Understanding Operating Systems Seventh Edition Chapter 15 Linux























- Slides: 58

Understanding Operating Systems Seventh Edition Chapter 15 Linux Operating Systems

Learning Objectives After completing this chapter, you should be able to describe: • The design goals for the Linux operating system • The flexibility offered by using files to manipulate devices • The roles of the Memory, Device, File, Processor, and Network Managers • The impact of open source software • Some strengths and weaknesses of Linux Understanding Operating Systems, 7 e 2

Introduction • Linux – Originally based on a version of UNIX – Powerful – Inexpensive or free to use • Portable – Versions for cell phones, supercomputers, and computing systems in between • Source code: freely available – Configurable: runs any device; meets any specification Understanding Operating Systems, 7 e 3

Introduction (cont'd. ) • Open source – Source code freely available to anyone for improvement – Under constant development – Contributors around the world: not paid for their work Understanding Operating Systems, 7 e 4

Brief History • Developed by Linus Torvalds (1991) • Original purpose – Maximize Intel 80386 microprocessor’s limited capabilities – Roots • MINIX: miniature UNIX with more functionality • First version meant for small microcomputer – Expensive commercial computer features • Flexibility and functionality – Brought UNIX features to small computer Understanding Operating Systems, 7 e 5

Brief History (cont'd. ) • User interface – First Linux operating systems: command-driven interface • Sometimes cryptic commands – Recent years • Graphical user interfaces (GUI) • Written and distributed under the GNU General Public License • Fedora Project responsible for the open-source development of the Linux kernel Understanding Operating Systems, 7 e 6

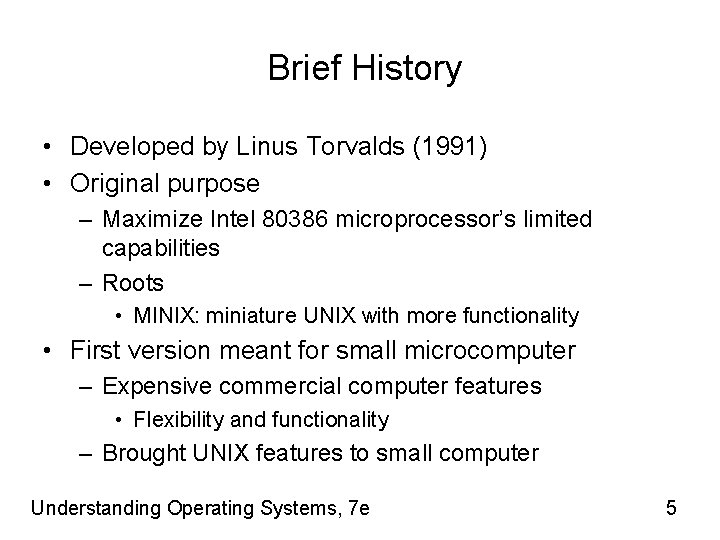
(table 15. 1) Selected releases of Ubuntu Linux. New releases are scheduled every 6 months. Normal Ubuntu releases are supported for 18 months; LTS releases are supported longer. (adapted from https: //wiki. ubuntu. com/Releases) © Cengage Learning 2014 Understanding Operating Systems, 7 e 7

Design Goals • Three goals – Modularity – Simplicity – Portability • Numerous standard utilities – Eliminate need to write special code – Used in combination for specific tasks • Numerous functions • IEEE POSIX (Portable Operating System Interface) specifications conformity – Programs’ portability Understanding Operating Systems, 7 e 8

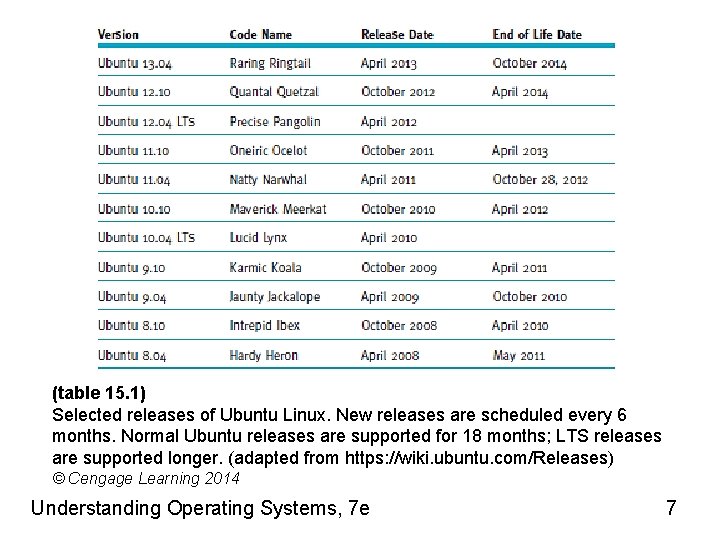
(table 15. 2) Select system functions supported by Linux. © Cengage Learning 2014 Understanding Operating Systems, 7 e 9

