UNITVII Advanced Micro Processors Introduction to 80286 Salient






- Slides: 33

UNIT-VII Advanced Micro Processors Introduction to 80286 Salient Features of 80386 Real and Protected Mode Segmentation & Paging Salient Features of Pentium Overview of RISC Processors.

Features of 80286 16 bit µp 16 Mbytes physical memory Multi-user Multitasking OS User protection Virtual memory management

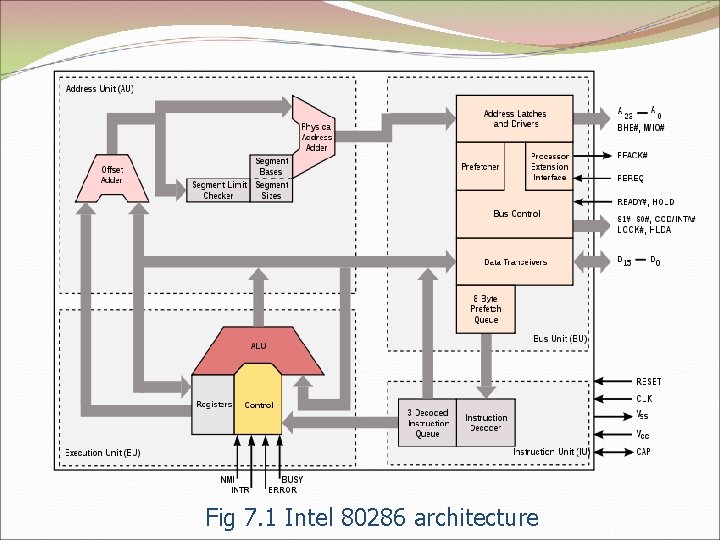
80286 Architecture The bus unit – BU Performs all memory and i/o reads and writes, pre-fetches instruction bytes and controls transfer of data to and from processor extension devices such as the 80287 math coprocessor. The instruction unit – IU IU fully decodes up to three pre-fetched instructions and holds them in a queue, where the execution unit can access them. Instructions in the pipeline The execution unit – EU Machine Status Word (MSW) register The address unit – AU AU computes the physical addresses that will be sent out to memory or I/O by the BU. Real address mode protected virtual address mode

Fig 7. 1 Intel 80286 architecture

Register organization Eight 16 -bit GPRs AX, BX, CX, DX, BP, SI, DI Four 16 -bit segment regs. DS, CS, SS, ES. Status and control reg. Flag reg. Instruction pointer (IP)

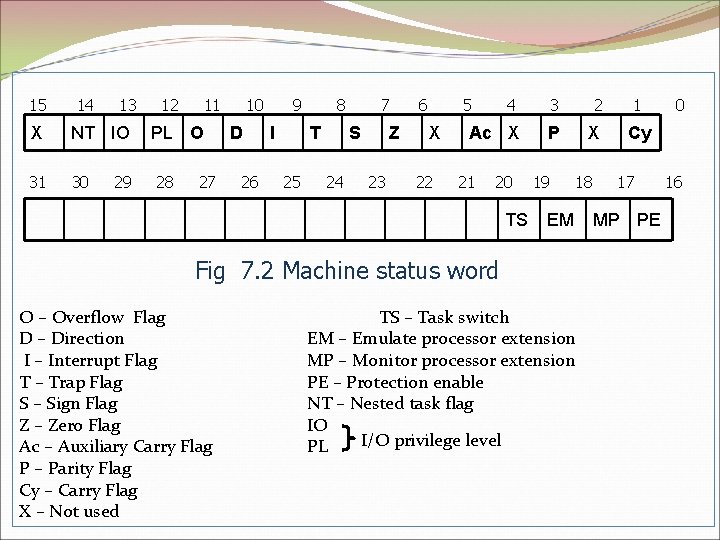
15 14 13 X NT IO 31 30 29 12 11 PL O 28 27 10 D 26 9 I 8 T 25 7 S 24 Z 23 6 5 X 22 4 3 2 Ac X P X 21 20 TS 19 18 EM Fig 7. 2 Machine status word O – Overflow Flag D – Direction I – Interrupt Flag T – Trap Flag S – Sign Flag Z – Zero Flag Ac – Auxiliary Carry Flag P – Parity Flag Cy – Carry Flag X – Not used TS – Task switch EM – Emulate processor extension MP – Monitor processor extension PE – Protection enable NT – Nested task flag IO I/O privilege level PL 1 0 Cy 17 MP PE 16

