • Ports where Fin. Spy Target or Fin. Spy Relay connect to FIN_TARGET_PORTS = 22, 53, 80, 443, 4111 174

Fin. Spy Master 175 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master § Misc Configuration 5. Fin. Spy Relay 6. Troubleshooting

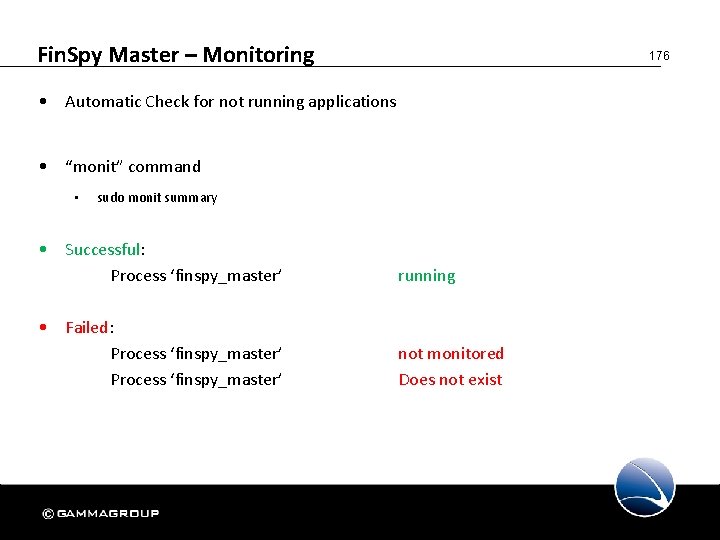
Fin. Spy Master – Monitoring 176 • Automatic Check for not running applications • “monit” command • sudo monit summary • Successful: Process ‘finspy_master’ • Failed: Process ‘finspy_master’ running not monitored Does not exist

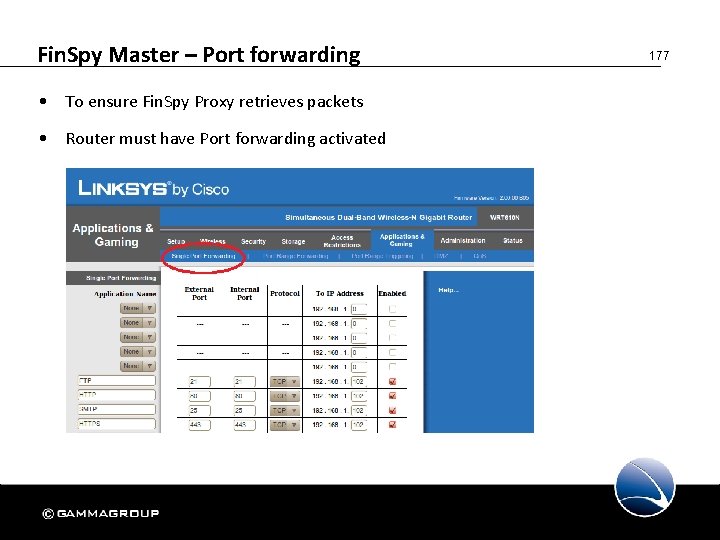
Fin. Spy Master – Port forwarding • To ensure Fin. Spy Proxy retrieves packets • Router must have Port forwarding activated 177