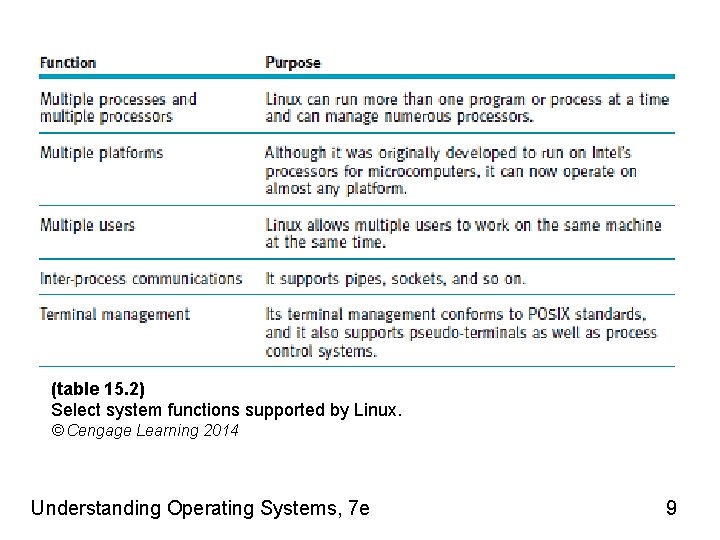
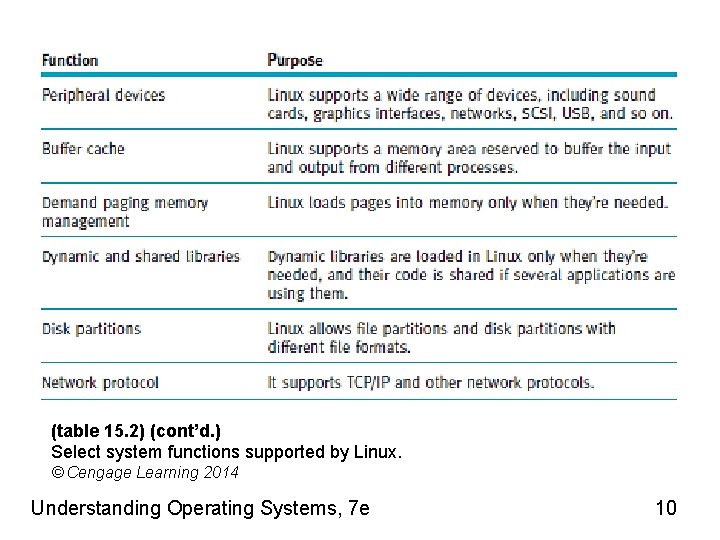
(table 15. 2) (cont’d. ) Select system functions supported by Linux. © Cengage Learning 2014 Understanding Operating Systems, 7 e 10

Memory Management • Space allocation – Kernel: 1 GB high order memory – Executing processes: 3 GB memory • Process execution – Fixed-size segment – System calls change segment size • Memory protection – Based on information type stored in address space region for process Understanding Operating Systems, 7 e 11

Memory Management (cont'd. ) • Page loading – Least recently used algorithm (LRU) – Maintains a dynamically managed memory area and page cache (new and old pages inserted and deleted) • System page tables – Track free and busy pages – Added flexibility with swap devices • Virtual memory – Managed using multiple-level table hierarchy • 64 - and 32 -bit architectures Understanding Operating Systems, 7 e 12

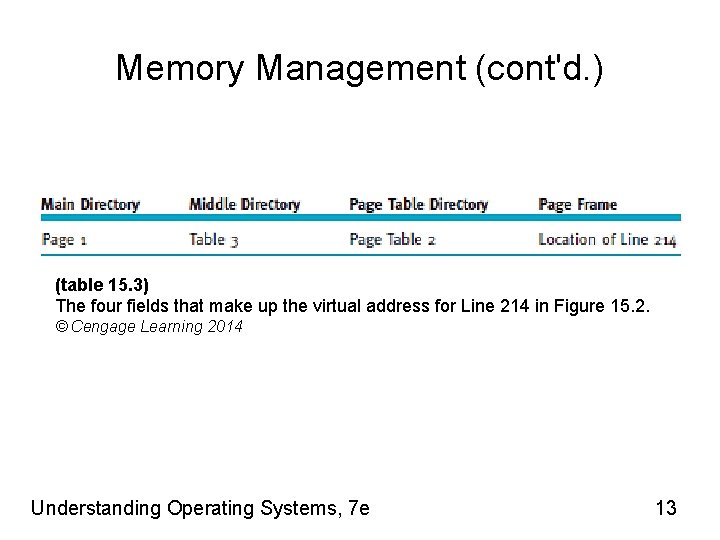
Memory Management (cont'd. ) (table 15. 3) The four fields that make up the virtual address for Line 214 in Figure 15. 2. © Cengage Learning 2014 Understanding Operating Systems, 7 e 13

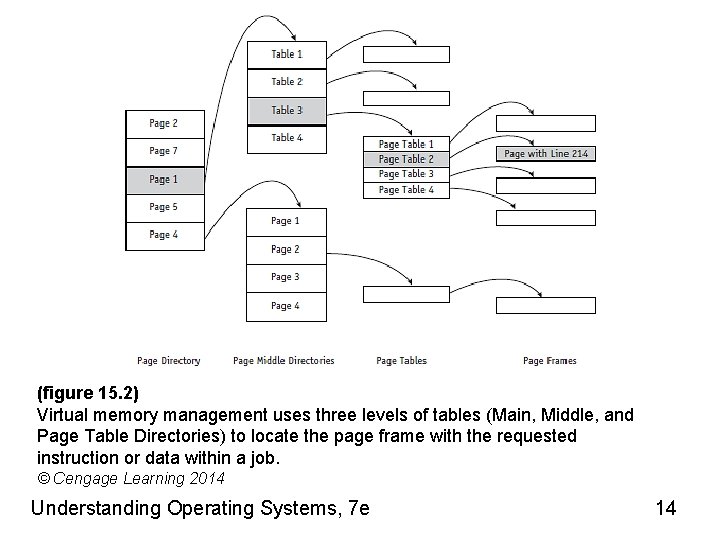
(figure 15. 2) Virtual memory management uses three levels of tables (Main, Middle, and Page Table Directories) to locate the page frame with the requested instruction or data within a job. © Cengage Learning 2014 Understanding Operating Systems, 7 e 14