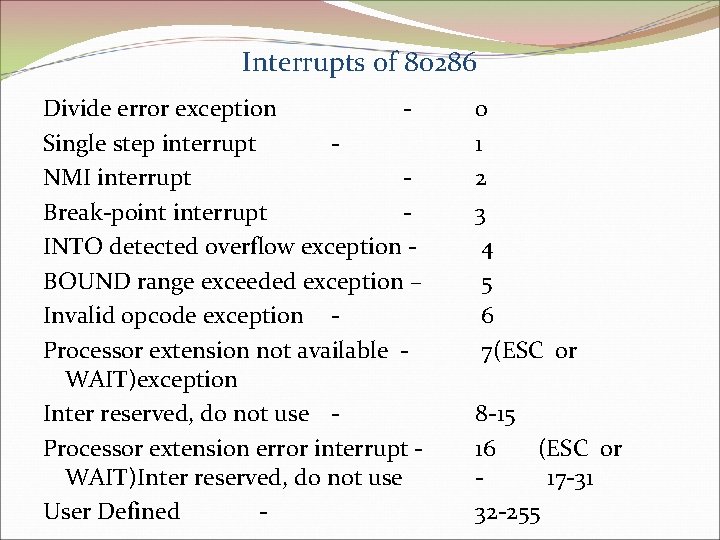
Interrupts of 80286 Divide error exception Single step interrupt NMI interrupt Break-point interrupt INTO detected overflow exception BOUND range exceeded exception – Invalid opcode exception Processor extension not available WAIT)exception Inter reserved, do not use Processor extension error interrupt WAIT)Inter reserved, do not use User Defined - 0 1 2 3 4 5 6 7(ESC or 8 -15 16 (ESC or 17 -31 32 -255

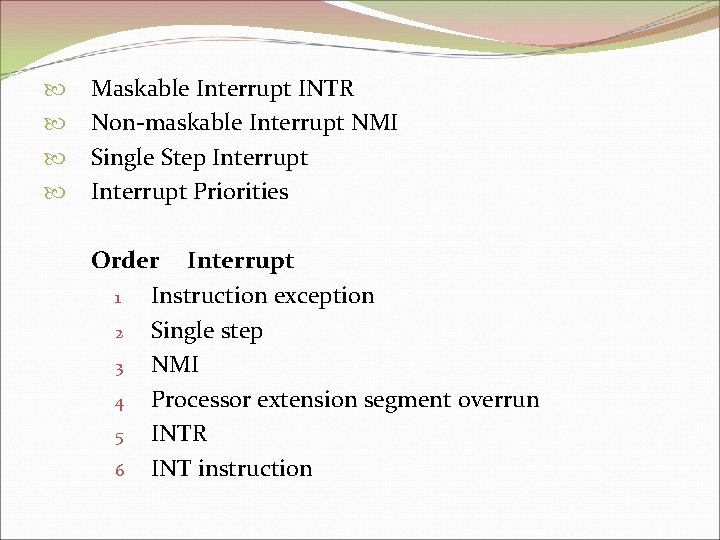
Maskable Interrupt INTR Non-maskable Interrupt NMI Single Step Interrupt Priorities Order Interrupt 1 Instruction exception 2 Single step 3 NMI 4 Processor extension segment overrun 5 INTR 6 INT instruction