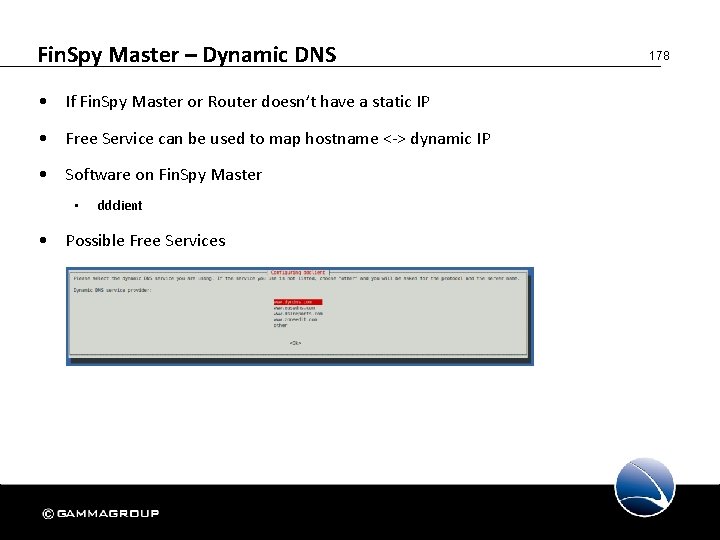
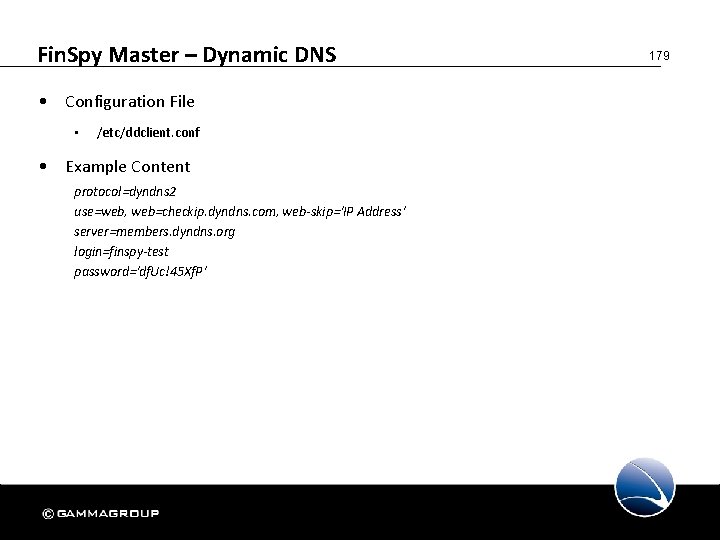
Fin. Spy Master – Dynamic DNS • If Fin. Spy Master or Router doesn’t have a static IP • Free Service can be used to map hostname <-> dynamic IP • Software on Fin. Spy Master • ddclient • Possible Free Services 178

Fin. Spy Master – Dynamic DNS • Configuration File • /etc/ddclient. conf • Example Content protocol=dyndns 2 use=web, web=checkip. dyndns. com, web-skip='IP Address' server=members. dyndns. org login=finspy-test password='df. Uc!45 Xf. P' 179

Fin. Spy Relay 180 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

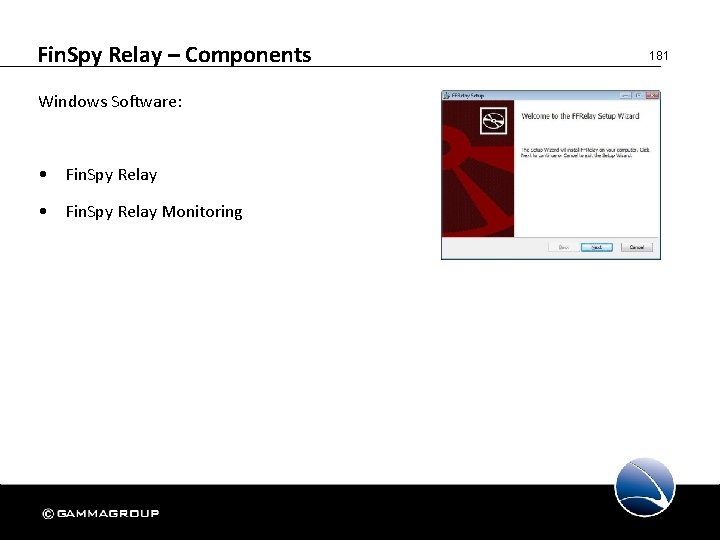
Fin. Spy Relay – Components Windows Software: • Fin. Spy Relay Monitoring 181