Memory Management (cont'd. ) • Buddy algorithm – Groups and splits into equal-sized page frames • Gives more contiguous space to job • Page replacement algorithm – Clock page replacement policy: expanded version – Uses eight-bit byte to track page’s activity: “age” – Page swap based on form of least frequently used (LFU) replacement policy Understanding Operating Systems, 7 e 15

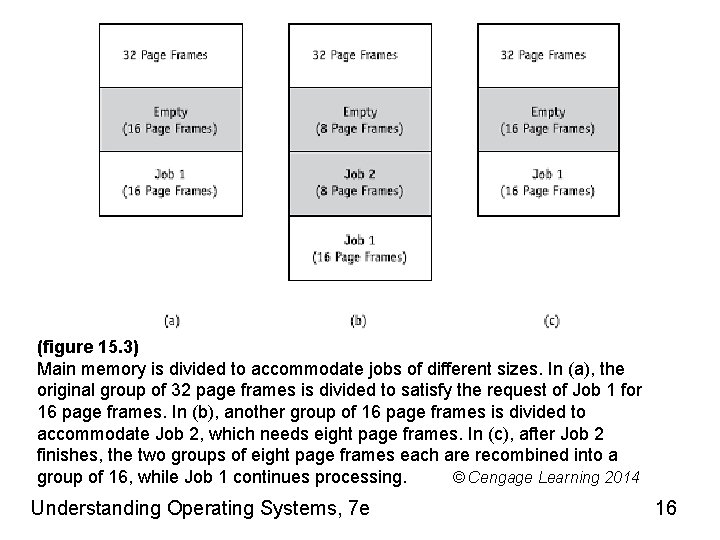
(figure 15. 3) Main memory is divided to accommodate jobs of different sizes. In (a), the original group of 32 page frames is divided to satisfy the request of Job 1 for 16 page frames. In (b), another group of 16 page frames is divided to accommodate Job 2, which needs eight page frames. In (c), after Job 2 finishes, the two groups of eight page frames each are recombined into a group of 16, while Job 1 continues processing. © Cengage Learning 2014 Understanding Operating Systems, 7 e 16

Processor Management • Uses same parent-child process management design found in UNIX • Supports “personality” concept – Allows processes from other operating systems to be executed Understanding Operating Systems, 7 e 17

Organization of Process Table • Descriptor: referencing process – Contains approximately 70 fields: describe process attributes – Includes information needed to manage process – Dynamically allocated by kernel • Process execution time – Organized by doubly linked lists • “Next run” field • “Previously run” field – Scheduler manages and updates descriptors using macros Understanding Operating Systems, 7 e 18

Process Synchronization • Wait queues and semaphores – Synchronize two processes with each other • Wait queue – Linked circular list of process descriptors – Problems solved • Mutual exclusion and producers and consumers • Semaphore structure – Three fields (semaphore counter, number of waiting processes, list of processes waiting for semaphore) • Counter contains only binary values: except if several units of one resource available Understanding Operating Systems, 7 e 19

Process Management • Linux scheduler – Scans processes list in READY state – Chooses process to execute • Using predefined criteria • Three scheduling types – Real-time processes (two) – Normal processes (one) • Process scheduling policy determination – Combination of type and priority Understanding Operating Systems, 7 e 20

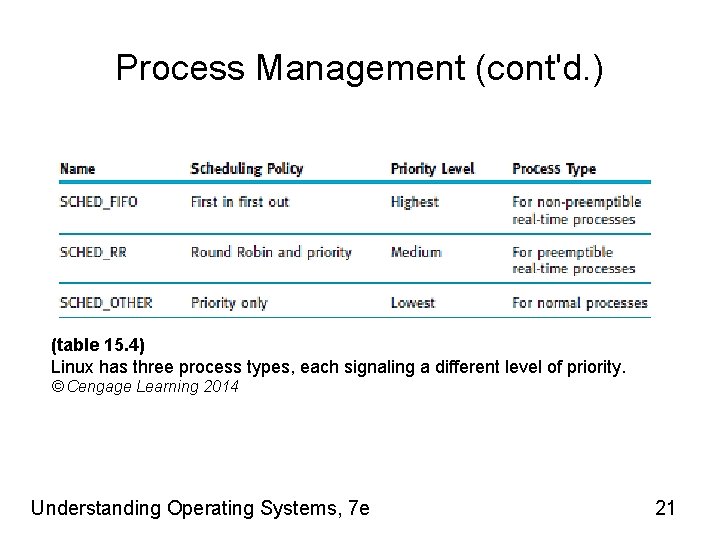
Process Management (cont'd. ) (table 15. 4) Linux has three process types, each signaling a different level of priority. © Cengage Learning 2014 Understanding Operating Systems, 7 e 21