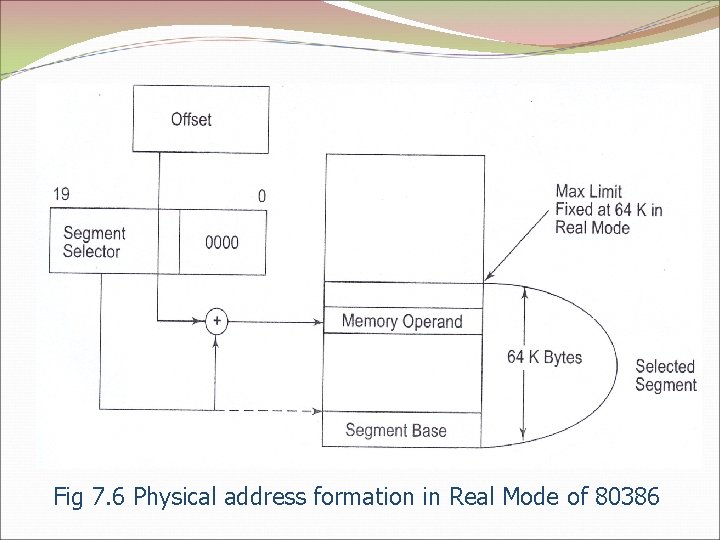
80286 Real Address Mode Operation After the 80286 is reset, it starts executing in its real address mode. MS-DOS systems operates in Real Address Mode In this mode 80286 can address up to 1 MB of physical memory. Interrupt Vector Table of the 80286 is located in the first 1 KB of memory. (from address 00000 h to 003 FFh ). The addresses from FFFF 0 h to FFFFFh are reserved for system initialization. Functions performed in this mode: It initializes the IP and other registers of 80286 Initializes the peripheral Enables interrupts Sets up descriptor tables Prepares for entering the protected virtual address mode.

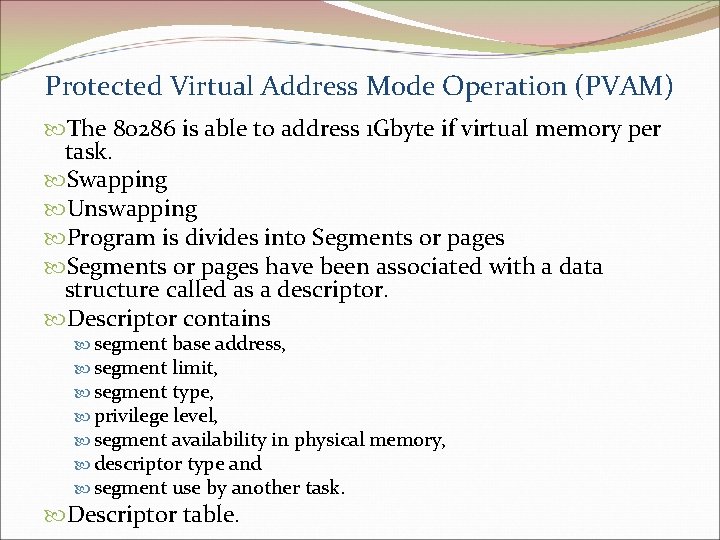
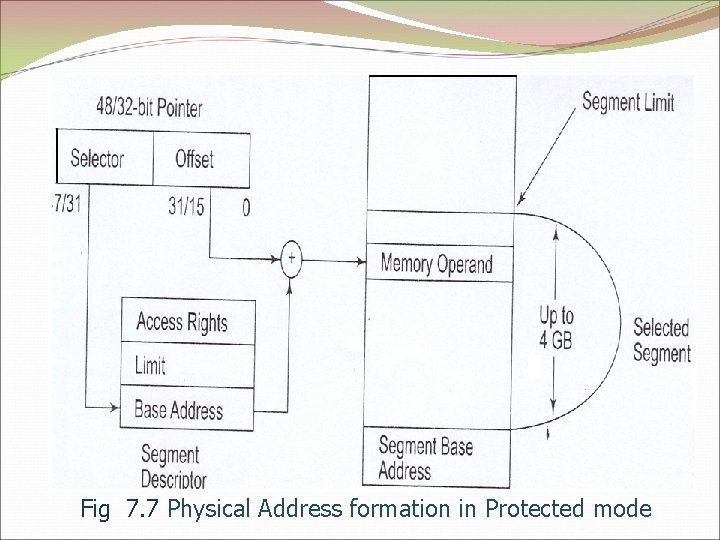
Protected Virtual Address Mode Operation (PVAM) The 80286 is able to address 1 Gbyte if virtual memory per task. Swapping Unswapping Program is divides into Segments or pages have been associated with a data structure called as a descriptor. Descriptor contains segment base address, segment limit, segment type, privilege level, segment availability in physical memory, descriptor type and segment use by another task. Descriptor table.