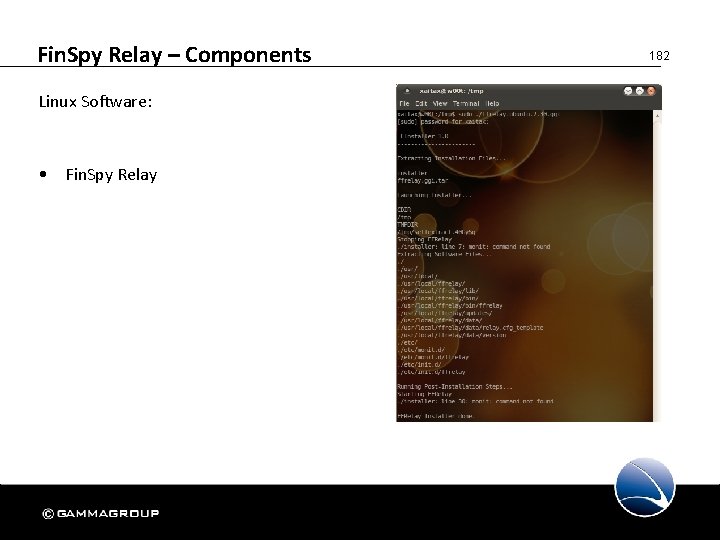
Fin. Spy Relay – Components Linux Software: • Fin. Spy Relay 182

Fin. Spy Relay – Overview • Anonymize Fin. Spy Connections • Can be located anywhere in the world • Small piece of software • No big hardware requirements • Chain of Relays possible 183

Fin. Spy Relay – Requirements Windows: • Windows Firewall must accept Fin. Spy Ports • Windows Server 2003 or higher • Administrator rights Linux: • Debian or Ubuntu System • 256 MB Ram • Monitor software installed (monit) 184

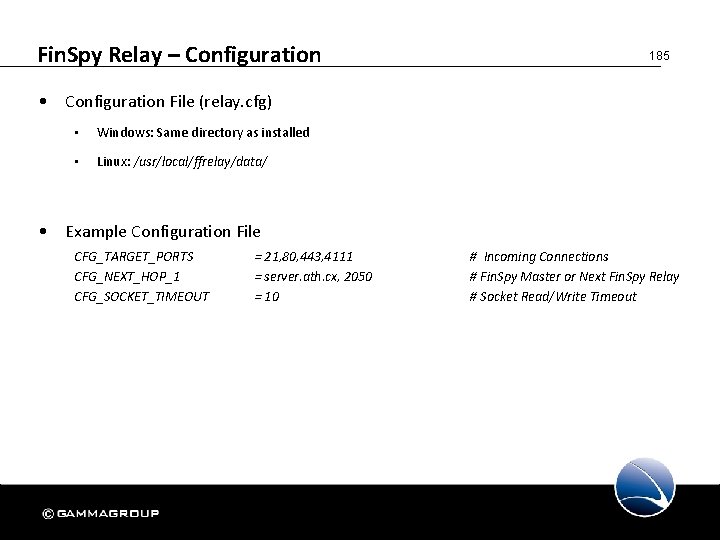
Fin. Spy Relay – Configuration 185 • Configuration File (relay. cfg) • Windows: Same directory as installed • Linux: /usr/local/ffrelay/data/ • Example Configuration File CFG_TARGET_PORTS CFG_NEXT_HOP_1 CFG_SOCKET_TIMEOUT = 21, 80, 443, 4111 = server. ath. cx, 2050 = 10 # Incoming Connections # Fin. Spy Master or Next Fin. Spy Relay # Socket Read/Write Timeout

Troubleshooting 186 1. Introduction 2. Fin. Spy Agent 3. Fin. Spy Administration 4. Fin. Spy Master 5. Fin. Spy Relay 6. Troubleshooting