Process Management (cont'd. ) • First type – Highest priority (SCHED_FIFO) • First in, first out algorithm – Cannot be preempted – Runs to completion unless: • Process goes into WAIT state • Process relinquishes processor voluntarily – All FIFO processes complete • Scheduler processes lower priority types Understanding Operating Systems, 7 e 22

Process Management (cont'd. ) • Second type – Medium priority (SCHED_RR) • Round robin algorithm with small time quantum – Time quantum expires • Other higher priority processes (FIFO, RR ) selected and executed: before first process allowed to complete • Third type – Low priority (SCHED_OTHER) – Executed if no higher priority processes in READY queue Understanding Operating Systems, 7 e 23

Device Management • Device independent – Improves portability • Device drivers – Supervise data transmission • Between main memory and peripheral unit • Devices assigned – Name – Descriptors • Further identify each device • Stored in device directory Understanding Operating Systems, 7 e 24

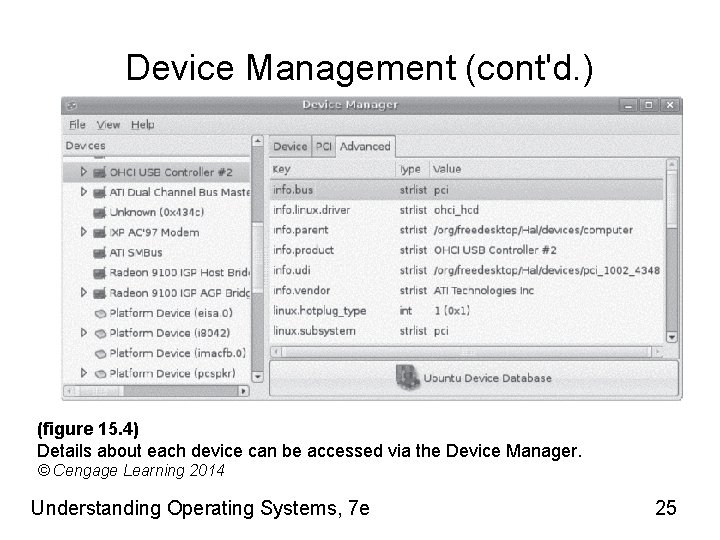
Device Management (cont'd. ) (figure 15. 4) Details about each device can be accessed via the Device Manager. © Cengage Learning 2014 Understanding Operating Systems, 7 e 25

Device Classifications • Device identification – Minor device number • Passed to device driver as an argument • Accesses one of several identical physical devices – Major device number • Index to array to access appropriate code • Configuration Table for each class – Entry point into driver – Only connection between system code and driver – Importance • Allows programmers quick creation of device drivers Understanding Operating Systems, 7 e 26

Device Drivers • Support for standard classes introduced by UNIX • Allow new device classes supporting new technology • Device classes not rigid – Creating large, complex, and multiple function drivers is discouraged because: • Users share code: wider demand for simple drivers • Modular code supports system scalability and extendibility goals – Encouraged: drivers maximizing system’s effective device usage Understanding Operating Systems, 7 e 27

Device Drivers (cont'd. ) • Notable feature – Accept new device drivers on the fly • System up and running • No reboot necessary Understanding Operating Systems, 7 e 28

Device Drivers (cont'd. ) • Open and release: functions performed when opening a device – Verify that the device is available and in working order – Increase usage counter for the device by 1: alert the subsystem that the module cannot be unloaded until its file is appropriately closed – Initialize the device: old data is removed and the device is ready to accept new data – Identify the minor number and update the appropriate pointer if necessary – Allocate any appropriate data structure Understanding Operating Systems, 7 e 29

Device Drivers (cont'd. ) • Open and release: functions (device_close or device_release) performed when releasing a device – Deallocate any resources allocated with the open function – Shut down the device – Reduce usage counter by 1 so the device can be released to another module Understanding Operating Systems, 7 e 30

Device Classes • Three standard classes – Character devices – Block devices – Network devices Understanding Operating Systems, 7 e 31

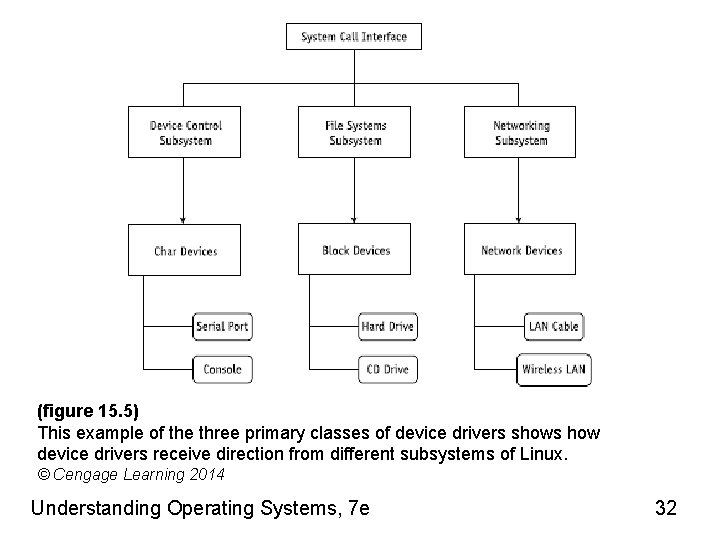
(figure 15. 5) This example of the three primary classes of device drivers shows how device drivers receive direction from different subsystems of Linux. © Cengage Learning 2014 Understanding Operating Systems, 7 e 32