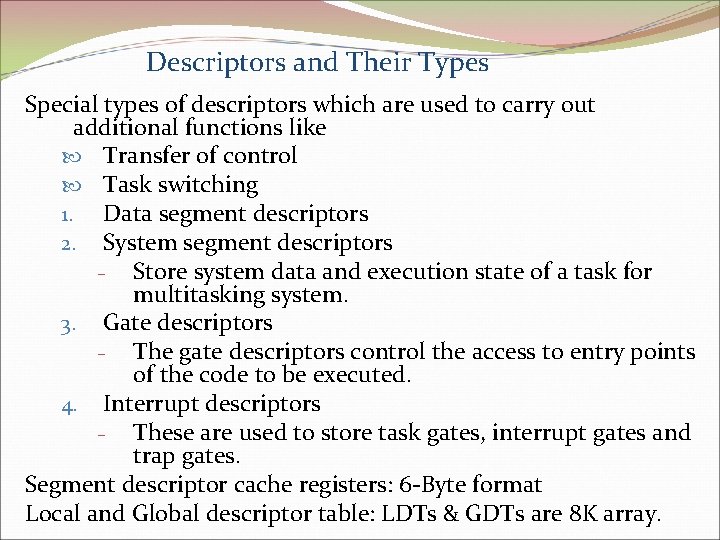
Descriptors and Their Types Special types of descriptors which are used to carry out additional functions like Transfer of control Task switching 1. Data segment descriptors 2. System segment descriptors – Store system data and execution state of a task for multitasking system. 3. Gate descriptors – The gate descriptors control the access to entry points of the code to be executed. 4. Interrupt descriptors – These are used to store task gates, interrupt gates and trap gates. Segment descriptor cache registers: 6 -Byte format Local and Global descriptor table: LDTs & GDTs are 8 K array.

Privilege The 80286 supports a four level hierarchical privilege mechanism to control the access to descriptors to prevent unwanted access to any of the code or data segments. Unintentional interference in the higher privilege level tasks. (level 0 is the most privilege level while level 4 is the least) The privilege levels provide protection within a task.

Protection The 80286 supports three basic mechanisms to provide protection: 1. Restricted use of segments (segment load check): • This is accomplished with the help of read/write privileges. The segment usages are restricted by classifying the corresponding descriptors under LDT and GDT. 2. Restricted Accesses to Segment (operation reference check): • This is accomplished using descriptor usages limitations and the rules of privilege check 3. Privileged Instructions or Operations (privileged instruction check): • These are to be executed or carried out at certain privilege levels determined by current privilege level (CPL) and I/O

Special Operations Processor reset and initialization The processor is reset by applying a high on RESET input that terminates all execution and internal bus activities till RESET remains high. Task switch operation A no. of task allocation strategies like FCFS, STF, Time sharing, etc. In case of time sharing, the CPU’s time is divided into equal duration slices. The switch-over operation from one task to another is called as task switch operation. This operation is carried out using a JMP or CALL to a new segment of the new task. Pointer testing instructions The pointer testing instructions of 80286 use the memory management hardware to verify whether the loaded selector value refers to a valid segment without generating any exception.