Fin. Spy Relay – Troubleshooting • Fin. Spy was distributed but Fin. Spy Target doesn’t show online • Discussion of Activation on Target PC and Network Issues 187

Fin. Spy Relay – Troubleshooting • Fin. Fly Dongle / Autostart CD didn’t auto execute • Is Autostart enabled on Fin. Spy Target system? • Windows Vista and Windows 7 have Autostart disabled by default • Correct entry in autorun. inf for Autostart CD? 188

Fin. Spy Relay – Troubleshooting 189 • Fin. Spy is detected by Anti-Virus Vendor XYZ (Be careful, as AV and ASW products these days flag every activity, whats important to Gamma are products that physically remove Finfisher. Otherwise press allow on the Application that flagged. ) • Report to Gamma Group immediately • support@gamma-international. de • I have a suggestion / bug report. Whom to contact? • Login to After-Sales Website • https: //www. gamma-international. de

Vielen Dank für die Aufmerksamkeit Questions? Thank you for your attention! 190
 Spy vs spy font
Spy vs spy font Finfisher download
Finfisher download Spf fin fod fin
Spf fin fod fin Fin fin
Fin fin U2 spy plane political cartoon
U2 spy plane political cartoon I spy creator
I spy creator Smali return true
Smali return true Spionage tools
Spionage tools They say he is spy rewrite in the other voice
They say he is spy rewrite in the other voice I spy simple machines
I spy simple machines Spyaware
Spyaware Robert townsend
Robert townsend Robert hansen spy
Robert hansen spy Picieces
Picieces Si spy net work, big fedjaw iog link kyxogy
Si spy net work, big fedjaw iog link kyxogy Opc data spy
Opc data spy New product development and product life cycle strategies
New product development and product life cycle strategies Contoh joint product dan by product
Contoh joint product dan by product Average product of labor
Average product of labor Product mix product line
Product mix product line Core augmented and actual product
Core augmented and actual product Cross product outer product
Cross product outer product First screen feasibility analysis
First screen feasibility analysis Product mix vs product line
Product mix vs product line Lima buah vektor digambarkan sebagai berikut
Lima buah vektor digambarkan sebagai berikut Core actual and augmented product
Core actual and augmented product Product portfolio mix
Product portfolio mix Rumus perkalian silang
Rumus perkalian silang Gdp 519
Gdp 519 Product compliance training
Product compliance training Embedded design life cycle
Embedded design life cycle Geia-std-0007
Geia-std-0007 Product training objectives
Product training objectives Develop and update food and beverage knowledge
Develop and update food and beverage knowledge Logistics product data training
Logistics product data training Training is expensive without training it is more expensive
Training is expensive without training it is more expensive Metode of the job training
Metode of the job training Aggression replacement training facilitator training
Aggression replacement training facilitator training Water bottle rocket nose cone designs
Water bottle rocket nose cone designs Viaje paris fin de curso
Viaje paris fin de curso Skull fin fish
Skull fin fish Final de tubo
Final de tubo Td gestion des stocks
Td gestion des stocks 4 señales de que cristo viene pronto