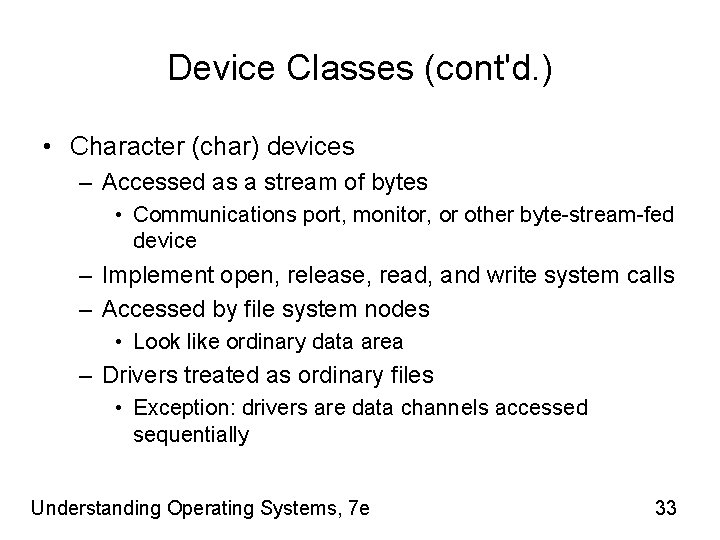
Device Classes (cont'd. ) • Character (char) devices – Accessed as a stream of bytes • Communications port, monitor, or other byte-stream-fed device – Implement open, release, read, and write system calls – Accessed by file system nodes • Look like ordinary data area – Drivers treated as ordinary files • Exception: drivers are data channels accessed sequentially Understanding Operating Systems, 7 e 33

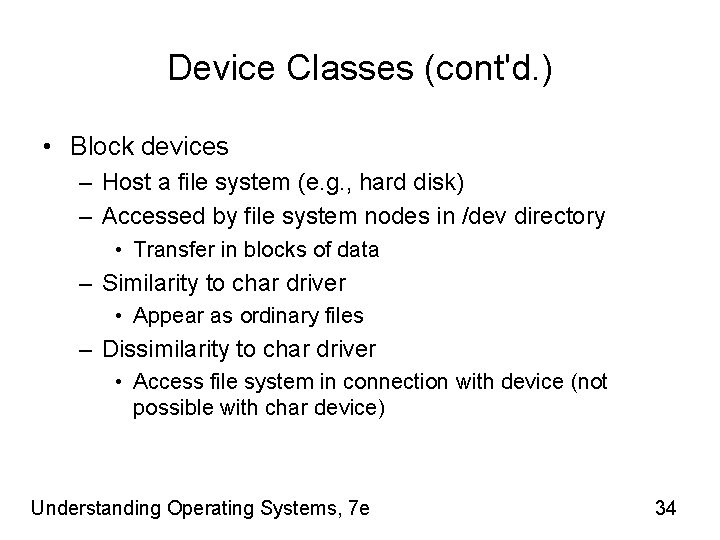
Device Classes (cont'd. ) • Block devices – Host a file system (e. g. , hard disk) – Accessed by file system nodes in /dev directory • Transfer in blocks of data – Similarity to char driver • Appear as ordinary files – Dissimilarity to char driver • Access file system in connection with device (not possible with char device) Understanding Operating Systems, 7 e 34

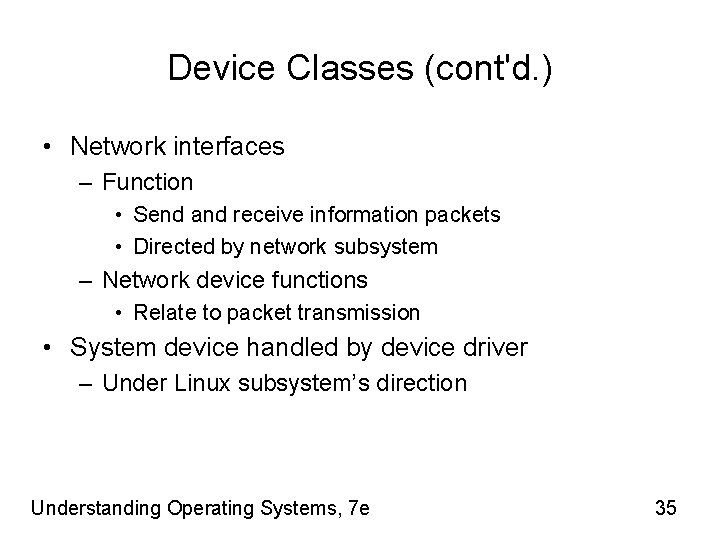
Device Classes (cont'd. ) • Network interfaces – Function • Send and receive information packets • Directed by network subsystem – Network device functions • Relate to packet transmission • System device handled by device driver – Under Linux subsystem’s direction Understanding Operating Systems, 7 e 35

File Management • Very similar to UNIX – Easy transition for programmers and administrators who are familiar with one operating system to move to the other Understanding Operating Systems, 7 e 36

Data Structures • Files organized in directories – Connected in treelike structure Understanding Operating Systems, 7 e 37