Protected mode initialization The initialization of protected mode is carried out in real mode by setting the internal registers of 80286 suitably. To enter into protected mode, 80286 executes LMSW (load MSW) instruction that set PE flag. How to enter protected mode? The execution of instruction LIDT (load interrupt descriptor table base) prepares the 80286 for protected virtual address mode. Then the PE flag of MSW is set to enter the PVAM, using the LMSW instruction. Halt This instruction stops program execution and prevents the CPU from restarting, till it is interrupted or RESET is asserted. If the CPU is interrupted in the HALT state, the execution starts from the next instruction after HLT.

80286 Bus Interface The I/O devices are also addressed using even and odd address banks technique, using A 0 and BHE. The 80286 bus cycles are of six types Memory read Memory write I/O read I/O write Interrupt acknowledge Halt. The 80286 bus at a particular instant may be in either of these four states: 1. Idle state (Ti) 2. Perform command state (Tc) 3. Send status state (Tc) 4. Hold state (TH)

80386 µp 32 -bit µp 4 GB physical memory 16 K - segment size Page size – 4 KB 8 debug registers DR 0 -DR 7 80386 has an on-chip address translation 80386 DX 132 pins, 20 MHz, 33 MHz 80386 SX 16 -bit data bus 24 -bit address bus

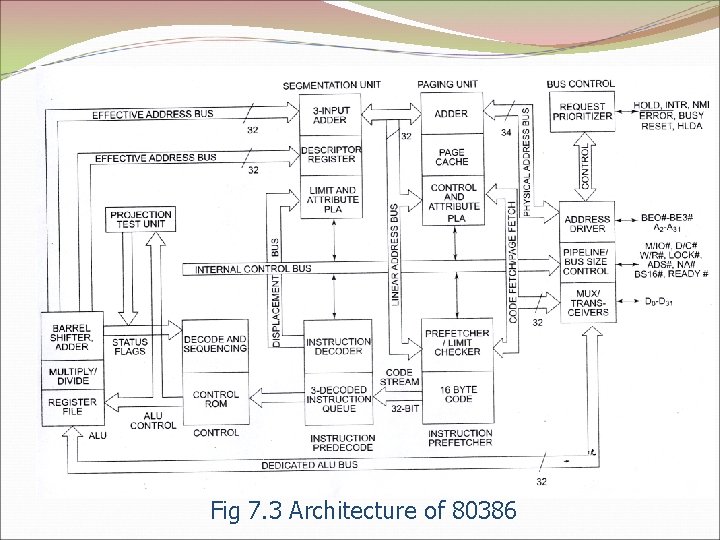
Fig 7. 3 Architecture of 80386

1. Central Processing Unit (CPU) • Execution Unit 1. 8 – General Purpose Registers 2. 8 – Special Purpose Registers • Instruction Unit 1. 16 -byte instruction code queue 2. 3 -byte instruction decoded queue 3. The barrel shifter increases the speed of all shift and rotate operations

2. Memory Management Unit (MMU) • Segment Unit 1. 4 -GB size of segment 2. Segment and offset for relocability 3. SU provides a 4 level protection mechanism for protection and isolating the system’s code and data. • Page Unit 1. Each segment is further divided into pages 2. 4 KB- page size 3. Page Unit works under Segment Unit 4. It converts linear address into physical address 3. Bus Control Unit (BCU) • Bus control unit had a prioritizer to resolve the priority of the various bus requests.