4 señales de que cristo viene pronto ¿qué vas a hacer esta semana?
¿qué vas a hacer esta semana? Nosotros ______ ganar.
Nosotros ______ ganar. My finace lab
My finace lab Syn/fin
Syn/fin Spin-fin kysely
Spin-fin kysely Marco logico
Marco logico On ne veut pas la fin du monde
On ne veut pas la fin du monde Fiche de lecture de la ficelle
Fiche de lecture de la ficelle Food chain dolphin
Food chain dolphin What does shark skin feel like
What does shark skin feel like Fish and shellfish processing
Fish and shellfish processing Fin aid eseog
Fin aid eseog Myo armband price in india
Myo armband price in india Fin bot
Fin bot Fin fails nnn
Fin fails nnn Fin 413
Fin 413 Fin 3000
Fin 3000 Fin 3000
Fin 3000 Fin del diluvio
Fin del diluvio Clases de lenguaje
Clases de lenguaje Diploma fin de curso infantil
Diploma fin de curso infantil Polar form to cartesian form
Polar form to cartesian form On old olympus towering tops a fin
On old olympus towering tops a fin Fin d'année scolaire college 2022
Fin d'année scolaire college 2022 Fin del parlamentarismo en chile
Fin del parlamentarismo en chile Cmup en fin de période
Cmup en fin de période What happened when the ladybug met the whale
What happened when the ladybug met the whale On veut pas la fin du monde
On veut pas la fin du monde Fin resistance
Fin resistance Michel delpech - la fin du chemin
Michel delpech - la fin du chemin Los 7 años de tribulacion
Los 7 años de tribulacion Fin valioso
Fin valioso Bottle rocket fins design
Bottle rocket fins design Nric checksum formula
Nric checksum formula Affirmative easement
Affirmative easement Fin 221
Fin 221 Neoclasismo
Neoclasismo I fin
I fin Shark fin etco2 waveform
Shark fin etco2 waveform Shark fin etco2 waveform
Shark fin etco2 waveform Fin viz map
Fin viz map Ifstream fin
Ifstream fin Viajes de fin de curso 4 eso
Viajes de fin de curso 4 eso Sistema cremallera
Sistema cremallera Pompe doshydro
Pompe doshydro Vilu fin
Vilu fin Bon dimanche dans le seigneur
Bon dimanche dans le seigneur Conditional asset retirement obligation
Conditional asset retirement obligation Rapport de fin de formation
Rapport de fin de formation Rapport de fin de formation
Rapport de fin de formation Afrika karte gebirge
Afrika karte gebirge Fin 303
Fin 303 Fin 3000
Fin 3000 Fin 3000
Fin 3000 Adonde vas ahora a la clase de matematicas
Adonde vas ahora a la clase de matematicas Fin
Fin En qué actividades se entona el himno nacional de panamá
En qué actividades se entona el himno nacional de panamá Cis 3360
Cis 3360 Au cours de la semaine prochaine
Au cours de la semaine prochaine Imágenes que digan fin
Imágenes que digan fin Imágenes que digan fin
Imágenes que digan fin Planteamiento del problema trabajo fin de grado
Planteamiento del problema trabajo fin de grado 65535/20
65535/20 Fin y
Fin y Sequence number
Sequence number Ciri piri
Ciri piri Dorsal fin
Dorsal fin Den fin reanimation
Den fin reanimation El fin de todo discurso es este teme a dios
El fin de todo discurso es este teme a dios Jour de la semaine au pluriel
Jour de la semaine au pluriel Fin 360
Fin 360 Sfas 109
Sfas 109 Temperatura constante
Temperatura constante Fin ops
Fin ops Fin diaporama
Fin diaporama Mm proposition i with taxes
Mm proposition i with taxes Fin 3000
Fin 3000 Double pipe
Double pipe Diploma
Diploma Inicio y fin
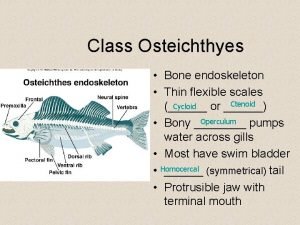