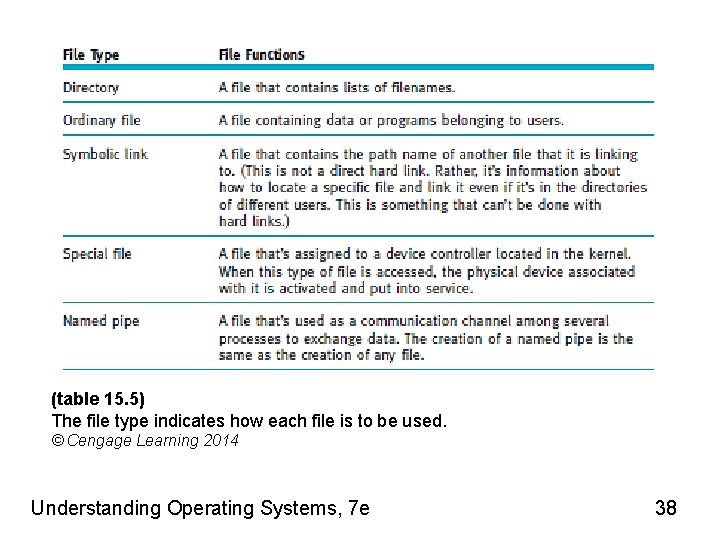
(table 15. 5) The file type indicates how each file is to be used. © Cengage Learning 2014 Understanding Operating Systems, 7 e 38

Filename Conventions • Case sensitive – Recognizes uppercase and lowercase letters • Up to 255 characters long • Contain alphabetic characters, underscores, and numbers • File suffixes: optional • Can include space – Complications if running command-line programs • File hierarchy – First slash indicates an absolute path name Understanding Operating Systems, 7 e 39

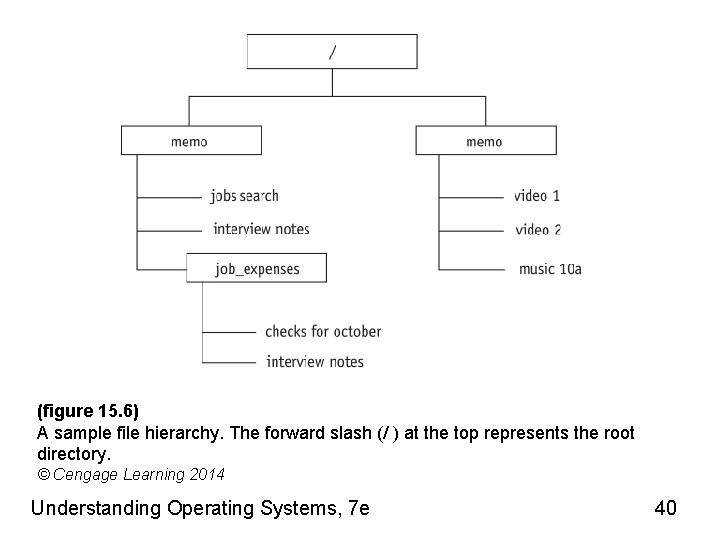
(figure 15. 6) A sample file hierarchy. The forward slash (/ ) at the top represents the root directory. © Cengage Learning 2014 Understanding Operating Systems, 7 e 40

Filename Conventions (cont'd. ) • Path name rules 1. Path name starting with slash: begins at root directory 2. Path name • One name or list of names separated by slashes • Last name on list: name of file requested 3. Two periods (. . ) in path name • Move upward in hierarchy: closer to root • Only way to go up the hierarchy Understanding Operating Systems, 7 e 41

Filename Conventions (cont'd. ) • Virtual File System (VFS) – Kernel • Allows processes to access files in a consistent manner • Maintains interface between file related system calls and file management code – Virtual file system layer • Receives process-initiated system call to files • Performs file operations independent of file system format • Redirects request to module managing the file Understanding Operating Systems, 7 e 42

New Versions • Linux operating systems: patched between version releases – Downloaded on request or – System setup checks for available updates • Patch management – Replaces or changes parts of the operating system that need to be enhanced or replaced Understanding Operating Systems, 7 e 43

New Versions (cont'd. ) • Reasons for operating system patches – Security precautions: constantly changing system threats – System compliance: government regulations regarding privacy and financial accountability – Peak efficiency • System manager must: – Maintain vigilance: security vulnerabilities – Assess patch’s criticality • If important, apply immediately Understanding Operating Systems, 7 e 44

User Interface • Early Linux versions – Required typed commands • Thorough knowledge of valid commands required • Current versions – Include powerful and intuitive menu-driven interfaces – Can still use Terminal mode • Type commands similar to those used for UNIX – Several graphical user interfaces available Understanding Operating Systems, 7 e 45

User Interface (cont'd. ) • Many Linux versions – Equipped with Windows-compatible word processors, spreadsheet, and presentation applications Understanding Operating Systems, 7 e 46