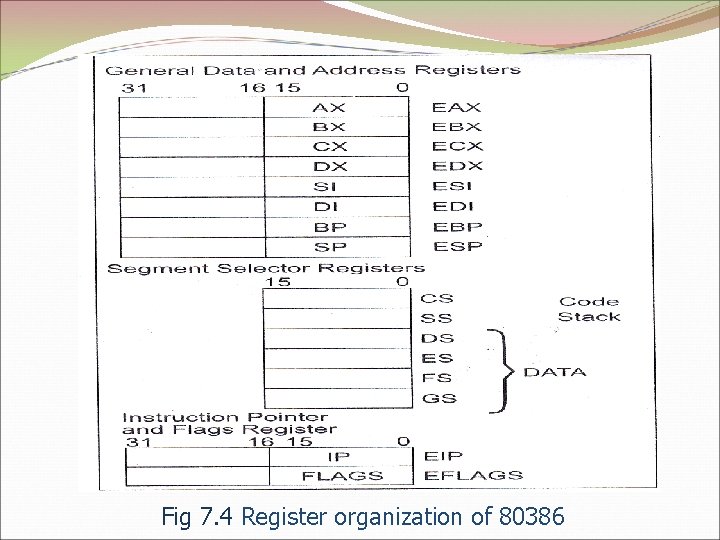
Fig 7. 4 Register organization of 80386

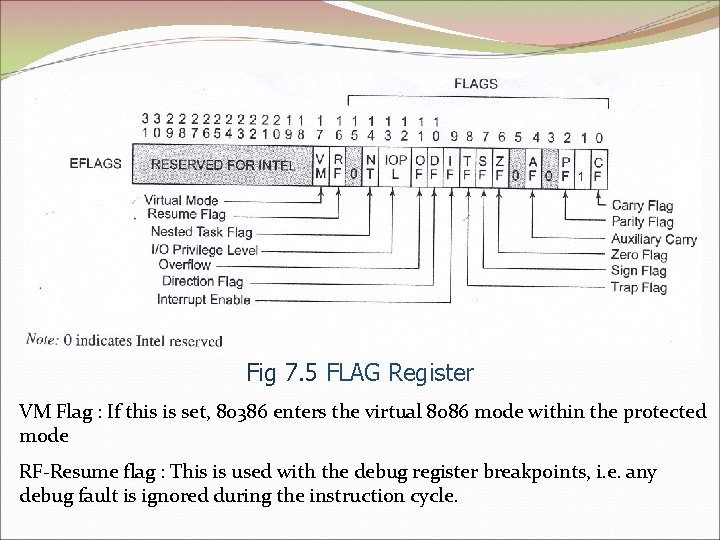
Fig 7. 5 FLAG Register VM Flag : If this is set, 80386 enters the virtual 8086 mode within the protected mode RF-Resume flag : This is used with the debug register breakpoints, i. e. any debug fault is ignored during the instruction cycle.

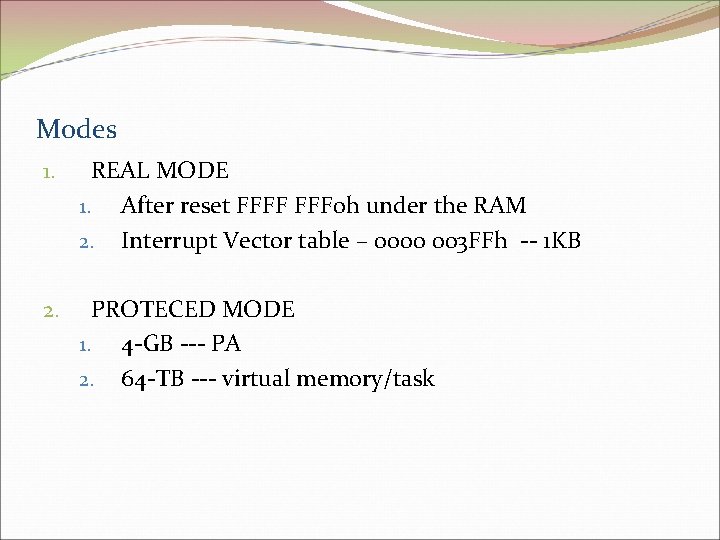
Modes 1. REAL MODE 1. After reset FFFF 0 h under the RAM 2. Interrupt Vector table – 0000 003 FFh -- 1 KB 2. PROTECED MODE 1. 4 -GB --- PA 2. 64 -TB --- virtual memory/task