Inicio y fin Bony endoskeleton
Bony endoskeleton La fin des haricots bourvil
La fin des haricots bourvil Fin del tiempo de gracia
Fin del tiempo de gracia Bacus dios
Bacus dios A ver si por fin
A ver si por fin Shark fin soup
Shark fin soup Bottle rocket fin designs
Bottle rocket fin designs Symboler dikt
Symboler dikt Funcion de identidad
Funcion de identidad Menudo fin de semana valladolid
Menudo fin de semana valladolid Rome fin
Rome fin Tornillo sin fin
Tornillo sin fin Market risk economic capital
Market risk economic capital Dorsal fin with spines
Dorsal fin with spines La otra voz. poesía y fin de siglo octavio paz
La otra voz. poesía y fin de siglo octavio paz Fin de la monarchie
Fin de la monarchie Que hice el fin de semana
Que hice el fin de semana Sylvie cogneau
Sylvie cogneau Lucky fin
Lucky fin Fin de la guerra fría mapa conceptual
Fin de la guerra fría mapa conceptual Fin à la faim charlemagne
Fin à la faim charlemagne Total fin
Total fin Fin 440
Fin 440 Fin 3310
Fin 3310 Représentation filetage
Représentation filetage Dichoso yo si al fin del dia
Dichoso yo si al fin del dia Engranes
Engranes A fin de conocerle y el poder de su resurrección
A fin de conocerle y el poder de su resurrección Fin fisher
Fin fisher Catharina glaas
Catharina glaas Bursar twu
Bursar twu Hannah xavier
Hannah xavier Fin aid uci
Fin aid uci Fin ulusunun ünlü destanı
Fin ulusunun ünlü destanı Swiftnet fin
Swiftnet fin Slant fin boiler reset button
Slant fin boiler reset button Dålig komparatiivi
Dålig komparatiivi Learning task 7 create a self portrait
Learning task 7 create a self portrait Narrow product launch windows
Narrow product launch windows Right hand rule physics torque
Right hand rule physics torque What product is being advertised?
What product is being advertised? 7elife plan
7elife plan Types of interior displays
Types of interior displays Dot ans
Dot ans Product rule probability
Product rule probability International product decisions
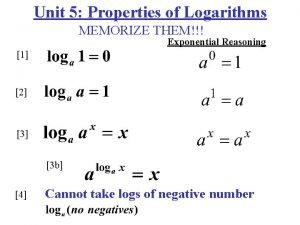
International product decisions Simplifying logarithms
Simplifying logarithms Advantages of product orientation
Advantages of product orientation Elements of product mix
Elements of product mix Condensing logs
Condensing logs Unified products and services inc
Unified products and services inc Agile product cost management
Agile product cost management Aqa product design
Aqa product design Tourism product development
Tourism product development Total product offering
Total product offering Product line depth
Product line depth Advantages of product orientation
Advantages of product orientation Biggest mistakes product management
Biggest mistakes product management Structured products technology
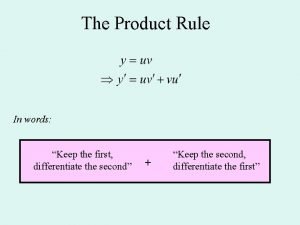
Structured products technology Product formula of differentiation
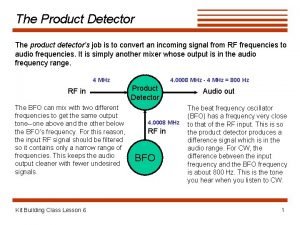
Product formula of differentiation Product detector
Product detector Svpg product strategy
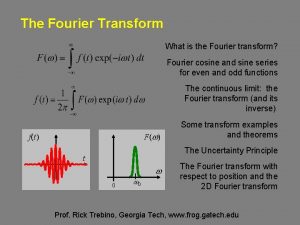
Svpg product strategy Fourier transform of product of two functions
Fourier transform of product of two functions Virtunet systems
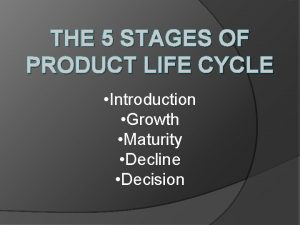
Virtunet systems Product life cycle 5 stages
Product life cycle 5 stages Ntp iso 20345:2008
Ntp iso 20345:2008 Product line definition
Product line definition