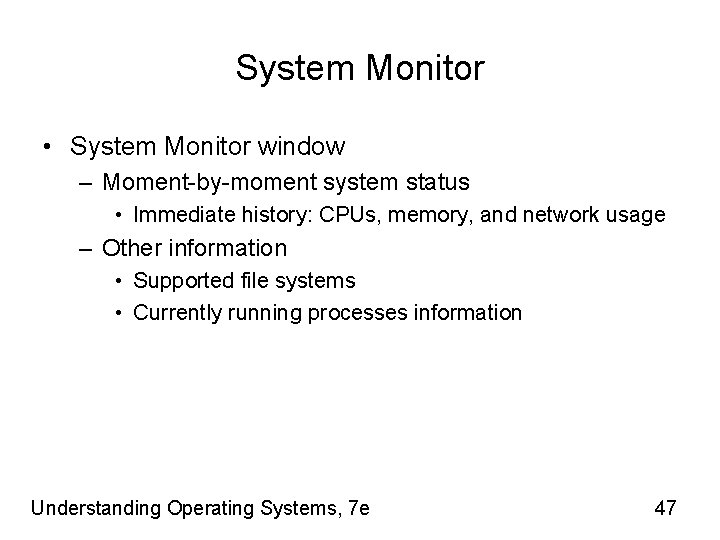
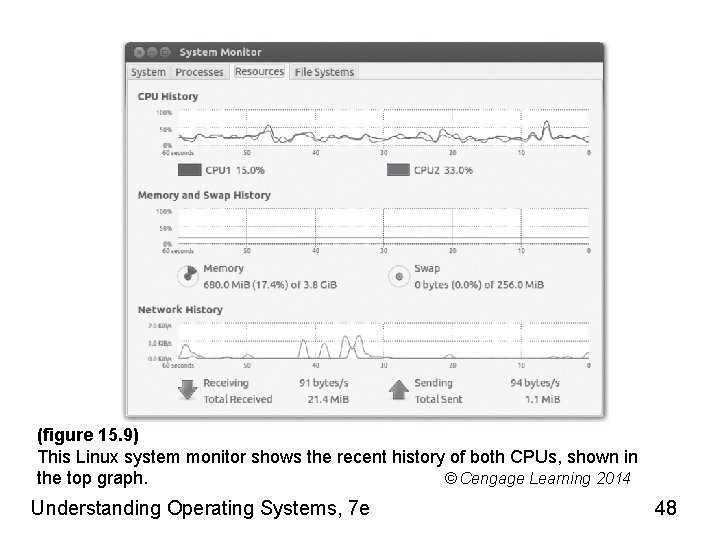
System Monitor • System Monitor window – Moment-by-moment system status • Immediate history: CPUs, memory, and network usage – Other information • Supported file systems • Currently running processes information Understanding Operating Systems, 7 e 47

(figure 15. 9) This Linux system monitor shows the recent history of both CPUs, shown in the top graph. © Cengage Learning 2014 Understanding Operating Systems, 7 e 48

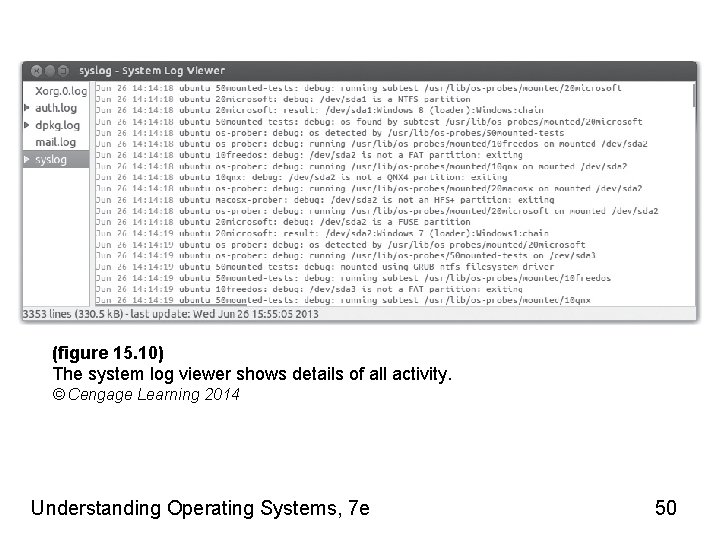
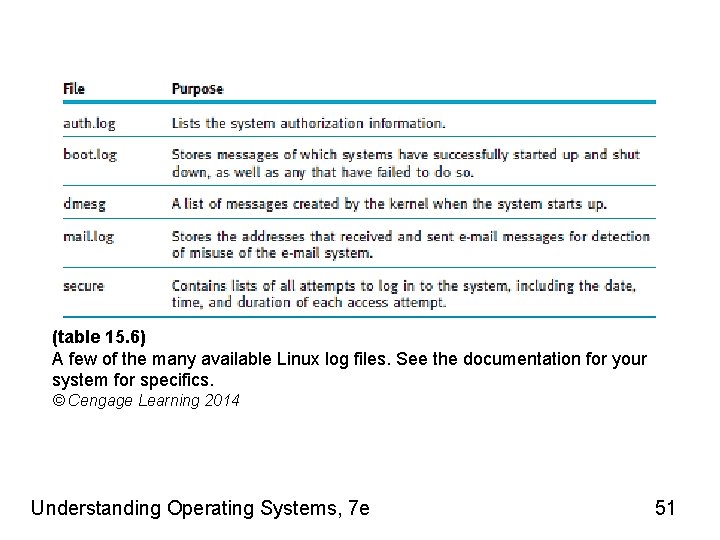
System Logs • Provide detailed description of activity on system • Invaluable to administrators – Tracking system malfunction – Firewall failure – Disabled device • Found in /var/log directory • Seen using a log viewer Understanding Operating Systems, 7 e 49

(figure 15. 10) The system log viewer shows details of all activity. © Cengage Learning 2014 Understanding Operating Systems, 7 e 50

(table 15. 6) A few of the many available Linux log files. See the documentation for your system for specifics. © Cengage Learning 2014 Understanding Operating Systems, 7 e 51