Fig 7. 6 Physical address formation in Real Mode of 80386

Fig 7. 7 Physical Address formation in Protected mode

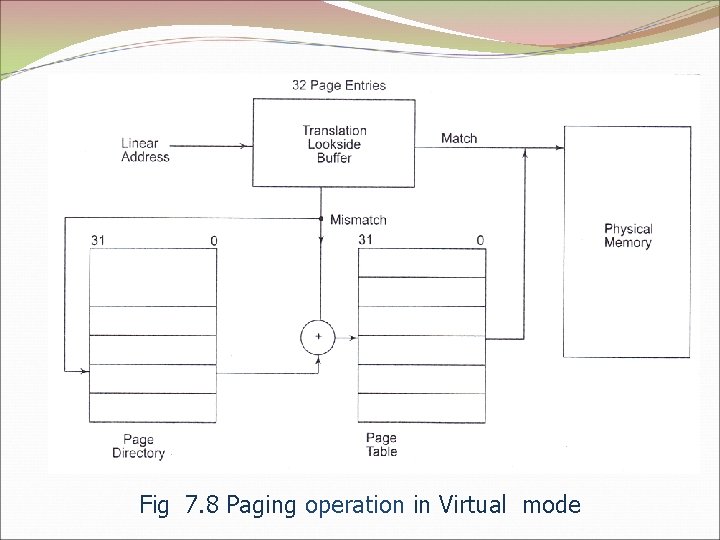
Fig 7. 8 Paging operation in Virtual mode

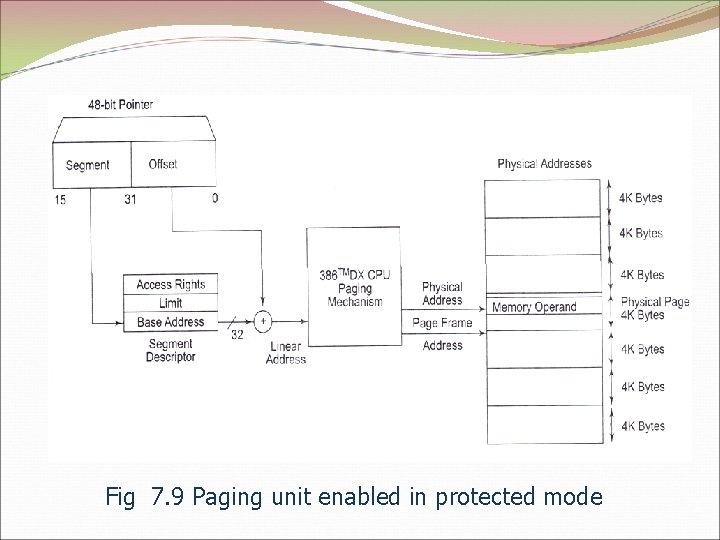
Fig 7. 9 Paging unit enabled in protected mode

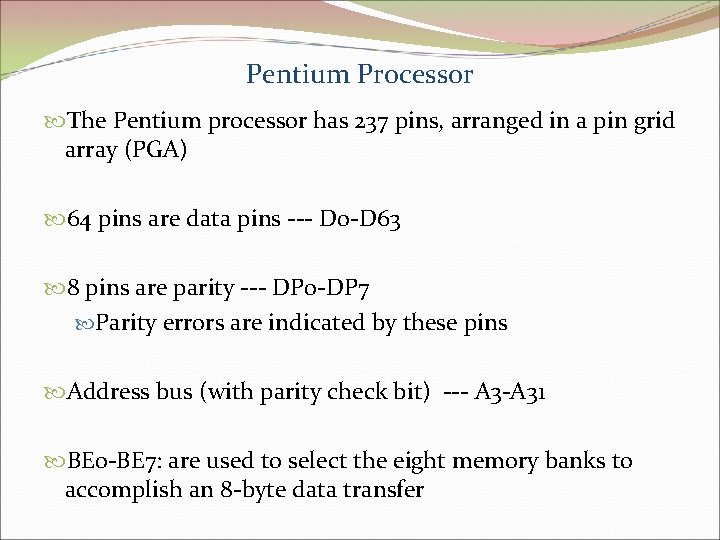
Pentium Processor The Pentium processor has 237 pins, arranged in a pin grid array (PGA) 64 pins are data pins --- D 0 -D 63 8 pins are parity --- DP 0 -DP 7 Parity errors are indicated by these pins Address bus (with parity check bit) --- A 3 -A 31 BE 0 -BE 7: are used to select the eight memory banks to accomplish an 8 -byte data transfer