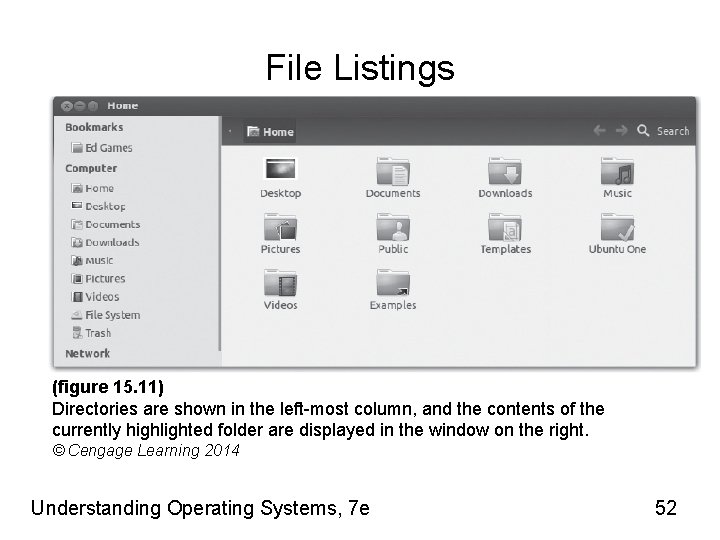
File Listings (figure 15. 11) Directories are shown in the left-most column, and the contents of the currently highlighted folder are displayed in the window on the right. © Cengage Learning 2014 Understanding Operating Systems, 7 e 52

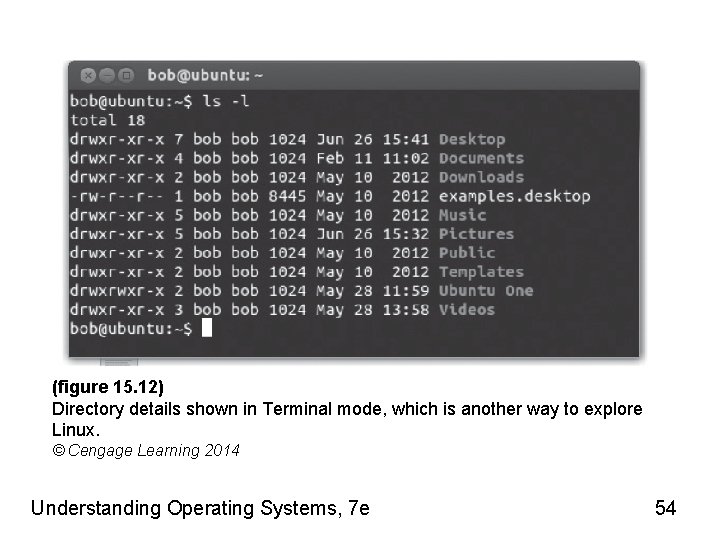
File Listings (cont'd. ) • Explore directory’s or file’s contents – Double click its icon • Establish the directory’s or file’s access control settings – Right click on item’s icon • Terminal window – Display directory details: type command ls-l Understanding Operating Systems, 7 e 53

(figure 15. 12) Directory details shown in Terminal mode, which is another way to explore Linux. © Cengage Learning 2014 Understanding Operating Systems, 7 e 54

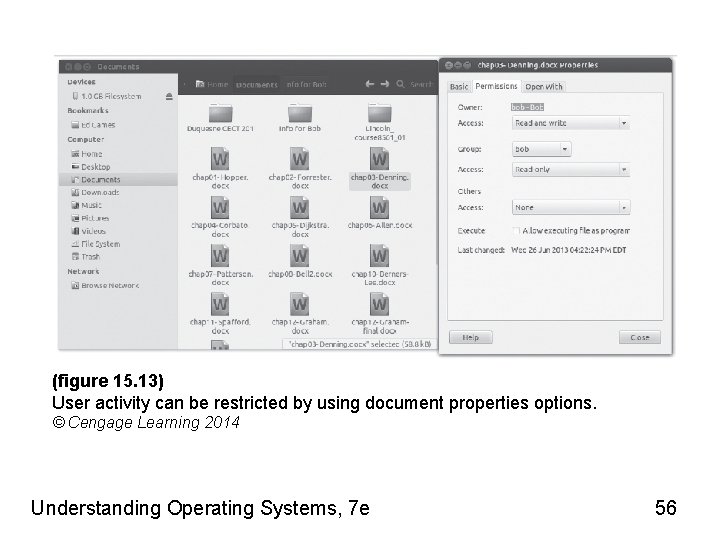
Setting Permissions • Network administrators – Full control: manage access to files and directories • Three levels of access – Owner – Group – Others • Access level settings: under properties option • Access types – Create and delete files, list files only, access files, and none Understanding Operating Systems, 7 e 55

(figure 15. 13) User activity can be restricted by using document properties options. © Cengage Learning 2014 Understanding Operating Systems, 7 e 56

Conclusion • Originally designed to gain more power from a 1990 s computer – Evolved into powerful, flexible operating system: runs supercomputers, cell phones, and many other devices • Unparalleled popularity among programmers – Contribute standard code set enhancements • Supports broad range of applications – Available for minimal cost and easy to install – Growing acceptance among non-programmers Understanding Operating Systems, 7 e 57

Conclusion (cont'd. ) • Large organizations – Commercial Linux products available • Viable marketplace player – Popularity expected to grow for many years – Android operating system foundation Understanding Operating Systems, 7 e 58