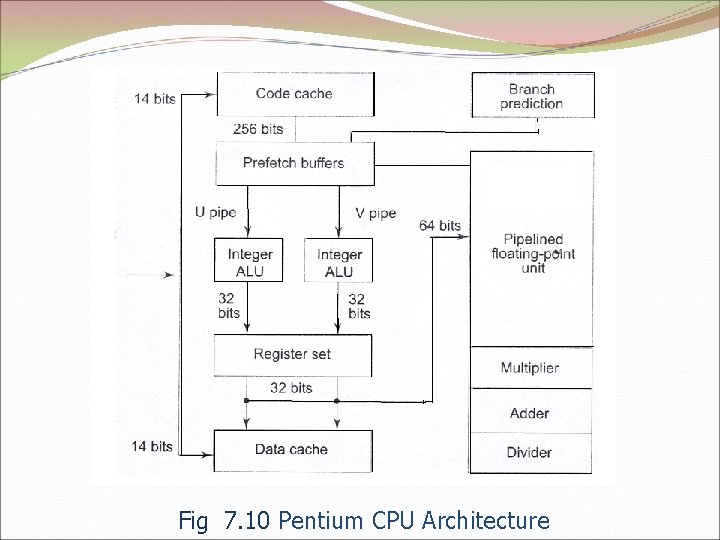
Fig 7. 10 Pentium CPU Architecture

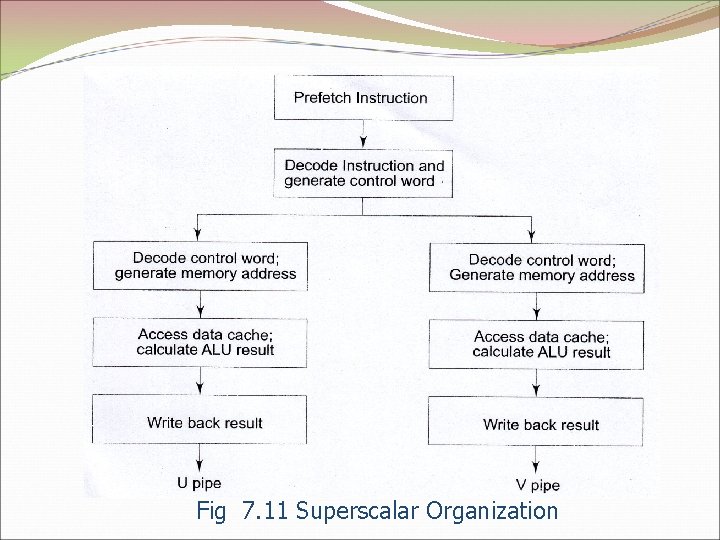
Fig 7. 11 Superscalar Organization

RISC Processors RISC: Reduced Instruction Set Computer CISC : complex instructions Increase in processor die size Consumes more power and silicon Needs more cooling arrangement. RISC: Small, highly optimized set of instructions Every instruction is executed in a single clock after it is fetched and decoded. Very fast execution Less power consumption

The Advantages of RISC instructions, being simple, can be hard-wired Processor can work at a high clock frequency and thus yields higher speed. On-chip MMU, Floating point arithmetic units. Chip cost is low More devises can place on chip Compilers produce more efficient codes in RISC µp Loading and decoding of instructions in a RISC processor is simple and fast.

Design issues of RISC processor Register Windowing Massive Pipelining Single cycle instruction execution Some RISC processors 1. MIPS 2. Sun Ultra SPARC